Operations of the Main Intelligence Administration (GRU)
Glavnoye Razvedyvatelnoye Upravlenie (GRU)
Russian military intelligence, known as the GRU (Glavnoye (Razvedyvatelnoye) Upravlenie Generalnogo Shtaba Vooruzhonnyh Sil RF), collects information for Russia’s political and military leadership on countries and alliances of countries that Russia considers its adversaries or likely adversaries. One of the distinctive features of Russian military intelligence compared with its counterparts in other countries is that, in addition to military intelligence, it also gathers information on the target countries’ and regions’ economy, politics, technology and ecology. Different intelligence disciplines and working methods are used to gather intelligence. The GRU is the foreign intelligence organ of the Russian Ministry of Defense, and it carries out the functions of the central organ of military intelligence within the General Staff. Though sometimes compared to the US Defense Intelligence Agency, its activities encompass those performed by nearly all joint US military intelligence agencies as well as other national US organizations. The GRU gathers HUMINT through military attaches and foreign agents. It also maintains significant signals intelligence (SIGINT) and imagery reconnaissance and satellite imagery (IMINT) capabilities.
GRU intelligence centers recruit agents in foreign countries to prepare Russian military operations. The GRU’s intelligence centers do not only work against countries bordering Russia but also gather information on other European nations. The GRU’s intelligence centers recruit people with access to classified information - but also ordinary citizens - to have them observe sites of interest to the GRU or carry out other more mundane tasks.
Like other Russian special services, the GRU conducts intelligence operations against foreign countries both on the territory of the target country and on Russia’s own soil (known as “intelligence from the territory”). In the target country, intelligence activities are mainly carried out by intelligence officers working in the Russian embassy (known as the “legal rezidentura”) or otherwise undercover (“non-traditional cover”). Intelligence from the territory includes cyber and influence operations that have been extensively covered in Western media, as well as signals intelligence and other technical intelligence. Still, traditional human intelligence (HUMINT), or information gathering through human sources, has not disappeared from the GRU’s toolbox. The GRU’s human intelligence (agenturnaya razvedka, “agent intelligence”) is divided into two categories: strategic agent intelligence (strategicheskaya agenturnaya razvedka, SAR), which covers for example legal rezidenturas and illegals, and operational agent intelligence (operativnaya agenturnaya razvedka, OAR).
The main task of operational agent intelligence, curated by the 15th Directorate of the GRU, is to prepare and support Russian military operations abroad using operational-tactical intelligence gathered on the target country. Networks of agents gather the intelligence. With the help of the information provided by the agent networks, the GRU maps the status and developments within the armed forces in the target country, particularly developments related to NATO presence. Information is also collected on the target country’s key institutions, critical infrastructure, political situation and public sentiment.
The GRU intelligence centers’ area of responsibility west of Russia extends from Scandinavia and the Balkans to Western Europe. Since 2014, the intelligence centers have been operating particularly intensively against Ukraine.
Five intelligence centers in Western Russia have been operating against Europe for decades:
- the 73rd Intelligence Center in St Petersburg,
- the 264th Intelligence Center in Kaliningrad,
- the 74th Intelligence Center in Smolensk,
- the 269th Intelligence Center in Moscow
- the 1194th Intelligence Center in Murmansk
GRU’s area of responsibility is estimated to be 1,500 km from the Russian border; the presence of agents in more distant locations cannot be ruled out either.
Broadly speaking, the intelligence centers’ networks include two types of agents: those permanently residing abroad and those in Russia. The recruited foreign nationals are primarily men who regularly visit Russia, speak fluent Russian, have a positive or at least neutral attitude towards the current Russian regime and are capable of performing intelligence tasks. The identification of suitable candidates, the cultivation of potential agents and their recruitment, training and further handling is generally carried out inside Russia to ensure the safety of the operational officers. During the meetings set up in Russia, the agent hands over the information gathered and receives new tasks and instructions, while the handler also collects information about the agent. If an agent no longer has the opportunity to visit Russia, the intelligence center can arrange a meeting in a third country. To carry out their tasks, the GRU intelligence centers cooperate with other security authorities in Russia, including the FSB, the ministry of the interior, the border guard and the migration service. The recruited agents are mostly male, regularly visit Russia and speak fluent Russian.
Operational officers at the GRU intelligence centers assign tasks to agents depending on their capabilities and access to information. The tasks range from seemingly innocent activities, such as monitoring media and public sentiment in the target country or buying maps, dictionaries and other freely available material, to observing military sites or critical infrastructure and stealing classified information. The agent forwards gathered materials electronically or hands them over to the handler at a meeting in Russia. In the event of a war or similar threat, a communications agent (a permanent resident of Russia) with radio equipment may be dispatched from Russia to agents living abroad to ensure that information is quickly transmitted even if other channels are disrupted.
Since 2014, the intelligence centers have also been organising “agent-combat groups” deployed against Ukraine to carry out bombings and assassinations and prepare arms caches for activation when receiving a signal from Russia (for example, in the event of a major outbreak of hostilities between Russia and Ukraine).
Intelligence centers also recruit agents among residents of Russia. These agents receive special training so that they are ready to deploy to a target country in the event of, or in the run-up to, a conflict where they will carry out intelligence tasks (in particular observation) and also prepare to perform diversions or other special tasks. They can operate abroad in groups or as individual agents and are equipped, among other things, with radio transceivers to communicate with their intelligence center. The intelligence centers in Kaliningrad and Murmansk also recruit agents from among seamen (known as a “ship agent”, sudovoi agent). Among other activities, ship agents carry out visual reconnaissance in port cities worldwide.
Agents generally receive negligible financial remuneration for their assignments or even perform them free of charge. Many operational officers at the intelligence centers are corrupt and keep some of the agents’ pay for themselves. Over the past decade, effective cooperation between intelligence services of NATO member states and partners has led to consistent identification and conviction of agents of GRU intelligence centers in countries bordering Russia.
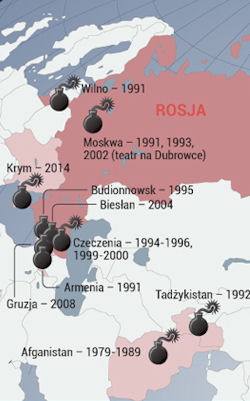 After the events in Ukraine, trust had returned to the Russian military intelligence service of the GRU, which became a secret weapon of Vladimir Putin. It is this organization, shrouded in unseemly glory, that was most responsible for destabilizing the Donbas. Hybrid warfare is an evolution of earlier indirect, proxy and covert wars. It is a way of expanding territory and pushing geopolitical agenda with every means possible up to the point of an overt military action. The Russian intervention in Ukraine generated much debate about the use and effectiveness of hybrid warfare, a type of warfare widely understood to blend conventional/unconventional, regular/irregular, and information and cyber warfare.
After the events in Ukraine, trust had returned to the Russian military intelligence service of the GRU, which became a secret weapon of Vladimir Putin. It is this organization, shrouded in unseemly glory, that was most responsible for destabilizing the Donbas. Hybrid warfare is an evolution of earlier indirect, proxy and covert wars. It is a way of expanding territory and pushing geopolitical agenda with every means possible up to the point of an overt military action. The Russian intervention in Ukraine generated much debate about the use and effectiveness of hybrid warfare, a type of warfare widely understood to blend conventional/unconventional, regular/irregular, and information and cyber warfare.
The term ‘hybrid warfare’ appeared at least as early as 2005 and was subsequently used to describe the strategy used by the Hezbollah in the 2006 Lebanon War. Since then, the term “hybrid” has dominated much of the discussion about modern and future warfare, to the point where it has been adopted by senior military leaders and promoted as a basis for modern military strategies.
The gist of the debate is that modern adversaries make use of conventional / unconventional, regular / irregular, overt / covert means, and exploit all the dimensions of war to combat the Western superiority in conventional warfare. Hybrid threats exploit the “full-spectrum” of modern warfare; they are not restricted to conventional means.
As the conflict in Ukraine illustrated, hybrid conflicts involve multilayered efforts designed to destabilise a functioning state and polarize its society. Unlike conventional warfare, the “center of gravity” in hybrid warfare is a target population. The adversary tries to influence influential policy-makers and key decision makers by combining kinetic operations with subversive efforts. The aggressor often resorts to clandestine actions, to avoid attribution or retribution. Without a credible smoking gun, NATO might find it difficult to agree on an intervention.
Many rules of conspiracy and espionage techniques were borrowed from prerevolutionary practice, and then updated and improved. However, new techniques and scientific advances have also begun to be used. As the simplest protection are aliases. All nicknames are assigned only by the Moscow Center. This precaution is necessary in order to avoid duplication. Residents and agents know each other only by pseudonyms, for understandable reasons it is strictly forbidden to try to find out the real name.
Among the new terms appeared such as a "music box" - a radio transmitter, a "shoe" - a passport, a "shoemaker" - a specialist in the forgery of passports. The local communist party is a "corporation", other agents in a given country (or at the country's embassy) are "neighbors". Conditional names of states are also used. So, Germany can be called "Jersey", France - "Florence", Britain - "Brazil". The chief of military intelligence in Moscow is the "director", and his first deputy is the "commander".
The GRU aggressively supplemented the KGB with espionage and massive technical surveillance operations. The GRU coordinated and supported Soviet SIGINT and overhead photography and trained foreign revolutionary cadres and insurgents. In the operational Soviet military, "Spetsnaz" (Special Forces) units had an overseas role as special purpose commando forces capable of covert infiltration, sabotage and assassination operations.
"Legal" HUMINT operations are conducted by intelligence officers under official cover. The term does not mean "lawful," because case officers recruit and handle espionage agents. The FBI estimated in the 1980s that at least 30% of the 1,500 Soviet officials in the US were KGB or GRU staff officers. Reportedly, over 3,000 KGB officers and approximately 1,500 GRU officers were posted outside the Soviet Union. "Illegals" are trained intelligence officers sent abroad, often with false identities, who maintain no overt contact with their government. The number of Soviet illegals and their activities were very difficult to estimate.
Within the Soviet services, GRU personnel were targeted primarily against military and scientific and technical information, while KGB personnel in its First Chief Directorate (foreign intelligence) are assigned to one of four operational departments or "lines"- Scientific and Technical (Line X), Political (Line PR), Counterintelligence (Line KR), or Illegals Support (Line N). S&T personnel specifically targeted U.S. advanced technology. Often, clandestine collection of S&T information is preferred over buying or developing technology because it is cheaper and provided the best short-termresults, although there was a risk factor in theft.
By the 1980s the United Nations employed, worldwide, approximately 800 Soviet nationals as international civil servants, with about 300 of them in New York. Approximately one-fourth of the Soviets in the Secretariat in New York were considered to be intelligence officers, and many others are co-optees who have been told to respond to KGB and GRU requests for assistance. The Soviet intelligence services also use their developed agents in the United Nations to collect information on UN activities; to spot, assess and recruit American and foreign-national agents; to support worldwide intelligence operations;and to collect scientific and technical information on the United States.
The openness of US society permitted the Soviets to acquire much of the information their Military Industrial Commission (VPK) of the Presidium of the Council of Ministers has identified for collection through non-clandestine means. The GRU was believed to have satisfied considerably more Military Industrial Commission (VPK) requirements than the KGB. This success was attributed partly to the GRU's greater scientific orientation and its wider variety of technology-related cover positions. The approximately 1,500 GRU officers serving outside the USSR had scientific and technological collection as an integral part of their responsibilities. The KGB S&T unit, Line X, had nearly 300 officers on foreign assignment operating under cover of Soviet embassies, trade and commercial organizations, as members of exchange groups, and as employees of international organizations (the United Nations Secretariat, for instance, as in the case of Gennadiy Zakharov).
Another program, managed by the Ministry of Foreign Trade and the KGB/GRU, sought, through trade diversions, to acquire relatively large amounts of dual-use manufacturing and test equipment for direct use on production lines. This program attempts to obtain export-controlled microelectronic, computer, telecommunication, machine-tool, robotic, diagnostic and other sophisticated equipment. This program also utilizes both legal and illegal means. The Ministry of Foreign Trade had hundreds of trade organizations and companies around the world. KGB and GRU officers operating under cover of these establishments collect large quantities of data openly, in addition to that derived from their covert operations. The Ministry, as an independent collector, helped meet about 15 percent of all fully satisfied VPK requirements during the late 1970s and early 1980s.
The GRU was led by General Fedor Ladygin in the 1990s, who stated that the GRU is increasingly focused on target areas, in which civil and military interests intersect. In an interview in the Komsomolskaya Pravda of 05 November 1996 Ladygin stated that one of the main priorities of his organization be the military-related economic and technical espionage, to prevent Russia from sinking "to the status of a third world country."
An agreement on intelligence cooperation between Russia and China was signed in Beijing at the end of the summer of 1992. It envisaged the restoration of the cooperation in the area of intelligence which had been cut off in 1959. This secret treaty covered the activities of Russian Military Strategic Intelligence (GRU) and the Foreign Intelligence Service, which are cooperating with the Chinese People's Liberation Army's Military Intelligence Directorate.
The FSB and the GRU Intelligence Directorate of the ZakVO [Transcausasus Military District] (now the GRVZ [Group of Russian Forces in Transcaucasia]) acted jointly in the 1991 "New Year coup" in Georgia. However, the two agencies were reportedly supporting different sides the war in Abkhazia.
Since 1992 the GRU was responsible for reconnaissance operations in the territories of the former USSR, but it was completely unprepared to perform its function after the end of the Cold War. An agent of the Federal Security Service (FSB) said that GRU can not do anything in the near abroad Russia "besides counting tanks". It was on GRU that Putin laid a partial responsibility for the worst-than-expected course of the Russian campaign in Georgia in 2008. In Moscow the prevailing opinion was that the concentration of the main directorate on "Kinetic operations ", such as actions carried out by paramilitary assault forces, did not correspond to the new times of cyber and more subtle elements of pressure, such as an energy policy.
The professional work of "polite people" made it possible to disarm, without a single shot, the 30,000-strong grouping of Ukrainian troops. The occupation of the Crimea without a single shot was made possible thanks to a plan under which the foundation of the intelligence activity of the GRU was laid. Moreover, many of the "green men" who captured the peninsula are current or former special forces trained by military intelligence. This was also the case of the Donbass. The profile of the GRU's activities fits well not only in the conflict in Ukraine, but also entirely in the alleged doctrine of Russia in the near future.
Russian government hackers broke into the computer network of the Democratic National Committee and gained access to "research" on Republican presidential candidate Donald Trump. “When we discovered the intrusion, we treated this like the serious incident it is," said Representative Debbie Wasserman Schultz, chairwoman of the Democratic National Committee. "Our team moved as quickly as possible to kick out the intruders and secure our network.” Russian spies also targeted the networks of Donald Trump and Democratic presidential candidate Hillary Clinton, as well as computers of Republican political action committees.
According to security researchers, two separate groups entered the DNC's system and read email and chat communications. CrowdStrike, the cyber firm that helped clean up the breach, said it has already kicked out the two hacker groups. The second group, nicknamed Fancy Bear, was said to be working on behalf of Russia's military, according to Dmitri Alperovitch, the company’s chief technology officer. It gained entry in April 2016 and reviewed the opposition research on Donald Trump.
Emails among Democratic Party leaders during the early stages of the 2016 presidential candidate selection process appeared to show that party insiders mocked and criticized Senator Bernie Sanders, even while they were publicly claiming neutrality in the contest between him and Hillary Clinton, according to information made public July 23, 2016 by WikiLeaks. Nearly 20,000 emails, all apparently copied from email accounts of seven members of the Democratic National Committee, cover a period from January 2015 through May of this year — before Clinton's victory over Sanders was confirmed.
WikiLeaks, a group that publishes original documents from anonymous sources and leakers, released the data without indicating its source, but the 17-month period ended just before a hacking incident in June 2016 at the DNC. Democratic officials said at the time that hackers based in Russia were responsible for the intrusion.
Clinton's campaign manager, Robby Mook, said on Transcript via ABC’s This Week: 24 July 2016 "... what’s disturbing about this entire situation is that experts are telling us that Russian state actors broke into the DNC, took all these emails and now are leaking them out through these Web sites.... And it’s troubling that some experts are now telling us that this was done by — by the Russians for the purpose of helping Donald Trump. ... It was concerning last week that Donald Trump changed the Republican platform to become what some experts would regard as — as pro-Russian."
"It is the ugly little secret that the Trump campaign doesn’t want to discuss. When Donald Trump Jr. was asked about support of his dad by the Russian government, he blew a gasket on CNN. Trump can ramble on about emails all he wants, but the reality is that there is only one candidate who is being backed by a government that the Republican Party considers an enemy to America."
On 29 December 2016 President Obama authorized a number of actions in response to the Russian government’s aggressive harassment of U.S. officials and cyber operations aimed at the U.S. election in 2016. Russia’s cyber activities were intended to influence the election, erode faith in U.S. democratic institutions, sow doubt about the integrity of the electoral process, and undermine confidence in the institutions of the U.S. government. The President sanctioned nine entities and individuals: two Russian intelligence services (the GRU and the FSB); four individual officers of the GRU; and three companies that provided material support to the GRU’s cyber operations. Sanctioned individuals include Igor Valentinovich Korobov, the current Chief of the GRU; Sergey Aleksandrovich Gizunov, Deputy Chief of the GRU; Igor Olegovich Kostyukov, a First Deputy Chief of the GRU; and Vladimir Stepanovich Alexseyev, also a First Deputy Chief of the GRU.The three other entities include the Special Technology Center (a.k.a. STLC, Ltd. Special Technology Center St. Petersburg) assisted the GRU in conducting signals intelligence operations; Zorsecurity (a.k.a. Esage Lab) provided the GRU with technical research and development; and the Autonomous Noncommercial Organization “Professional Association of Designers of Data Processing Systems” (a.k.a. ANO PO KSI) provided specialized training to the GRU.
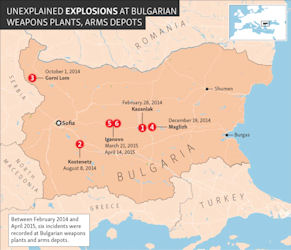 Bulgaria accused and wanted three Russian agents of the attempted murder of arms dealer Emilian Gebrev in 2015. The prosecutor's office detained a group of Bulgarians on charges of organizing a military espionage network in favor of Russia . For several months, Sofia has been prosecuting Russian diplomats for espionage. What remained unexplained, however, was the series of incidents in military production and warehouses that coincide with frequent visits by Russian agents to Bulgaria. Exactly on this topic were expected more developments - the international investigation platform Bellingkat announced that it will publish its findings, and two Bulgarian MPs sent a question and expect an answer from Borisov on the topic of Russian agents and explosions.
Bulgaria accused and wanted three Russian agents of the attempted murder of arms dealer Emilian Gebrev in 2015. The prosecutor's office detained a group of Bulgarians on charges of organizing a military espionage network in favor of Russia . For several months, Sofia has been prosecuting Russian diplomats for espionage. What remained unexplained, however, was the series of incidents in military production and warehouses that coincide with frequent visits by Russian agents to Bulgaria. Exactly on this topic were expected more developments - the international investigation platform Bellingkat announced that it will publish its findings, and two Bulgarian MPs sent a question and expect an answer from Borisov on the topic of Russian agents and explosions.
After 2014. Russia then occupied and annexed the Crimean peninsula, while at the same time supporting militarily and financially the pro-Russian separatists in eastern Ukraine who were fighting the Ukrainian army. Ukraine is experiencing difficulties in supplying its armed forces with weapons and ammunition and is beginning to look for products that are compatible with its army, staffed by Warsaw Pact standards. The required products are available to the former allies, who are now part of NATO.
Then military productions and warehouses began to explode in the countries of the North Atlantic Alliance. At the same time, Russian military intelligence agents, known as the GRU, often travel to Europe. In particular - to secret detachment 29155. Members of this group have already been formally charged and wanted by Britain, the Czech Republic, Montenegro and Bulgaria - charges ranging from attempted murder, through explosions, to coup attempts.
On 17 April 2021, the Prime Minister of the Czech Republic, Andrej Babiš, announced data from the investigation of the Czech services. They show that two Russian military intelligence agents were responsible for two explosions in late 2014 at a military production warehouse in Vrbetice, southern Bohemia. The Czech Republic was backed by all European Union and NATO countries, and several other countries also expelled Russian diplomats in solidarity.
On February 28, 2014, an explosion at the Arsenal weapons complex in Kazanlak, east of Sofia, partly destroyed a workshop where gunpowder was produced, killing one person. Six months later, on August 8, 10 people were injured in a series of explosions at the TEREM-Tsar Samuil military plant in Kostenets, in southwestern Bulgaria. Less than two months later, on October 1, the deadliest disaster to hit a Bulgarian munitions facility struck at the Midzhur plant in Gorni Lom. Aside from the 15 dead, two other people were wounded. In the third week of December, a private manufacturing company of ammunition and hunting ammunition in Maglizh, in southern Bulgaria, was hit with an unexplained explosion that killed one person. The explosions all occurred during a period of high tensions in Eastern Europe sparked by Russia's invasion and annexation of Ukraine's Crimean Peninsula, and the outbreak of a Russian-backed separatist war in eastern Ukraine.
GRU Unit 29155 was specifically named by Czech Prime Minister Andrej Babis in an emergency news conference on 17 April 2021 in which he accused the unit of being involved in at least one of the arms-depot explosions in the east of the Czech Republic in 2014. The ammunition has been linked to Gebrev, who allegedly was arranging to broker a sale with Ukraine as officials there sought to bolster their beleaguered armed forces. Gebrev has denied those allegations. A top former Ukrainian intelligence official confirmed that Ukraine was working with a Bulgarian arms dealer at the time.
Todor Tagarev, a former Bulgarian defense minister, said the Czech revelations and new data about GRU agents in Europe absolutely called for a new investigation into the Bulgarian explosions. "The arms industry is dangerous, there are accidents. But production processes are structured in such a way that in case of an accident there are minimal damages and consequences, but six explosions in less than two years, this is already becoming very dubious," Tagarev told RFE/RL's Bulgarian Service.
Police in the Czech Republic on 30 April 2024 shelved a probe into the destruction of ammunition warehouses that took place ten years ago. Despite all of their leads turning up cold, the investigators maintain that Russian military intelligence blew up the structures. The explosions occured in October and December 2014 at arms depots in Vrbetice in the south of the country, killing two Czech nationals. Prague said at the time that the warehouses had been storing ammunition that was to be sent to Ukraine. The authorities claimed that Russia sent operatives to destroy the consignment in an attempt to disrupt the shipment. In April 2021, the Czech Republic expelled 18 Russian diplomats over the incident, a move to which Russia responded in kind. In a statement, the head of the National Central Office against Organized Crime of the Criminal Police and Investigation Service (NCOZ), Jiri Mazanek, announced that the case had been closed and that no criminal charges would be filed. “Russian military intelligence had the means to cause explosions,” Mazanek claimed, adding that the NCOZ believes a number of Russian operatives traveled to the Czech Republic at the time of the bombings before immediately returning to Russia. However, he admitted that “some information is missing” about these supposed agents’ movements within the country, and “one can only assume what tasks” they actually carried out and with whose help. With Russia refusing to assist the investigation and no further evidence available from the crime scene or from neighboring countries, Mazanek explained that “the police authority cannot obtain additional information that would allow the initiation of criminal prosecution, and for this reason decided to postpone the case.” Despite the dead end, the police authority “considers it proven” that the explosions were “carried out by members of the Russian military intelligence, the Main Administration of the General Staff of the Armed Forces of the Russian Federation, known by the abbreviation GRU,” Mazanek added. According to the statement, the 2014 blasts were “part of a long-term diversionary operation by Russian military intelligence” on EU and Ukrainian soil. Commenting on similar claims by Czech authorities back in April 2021, Russian Foreign Ministry spokeswoman Maria Zakharova described them as a “shameful dead end,” suggesting that Prague had failed to provide any meaningful evidence. Around the same time, Kremlin spokesman Dmitry Peskov alleged that the Czech Republic had imitated the US in taking “unpredictable and aggressive actions” against Moscow and said that the claims were “absolutely groundless.” A blaze engulfed a plant in Berlin belonging to German arms manufacturer Diehl, the local fire department reported 03 May 2024. The company produces the IRIS-T air defense system, several units of which the German government has supplied to Ukraine since late 2022. In a post on X (formerly Twitter) on Friday, the Berlin Fire Department reported that a “factory building is burning in which chemicals are also stored,” and that 190 personnel had been deployed at the scene. “Air quality tests are being continuously conducted” in the area, the message adds. Several large detonations have been observed inside the facility since the start of the blaze, which has been raging for more than five hours. A fire department representative told the press that emergency personnel have not yet been able to bring the situation under control and that the operation is expected to last well into the night. Berliner Zeitung reported that the industrial facility had a stockpile of sulfuric acid and copper cyanide, among other materials. According to the newspaper, citing emergency service officials, elevated pollution levels have so far been detected only in the immediate vicinity of the burning building. In a subsequent post on X, the fire department advised local residents to shut their windows and doors and switch off air conditioning. Berliner Zeitung also quoted a spokesperson for the fire department as saying the blaze had engulfed an area of some 2,000 square meters. Due to the hazardous chemicals inside the plant, firefighters cannot enter the premises and are extinguishing the flames from the outside. On 03 May 2024, the NATO Council adopted a statement in which it accused Russia of hybrid attacks against member countries of this military bloc. "NATO Allies are deeply concerned about recent malign activities on Allied territory, including those resulting in the investigation and charging of multiple individuals in connection with hostile state activity affecting Czechia, Estonia, Germany, Latvia, Lithuania, Poland, and the United Kingdom..... "These incidents are part of an intensifying campaign of activities which Russia continues to carry out across the Euro-Atlantic area, including on Alliance territory and through proxies. This includes sabotage, acts of violence, cyber and electronic interference, disinformation campaigns, and other hybrid operations. NATO Allies express their deep concern over Russia's hybrid actions, which constitute a threat to Allied security." Russian Foreign Ministry spokeswoman Maria Zakharova detailed 04 May 2024 that NATO accused her country of carrying out hybrid attacks against countries of the military bloc to justify the increased militarization of Europe. "The North Atlantic Alliance and the leadership of individual member states are doing what they do best – disinformation, inflating the degree of anti-Russian hysteria in order to justify the unprecedented scale of militarization of Europe. In the same vein is complicity and concealment of the results of the investigation into the Nord Stream explosion. The NATO Council statement fits well with efforts to mislead the people of Europe and North America in order to divert public attention from the real actions of the alliance itself. Right now, NATO's largest exercise since the Cold War, Steadfast Defender, is taking place near Russia's borders. According to their scenario, coalition actions against Russia are being practiced using all instruments, including hybrid and conventional weapons. We have to admit that NATO is seriously preparing for a “potential conflict” with us, which, by the way, is openly spoken about by high-ranking NATO representatives - the head of the Alliance Military Committee R. Bauer and the Supreme Commander of NATO Allied Forces in Europe K. Cavoli. "But it was NATO that launched a hybrid war against Russia in all operational environments and in all geographic directions. And not only hybrid - in the conflict around Ukraine, NATO members are actively involved in a real military confrontation with our country. They not only finance the Kiev regime, supply weapons, but also supply it with intelligence data, after which Western weapons strike civilians and civilian infrastructure on Russian territory." In an 05 May 2024 exclusive, the Financial Times reported that intelligence services from three different European countries have warned their governments that Russian agents are in the midst of plotting a series of bombing, arson and infrastructure attacks on European soil. “We assess the risk of [Russian] state-controlled acts of sabotage to be significantly increased,” Thomas Haldenwang, the head of German domestic intelligence, told a security conference in April, noting that the attacks would come with “a high potential for damage”. NATO is also on alert, a senior European government official told the paper, saying the alliance’s security services have brought to the table “clear and convincing information on Russian mischief”. The Kremlin scoffed at the claims, rejecting them as “unfounded” and “not serious”. But the warnings are not all that easy to dismiss. Especially as they have come amid of spate of sabotage attacks in both Europe and the United States in recent months with suspected links to Russian intelligence services. And the list of incidents continues to grow. A London warehouse containing aid shipments to Ukraine was destroyed in a fire on March 21, for example. Then, on April 15, an American artillery shell factory that ships some of its products to Ukraine went up in flames. Two days later, on April 17, an explosion rocked British defence contractor BAE Systems’ factory in Wales. The factory also manufactures weapons for Ukraine. And on April 18 a man linked to the Russian intelligence services was arrested in Poland after trying to collect information about security at the country’s Rzeszow airport. That same day, Germany arrested two German-Russian nationals suspected of plotting sabotage attacks in the country, including on US military facilities. Jenny Mathers, a specialist in Russian intelligence services at Aberystwyth University in Wales, said there has been a notable increase in the number and intensity of Russia-linked incidents for the past year, adding that “we are likely to see an acceleration of this trend". Larger infrastructure networks have been targeted too. Last month, Czech authorities accused Russia of having made “thousands” of hacking attempts to sabotage European railway systems and their ability to transport Western arms and material to Ukraine. According to the country’s transport minister, the campaign began shortly after Russia launched its full-scale invasion of Ukraine in 2022 and has included attacks on signalling and ticketing systems. Kevin Riehle, an intelligence and security expert at Brunel University in London, said that one of the reasons for the presumed Russian sabotage is that Moscow already sees itself as being at war with the West. President Vladimir Putin made this fairly clear on March 28 when he said that any Western military bases hosting F-16 fighter jets destined for Ukraine would be considered “legitimate targets” for the Russian army. Mark Galeotti, director of the London-based think tank Mayak Intelligence and author of “Putin’s Wars: From Chechnya to Ukraine”, said that as the West continues to pile pressure on Russia, “we should not be surprised by a pushback”. Galeotti added that the increase in sabotage operations also comes as Ukraine has intensified its attacks on Russian soil and that they can be viewed as a sort of payback. “As far as Putin is concerned, Ukraine does what it is told. When he sees Russian factories being attacked, he sees the hands of the CIA, of NATO," he said. Daniel Lomas, an expert in intelligence services at the University of Nottingham, said the timing for Russia to put pressure on the West in this manner is opportune too, especially as a certain war fatigue – evident in the US's long-delayed aid package for Ukraine earlier this year – has begun to set in. On top of that, Russian attacks on European soil are “an opportunity to sow more divisions” in the West, he said. The attacks also serve a strategic purpose in Ukraine, in the sense that Russia is trying to coordinate the wider sabotage campaign with its push on the ground in a bid to create a greater military advantage, Mathers said. “There is a psychological impact [on the West], but also a material one [for Ukraine],” she said, referring to the fact that most of the targets are either ammunition depots intended for the Ukrainian army or infrastructures in the supply and delivery chain, such as rail networks or airports. Lomas agreed. "One of their key priorities is to stop the flow of weapons to Ukraine." While the Financial Times warned that the attacks Russia is preparing will be carried out “with little concern for civilian fatalities”, the experts FRANCE 24 spoke with do not seem quite as worried. Riehle of Brunel University noted that the main purpose of the Russian intelligence services has always been to “reduce their adversaries' ability to conduct war” rather than to rack up collateral victims. This does not mean casualties do not happen, Lomas said, and pointed to the 2018 Sergei Skripal case in Britain where a woman died after accidentally being exposed to the nerve agent that Russia used to target a former double agent. Galeotti said the Russians also seem careful to avoid crossing any red line. “Not killing people and going after infrastructure facilities show they still have political limits, for the moment. Even if Putin speaks of a war against the West, in reality he doesn't want an open conflict. So Russia is using operations that remain just below the threshold." And, Lomas said, if Russia wants to target NATO countries without actually triggering a NATO response then it has no other choice but to use its intelligence services to conduct sabotage operations. But to do so efficiently, it needs to have a large network of agents in place. In the weeks following Russia’s invasion of Ukraine, Europe dealt a huge blow to that network by expelling hundreds of Russian intelligence officers who were operating out of embassies across the continent. The fact that the sabotage campaigns are intensifying, however, could mean that Russian intelligence services may have recovered from the worst of these losses, Riehle said. But for now, Russia’s sabotage operations have mostly been restricted to arson here, attempted railway attacks there, and dual nationals who have been arrested before they can cause any real damage. In other words, Russia’s European network of agents is likely still quite fragile. And this is probably why the European intelligence warnings have been issued now – while there is still time to prevent Europe from once again becoming a nest for Russian agents who could ruin the Ukrainian supply chain for good. Czechia confirmed that Russian military intelligence was directly involved in the explosions at ammunition depots in Vrbetice. The Czech National Center for Combating Organized Crime said that the perpetrators were members of unit 29155, which deals with sabotage operations abroad and is part of the 161st GRU Special Purpose Specialist Training Center. The suspects, whose names have not been released, entered the Czech Republic from the Russian Federation and then returned. At the same time, the Russian opposition online newspaper The Insider published a large investigation that indicates that the bombing was facilitated by Czech citizens - the Shaposhnikov couple, Elena and Mikhail.
GRU Unit 29155
Russian military intelligence (GRU) Major General Andrey Averyanov was the commander of the notorious GRU Unit 29155, associated with assassinations and destabilization operations outside of Russia. The unit was also reportedly behind the poisoning of ex-Russian intelligence officer Sergei Skripal in 2018. Diplomatic finesse is arguably not Averyanov's strong suit. GRU's infamous 29155 unit specialises in covert operations like sabotage and assassination. Spies from this unit are suspected of having blown up an ammunition depot in the Czech Republic in 2014, attempting to stage a pro-Serbian coup in Montenegro in 2016 and the attempted poisoning of former double agent Sergei Skripal and his daughter in the UK in 2018. But Averyanov is more than a cold-blooded killer. "Averyanov is a decorated veteran from Afghanistan and Chechnya and was also active in Moldova and Crimea. As with all Russian special operatives, he is trained to take the initiative, operate cut off from superiors’ orders, and make links with local allies," says Jeff Hawn, Russia specialist and an external consultant for the New Lines Institute. This pedigree makes him an ideal candidate to negotiate with local military groups, just as Wagner's managers would do when arriving in a new country in Africa. On 17 April 2021, Prague announced it was expelling 18 Russian diplomats over suspicions that GRU Unit 29155 had been responsible. Russia disputed the charges the following day; in recompense it sent packing 20 staff at the Czech embassy in Moscow. All 27 EU member states risked being drawn into this dispute ahead of Prague presenting evidence to the other countries’ foreign ministers. The Czech Republic claimed that the Russian spies who were at work on its territory were the same ones involved in the poisoning and attempted assassination of ex-double agent Sergei Skripal in Salisbury in 2018 – a scandal that further poisoned relations between Russia on the one hand and the UK and its Western allies on the other. Since the Skripal affair put the GRU in the world’s headlines, Western intelligence agencies and media such as the British open-source investigation outlet Bellingcat and the German weekly Der Spiegel have linked several events to unit 29155. This section is suspected of organising a political destabilisation campaign in Moldova in 2016, of participating in a pro-Serbian coup attempt in Montenegro the same year, and of trying to poison an arms dealer twice in Bulgaria in 2015. Spanish intelligence agencies even spotted unit 29155 agents during the 2017 Catalonian independence demonstrations. They even established a “rear base” in France’s rural Alpine Savoie region, according to a 2019 Le Monde investigation. All this gives the impression of a highly mobile special forces cell, capable of striking at any place or time on Moscow’s command. The New York Times described them in 2019 as an “elite force”. Speaking at the Munich Security Conference the same year, then MI6 chief Sir Alex Younger said that “you can see there is a concerted program of activity – and, yes, it does often involve the same people”, pointing to the Skripal assassination attempt and Montenegro attempted coup. “We assess there is a standing threat from the GRU and the other Russian intelligence services and that very little is off limits,” Younger continued. Nevertheless, it has since emerged that this spectre of an all-powerful Russian unit lurking in Europe’s shadows to hunt down the country’s enemies could well overestimate the threat. The GRU’s most illustrious moments were during the Chechen Wars and the 2014 invasion of parts of Ukraine. “They are of course very well-trained special force fighters who’ve all gone through the famous Spetsnaz training,” said Mark Galeotti, a British expert on Russian intelligence agencies and director of Mayak Intelligence, a consulting firm on security issues relating to Russia. Unit 29155 is very small. “Ever since it was founded in 2018 it’s probably only had around 20 agents,” said Gerhard Mangott, a specialist in Russian security issues at the University of Innsbruck in Austria. Galeotti made the same assessment: “They don’t have many people compared to the other branches of Russian intelligence.” “They’re not these super-agents who can do anything – as some have suggested,” Galeotti continued. A better way of thinking about Unit 29155, he continued, is as a team “specialising in sabotage and assassination – the dirty work”. Consequently, Moscow only deploys them when “the ends matter more than the means”, Galeotti said. Unlike agents in the FSB – the internal agency and main successor to the KGB – or the SVR – the external intelligence organisation – who are renowned for their discretion, unit 29155 members “don’t show the same degree of finesse; they’ll do everything it takes to achieve their objectives, even if it means using an unsubtle modus operandi”, Galeotti explained. That’s why their failures – including their failure to kill Skripal and the abortive coup attempt in Montenegro – “can appear unprofessional, leaving traces that allow us to trace the perpetrators”. But in the end, these failures mean little to Moscow. Firstly because we “don’t know how many other missions have been completed successfully”, Mangott said. Furthermore, even if these missions fail they allow Russia to send a signal to other European powers. “It’s a way of showing that they can act on their soil,” Galeotti said. Czech authorities placed Averyanov on the country's wanted list, Seznam Zpravy reported on 10 May 2024. The country's investigators believe that Averyanov coordinated the supposed Russian sabotage operation in 2014 that led to ammunition depot explosions in the eastern Czech town of Vrbetice, killing two people and causing damages in tens of millions of dollars. The wanted notice was published on the Czech police's website, indicating that the search was declared on May 7. The Czech police concluded the investigation into Vrbetice blasts last week, saying that Russian operatives were responsible for the sabotage. Media reports emerged in 2021 that the ammunition was supposed to be transferred either to Ukraine or to Syria, reportedly for the Syrian opposition battling the regime of Bashar al-Assad, an ally of Russia. The company that owned the supplies disputed these claims. The Insider investigative outlet reported on April 29 that two Russian-born Czech citizens, Nikolay and Elena Saposnikov, aided Moscow's agents in the operation.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

