PLANNING AND COORDINATION
Corps planning for deception begins immediately upon the receipt of a warning order or guidance from higher headquarters. This planning is not separate from the operation planning; it is an integral part of the Corps total planning process.
RESPONSIBILITIES
The commander and the operations officer at each echelon have explicit and inherent responsibilities for the deception effort.
Commander
The Commander should:
- Assess mission order for stated and implied deception tasks.
- Consider the use of deception in the operation.
- Task staff to evaluate utility of deception during "preliminary consideration" phase of planning.
- If deception appears feasible (it may be infeasible due to lack of time or resources), state the tentative deception objective with initial planning guidance.
- Approve deception objective, story and plan, and allocate resources to ensure successful execution.
- Monitor battle for point at which deception should be exploited.
Operations Officer
The Operations Officer must:
- Recommend the deception objective, story and plan.
- Plan the deception effort.
- Ensure the deception effort is coordinated.
- Supervise execution of the deception plan.
- Control termination of the deception effort.
- Evaluate the deception effort.
COORDINATION VERSUS SECURITY & RISK
A fundamental requirement of a successful deception operation is that the enemy must not discover that the operation is being conducted. Failure fully to coordinate and execute a deception operation in detail can also risk mission failure. The commander is faced with this dichotomy every time he considers the conduct of a deception.
The commander must examine his ability to conduct deception while maintaining security. He must decide who must know of the deception and how much they must know.
Will the commander have subordinate commanders conducting operations that are a part of the plan, wittingly or unwittingly? If he does not inform key people, they might execute their portion of the plan in a manner detrimental to the overall plan. But if too many people are aware of the deception, security is more difficult.
An example of this occurred in a NTC rotation. A Task Force Commander established a deception plan to make the OPFOR Commander commit his Regiment on a particular avenue of advance. The OPFOR Commander believed the TF Commander's story and had started to commit on the desired avenue. A scout, who had been established in an OP to report the progress of the OPFOR Regiment, reported, via an unsecure radio net, that the Regiment was proceeding along that avenue ". . . just like we wanted them to do!" The OPFOR was monitoring the net. The Regimental Commander changed his axis of advance and successfully accomplished his mission, much to the chagrin of the Task Force Commander.
The relationship between coordination and security can be seen in the diagram below.
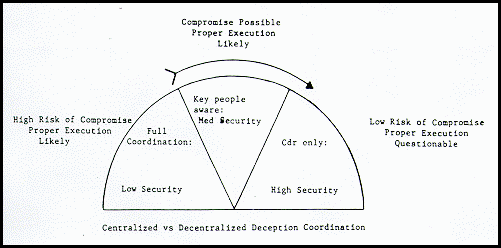
A widely coordinated plan will ensure smooth execution, but it likely will be compromised.
"Know the enemy and know yourself; in a hundred battles you will never be in peril. When you are ignorant of the enemy but know yourself, your chances of winning or losing are equal. If ignorant both of your enemy and of yourself, you are certain in every battle to be in peril."
--Sun Tzu, The Art of War
PLANNING
History shows that successful deception plans are executed prior to the start of actual operations. Planning for deception operations must start prior to the beginning of a conflict. Without a file or data base of certain information concerning friendly and enemy forces, it is impossible to conduct a successful deception effort on the time-constrained AirLand battlefield. Once a conflict starts, commanders will have few resources available to develop a data base to be used in planning deception operations. Deception planners must have detailed information on what friendly forces look like to the threat, available enemy sensors, and the enemy commander and his troop control cycle. This can be developed in peacetime.
Know Yourself
The deception planners at corps and division must have available to them the profiles of friendly units and installations within their area.
These profiles are a composite of all the signatures an element provides to enemy intelligence collection assets. These include:
- Physical: What does the unit look like to satellite photography? What does the unit look like to aerial reconnaissance photography? What does the unit show to a ground observer (includes the unit's sounds and smells as well as visual)? What does the unit look like conducting different operations (movements, preparations for movement, attack, assembly areas, defense, bivouac, air traffic, etc.)?
- Thermal: What are the thermal emissions from the unit? How do these change from warm weather to cold weather?
- Infrared: What are the IR signatures from the air and from the ground?
- Signal Emissions: How many transmitters does the unit have and how many are active during certain operations (in an assembly area, prior to an attack, in defensive positions, etc.)? What is the volume of traffic displayed by a unit? What type of traffic does the unit have (insecure, secure, digital), what means do they use (AM, FM, PCM, etc.), and in what frequency spectrum do they operate? This must also include sister service and allied liaison communications means. Are they good or poor in RTO procedures?
- Electronic Emissions: What are the unit's other electronic signatures? These include radars, beacons, computers, etc.
Do It Now!
These profiles must be developed by the Corps and updated on a continuing basis since they will change as equipment and TOEs change and as the proficiency of the unit in OPSEC and SIGSEC changes. Commanders must commit organic assets or obtain support from higher headquarters to gather this information. Request aerial recon of units during FTXs. Fly Guardrail against your own forces. Send out ground observers and exercise ground surveillance and target locating radars. This will not only build a data base for deception planners, but it will show strengths and weaknesses in our own forces and how easy it is for the enemy to identify us.
Know the Enemy
A deception plan must be based on detailed knowledge of the enemy. Most of the knowledge required can be developed in peacetime. You must know your target -- the specific enemy commanders controlling the forces you want to influence, the enemy sensors, and how the sensors feed the enemy.
The Target
The target for the deception effort at Corps is normally a Front commander, although in some cases the target might be an Army commander. What is his personality profile? What is his educational background and how has he grown up? What sensors does he trust the most? Is he enamored by high tech sensors or does he believe reports from scouts or operatives? You must know him if you want to deceive him!
Sensors
You must know the capabilities of enemy sensors. What frequencies do they operate on? What is their doctrinal mode of operation (day, night, intermittent, or on a schedule, etc.)? What is their range across the FLOT? Where are they positioned on the battlefield? Are they in line of sight or non-line of sight? Which ones are organic to the front or army and which ones are controlled by higher headquarters? (Those that are organic feed the target's decision cycle directly, while those controlled by higher headquarters usually have a time lag.) This file must be kept current. There will not be time to develop a file when the shooting starts.
Decision Cycles Versus Troop Control Cycles
One problem facing Corps planners is whether a deception effort, other than higher headquarters directed, is feasible considering available time. Since the result of deception is action/inaction by enemy forces, consideration must be given to time available to influence troop control cycles. The C3CM Joint Test Force has determined that it is possible to influence the Soviet troop control cycle. But without a thorough understanding of the Soviet process, deception can be dangerous to the deceiver. The deception plan must be developed, coordinated, executed, sensed by enemy sensors, input into the enemy's decision cycle, orders promulgated, and actions taken by enemy forces -- all on a time constrained battlefield.
Realizing that the planning process is continuous and concurrent, the diagram below compares doctrinal cycles for a U.S. Corps and a Soviet front.
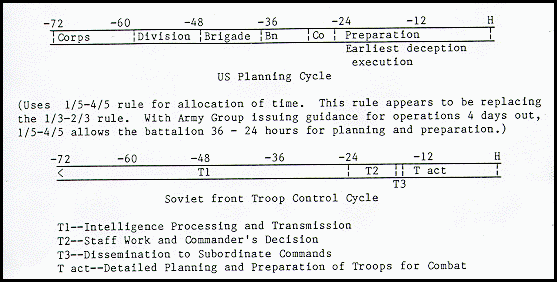
If the intent of the commander is to influence enemy action at H hour, the Corps can (best case) start having company-sized units executing deception activities at H-24 hours. But at H-24 hours, the Soviet front has completed their intelligence collection for actions to be taken at H hour and are formulating plans without being aware of our deception activities. This does not mean that we cannot or should not conduct deception, but that deception activities must be designed with a thorough understanding of the threat troop control cycle and when and where to influence it.
COORDINATION
As stated earlier, the commander must decide the trade-off between a fully coordinated plan and the security/risk associated with full coordination. Based on his decision, the G3 is responsible for ensuring that the plan is coordinated as desired and integrated into the operation.
G3 Plans
The staff deception element should be an integral part of the G3 Plans section at Corps. Upon receipt of a new mission, the G3 Plans and the plans officer assigned the responsibility for the new operation should have the deception element conduct a preliminary analysis concerning feasibility of deception. This analysis, internal to G3 plans, should reveal the feasibility of a deception effort. If deception is feasible, internal coordination with other staff elements should begin.
Internal Staff Coordination
Checks should be made with other Corps staff elements to ensure that the deception plan being developed can be executed. Some of the coordination required is:
G2:
- Specific information on the target, his sensors, and his probable course of action, if not already known.
- Ability to feed back PIR and IR to the deception element to allow monitoring of the enemy's acceptance of story.
- Ability of organic and higher IEW assets to feed or deny information to the enemy commander.
G4:
- Determine logistics plans to support the operation.
- Ability of logistics units to support the deception plan without hindering the support necessary for execution of the overall operation.
Corps Artillery:
- Ability of Corps artillery to neutralize enemy sensors or C2 linkages, based upon fire support assets available and planned, and targeting priorities.
- Ability to support with intelligence and targeting information.
Corps Signal:
- Backup assets available to portray communications linkages that may be required.
- Development of the Corps communication plan to ensure it supports the deception effort.
Corps Engineer:
- Assets available to portray mobility, countermobility, or survivability work.
Corps ADA:
- Assets available to portray protection of critical assets.
Corps ALO:
- Current Low Level Transit Routes (LLTRs) and known reconnaissance flights.
Coordination may be required with elements outside Corps headquarters. In a mature theater this is almost always needed due to the Corps operating as part of an Army Group, with Corps adjacent to it. If the Corps is executing the Army Group's operational deception plan, the coordination with higher and adjacent units should be minimal, but coordination with some subordinate units may be required.
Adjacent Corps:
- Units that can be positioned to support the Corps plan.
- Communications linkages available.
- Adjacent Corps plans for the operation, to ensure synchronization and non-interference of deception efforts.
Higher:
- Assets available to support Corps effort; i.e., positioning of reserves, establishment of C2 linkages, instructions to adjacent units, etc.
Air Force Tactical Air Control Center or Air Support Operations Center:
- Planned LLTRs and recon flights.
- Air Force plans that impact on the operation.
PLANNING GUIDE
The ability of planners to develop an effective deception effort within the time constraints of the Corps planning cycle is facilitated by a structured approach to planning. Previous doctrinal publications contain deception planning guides. These are good outlines, but too general for detailed planning. V Corps developed the more detailed Deception Estimate/Planning Guide that follows. Though designed for Corps use, the guide can be modified for any echelon.
1. Current Situation.
2. Courses of Action.
3. Based on the above information, does the enemy appear to be vulnerable to deception?
4. What do we want the enemy to do and whom do we want to deceive?
5. What do we need to tell and show the target commander to make him do what we want?
6. What resources are available to convey the deception to the target?
7. OPSEC considerations:
8. How is the enemy likely to react to the deception? (possible courses of action)
9. What are the risks to U.S. forces?
10. Will compromise of the deception significantly degrade actual operations?
11. Based on the above, is there an opportunity to perform deception?
12. If the opportunity exists:
- Prepare the plan (Annex to the OPLAN/OPORD).
- Prepare RFI/PIR to provide feedback on deception efforts.
- Task units to perform the deception (integration of specific tasks/events into basic OPLAN/OPORD and functional annexes).
- Coordinate efforts; manage mission.
- Modify deception based on feedback, if necessary.
- Phase out operations.
 Table
of Contents
Table
of Contents Doctrine
Doctrine Postscript
Postscript
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

