CHAPTER 1
Doctrinal Update
by MAJ Michael Kinard, U. S. Army Engineer School
 |  |  |
| "One
of the serious problems in planning the fight against American doctrine is
that the Americans do not read their manuals, nor do they feel any obligation
to follow their doctrine...."
--From a Soviet Lieutenant's Notebook |
Purpose
This chapter familiarizes the reader with recent doctrinal changes, reviews the breach tenets, and standardizes terminology used in the force. The intent is also to entice readers to dig into the doctrinal references for inclusion into OPD/NCOPD training at all levels.
Doctrinal Changes
FM 3-34.2, Combined Arms Breaching Operations, 31 August 2000, has replaced FM 90-13-1 with Change 1, Combined Arms Breaching Operations, 7 May 1993.
The biggest changes in the new doctrine are:
Assault
Assault was added as a breach fundamental to counter disturbing trends identified by field units and the CTCs indicating that when planning breach operations, we, as a force, were losing focus on the objective. The mission is not "to breach;" the mission is "to attack." The assault is arguably the most important part of the attack. Yet, many units plan the breach separate from the assault and the rest of the mission. The result is not only a lack of synchronization, but also a lack of planning and resources for the assault. The addition of assault as a breach fundamental is meant to underscore that "A breaching operation is not complete until:
In short, the assault is an integral part of the operation. We must ensure that there are enough lanes to project enough forces, with enough support to seize or destroy enemy forces at the point of penetration and/or the objective.
Deletion of Breach Types
We no longer distinguish between breach types (i.e., In-stride, Deliberate, Assault, and Covert). The deletion of the breach types counters trends identified by field units and the CTCs indicating that we allow breach type to drive planning and task organization instead of the MDMP, Staff Estimates, and the Reverse Breach Planning process. For example, unit planners were mistakenly "task-organizing for a deliberate breach" instead of task-organizing for mission accomplishment. The intent is to focus on using the MDMP, Staff Estimates, and the Reverse Breach Planning process to drive the amount and allocation of mobility, maneuver, fire support, and other assets throughout the breach organization to achieve the breach fundamentals. In this manner, the situation and commander's intent don't just drive the scheme of maneuver, but also the task organization, as well as the level at which the operation is controlled. The deletion of the Assault and the Covert breach should not be interpreted to mean that the assault force no longer requires mobility assets to breach protective obstacles, nor does it mean that there will never be a COA requiring a breach executed under covert conditions. It merely asserts that regardless of the type of operation, breach planning must follow the breach tenets and breaching fundamentals. The new doctrine places the focus on planning for the success of the mission, whatever the situation; furthermore, it deletes doctrine that served little purpose and was a source of confusion for some.
Reverse Breach Planning
The reverse breach planning process, widely accepted as TTP, was added to doctrine to aid units in developing more synchronized plans, and better allocate available mobility assets throughout the breach organization.
The process is conducted during COA Development. Most units already reverse-plan to some extent, but often fail to start at the objective and work back to the LD when identifying the number of breach lanes and the mobility assets required for the main effort, then each supporting effort. As a result, during execution, we often run out of assets before reaching the objective. The process can be organized, and is typically executed in six steps:
Rules of Thumb:
Restrictive Terrain: According to FM 3-34.2, Appendix D, ".the number of lanes available to the assault force may be less than what is actually needed. For example, a battalion-size assault force may be restricted to using a single lane through an obstacle because of the restricted terrain. A more detailed look at the reverse breach planning process is included in Chapter 5: Synchronizing the Breach.
Breach Tenets: The Breach Tenets have not changed except for the addition of Assault to the Breach Fundamentals (SOSRA).
| I | Intelligence |
| B | Breach Organization (Support Force, Breach Force, and Assault Force) |
| B | Breach Fundamentals - SOSRA (Suppress, Obscure, Secure, Reduce, and Assault) |
| M | Mass |
| S | Synchronization |
Terminology: The following terms are used in breaching operations:
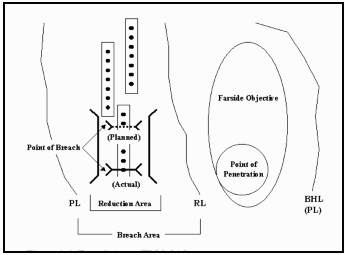
Figure 1. Breach Area (FM 3-34.2).
 |  |  |
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

