CHAPTER
7
SECURITY OF KEY ASSETS
by CPT Nicholas Panagakos1. GENERAL. The Light Infantry Brigade Combat Team is task-organized with a complicated mix of combat, combat support, and combat service support units. Within this organization, there are always assets that do not have the organic capability to secure themselves. Such assets may include:
- Q-36 Radar of the FA battalion
- Reverse Osmosis Water Purification Unit (ROWPU)
- Brigade Tactical Operation Center (TOC)
- Brigade communication assets
- Other assets deemed key by the commander
These assets are important parts of the Brigade Combat Team. Their destruction will hamper the brigade's ability to accomplish the mission. Therefore, the commander must decide how to secure them. Normally there are only two courses of action available:
- Require the parent unit to provide the security required.
- Task-organize a combat element to provide the necessary security.
The parent unit support is unlikely. Current CSS organizational structure frequently prohibits soldiers from conducting security operations, associated patrols, and other tasks essential to providing even the most fundamental local security. By default, task-organize is the usual and probable choice. This makes it tough on commanders and their units. They have the difficult task of deciding how to allocate valuable combat assets to protect these critical C2, logistics, and other specialized nodes.
Regardless of the choice the commander pursues, make sure that the security element is a combined arms team and possesses the combat power to counter any enemy threat.
Protect your key assets. Task-organize combat units to provide them with the force protection necessary to survive on the battlefield.
2. DOCTRINAL BASE. The schoolbook solution and one most commanders favor is tasking a subordinate command for a rifle platoon or tank section to serve as security element. This unit is then assigned to secure and protect the brigade TOC, Q-36, ROWPU, or other assets. It is also a doctrinal consideration.
3. PLANNING. A better idea may be to consider task-organizing an element to accomplish the security mission. Put together a combined arms team rather than assigning an infantry-pure or tank-pure unit to provide security.
Issue: Pure units have inherent strengths and weaknesses. Since the security element must possess the combat power to defeat the enemy threat over a wide spectrum of scenarios, a combined arms team is the answer. The elements of a combined arms team complement each other's strengths and support each other's weaknesses.
EXAMPLE: In restrictive terrain, the infantry has the ability to patrol along the dismounted enemy avenue of approach. Firepower is limited to small arms, some anti-armor weapons, and NODs. They lack the internal transportation assets to move when the element they are guarding moves. Tanks, on the other hand, have the firepower, mobility, and enhanced optics, but in restrictive terrain lack the ability to provide close protection. They are, in fact, vulnerable to the very threat they are defending against. In addition, tank crews are not trained to conduct aggressive counter-reconnaissance patrols.
Discussion: By creating a combined arms team, the infantry and armor become a formidable force, capable of reacting to a variety of enemy threats with the speed, maneuverability, and firepower needed to win. The infantry can man checkpoints overwatched by tanks. They can conduct patrols and counter-ambushes overwatched using the tank's superior thermal imaging system. This same system can guide infantry to potential enemy observation posts (OPs) by using thermal imagery to help guide unit patrols to potential hot spots.
Commanders must consider the risk when augmenting support elements with infantry, armor, or a combination of both. The first consideration is whether the Q-36, ROWPU, TOC, etc. can secure themselves. If so, the commander can deploy more combat elements forward to fight the enemy.
On the other hand, if support assets are inadequate to secure their equipment, the commander must determine the number and mix of the combat force needed to accomplish the task. This decision depends on how aggressively the enemy is pursuing the destruction of these assets. The commander responsible for securing the assets should confirm his estimates by conducting detailed IPB and METT-T analyses. He can use the results to recommend to his higher commander whether or not to provide the necessary assets. The accompanying illustrations highlight techniques for securing assets within the Brigade Combat Team:
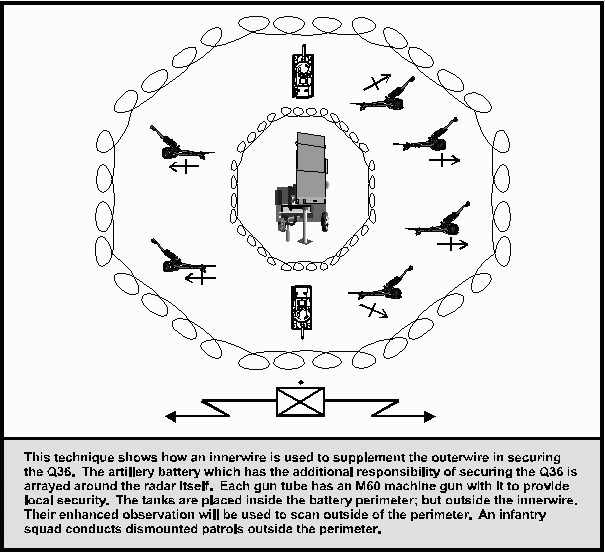
Figure 7-1
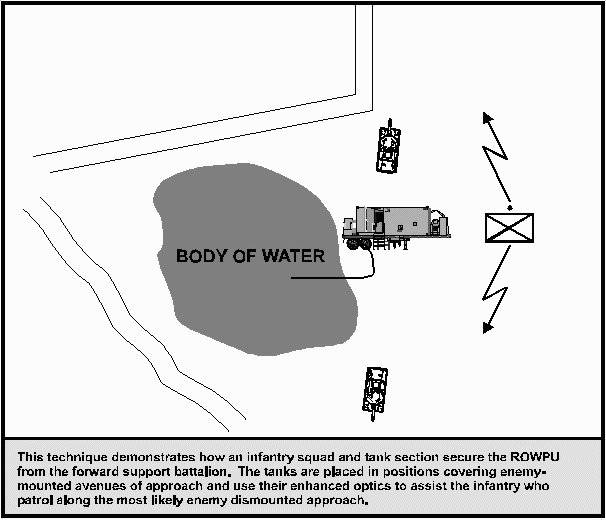
Figure 7-2
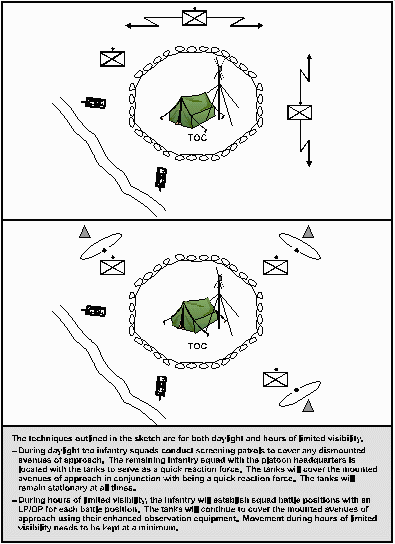
Figure 7-3
TTP:
- Infantry and armor elements tasked with the security mission need to be alerted as early as possible. This will allow the two units to plan and issue an operations order and allow for preparation of equipment and rehearsals prior to execution.
- The senior leader of the security element is responsible for the employment of that element and the security of the key asset. This will allow input on the defense and survivability of the location. He then answers to the unit commander; i.e., the brigade XO for the TOC security or the battery commander for the Q-36.
- The security element leader needs to be a member of the leader's reconnaissance for the proposed location prior to the arrival of the key asset to properly clear and secure the area.
- Establishing security for a key asset is no different then setting in a defense. A priority of work must be set and followed for all tasks to be accomplished.
- Ensure the tanks are given sectors of fire to observe which enable them to exploit the use of their enhanced optics.
- The tank's thermal sight can be used to guide infantry patrols toward potential enemy locations.
- The security element's sole mission is to provide protection for the key asset. They should not be tasked with performing other activities for the host unit, i.e., guarding LOGPACs, pulling radio watch, escorting other vehicles, and other unrelated tasks.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

