Chapter
ThreeOperations
(cont)
Operations (cont)
Physical Destruction Operations in TFE
Seizure of Bosnian-Serb Radio/Television Towers
Following the civil war in Bosnia, much of the communications media lay in ruins. At the cessation of hostilities, newspapers and magazines were few, expensive, and had limited circulation. In such circumstances, broadcast media were extremely influential, despite the small number of operating transmitters. The broadcast media of the FWFs were politically driven and controlled. Reporting was biased by either omission of the truth, distortion through emphasis on only those elements of information which reinforced a political view, or outright disinformation, i.e., fiction-based propaganda. In May 1997, the North Atlantic Council granted authority to SFOR to take actions against any media undermining the peace accords.(62)
During the early summer of 1997, a power struggle erupted between the rival factions of the Bosnian Serb (Republika Serpska, or RS) leadership, that is, the RS President Bijlana Plavsic and the Bosnian-Serb member of the Bosnian presidency, Momcilo Krajisnik (loyal to the former RS President and indicted war criminal Radovan Karadzic). The struggle began when Madame-President Plavsic decided to dissolve the RS parliament and called for new elections in November 1997. The struggle caused a split within the RS state television, with journalists and editors from the Banja Luka studio deciding to split away from Pale direction after Pale manipulated a broadcast on SFOR searches in police stations. SFOR and OHR tried to exploit these developments to their advantage. SFOR and OHR encouraged SRT Pale to tone down its anti-Dayton, anti-NATO campaign and air programs on the DPA sponsored by the international community. In exchange for their cooperation, they would remain open, whereas non-compliance would bring military action.(63)
The pro-Karadzic, or Pale faction and its politically-controlled media continued the barrage of anti-SFOR propaganda and hate. SRT television stations for example, referred to the Muslim head of Bosnia's Presidency as "Alija Izetbegovic, Muslim murderer."(64)These same stations televised anti-SFOR propaganda to the Bosnian Serb audience attacking the legitimacy of SFOR and its mandate. One anti-SFOR propaganda item accused SFOR of using "low-intensity nuclear weapons," during the 1995 attacks on VRS positions around Sarajevo, Gorazde, and Majevica in 1995.(65)In another propaganda piece, Serbian Radio Television (SRT) showed alternating images of World War II German Army and present-day NATO forces while the commentator drew the comparison, likening SFOR soldiers to a Nazi occupation force.(66)NATO officials have expressed concerns that such "venomous propaganda" threatened the safety of the NATO-led peace operations force.(67)
Despite the efforts of both the High Representative and the OSCE, the dissident RS faction repeatedly refused to cease or moderate their broadcasts. After SRT Pale heavily edited a tape on the International Criminal Tribunal for the former Yugoslavia (ICTY) war crimes mission, using it to spread disinformation, the international community took direct action. Under the authority of the GFAP and orders from the NATO Council and the Office of the High Representative, SFOR seized four SRT transmission towers, considerably reducing the broadcast footprint of SRT. The seizure of these towers was a physical destruction mission in that SFOR targeted the TV transmitter towers for neutralization, which is a condition achieved by physical destruction operations. Within TFE, U.S. soldiers secured several transmitters used by media elements loyal to the pro-Karadzic faction. On October 1, 1997, TFE units executed the physical destruction operation, securing the Bosnian-Serb television/radio transmitter complexes on Hill 619 in Duga Njiva, Hill 562 near Ugljevik, Trebevica (near Sarajevo) and Leotar.(68)In pre-dawn raids, SFOR French, Polish, Scandinavian and American soldiers secured the sites and immediately fortified them against anticipated resistance.(69)
At Hill 619, U.S. Engineers operating Armored Combat Excavators (M-9 ACE) constructed protective berms for the troops, and cleared fields of fire, while other engineers emplaced a triple-standard concertina barrier around the site.(70)At Hill 562, 200 Bosnian-Serb protesters staged a 15-hour confrontation in which the protesters hurled rocks and attacked with clubs, damaging several vehicles.(71)The application of combat power, in the form of maneuver to occupy ground, neutralized the adversary's ability to propagandize over the air waves.
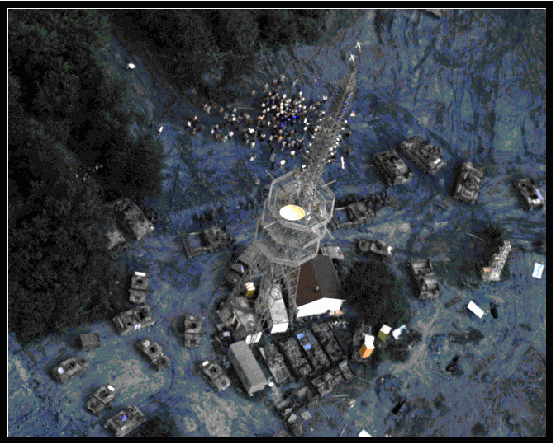
Seizure of SRT Tower at Hill 619.
Targeting Adversary Early Warning Devices for Destruction or Neutralization
On 27 August 1997, SFOR received indications that Replubika Serpska (RS) police forces were attempting to take control of Police Stations in MND-N. This information followed a change in the status of Special Police units, some of which were equipped with armored cars, anti-tank rockets, anti-tank and anti-personnel mines, and other combat equipment. The change in status meant that these units were to be treated as military units and conform to the military provisions of the Dayton Peace Accord (DPA) under SFOR oversight, unless they were transformed into proper civil police units with a clear law-and-order mission. Special Police units in the RS declined to change their organization and, therefore, fell under the military provisions of the DPA, which meant that SFOR troops could inspect their facilities, and control their movements and training in accordance with Annex 1A.
In an operation intended to enforce compliance from the entity police forces, SFOR supported the International Police Task Force (IPTF) in an inspection of the Special Police units in Bijlijina, Brcko, and Jajna. As SFOR forces commenced operations early in the morning on 27 August, civil-defense sirens were used to mobilize the populace into action. Hostile crowds quickly massed in Brcko to demonstrate against the IPTF and the supporting SFOR forces.
The operation commenced during darkness at approximately 0200 to rapidly establish situational dominance while the populace was unaware. However, although the operation was initiated during the early morning hours, hostile crowds quickly gathered to thwart SFOR forces around the targeted facilities. At approximately 0500, two civil-defense sirens sounded in Brcko, alerting the populace to mobilize.(72)These sirens were complemented with radio broadcasts, one of which aired at 0700 urging the "Serb people" to respond to the "call of danger and call to all citizens to assemble in the center of town.."(73)One Sergeant on the scene reported "They sounded an air defense siren and people just started bombarding us. We were getting pelted with bricks and blocks."(74)During the remainder of the day, SFOR vehicles were damaged in attacks executed with "molotov cocktails," rocks, and bricks - soldiers were assaulted and injured. SFOR had lost the initiative to the hard-line Bosnian Serb faction leaders who orchestrated the demonstrators and who controlled the situation. RS Police refused to control the crowds and they achieved their objective of interfering with the IPTF Police site inspections. SFOR lost situational dominance early in this operation.
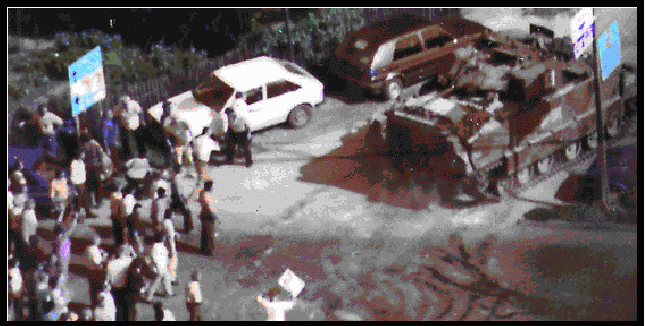
Rioters in Brcko confronting SFOR Soldiers, 28 August 1997. (75)
Following the operation, it became clear to the MND-N staff that in future operations, this warning and alert capability would have to be neutralized to allow SFOR to maintain the initiative and situational dominance. Neutralizing the civil-defense sirens to hamper the Bosnian Serbs' ability to muster is an example of a C2-Attack Physical Destruction operation. C2-Attack seeks to "gain control over our adversary's C2 function.targeting personnel, equipment, communications, and facilities in an effort to disrupt or shape adversary C2."(76)Neutralizing adversary C2may be accomplished through electronic warfare, deception, and physical destruction. Neutralization is, therefore, a physical destruction effect, as the actual destruction of the facility or capability is not required. The definition of physical destruction in IO doctrine includes the neutralization of targets, which may be preserved and denied to the adversary selectively.(77)Although the sirens were very "low-tech" C2, their effectiveness is irrefutable in light of the crowds that assembled in short order and numbered approximately 1,200.(78)
During peace operations in a MOUT(79)environment, in which the aim is to establish control over entities or functions of FWFs, the intelligence preparation of the battlefield (IPB) of adversary C2must address seemingly "low-tech" early warning capabilities such as civil-defense sirens. Denying the FWFs their warning and alert capabilities will delay and disrupt any organized response to friendly operations and ensure that friendly forces maintain the initiative and situational dominance.
Electronic Warfare (EW)
Electronic Warfare is the military use of electromagnetic and directed energy to control the electro-magnetic spectrum or to attack the enemy - it is divided into the three subdivisions of Electronic Attack, Electronic Protection, and Electronic Warfare Support. As stated before, C2W in peace operations are primarily aimed at co-opting the INFOSYS of the FWFs to support the objectives of the peace operations force. In peace operations, electronic protection is continuous, as is electronic warfare support, while electronic attack is primarily a "be-prepared" or "stand-by" mission. Electronic Warfare Support (ES) measures can provide commanders the means to intercept, locate, and identify communications emitters used by FWF political and military leadership either for exploitation or for targeting.(80)In peace operations, EW assets are continuously collecting R.I.I. from adversary and FWFs' INFOSYS, exploiting those systems to maintain information dominance over the FWF political and military leadership.
The commander in peace operations plans EW for the contingency that friendly forces must act with force against the FWFs or other adversaries. The EW process is directed to be prepared to disrupt, degrade, neutralize, or decapitate adversary target acquisition, intelligence gathering, and C3systems while simultaneously protecting friendly C3systems from similar adversary actions.(81)Friendly EW capabilities are planned against targeted adversary C3I systems to disrupt or destroy those systems when required. Successful implementation of EW operations demands that intelligence operations produce the required knowledge of the adversary INFOSYS and decisionmaking processes so that EW capabilities are accurately targeted for attack on adversary systems and positioned and postured for the defense and protection of friendly systems.(82)
Through EW, the commander may access the adversary's C3I systems to exploit intelligence through monitoring and manipulate those systems through deception to create a knowledge-based battlefield advantage that can be exploited by military forces to dominate the situation and the FWFs.(83)Intelligence acquired on FWF and adversary intentions through their INFOSYS provides a greater degree of force protection to the friendly force.(84)EW employed in this manner then provides a degree of transparency to the military, para-military, and police forces of the FWFs that permits monitoring of compliance with the established peace terms and provides early warning of potential violations or threats to the safety of the friendly force.
EW capabilities in TFE included jamming and sensor systems. In response to the virulent anti-NATO propaganda being disseminated over SRT television, SACEUR, on 28 August 1997, authorized use of jamming and other military action to stop the Bosnian Serb television propaganda campaign.(85)On 12 September 1997, three U.S. EC-130 aircraft deployed to Bosnia, to provide a jamming capability.
Tactical EW in Task Force Eagle initially focused on providing forewarning of EAF military activity and to assess their intentions and determine their resolve to use military force. As the military provisions were successfully implemented and the situation stabilized, the focus of EW operations was to monitor the EAFs for compliance, co-opting their C2 systems.(86)Much of the EW that took place in TFE consisted of using EW surveillance assets to monitor movement in the AO of the EAFs and noncombatants.
Ground surveillance technology, such as ground surveillance radar (GSR), and remote battlefield sensor systems, supported by night-vision devices, sensors, and thermal sights are useful in peace operations to observe and monitor situations.(87)
TFE ElectronicWarfare - Ground Surveillance Sensor Systems
Ground Surveillance Systems (GSS) include ground surveillance radars (GSR) and remote sensors that track movement by acoustic, seismic, electromagnetic, or visual means.
Remotely Monitored Battlefield Sensor System (REMBASS)
While the doctrinal reference for the TTPs for REMBASS does not address the use of ground surveillance sensors in peace operations,(88)their use in past peace operations is a proven concept. The Multi-National Force and Observers mission in the Sinai uses remote sensors to monitor the demilitarized zone and compliance.(89)A demilitarized zone, or zone of separation (ZOS) is a common feature in peace operations. Task Force Eagle Teams used REMBASS and Improved-REMBASS (I-REMBASS) to monitor movement and activities in its AOR. The TFE GSS teams modified sensor employment and data analysis techniques to meet the needs of an environment which was non-linear and where there was no "enemy" per se.
The TFE MI battalion provided GSS teams to subordinate battalion task forces in direct support. The teams were composed of MOS 96R personnel who operated ground surveillance radars (GSR), REMBASS, and I-REMBASS. The initial emplacement of REMBASS "monitored the withdrawal of the military forces of the FWFs from the Zone of Separation (ZOS) and confirmed FWF reports of departure. As the factions withdrew, the systems were moved to monitor concentrations of FWF equipment, suspected areas of treaty violations, and force protection around base camps."(90)The teams provided support to perimeter security, a traditional mission, but were also employed in a variety of non-traditional roles and developed innovative tactics, techniques and procedures to support their new roles. TFE's REMBASS allowed remote monitoring of routes during key events, such as elections, resettlement operations, and provided alert, warning and indicators when large-scale movements were detected unexpectedly.
TFE developed new REMBASS employment techniques for peace operations, which included monitoring the movement of displaced persons and detecting movement along friendly, secured routes. GSS teams have conducted limited pattern analysis of data from sensors that have remained in place for extended periods. In a wartime environment, REMBASS are emplaced on the battlefield or in rear areas where movement is controlled. During OJG, GSS teams emplaced sensors in areas where the local populace had free or less restricted access. Mission requirements dictated the emplacement of sensors in areas settled or frequented by local civilians. The GSS teams regularly placed sensors in or near areas where friendly forces moved about in heavy equipment, and the civilian populace had free access. Although the teams found that sensors were more likely to become damaged, discovered or even stolen, the information the sensors provided proved to be more than worth the cost of the expendable sensors.
GSR
TFE employed Ground Surveillance Radars (GSR) to maintain situational awareness. GSS teams employed the AN/PPS-5C GSRs to monitor named areas of interest (NAI), cantonment areas, and intersections, and to provide force protection to the base camps. Radar teams positioned on top of high areas had excellent line of sight and early warning.(91)
GSS teams supported the command's requirement to monitor "unusual" or "suspicious" movement by the local populace and the resettlement of areas by refugees. For example, the teams emplaced sensors in named areas of interest (NAI) located in both rural and urban areas that had not been inhabited since the end of hostilities. Any movement in those areas, especially at night, would be considered unusual. Over time, the teams developed a database of sensor data about movement within those NAIs. They then conducted a limited pattern analysis of the data to assist TF S2 in determining its significance. By analyzing the data and tasking reconnaissance from other assets, the TF S2 and GSS teams were eventually able to determine what constituted unusual or suspicious movement, and to distinguish it from the planned resettlement of an area.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

