Force Protection
This appendix outlines force-protection measures
that engineer units may employ beyond traditional methods, such
as triple standard concertina. The intent of this appendix is
to provide general force-protection guidance to engineer battalion
and brigade commanders and staffs.
This appendix concentrates on the physical-security
aspects of force protection. It highlights passive measures for
integration into force-protection planning. This appendix also
discusses engineer-specific planning considerations required in
force protection. It contains very general design criteria. The
Security Engineering Manual, published by the Omaha District,
United States Army Corps of Engineer (USACE), provides more detailed
information on the design of installations and structures requiring
protection. This manual also contains information designated "For
Official Use Only" on threat capabilities, design of protective
measures, and the options outlined in this appendix. Engineer
planners should use the USACE manual if they require more specific
guidance or if they are designing a permanent facility. Planners
should use this appendix in conjunction with Field Manual (FM)
5-103 and Technical Manuals (TMs) 5-301-1/2/3/4 which also contain
information applicable to force-protection planning.
ENGINEER PARTICIPATION
IN FORCE-PROTECTION PLANNING
Unit operations officers have staff responsibility
for their unit's force-protection plan. Engineers will be involved
in force-protection planning from two perspectives. They will
prepare their unit's force-protection plans, and they will provide
input (and capability) to the unit they are supporting. As with
other missions, engineer force-protection planning must be well
thought out, logical, and integrated with other staff planning.
Force-protection plans or policies must be developed in line with
the command estimate process. The engineer must be involved in
the intelligence preparation of the battlefield (IPB) process
to ensure that engineer intelligence needs are integrated into
all reconnaissance and collection plans, information requirements,
and priority information requirements.
The engineer must participate in the overall
mission analysis, ensuring that engineer mission-essential tasks
are integrated into the commander's estimate and that all engineer
missions are identified. Using the same analysis process as the
maneuver commander, the engineer must focus on--
- Engineer specified and implied tasks.
- Assets available to enhance force protection.
- Constraints.
- Restrictions.
- Risks.
- Time analysis (the Security Engineering Manual calls this "response time").
- Essential tasks.
In developing a force-protection policy, the
following process should be used:
- Determine the composition of assets (personnel, equipment, and facilities).
- Define the threat and attack probability.
- Determine levels of protection for each asset.
- Identify constraints.
- Design protective systems to counter threats.
The engineer must ensure that the maneuver staff
and commander develop a force-protection policy based on the threat.
The plan must balance the attack probability, the consequences
of inadequate protection, and the cost of adequate protection
(risk level). The commander must set the priority of protection
for United States (US) forces and equipment, local assets, infrastructure,
and the local populace.
Engineers must understand threat components,
which they must then counter. The threat has three components:
aggressors; their tactics; and their associated weapons, explosives,
and tools. There are four types of aggressors that engineers must
understand and plan against in a low intensity conflict (LIC)
environment:
- Criminals. Subdivided into three categories: unsophisticated, sophisticated, and organized. Unsophisticated criminals are unskilled in the use of weapons and tools and have no formal organization. Their targets are those that meet their immediate needs, such as drugs, money, and pilferable items. They are interested in targets that pose little risk. Sophisticated criminals working singly are organized and efficient in the use of certain weapons and tools. They target high-value assets and frequently steal large quantities. Organized criminal groups are sophisticated and rely on specialists to obtain equipment to achieve specific goals. Targets of organized criminal groups may involve large quantities of money, equipment, arms, ammunition, and explosives.
- Protestors. Categorized as either vandals, activists, or extremists. Engineers must be concerned with all violent protectors. Protectors are politically or issue-orientated and act out of frustration, discontent, or anger. Their primary objectives include destruction and publicity. Vandals and activists are unsophisticated and superficially destructive. They generally do not intend to injure people. Extremist groups are moderately sophisticated and more destructive. Their actions are frequently overt and may involve individuals as targets.
- Terrorists. Oriented on an ideology, a political cause, or an issue. Terrorists commonly work in small, well-organized groups. They are sophisticated and possess an efficient planning capability. Terrorist objectives include death, destruction, theft, and publicity. Terrorist groups are generally classified by their government affiliation. They are categorized as nonstate-supported, state-supported, or state-directed. Chapter 1 contains a detailed description of these categories. Chapter 5 lists specific terrorist tactics.
- Subversives. Classified into two groups: saboteurs and spies. Saboteurs include guerrillas and commandos. They are very sophisticated and highly skilled and employ meticulous planning. Saboteurs commonly operate in small groups and have an unlimited arsenal. Their objectives include death and destruction. They often target mission-critical personnel, equipment, or operations. Spies are highly skilled and very sophisticated. They are generally foreign agents but frequently employ insiders. They target military information and attempt to avoid detection. In some cases, they may use the activities of other aggressors.
Threat personnel employ a wide range of tactics
to accomplish their objectives. These strategies have been categorized
into 15 tactics, which are specific methods of achieving an aggressor's
goals. Not included in this appendix are other tactics that engineers
have little capability of countering. These include kidnapping,
hijacking, and assassinations that are executed away from a facility
or installation. The following descriptions of aggressor tactics
will assist engineer planners in developing protective methods,
devices, facilities, and systems:
- Moving-Vehicle Bomb. Used when an aggressor's
goal is to damage or destroy a facility (or assets within a facility)
or to kill people within the blast area. The moving-vehicle bomb
is a suicide attack where an explosive-laden vehicle is driven
into a facility and detonated.
- Stationary-Vehicle Bomb. Used when an aggressor's
primary objective is to damage or destroy a facility (or assets
within a facility). This type of bomb may be detonated by time
delay or remote control. This attack has three versions:
- An explosive-laden vehicle is driven to a preselected location and abandoned.
- Explosives are placed in an unsuspecting person's car. He then unknowingly delivers the bomb to the targeted facility.
- Someone is coerced into delivering a vehicle bomb.
- Exterior Attack. Used when an aggressor's goal
is to damage or destroy a facility (or assets within a facility)
and kill or injure its occupants. This attack is at close range
of a facility or exposed asset. Using clubs, rocks, improvised
incendiary devices, hand grenades, or hand-placed bombs, the aggressor
attempts to inflict destruction and death.
- Standoff Weapons Attack. Used when an aggressor's
goal is to damage or destroy a facility (or assets within a facility)
and kill or injure its occupants. These attacks are executed using
military or improvised direct-and indirect-fire weapons, such
as antitank weapons and mortars.
- Ballistic Attack. Used when an aggressor's goal
is to kill or injure a facility's occupants. Using small arms
at varying distances, the aggressor attempts to inflict death.
- Forced Entry. Used when an aggressor's goals
are to steal or destroy assets, compromise information, or disrupt
operations. Using small arms or forced-entry tools, the aggressor
enters a facility through an existing passage or creates a new
opening in the facility.
- Covert Entry. Used when an aggressor's goals
are identical to those listed for the forced-entry tactic. The
difference in these entries is that the aggressor will attempt
to enter the facility covertly using false credentials. The aggressor
may attempt to carry weapons or explosives into the facility.
- Insider Compromise. Used when an aggressor's
goals are similar to those listed for the forced-entry tactic.
The aggressor uses an insider (one who has legitimate access to
a facility) to accomplish their prescribed objectives.
- Electronic Eavesdropping. Used by an aggressor
to monitor electronic emanations from computers, communications,
and related equipment. This eavesdropping is normally done from
outside a facility or restricted area.
- Acoustical Eavesdropping. Used by an aggressor
(using a listening device) to monitor voice communication and
other audible information.
- Visual Surveillance. Used by aggressors employing
ocular and photographic devices to monitor facility, installation,
and mission operations.
- Mail Bombs. Used when the aggressor's objective
is to kill or injure people. Small bombs or incendiary devices
are incorporated into envelopes or packages that are delivered
to the targeted individual.
- Supplies Bombs. Used when the aggressor's objective
is to kill or injure people or destroy facilities. Bombs or incendiary
devices, generally larger than those found in mail bombs, are
incorporated into various containers and delivered to facilities
or installations.
- Airborne Contamination. Used when the aggressor's
objective is to kill people, The aggressor uses chemical or biological
agents to contaminate the air supply of a facility or installation.
- Waterborne Contamination. Used when an aggressor's
objective is to kill people. The aggressor uses chemical, biological,
or radiological agents to contaminate the water supply of a facility
or installation.
Aggressors use various types of weapons, explosives,
and tools to attain their objectives. Weapons range from clubs
and rocks to mortars. Explosives are commonly used to destroy
facilities and housing assets and to kill people. Tools are primarily
used in forced-entry operations to breach protective components
or barriers. Understanding the aggressor's options will aid the
engineer in protecting forces from these items. Listed below are
various weapons, explosives, and tools and their potential use:
- Rocks and Clubs. Used in exterior building attacks to damage exterior building components or exposed assets or to injure people.
- Incendiary Devices. Used to damage the facility's exterior or sabotage other assets. These include hand-held torches and improvised incendiary devices (IID). An example is a "Molotov cocktail."
- Firearms. Used in the ballistic tactic to attack facility assets from a distance and in the forced-entry tactic to overpower guards. These include pistols, rifles, shotguns, and submachine guns, both military and civilian. Weapons capabilities are outlined in the Security Engineering Manual.
- Antitank Weapons and Mortars. Used in standoff attacks of facilities. For example, the direct-fire antitank weapons most often used by terrorists are the Soviet, rocket-propelled grenade RPG-7 and the US light antitank weapon (LAW). These weapons increase the terrorist's ability to penetrate and damage a facility and to kill or injure people. Mortars are indirect-fire weapons and include both military and improvised versions.
- Nuclear, Biological, and Chemical. Delivered as airborne or waterborne gases, liquids, aerosols, or solids. Very powerful chemical agents can be manufactured with relative ease from commercially available products. Biological agents can be grown in unsophisticated home laboratories. Radiological agents are radioactive elements that pose a potential threat to water supplies. They can be delivered in liquid or solid form.
- Improvised Explosive Devices (IED). Used in the exterior-attack, mail- and supplies- bomb-delivery, forced-entry, covert-entry, and insider-compromise tactics to destroy assets and to injure or kill people. They are commonly "homemade" bombs made of plastic explosives or trinitrotoluene (TNT). Plastic explosives are chosen by terrorist and extremist protester groups because they are easily molded, stable, and difficult to detect.
- Hand Grenades. Used in exterior attacks to injure or kill people. These include common military antipersonnel and fragmentation hand grenades.
- Vehicle Bombs. Used to destroy facilities and kill people. They contain large quantities of explosives and have the potential to do catastrophic damage.
Potential aggressors have access to a wide variety
of tools, ranging from forced-entry tools, (hand and power tools,
cutting torches, and burn bars), to sophisticated surveillance
tools and devices. The quality and effectiveness of tools and
devices used depends on the type of aggressor. The more sophisticated,
trained, and organized the aggressor is, the more dangerous his
tools and devices will be.
PROTECTIVE MEASURES AND
TECHNIQUES
Engineers may play a significant role in protecting
deployed US forces. They have the capability, when given time,
priority, and a thorough IPB, to effectively establish defensive
measures to protect forces, facilities, and equipment from potential
aggressors. The following list of measures will enhance a force's
survivability. The specific options that the engineer planner
selects will be based on the--
- Specific threat in the area of operations.
- Degree of protection required.
- Time available.
- Materials available.
To tailor the force-protection package to the
local threat, the engineer planner should consult the provost
marshal and intelligence personnel when selecting options from
these lists.
Basic considerations--
- Eliminate potential hiding places near facilities.
- Provide an unobstructed view around all facilities.
- Site facilities within view of other occupied facilities.
- Locate assets stored on-site but outside facilities within view of occupied rooms of the facilities.
- Minimize the need for signs or other indications of asset locations.
- Minimize exterior signs that may indicate location of assets.
- Provide a 170-foot minimum facility separation from installation boundaries.
- Eliminate lines of approach perpendicular to buildings.
- Minimize vehicle and personnel access points.
- Eliminate parking beneath facilities.
- Locate parking as far from facilities as practical.
- Illuminate building exteriors or exterior sites where assets are located.
- Secure access to power and/or heat plants, gas mains, water supplies, and electrical service.
- Locate public parking areas within view of occupied rooms or facilities.
- Locate construction staging areas away from asset locations.
- Locate facilities away from natural or man-made vantage points.
- Locate facilities' critical assets within areas that do not have exterior walls, when possible.
- Minimize window area.
- Cover windows next to doors so that aggressors cannot unlock the doors through them.
- Secure exposed exterior ladders and fire escapes.
- Design building layout so that there are no areas hidden from view from control points or occupied spaces.
- Arrange building interiors to eliminate hiding places.
- Locate assets in spaces occupied 24 hours a day, when possible.
- Locate activities with large visitor populations away from protected assets when possible.
- Locate protected assets in controlled areas where they are visible to more than one person.
- Place mail rooms on the perimeter of facilities.
- Provide emergency backup power generation for critical activities/facilities.
Moving- and Stationary-Vehicle-Bomb Checklist.
(Note: When designing/planning to defeat the moving-vehicle tactic,
you must plan to defeat the vehicle, not the driver. For example,
a guard with an M16 will not stop a vehicle.) In addition to the
minimum-level measures, consider the following measures to counter
a moving- or stationary-vehicle bomb threat:
Site design--
- Provide exclusive standoff zones for facilities.
- Provide nonexclusive standoff zones for facilities (high to very high threat).
- Cluster facilities in common exclusive and nonexclusive standoff zones when possible.
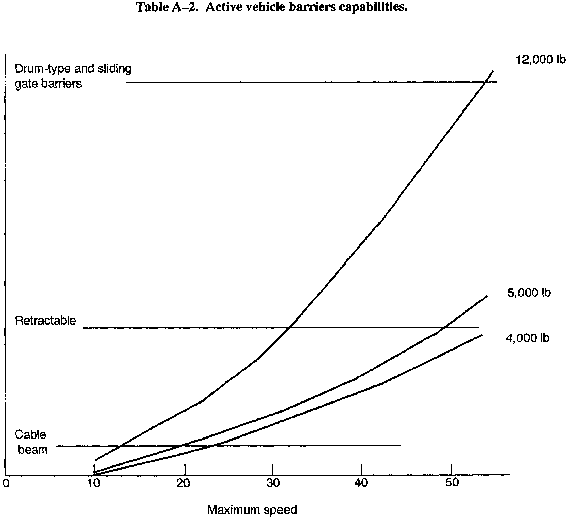
- Use passive vehicle barriers, Table A-1 shows the maximum speed that a vehicle of a given weight can impact a barrier and still be stopped by that type of barrier.
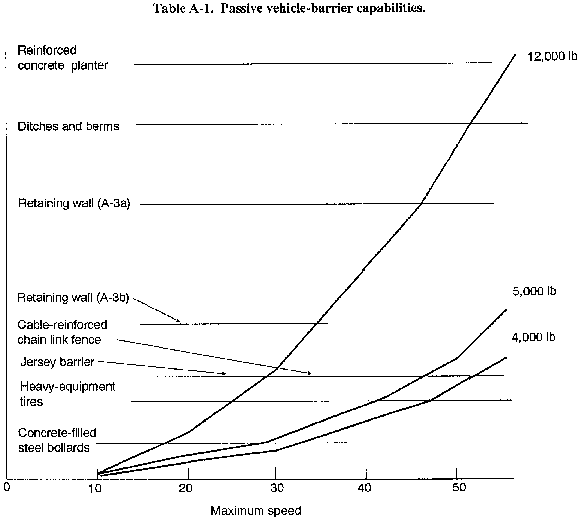
- 8- to 12-inch straight curbs.
- Chain link or ornamental fence.
- Decorative posts (4-inch diameter at 4-foot centers) with or without chain.
- Trees and shrubs.
- Shallow ditches.
- Low berms.
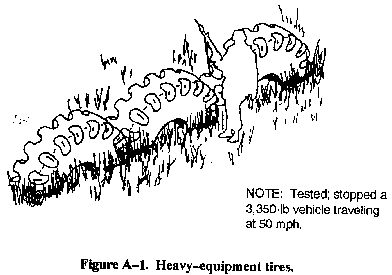
- Half-buried heavy-equipment tires (see Figure A-1).
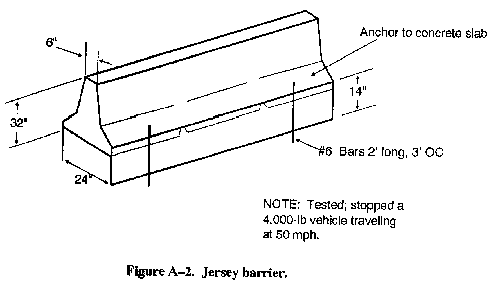
- Concrete barriers (Jersey barrier) (see Figure A-2).
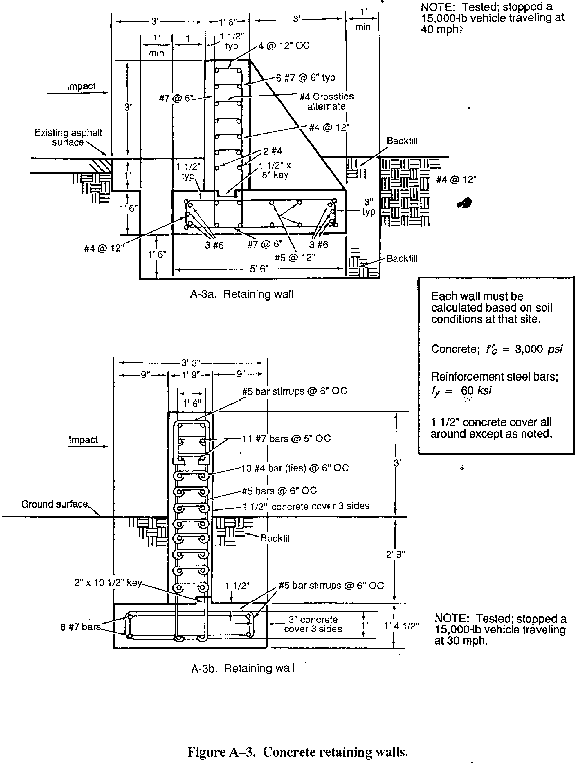
- Concrete retaining walls (see Figures A-3a and A-3b).
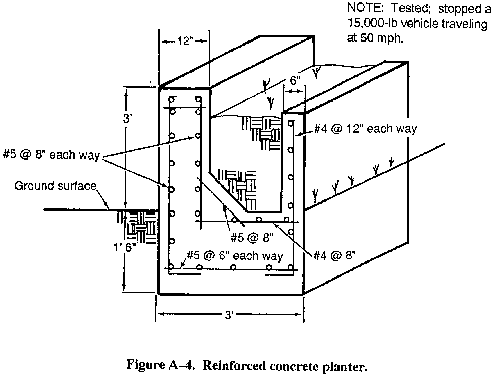
- Reinforced concrete planters (see Figure A-4).
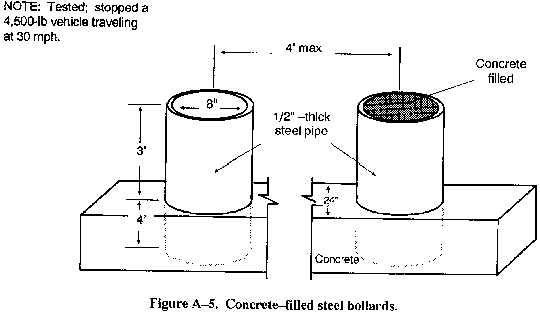
- Concrete-filled steel bollards (see Figure A-5).
- Cable-reinforced chain link fences. (Chain link fence reinforced with two 3/4-inch- diameter cables, one at 30 inches and one at 35 inches above ground level.)
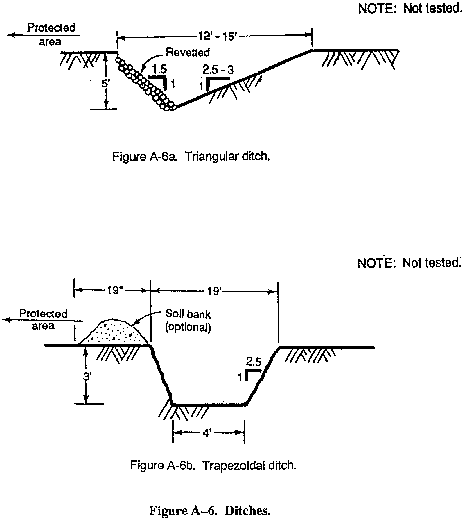
- Ditches (triangular or trapezoidal) (see Figures A-6a and A-6b).
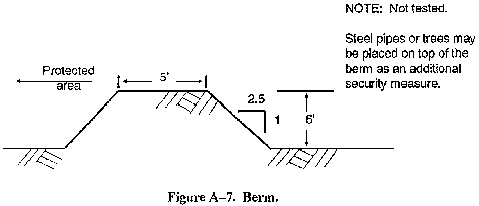
- Berms (see Figure A-7).
- Sandbags.
- Tetrahedrons (steel or concrete).
- Concrete-, rock-, or sand-filled 55-gallon drums connected with wire rope.
- Use active vehicle barriers (see Table A-2)--
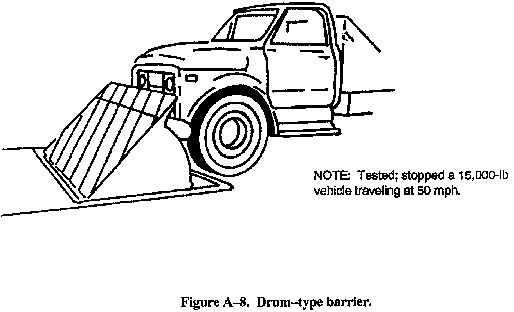
- Drum-type barriers (see Figure A-8).
- Plate-type barriers.
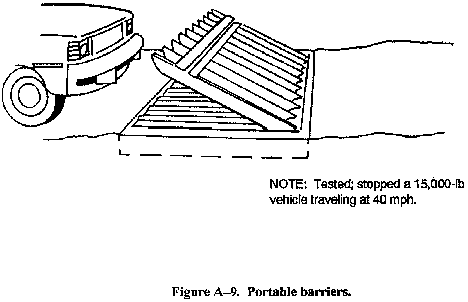
- Portable barriers (see Figure A-9).
- Crash beams.
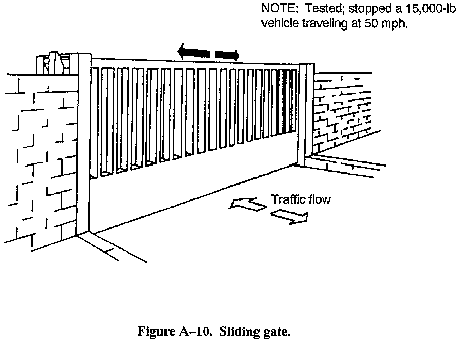
- Crash gates (sliding gate) (see Figure A-10).
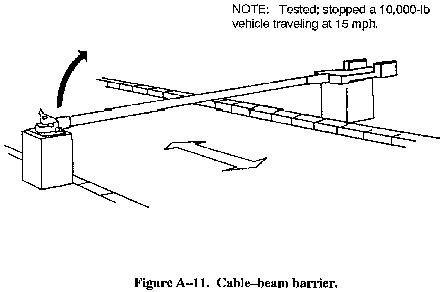
- Cable-beam barrier (see Figure A-11).
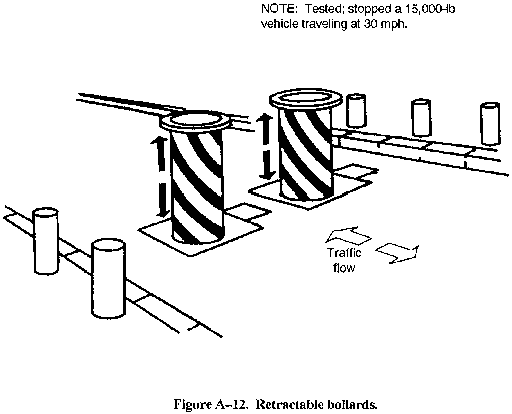
- Retractable bollards (see Figure A-12.).
- Use speed-control obstacles--
- S-curves.
- 90-degree bends.
- Traffic circles.
- Speed bumps.
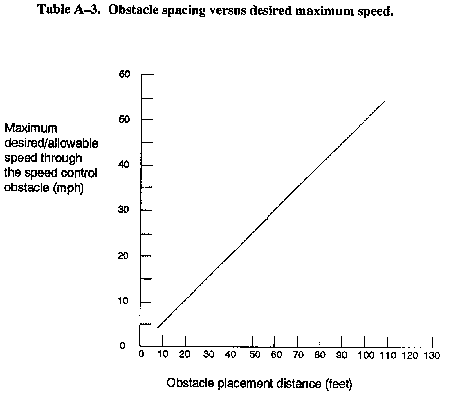
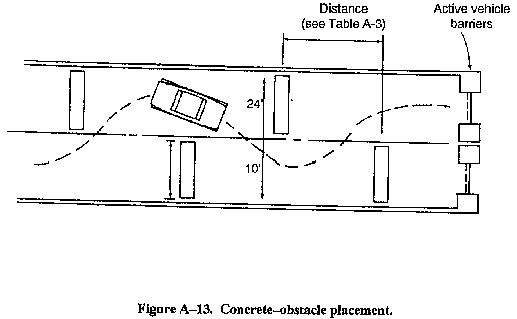
- Concrete obstacles (see Table A-3 and Figure A-13). Table A-3 shows the
- placement distance between obstacles (as shown in Figure A-13) to limit
- vehicles to a maximum desired speed.
- Concrete obstacles (see Table A-3 and Figure A-13). Table A-3 shows the
Exterior-Attack Checklist. In addition to the
minimum-level measures, consider the following measures to counter
an exterior attack of a facility or installation:
Site design--
- Provide a 50-foot standoff zone around facilities.
- Provide a 30-foot clear zone around facilities.
- Provide a 7-foot perimeter fence around installations.
- Provide trees and tall shrubs to resist thrown objects.
- Do not place trash receptacles within clear zone.
- Provide entry control point at perimeter gates in fences.
Standoff-Weapons-Attack Checklist. In addition
to the minimum-level measures, consider the following measures
to counter a standoff weapons attack:
Site design--
- Site facilities on high points of ground, when possible.
- Block direct lines of sight to sensitive areas of the facilities using one or more of the following:
- Other facilities housing less critical assets.
- Dense plantings of trees or shrubs.
- Obscuration fences.
- Walls.
- Earth berms.
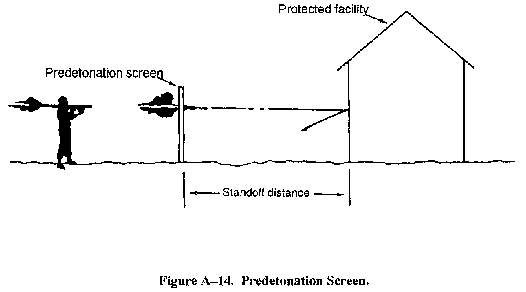
- Provide predetonation screens surrounding facilities (see Figure A-14). A predetonation screen may have several effects. Preferably it will damage the fuse on an antitank rocket, "dudding" the rocket (any structure behind the fence must still defeat the kinetic energy of the round). The second possible effect of the screen is to detonate an antitank rocket if it strikes the screen. In this case, the combination of standoff distance and the construction of the protected facility must defeat the gas jet from the shaped charge. In some cases, a predetonation screen may have no effect on an antitank rocket. For specific information on how to design predetonation screens and determine stand off distances, see the Security Engineering Manual referenced at the beginning of this appendix.
Building utilization--
- House critical assets away from the exterior of facilities.
- Provide an 8-foot-wide area (minimum) within the facilities (around the facilities' perimeter) that houses only noncritical assets.
- Place assets in protective areas below grade or underground.
- Provide entry foyers.
- Arrange furniture so that people are out of sight of windows.
- Minimize exterior access by blocking some of the existing doors.
Ballistic-Attack Checklist. In addition to the
minimum-level measures, consider the following measures to counter
a ballistic attack:
Site design--
- Site facilities on high points of ground, when possible.
- Block direct sight line to sensitive areas of the facilities using one or more of the following:
- Other facilities housing less critical assets.
- Dense plantings of trees or shrubs.
- Obscuration fences.
- Walls.
- Earth berms.
Building utilization--
- House facilities' critical assets within areas that do not have exterior walls when possible.
- Arrange entryways to eliminate sight lines.
- Arrange furniture so no personnel are within sight line of windows.
- Provide drapes or window shades to use at night.
- Provide fragment-retention film on glass windows and skylights.
- Cover skylights where there are potential sight lines through the roof.
Forced-Entry-Attack Checklist. In addition to
the minimum level measures, consider the following measures to
counter a forced-entry attack:
Site design--
- Provide unobstructed view around facilities.
- Site facilities away from installation boundaries and areas open to the public.
- Site facilities within view of other occupied facilities.
- Locate assets stored on-site but outside the facilities within view of occupied rooms in the facilities.
- Use screens or vegetation to conceal assets located on-site but outside of any facilities.
- Denote boundaries with fences or freestanding walls.
- Conceal and lock access ports to utilities.
- Illuminate building exterior or exterior sites where assets are located.
- Minimize shrubbery or other landscaping higher than 1 foot above finished floor height of buildings.
Building utilization--
- Locate protected assets as far from exterior walls as possible.
- Cluster assets to minimize the number of hardened spaces within facilities, or
- Distribute assets in large facilities to increase the difficulty of access, or
- Locate assets in basement spaces or underground facilities.
- Plan alternate locations for assets to allow the change of location periodically or during higher threat conditions.
- Locate assets above, below, or oblique to sight lines.
- Design building layout so that there are no areas hidden from view from control points or occupied spaces.
- Arrange building interiors to eliminate hiding places.
- Locate assets in spaces occupied 24 hours a day, when possible.
- Provide temporary sites for assets that may be threatened during higher threat conditions in spaces occupied 24 hours a day.
- Lay out buildings to conceal assets and make access difficult for intruders.
- Do not expose a buildings' structure or otherwise advertise the nature of the facilities' construction.
- Secure skylights.
- Secure roof access hatches.
- Eliminate exterior access to roofs, where possible.
- Secure exposed exterior ladders and fire escapes.
Cover-Entry-and Insider-Compromise-Attack Checklist.
In addition to the minimum-level measures, consider the following
measures to counter covert entry and insider aggression. This
list does not include the many options available to detect unauthorized
activity or to control access.
- Locate activities with large visitor populations away from protected assets.
- Locate protected assets in common areas where they are visible to more than one person.
- Minimize the number of entrances into protected areas.
- Place protected assets in restricted areas to which access is limited to authorized personnel or escorted visitors.
- Compartmentalize protected assets within restricted areas to limit access among authorized personnel.
- Establish access control points outside of controlled areas to search personnel and carry-in items.
- Provide metal or metal-clad doors and metal frames on exterior walls of access control points.
- Provide blast-resistant doors between access control points and protected areas.
Electronic-and Acoustical-Eavesdropping Checklist.
In addition to the minimum-level measures, consider the following
measures to counter eavesdropping:
Site design--
- Eliminate hiding places near the facilities from which aggressors can eavesdrop.
- Control access to exterior areas around the building.
- Control access to utility openings.
- Locate protected assets in buildings away from installation boundaries.
Building utilization--
- Locate protected assets away from the exterior of buildings and away from interior, uncontrolled areas.
- Surround protected areas with controlled-access rooms that house noncritical assets.
- Do not allow operable windows in protected areas.
- Account for all telephone and other cables.
- Disconnect and remove unused cables.
- Do not use intercom systems.
Visual-Surveillance Checklist. In addition to
the minimum-level measures, consider following measures to counter
visual surveillance:
Site design--
- Site facilities on a high point of land, when possible.
- Obscure assets from sight lines; use one or more the following methods:
- Screen critical assets with facilities housing less critical assets.
- Use visual barriers to block views of the asset (dense plantings of trees or
- shrubs, decorative walls or fences, earth berms, or obscuration fences.
- Use visual barriers to block views of the asset (dense plantings of trees or
Mail-Bomb-Tactic Checklist. In addition to the
minimum-level measures, consider the following measures to counter
a mail-bomb threat (measures for detecting bombs are not included):
Building utilization--
- Locate mail rooms away from main facility entrances, areas of high density population, and critical assets.
- Provide a bomb-disposal container in the mail room.
- Place mail rooms on the perimeter of facilities, or
- Use a central mail-handling facility that is separate from protected facilities.
Supply-Bomb-Tactic Checklist. In addition to
the minimum-level measures, consider the following measures to
counter a supply-bomb threat (measures for detecting bombs or
explosives are not included):
Site design--
- Park vehicles away from loading dock areas.
- Site facilities so that loading dock areas are away from other facilities or high density population areas.
- Site facilities as far from other facilities as possible.
Building utilization--
- Place supplies so they are at least 8 feet from facility walls to provide a standoff distance between bombs and walls.
- Place receiving areas away from facility entrances.
- Locate assets away from receiving areas.
- Provide a separate facility for handling and receiving supplies.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

