FM 34-80: Brigade And Battalion Intelligence and Electronic Warfare Operations
CHAPTER 1
THE MISSION
Brigade and battalion commanders plan and direct the close operations on the air-land battlefield against enemy battalions and companies of first-echelon regiments. They must also be prepared to engage follow-on forces and first-echelon sustainers located within or entering their assigned areas of operations (AO).
Successful close operations depend on the ability of the combined arms team to find, fix, fight, and finish enemy forces through a combination of offensive and defensive operations. IEW resources, to include the S2, the S3, and all reconnaissance, surveillance, and target acquisition (RSTA) assets are members of the combined arms team. Their mission is to provide brigade and battalion commanders the accurate, timely, and effective intelligence, counterintelligence, and electronic warfare support necessary to plan, direct, and conduct successful combat operations.
INTELLIGENCE
Intelligence impacts directly on the effects of maneuver, firepower, protection, and leadership--the components of combat power. Accurate intelligence is critical to the brigade and battalion commander's decisions regarding when, where, and how to employ maneuver and firepower. It provides the information necessary to select appropriate protective measures essential to the security of the command. It also provides the knowledge which enables leaders to lead and win. Historically, commanders who have possessed superior knowledge of the enemy, weather, and terrain--intelligence--have proven victorious in battle. Their success, the result of avoiding enemy strengths while exploiting weaknesses and the element of surprise, depended on their knowledge of the area in which they fought.
Today, brigade and battalion commanders consider the battlefield in terms of the time and space necessary to defeat or bypass an enemy force before it can reactor be reinforced. They are concerned about an area of operations in which they need to see and fight by means of maneuver and fire support; and an area of interest about which they seek and receive information regarding the enemy, weather, and terrain.
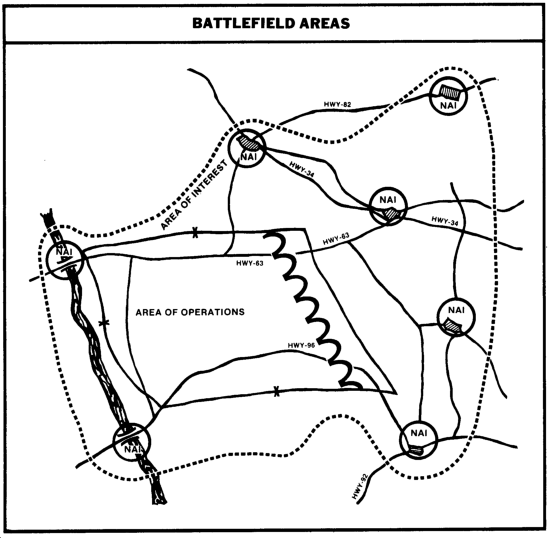
AREA OF OPERATIONS
An area of operations is defined as that portion of an area of conflict necessary for military operations (JCS Pub 1). Areas of operations are geographical areas assigned to commanders for which they have responsibility and in which they have authority to conduct military operations. The assigned area of operations is based on the factors of METT-T and must be of sufficient size to allow completion of the assigned mission. Commanders at each level are normally assigned areas of operations which extend beyond the FLOT or attack objectives a distance commensurate with the planning horizons shown below. They rely on the next higher echelon and adjacent units for information pertaining to enemy forces located beyond the limits of their respective AO and within their areas of interest.
AREA OF INTEREST
An area of interest is not assigned by a higher headquarters and is not delineated by any boundaries. It is determined by brigade and battalion commanders and usually includes their assigned area of operations and adjacent areas in which enemy forces are or maybe located. The area of interest extends into enemy-held territory to the objectives of current and planned operations. Such areas frequently contain named areas of interest (NAI), routes or avenues of approach, and specific enemy units which may jeopardize the accomplishment of the unit's mission. A phase line is normally used to distinguish the forward limits of the assigned AO. Phase lines support "hand-off" operations as enemy forces enter or exit the division, brigade, and battalions' assigned AO and specified areas of interest, respectively, as shown below.
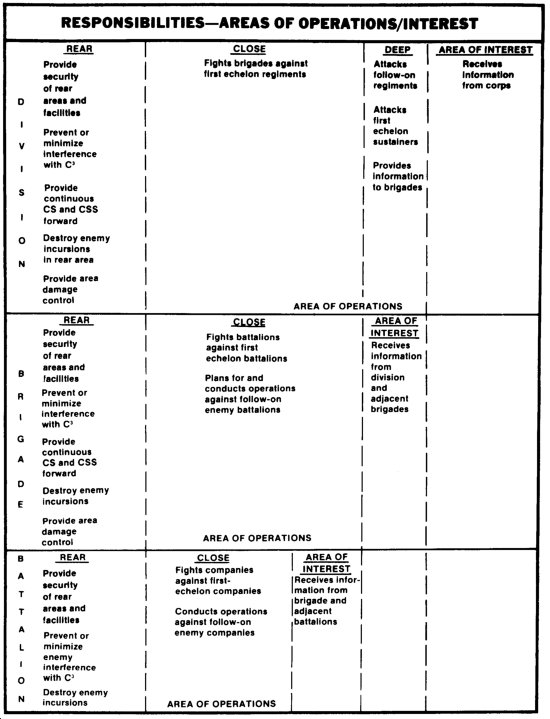
Rear, close, and deep operational responsibilities for the division are summarized below. Brigade and battalion responsibilities for rear and close operations are also shown. Divisional brigades and smaller tactical units do not normally conduct separate deep operations but their planning and operations must anticipate actions of enemy uncommitted units.
Commanders' Information Needs
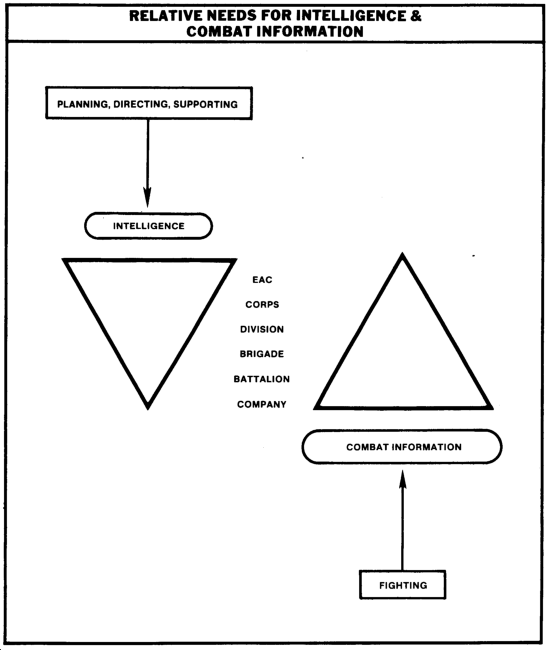
Areas of operations and interest are significant because they generate, in general terms, the commanders' information needs. There are two categories of information which are critical to brigade and battalion commanders. They are intelligence and combat information.
Intelligence is the result of processing all available information known about enemy forces--their composition, disposition, and intentions, as well as their locations, their direction and speed, and their combat readiness. Expeditious processing, timely production, and rapid dissemination of intelligence is necessary to plan, direct and support the brigade and battalions' close operations.
Combat information, on the other hand, is unevaluated data gathered by, or provided directly to, the tactical commander. Due to its highly perishable nature or the criticality of the situation, it cannot be processed into tactical intelligence in time to satisfy the user's tactical intelligence requirements.
Intelligence and combat information are equally important. Both provide targeting data for IEW, maneuver, and fire support systems at each echelon. The inverse relationship regarding their relative worth at higher and lower echelons is directly keyed to the time available for respective commanders to make decisions and take the action necessary to accomplish their mission.
Company and battalion commanders fight what they can see and shoot. They need information about enemy activity within their AO as it becomes available. Brigade commanders need such information within 15-30 minutes. Information about enemy activity within brigade and battalion areas of interest must be provided in time to plan future operations. The specific time required to plan future operations at brigade and battalion is METT-T dependent.
Specific Information Requirements
Tactical intelligence operations at the brigade and battalion begin with the commander. He conveys his information needs to the S2 who converts them into priority intelligence requirements (PIR) and other information requirements (IR) for the commander's approval or modification. The intelligence officer translates PIR and IR into specific intelligence, reconnaissance, and surveillance missions for subordinate, attached, and supporting units and requests information from the next higher echelon. He receives and evaluates information from all sources, develops and nominates high payoff targets (HPT), and reports intelligence results to higher, lower, and adjacent units.
Battalion commanders plan, direct, coordinate, and support the brigade's close operations against enemy first-echelon battalions. Their mission is to locate, close with and destroy enemy forces using fire-power, maneuver, shock effect and surprise in coordination with other combat arms. They must also be prepared to attack enemy second-echelon battalion maneuver forces and first-echelon sustainers, as well. Detailed preplanning and rigorous RSTA activities prior to the initiation of hostilities or before actual contact with enemy forces is made are absolutely critical to the battalions' success.
Battalion commanders need specific information and accurate intelligence from the brigade and higher headquarters to plan their operations. They need timely combat information and targeting data from subordinate, adjacent, and supporting units to refine their plan and to win their offensive and defensive battles. Their specific information requirements for attacking and defending are consolidated, due to the speed with which they must react on the extremely dynamic and volatile air-land battlefield. They must know--
- Location, direction, and speed of platoon and company-size elements within the enemy's first-echelon battalions.
- Location, direction, and speed of enemy second-echelon battalions which indicate the first-echelon regiment's main effort.
- Locations and activities of follow-on battalions in enemy second-echelon regiments.
- Disposition and strength of enemy defensive positions and fortifications.
- Location of antitank positions, crew-served weapons, individual vehicle positions, and dismounted infantry.
- Locations of barriers, obstacles, minefield, and bypass routes.
- Effects of terrain and prevailing weather conditions throughout the course of combat operations.
- Capability of enemy force to employ air assets.
- Availability and probability of use of enemy radioelectronic combat (REC) assets to disrupt friendly C3.
- Possibility of special weapons.
- Probability of enemy use of nuclear, biological, and chemical (NBC) weapons.
Brigade commanders need and use specific information to plan, direct, coordinate, and support the close operations of the division against enemy first-echelon regiments, their battalions, companies, and combat support units--the sustainers. They also need accurate intelligence about enemy second-echelon regiments within first-echelon divisions and any follow-on forces which can close on their AO before the current engagement can be decisively concluded.
Brigades strive to attack enemy first-echelon forces while they are on the move and before they can deploy into combat formations. The brigade commander needs specific information about--
- Composition, equipment, strengths, and weaknesses of advancing enemy forces.
- Location, direction, and speed of enemy first-echelon battalions and their subordinate companies.
- Locations and activities of enemy second-and follow-on echelons capable of reinforcing their first-echelon forces in the close operations area.
- Location of enemy indirect fire weapon systems and units.
- Location of gaps, assailable flanks, and other tactical weaknesses in the enemy's order of battle (OB) and OPSEC posture.
- Air threat.
- Enemy use of NBC.
- Effects of weather and terrain on current and projected operations.
- Anticipated timetable or event schedule associated with the enemy's most likely course(s) of action.
Should the enemy succeed in establishing his defensive positions, then brigade commanders' specific information requirements increase. They must then know the specific types, locations, and organization of enemy first- and second-echelon defensive positions and fortifications. These include--
- Barriers, obstacles, fire sacks, and antitank (AT) strong points.
- Locations of antiaircraft and missile artillery (AAMA) units.
- Locations of surface-to-air missile (SAM) units.
- Location of REC units.
- Location of reserve maneuver forces.
- Enemy ability to conduct deep attack into friendly rear area.
Brigade commanders given defensive missions, or forced to defend in given sectors, require specific information about assaulting enemy companies, battalions, regiments, and divisions--generally, their strength, composition, and direction of attack. The same information is required about enemy follow-on units that can affect brigade combat operations. Of specific concern are the locations, size, activities, direction, and speed of enemy air-assault, heliborne, and tactical air (TACAIR) units capable of dealing lethal and decisive blows to brigade units and which could potentially be used to thwart any counterattack.
Specific information about enemy first- and second-echelon regimental C3 facilities is of paramount concern to the brigade commander, whether on the offense or defense. He must know the specific locations of enemy--
- Division forward, and main command posts (CPs).
- Regimental and battalion CPs.
- Fire direction control (FDC) centers.
- Command observation posts (COPs).
- Radio and radar reconnaissance sites.
- Radioelectronic combat sites.
- Target acquisition sites.
The suppression, neutralization, and destruction of enemy C3 systems and facilities are critical to the success of the close operations. Brigade commanders, in concert with supporting division and corps IEW, maneuver, and fire support (FS) units, use all available means to identify, locate, disrupt, and destroy these extremely high payoff targets. Their objective is to neutralize the enemy commanders' capability to command troops and control weapon and combat support systems. Degrading or denying the ability of the enemy commander to conduct his attack as planned is done by systematically attacking key "nodes" and "information links" in the enemy commander's command and control (C2) system, which supports their decision making process. This form of command and control warfare is founded upon the basic tenets of command, control, and communications countermeasures (C3CM) strategy, defined below.
The integrated use of operations security (OPSEC), military deception, jamming, and physical destruction, supported by INTELLIGENCE, to deny information, to influence, degrade, or destroy enemy command, control, and communications (C3) capabilities; and to protect friendly C3.
The protection of friendly command, control, and communications--protect C3--is the number one priority under C3CM strategy. Intelligence supports the protection of friendly C3 primarily through counterintelligence support to OPSEC and deception.
COUNTERINTELLIGENCE
The mission of CI is to detect, evaluate, counteract, or prevent hostile intelligence collection, subversion, sabotage, and international terrorism conducted by or on behalf of any foreign power, organization, or person operating to the detriment of the US Army. CI personnel are responsible for identifying the hostile intelligence collection threat. They, together with operations personnel, develop friendly force profiles, identify vulnerabilities, and make recommendations to reduce those vulnerabilities.
Counterintelligence operations support the division's overall OPSEC program. They are designed to protect the brigade and battalion by countering enemy attempts to identify and locate friendly combat and combat support forces. Division CI operations are conducted to support OPSEC, deception, and rear operations.
COUNTERINTELLIGENCE SUPPORT TO OPSEC
CI support to OPSEC is the principal role of CI at echelons below division. It includes--
- The identification and analysis of enemy reconnaissance, surveillance, and target acquisition (RSTA) capabilities, personnel, units, and activities.
- The identification and analysis of enemy REC units, locations, and activities.
- Assisting in the development of friendly force profiles.
- Determining friendly vulnerabilities to enemy RSTA and REC activities.
- Recommending and evaluating appropriate OPSEC and deception measures.
COUNTERINTELLIGENCE SUPPORT TO DECEPTION
Military deception operations are planned, controlled, directed, and conducted by commanders at echelons above division (EAD). They are designed to mislead enemy senior military and political leaders regarding our true military objectives, our combat capabilities and limitations, and the composition and disposition of our combat forces.
Battlefield deception operations are controlled, directed, coordinated, and executed by corps and division commanders in accordance with the overall military deception plan. Battlefield deception is deliberate action to achieve surprise on the air-land battlefield. Its purpose, ultimately, is to mislead enemy ground force commanders as to our true combat objectives, our tactical order of battle, our major axis of advance, and the disposition of our reserve and combat support units, defensive positions, fortifications, and C3 facilities.
Corps, division, brigade, and battalion commanders also plan, direct, coordinate, support, and conduct battlefield deception operations to achieve surprise and create opportunities for decisive tactical maneuver in order to break contact with and bypass enemy forces, seize their true objectives, and accomplish their missions. Such battlefield deception operations support the attack and defense; however, they are offensive rather than defensive in nature. They are directly keyed to deceptive forms of maneuver, such as demonstrations and feints. Such deceptive maneuvers may be used to seize secondary tactical objectives. They may also represent or turn out to be the preparatory phase of a combat operation designed to achieve surprise in seizing primary tactical objectives.
Brigades and battalions participate in the deception effort regardless of its nature, military or tactical, and whether they know it or not. Their participation may be limited to practicing sound OPSEC measures on a regular and standard basis in accordance with established unit standing operating procedures (SOP). They may also participate in or employ active deceptive measures such as outlined above. In either case, counterintelligence does support their deception operations. The principal CI functions conducted in support of brigade and battalion deception operations are similar to those performed in support of OPSEC.
COUNTERINTELLIGENCE SUPPORT TO REAR OPERATIONS
Counterintelligence support to rear operations includes identifying and analyzing the enemy threat to brigade trains and both division support command (DISCOM) and corps support command (COSCOM) operations. CI personnel recommend steps to neutralize enemy agents, saboteurs, terrorists, sympathizers, and special purpose forces. Brigade and battalion commanders, their staffs, and all subordinate personnel must be trained and prepared to identify and report enemy units or activities which may pose a threat to brigade trains, DISCOM, and COSCOM operations. The potential impact on close operations from the rear cannot be overlooked.
ELECTRONIC WARFARE
EW is an essential element of combat power. It can provide brigade and battalion commanders both a passive and an active means to protect their C3 systems and a passive and an active means to attack the enemy commanders' C3 system as well. Protecting C3 is the number one priority for EW in accordance with C3 CM strategy. Action taken to deny, influence, and degrade or destroy enemy C3 capabilities, counter-C3, is equally important. Electronic warfare, like other elements of combat power on the air-land battlefield, is waged by employing a combination of both offensive and defensive operations, tactics, and procedures. Air-land battle doctrine and the spirit of the offense are the overriding considerations in planning and conducting EW operations. (See Chapter 5, FM 34-l.)
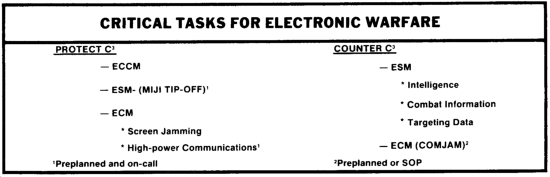
PROTECT COMMAND, CONTROL, AND COMMUNICATIONS
Electronic counter-countermeasures (ECCM), or defensive EW, are the responsibility of all soldiers who use or who supervise the use of communications-electronics (C-E) equipment. ECCM are passive in nature and are used to protect friendly C3 systems against enemy REC activities. Passive ECCM include both antiintercept and locate (for example, emission control, terrain masking, and avoidance) procedures and antijam or kill (for example, C-E equipment design) features. ECCM also includes the immediate identification and reporting of meaconing, intrusion, jamming, and interference (MIJI) on a friendly C3 facility.
Electronic warfare support measures (ESM) can provide commanders the capability to intercept, identify, and locate enemy emitters. It represents a source of information required for jamming, deception, ECCM, targeting, and other tactical employment of combat forces. ESM supports the destruction and jamming of enemy C3 systems through acquisition and reporting of targeting data. ESM also supports the commander's efforts to counter enemy OPSEC and deception.
Electronic countermeasures (ECM), in general, and communications jamming (COMJAM systems, in particular, can provide brigade and battalion commanders two active capabilities to protect their C3 systems. The first is screen jamming, or COMJAM screening. COMJAM screening is the jamming of enemy communications intercept and direction finding (DF) receivers to preclude this information gathering or locating efforts against friendly high-value communications.
Communications jamming systems can provide brigade and battalion commanders with a means to communicate with one another, as well as with senior and adjacent unit commanders in worst-case situations when enemy jamming is experienced and no other means of C3 is possible. The high-power amplifier provided with COMJAM systems is used to "burn through" enemy jamming. Calls for fire, situation reporting, and orders to subordinate units can still be communicated.
COUNTER COMMAND, CONTROL, AND COMMUNICATIONS
The offensive components of EW, passive ESM and active ECM, provide to brigade and battalion commanders--
- Intelligence to plan, direct, coordinate, support, and conduct combat operations.
- Combat information and targeting data to maneuver their forces and target their weapon systems.
- ECM nonlethal attack capability to systematically disrupt the C3 systems of enemy first- and second-echelon units located within the brigade's and the division's assigned AO.
CRITICAL TASKS
Command and control warfare in air-land combat operations is complex when viewed as a maze of intangible electronic signals criss-crossing above and over the battlefield. Command and control warfare, however, can be reduced to the most simple terms of reference and understanding. It is composed of both tangibles and intangibles. The tangibles are the C3 "nodes" which present visual signatures for commanders to see and shoot. The intangibles are the "information links" between the nodes which can be intercepted, identified, and jammed. There are also the nodes themselves which can be intercepted, identified, and jammed. Depending on the tactical situation and the desired effects of friendly operations, there may also be nodes and links which must be seen and monitored, but neither shot nor jammed. As a general rule, we normally jam and kill the fighters and sustainers, and collect information from the planners and coordinators. When attacking the planners and coordinators will result in the desired alteration of the enemy commander's battle plans, this general rule would obviously by reversed.
Electronic warfare resources available to, or in support of, the brigade and battalions, close operations, though limited, are specifically trained to cope with the intangibles of command and control warfare. However, the critical tasks they must perform in support of the battalion and brigade to win, begin and end with the commander. His operational needs for EW support are just as important as his information needs discussed earlier in this chapter. The following list summarizes the brigade commander's critical tasks for EW.
Each of the IEW tasks derived from the IEW mission (situation development, target development, EW, and CI) is essential to the success of the brigade's and battalion's operations. The composition of the IEW system and how it fulfills the commander's requirements of each IEW task, the employment for specific operations, and the critical functions of sustaining combat operations are explained in specific terms in the chapters which follow. The doctrine is based on, and requires an understanding of, the air-land battle doctrine of FM 100-5 and IEW doctrine espoused in FM 34-1.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|