FM 34-80: Brigade And Battalion Intelligence and Electronic Warfare Operations
CHAPTER 4
Preparation For Combat
Combat support operations are organized as integral parts of combined arms operations. Maneuver, fire and IEW makeup the significant components of combat power.
This chapter describes how combat operations are preplanned to support brigade and battalion combined arms operations. It describes IEW system interface to accomplish the IEW mission and how IEW is integrated with other combat functions in combined arms operations. This chapter focuses on those activities conducted prior to combat with support from division IEW assets.
In preparation for combat, each staff section reviews the commander's mission and determines the specific task to be performed. The commander's guidance and concepts of the operation, along with individual staff estimates, provide the basis for determining brigade and battalion IEW requirements to organize the unit's contingency mission.
The brigade or battalion S2 focuses on critical intelligence and information needs dealing with enemy, weather, and terrain. He supplies the information on potential enemy forces, thereby assisting other staff elements and subordinate elements in satisfying their requirements.
The brigade or battalion S3 depends on the S2 for information needed to support EW and OPSEC. This data assists in the deployment of EW systems, the selection of OPSEC measures and the selection of possible jamming targets to support brigade and battalion OPLANs.
DECISION-MAKING PROCESS
When this mission is received, the S2 begins a preliminary analysis of the AO and enemy situation. Obtaining a copy of higher headquarters analysis is vital to support this function (see OPLAN/OPORD on specific requirements). Data is derived from a variety of sources available to division and higher echelons.
Examples are--
- Intelligence estimates of higher headquarters.
- OB books.
- Register of Intelligence Publications (RIP).
- Defense Intelligence Agency (DIA) handbook on (specific country) armed forces.
- Scientific Technological Intelligence Reports (STIR).
- DIA and Central Intelligence Agency (CIA) periodical technical intelligence reports.
- Area studies handbook (specific country).
- Foreign materiel catalog (FOMCAT).
- Division, corps, and theater intelligence products, which include intelligence estimates and OB listings.
- Theater topographic products.
- Engineer soils analysis.
- Climatic weather studies.
These data are consulted for additional information or to answer questions when developing initial estimates. The results of the initial work are provided to the commander.
The planning guidance phase consists of mission analysis, restated mission, and commanders' planning guidance.
MISSION ANALYSIS
Mission analysis ensures that the commander identifies all of the tasks required to accomplish the mission. Some tasks are specified in the OPLAN/OPORD as received from higher headquarters. Other tasks may be implied by the situation, mission, and purpose of the operation, and must be deduced by the commander during the analysis. The commander relates tasks, if possible, to the terrain or enemy.
RESTATED MISSION
The restated mission results from the commander's mission analysis. It is a clear, concise statement of the task (or tasks) to be accomplished by the command and the purpose to be achieved. Multiple tasks are normally described in the sequence to be accomplished. Many tasks may be identified during the mission analysis; however, the commander's restated mission includes only those tasks which are essential to the overall success of the operation. Tasks which are routine or inherent responsibilities of a commander are not included in the restated mission. For example, routine tasks, such as establishing liaison, or refueling of vehicles are a matter of SOP and, while important, should not be included in the restated mission. The restated mission becomes the basis of all command and staff estimates and is paragraph 1 of those estimates, whether oral or written. The restated mission is also paragraph 2 (Mission) of the command's OPLAN/OPORD.
COMMANDER'S PLANNING GUIDANCE
Commander's planning guidance is provided by the commander to the staff as required. The frequency, amount, and content of planning guidance will vary with the mission, time available, situation, information available, and experience of the commander and staff. The commander may choose to issue initial planning guidance to the staff when the restated mission is announced. This guidance is used to direct or guide the attention of the staff in the preparation or revision of staff estimates and serves to expedite the decision-making process. Initial planning guidance might include:
- Courses of action that should be addressed or disregarded.
- Unusual restrictions placed on the command.
- Considerations for the employment of nuclear or chemical weapons.
- Directions regarding deception.
- Other factors considered important.
If planning guidance is necessary, the commander must take care not to unduly bias staff estimates.
Estimate
The staff assists the commander in reaching a decision by making estimates in their assigned areas of responsibility. These estimates analyze the influence of factors within the staff officer's particular field of interest on the accomplishment of the command's mission. It also identifies factors that affect formulation, analysis, and comparison of feasible courses of action. The staff estimate concludes and recommends feasible courses of action. In making an estimate, the staff officer consults with other staff officers and agencies. The S2 is key to the estimative process at all echelons. IPB formulations concluding with a decision support template (DST), the intelligence estimate in graphic form, serve as the basis for other staff planning.
Staff. The staff estimates may be prepared mentally, orally, or in writing. Often, only the staff officer's conclusions or recommendations are presented to the commander. The intelligence estimate format is found in Appendix A. At battalion and brigade, enemy capabilities are normally drawn from the higher headquarters' estimates and restated in terms specific to the brigade's and battalion's assigned area of operations.
Commander. The commander's estimate is based on personal knowledge of the situation and estimates provided by the staff. It also contains modifications to compared courses of action and judgment on facts not known, recognized, or available. The estimate should ensure a course of action that is feasible when supported with available resources. The commander's estimate is constantly reviewed as new information is obtained.
Concept
The commander announces his decision and concept to key members of the staff. Subordinate commanders may also be present. The concept is the commander's description of the present operation. The commander normally announces his decision and concept orally to staff officers and subordinate commanders so they can execute the operation in the absence of further instructions.
Plans and Orders
Plans and orders are procedures for the commander's decision and concept. This procedure requires some compromise between speed and responsiveness and orderly procedure and detailed planning. At this point, the S2 prepares the intelligence plans and intelligence portions of OPLAN/OPORD.
Specific documents include but are not limited to--
- Intelligence Estimate.
- Intelligence Annex.
- R&S plan to the OPORD.
Detailed discussions of these documents are found in FM 101-5, Appendix G. Once approved by the commander, the OPORD/OPLAN is published and issued to the command. The next step is to supervise the operation.
The military decision-making process is illustrated below.
COLLECTION MANAGEMENT
Collection management is defined as the timely, efficient process of assigning approved intelligence requirements (including the commander's PIR and IR) to collectors in support of military operations. Principles governing collection management include--
- There is only one top priority--the commanders. All other IR are prioritized by the collection manager.
- The OB data base must be checked to ascertain if requirements can be answered immediately.
- Specific questions must be asked of collectors--they must know where to look, when to look, and what to look for.
- A higher headquarters should not be told what collector to use; the collection manager at that level is better able to determine that.
In the battalion task force and brigade, collection management is defined as limited by the principles above, and is the job of the S2 and BICC. The BICC, under the direction of the S2, prepares a complete R&S plan which is most often accompanied by an overlay. The R&S plan is disseminated as an appendix to the Intelligence Annex of the unit OPORD and updated via fragmentary orders (FRAGO).
The collection plan (Appendix A) assists the S2 in managing requirements, collection agencies, and time constraints. As such, the collection plan is dynamic and is updated continually. The collection plan format should include the following entry headings, as a minimum:
- PIR/IR.
- Indicators.
- Specific information requirements (SIR).
- A list of collection agencies.
- A place and time to report.
The plan identifies the basic information required to answer the commander's PIR/IR, indicates the collection agencies available to best satisfy the collection requirement, and identifies the timeliness and reporting procedures to be followed. Any collection requirement(s) that cannot be accomplished by organic, subordinate, or adjacent units' collection agencies are passed to higher headquarters for consideration.
The collection effort involves continuous planning, updating, and revising to satisfy the commander's PIR/IR. As PIR/IR and available collection agencies change, so does the collection plan. The collection management cycle is depicted in the following illustration.
RECEIVE AND ANALYZE REQUIREMENTS
Collection requirements and priorities are expressed in terms of PIR/IR. The most important collection requirements given to the BICC are the commander's PIR. To accomplish this support it is necessary to--
- Receive requirements.
- Determine indicators.
- Determine SIR.
- Determine reporting requirements.
Received requirements are processed by the brigade or battalion BICC in the following manner:
- They are logged into the journal. The system used is flexible or dependent upon SOP; a control numbering system, however, will ensure uniformity and an audit trail.
- The new requirements are compared to active collection requirements to ascertain if current collection missions can answer those new requirements, thereby reducing the number of collection missions assigned to already limited numbers of collectors.
- The validity of the requirement must be determined. (The commander's PIR are always valid.) Requirements generated outside the headquarters are usually accepted as valid. However, requirements levied by organizations which have the organic means of collecting that requirement will be considered invalid.
- The new requirements are then compared to the OB data base to ascertain if the required information is already available. If so, collection agencies will not be tasked, leaving them free to execute other collection missions. New collection missions should never be tasked without researching the data base.
- The requirement must then be evaluated to determine its priority of collection. For example, a battalion task force in a movement to contact has varying levels of requirements. The GSR platoon leader requires the friendly avenue of approach (or mobility corridor) more than the air defense officer needs an obstacle overlay. The most critical requirements should be satisfied first.
An indicator is any positive or negative evidence of enemy activity or any characteristic of the area of operations that points toward enemy capability, vulnerabilities, or intentions. Indicators provide the "what to look for" information required by collectors. A list of enemy indicators is found in Appendix F of FM 34-3.
Indicators can be specified by location through the use of NAI. An NAI is any point or area on the ground, usually along an avenue of approach or mobility corridor, where activity (or lack of activity) will confirm or deny a particular enemy course of action. The S2 depicts NAI on the event template, thus using it as a collection tool. In fact, the event template is the vital link between the collection effort and IPB, because NAI specify the "whereto look" information required by collectors. NAI can be numbered, named, or lettered.
Determining SIR is a function of the BICC. SIR are the basic questions that need to be answered to confirm or deny the existence of an indicator. Essentially, SIRS are indicators in question form in sufficient detail to be the basis for tasking collection agencies. For example, as an indicator of possible enemy intentions, the locations of air defense units are needed. An SIR would be a question, asking whether or not there are any ZSU-23-4s at location X. Medium air defense guns are displaced forward prior to the attack to protect assault forces and to facilitate forward displacement during the attack. ZSU-23-4s protecting the regimental artillery group (RAG) are approximately 1.25 KM to the rear of the FLOT. After SIR have been prepared, the S2 incorporates them into the collection effort.
Like PIR, SIR should be assigned priorities. Remember that the commander's PIR are always the highest priority collection requirements. The primary basis for determining the priority of any requirement is its criticality to the friendly mission accomplishment and the time and information is needed (or will no longer be of value).
Reporting requirements specificy when, where, and in what detail information is reported. Reporting requirements are developed in terms that are understandable by collection units or agencies. The collection manager must speak the language of the HUMINT, IMINT, or SIGINT collector. The purpose is to provide the collection agency with specific collection and reporting requirements which ensure that the right data is collected and reported promptly to the appropriate user. (Where to look, when to look, and what to look for.)
Unit SOP should outline the reporting requirements, to include report format, frequency of reports, and methods of transmission. Requirements are based on the needs of the requester.
DETERMINE RESOURCE AVAILABILITY AND CAPABILITY
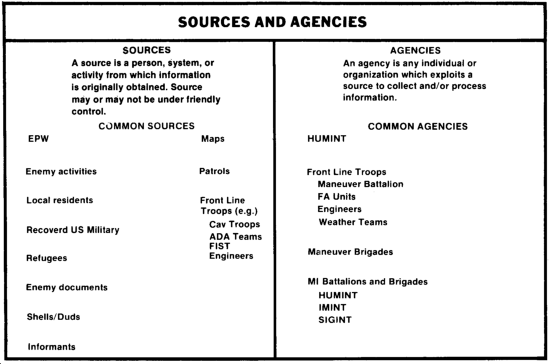
The selection and tasking of organic and supporting collection units and the formulation of requirements for higher echelon support require a basic knowledge of the units, agencies, and sources that can provide information by the S2/BICC. The following chart defines sources and agencies and lists what units and activities fit into each category. Usually, only capable agencies will be tasked; rarely will a collection manager task a source directly. Sources and agencies are explained below.
The capability and requirement correlation matches the collector to an SIR. For example, to locate a ZSU-23-4 air defense-related radar, the tasking would be submitted to a unit capable of collecting radar signals (ELINT) or a unit or agency capable of seeing or imaging a ZSU-23-4 (aerial scouts or IMINT). This understanding of capability eliminates tasking an incapable collector. For example, a SLAR mission would be inappropriate to locate the whereabouts of the enemy commander. The collection manager specifies the most capable collector. There may be several collectors capable of answering an SIR; the collection manager must choose those collectors most capable of collecting the SIR. The specific elements of the capability and requirement correlation are--
- Range-to-target location. (Consider the tactical employment of collectors and the range of the collectors, usually from the FLOT.)
- Time available should be compared to the historical or estimated response time of the collector. The period begins when an information request (PIR or IR) is received and concludes when the information is received by the requester. Times required to complete each event should be calculated or estimated from each available collector based on the tactical situation and local SOPS. The S2/BICC must ensure that communication media times and priorities are considered. Often, timeliness can only be derived from experience.
- The technical characteristics of each collector must be examined in detail to ensure that the collector has the technical capability to perform the mission. The S2 should not hesitate to refer to the DOD Sensor Capabilities Handbook which provides information on the technical characteristics of collectors. Location by IMINT/HUMINT sensors is very accurate; however, the ESM/SIGINT sensors may not be as accurate as IMINT/HUMINT. The local weather conditions can affect collection capability and exploitation of data collected. Weather support can be obtained from the USAF staff weather officer (SWO) at division or from the artillery meteorological sections. Another source at brigade and battalion level is the forward area limited observing program (FALOP) or "belt weather kit".
- Collector vulnerability to the anticipated threat depends on the collector. Penetrating collectors, such as patrols, are the most vulnerable.
- The local terrain with its potential LOS limitations will affect the LOS capabilities of given types of collection systems (such as SIGINT and GSR).
The above factors must be matched or correlated to determine the proper or capable collector. Although a collector may be evaluated as capable, the collector may not be physically available for the mission. For example, if it's determined that an aircraft photo mission is the most capable collector, the collection agency to which the collector is organic could respond that no aircraft are available because of maintenance, adverse weather, or existing requirements of a higher priority. The next most capable collection agency would then be tasked to execute the collection mission.
The brigade or battalion S2, in conjunction with the S3, determines selection of collection resources based on their unit's primary mission, outstanding collection requirements, and that collection resource's ability to collect SIR. Combat and combat support units constitute the primary collection capability of the maneuver brigade and battalion task force (BTF). The brigade may have multidisciplined MI collection support available; however, the BTF relies primarily on maneuver and fire support elements, which are controlled by the S3.
The collection manager should use one collection agency to cue another when possible. For example, a communications intercept may detect and determine the approximate location of an enemy battalion's CP. The collection manager can then effectively use other collection systems to pinpoint the location. He must plan and coordinate the use of cuing and confirming systems against priority targets. The unit SOP, however, should specify standard cuing and confirming relationships and procedures for coordination of these collection agencies.
The collection manager also uses a selected redundancy and resource mix against high-priority targets. Redundancy is the use of multiple agencies with known capabilities to provide information concerning a single target or SIR. Similarly, the collection manager may employ a mix of collection agencies with different capabilities to exploit the different signatures of a target.
Various procedures may be used to select the collection agencies capable of SIR. One format is the asset evaluation worksheet (AEW). The purpose of the AEW is to determine the capability of a collector to satisfy SIR. When the AEW is completed and the collectors identified as fully or marginally capable, those assets are applied to the collection plan beside the SIR they could possibly supply.
Devising a collection strategy includes resource integration, cuing, collector mix, and redundancy. Resource integration enhances the efficiency of the overall collection effort. The collection manager must attempt to integrate new collection requirements into current missions, which offers three benefits:
- Employs the fewest number of collectors.
- Decreases cost and risk.
- Increases the utilization of overall collection capacity available.
The result is increased productivity. Before requesting additional missions, however, the collection manager must consider three factors: present operating missions, scheduled future missions, and new tasking requests. The S2/BICC should, as a rule, task those agencies under his control first before requesting collection missions from higher or adjacent units.
Cuing is the use of one collector to provide necessary targeting information to direct collection by a more accurate point-target system.
Collection against a target requires using a combination of collectors. This may be justified against high priority targets when the probability of intercept by any one system is less than 100 percent. Examples are air defense (AD) units and CPs.
TASK COLLECTION RESOURCES
Following selection of collection agencies, intelligence requirements tasking is prepared. The tasking of organic agencies is accomplished according to command SOPs but is normally accomplished through the use of the R&S plan at the brigade and battalion levels. Tasking of agencies controlled by higher headquarters must be submitted through proper channels and requires justification. Issuing specific orders and requests (SOR) depends entirely upon command relationships. For example, a battalion S2 can initiate patrolling missions by the authority of the battalion S3. The line companies must provide the patrols to execute the orders from battalion. On the other hand collection missions stated to higher headquarters are requested, not tasked.
The key to successful tasking of collection missions is in remembering which echelon is involved. Lower echelons "ask" or request from higher, and higher echelons "tell" or task the lower ones. The standard collection asset request format (SCARF) is used for intelligence requirements tasking and for requesting information from higher or adjacent headquarters. The SCARF can be used for all intelligence disciplines. It specifies the following: the information needed (what to look for); where and when to look for the movers, shooters, sitters, and emitters; and when the information is needed. In some cases, a collection means may be recommended. For additonal information on the SCARF, refer to Appendix A and Chapter 3 of FM 34-1.
The S2 coordinates all taskings with the S3 for those collection agencies organic to the battalion or brigade. This coordination ensures that the collection taskings are compatible with, and support, the current scheme of maneuver and future operations. Units assigned, attached, or supporting the brigade or battalion, except for MI units, are tasked through the operations (S3) channels. Intelligence tasking channels for potential IEW resources supporting brigade and battalion collection missions were outlined in Chapter 2.
Another method of tasking is through the use of the brigade and battalion OPLAN or OPORD. If an intelligence annex is not published with the OPLAN or OPORD, tasking instructions may be included in paragraph 3 of the OPLAN or OPORD. Tasking instructions are as follows:
A further explanation of OPLAN and OPORD is given later in this chapter.
EVALUATE REPORTING
Collection management is a dynamic process that does not end with tasking. The BICC must monitor collection and reporting to ensure that collection agencies respond to assigned collection missions and report their results to designated users in a timely manner.
UPDATE COLLECTION PLAN
The BICC continuously updates the collection or R&S plan in response to changing requirements. It purges the plan to eliminate requirements that have been satisfied or are no longer needed, due to changes in the situation.
The S2 integrates new requirements according to priorities, changing the priority, or eliminating old requirements when necessary.
A formal R&S plan is normally prepared as part of the S2's intelligence planning process at battalion and brigade levels prior to combat. A collection plan may also be prepared informally at the brigade level to help define the numerous tasks and collection agencies applicable to brigade collection operations. This collection plan serves as the basis for the development of the R&S plan which is an appendix to the Intelligence Annex to the OPLAN or OPORD. Once engaged in combat, this collection plan is updated as required.
IEW TASKS
IEW operations, in both peace and war, support the winning of campaigns and batties. The mission of IEW operations is to provide the combined arms commander with three forms of support: intelligence, counterintelligence, and EW.
The combined application of these forms of support, the IEW mission, translates into four major tasks: situation development, target development, CI support, and EW.
SITUATION DEVELOPMENT
The situation development process provides to commanders the intelligence data they need to plan and conduct combat operations. This process incorporates the intelligence cycle and IPB functions.
Situation development enables commanders to see and understand the battlefield in sufficient time and detail to employ their forces and weapons systems effectively. In situation development, the S2 uses IPB to produce a description of enemy force dispositions on the battlefield in terms of location, size, type, direction, rate of movement, and activity. This portrayal is based on an analysis of intelligence data which is continuously updated through the collection and processing of information.
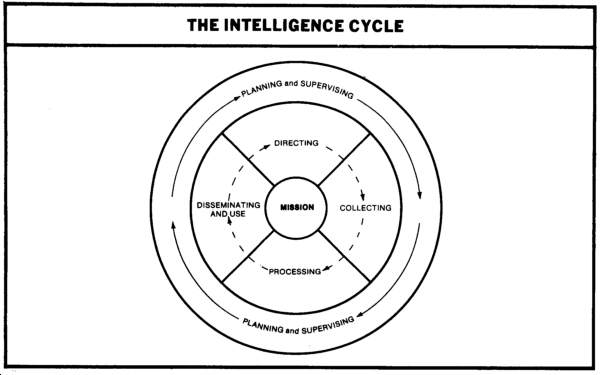
Intelligence Cycle
The intelligence cycle consists of four phases: directing, collecting, processing, and disseminating. It is a continuous process, and each phase is conducted in sequence. However, all phases are being conducted concurrently. While new information is being collected, the intelligence staff plans and redirects efforts to meet new demands, while previously collected information is processed and disseminated. All phases of the cycle focus on the commander's mission. The intelligence cycle is illustrated below.
Directing. The commander, through the S2, directs the intelligence effort. The S2 translates the commander's guidance and concept of the operation into intelligence requirements and established priorities. Intelligence requirements and priorities are expressed in terms of PIR and IR. These terms are defined as shown below.
Collecting. This is the process of gathering information from all available sources. Collection operations are guided by the commander's requirements and are facilitated by use of the collection plan and IPB.
Processing. This is the phase of the intelligence cycle whereby information becomes intelligence. Information from all sources is evaluated, correlated, and analyzed to produce a current all-source assessment stating the enemy's current dispositions, capabilities, and most probable course of action.
Dissemination. The dissemination and use of intelligence is the last and most vital step of the intelligence cycle. Usable information and intelligence is distributed to those who need it.
Most information is used in the development of intelligence, and can often be used immediately for fire, maneuver, or ECM. When raw data can be used as received for fire, maneuver, or ECM, with no interpretation or integration with other data, it is combat information.
Combat information is further defined as unevaluated data gathered by, or provided directly to, the tactical commander. Due to its highly perishable nature or the criticality of the situation, combat information cannot be processed into tactical intelligence in time to satisfy the user's tactical intelligence requirements.
Once raw data (including combat information and ESM) is validated, integrated, compared, and analyzed, it becomes intelligence. In other words, the difference between intelligence and combat information is in the method of handling the data. If the information must be processed and analyzed, it is intelligence and not combat information. Information may be both combat information and intelligence.
Intelligence Preparation of the Battlefield
IPB is an important function in situation development. It is an excellent tool for preparing for combat. It provides a guide to the commander and his staff in determining where and when to use available resources to achieve decisive results based upon expected dispositions.
The brigade S2 initiates intelligence operations by developing an intelligence data base, which is applicable for each potential area in which a unit may be required to operate. The BICC acquires the required data, and using IPB methodology, converts it into graphics that can be readily used by the brigade and battalion commanders and staffs. Brigade and battalion BICCs are not sufficiently resourced to perform formal IPB without assistance from higher echelons. They request IPB products from the division all-source production section (ASPS), which they refine to satisfy their commander's needs based on their specific assigned area of operations, mission, and PIR or IR. They do, however, use IPB methods to record and analyze information about the enemy, weather, and terrain that the commander and staff needs for planning, decision making, and the conduct of combat operations.
In preparation for combat, IPB is conducted based on assigned missions. It supports the planning and execution of most other battlefield functions, as well.
IPB is a vital function of situation development. Actually, it is the key to preparing for combat. Today's intelligence must enable the commander to "see" the battlefield in all its aspects: graphically, red depicts the enemy, white shows the terrain and weather, and blue portrays friendly forces.
IPB provides a mode that ensures uniformity in how intelligence personnel within each echelon of command are to analyze weather and terrain and evaluate the effects of each on enemy and friendly courses of action. Commanders must make more complicated decisions than ever before. Therefore, each commander needs timely and accurate intelligence that will aid his decision-making process.
IPB is the continuous and systematic process of evaluating the enemy, weather, and terrain for a specific battlefield area. IPB provides the basis for a dynamic R&S plan and a guide for the effective employment of collection, reconnaissance, and surveillance assets. Through the systematic process, all the battlefield's elements can be incorporated into easily understood graphic products. IPB graphics are communicated through the use of templates and multi-layered overlays. These graphic data bases provide a basis for situation and target development.
The IPB process and the associated products have applications across a broad continuum of operations. Terrain analysis, integrated with knowledge of how a specific foe would like to fight, can provide likely areas on the battlefield where intelligence operations can be focused to determine enemy courses of action. Likewise, terrain and weather analysis can be used to support friendly OPSEC operations, allowing for optimum siting of units to deny the enemy vital intelligence.
IPB is the link between intelligence operations and airland battle doctrine. By integrating the airland battle with the IPB process and carrying it over to intelligence operations, the airland battle can be won. Intelligence is vital to the successful conduct of the airland battle. The commander must know where the enemy is and know the best point to engage him in order to win the next battle.
IPB is "homework" that each echelon must accomplish before the battle begins. Through IPB, gaps in the intelligence data base become readily apparent. Thus, through collection management, requirements can be fulfilled before the first shot is fired.
IPB analysis provides a basis for planning and executing the battalion and brigade battles. It helps the commanders to visualize the battlefield--where friendly and enemy forces can move, shoot, and communicate; where the critical areas of the battlefield are; and where enemy systems become most vulnerable to attack. It helps the S3s to determine where the battalion and company teams can be employed to take maximum advantage of the terrain, and where and how the terrain can best be reinforced. It guides the S2 concerning when and where to employ collection systems for maximum effectiveness. It also provides a basis for analyzing collected information to determine enemy intentions.
The products developed through IPB are used to support many battlefield functions. IPB is most valuable to commanders and operations officers, allowing the commander to better track and predict enemy movement, and interdict and target enemy units. IPB, also referred to as the intelligence estimate in graphic form, enables the commander to make better decisions regarding operations and planning.
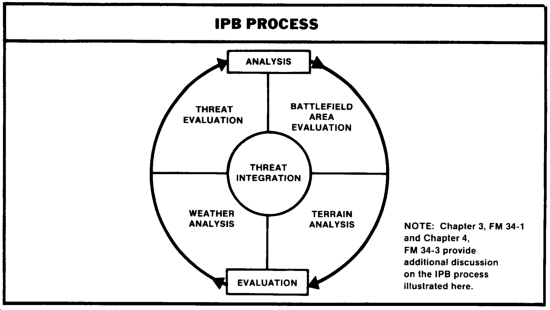
IPB, as illustrated, is a continuous and systematic process performed for a specific geographic area. It consists of five functions or steps. Step 1 is the battlefield area evaluation. Steps 2 and 3 are the analysis of the terrain and weather. Step 4 is an evaluation of the Threat forces expected to be found operating in the battlefield area. Step 5 is the nucleus of IPB where Threat forces (red) are integrated with the weather and terrain (white) and friendly operations (blue). This combination of red, white, and blue into final graphic products aids the commander's decision-making process in the areas of--
- Battlefield area evaluation.
- Terrain analysis.
- Weather analysis.
- Threat evaluation.
- Threat integration.
NOTE: Chapter 3, FM 34-1 and Chapter 4, FM 34-3 provide additional discussion on the IPB process illustrated here.
The battlefield area evaluation function of IPB must be performed first. Terrain and weather analysis and threat evaluation may be performed concurrently or in sequence, since all three are equally important. For example, a unit assigned a mission might first need the evaluation of the areas of operation and interest. The key is to use the IPB process to satisfy the mission. But keep in mind that the first four functions or steps must be completed before Threat integration can be accomplished.
However performed, one of the significant benefits of IPB is that the framework is complete before the battle begins. Since it is paramount that the first battle be won, IPB must be conducted and constantly updated before the conflict begins.
The first function of the IPB process deals with an evaluation of the battlefield area; for example, the areas of operation and interest. It is within these areas that the battles will be fought. The AO is defined by higher headquarters. Commanders select their own areas of influence and interest. The following illustrations depicts the areas of operations and interest.
This function involves filling in the time and space framework of the Threat model and can be referred to as thinking "white". This creates an organizational structure for the Threat model and identifies the impact of the environment on the enemy (red) and friendly (blue) units. We need to be able to think about the environment in two basic modes: time and geography.
Commanders must be able to "see" the battlefield in terms of the dimensions of depth, width, height (airspace), and time. These dimensions are examined in light of the defined areas of operations and interest. As a result, PIR are developed by the commander (that is, his highest priorities).
In terrain analysis, the military significance of terrain is analyzed in detail to determine how it affects friendly and enemy capabilities, vulnerabilities, and courses of action. To be successful, a combat force must be able to move, shoot, and communicate. Thinking "white" is used when considering environmental effects on battle outcome, regardless of whether it is the enemy or friendly force. In other words, rarely does the terrain change.
Terrain includes natural features, such as mountains, forests, rivers, and manmade features, including cities, highways, and cultivated areas. Terrain usually dictates how the battle will be fought.
Terrain analysis is one of the most critical and important steps of IPB, since commanders must use terrain to site weapon systems, minimize vulnerability to enemy fires, canalize enemy movement, and protect vital lines of communication (LOC).
Regardless of who does the work, there are certain aspects of terrain analysis that apply in all areas. Commanders and their S2s must have information on observation and fields of fire, concealment and cover, obstacles, key terrain, and avenues of approach and mobility corridors (OCOKA), to be successful in their missions.
Basic topographic maps serve as the foundation for terrain analysis. Depending upon the map editions and the actual terrain, the information contained on each may may not be totally accurate. They do, however, depict elevations, road systems, towns, waterways, depressions, and other vital terrain information. Topographic maps provide a wealth of good information. Layer tinting, or presenting elevations in different colors, is a technique that can be used for LOS.
The S2 should not rely solely on map reconnaissance. Visually observing the terrain will add another dimension to terrain analysis. If this is not possible, discussion with scouts, OP and listening post (LP) personnel, reconnaissance patrols, and GSR teams will establish more credibility with the commander and staff.
The S2 does not have the organic capability to produce the detailed products necessary to support the terrain analysis process. The S2 can request terrain support or products from the division's terrain team. These teams have personnel trained and equipped to create the detailed terrain products called terrain subfactor overlays. These overlays--not templates--present detailed information for specific areas.
Should the terrain team (or its products) not be available, the S2 should develop a system or technique for terrain analysis. This should include--
- Establishment of a terrain data base and identification of intelligence gaps.
- Development of terrain subfactor overlays based upon different times of the year.
- Development of combined obstacles overlays.
- Identification and analysis of avenues of approach and mobility corridors.
- Consideration is to analyze the terrain from both offensive and defensive standpoints.
Although the terrain doesn't change, defending a battle position is different than a movement to make contact with an armor unit. The same terrain may be viewed differently. The numbers of overlays will depend upon factors of METT-T.
Terrain cannot be analyzed without taking the effects of weather into consideration. During Step 3, climatic data and weather for the AO are analyzed to determine their effects on friendly and enemy operations. Historic weather data and weather subfactor overlays are integral parts of the intelligence data base. The close relationship between terrain and weather in a tactical environment make Steps 3 and 4 inseparable.
The five military aspects of the weather that concern intelligence support to operation planning are: temperature and humidity, precipitation, winds, clouds, and visibility. The tactical significance of these aspects, and the risk or opportunities they present, depend upon knowledge of weather data acquired and the significance of the effects of weather elements on Army user operations.
The S2 can obtain weather support from the division's SWO, the division's artillery meteorological section, or from their own assets. The FALOP or "belt weather kits" provide the S2 with the organic capability to gather existing weather data.
There are numerous weather subfactor overlays that can be developed. For example, for the brigade commander on the demilitarized zone (DMZ) in Korea, an ice thickness overlay would be extremely important. Weather overlays are used to augment the more traditional weather products such as light data tables and climatic summaries.
Weather is critical to Army tactical operations. Reliance on mobility requirements for thoroughly integrated air and ground operations, and the need to see and attack deep into the battlefield, may be affected significantly by prevailing weather conditions. Complex weapon and support systems frequently depend on favorable weather conditions for accuracy and effectiveness. Virtually every operation, every piece of equipment, and every person on the battlefield is affected by the weather. Commanders plan to take advantage of weather conditions favorable to the mission. Similarly, they plan operations to minimize the adverse effects of the weather.
Threat evaluation focuses on the specific enemy force expected to be found operating in the battlefield area. To adequately evaluate the Threat, the analyst must think like the enemy. That is, he must see the battle through the enemy's eyes. The analyst begins to create a baseline threat model by building an OB data base. Although a data base usually exists, none is totally complete. The data base should be established around the nine OB factors: composition, disposition, strength, tactics, training, logistics, combat effectiveness, electronic technical data, and miscellaneous information. Chapter 3, FM 34-3 contains a detailed discussion of OB factors.
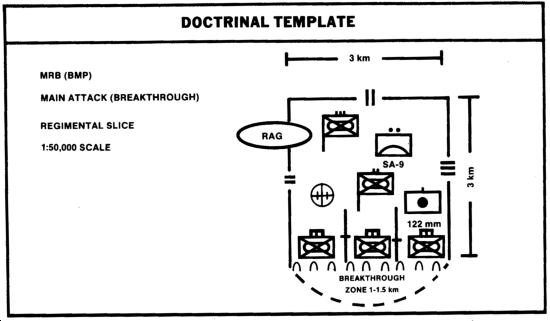
As much of the written data as possible is then portrayed graphically in the form of doctrinal templates. Steps 1 and 5 of the IPB process are accomplished through the analytical technique known as templating, or converting written data into graphics. Templating itself can be thought of as a visual OB data base, and thus is another technique of "cataloging" information on the enemy and the environment. OB factors, to include formations, frontages, depths, equipment numbers, and HVT are types of information that can be displayed on doctrinal templates. Doctrinal templates depict enemy doctrinal deployment for various types of operations without the constraints imposed by the terrain and weather. In other words, if the world were flat, with no terrain or weather, the enemy could deploy units exactly as desired; however, such is not the case. Practically any situation, unit, formation, or rate of movement, or such features as petroleum, oils and lubricants (POL) points and ADA systems, can be doctrinally templated.
Examples are, an MRR in a hasty river crossing, ZSU-23-4 deployment, MRB in the defense, MRD in the attack of a defending enemy, an MRB in pursuit, and so on. This is only a sampling of the doctrinal templates the S2 can produce. Depicted below is a type of doctrinal template.
The last function of the IPB process is the integration of the Threat with the weather, terrain, and friendly operations. Threat doctrine is examined in relation to the existing situation and to the constraints imposed by the weather and terrain. By doing this, the analyst is able to determine how the Threat forces will probably fight.
Friendly courses of action are also integrated with the effects of the terrain and weather and anticipated enemy courses of action. This assists the commander in selecting a friendly course of action.
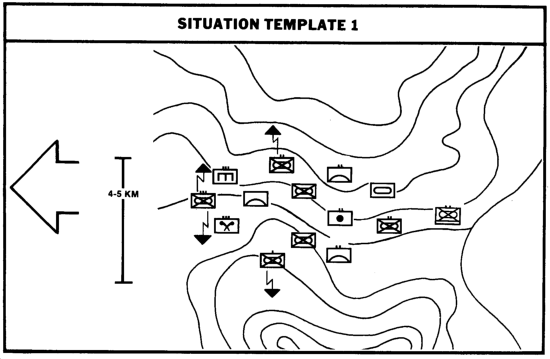
Through the use of situation templating, the enemy's doctrine is integrated into the constraints created by the weather and terrain for a specific battlefield area. The situation template is basically a doctrinal template with terrain and weather constraints applied. It is produced by placing a doctrinal template over a selected mobility corridor or specific terrain configuration and noting how the enemy force must modify its doctrinal configuration to account for environmental constraints.
The analyst uses military logic to fit the enemy force to the terrain as closely as possible. As an enemy force moves along a particular area of the battlefield, it will be required to do certain things at certain places which are dictated by weather, terrain, and tactical doctrine.
The situation template shows how Threat forces might deviate from doctrinal dispositions, frontages, depths, and echelon spacing to account for the effects of the terrain and weather.
The following illustrations are examples of situation templates. Note how unit dispositions have been adjusted and frontages compressed.
A doctrinal template of an MRR is overlaid on subject terrain. Obviously, doctrinal frontages and unit configurations do not fit the confines of the subject terrain.
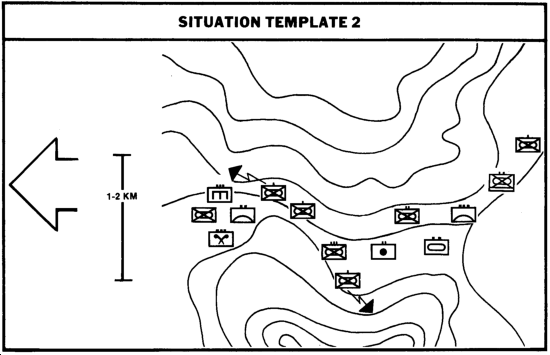
As enemy forces move along mobility corridors, their actions continue to be influenced by terrain and the tactical situation. Since this movement is sequential, situation templates are sequential snapshots of how the enemy might look as the force progresses.
Unit distances and frontages are adjusted, but kept as close to doctrine as possible with relation to the subject terrain.
In order to generate hypotheses concerning the enemy and environmental effects on the friendly mission, it is important that the S2 know the commander's mission so that the information needs can be anticipated, identified, and understood. This involves more than "knowing" the mission. To "understand" the mission, the S2 must think like the commander. That is, he must know how the friendly unit is organized and equipped, as well as friendly tactics and battlefield functional systems. Once this. is known, a hypothesis as to the impacts of the enemy and environment can be assessed.
Situation templating is a basis for event templating. Event templating is the identification and analysis of significant battlefield events and enemy activities which provide indicators of the enemy course of action. As the enemy force moves along a mobility corridor, critical areas become apparent. These areas are significant because, within them, significant events and activities will occur. It is within these areas that targets will appear. These areas are identified as NAI, An NAI is a point or area along a mobility corridor where enemy activity or lack of activity will confirm or deny a particular enemy course of action.
NAIs facilitate intelligence collection, reconnaissance and surveillance, and analysis because--
- Attention is focused cm areas where the enemy force must appear if it has selected a particular mobility corridor.
- Significant military events can be framed by time and location within NAIs.
- Events in one NAI can be compared to events occurring in NAIs of other mobility corridors as the basis for determining enemy intentions.
- Information thresholds can be assigned to each NAI, which alert the analyst that the expected action is confirmed or not confirmed within the time limit set.
- Events within NAIs can be analyzed for indicators against which intelligence and target acquisition resources can be directed or redirected as required. NAIs are a basis for collection and R&S planning.
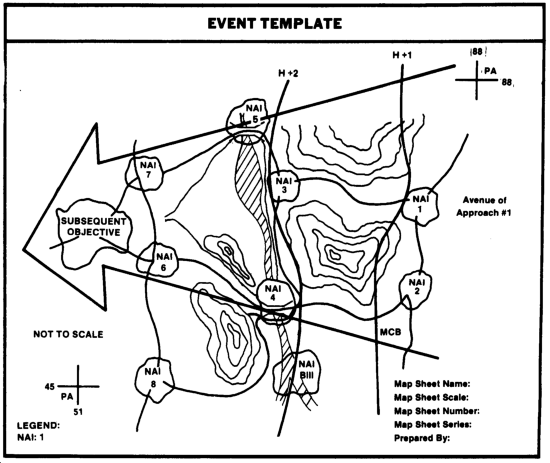
The third of four templates produced during the IPB process can be created at this point. The event template is nothing more than a collection of NAIs which are time-related, logically sequenced indications or events based on a series of situational templates. The NAIs will determine what you are looking for, and generally when and where to look.
Thus, event templating is the vital link between intelligence collection requirements and the commander's intelligence needs.
The following illustration is an example of an event template. NAIs numbers 1 through 9 are areas where particular types of activity would provide indications of intent.
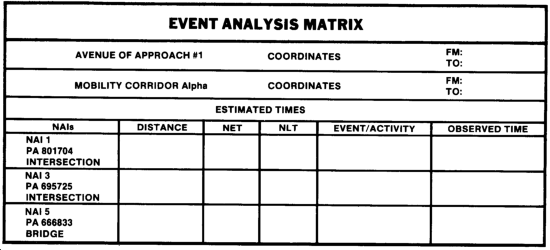
The event analysis matrix (EAM) is another IPB tool used in conjunction with collection and R&S management. An event analysis matrix is developed for each mobility corridor. Based on terrain constraints and enemy doctrinal rates of movement, estimated times between NAIs can be computed. For example, using the previous illustration, the distance between NAI 1 and NAI 3 is 7 kilometers. Time phase lines (TPLs) graphically depict estimated enemy movement rates. Using a covering force rate of movement of 6 kilometers per hour, the estimated time between these NAI is 70 minutes (1 hour 10 minutes).
The EAM assists in the collection by specifying the "when to look" information required by a collector.
Through the use of both the event template and the event analysis matrix, the S2 can direct assets to the NAI at the right time to observe enemy acts and events. Both of these tools will confirm or deny enemy intentions by location and time. Depicted below is an example of an EAM. Note the NET (not earlier than) time and NLT (not later than) time. The observed time column allows for adjusting enemy rates of movement and estimated times in subsequent NAIs.
The matrix enables the analyst to more precisely correlate what event or activity is expected within the geographical location and at what time the event is expected to take place. This capability, along with doctrinal and situation templates, provides the basis for critical node of HVT analysis. The estimated times between NAI within a mobility corridor are derived from determining the effects of terrain and normal seasonal conditions on doctrinal rates of advance. The event template and EAM allow for the initiation of precise collection requirements, maximizing the use of limited collection assets against the vast array of potential targets on the future battlefield. By knowing in advance what the enemy can do and by comparing it with what he is doing, the analyst has the basis for predicting what the enemy intends to do next. Such information provides the basis for constructing decision support templates.
Intelligence products are the "output" of the IPB activities. To produce usable products, it is necessary to know what the various users require, the detail required, and in what format. Up to this point in the IPB process, a number of products have been created. For instance, the doctrinal templates created during threat evaluation were essentially for intelligence use. The event template can be used by all collection managers, and by the collection agencies themselves.
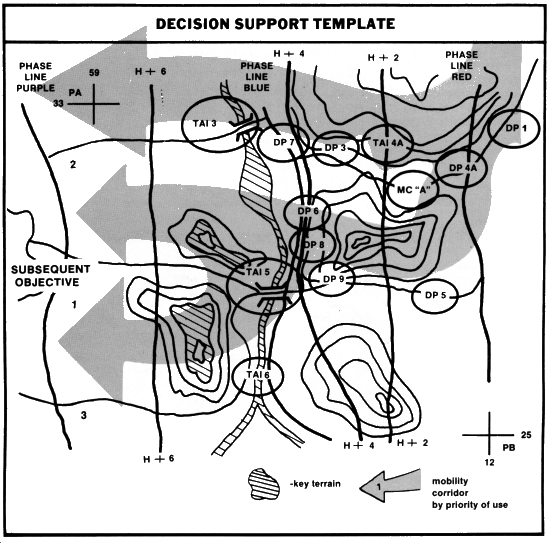
The basic product used by the tactical commander is the decision support template (DST). As a matter of fact, the DST is traditionally considered the only real product of the IPB process, with all the other templates and overlays serving as the basis for its creation.
The DST is essentially the intelligence estimate in graphic form. It relates the details of event templates to decision points (DP) that are of significance to the commander. It does not dictate decisions to the commander, but rather identifies critical events and threat activities relative to time and location, which may require tactical decisions.
Central features of the DST are target areas of interest. These TAIs are areas along each avenue of approach or mobility corridor where the commander can influence the enemy through fire and maneuver. Usually identified previously as NAIs, these areas afford the commander the option of delaying, disrupting, destroying, or manipulating the enemy force. Key bridges, tunnels, major road junctions, choke points, and known drop and landing zones are examples of TAIs.
TAIs which are essential to the uninterrupted advance of the enemy (for example, a tunnel) may become HVTs. Other areas may be designated as TAIs because they are good interdiction points through which HVTs are expected to move.
Part of determining TAIs involves TVA. TVA is a joint activity among intelligence, operations, and fire support personnel. Through analysis of enemy doctrine, TVA names and provides the basis for locating enemy elements which are key to the enemy's success. These enemy elements are known as HVTs. A second category of targets is known as HPTs. Destruction of HPTs is advantageous to friendly operations. HPTs are designated by the commander. For example, suppose the enemy must cross a wide, deep river in a friendly sector as part of a probable attack. Enemy engineer assets will be very important to the enemy commander's success. The engineer units and equipment are HVTs, without which the river crossing would be impossible. The friendly commander, who is briefed on this HVT, may designate the enemy engineers as an HPT, since their destruction would be of great value to the friendly defense plan. If so, then this particular HPT is prioritized among other HPTs for location by intelligence personnel and subsequent attack by fire support or EW personnel.
An analyst who has an in-depth knowledge of doctrine can indicate potential HVTs (CPs, missile units, logistics points) on situation and event templates. This helps cue collection assets to possible HVT locations, and helps designate TAIs for the decision support template. The S2 recommends areas (usually NAIs) as potential TAIs. The actual selection of TAIs is a command responsibility.
Following the selection of TAIs, DPs are identified.
DPs link battlefield events to friendly options for action. They represent the last point in time for a decision to be made that will allow effective action with a specific system or weapon. Decisions must be made early enough to ensure that they can be implemented in time to achieve the desired effect. However, decisions cannot be made until there are indications that particular battlefield events will occur and their locations are determined with a high degree of confidence.
DPs equate time to specific points on the battlefield. They are determined by comparing times required to implement decisions, enemy movement rates, and distances. For example, if it requires 2 hours to implement a decision, the decision must be made while the enemy is at least 2 hours from the NAI where the event will occur. Enemy doctrinal movement rates, adjusted to compensate for the effects of the terrain, weather, and friendly action on mobility, provide the basis for computation.
For example, the enemy has been templated within an avenue of approach that requires crossing a bridge. S2s should think like the commander by anticipating his needs. In other words, will the commander want to interdict the enemy in terms of EW, artillery, air interdiction, or maneuver of forces? Thus, each TAI should have a series of DPs, or a decision point cluster (DPC). For example, though not doctrinal, the following items could apply to a DPC:
- EW (depends on the enemy electronic order of battle (EEOB) developed): 5 minutes to 12 hours
- Artillery: 15 minutes
- Air Force: 1 hour
- Maneuver forces: 5 to 6 hours
Based upon this information, the S2 could accurately depict areas where the commander must decide which course of action to employ. He may not take any action, but the S2 has to anticipate the commander's needs. There should be as many DP (within each DPC) as there are tactical options.
By referring to the EAM, the S2 can depict enemy time-phase lines.
TPLs are based upon enemy doctrinal rates of advance modified by terrain constraints. They are drawn across the avenue of approach or mobility corridor and listed as H+1, H+2, and so forth.
Through the use of well-prepared DSTs, the commander can influence the battle by concentrating critical assets at the right time and place. The DST allows the commander to act, not react.
The production of one DST does not conclude the IPB process. The threat model is never complete. IPB is a continuous process with one or all five steps occurring at the same time. New contingencies arise and missions change; IPB developed for both the offense and defense--before the battle--ensures success on the modern battlefield. A sample of a DST is shown below.
TARGET DEVELOPMENT
The target development role of the brigade and battalion S2 in support of combat operations is very important. Principally concerned with situation development, the S2 staff and supporting IEW elements process a great deal of target information. This section discusses target development (primarily the tactical situations when targets are encountered and the method for determining the value of the targets) and the role of the S2 and his staff in formulating target data during preparation for combat. Target acquisition and the actual development of the target, once it is acquired, will be discussed in Chapter 5.
Upon receipt of a mission (whether contingency or actual), the BICC will conduct an analysis of the AO and implement the IPB process based upon this information. The intelligence staff determines enemy capabilities and determines the most probable course of action.
Contingent on enemy courses of action and the commander's tactical requirements, the TVA tools are used by the S2 (who coordinates with the S3/FSO) to determine which elements of the enemy's force are most important to his success.
Tactical requirements vary among the following areas or conditions of the battlefield:
- Close operations.
- Deep operations (as battalion/brigade operations support the division's deep operations effort).
- Rear operations.
- Protect/counter-C3.
- Battle damage assessment.
The location and composition of the enemy force compared against the mission and targeting assets of the friendly forces drives the TVA process.
TVA involves--
- Determination of HVT.
- Preparation of target spread sheets.
- Preparation of target sheets.
- Establishment of target list.
Using IPB templating, TVA is done before the battle so that, during the battle, the commander can quickly select and attack specific targets to manipulate the enemy force. When faced with a numerically superior enemy force, commanders will not have enough resources to attack every target that can be acquired. Therefore, TVA must be keyed to determining which targets, out of the entire enemy array, should be attacked (and when) to achieve the greatest tactical benefit for the resources expended. TVA determines--
- The critical targets.
- When these targets should be attacked.
- Where these targets should be attacked.
TVA begins in IPB by a detailed analysis of enemy doctrine, tactics, equipment, organizations, and expected behavior. Information derived is then used to project how, in each tactical formation, the enemy will respond when confronted with different tactical situations. TVA identifies activities, behavior, equipment, and elements of the selected enemy force which are critical to successful operations in each situation. An example of this is the engineer company in an MRR during a march to contact. When the MRR is faced with making a river crossing, the engineer company's location within the march formation changes. Other preparatory activities must also take place in order for the river crossing to succeed. Through TVA, a listing of actions and elements is developed that would prevent the MRR from conducting a river crossing. Preventing the river crossing may accomplish the desired effect by disrupting, delaying, or blocking the MRR based on the commander's tactical plan. In-depth TVA provides a means of determining which targets should be attacked for the greatest tactical benefit in a given situation. These targets are identified as HVT.
When conducting TVA, the situational value of a target is a significant factor. As the distance from the FLOT increases, the value of combat forces decreases with respect to CSS forces and facilities. For example, at the FLOT, an attack battalion is a significant threat and is a very important target to the maneuver battalion commander. However, 100 kilometers forward of the FLOT, that tank battalion is not as important to the success of the enemy's immediate mission as an ammunition supply point (ASP) or a fuel dump. Recognition of this situational value element is important in TVA.
Each echelon of command should have and use target spread sheets that apply to the enemy forces that commanders can be expected to face. These sheets are maintained within the brigade TOC by the S2 and S3.
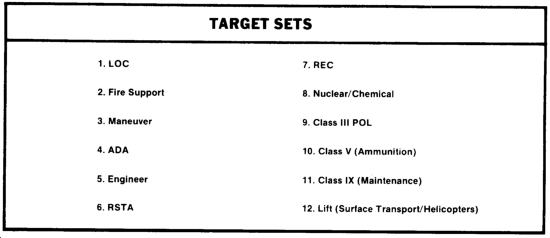
During TVA and preparation of target spread sheets, potential targets are grouped into 12 sets. These sets are shown in the following illustration.
Once an analysis of enemy doctrine is completed, a spread sheet is prepared for each specific tactical situation and level of command.
The results of TVA are used to prepare target spread sheets and target sheets.
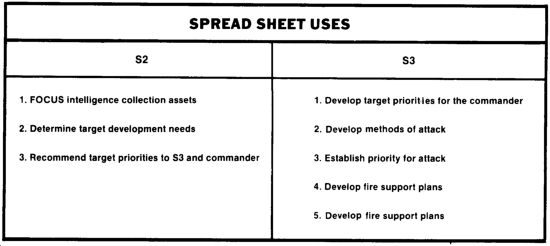
Spread sheets are a means of describing and identifying targets in specific situations and various echelons of Soviet-type forces. The S2 and S3 use spread sheets as indicated below.
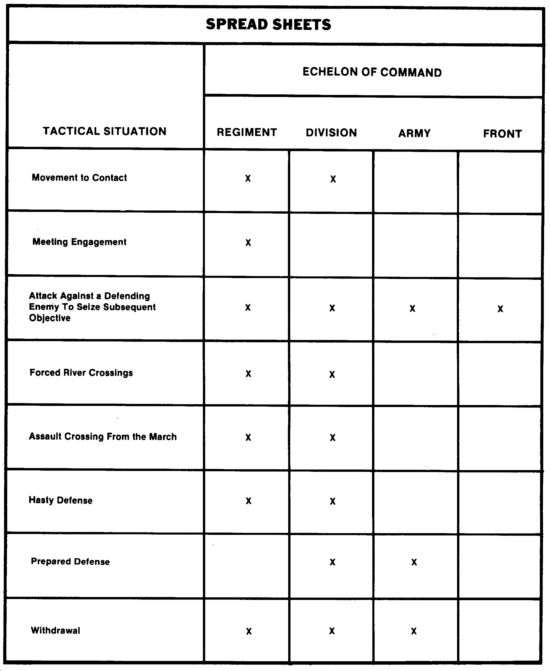
Currently, spread sheets have been prepared for use in Europe against Soviet- or Warsaw Pact-type forces in any mid- to high-intensity environment. Spread sheets normally used are shown in the following matrix.
A sample spread sheet is illustrated below.
The spread sheet is divided into five columns. The first three columns describe the effect desired from attacking the target. The Xs in the columns identify which effects can be achieved in a particular situation against the size of formation for which the sheet is being prepared.
The TARGET SET column lists the 12 target sets identified previously. The RELATIVE WORTH column depicts the worth of attacking one target set with respect to the other target sets on the sheet. The subdivisions in the column are not scaled and should not be interpreted as absolute values. This column allows a rapid identification of the priority which different target sets should have when resources for attack are scarce.
The spread sheet also contains information on enemy doctrine. This includes likely formations and distances (event template), objectives of the force, and likely enemy courses of action if the attacks on this force are successful.
The spread sheet presents the attack objective for a particular target set and refers to specific targets within that set which should be attacked. Individual spread sheets identify which specific targets within a set should be attacked. For example, in the blank left column, ZSU-23-4S within the ADA set would be indicated.
A target sheet is prepared for each potential HVT and supports the spread sheets discussed earlier. Target sheets are designed to indicate the critical elements of various target groups which, when attacked, will restrict options or capabilities of the enemy. The target sheet identifies the target and provides information target category, nomenclature and command relationship, function and capability, physical description, signature (visual and electronic), graphic representation of critical target elements, and the effects of a successful attack against the target.
The target sheets are further enhanced by electronic target sheet addenda provided by the MI battalion TCAE. These target sheet addenda are organized into two major sets of information for each target:
- Organizational, radio, radar, and operational data.
- Radio, radar, and photo profiles.
Both of these products are classified because of the nature of the information depicted. Once completed, these sheets are used by the S2 and S3 to identify and prioritize enemy potential HPTs.
A list of HPTs is provided to the commander. Upon approval, the HPTs subsequently drive the friendly collection effort and attack planning. The S2 will designate certain targets on the HPT list as protected targets (those elements that might be exploited using COMINT assets). See FMs 34-1 and 6-20 for a more detailed explanation of the above procedures.
COUNTER INTELLIGENCE SUPPORT TO OPSEC
CI support to OPSEC is a critical element in preparation for combat operations and determines what actions the CI personnel will take. CI support orients on defeating or degrading an enemy's multidisciplined RSTA capabilities.
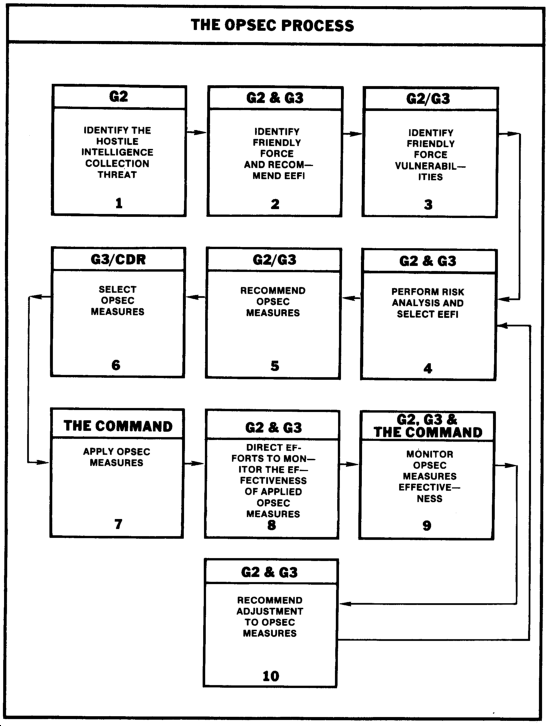
The support requires continuous planning, data collection, analysis, reporting, and execution of orders and instructions. It is a 10-step process that is cyclic in nature, which continually considers the changing nature of the enemy threat and friendly vulnerabilities. The following chart depicts the OPSEC cycle.
Step 1. Identify the Hostile Intelligence Collection Threat
This step is an intelligence function performed by the CI analysts. The enemy intelligence collection threat is all-source, multidisciplined, and extremely effective.
Information on the enemy intelligence collection systems is developed and stored in the OPSEC data base at division level.
Step 2. Develop Friendly Force Profiles and Recommend EEFI
Friendly force profiles, signatures, patterns, and indicators show how a unit might appear through the eyes of the enemy. The friendly force data base is crucial to planning operations because it aids in developing EEFI, countermeasures, accurate appraisals, and effective deception plans.
Profiles result from actions, including the timing of those actions, taken by military units and individual soldiers. Analysis of a unit's profiles reveals signatures and patterns about unit procedures and may be used to determine intentions. Collectively, profiles can be used by the enemy to predict probable friendly courses of action. The CI analysis section develops profiles on all division units to determine weaknesses and to recommend corrections. Profiles which must be maintained include--
- Administration.
- Intelligence.
- Logistics.
- Operations.
- Communications.
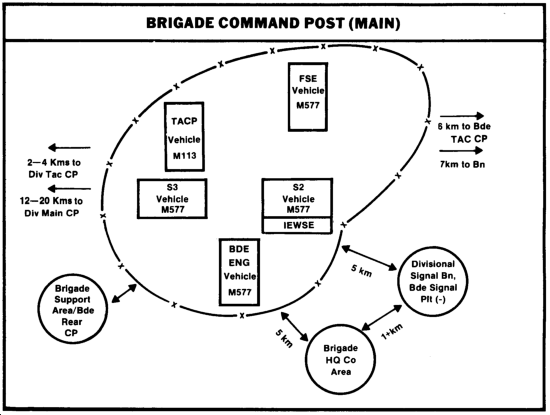
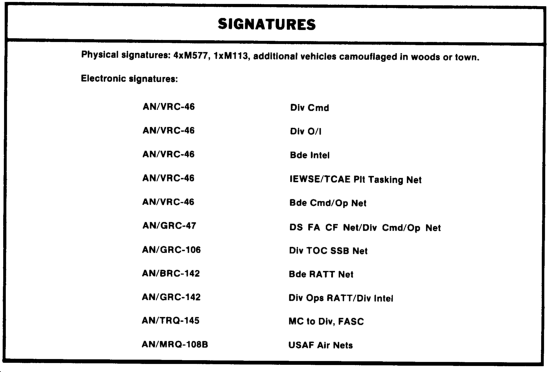
The following illustration depicts a type of brigade CP showing physical and electronic signatures.
Unit profiles should be developed by OPSEC support teams which will subsequently be compiled to develop major unit profiles. For example, the profile of a brigade will include all profiles of units within that brigade area plus patterns that will occur to support the operations. (See the following example.)
This profile will be an in-depth analysis of the signatures and patterns of the brigade and must show the interrelationships of command, support, and maneuver units.
Signatures result from the presence of a unit or activity on a battlefield. Signatures peculiar to specific units are detected and the units identified based on unique characteristics of equipment, size, electronic signal emission (communications, noncommunications, thermal, acoustic, and seismic emanations). Detection of individual signatures can be grouped by analysts to show installations, units, and activities.
Patterns are the result of the way operations are conducted. Military forces have SOPs for virtually everything they do. Predictable patterns may be developed by commanders, planners, and operators. Types of patterns are as numerous as procedures in military operations. For example, before every offensive operation the volume of communications increases dramatically and then drops off equally dramatically just before the attack. Enemy analysts would note this pattern and be able to predict our intentions for future offensives.
Indicators are activities that can contribute to the determination of a friendly course of action. In preparing for a tactical operation, it is virtually impossible for military forces to avoid or hide all indicators. In many cases, these activities can be detected by the enemy and used to predict probable courses of action. Indicators that cannot be eliminated or hidden may be considered as a basis for a deception plan.
Identification and interpretation of specific indicators are critical tasks in intelligence operations whether the indicator is friendly or enemy. CI analysts look for indicators, analyze them, and make estimates of capabilities, vulnerabilities, and intentions. These analyses lead to requests for information and planning and eventually provide the basis for decisions and orders.
Data bases on friendly forces are continually updated as the situation changes. Changes in operations, tactics, equipment, or personnel that may alter any signatures and patterns are immediately entered into the data base. Reports from the OPSEC survey teams may disclose indicators not previously considered in assessing a command's subordinate unit's profile.
Determining EEFI is based solely on the analysis done in Step 2 of developing friendly force profiles. Once identified, this EEFI will be recommended to the commander to protect the combat force.
Step 3. Identify Friendly Force Vulnerabilities
Vulnerabilities are specific weaknesses in a command's OPSEC posture that are susceptible to the enemy's intelligence collection threat. Vulnerabilities may include poor COMSEC, inadequate use of camouflage, poor physical or document security, or any predictable patterns or activities offering indications of specific intentions. This step is primarily an intelligence function. Vulnerabilities are determined through comparison of friendly profiles (or indicators) to hostile collection capabilities. A vulnerability exists whenever the enemy has the capability to collect information on our forces which would cue him as to our intentions (or courses of action). Time, date, locations, and type of collector are the first important considerations during this step.
Threat evaluation is accomplished through comparison of friendly indicators and hostile collection capabilities to identify friendly force vulnerabilities. As an aid to analysis, IPB techniques are applied to friendly force patterns and signatures so we can see ourselves as viewed by enemy collection systems. For example, the range and focus of hostile collection means can be plotted on a map and, with intervisibility overlays, a determination made regarding what friendly activities are vulnerable to enemy observation. Further, IPB can be applied to develop countermeasures recommendations. For example, a map overlay could be constructed to indicate which routes minimize detection during movement, or which areas would afford concealment and cover for signature-unique equipment.
Step 4. Perform Risk Analysis and Select EEFI
Risk analysis is the process by which projected friendly vulnerabilities are compared to the enemy's capabilities to defeat the friendly force. Nonelection of a countermeasure may incur certain risks to the force or its operations and activities. This cost of countermeasure versus benefit expected to be derived requires the coordinated efforts of the S2 and S3 staff elements. The coordinated risk analysis is presented by the S3 to the commander for decision. The results of risk analysis include the selection by the S3 of the EEFI which are critical enough to warrant the application of countermeasures to conceal them from the enemy.
EEFI provide the basis for applying appropriate OPSEC countermeasures. The EEFI are derived from the commander's guidance and from after-action reports, staff evaluations, and vulnerability analysis.
Once the threat has been identified, to include methods of operation, timeliness of reaction, and known capabilities, it is compared with the OPSEC profiles and the friendly mission. The S3 outlines the plan for the aspects of the assigned mission. These aspects include many terms of information that could, if compromised, lead to failure, or could limit the success of a given operation.
Step 5. Recommend OPSEC Measures
Based on the risk analysis process of Step 4, countermeasures are selected to minimize vulnerabilities. Because this selection is a resource management and risk decision function, it falls to the operations staff element to make the decisions. Resolving the competition-for-resources problem is an S3 function. Generally, there are five options for the decision maker:
- Apply countermeasures.
- Accept risk of detection.
- Use deception.
- Combine any of the above.
- Prohibit the activity (cancel the mission).
Selected countermeasures are directed by the OPSEC annex to the OPORD.
The OPSEC annex to the OPORD is, in reality, the OPSEC plan. There are five paragraphs: Situation, Mission, Execution (Countermeasures), Service Support, and Command and Signal. (See FM 34-60, Appendix B.) The EEFI (which should be listed in paragraph 3 of the OPSEC annex) are set up in priority order. Generally, these priorities will coincide with enemy doctrinal priorities for reconnaissance and the employment of their fire support and jamming resources.
The plan may be disseminated by any of the following means:
- Annex to the OPORD.
- Fragmentary order (FRAGO).
- Verbal or written instructions.
In selecting and planning countermeasures, the OPSEC countermeasures worksheet is completed. The worksheet describes countermeasures for the force as a whole and specific countermeasures to be employed by the subordinate maneuver and support units. The worksheet becomes part of the OPSEC annex to the OPORD (see FM 34-60, Appendix C).
Steps 6, 7, 8, and 9
Step 6, Select OPSEC Measures; Step 7, Apply OPSEC Measures; Step 8, Direct Efforts to Monitor the Effectiveness of Applied OPSEC Measures; and Step 9, Monitor OPSEC Measures Effectiveness, are closely related to the previous step. It is in these steps that an OPSEC survey is done and countermeasures are evaluated. Teams are formed with personnel from the operations staff (the team leader), and representatives from the functional areas of intelligence, communications, logistics, and administration. Other specialists may be required. For example, if engineer operations are to be evaluated, then an engineer expert should be designated as a team member.
CI personnel assigned to the teams assist in evaluating units for identifiable patterns and signatures exploitable by the enemy. Their knowledge of enemy intelligence collection capabilities and effective countermeasures is critical to the effectiveness of the team. Additionally, the CI personnel interrogate EPW and refugees to determine enemy intelligence requirements and to gage the effectiveness of OPSEC measures.
During the course of OPSEC surveys, the OPSEC teams advise their commanders and staffs about security practices that may compromise EEFI or provide indicators of any planned or ongoing operations. If any actions indicate possible compromise of essential information, the data is reported to the CI element for analysis of the probable information disclosed and the risks to which the command may be subjected. Examples of data to be reported are--
- Suspected disclosure of designated EEFI.
- Serious violations of established security procedures.
- Friendly losses attributable to probable compromise.
- Indications that the enemy had prior knowledge of a friendly operation.
- Enemy activity directed against otherwise well-concealed friendly vulnerabilities.
Step 10. Recommend Adjustments to OPSEC Measures
Intelligence and operations staffs jointly make adjustments to the OPSEC program. When necessary, new EEFI are recommended and changes to countermeasures are devised and recommended.
After-action reports about OPSEC conditions and the effectiveness of countermeasures previously implemented are presented to commanders and operations officers. The detail of these reports will vary with the extent of an operation, size of a unit, time available, and current situation.
Additional Functions
CI personnel perform various additional functions. These functions include--
- CI screening or line-crosser operations. During initial screening, individuals are approached for possible return as low-level US agents to the enemy-held territory from which they came. Individuals are also screened for their identification on the black, gray, and white lists (see below).
- Investigations. CI personnel investigate incidents to try to detect and nullify espionage, sabotage and subversion activities. In overseas areas, they also investigate personnel to ensure they are suitable for a position of trust and responsibility with the US Government.
- CI defensive operations. CI personnel develop defensive source operations to obtain information on potential threats to the rear area.
- Liaison. Liaison is conducted at all levels of the Army. It is essential to the success of the CI exploitation of information in overseas areas of operation. Liaison is conducted with both military and civilian agencies in the area.
- Black, gray, and white lists. These lists identify persons selected as US targets. Black lists contain those hostile to the US, gray lists identify those whose inclinations and attitudes toward the US are obscure, and white lists contain those friendly to the US. They are used during screening operations to locate personnel of CI interest.
- Training. CI personnel conduct security training in various areas, such as SAEDA and counterinterrogation. This includes classes, briefings, and other training to meet the requirements of the command's mission.
ELECTRONIC WARFARE
The ground-based EW resources available to the MI battalion and MI brigade at division and corps, respectively, and the three QUICKFIX aircraft of the division CAB, are all capable of providing EW support to divisional brigades and their subordinate maneuver battalions. These resources, however, as discussed in Chapter 2, are extremely limited, and the missions they may be called upon to perform are extremely diversified. Their individual and collective capability to effectively support any battalion or brigade, or the division as a whole, for that matter, ultimately depends upon how well EW operations are planned, prior to combat. The following describes the formal top-down, bottom-up EW planning process in which the battalions and brigades participate.
The brigade S3 has the primary responsibility for the planning, targeting, execution, and evaluation of EW operations in support of the brigade. Maneuver battalion EW needs are identified to the brigade for incorporation in brigade priorities. The brigade S3 is specifically concerned with ECM and ensuring that EW operations support the commander's overall concept of the operations by integrating ECM with the targeting of lethal fires and the scheme of maneuver. ESM, although a critical element of EW, are the responsibility of the S2. ESM operations are conducted the same as other collection operations and require the same type of S2/S3 coordination. The S3 identified his combat information requirements to the S2, who incorporates them with other ESM/SIGINT needs. The six principles of EW support, shown in the following illustration, provide corps, division, and brigade staff officers alike with a common point of reference to ensure maximum effectiveness of EW operations to support all operations.
Types of Targets
The types of targets for EW missions are the same as for other fire missions. They are: preplanned targets, on-call targets, and targets of opportunity.
Preplanned EW targets are communication or noncommunication entities which are identified during the planning of an operation. These targets can be identified before the operation as key elements to be jammed or collected on during the operation. Through IPB and existing data bases, target locations are predicted. Through analysis of the concept of the operation, their importance and priority for EW action is determined.
On-call EW targets are elements identified during the conduct of an operation for immediate jamming or collection. These are targets which could not be predicted before the start of the operation, and whose importance is identified as the operation progresses.
EW targets of opportunity are communication or noncommunication entities which were not identified as specific preplanned targets and which the EW operator acquires and recognizes during the conduct of ESM or ECM operations. Once these targets are recognized, they become candidates for jamming or intercept operations. Normally, categories of targets of opportunity are preplanned to allow action by operators upon recognition. They are usually given a lower priority than specific preplanned targets or on-call missions.
All three types of targets will be identified in an operations. Preplanned ESM targets are selected so as to detect the movement of enemy second-echelon forces at key times. Preplanned ECM targets are identified to degrade critical communications. Additionally, categories for targets of opportunity are generally identified to degrade enemy operations if and when these targets are located. Finally, as the operation progresses, on-call targets are identified and missions attacking or exploiting them are requested.
The development of targets of all types is through the standard target development process described in FM 34-1 and FC 34-118. Initial analysis of the enemy's deployment and intentions leads to the development of HVTs. Comparison of these HVTs to the friendly commander's intent and concept of the operation leads to the selection of HPTs. Identification of the priority for each target relative to other targets of all types is critical to ensure effective control. For example, if an on-call mission is requested, the requester must identify the priority of that mission as compared to existing priorities for preplanned and other targets. If he does not, that on-call mission may preempt a more important preplanned mission or other on-call missions.
Planning Process
The planning process for EW operations closely parallels the targeting process. The S3, S2, and IEWSE cooperate closely to plan EW missions. The initial planning process is performed prior to an operation for development of preplanned targets and identification of categories of targets of opportunity. The process continues during the actual conduct of an operation to identify on-call targets. As well as the identification of targets, the EW planning process drives the task organization of EW assets and initiates requests for EW missions to be performed by higher echelons.
The EW planning process begins with the analysis of the battlefield situation based on IPB and current intelligence data. EW system capabilities and limitations are then compared to the emitters associated with the targets identified through IPB. The result of this first step is the identification of significant targets which we can affect with available EW assets. This is the selection of HVTs in the targeting process. This step is performed by G2 or S2 staffs in close coordination with the electronic warfare section (EWS) or IEWSE.
The second step in the EW planning process entails development of a strategy for use of EW in the operation. The corps G3, assisted by his EWS, will identify the general focus of EW operations. This includes establishing priorities for EW operations throughout the area of influence. Priorities are identified for each phase of an operation. For example, a strategy in a particular operation might be to prioritize SEAD operations, and to counter the enemy's intelligence and reconnaissance systems during movement-to-contact. As the main attack begins, this priority might shift to countering enemy artillery. Finally, in the exploitation of success, priority would be to disrupt the enemy command and control to prevent his regaining control of the situation. In turn, the division G3 and brigade S3 will apply this strategy to their operation, assisted by their EWS or IEWSE. They compare the focus and phases of higher echelon EW strategy to their operations plan, and identify a focus or priority for EW missions that will support their operation and comply with the overall strategy. This ensures that EW operations at all echelons complement each other and apply limited EW assets with maximum effectiveness.
After targets which we can jam or collect against have been identified and the general strategy has been established the next step is to decide which specific targets to preplan. At brigade the S3 makes this determination based on recommendations from the IEWSE. Key enemy elements whose movement or action is considered important are prioritized for ESM missions. If appropriate, their control links are prioritized for jamming to delay receipt of orders to move. Other key communications links are also prioritized for jamming and emitters associated with unique missions or enemy actions are prioritized for intercept.
After the G3 or S3 has selected the preplanned targets which he desires to influence or exploit, the IEWSE at the brigade documents these missions on worksheets called EW target lists. These worksheets serve as planning documents for coordination between elements in the EW system. The worksheets at brigade are provided to the division's EWS to coordinate missions and to request support for missions which are beyond the capability of the assets available at a given echelon. Giving these worksheets to the next higher level allows for review to avoid conflicts, such as simultaneously tasking for both jamming and collecting on the same target. These worksheets also are exchanged with adjacent units to avoid similar conflicts.
To complete the planning process, the EWS at division uses the completed EW target list to examine the distribution of missions and recommend allocation of EW assets. At division, this involves recommendations for placing assets in DS of brigades or in GS of the division.
EW Target Lists
The worksheets described above list desired preplanned EW targets with details on unit identifications and locations. Technical data is added only when the tasked mission reaches the appropriate TCAE.
A proposed format for a brigade-level EW target list is provided below.
The EW target lists developed at the brigade level are consolidated at the division EWS on a similar worksheet. Missions planned at the division level are added to this worksheet. A proposed format for a division composite EW target list is also provided below:
Planning On-call EW Targets
Unlike preplanned EW targets, information regarding on-call EW targets cannot be predicted in detail. Their locations and the key times to interdictor collect on these targets are not clear until the operation is underway. Therefore, these missions could not be included on the EW target lists which were prepared before the operation, and will need to be forwarded separately for execution.
While the specific data to jam or collect on these targets cannot be predicted, potential targets can be identified and tracked until they are selected for EW action. To do this, the IEWSE monitors the situation map in order to identify enemy units of potential significance. He maintains his own overlay depicting the location of EW assets in his area with their range based on LOS. Comparison of this overlay to the situation map then determines which of the potential targets may be engaged.
Based on his overlay and the current situation map, the IEWSE will recommend on-call EW targets to the S3 as the operation progresses. The S3 will also select on-call targets based on his analysis of the ongoing friendly operation.
The IEWSE will normally maintain a separate list of potential targets. Using the same format as the EW target list, this list will be a working document which is not provided to higher and adjacent units. As the detailed data on these potential targets is not all available, there will be many blanks or incomplete entries on the worksheet. The IEWSE will fill in this worksheet as the situation map provides answers. By maintaining and constantly updating this worksheet, on-call EW targeting data is ready for rapid identification and for request of EW missions. When these targets are to be jammed or exploited, the IEWSE at brigade calls these missions directly to their servicing TCAE for execution. FM 34-40(S) provides more detail on planning and tasking of both on-call and preplanned EW missions.
Electronic Warfare Operations
COMJAM attack and ECM control procedures are initially determined during the EW planning process with specific attention to the C3 means available for implementation. They are specified in the "control mechanism" and "coordinating instructions" columns of the refined EWTL, previously described. Each type of COMJAM attack and ECM control procedure requires extensive preplanning in critical situations.
Negative ECM control procedures against categories of targets of opportunity are used by COMJAM operators extensively during the initial hours of combat when little or no technical data base is available to support their operations. Such procedures are used predominantly against enemy secure communications facilities to support the division and corps' overall SIGINT collection, processing, analysis, and reporting effort. They provide COMJAM operators a positive means to "get into" the enemy's decision-cycle or "event schedule." HPTs for jamming are developed by the EWS at division and corps. Extensive coordination with the G2, MI unit S3, and each TCAE, is required. Target of opportunity jamming missions are reflected on the EWTL, previously described. They are based on the commander's specified rules of attack priorities, and critical task lists.
Targets of opportunity jamming missions are usually conducted on an area-wide basis against generic sets of HPTs such as all enemy secure communications facilities operating in a specified frequency band; all fire support facilities operating within a specified attack zone; or all SAM/AAA C3 facilities passing operational information within a given time period. Generic HPT sets are prioritized by the G3/S3 based on recommendations from the G2/S2, EWS, FSE, and the MI unit S3 and TCAE. SIGINT analysts and ECM managers within the TCAE determine the specific elements of information or types of transmissions to be jammed, the respective employment area for each EW team or platoon, and the frequency bands for which each EW team or platoon is responsible. COMJAM operators execute missions against high payoff targets of opportunity "upon recognition" only when the specific attack criteria, specified on the EWTL have been met. Voice collection and DF operators monitor the mission. All combat information, technical EOB data, frequencies, and COMJAM results are transmitted to the TCAE via the IEW C2 system.
Positive ECM control procedures for offensive COMJAM attack against preplanned EW targets begin at the earliest possible point in battle. They commence as specific HPTs are identified and located. Again, the reporting of combat information regarding enemy activities or "events" provides the key for synchronizing the overall fire support effort. Knowing where the enemy is and what the enemy is doing, and slowing the enemy down by disrupting his critical communications means, provide the time necessary to "adjust" all lethal and nonlethal attack schedules.
Preplanned jamming requires the greatest amount of detail, identifying the unit, location, and time. It must be totally synchronized with fire support and maneuver to achieve maximum results. Preplanned jamming missions may engage a target simultaneously with fire, or singularly engage lower priority targets, while simultaneous fire is brought to bear on higher priority targets. Preplanned targets, like targets of opportunity, are reflected on the EWTL for each EW team or platoon. Technical data (such as frequencies and call signs, or indications that technical data is available to support attacks against specific HPT facilities) are the primary means for differentiating preplanned HPTs from target of opportunity sets on the EWTL. Preplanned COMJAM operations are conducted on a scheduled or on-call basis.
Preplanned missions, depicted on the EWTL, as previously mentioned, are both time- and location-phased according to the scheme of maneuver and the supporting fire plans. The enemy unit's C3 facility, its location, and the time at which the COMJAM attack is to begin are all reflected on the EWTL. This type of COMJAM attack is usually synchronized with the lethal attack fire missions to provide the greatest support to the supported maneuver unit and to ensure maximum degradation to the enemy's C3 system. SOP COMJAM attack priorities allow for the immediate attack of unforeseen or nonscheduled HPTs as the battle develops. Such targets are normally attacked on an on-call basis, having been anticipated early in the planning process. Extensive coordination is required among the S3, S2, and the FSE of the supported maneuver unit, their counterparts at higher echelons, and, most importantly, the IEW resources operating within their AO. This will ensure that preplanned and on-call targets are attacked at the time and place they require COMJAM support. Such coordination in combat is virtually impossible unless detailed targeting, COMJAM attack and ECM control procedures, alternate communications means, and coordinating instructions are determined prior to combat. On-call COMJAM attack and ECM support missions are the most difficult tasks to perform.
On-call jamming missions, like other preplanned missions, are reflected on the EWTL for given EW teams or platoons operating in each AO, as HPT C3 facilities are identified, located, and scheduled for attack. Positive control procedures and specific coordinating instructions are always stipulated. However, the basic technical data and the exact time of the COMJAM attack may not be available or immediately known. There are three types of on-call missions:
- COMJAM attacks against immediate HPTs as they become active or cross into pre-established attack zones.
- High-power communications support to specific commanders in critical situations.
- COMJAM screening missions, discussed in Chapter 2.
COMJAM attacks, performed on an on-call basis against immediate HPTs are very similar to preplanned jamming, previously described. On-call jamming missions, however, differ from preplanned missions, in that they are developed as the battle progresses to attack specific HPT C3 facilities supporting specific enemy units in specific attack zones during specific time periods. On-call COMJAM attacks are conducted primarily in support of "hand-off' operations as enemy units transcend attack zone boundaries or when the COMJAM effectiveness of one ECM system is degraded and another ECM system can acquire the HPT and conduct operations more effectively. On-call targets are anticipated in the planning process prior to deployment. The IEWSE and TCAE personnel develop and refine on-call attack missions as the battle unfolds. ECM managers in the TCAE schedule on-call targets for given EW teams or platoons as HPTs are identified and located. COMJAM operators report the time of acquisition and their readiness condition to the TCAE and supported command following SOP and predetermined coordinating instructions. On-call COMJAM control authority in such situations may reside with the supported commander or his S3 to ensure that the COMJAM attack is synchronized with his specific maneuver and fire support operations. Proper authentication procedures must be used and CEOI must be known by all members of the combined arms team involved in these types of operations.
On-call high-power communications support should be considered when determining the manner in which ECM resources are task organized to support the synchronization of all operations. These operations are performed only in extreme circumstances, COMJAM screening operations are also used only in extreme situations. FM 34-40(S) will provide more detail on these operations.
Effective on-call COMJAM support may ultimately determine the outcome of close operations. The MI battalion and its TCAE and EW resources must render that support to the brigades and battalions conducting close operations. This includes COMJAM attacks against immediate HPTs, highpower communications to call in air or artillery strikes, or screen jamming protection for friendly C3 activities. These subjects are discussed in greater detail in Chapter 5. Additional information regarding the procedures, tactics, and techniques used to plan, conduct, coordinate, and evaluate such operations are provided in FMs 34-10, 34-25(S), and 34-40(S).
RECONNAISSANCE AND SURVEILLANCE
R&S provides a systematic watch over the battlefield. It provides early warning of enemy activity, targets for fire and maneuver, and, most important, information to help satisfy the commander's PIR in preparing for combat operations. R&S therefore provides the commander with information-collection capabilities throughout the battle area. In addition, other services' capabilities may augment those of the Army. For example, Army capabilities are extended well forward by Air Force tactical air reconnaissance. This extension provides critical intelligence of enemy second-echelon forces before they are within the range of Army collection capabilities. R&S yields much of the information necessary for decisions and targeting.
Most information needed in combat comes from assets within the combat force. These assets perform R&S operations in the area of immediate interest.
INTERRELATIONSHIPS
Reconnaissance is undertaken to collect information by visual or other detection means. It is characterized by its direction toward coverage of one or more specific target areas. The reconnaissance mission may be developed from cues indicating that an area possesses intelligence value or because current or planned operations require detailed coverage of a specific area.
Surveillance is the systematic observation of aerospace, surface or subsurface areas, places, persons, or things by visual, aural, electronic, photographic, or other means. Surveillance is characterized by wide coverage of a target area and by repetition. It is normally used to gain information in those aforementioned areas over a long period of time to note any changes that may take place.
Because of the interrelationship of reconnaissance and surveillance, the same assets used to execute reconnaissance missions may also be used for surveillance tasks.
As noted above, surveillance missions are characterized by a systematic, constant watch of persons, places, or things by HUMINT, IMINT, or SIGINT resources. Surveillance missions are usually preplanned. Surveillance missions are particularly suited to--
- Cover large areas rapidly and repetitively.
- Minimize risk to the collector.
- Observe or detect changes on the enemy side of the FLOT.
- Cue other collectors for more detailed coverage.
ROLES OF RECONNAISSANCE AND SURVEILLANCE
R&S is a vital part of the battalion and brigade intelligence collection effort. The BICC does the detailed R&S planning and integrates it into the overall collection effort. For a more detailed discussion of the S2/BICC responsibility and procedures in R&S planning see Appendix E.
The main reconnaissance effort supports the main maneuver effort: main attack along with main defensive effort. The primary reconnaissance effort is designated by redundancy; for example, using two patrols along the main axis of advance or attack. Detailed instructions given to R&S assets include: mission, start-completion time, objective-passage points, action on enemy contact at barriers, control measures (that is, phase lines and checkpoints), PIR, SOR, and actions on completion of mission. The higher headquarters' (brigade and division) intelligence and combat information on the TF area of operations must be confirmed. The commander should receive timely information in order to adjust his scheme of maneuver as new combat information is acquired.
In preparing for R&S in the offensive, the TF commander must focus the collection effort, based on SOR derived from a situation or event template on platoon locations, vehicle locations, crew-served weapon locations, individual fighting positions, barriers and obstacles, and locations of the reserve and counterattack elements. For planning purposes, the collection effort focuses on the threat echelon two levels below the R&S planning level. Reconnaissance patrols will watch the objective during changes to the threat posture.
For R&S in the defensive, the commander must focus collection effort on the following:
- Identifying the enemy reconnaissance effort for counter-reconnaissance purposes.
- Identifying the enemy main effort as indicated by enemy unit locations, particularly the second echelon.
For counter-reconnaissance purposes the collection effort must--
- Define EEFI: barriers or obstacles, platoon locations, reserve and counterattack elements.
- Assess enemy collection capabilities and methods.
- Assess friendly vulnerabilities.
- Coordinate countermeasures with the S3.
Countermeasures accomplish two things:
- Orientation of TF collection capabilities (scouts, patrols, GSRs, and OPs) on protecting EEFI to identify enemy reconnaissance.
- Orientation of combat elements on the identified reconnaissance to neutralize or destroy them by combat.
PLANNING PRIORITIES
In planning R&S, it should be understood that long-range planning of R&S operations and events is conducted by division echelon and higher, using the formal collection management process, whereas brigade and battalion planning usually involves events that will occur within a few days. The results of planning at the brigade and battalion levels includes a written or graphic R&S plan. The R&S plan prepared at brigade and battalion levels may include all R&S data.
The BICC will assign priorities to all R&S requirements based on the urgency and importance of the information needed.
- Priority 1: Takes precedence over all other requirements except previously assigned Priority 1 missions. The results of these missions are of paramount importance to the immediate battle situation or objective.
- Priority 2: The results of these requirements are in support of the general battle situation and will be accomplished as soon as possible after Priority 1 requirements. These missions are to gain current battle information.
- Priority 3: The results of these missions update the intelligence data base, but do not affect the immediate battle situation.
- Priority 4: The results of these missions are of a routine nature. These requirements will be fulfilled when the reconnaissance effort permits.
- Priority 3 and 4 taskings are not assigned to subordinate units. Information required which falls in these categories is included in PIR and IR transmitted to subordinate units.
The BICC will also use planning factors to develop R&S information. Planning factors are those elements or conditions which may have a serious impact on the command's R&S effort.
The friendly and enemy situation includes the composition and disposition of friendly and enemy forces, enemy tactical doctrine, and the type and extent of planned operations.
Resources include brigade and battalion collection assets (discussed previously) and supporting assets. Capabilities, limitations, and availability of collection assets are considered when allocating resources for reconnaissance and surveillance requirements. The objective is to assign each requirement to the best available collection asset or assets to most economically support the requirement.
Terrain and weather are studied to determine their effects on available resources and are also considered during the determination of R&S requirements. That is, likely avenues of approach would normally be allocated greater resources.
EW is considered in all R&S plans. Planning should include consideration of friendly and enemy SIGINT, DF, and jamming capabilities. SIGINT, DF, and jamming capabilities.
OPSEC includes all measures that can be taken to deny intelligence of friendly force composition, disposition, and activities to the enemy.
R&S plans must be scrutinized to ensure that they do not inadvertently disclose such information to the enemy.
See FMs 30-20 and 100-5 for further explanation of R&S planning.
REQUESTS FOR INFORMATION
Generally, requests for information can be identified as either reconnaissance or surveillance. Classifying requests by this method assists the brigade or battalion S2 in determining the basic elements of the request.
Planning for surveillance operations is conducted after determining the general mission of the tactical force. Surveillance missions are often developed as a joint effort involving all of the intelligence organizations having an interest in the same AO. This is due to the limited availability of surveillance systems and the large number of overlapping requests that could be generated in a joint or combined operation.
A reconnaissance mission seeks to obtain information by visual or other detection means and is characterized by limitations of coverage to one or more specific target areas at a particular time without the requirement for systematic coverage.
Reconnaissance missions are conducted by HUMINT, IMINT, and SIGINT resources and are designed to--
- Collect specific, detailed information at a particular location and time.
- Support current or planned operations.
Most reconnaissance requests are preplanned before the operation; however, once operations begin, many reconnaissance requests will be immediate. The time constraints of the typical reconnaissance request will not allow for elaborate planning or coordination. A request that would be classified as a requirement for a reconnaissance mission might be for urgent photographic coverage of a proposed helicopter landing zone (LZ) some distance beyond the FLOT.
Valid justification is particularly important for immediate surveillance or reconnaissance requests. This is critical if corps and EAC systems may be required to collect the information.
The BICC manages all R&S assets available which provide a complete picture of the area of operations to the commander, staff, subordinate commanders, and higher headquarters. Effective management requires the determination of R&S requirements, tasking, controlling and coordinating assigned assets, and requesting R&S support from higher headquarters to satisfy those requirements beyond the capabilities of assigned assets.
To effectively manage the R&S effort, the BICC must consider the following:
- Unit mission and the commander's concept of the operation.
- R&S assets available from assigned units.
- Resources available from higher headquarters and other services.
- Capabilities situation, including location, composition, and disposition of both friendly and enemy forces.
- The S2's estimate of the situation and possible enemy course of action.
- Weather, vegetation, and terrain as they may affect employment of R&S resources.
The BICC analyzes all available R&S data and uses organic R&S resources to best cover the battlefield and satisfy PIR and targeting requirements. It requests additional resources or support needed to accomplish R&S requirements from higher headquarters. See Chapter 2 and Appendix E for the R&S resources assigned to and supporting the brigade and battalion.
The BICC examines the capabilities and limitations of each R&S resource and matches resources to specific information and R&S requirements. Careful planning ensures the most effective use of R&S resources.
The BICC uses various aids to help manage R&S operations, including the unit intelligence SOP. The SOP specifies standard R&S procedures. It standardizes procedures that are done repeatedly in order to reduce the number of orders that must be transmitted during combat. The R&S SOP should include the following:
- Procedures and formats for requesting R&S support.
- Reporting procedures, channels, and formats.
- Standard R&S activities, such as conducting patrols and operating OPs.
Another aid used by the BICC is the SITMAP. The SITMAP portrays the friendly and enemy situation and conveys plans and orders in a condensed form. The BICC posts pertinent parts of the R&S plan to the SITMAP to ensure that R&S operations are integrated with maneuver, fire, and other intelligence operations. (See Appendix E.)
The R&S plan includes the R&S requirements of subordinate units. Each echelon requests R&S support from higher headquarters to satisfy those requirements that are beyond its own capabilities. The BICC evaluates these requirements, assigns priorities, and satisfies them in one or more of the following ways:
- Includes them in the R&S plan.
- Allocates R&S resources to the requesting unit.
- Forwards the request to higher headquarters, indicating approval.
The BICC coordinates the R&S plan within the brigade or battalion staff with subordinate and supporting units, and higher headquarters. Coordination objectives are as follows:
- Ensure that the plan identifies and meets all R&S requirements.
- Avoid duplication of effort and to consolidate missions, when practical.
- Avoid conflicts with other combat activities.
- Identify and task R&S resources and ensure that R&S missions are compatible with other assigned missions.
When time permits, the BICC coordinates the R&S plan through informal and formal means, including briefings, personal contacts, and liaison visits. The BICC uses several methods to disseminate orders and requests for R&S support. These include, but are not limited to--
- OPORDs.
- R&S plans as part of or separate from the OPORD.
- SCARFs.
Battalion plans are generally informal, while the brigade plan is more formalized. As the plans move vertically, the BICC reviews them to ensure there is no gap in the R&S scheme. It satisfies any gaps with assigned resources. If this is not possible, it requests assistance from higher headquarters. A formal R&S plan follows the format of a five-paragraph OPLAN/OPORD with appropriate overlays. (See Appendix E.)
Aerial surveillance is vital to the R&S program, particularly at brigade level and above. The OV1-D Mohawk, with SLAR, infrared, and aerial photography capabilities, represents the primary Army surveillance system available to the tactical commander. The supporting Air Force tactical air reconnaissance squadron satisfies aerial R&S requirements that exceed the capabilities of Army aircraft. There are two types of aerial surveillance and reconnaissance requests: Preplanned and immediate.
The brigade or battalion S2 submits preplanned requests for aerial surveillance through intelligence channels to division. They are submitted for anticipated requirements for reconnaissance support. The approval or disapproval of each request is contingent upon the following questions:
- Is the request valid?
- Can the requesting unit satisfy the requirement with organic or supporting resources?
- Can the request be satisfied in time?
- Is the requested information or intelligence already available?
- Can it be included in missions which are in progress?
- Can it be satisfied by missions previously requested and planned at the reviewer's level?
- Are air assets available at the reviewer's echelon which can accomplish the mission?
Actions taken upon completion of this review include--
- Disapprove the request and return it to the requestor with the reason for disapproval.
- Approve the request and task assets at the local echelon.
- Approve the request and pass it on to the next higher headquarters.
Immediate requests, by virtue of their urgency, are sent by a different communications channel. The USAF maintains a system from battalion to corps to provide liaison, rapid communications, and control for both close air support and air reconnaissance. A TACP, equipped and staffed by the Air Force, is assigned to each Army echelon from battalion to corps and has direct radio contact with all echelons. (It should be noted here that TACP radios are not usually compatible with those of the supported unit.) The immediate request is delivered to the TACP, which transmits it directly to the air support operations center (ASOC) at corps. The TACPs at intermediate command echelons monitor immediate requests, and notify their Army counterparts. Approval at each echelon is signified by remaining silent on the air request net. If a higher echelon decides to disapprove the request or to accomplish the mission with organic assets, then that echelon enters the air request net and notifies the originating TACP of its decision. If all echelons approve the request by maintaining silence, the corps ASOC forwards it to the TACC.
Each echelon of command has a time limit (established by SOP) within which to disapprove a request.
In addition to the preplanned and immediate requests, the brigade or battalion S2 may request intelligence imagery reports (IIRs) on missions already flown that may have information they can use.
The following illustration shows the procedures for requesting tactical air reconnaissance support. As shown, the S2 and tactical surveillance officer at each level are responsible for the request, and must assume responsiblity for satisfying valid requests they disapprove. See TC 34-50 for further explanation of R&S.
OPERATION ORDER/OPERATION PLAN
The preparation of an OPORD/OPLAN is an essential element in preparing for IEW operations. Upon determination of intelligence tasking requirements, the brigade or battalion staff will prepare an intelligence estimate and annex to support the OPORD or OPLAN which is used for initial tasking.
An operation order gives subordinate commanders the essential information needed to carry out an operation. This includes the situation, mission, assignment of tasks, and support and assistance to be provided. When an operation is to be conducted immediately, the complete order is prepared, based on the commander's announced decision and concept. When an operation is to be conducted at some future time, the OPORD may be an OPLAN that will be implemented by appropriate instructions. A new order is prepared whenever a significant change in the mission occurs or a new mission is received.
An OPORD should include only the details that are necessary to enable commanders of subordinate units to issue their own orders, and to ensure coordination.
The brigade or battalion S3 has the primary responsibility of preparing the OPORD in accordance with the commander's guidance.
When preparing the OPORD/OPLAN, the S2 must read and review the higher headquarters intelligence estimate and annex before writing his own. Essentially, the battalion or brigade S2 is scaling down the higher headquarters annex or estimate to fit the needs of his echelon. The generated annexes and estimates should provide more specific information about the enemy and AO as it affects the battalion or brigade. Formats for the intelligence annex and estimate, and the analysis of the AO can be found in Appendix A.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|