CHAPTER 5
CONCURRENT OPERATIONS
Concurrent operations are those functions which are routinely conducted as part of any division operation. They contribute to overall combat effectiveness, but are not stand-alone actions such as offensive or defensive operations. The division conducts them to enhance overall operations. This chapter provides some examples of techniques for planning and executing concurrent operations.
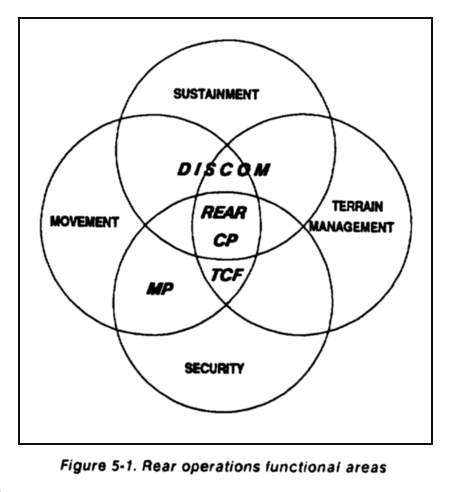
The division's rear operations include all activities conducted to the rear of elements in contact to ensure freedom of maneuver and sustainment of close, deep, and rear operations. Rear operations comprise four interrelated functions:
- Sustainment.
- Movement.
- Terrain management.
- Security.
Area damage control supports all four functional areas and is addressed separately.
Figure 5-1 shows how these functional areas interrelate. The rear CP synchronizes these key rear area activities.
The division conducts rear operations within the division's rear area (DRA). The DRA extends from the rear boundaries of forward brigades to the division's rear boundary. It contains a large number of CS and CSS units, chemical munitions and delivery means, C2 headquarters, and noncommitted combat units. It may also contain joint facilities, such as air bases, and host nation facilities and population centers.
The ADC-S is the rear operations commander. He is responsible for conduct of division rear operations. The direction and synchronization of sustainment operations is the responsibility of the rear commander. He and the rear CP staff ensure that sustainment operations respond to the needs of the division.
The rear commander commands and controls rear operations through the division rear CP. The CP has three cells: a HQ cell, an operations cell, and a CSS cell. The rear CP normally collocates with the DISCOM CP for security, life support, and ease of coordination. However, both CPs are separate and distinct. See Chapter 2 for a detailed discussion of the rear CP.
Sustainment
The basic mission of CSS units is to sustain the battle. Their sole purpose is to maintain and support division soldiers and their weapons systems before, during, and after operations. Sustainment functions consist of those actions that man, arm, fuel, fix, move, and sustain soldiers and their systems. Maintaining the capability to sustain the force continuously is the focus of rear operations. The rear operations functions of movement, security, and terrain management, as well as area damage control, must be integrated with sustainment to provide synchronized logistics support.
Sustainment planning is the responsibility of coordinating staff officers with personnel and logistics responsibilities and special staff officers with CSS responsibilities. The G1 or AG plans and coordinates those measures necessary to man the force. The G4 plans and coordinates (with DISCOM) measures to arm, fuel, and fix the force. The DTO plans movement control and highway regulation. The G5 assists in obtaining host nation resources such as civilian labor and supplies; he also helps coordinate these activities. Personnel and logistics staff officers perform their planning and supervisory functions primarily from within the CSS cell of the division rear CP. They collocate with the DISCOM CP to aid in logistics planning, coordination, and execution. Their location also helps integrate the functions of terrain management, movement, security, and area damage control.
DISCOM, the logistics operator of the division, translates logistics planning into logistics support. DISCOM provides supply, maintenance, HHS, and transportation assets to the division.
The DISCOM S-2/3 section is the commander's interface with the division rear CP, The S-2/3 section develops the DISCOM critical asset list and recommends its priorities to the commander in concert with the division materiel management center (DMMC). Once the list is approved, the S-2/3 section furnishes it to the rear CP operations cell where it is continually monitored and adjusted.
The S-2/3 section is also the key interface with supporting criminal investigation division (CID) elements for the command's logistics security (LOGSEC) operations. As the DISCOM link with the rear CP, the S-2/3 section maintains an operations map and updates other staff officers on the current situation. (For detailed discussions of CSS sustainment operations, see FM 63-2-1.)
Movement
Movements are generally divided into two categories--tactical and nontactical. Tactical movements are combat units moving to or from close or deep operations. Nontactical movements include all other types of movement.
Movement includes planning, coordination, and synchronization of mode operations, terminal operations, and movement control. Movement is inherent in all combat, CS, and CSS functions, tying sustainment and all other battlefield operations together.
Movement makes sustainment possible. Supplies and personnel replacements constantly move from the sustainment base at corps (and EAC) into the DRA and then forward to support close operations. Casualties and damaged equipment are evacuated from the forward area for treatment or repair and returned. Movements take place between the forward brigade areas, the DRA, and the corps rear area. They also take place laterally within the DRA.
The division G3 at the main CP plans and directs all tactical movements. The rear CP operations cell executes the G3's priorities in deconflicting and controlling movements to ensure movements support close and deep operations.
The rear CP operations cell controls nontactical movements in the DRA as well as the tactical maneuver of response forces and the TCF. It monitors and deconflicts movement of nondivisional forces through the DRA. It ensures necessary routes are cleared and additional CSS support is available as needed. The rear CP operations cell coordinates CS resources, to include engineer, NBC, reconnaissance, and chemical decontamination support. It also coordinates MP support with PM operations at the rear CP for movements within the DRA.
The rear operations cell also deconflicts tactical and nontactical movements within the DRA. It enforces movement priorities and directs the use of alternate routes to lower priority traffic. The operations cell must coordinate closely with the G3 at the main CP, and with the DTO, DISCOM MCO, and provost marshal to ensure tactical movements are not hindered.
The G4 designates MSRs. He determines MSR conditions (red, green, and yellow) based on information received from users, MPs, and engineers. He maintains the status, and expected recovery time, of those routes which are not green. A timely exchange of information between the military police, engineers, and G4 is essential.
The DTO and CSS cell of the rear CP plan and coordinate all nontactical movements. The DTO coordinates movement priorities with the rear CP. On approval of priorities by the division's rear operations commander, the DTO provides them to the DISCOM MCO.
The DTO and CSS cell of the rear CP plan and coordinate all nontactical movements. The G3 provides movement priorities from which the DTO deconflicts nontactical movement requests and issues movement orders. The DTO and G3 operations cell deconflict tactical and nontactical movements. They plan movement of supplies and material from the DSA forward to BSAs and back. They also coordinate CSS movements between the corps rear and DSA, or, in the case of throughput, directly to BSAs.
The DISCOM MCO controls division motor transport assets for CSS. He ensures established movement priorities are followed. The MCO requests additional transportation from the DTO if requirements exceed DISCOM assets. The DTO, in turn, recommends tasking other assets or requests COSCOM support to resolve the shortfall.
The CS and CSS units execute nontactical movement and assist with tactical movements. Through coordination with the DTO, movement control officer, and the rear operations cell, they ensure that convoys receive necessary security, road congestion is minimal, and supplies reach their required locations at the right time.
If the division does not coordinate tactical and nontactical movements, road congestion can foil the best plans. This degrades the ability to deliver supplies and replacements to maneuver units or evacuate casualties and damaged equipment. Tactical movements normally receive priority over nontactical movements. (FMs 55-2 and 55-10 discuss movements planning and execution in greater detail.)
The division rear CP establishes a process of tracking convoys in the DRA and from the division rear boundary to their destination in the division area. Further, it--
- Monitors LOCs to determine problems in movement flow.
- Develops alternatives to ensure movements remain constant.
- Keeps transportation users informed of available assets.
- Programs back-haul availability to cut down on delayed returns.
- Directs MSR maintenance and security.
- Processes convoy clearance request for units requesting movement on division's MSRs.
Terrain Management
Terrain management demands highly centralized planning and control. The major problem in positioning units within the DRA comes from the competing demands of mission and security. Positioning of units in the DRA requires a fine balance between the needs of units, the requirement to support the concept of operations, and the need to provide security to units. Terrain management should facilitate current and future operations. Faulty terrain management can result in congestion, interruption of rear area traffic patterns, and degradation of support operations.
Terrain management for the DRA is the responsibility of the rear CP. The operations cell manages terrain in coordination with the CSS cell, major subordinate commands, and separate units. Terrain management involves all real estate in the DRA. Locations of bases, base clusters, MSRs, key facilities, risk areas, TCPs, and target reference points are posted on the situation map. The map is used for terrain management and movement deconfliction and control.
Terrain management requirements should be analyzed using the factors of METT-T. A unit's mission must be analyzed to determine specific terrain requirements. Field artillery units must be within range of intended targets; transportation units should be near road networks; supply units, near LOCs. Unit missions must also be evaluated to determine their importance to the division mission. Once unit missions and contributions to the division operation have been analyzed, conflicts between unit requirements can be resolved, and units positioned.
A continual IPB of the rear area will provide much of the data needed to accurately assess terrain management needs. The rear CP operations cell uses the intelligence estimate and other intelligence products from the main CP to analyze enemy capabilities and determine possible threats. If a significant air assault threat exists, CSS units should be positioned away from likely landing or drop zones. Combat units, such as the division reserve or TCF, may be positioned close to likely enemy LZs to counter the threat at its most vulnerable time--during insertion.
The rear CP operations cell should not position CSS units on enemy air or ground avenues of approach or adjacent to likely threat objectives. However, it should position units to provide reconnaissance and surveillance of these avenues as part of security and counterreconnaissance actions.
CSS units have unique terrain requirements. When possible, they should be near established air, road, rail, and water LOCs to aid in mission accomplishment. Positioning must simplify receipt of supplies and materiel from higher echelons and ease their movement forward to the MBA. Positioning must also make evacuation, repair, and return of damaged equipment easier.
The rear CP operations cell analyzes the terrain to determine trafficability, facilities available, and natural obstacles which can support DRA security or hinder sustainment or movement operations. The CSS cell and DISCOM ensure that terrain managers in the operations cell are aware of terrain needs of divisional and corps CSS units.
Terrain impacts on mission effectiveness. A maintenance unit in a built-up area with adequate power, hardstand, and civilian resources can repair material more efficiently than under field conditions. The HHS activities need trafficable roads, shelter, warmth, and proximity to LZs to receive, care for, and evacuate casualties. Supply units require storage space and adequate room to disperse. The G5 coordinates facilities with the host nation and the rear CP.
All CSS units require transportation networks which connect them with sources of supply and support and with their customers. Routes selected should be able to sustain heavy traffic in all weather conditions. They should accommodate the expected traffic volume to eliminate congestion and avoid choke points. Routes should not conflict with tactical maneuver plans. Planners must identify alternate routes and develop procedures to switch nontactical traffic to them as needed. During offensive operations, the operations cell chooses unit locations to extend supply routes and minimize changes to division and corps CSS transportation plans.
The G3 in the main CP positions maneuver and fire support assets based on the concept of operations. This may include units in the DRA such as the division reserve and aviation brigade. Once he makes these tactical positioning decisions, the rear CP (in coordination with DISCOM and G3) positions CS and CSS assets in the DRA.
Planners in the rear CP must know how the division is task-organized and which units (divisional, corps, EAC, or host nation) are located in the DRA. The division's rear operations cell establishes priorities for terrain and maintains them based on unit missions within the DRA.
After initial positioning, the operations cell monitors the tactical situation. It directs or responds to requests to position and reposition units in the DRA to enhance continuous support and survivability. This centralized management process prevents positioning conflicts, maintains an integrated security plan, ensures unit survivability, and improves OPSEC.
Whenever the division moves, either forward or to the rear, the rear CP plans for gaining additional terrain within the DRA as the tactical situation dictates. The G3 at the main CP establishes phase lines during offensive operations to indicate future DRA boundaries. He coordinates with the corps G3 for establishing phase lines within the DRA for additional terrain during retrograde operations. Close coordination with the corps rear area operations cell through the corps rear CP liaison is essential. This ensures a logical handoff of terrain management responsibilities.
The G3 operations cell in the rear CP compares terrain preferences with security requirements. It positions CSS units to enhance their survivability. Cover and concealment are keys to protecting them from detection and attack. Dispersion avoids catastrophic damage from air, artillery, and mass destruction weapons. The commander must weigh this against the advantage of positioning units close enough together to enhance security.
Base Configuration
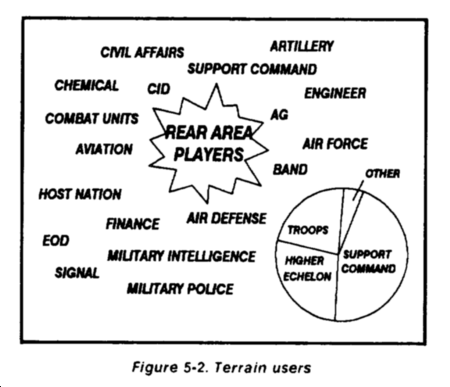
Numerous units and activities occupy terrain and conduct operations in the rear area. The units and activities shown in Figure 5-2 all compete for usable terrain and facilities.
The rear CP operations cell plans for units two echelons down. For rear operations, these echelons are base clusters and bases. This means placing units together to form multiunit bases.
The rear CP operations cell designates base commanders. The base commander normally is the senior unit commander when more than one unit is present in the base. However, a medical unit commander, even if senior, is prohibited from commanding a base or base cluster containing nonmedical units (AR 600-20).
Many factors determine which units are grouped into bases and their location. A thorough METT-T analysis, including size and composition of each unit, is required. Medical units should not collocate with units that may be priority enemy targets. They should, however, collocate with units capable of assisting in their defense.
Bases have clearly defined defensible perimeters and entry and exit points. By grouping units together, they share responsibilities for security, capitalizing on each unit's strengths while minimizing weaknesses. A mix of weapons systems, sufficient personnel for planning and supervising, and adequate communications assets form a viable base. Positioning similar units in different bases, unless it is absolutely necessary to collocate them in the same base, ensures a degree of dispersion.
Bases are represented on situation maps by drawing a line around them similar to an assembly area. This establishes the base commander's AOR. The base is labeled with a numeric designator. The rear CP maintains lists of units occupying specific bases, including types of units, personnel strength, major weapons available, and other information not shown on the situation map.
The base commander's AOR should allow sufficient space for subordinate units to operate, establish perimeter defenses, and conduct surveillance and counterreconnaissance. The line denoting the base should be drawn far enough from its internal installations to allow the use of artillery without endangering the base. For example, DANGER CLOSE range for cannon artillery is 600 meters. The line designating the base should beat least 600 meters from subordinate units.
Most bases are in a base cluster. However, some may operate separately. These separate bases report directly to the rear CP which integrates them into rear security plans. Units in the DRA not designated as bases, such as air defense and artillery tiring units or signal sites, should be incorporated under a base cluster commander.
Base Clusters
The rear operations cell establishes base clusters by placing geographically contiguous bases under the control of a headquarters and designating it a base cluster. The base cluster becomes the next higher tactical headquarters of those bases. The rear CP may also establish a base cluster for a corps support group operating in the DRA. The corps support group then assigns bases within its cluster to its subordinate units and informs the rear CP of these locations and the information required by the rear CP as to type, composition, and weapons.
The rear CP operations cell should designate, whenever possible, a battalion- or brigade-level headquarters as the base cluster headquarters. Battalions and brigades have organic staffs that can function as the base cluster staff. CSS battalions and brigade-level headquarters have this capability in their TOES with a support operations section for customer mission support activities and a separate operations section for C2 of internal unit operations. The operations sections functions as the base cluster operations center (BCOC). It coordinates terrain management planning and use, and security planning and execution, with the rear CP.
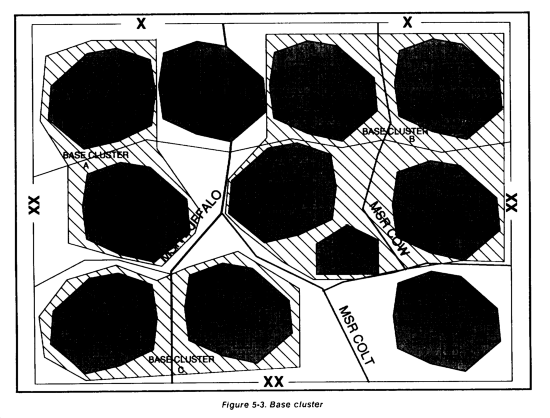
Base clusters are shown on the rear operations situation map by drawing a line around those bases that have been clustered together and placing an alphabetic designator within the area. Figure 5-3 shows a typical base cluster. The base cluster commander's AOR should provide sufficient area for him to organize his subordinate bases and units and sufficient depth to organize a defense.
The rear CP analyzes the DRA to develop risk areas. Risk areas are areas of terrain that are not useful to the division and provide no advantage to the enemy. By designating risk areas, the rear CP weights the limited MP force within the remainder of the DRA. Occasional overflights or mobile patrols monitor risk areas.
Security
An understanding of the threat to the rear area and a good IPB for the DRA are needed to ensure proactive security operations. The IPB for the DRA determines the potential effects of enemy capabilities and weather and terrain on rear operations. The specific focus of rear IPB is the enemy's air threats, airmobile and air assault threats, SOF threats, and the counterintelligence threat (agents, sympathizers, and terrorists). This IPB becomes the basis for initial patrol plans and a consideration in selecting base cluster locations. Continuous IPB ensures that the rear operations commander has current intelligence and information for decision making. A detailed discussion of the IPB process for rear operations is found in FM 34-130.
Security of the DRA is a command responsibility extending from the division commander through the rear operations commander, the base cluster and base commanders, to the unit commander. It includes all actions from local defensive measures through commitment of TCFs.
The rear operations commander exercises OPCON over base defense forces, response forces, and TCFs in response to rear area threats. The rear CP operations cell supports the rear operations commander's efforts by--
- Grouping units into bases.
- Forming base clusters when necessary.
- Designating base and base cluster commanders.
- Collecting, analyzing, and approving base defense plans.
- Developing an integrated DRA security plan.
- Approving and coordinating obstacle and fire support plans.
- Positioning response forces and fire support assets.
- Providing continual METT-T analysis of the DRA.
- Providing continual information on the enemy and other matters to units within the DRA.
Units positioned in the DRA normally operate from bases or base clusters which provide a defensive barrier for sustainment. Military police units provide area security around bases and may detect and engage threats before bases becoming involved.
Security operations in the DRA are based on economy of force measures and are designed to provide a graduated response to threat activity. There are three levels of response:
- Level I. Response to threats which base defense forces can defeat.
- Level II. Response to threats which are beyond the capabilities of base defense forces but which response forces can defeat.
- Level III. Response to threats which necessitate a command decision to commit tactical combat forces.
These guidelines should not restrict a commander's response to a threat. He must apply the necessary force to destroy the threat.
Base Defense Forces
Every unit or base is responsible for its own security. It must be capable of detecting and defending against enemy forces. Bases should use both active and passive measures to avoid detection. The base, if detected, must be able to defeat the threat or withstand attacks until assistance arrives.
Base defense is the cornerstone of rear security operations. The unit or base commander--
- Prepares a base defense plan.
- Rehearses all personnel and units within the base on the effective execution of the base defense plan.
- Organizes a reaction force.
- Recommends movement or repositioning of the base to enhance security.
- Coordinates mutual support from other bases or the base cluster commander.
- Coordinates response force operations.
- Adjusts base defenses as the threat changes.
- Determines the base defense status.
Planning and Coordination. Unit and base commanders are responsible for developing and implementing comprehensive security plans to defend their sites and protect their sustainment capability.
In establishing a base defense, the base commander employs the same procedures and techniques maneuver commanders use in developing a perimeter defense. Security is established for 360 degrees and the bulk of combat power is placed on the outer edge of the position. Interlocking fields of fire are used to prevent penetrations of the perimeter. Perimeter defenses must be established in either urban or rural terrain.
Base commanders must ensure they and their subordinate units are aware of other units and bases in their areas of interest and establish limits of fire to prevent fratricide between units. To coordinate indirect fires, base commanders may establish restricted fire areas around subordinate units and restrictive fire lines between units.
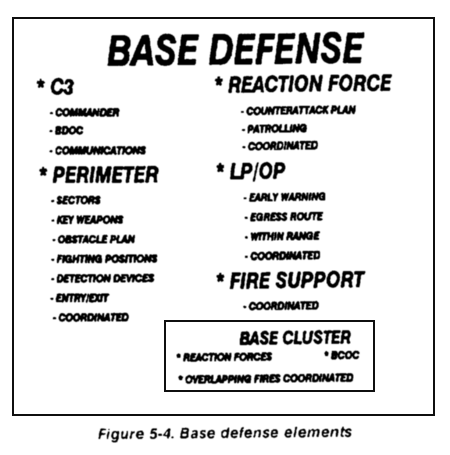
Base commanders must coordinate with their base cluster commander or the rear CP to ensure they are assigned sufficient terrain to establish OPs and patrols outside their perimeter. These locations must be integrated with NAIs established by the base cluster commander or the rear CP. Figure 5-4 outlines the elements needed for a viable base defense.
Base and Base Cluster Defense. Base defense operations include all active and passive measures units take to protect themselves from enemy activity. Units conduct defensive operations concurrent with normal support operations. These include hardening and dispersal actions, cover and concealment, deception, and immediate reaction to enemy threat or attack. Extensive use of obstacles, sensors, surveillance devices, and OPs enhances these operations.
Base and base cluster commanders must identify shortages in materiel or weaknesses in their defenses. Protective obstacles (wire, demolitions, and mines) are essential to each base's defense. Repositioning should be considered when a unit's defensive posture is inadequate to defend itself. The rear CP coordinates the relocation of a unit with its parent unit. Military police may assist in movement of critical units.
Base defenses should not automatically engage hostile forces. The first line of defense is to avoid detection. Base and base cluster commanders should implement counterreconnaissance actions in coordination with those established by the rear CP. Surveillance of NAIs, routine patrolling, and use of OPs support these actions. Base commanders should prepare to defend the base, report the hostile force, and observe it. They must understand when and if the enemy should be engaged, and when to do it. They must inform the base cluster or rear CP if they engage the threat.
The base commander establishes a base defense operations center (BDOC) in support of the tactical chain of command. The base commander, when possible, should be a battalion commander with a battalion staff. The battalion staff can plan and control base defenses and battalion operations. The BDOC plans, coordinates, and supervises base defense operations. Personnel from the base commander's unit normally form the BDOC. However, the base commander may draw personnel and equipment from his own unit and tenant units to form a functional BDOC. The BDOC may be a relatively small element, possibly as small as two personnel per shift (an NCO and a clerk/radio operator). The BDOC--
- Defines the base perimeter and establishes responsibilities for sectors.
- Ensures communications are established and maintained within the base and key locations such as entry and exit points, OPs, and the BCOC.
- Increases or decreases defensive postures based on threat condition (THREATCON).
- Develops and monitors the base defense plan.
- Monitors and reports the base defense status.
- Coordinates fire support, obstacles, reaction force, and response force plans for the base.
- Maintains a current situation map of base units, OPs, patrols, and other friendly and enemy data as required.
Base clusters rely on mutual support between bases to enhance security. Mutual support comes from the use of reaction forces to assist threatened bases, from the integration of MP patrol and surveillance plans, or from coordinated and interlocking fires if the bases are in close proximity. It is important to note there are no fire support personnel on a base cluster commander's staff. Requests for fires are processed through the division rear CP.
Base cluster commanders, like base commanders, must exercise positive clearance prior to initiating fire missions in the DRA. Positive clearance in this situation means asking the right questions of the unit requesting fire. Can you actually see and positively identify the target as enemy? Is the target doing anything hostile that requires fire now, rather than maneuver action a little later? As a general rule, the rear FSE should require "eyes on target" prior to initiating fires in the DRA.
The base cluster commander coordinates base defense force operations and conducts security operations by using the reaction forces of each base in the cluster if response forces are unavailable. Base commanders must have a plan to reestablish their reaction force if the primary reaction force is committed.
Each base cluster commander forms a BCOC to monitor the status of subordinate bases and to receive and pass information from the rear CP. The base cluster commander should be a battalion or higher commander with a staff that can accomplish unit and base cluster functions. BCOC tasks include--
- Defining the base cluster perimeter and establishing responsibilities for sectors.
- Developing and monitoring the base cluster defense plan.
- Establishing and maintaining communications with all assigned bases, separate units in the base cluster, and the rear CP.
- Receiving and passing on threat and base defense status reports.
- Adjusting defense posture based on the threat.
- Coordinating fire support, obstacle, reaction force, and response force plans.
- Maintaining a current situation map.
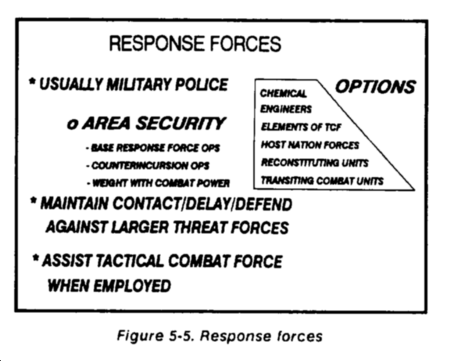
Response Forces
Response forces (Figure 5-5) are normally made up of MP units weighted by fire support assets. Fire support for MP response forces may consist of artillery or army aviation. Military police are trained in calling for and adjusting indirect fires. They can control CAS with assistance from a TACP or Army aviators trained in JAAT operations.
Military police elements may be committed to other priority missions or be unavailable for commitment in sufficient strength for response force operations. In this event, back-up or alternative response forces may be formed from base CSS units; engineer, chemical, or transiting combat units; and elements of the reserve (or host nation assets, if available). The rear CP will coordinate with the division G3 prior to committing other than MPs to response force missions. Under certain circumstances, committing the TCF may be preferable. It avoids risking degradation or destruction of critical CS assets.
Planning and Coordination. Execution of response force operations requires extensive planning and coordination prior to its commitment against an enemy. Success depends on the response force knowing and properly using terrain to gain advantage over the enemy. It also depends on massing sufficient combat power to destroy the enemy.
Whenever possible, response forces should be designated for specific bases or base clusters instead of one response force for the entire DRA. This reduces reaction time for the response force, and facilitates coordination between the response force commander and base or base cluster commanders. With fewer units, the response force can concentrate its preparation in a smaller geographic area.
In addition to knowing the location of bases in his AO, the response force commander must know which bases are most critical and most vulnerable. The response force commander should have the following information available for each base and base cluster in his AO:
- Defensive capability.
- Base defense status.
- Location of any obstacles near the base.
- Location and direction of the of crew-served weapons.
- Signal for final protective fires.
- Location of target reference points (TRPs) and preplanned fires.
- Method of contacting the BDOC or BCOC, including call signs and frequencies.
- Location of OPs and patrols, if employed.
Additionally, the response force commander must be able to mass supporting fires and facilitate TCF operations, if committed. Therefore, he must know the call signs and frequencies for supporting artillery, Army aviation units, the TCF, and the rear CP. He must also know the approved DRA fire support target list.
Response Force Operations. The purpose of response force operations is to hasten a base's ability to return to mission accomplishment as quickly as possible. This avoids devoting sustainment resources to self-defense or limited tactical operations. Response forces must commit rapidly to force an enemy to disengage from an attack before he causes significant damage to a base or bases. Once the enemy has abandoned his attack, the response force should fix and destroy him with fire support or in close combat.
Ideally, response forces will engage identified enemy elements through reconnaissance, surveillance, and counterreconnaissance actions before they attack bases. If response forces cannot mass sufficient combat power to destroy or deter an enemy, they should delay and disrupt him using fire support until additional response forces or a TCF is available.
When the response force is committed, the response force commander normally has OPCON of an AO. The base cluster commander and rear CP should develop on-order graphics to implement when a response force or TCF is committed. Base commanders support the efforts of the response force by lifting or shifting base defense fires to support the response force's maneuver. If a TCF is subsequently committed, the TCF commander will have OPCON of all bases and response forces within the TCF's designated AO.
Response forces are only effective if they can react swiftly. They must be familiar with the locations and dispositions of bases in the threatened area. Military police squads are typically assigned AOs that include bases. These units are responsible for executing MP missions within their assigned areas. This includes coordinating base defense response force operations with the bases in their AOs. Military police platoon leaders and company commanders normally coordinate with BCOCs to ensure unity of effort. When threats materialize, the rear CP conducts an assessment and, if appropriate, commits additional response force assets. If the threat exceeds the capability of response forces, a TCF may be committed. Response forces maintain contact with threatening forces and render spot reports to the rear CP and TCF commander until the TCF arrives to engage the threat.
Tactical Combat Force
The primary mission of a TCF is to defeat those enemy forces in the DRA that exceed the capability of response forces. To counter the wide variety of possible threats to the rear area, a TCF must be flexible, capable of either day or night operations, and able to obtain an advantage in mobility. It does this either by positioning or speed of movement.
The division TCF is normally a task-organized combined arms force comprising ground or air maneuver units, FSEs, and a headquarters capable of planning and coordinating tactical operations (however the TCF is designed based on METT-T). Light infantry, augmented with attack and assault helicopters, may conduct TCF operations against similarly equipped enemy forces. Light infantry must be augmented with armor and attack helicopters if committed against armored forces. If drawn from the aviation brigade, the TCF should be an attack helicopter battalion (AHB).
The DRA IPB and METT-T analysis help determine the size and composition of the TCF. Under the division commander's guidance, the G3 designates or dedicates one or more forces as TCFs to provide flexible responses to competing needs. A TCF may be designated with an on-order mission or task-organized under the rear command. It should be organized under the rear CP when the commander determines the threat to his rear area is sufficient to justify the employment of combat forces of battalion size or larger.
A designated TCF is not committed to rear operations. It has a "be prepared" mission to respond to threats. Once committed to rear operations, a designated TCF is OPCON to the rear operations commander until the enemy is defeated. It is then released to parent unit control.
Planning and Coordination. The rear CP plans, coordinates, and controls TCF operations. The DRA defense plan incorporates base and base cluster self-defense measures, response force operations, and TCF operations. The rear CP provides copies of the DRA defense plan, including fire support and obstacle plans, to the TCF. The TCF coordinates possible response plans with the rear CP, response force commanders, and base and base cluster commanders. The TCF positions liaison officers with the rear CP to help with contingency planning and employment of the TCF.
Operations. The rear CP is the headquarters for the TCF once committed. When the rear CP has task-organized TCFs, it positions them in assembly areas based on requirements of METT-T.
The rear CP develops security plans to deal with rear area threats, and coordinates these plans among bases and base clusters, response forces, the TCF, and FSEs. It also supervises and controls security operations in the DRA. When a large enemy force is detected moving to or in the rear, the rear operations commander requests that the G3 place the TCF under his OPCON.
If the TCF is a dedicated force, the rear CP notifies the TCF commander of the nature, location, and perceived enemy intentions and directs the TCF to close with and destroy the enemy. The rear operations cell designates an AO for the TCF. All base defense and response forces within the AO are OPCON to the TCF commander, ensuring unity of command.
When a threat in the DRA exceeds the division's capability to defeat it, the division must request assistance from corps. The corps TCF, or a portion of the corps TCF, can be either OPCON to the division or remain under corps control, based on tactical needs. The corps TCF reverts to parent unit control on mission completion, and response forces resume normal security operations.
Area Damage Control
Area damage control consists of measures taken before, during, and after hostile action or natural disasters to reduce the probability of damage and minimize its effects. Area damage control within the rear area affects all rear operations. The division rear operations commander is responsible for area damage control within the DRA.
The area damage control process includes continuous planning and action to minimize damage and a systematic approach to resolving the impact of damage on operations. Damage control teams must accurately assess damage to determine its extent and impact on operations. Alternatives and priorities must be set for repairs to damaged facilities or materiel. Damage control plans consider rescue, firefighting, life saving, and communication.
Continual area damage control planning, including specific responsibilities and the identification of available resources, ensures continuity of rear operations. Every echelon conducts area damage control planning.
Base commanders identify available resources within their bases and assess their capability to conduct area damage control operations. The continual upgrading of base defenses includes measures to reduce the effects of damages sustained. Detailed area damage control planning is an important part of the base defense plan.
Each BCOC compiles area damage control capabilities from each subordinate base and develops a comprehensive damage control plan which it forwards to the rear CP. The base cluster plan identifies available resources within each base to direct assistance from one base to another as required.
The rear CP reviews each base cluster area damage control capability. It maintains a status of the damage control posture of each independent base and base cluster. The rear CP coordinates directly with MP, engineers, chemical, and medical treatment facilities to ensure compatibility with subordinate plans. The rear CP ensures each base's capabilities are clear and that all available resources have been identified, including host nation assets.
Planning Considerations
Military Police. Military police provide local support, including battlefield circulation control and area security. They notify the rear CP of blocked LOCs and divert traffic as necessary to ensure maintenance of forward support. They ensure evacuation routes do not become cluttered. When possible, host nation assets conduct crowd control during area damage control operations to free up limited MP support.
Engineers. Engineer support includes constructing fortifications and obstacles which reduce the impact of damages. Engineers also clear debris and rubble, to include MSR maintenance. Commanders should exercise caution in committing engineer assets to every incident. Engineers fulfill critical mobility, survivability, and countermobility missions. Division light engineers normally require external support from nondivisional engineers to perform area damage control missions.
Medical Units. Medical units accept casualties from units near their locations. All units must know the exact location of medical facilities nearest to them so that injured personnel can receive prompt treatment.
G5 or Civil Affairs. G5 or civil affairs elements identify host nation support, especially engineer assets, to augment resources. They coordinate civilian involvement with area damage control operations.
Chemical. Chemical units support area damage control operations through decontamination of personnel, equipment, supplies, key sites, and LOCs. Survey teams from the division chemical company assist units on a priority basis as directed by the rear CP.
Explosive Ordnance Disposal. The presence of unexploded ordnance and the possibility of detonation can pose a threat to operations. Explosive ordnance disposal (EOD) operations deal with unexploded ordnance.
Explosive ordnance reconnaissance agents in each unit assist in reducing hazards and reporting unexploded ordnance to the rear CP. The agents should be trained by EOD units to assist local commanders. They should include all military police and at least two soldiers from each company-sized unit.
Aviation. Aviation assets may assist in transporting casualties. Utility helicopters can provide emergency resupply, communication relay, and aerial assessment of damages.
Operations
Once an event causes or has caused damage, specialized personnel must simultaneously--
- Treat and evacuate casualties.
- Control damage.
- Identify and mark unexploded ordnance.
- Secure critical assets.
- Reestablish operations.
- Conduct a damage assessment.
- Report assessment of damages and status of operations.
The rear CP evaluates the information received and, if necessary, directs further assessment of damage by aerial observation, by MP patrol, or by either its own experts or those from the DISCOM.
In developing alternatives, the rear CP or DISCOM must determine the following:
- What has been damaged (facilities, supplies, and equipment)?
- How extensive is the damage?
- Will engineer assets be needed for repairs?
- Can the unit continue its mission without major repairs?
- Can the unit relocate and still perform its mission?
- Are other facilities, supplies, and equipment available in sufficient quantity to accomplish the mission?
The rear operations cell develops damage assessments and alternatives for repair or support. Based on its evaluation, the rear operations cell develops recommendations for the rear operations commander. He then directs actions to repair damages or pursue alternatives. Other important considerations include:
- Are remaining supplies, facilities, equipment, or personnel now critical to operations? Is additional security needed?
- What is the impact on future operations, considering the losses sustained?
- Is it necessary to reposition units to bolster sustainment?
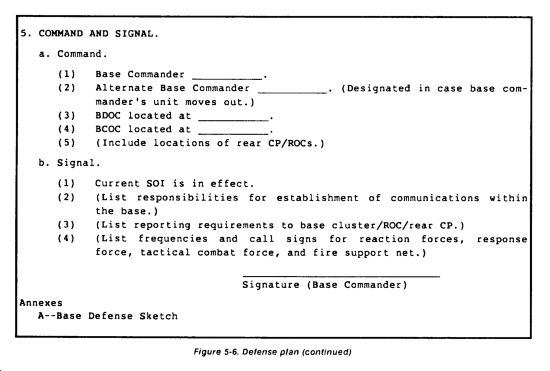
Division Rear Area Defense Plan
A sample base, base cluster, or rear area defense plan is at Figure 5-6. It contains the minimum essential elements which should be found in any defense plan. Division SOPs should expand on them as needed.
Division deep operations comprise tactical activities directed against enemy forces not in contact. The division commander must envision the battlefield in terms of depth and time. He does so by reviewing the corps commander's intent and concept of how the corps battle will be fought. The corps commander envisions a series of smaller battles where subordinate divisions defeat and destroy the enemy in piecemeal operations. The commander articulates this vision as an implicit contract with division commanders as to what must be done, a concept of time or events, and how the corps creates favorable battlefield conditions for divisions to defeat enemy forces. He sees a series of division battles by time or event windows, locations in depth, combat power ratios, and specific desired results.
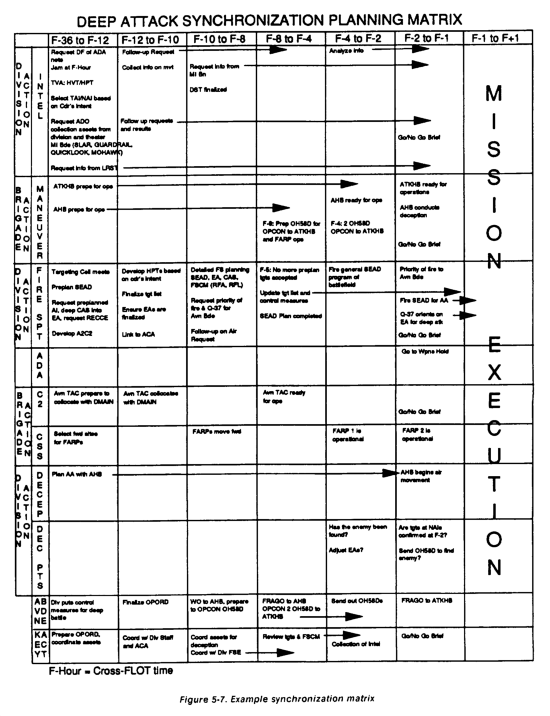
Deep operations are used to influence the enemy so that divisions can accomplish the piecemeal destruction of enemy forces. The division commander also envisions the battlefield in terms of depth and time to develop a series of piecemeal engagements for his brigades. He develops a deep operations plan to create favorable conditions. Deep operations will normally impact enclose operations. (See synchronization matrix, Figure 5-7.) To ensure an effective system, deep operations are planned, controlled, and synchronized by the commander and the G3. The G3 is the primary staff officer responsible for deep operations. Fire support and intelligence BOS are tasked for targeting and execution.
Destruction of enemy forces in the deep operation is not always the intent and is difficult to achieve because it requires massive resources. Lethality of improved conventional munitions in an air superiority environment, however, may make destruction possible. Limiting enemy movements is an asset-intensive goal requiring significant reinforced terrain obstacles. Therefore, disruption is probably the realistic goal.
Disruption reduces the enemy's correlation of forces by desynchronizing or delaying his subordinate elements. The division combat commander's intention is to create engagements where friendly brigade power ratios allow brigades to defeat enemy forces.
The commander cannot just target a unit for destruction or specify an unreasonable delay period. Deep operations include the cumulative effects of many different actions on the enemy. Tangible actions include attrition, destruction, and delay of combat formations that generally alter combat force ratios. Intangible actions alter combat power multipliers by degrading or disrupting the enemy's cohesion, synchronization, massing, sustainment, or control. Deep operations, such as AI, deception, psychological operations (PSYOP), EW, direct action special force operations, counterfire, and complementary SEAD, and maneuver within the close battle are division planned and directed. They produce effects at specific points of attack, counterattack, or defense.
Deep operations are not continuous or sustained at constant levels of effort. They are developed to achieve specific results, based on the enemy, situation, and available assets. Limited assets are scheduled to support deep (and close) operations execution--not dedicated to one specific operation or unit. Deep fires may shift to mass fires against an enemy unit in the close battle and then back to deep targets until massed fire is again needed in the close operation.
The outcome of the close operation should never totally depend on deep operation results. The effect of deep operations on combat power ratios is a key factor in determining when and where to accept or initiate decisive close battle. Favorable conditions must be achieved before risking potential critical losses in decisive close battle.
The commander develops his deep operations concept when war-gaming COAs. He determines responsibilities and control for those operations and establishes phase lines and specific targets by type. Successive phase lines provide on-order lines defining deep and close operations areas for the division and corps. Either echelon may reserve specific targets or missions as deep operations. Examples are counterfire against specific artillery echelons or mission-capable units, or counterfire into one specific area, reserve units, and division C2 facilities. Specific targets reserved by type may also be attacked anywhere on the battlefield when reserved. However, the target must be identified by means other than map reconnaissance. The decision to fire on templated locations is made by the commander during war gaming. The criteria to fire targets is based on battlefield need and urgency in terms of time. Risk is reduced when the target is under surveillance by human intelligence (HUMINT) or SIGINT sources.
Corps deep operations normally interdict the enemy operational reserves (regiment- or division-sized force), degrade C2 facilities, destroy sustainment facilities and distribution assets, and destroy army rocket and tube artillery assets. The division normally attacks uncommitted forces, disrupts movement of reserves or counterattacks, destroys enemy division C2 facilities and ADA systems, and conducts counterfire against direct and general support artillery opposing brigades.
Maneuver and deception are used at each echelon to create overwhelming strength at a point and delay enemy repositioning of uncommitted forces. The integration of maneuver, deception, and other deep operations to the close operation is required for success.
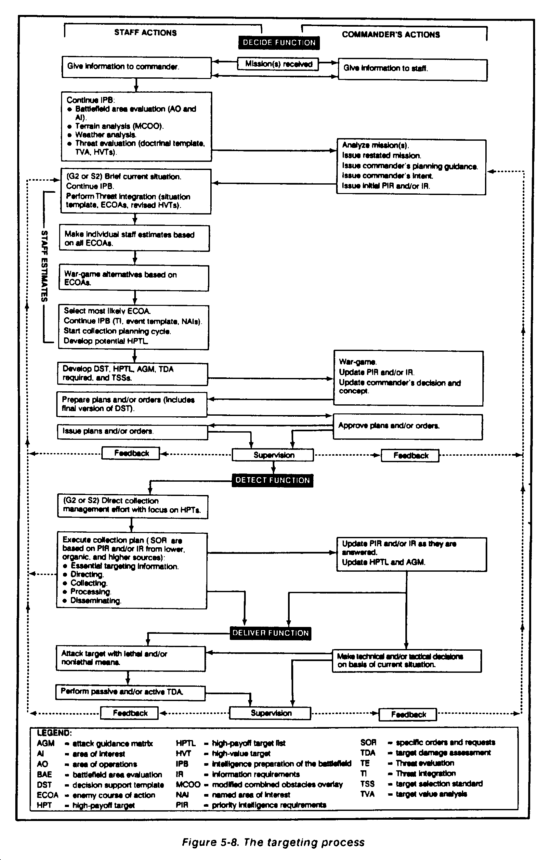
Deep operations are planned using the estimate of the situation as detailed in FM 101-5. The estimate of the situation process also must incorporate the targeting methodology described in this chapter. (Also see Figure 5-8 for the targeting process.)
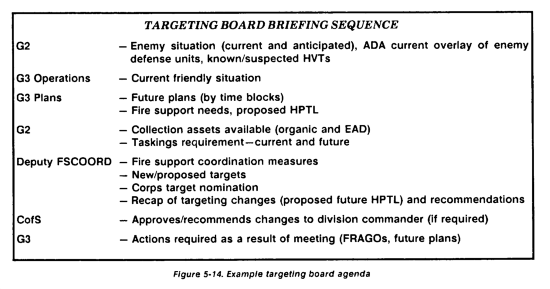
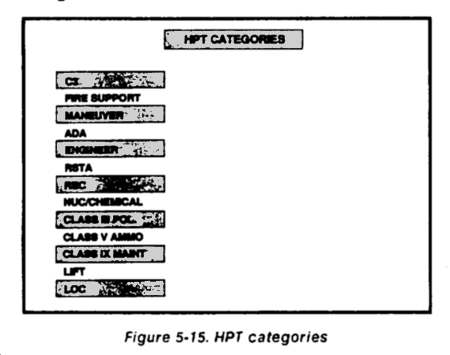
Desired damages (destroy, suppress, or neutralize) are associated with enemy units to achieve desired results. This targeting guidance must be used to evaluate targets according to attack criteria. Direct attacks attrit enemy combat forces. Indirect attacks attrit assets, facilities, or systems which support enemy forces. This evaluation begins with the development of the high payoff target list (HPTL). The targeting team matches systems to the detection means and target effects.
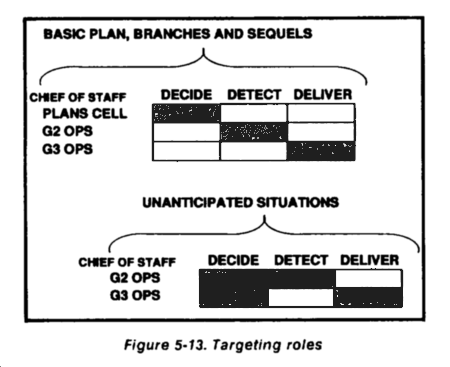
The targeting team comprises the CofS, G3 and G2 representatives, DFSCOORD, FAIO, FLO, electronic warfare officer (EWO), and G3 air. The targeting team is a full-time organization chaired by the G3. The commander is present for planning and war gaming. The others are readily available during the operation. The G3, G2, and DFSCOORD are the primary full-time members for planning, war gaming, and execution. Although they may not be collocated, they function as a full-time decide, detect, and deliver targeting team. They develop the decide phase and control the execution of the detect and deliver phases by subordinate and supporting units or HQ.
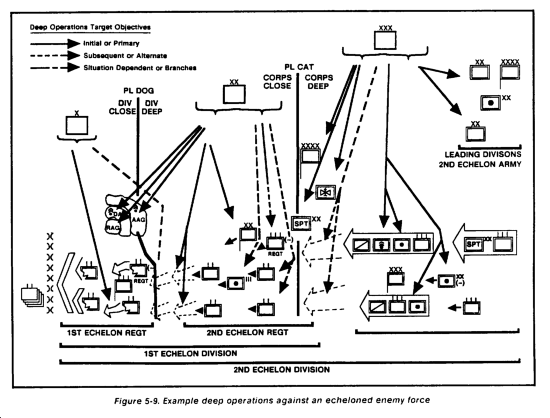
The G3, G2, and DFSCOORD continuously monitor the current battle, deep operations battle damage assessment results, intelligence assessments, and sequel mission requirements. The G3 issues FRAGOs (approved by the commander), to change decide guidance or provide new guidance when required. The G2 is the principal controller for the detect phase and for its execution. The DFSCOORD is the principal controller and coordinator for the technical planning and tasking of the deliver plan and for its execution. (See Figure 5-9.)
Reconnaissance is an essential and continuous operation which the division conducts to collect information and gain and maintain contact with the enemy. The G2 processes information into intelligence and provides combat information to the commander.
Reconnaissance should not be confused with security operations, nor should a unit have both reconnaissance and security missions at the same time. The objective of reconnaissance is to find (and acquire information about) the enemy. Security operations protect the friendly force from enemy actions and deny him information.
The G2 has staff responsibility for reconnaissance. He assigns reconnaissance tasks to subordinate units through the collection plan. He coordinates with the G3 to allocate resources and assign specific reconnaissance missions to subordinate commanders when required.
Reconnaissance of some type should always precede a commitment of forces. Time available will determine the extent of reconnaissance. Failure to conduct a thorough reconnaissance may result in loss of initiative and unacceptable losses in personnel and equipment.
Reconnaissance enables the G2 to confirm or deny enemy templates and the enemy's most probable COAs (developed during the IPB process). Reconnaissance by ground or air maneuver elements can confirm information developed by IEW assets. It can provide detail and verification that IEW assets cannot. For example, direction-finding assets may locate enemy CP transmitters. Ground or air reconnaissance elements may physically locate the CP. Similarly, reconnaissance elements in front of the covering force can assist a covering force commander to orient on specific avenues of approach.
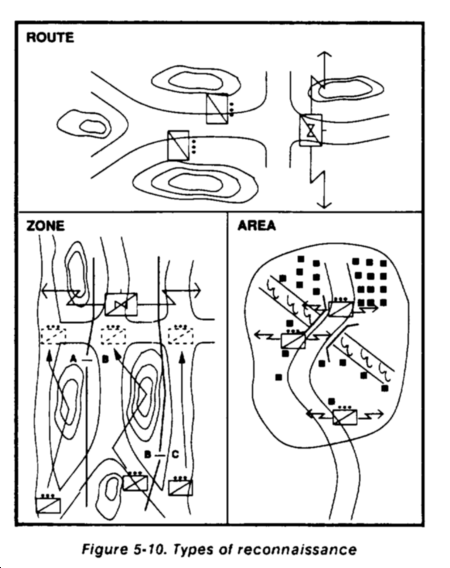
The three types of reconnaissance (See Figure 5-10) are route, area, and zone. Route reconnaissance is conducted to obtain detailed information about a specified route or routes and surrounding terrain the enemy could use to influence movement. Area reconnaissance obtains information about a specific area such as a town or a proposed assembly area. Zone reconnaissance is a detailed, thorough, time-consuming reconnaissance of all important terrain within specified boundaries. Methods of reconnaissance include--
- Patrols.
- Reconnaissance by fire.
- Armed reconnaissance.
Reconnaissance may be aerial, ground-based, or a combination of both. Each method has its purpose and techniques. Armed reconnaissance can locate and attack targets of opportunity in its prescribed area or route. Reconnaissance by fire causes an enemy to disclose his position by movement or return fire. A reconnaissance patrol gains information about the enemy without his knowledge.
Planning
The G2 plans the division reconnaissance effort using the collection plan, which fills gaps in combat intelligence. The G2 integrates division assets into the reconnaissance effort by developing intelligence acquisition tasks to support the collection plan. He considers availability and capability of units, IEW assets, air and ground maneuver capabilities, field artillery radars, and TACAIR reconnaissance.
The G2 prioritizes the reconnaissance effort using the commander's PIR and IR. He coordinates the reconnaissance effort through assignment of intelligence acquisition tasks to units through the intelligence annex to the division OPORD. During the execution of the division's mission, the G2 coordinates specific reconnaissance missions with the G3.
The G2 synchronizes the reconnaissance effort by sequencing reconnaissance tasks. He considers when information is required as well as the acquisition time required.
The G2 determines the reconnaissance required in the deep operation and tasks assets, or recommends their tasking to the G3. These will normally be SIGINT or IMINT sources. However, the G2 may recommend that the reconnaissance squadron or aviation brigade conduct a deep area reconnaissance.
The G2 may assign reconnaissance tasks to the security force's covering force, advance guard, or both. These reconnaissance tasks are accomplished as concurrent operations to the unit's security mission and may include route or area reconnaissance tasks.
In the close operation or MBA, the G2 may assign reconnaissance tasks to committed forces. These tasks are collateral to the unit's assigned mission. Tasks may include reconnaissance of defensive positions or lateral routes. The G2 may recommend that the G3 assign units to reconnaissance in force, reconnaissance by fire, or armed reconnaissance. These missions may refine intelligence collected by IEW sensors or complete more detailed reconnaissance. For example, the air troops of the reconnaissance squadron might report heavy ground fire along a route they were reconnoitering as part of an offensive covering force. The G2 may recommend an advance guard to conduct a reconnaissance in force of the suspect area.
The G2 may assign reconnaissance tasks in the reserve area to the reserve brigade, MPs, or engineers. These reconnaissance tasks may include route reconnaissance of counterattack routes or reconnaissance of likely pickup zones (PZs) or LZs.
In the division rear, the G2 may assign reconnaissance tasks to CS or CSS units. Tasks may include patrols of likely PZs or LZs, reconnaissance of reconstitution sites, or route reconnaissance to support the movement of another unit across the division rear.
The G2, in coordination with the G3, resources the reconnaissance effort. On the basis of intelligence gaps, the collection plan, assets available, and sequencing, the G2 recommends task organization of IEW assets to support the division reconnaissance effort and those of subordinate commands. When required, the G2 may recommend assigning reconnaissance missions to subordinate commands.
Reconnaissance tasks should be specific. Mission-type orders will not suffice. The G2 must be specific about where to look, what to look for, and what information is required. This assists the G2 and G3 in determining the resource allocation to subordinate commanders. It also provides specific tasks to subordinate commanders for their own mission planning.
The G2 must ensure that the plan does not spread available reconnaissance assets too thin. It is not wise to disperse reconnaissance elements across wide frontages to accomplish multiple tasks simultaneously. The capabilities of IEW assets and moving target locating radars should be part of the reconnaissance effort. These can focus the reconnaissance of ground or air maneuver elements.
Reconnaissance should include specialists such as engineers and chemical personnel. The division reconnaissance squadron and battalion scouts are not the only organizations that conduct reconnaissance.
The G2 should assign reporting schedules to the assets conducting the reconnaissance. This allows him to monitor the progress of the reconnaissance and redirect efforts as required.
Routine reports should pass through the division intelligence or operations and intelligence nets. Critical information should be submitted using the division command net. This combat information, although unevaluated, may have immediate tactical significance to the commander.
In offensive operations, the commander should base his plan for maneuver on the concept of "reconnaissance-pull." Reconnaissance determines which routes are suitable for maneuver, where the enemy is strong and weak, and where gaps exist. Thus, reconnaissance should pull the main body towards and along the path of least resistance. This facilitates the division's initiative and agility.
Reconnaissance-pull is also valid in defensive operations. Reconnaissance determines which routes the enemy is using, where the enemy is strong and weak, and where gaps exist. Thus, reconnaissance enhances agility by identifying opportunities and pulling the division along the path of least resistance to mass the division's combat power at the critical time and place.
Techniques
Reconnaissance missions inherently place units in harm's way. Stealth cannot be ensured and is at best circumstantial. Firepower, aggressive action, and deception are required for survival and mission accomplishment.
The division should expect the unit assigned a reconnaissance mission to do more than just find the enemy. Reconnaissance operations at the divisional level should develop the situation by--
- Penetrating or disrupting the enemy's security forces.
- Forcing the premature commitment of reserves.
- Forcing the early uncovering of artillery.
- Fighting through and uncovering enemy deception schemes.
Reconnaissance operations should develop the situation to the tactical depths of the opposing enemy formation. The reconnaissance squadron is the division's primary reconnaissance unit. Its use should prevent the decisive commitment of main force units. By locating the enemy, developing the situation, and discovering or creating weakness, the squadron should improve the division's ability to put decisive combat power at the right place at the right time.
The reconnaissance mission should also be closely integrated with the other division intelligence collection assets for a cohesive battle picture. When possible, the reconnaissance squadron should be tied into the LRSD and combat radio nets of the intelligence and electronic warfare support element (IEWSE).
The division conducts security operations to provide maneuver space and reaction time, and protect the main body. It incorporates security as part of the battlefield framework in planning all offensive or defensive operations.
The G3 develops and recommends the concept of operations. This includes assigning security responsibilities and missions to subordinate commanders, who then plan, prepare, and execute security operations. Every unit has a continuous security role.
Types of Operations
Security operations include screen, guard, cover, and counterreconnaissance operations. Screens maintain surveillance, conduct counterreconnaissance, provide early warning to the main body, and harass and impede the enemy through indirect fires. Guard missions include the functions of screen and protect the main body from ground observation and direct fire. Cover includes the functions of screen and guard operations but also develops the situation. Cover deceives, disorganizes, and destroys enemy forces.
Counterreconnaissance is inherent in all combat operations. It prevents the enemy from obtaining information about the division through visual observation or other detection means.
Planning Considerations
As the G3 and other staff members incorporate security requirements into the planning of division operations, they should consider--
- Adequate support to security forces.
- Ranges and capabilities of IEW, fire support, and communications systems.
- Time-distance relationships.
- Economy of force factors.
- Passage of lines.
- Formation of the main body.
The covering force, especially in offensive operations, operates well forward of the division main body. The G3 allocates resources to the covering force so that it functions as a tactically self-sufficient force.
Guard forces operate within supporting range of the main body. However, the G3 and other staff elements must consider relationships between the main body and the guard force.
The staff must consider the range and capabilities of combat and CS weapons and systems as it assigns security responsibilities and missions to subordinate commanders. While some cannon artillery may range to 30 kilometers with rocket-assisted projectile (RAP) ammunition, the amount of RAP ammunition and its capabilities are less than dual-purpose improved conventional munitions (DPICMs). Similarly, IEW assets may range to 30 kilometers; however, terrain, weather, and enemy ECCM actions may significantly reduce the range.
The staff should consider time-distance relationships when using screens or guards. Screens provide early warning to the main body. Planning must consider the time required for the main body to counter a threat and compute the distance the enemy could move during that time. This aids in determining location of the screen. If sufficient maneuver space is not available to accommodate this time-distance relationship, then the staff should consider employing a guard rather than a screen.
Planners should consider economy of force in assigning security responsibilities and missions. Fewer forces are required to screen a force than to guard it. Where possible, the plans element should consider employing screens as opposed to guards. The considerations of adequate support, time-distance, and the threat will affect this decision.
Planners should consider the requirements for passage of lines by security forces. An offensive covering force may be required to conduct a forward passage as it begins a movement to contact, or leads the division in an exploitation or pursuit. Similarly, a defensive covering force may execute a rearward passage into the MBA. Screens or guards may conduct a passage with main body forces. This consideration may assist the G3 in determining which headquarters provides and controls the security force. A brigade passing through an advance guard which it controls is easier to coordinate than one passing through a division-controlled advance guard.
The staff must also consider the division formation. Each formation has its own strengths, weaknesses, and planning considerations for security.
Offensive Covering Forces
Cover missions differ between offensive and defensive operations. A division offensive covering force may be a brigade reconnaissance in force. The division commander establishes objectives to support his scheme of maneuver based on the IPB and available intelligence about the enemy.
A covering force orients on objectives established by the G3 and division commander. These objectives may be in the enemy's security zone with a counterreconnaissance orientation to strip the enemy's ability to determine in what force, and where, the division is attacking. This requires the covering force to use a two-team method. One team locates the enemy reconnaissance in the security zone and another team destroys it.
Locating enemy reconnaissance normally requires a mix of ground, aerial, and electronic reconnaissance to confirm the situational templating of enemy security zone forces. Ground forces may include battalion scouts, COLTs, and LRS teams. Their mission is to locate enemy forces so that other maneuver and fire support assets may attack them. During this phase of the covering force operation, enemy reconnaissance is a high payoff target.
Another objective of a covering force may be to determine routes through enemy defensive belts. The covering force uncovers enemy strengths, weaknesses, gaps, locations, and dispositions and serves as a reconnaissance-pull for the main body. It may conduct limited objective attacks or probes across a wide front.
If the covering force successfully negotiates the first defensive belt, it continues to the second belt. If it is not successful, it establishes a hasty defense and waits to pass the main body. It maintains contact with the enemy. It coordinates the passage of the main body with the TAC CP.
If the covering force conducts a movement to contact against a moving enemy, it still operates as a reconnaissance in force. It conducts a series of limited objective attacks. It uses the objectives to orient its movement. The battalions of the covering force seize each objective and continue until contact is established. Reconnaissance and counterreconnaissance continue to be paramount. Once it establishes contact, the covering force conducts a hasty attack or hasty defense to pass the main body.
The G2 must consider IEW support for the offensive covering force. He must allow for redundancy in IEW systems to support its rapid forward displacement. He must disseminate combat information and intelligence to the covering force. The IEWSE provided to the maneuver brigade by the MI battalion assists in this function.
The G2 must provide a full complement of multidisciplined MI resources to the covering force. To ensure effective coordination and control, they will normally be task-organized into an MI company team. Ground-based systems must be able to rapidly displace. They should operate in pairs to leapfrog between positions and maintain continuous coverage.
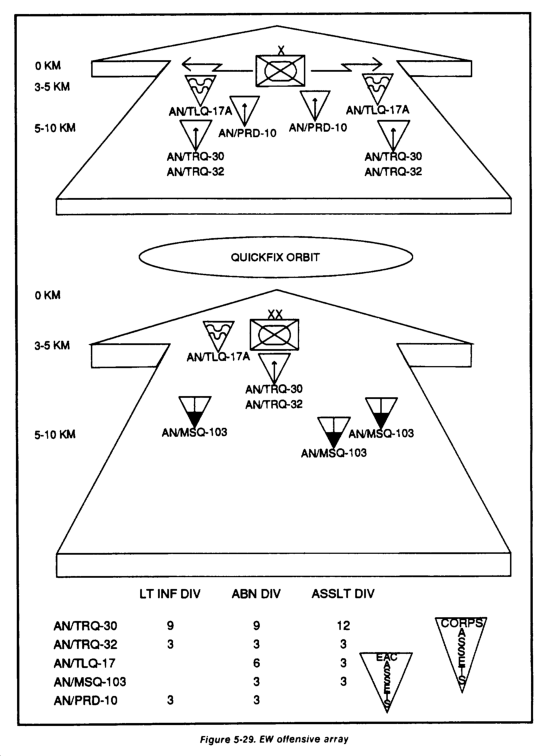
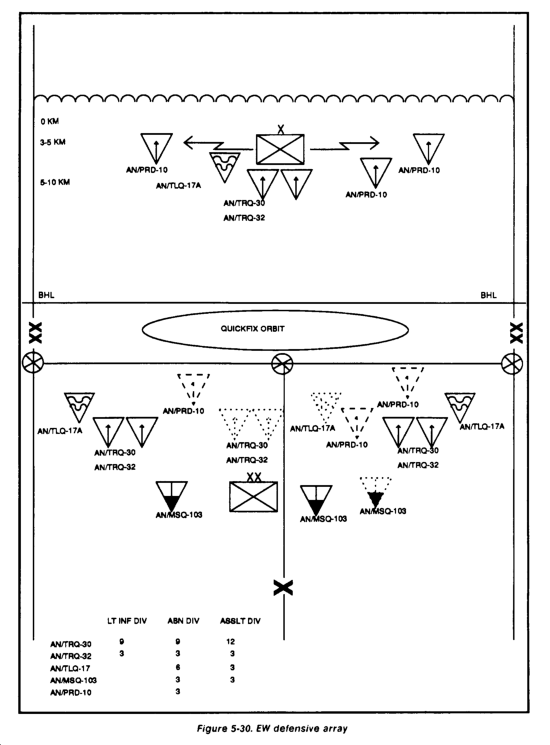
Aerial intelligence assets, such as Quickfix, should habitually support the offensive covering force. They can provide continuous long-range coverage over wide areas forward and to the flanks of the covering force. They may also cue other systems to confirm or deny information provided by other agencies, and to provide coverage while ground-based systems displace.
Aerial reconnaissance may include tactical air reconnaissance on the use of remotely piloted vehicles (RPVs) or aerial scouts. Voice intercept and Quickfix (when not jamming) may be used for communications intercept.
Signal intercept systems identify and collect technical data on key enemy command, control, and communications target acquisition, and fire control systems. They monitor nets for exploitable information and pass target data to maneuver units, the FSE, and jammers.
Ground support radars provide early warning, information on enemy movement, and targeting information. They provide continuous support through leapfrog movements between positions on dominant terrain.
The division may insert LRS teams along routes to observe enemy activities. Interrogators can move with and support the covering force through interrogation of noncombatants until EPWs are taken. Intelligence teams conduct hasty screening and interrogations for information of immediate tactical value. This includes information about enemy forces, obstacles, the terrain, and enemy plans and intentions.
Fire support planning must include both supporting and deceptive fires. If sufficient artillery is available, each battalion in the covering force should have a DS battalion.
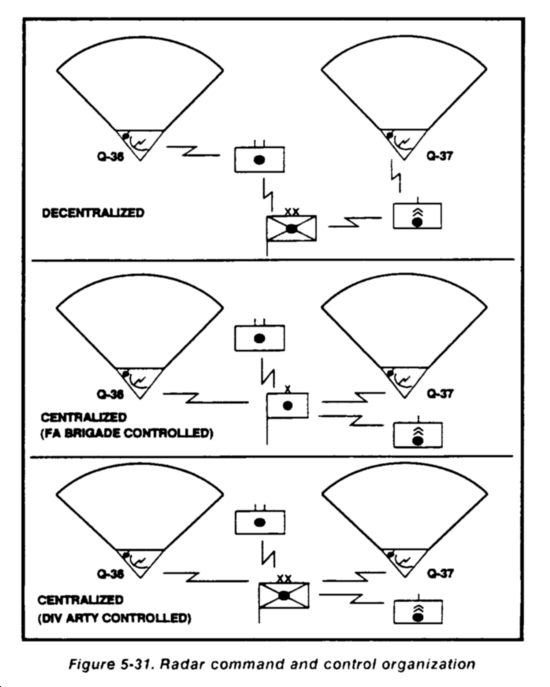
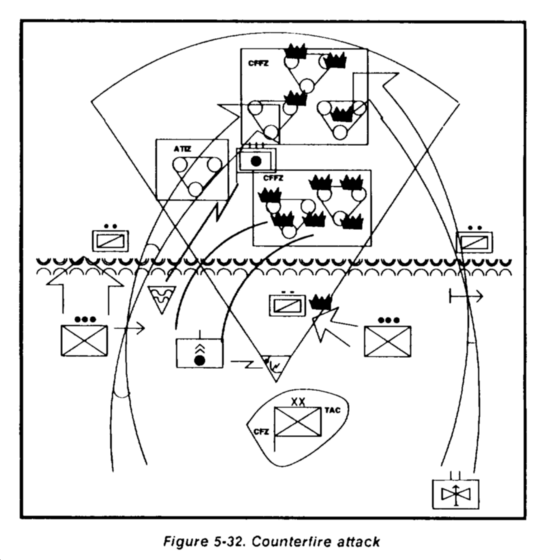
Counterfire radars should be part of artillery task organization. The covering force should establish critical friendly radar zones around the main effort to expedite reactive counterfire. Call for fire zones (CFFZs) should be established on suspected enemy firing locations.
Fire support coordination measures should be permissive and on order. They should be in conjunction with phase lines and well ahead of the covering force. Fire plans should be simple, but as detailed as possible. The FSE should plan groups and series of targets to support the rapidly moving maneuver forces and plan FASCAM on flank avenues of approach.
The FSE should include jamming, especially against the enemy's reconnaissance and fire support (FS) nets in the FS plan. Quickfix provides a relatively deep capability to jam enemy C2 nets.
Close air support should be integrated into the FS plan, and when possible, preplanned against the enemy. Even when the enemy is moving, the G2, G3, and FSE can project when they expect to make contact with the enemy. Wargaming this event may provide an approximate location and time for preplanning CAS.
The G3 task organizes AD assets, based on the ADA battalion commander's recommendation, to the covering force from the AD battalion. These may be a mixture of Vulcan and Stinger systems. Stinger teams are positioned on dominant terrain and along likely air avenues. Because of their short range and need to match the momentum of the covering force, AD assets should be part of the subordinate units of the covering force. These teams can also be reconnaissance assets. Each Stinger team has a vehicle, radio, and binoculars. Locating them with IEW assets assists in local protection and air defense for the IEW assets, and simplifies terrain management and movement control.
The covering force AD commander must coordinate with the AD battalion, the covering force signal officer, and the S3 to provide the covering force AD systems the capability to monitor the division AD early warning net. The covering force engineer plans mobility and countermobility support.
Engineers with the covering force identify routes for forward movement and lateral routes to provide the commander flexibility as he develops the situation. In coordination with the FSE, the engineer plans FASCAM on avenues of approach into the flanks of the covering force. The engineers should be prepared for earth moving, rapid obstacle breaching, and assault bridging (if required).
Defensive Covering Forces
In the defense, the corps, not the division, normally provides the covering force. This allows the corps to control the covering force battle and shape the battlefield rather than allowing each division to fight an independent battle. If required, however, the division's covering force operates well forward of the main body to develop the situation and deceive, disorganize, and destroy enemy forces. The covering force mobility is normally equal to or greater than that of the opposing force.
The defensive covering force mission may be to delay forward of a given phase line or time or event. For example, the division commander may tell the covering force commander to delay forward of a phase line for 24 hours or until the covering force is 70 percent combat-effective.
The division must plan for the rearward passage of the covering force by establishing passage points with the MBA brigades, and the battle hand-over line. A phase line depicts the area the covering force is to delay in front. It should be forward of the battle hand-over line. This gives the covering force commander the depth to complete the delay and yet retain enough maneuver space to conduct an orderly passage. This also aids in the covering force's staggered withdrawal. Maneuver forces in the covering force should execute detailed counterreconnaissance plans. These incorporate measures discussed later in this section.
Intelligence and EW assets supporting the defensive covering force are much the same as in the offensive covering force. In the defense, IEW resources leapfrog to the rear, withdrawing in a way that facilitates their use in the MBA.
Fire support assets are organized and function in much the same manner. Fire support plans are more detailed and an integral part of the scheme of defense. Artillery and other fire support must be planned to mass at critical times and places. Observers watch obstacles and plan fires to cover them. Fire support measures are permissive and close enough to the covering force to facilitate engaging the enemy. This is especially critical as the covering force withdraws into the range of artillery in the MBA.
Close air support is planned for EAs. The LRS teams observe and monitor decision points for initiation of these attacks. Engineers with the covering force conduct countermobility and survivability tasks as their first priority.
Air defense assets provide coverage on likely air avenues of approach. This is critical as the covering force tends to mass during the withdrawal. Coverage of passage points and lanes into the MBA must be coordinated with the MBA air defense forces.
Guard Missions
The advance guard and the offensive covering force differ in their orientation during movement and in their zone of operations. The covering force focuses on the enemy, maneuvers towards him, and covers the entire division zone. The advance guard orients on the movement of the main body. It provides security along specific routes of movement of the main body.
The advance guard operates within supporting range of the main body and protects it from ground observation and direct fire. The division may provide and control the advance guard or assign a maneuver brigade this responsibility.
The G3 operations in the TAC CP monitors the advance guard's operations if it is division-controlled. The G3 monitors its advance and operations as with any other committed force. He integrates the actions of the advance guard with those of the covering force and main body.
The advance guard conducts route reconnaissance in front of the main body. The TAC CP coordinates its movement with the main body to ensure that it remains within supporting range. Phase lines control this movement and allow the advance guard to speed up or slow down, depending on the status of the main body. Generally, reconnaissance elements of the advance guard should remain within range of supporting artillery.
Artillery moves to provide support to the advance guard (as well as flank and rear guards) and to rapidly occupy positions when the main body must deploy. This gets the artillery off-road networks to allow movement of maneuver forces. Priority of fires is to the advance guard during movement. This facilitates conduct of a hasty attack or hasty defense. The FSE at the TAC CP coordinates this for the advance guard FSE when the advance guard is under division control.
The advance guard FSE plans fire support much like the covering force's, emphasizing simple fire plans with as much detail as possible. Groups, series, and smoke missions are planned to support the maneuver commander's scheme of maneuver. The FSE coordinates these through the TAC CP FSE.
The TAC CP coordinates IEW support for the division-controlled advance guard. The G2 operations at the TAC CP disseminates combat information and intelligence from the covering force and main CP to the advance guard.
Similarly, the G3 at the TAC CP coordinates engineer and AD support for the division-controlled advance guard. He coordinates with the AD battalion and the engineer battalion to provide required support.
Engineer elements in the main body respond to the advance guard requirements. Because of their short range, air defense assets move with the advance guard, leapfrogging with the maneuver force as it moves. When the lead brigade or brigades provide the advance guard, the maneuver brigade coordinates, integrates, and supports the advance guard.
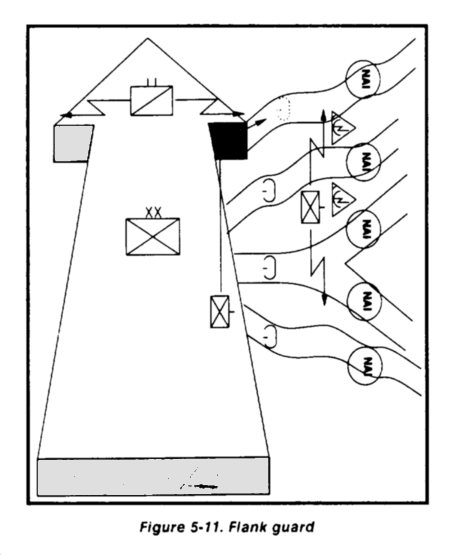
Flank Guard
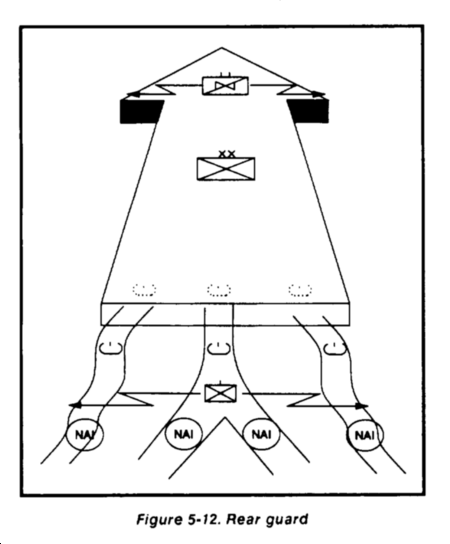
The maneuver brigades of the main body normally provide and control flank guards. This mission entails the conduct of defensive operations to the flanks to prevent ground observation and direct fire against the main body.
The flank guard (see Figure 5-11) establishes defensive positions to the flanks for stationary or moving forces. To secure the moving force, the flank guard leapfrogs forces to successive positions along the flank of the main body. These focus on battalion mobility corridors. This allows the battalion conducting the flank guard to occupy two positions while one company team leapfrogs to a forward position. The antitank (AT) company of the airborne or air assault division may act as a counterattack force. The scout platoon may conduct a screen to the flank or to the front of the task force. This requires close coordination of engineer assets and fire planning by the flank guard.
Similarly, the brigade S2 closely coordinates IEW support for the flank guard. The flank guard must plan R&S in detail. Intelligence and EW assets such as GSRs must be part of this plan for early warning, monitoring of threats, and economy of force. The flank guard S2 must establish NAIs and TAIs. Counter-reconnaissance actions assist in providing security to the flank guard and ultimately the main body. They may also provide the first indication a threat is developing to the flank.
The maneuver brigade controlling the flank guard should plan for its reinforcement or withdrawal. To reinforce the flank guard, it becomes the fixing force while other brigade elements engage the enemy with fire and maneuver. To withdraw the guard, the brigade establishes a hasty defense and passage points for the flank guard to withdraw into the brigade positions.
Rear Guard
The rear guard protects the main body from the rear during retrograde operations or from bypassed units during exploitation and pursuit. (See Figure 5-12.) The rear guard must orient on the movement of the main body to prevent gaps from developing and being cut off. Main body forces must position supporting elements toward the rear of the main body to support the rear guard. This is particularly true of artillery. During retrograde operations, the first priority of CAS should be to the rear guard.
The rear guard commander prepares to conduct a series of delays from subsequent battle positions. He must not decisively engage unless the controlling commander approves. The main body may not be in a position to reinforce the rear guard.
During offensive or retrograde operations, the rear guard occupies battle positions. It leapfrogs to new positions towards the main body. The rear guard elements closest to the enemy should not be outside supporting range of the main body. This requires close coordination between the rear guard and its controlling headquarters. The rear guard commander must closely monitor his subordinate units to allow displacing forces to occupy new positions before in-place units vacate theirs.
The rear maneuver brigade or TAC CP controls the rear guard. During the exploitation and pursuit, the rear maneuver brigade controls the rear guard. During retrograde operations, the TAC CP controls the rear guard.
Main body forces should identify and assist in preparing battle positions for the rear guard force. Engineers should prepare survivability positions. They also conduct countermobility operations to delay, disorganize, and limit the enemy force. In retrograde operations, they coordinate obstacle free zones and lanes through obstacle belts with the rear guard. Artillery, helicopter, and AF-delivered mines can rapidly close these lanes and reinforce breached obstacles. In the exploitation and pursuit, FASCAM should assist the rear guard to delay the enemy and to block approaches from the rear. Fires should be planned to assist the rear guard to disengage and move to subsequent positions.
Screen
Screens provide early warning and harass and impede the enemy with indirect fires. The division may use screens as an economy of force security mission. When sufficient maneuver space exists, the division should position the screen far enough away from the main body to allow sufficient time to identify and counter the threat. This distance will probably be outside the range of supporting artillery. For this reason, CAS and attack helicopters should support the screen.
The screen commander combines reconnaissance, surveillance, and counterreconnaissance techniques to identify threats to the main body. He uses the IPB process to identify enemy avenues of approach and to establish NAIs for his forces to observe. As he identifies a threat, the screen commander reports to the TAC CP and uses counterreconnaissance within his capability to impede the enemy. Concurrently, he uses FS assets against the threat. This may require the screen to leave stay-behind forces to direct the attack. Scouts with attack helicopters may also direct the attack. As the screen withdraws into range, it employs main body artillery.
Counterreconnaissance
Counterreconnaissance is the sum of actions taken by all division units to counter enemy reconnaissance efforts throughout the division's AO. A detailed analysis of the enemy's reconnaissance capabilities during the IPB is crucial to understanding the nature, composition, and timing of the enemy's reconnaissance elements. The division will face different threats. For example, if the division is defending in the MBA behind a covering force, it may face reconnaissance elements not destroyed by the covering force as well as reconnaissance elements of follow-on echelons.
The G2 develops doctrinal and situational templates for reconnaissance and main body elements during the IPB process. He identifies likely avenues of approach and develops NAIs to focus the collection and monitoring assets of the division.
The division G3 uses this information to determine required counterreconnaissance actions and to task units to execute them. The G3 fixes responsibilities and provides resources to units to locate, fix, and destroy enemy reconnaissance forces. Counterreconnaissance requires a two-team approach--one to conduct surveillance and acquire enemy reconnaissance elements, another to close with and destroy them.
Counterreconnaissance consists of active and passive measures. Active measures detect, fix, and destroy enemy reconnaissance elements. Passive measures conceal friendly units and capabilities and deceive and confuse the enemy. The G3 integrates both types into the division's counterreconnaissance plan.
All subordinate units develop and coordinate their counterreconnaissance actions. They fix responsibility for patrols, ambush requirements, specific OP locations, GSR sites, and observing of NAIs. The G3 reviews subordinate unit counterreconnaissance actions and issues additional taskings to fill any gaps.
Countering the enemy's reconnaissance presents a two-part problem. First is how to acquire the reconnaissance elements. Second is how to destroy them, once acquired. The commander and staff should--
- Develop NAIs and assign responsibilities for observation.
- Provide for continuous surveillance (over-commitment of the counterreconnaissance force weakens security).
- Use aviation assets to detect infiltration.
- Assign specific responsibilities for obstacle security.
- Plan to recover forward security elements.
The central purpose of enemy reconnaissance is to gain accurate, timely, and current information about friendly forces, terrain, and weather along the enemy avenue of approach. Typical enemy reconnaissance objectives are to--
- Identify, locate, and report on friendly headquarters, nuclear-capable weapons systems, troop locations, communications centers, and movement of enemy forces.
- Determine the disposition of friendly defenses, locate friendly boundaries and artillery positions, provide terrain information on the approaches to friendly defensive positions, and report friendly emplacement of demolitions, minefield, and other obstacles.
- Determine obstacle crossing sites and provide hydrographic information on water obstacles.
- Monitor areas of suspected NBC contamination.
- Identify routes for advance, withdrawal, and lateral communications.
- Identify possible sites for communications installations.
The division conducts targeting to mass combat power at critical times and places. The targeting process results in integrating all means of fire support. Targeting aids the division commander in seizing the initiative and synchronizing combat power in deep, close, and rear operations. Its purpose is to disrupt, delay, or limit enemy capabilities which can interfere with division operations by destroying, neutralizing, or suppressing enemy units and systems.
Targeting is an integral part of planning, preparing, and executing division operations. It begins with receipt of the mission and continues through completion of the operation. FM 6-20-10 is the division's base manual for targeting operations.
Considerations
The targeting process supports synchronization by focusing detection and delivery capabilities on high payoff targets. The HPTs warrant expenditure of resources to ensure the division's success or subordinate commander's intent and concept of operations. Diluting the targeting effort by identifying large numbers of HPTs defeats the purpose. The greater the number and diversity of HPTs, the less likely the division can detect and engage them all. This is also true of attack guidance. The greater the number of immediate targets, the less likely the division will be able to engage them all.
A finite capability exists to detect and deliver attacks against HPTs while simultaneously conducting tactical operations. The division must balance its capability to detect HPTs with its capability to engage them. The division must also consider the effect on subordinate commanders and their plans. If detection and delivery assets are totally committed to the detection and attack of division targets, they cannot support subordinate commanders' requirements. The G2, G3, and fire support coordinator (FSCOORD) must consider this problem. Attacking division HPTs with artillery units working for a subordinate maneuver force may desynchronize that subordinate commander's plan.
During the development of COAs and war gaming, the division plans element, which also functions as the planning cell's targeting team, must identify critical targets and critical times or events. This establishes priorities for detection and engagement.
These critical targets and times focus and integrate the intelligence effort on what is really important. This enhances and expedites the collection, processing, and dissemination of intelligence and target information. Similarly, these critical targets and times focus and synchronize fire support, maneuver, and CS assets at decisive times and places. This facilitates the allocation and prioritization of resources.
Time may be the most critical resource. The targeting process creates opportunities for the division and subordinate commanders. Utilizing the time available, they position assets to detect and engage critical enemy units and capabilities. Without this focusing effort, detection and delivery assets may be mispositioned, or they may detect and engage inappropriate targets or those of less value. Intelligence and attack assets may incorrectly focus on targets critical to the enemy but not to the division or subordinate commanders' intent and concept of operations. At best, these actions do not achieve the high payoff desired; at worst, they may have a desynchronizing effect.
Methodology
The targeting methodology is to decide the HPT, detect it, then deliver the attack. The decide portion is the planning phase of the targeting methodology. The detect and deliver portions are the execution phase. The G3 is responsible for the decide and deliver portions of this process. The G2 has staff responsibility for the detect portion. (See Figure 5-13.)
During the development of sequels to the current operation, the planning cell of the division main CP also functions as the plans' targeting team. The targeting team, under the supervision of the G3, develops the decide portion of the targeting process during COA development and war gaming. (Example of a generic targeting team includes representatives from G2 and G3 plans, FSCOORD, FA intelligence, G3 air, aviation brigade, EW, ALO, engineer, and NBC.)
During the execution of current operations, the targeting cell comprises the G2 operations, G3 operations, and DFSCOORD. They coordinate with the TAC and rear CPs and synchronize changes to the targeting effort (detect, deliver) as it is executed.
A targeting board meeting (team and cell members) is held periodically to validate the current HPTL and attack guidance based on current METT-T analysis and future plans. A standardized targeting board agenda (Figure 5-14) is followed to focus team members on events that may affect the current HPTL and attack guidance. A technique for validating the current HPTL and attack guidance is for the G3 to brief future operations in blocks of time (for example, H + 12 to H + 24, H + 25 to H + 37). The team then validates the current HPTL against each time block. Based on its analysis of each time block and its synchronization with future operations, the team recommends necessary changes to the HPTL and attack guidance for approval by the division commander or his designated approving representative (for example, CofS). This same process occurs during each scheduled targeting board meeting. The targeting process is dynamic, requiring constant validations and updating.
Similarly, when the targeting cell discovers an unanticipated opportunity or threat that affects the current operation, it develops, coordinates, and synchronizes the division's FRAGO to incorporate this change in the situation. During the development of the FRAGO, the cell uses the targeting methodology to determine any changes in targeting. It coordinates any recommended changes with the TAC and rear CPs.
Decide
The decide phase of the targeting process develops a HPTL, target selection standards, and attack guidance. The targeting team in the division main CP conducts this portion of the targeting effort during COA development and war gaming of the division OPORD for the sequel to the current operation. The targeting team presents its recommendations to the CofS, G2, G3, and FSCOORD for review prior to the division commander's approval.
The intelligence plans officer conducts the first step in the decide phase. Using target value analysis, he identifies high value targets (HVTs), to include units or capabilities critical to the success of the enemy's most probable COA.
Using this set of HVTs and the friendly COAs, the targeting team determines which of the HVTs to engage to ensure success of the friendly plan. These are normally expressed as target sets such as maneuver; fire support; reconnaissance, surveillance, and target acquisition (RSTA); air defense; or other categories as shown in Figure 5-15.
The targeting team then determines critical nodes within these categories. Within FS, a critical node might be artillery C2 or cannon and rocket artillery that can range the division main attack. Within RSTA, it might be the enemy's division reconnaissance battalion.
The targeting team then determines which of the critical nodes division or supporting assets can detect and attack. The plans officer and deputy FSCOORD consider the HPTs in terms of their importance to the division plan and develop a prioritized list. This list may be an overall priority listing; priorities by phase of the plan; priority for deep, close, and rear operations; or a combination.
The targeting team must also determine the desired results of an attack on the HPTs. The element measures the results sought in terms of delay, disruption, or limitation of the enemy's force or capability. Delay is expressed in terms of time or events. For example, the desired results may be to delay uncommitted divisions for six hours or delay the enemy counterattack force until the division's exploiting brigade has passed through the penetration.
Disruption is expressed in terms of an enemy capability. It is less precise than delay or limitation. For example, the desired results of an attack might be to disrupt the enemy's fire support system (engaging the penetration of the main defensive position), or to disrupt his air defense (engaging the aviation brigade). In defensive operations, the result may be to disrupt the enemy's RSTA capability in the main effort's defensive sector.
Limitation is expressed in terms of geographical approaches. For example, the desired result of an HPT attack might be to limit the enemy's approach to a specific avenue of approach. In rear operations, the desired result might be to limit the enemy's capability for air assault on division's rear.
To achieve the desired results may require the division to integrate several actions into one coordinated effort against the HPT. Limiting the commitment of an enemy force into a given area may require integrating maneuver, fire support, and engineer assets. In rear operations, limiting the enemy's capability for air assault may require integrating engineers to create obstacles on likely LZs, and AD assets to control likely air avenues of approach. The commander may have to position FS assets to range likely LZs, and assign R&S tasks to rear operations units. He may also position the reserve and TCF to enhance response time to air assaults.
The targeting team also develops target selection standards (see Figure 5-16) during the decide portion of the targeting methodology. It defines what sources or agencies will identify targets or suspected targets. The G3 and FSCOORD use these standards during execution to determine which target information warrants commitment of attack assets. Discriminators used to determine target selection standards include--
- Target location error inherent to the system.
- Susceptibility to deception.
- Previously demonstrated reliability.
- Weather.
- Enemy direction finding and jamming capability.
- Rules of engagement.
- Time since acquisition.
The targeting team then develops attack guidance which assists in synchronizing engagement of HPTs during execution. The attack guidance gives the G3 and FSCOORD a predetermined priority of targets to use during the battle. It assigns each HPT an attack parameter--immediate, as acquired, or plan.
Immediate means the target's priority requires engagement as rapidly as possible, even if an ongoing attack must be suspended to shift assets to this target. An immediate HPT may require diverting artillery or CAS from a different target to this one.
As acquired targets are those the division should engage expeditiously, but do not warrant stopping another attack to do so. This may be a HPT of lower priority or with loiter time that allows the division to engage it as attack assets become available.
Plan means the target is included in a list of targets for future engagement. These HPTs are lower in priority, have a long loiter time, or are only critical at certain times or as certain events happen. They require division monitoring and location validation prior to the attack. For example, AD targets maybe critical during an aviation brigade cross-FLOT operation but still not warrant immediate or as acquired priority. However, this parameter will involve committing resources to continue to monitor and track the target location. The attack guidance is normally prepared as a matrix. (See Figure 5-17.)
The targeting team determines the requirement to conduct target damage assessment during the decide process. Target damage assessment shows if the HPT attack achieved the desired results. The first decision is whether or not target damage assessment is required against the HPT. Some HPTs may not be suitable for development of timely target damage assessment. For example, disruption of AD capabilities or capabilities may be transient. The desired result may be achieved at the critical time and place. However, there may be no requirement or capability to conduct assessment. If a requirement exists to conduct target damage assessment, as in the case of delaying follow-on forces, the plans element must allocate resources and determine how to conduct it.
During the COA briefing and orders approval process, the targeting team (DFSCOORD) presents the results of the decide portion to the CofS, G2, G3, and division commander for approval. The commander ultimately approves HPTs, target selection standards, and attack guidance. During COA and order development process, the CofS coordinates the actions of the G2 and G3 operations elements at targeting board meetings, providing for parallel planning. Meetings occur as the elements transition from one plan to its sequel or at periodic intervals as listed in unit SOP. It allows the elements to make decisions which support the current operation and facilitate future operations, providing continuity to the targeting effort.
Detect
The detect portion of the targeting process includes allocating resources, developing the collection plan, assigning intelligence acquisition tasks, processing information into target intelligence, and disseminating target intelligence to attack systems. In the decide phase, the more specific the HPT targets, the more likely the G2 can identify, locate, and accurately target them.
The detect portion of targeting has a relationship to the attack system. If ECM assets are to attack the target to disrupt C2, then the detect process not only includes a location but also technical data that ESM collected to jam the target effectively. If surface-to-surface indirect fires are to engage the target, detect includes an accurate target location and projected loiter time. If helicopters will attack the target, the need for location accuracy is less than for artillery. However, due to reaction time, target location must be projected and closely tracked. This allows the aviation brigade to conduct final preparations and update locations prior to executing the attack. The HPTs targeted for attack by AI require early identification, nomination, and continuous tracking because of the long lead times required for AI.
The G2 identifies, locates, tracks, and targets HPTs in his recommendation for IEW task organization and the division collection plan. Because of the limited range of division intelligence assets, he must coordinate with the corps collection manager to request intelligence for deep HPTs.
The G2 operations and ASPS detect HPTs for close and deep operations, relying heavily on corps and EAC intelligence products. The division detects HPTs with LRS teams, Quickfix, Q-37 counterfire radars, and TACAIR.
Within the division intelligence system, G2 ensures that all personnel are aware of division HPTs. The HPT list is distributed to G2 operations, the ASPS, and the TCAE as a ready reference, particularly as soldiers become fatigued.
The FAIO in the ASPS assists the G2. He ensures personnel are aware of the HPTs. He coordinates with intelligence managers to screen all intelligence for targeting information. He serves as a conduit to disseminate targeting information to the FSE.
The heart of the detection phase is the IPB process. The ASPS continuously updates the IPB to confirm or deny situational and event templates, using information provided by organic, supporting, higher, adjacent, and subordinate assets.
The EW section of the ASPS develops the electronic preparation of the battlefield (EPB) which supports the detection of HPTs. It tasks the TCAE to provide information to accomplish this. It also integrates information and intelligence from corps and EAC to assist in HPT development.
Reconnaissance reports support targeting in close operations. Intelligence acquisition tasks in the collection plan, or specific reconnaissance missions assigned to units by the G3, provide this information.
Counterfire radars provide accurate locations of artillery firing locations. These targets may have already been engaged, depending on their priority and division's attack guidance. However, their locations may assist the ASPS to adjust and update situational and event templates and assist in locating other HPTs. The DIVARTY counterfire officer must routinely pass radar acquisitions to the G2 special compartmentalized information facility.
Terrain analysis helps detect HPTs for rear operations. The rear CP identifies likely LZs and assigns surveillance responsibilities that are integrated with the air IPB. Air defense and Air Force early warning radars provide the enemy's air activity. The rear CP integrates this information with surveillance of likely LZs.
The G2 synchronizes HPT detection in deep, close, and rear operations using the situational, event, and decision support templates. These help him to coordinate and integrate resources at critical times to provide the targeting information required.
Committed forces detect HPTs in close operations. These include ground maneuver units, division IEW assets, artillery radars and FISTS, air cavalry troops, and aerial FS officers. These forces and assets detect both division HPTs and those of their respective subordinate maneuver commanders. They detect division HPTs as a result of intelligence acquisition tasks in the collection plan and through the reporting of combat information to the TAC CP.
The division commander and subordinate commanders may have different HPTs. The G2 may task the 1st brigade to identify and locate enemy AD in its sector in support of a cross-FLOT aviation mission. However, AD may not be a HPT for the 1st brigade commander. His priority may be artillery and mortars arrayed against his main attack or RSTA elements. Conversely, a subordinate commander's HPT may duplicate those of the division commander. Coordination between echelons precludes duplicating effort and resources. The G2 operations at the main CP coordinates the collection effort with the subordinate commander's S2, integrating it into the division collection plan. Likewise, the G3 operations at the main CP coordinates the attack plan with the subordinate commander's S3 and integrates it with the division's attack.
The G2 operations at the TAC CP coordinates HPT detection in close operations using the HPTL, the DST, combat information from committed forces, and intelligence received from the main CP. He coordinates with S2s of committed forces and the G2 at the main CP to ensure collection assets focus on HPTs. As HPTs are detected, he informs the FSE and G3 for commitment of attack resources.
The G2 operations in the rear CP coordinates detection of HPTs in rear operations with the G2 in the main CP and base and base cluster S2s. His primary means of detecting HPTs are reconnaissance and surveillance efforts of base and base cluster commanders. Using doctrinal and situational templates as well as terrain analysis and the air IPB, he integrates and coordinates the R&S effort into one plan. This plan incorporates reports from MP traffic control, information from divisional counterintelligence, and interrogation of detainees.
Detection of HPTs in an enemy force requiring a Level II or III response to a rear area threat depends on contingency planning between the rear and main CPs' G2 operations. Intelligence and EW assets may be required to detect HPTs quickly and accurately to engage them with the TCF, supporting artillery, attack helicopters, or CAS. The G2 operations at the main CP coordinates, integrates, and synchronizes reallocation of assets.
Deliver
The deliver phase is the execution of the attack against the target. The G3 operations and FSE are the focal point. Using the prioritized HPTL, target intelligence from the G2, target selections standards, and attack guidance, they direct the attack.
The G3 operations role in the deliver phase is to confirm HPTs and to direct their attack by maneuver forces. The FSE directs attack of HPTs by FS assets once they are detected and meet attack guidance.
Attack of HPTs in deep operations normally involves attack by AI or attack helicopters. The range of division attack assets normally does not reach uncommitted enemy forces. Deep maneuver, though an attack option, is a high risk.
The aviation brigade plans and executes attack of HPTs by attack helicopters. The division main CP integrates this attack as part of the concept of operations. Using the DST, the main CP G3 coordinates the attack time and location with the aviation brigade. He aids planning and execution by allocating resources and changing intelligence and FS priorities.
The FSE and G3 operations in the main CP coordinate and integrate attack of HPTs by AI. The FSE submits AI nominations to the corps FSE 24 to 36 hours prior to the desired attack. The division FSE submits periodic updates on the location and status of targets to the corps FSE. The G2 operations provides information for these updates. The division FSE informs G3 operations of the impending attack. The G3 operations either confirms the attack or requests diversion to a different target. The Air Force approves requests to divert after considering--
- Types of aircraft.
- Effectiveness of munitions against the new target.
- Enemy air defense in the vicinity of the target.
- Effects of weather on target engagement.
- Target distance from the old target.
Committed forces attack HPTs in close operations. Committed forces' CPs, and the TAC and main CPs, coordinate and synchronize the attacks. Attack assets include maneuver, FS, and engineers. Maneuver forces may attack enemy reconnaissance as part of counterreconnaissance efforts. They may conduct limited objective attacks to disrupt AD during aviation operations. Smoke may be used to disrupt enemy reconnaissance and target acquisition. Fire support may attack a range of targets including enemy mortars, artillery, AD, reconnaissance, and C2 nodes. Engineers may place mines or demolitions to limit the enemy's avenues of approach or delay his arrival.
Attack of HPTs in support of rear operations may actually be conducted as part of the deep or close operations. These may include engaging air assault forces and support assets, long-range fire support, and infiltrating forces. In the rear area, attack of HPTs may be seen as counterreconnaissance, surveillance, and security against SOF-type forces, or a Level II or III response to a rear area threat.
The rear CP coordinates and integrates base and base cluster plans to attack HPTs in the rear. It coordinates with the main CP to change priorities of fire support to engage HPTs. It directs Level II and III responses to rear area threats. The main CP coordinates and synchronizes these actions with deep and close operations. For example, it may have to divert CAS to support rear operations or change the priorities of CAS to synchronize with those of the close operation. The use of attack helicopters to support the rear CP may also impact on deep operations.
The main CP commands and controls the division targeting effort by executing branches to deep operations and integrating, coordinating, and synchronizing actions to support branches implemented by the TAC or rear CP. For example, it may request to divert an AI mission in deep operations requiring the TAC CP to implement a branch of the close operations plan. The TAC CP would issue a verbal FRAGO to execute the close operations branch.
The TAC CP may direct execution of branches of the close operations plan and coordinate them with the main CP. This ensures the attack of HPTs in the deep operation is synchronized with the close operations branch. As a result, the TAC CP may direct a new or revised HPTL and place attack guidance in effect. This may require changes to collection plans and priority to detect the HPTs. For example, the opportunity to effectively employ a JAAT in the close operation may require changing AD targets from plan to as acquired.
SUPPRESSION OF ENEMY AIR DEFENSE OPERATIONS
Division air assets must survive to contribute their full combat potential. For this reason, SEAD is critical. It must be accomplished quickly and efficiently to support aviation operations.
Suppression of enemy AD is a concurrent operation inherent in division aviation missions. The concept of the aviation mission determines the complexity of the supporting SEAD operation.
When the division commander decides to commit the aviation brigade, the aviation brigade plans SEAD support for the mission. The division supports the aviation brigade commander and his staff and synchronizes overall operations, to include SEAD.
The division has the primary responsibility to support suppression of ground-based enemy AD weapons to the limits of observed fire. Targets that observed fire cannot engage are the primary responsibility of the Air Force. In this area, the division has secondary responsibility out to the range limit of its indirect fire weapons. In most situations, the division can suppress targets with unobserved indirect fire, if they are accurately located.
The division supports SEAD operations with specific critical combat and CS elements to synergize combat power against the enemy's air defense. Unity of effort is essential and requires detailed planning, close coordination, and precise timing.
SEAD Categories
There are three categories of SEAD operations--campaign, localized, and complementary. Within each category, SEAD may be destructive or disruptive.
Destructive SEAD destroys surface-to-air defenses or personnel. Its effects are cumulative and steadily reduce aircraft attrition. Destructive SEAD, employed alone, places large demands on combat power. The commander must integrate destructive SEAD with disruptive SEAD, such as jammers, which are generally reusable resources.
Disruptive SEAD can temporarily degrade, deceive, delay, or neutralize surface-to-air defenses or personnel. There are two types of disruptive SEAD--active and passive. Active suppression includes jamming, chaff, flares, and tactics such as deception, avoidance, or evasive flight profiles. Passive suppression includes camouflage, infrared shielding, warning receivers, and materiel design features.
Disruptive SEAD complements destructive SEAD. It can--
- Degrade jammable threats.
- Assist destructive airborne suppression systems in suppressing surface-to-air defense systems.
- Temporarily degrade or neutralize enemy AD systems when their destruction is not possible or feasible.
- Sustain suppression effects achieved by destruction once threats are at levels commensurate with joint suppression of enemy air defense (JSEAD) objectives.
Campaign SEAD
Divisional artillery, IEW, and aviation assets may join in suppressing campaign SEAD targets; however, corps or Air Force assets usually engage these targets when they are available. The division uses artillery to its maximum range to destroy accurately located targets. It employs IEW assets to jam, degrade, or disrupt enemy AD systems. Although Army aviation assets are not a primary weapons system for SEAD operations, the division may use them to engage deep campaign SEAD targets.
Localized SEAD
The division conducts localized SEAD to support cross-FLOT operations as part of its scheme of maneuver. Indirect fire support weapons and IEW assets are the primary systems used to open corridors or suppress specific attack objectives. Suppression will begin prior to arrival of the aircraft, and should continue as long as aircraft are in range, unless aircraft would be endangered by the system suppressing the ADA. Egress routes are established and suppressed in a similar manner. Coordination, synchronization, and timing are critical to the success of these operations; fire support, Army airspace command and control (A2C2) and TACAIR control systems coordinate these aspects with aviation elements conducting cross-FLOT missions.
Complementary SEAD
Divisions conduct complementary SEAD continuously. They attack enemy AD targets of opportunity that can adversely affect current or future aviation operations when they are identified and located, and when attacks are consistent with available resources and commander's priorities. The FSE may prioritize complementary SEAD efforts in specific areas to facilitate a future aviation mission. When this exceeds the division's capabilities, the G3 requests support from corps.
Division SEAD Operations
The best protection against every air defense is to select enemy routes that avoid ADA. The routes selected determine the resources required to conduct an effective SEAD program. The G3 must consider factors of METT-T as he develops COAs for cross-FLOT or near-FLOT employment of the aviation brigade. He must ask: Is this an attack mission? Against what? Is it an aviation mission to support an air assault? Is it an aviation mission to insert a LRST?
Key considerations in staff estimates which may impact division support of aviation brigade's SEAD operations include--
- What is enemy force and status (not just the enemy ADA)?
- Is the enemy attacking or defending?
- Is the division facing the enemy's main or supporting effort?
- Does terrain reinforce nap-of-the earth flights or have the effect of segmenting the enemy ADA?
- Does terrain result in radar blind spots the division can exploit?
- Does weather favor use of aviation assets?
- What current division operations will impact on troops available to support the SEAD program for the aviation mission?
- What, if any, intelligence collection will have to be reduced or terminated to support the development of SEAD targets?
- Was ADA already identified as a HPT?
- Has intelligence developed and maintained a good enemy AD data base or will collection assets have to be redirected to target ADA? (An electronic intelligence (ELINT) or communications intelligence (COMINT) report on ADA used for situation development may be insufficient for artillery targeting.)
- What attack assets are available to support the SEAD program?
- Will they have to reposition?
- Do attack assets have the correct amount and types of munitions?
Staff Responsibilities
Suppression of enemy air defense is a force protection requirement inherent in aviation operations. The division aviation brigade plans, prepares, and executes SEAD in support of its operations. The division commander and staff synchronize SEAD support for aviation operations with the division's current and future operations.
G3. The division G3 coordinates with the aviation brigade's S3 during development of the mission. He coordinates, integrates, recommends, and synchronizes changes to priorities and task organization to support the aviation brigade. The aviation brigade S3 integrates and synchronizes these assets and capabilities into the aviation brigade plan.
The aviation brigade S3 A2C2 element plans, coordinates, and submits air corridors to G3 operations A2C2 element for synchronization and division commander approval. The G3 may synchronize a ground attack with an air operation to open a corridor. A forward thrust by maneuver forces may effectively disrupt the enemy and his forward air defense system. Direct fire weapons of the maneuver units are the most responsive and effective means of attacking close-in AD targets. Since the enemy may locate significant AD near the FLOT, planners should look for opportunities to bring ground and air penetrations together in time and space to benefit from each. Maneuver units engaging enemy AD systems report them through operations channels in accordance with unit SOPs.
The aviation brigade S3 coordinates FARPs, forward assembly areas (FAAs), and other terrain requirements with committed maneuver brigades. The G3 resolves conflicts or recommends solutions to the division commander.
Although there may be exceptions, the G3 will not normally assign SEAD missions to aviation units. Aviation contributes to complementary SEAD by engaging targets of opportunity and through self-defense tactics. Army aviation can also call and adjust fires against enemy targets. This capability can extend the division's range of observed fires significantly.
The G3, assisted by the A2C2 element, synchronizes air corridors for the aviation brigade. Synchronization is based on--
- Current and future airspace control measures.
- Current and future artillery and AD locations.
- The enemy's AD situation and probable COA.
- Weather and terrain.
- Capabilities of friendly aircraft.
The aviation brigade representative in the division A2C2 element coordinates this with and for the aviation brigade.
G2. Situation and target development is critical in SEAD. Working closely with the aviation brigade S2, the G2 directs intelligence organizations to identify and locate enemy AD order of battle. He also finds critical nodes which, if interdicted, will significantly degrade enemy capability. He integrates the aviation brigade commander's PIR and IR, and requests for intelligence information, into the division collection plan.
Based on the aviation brigade mission, the G2 may recommend changes to the division commander's PIR and IR. However, he must ensure that they support the division operation, not just the SEAD for the aviation brigade.
The G2 uses down links of corps and EAC assets to obtain real-time or near real-time combat information and targeting data. He develops AD radar locations from ELINT down links. He may direct GSRs to track the AD radar location as it moves.
The aviation brigade S2 forwards requests for intelligence information to committed maneuver units to determine enemy AD locations in their AOs. He integrates this information with intelligence received from the G2 and develops and disseminates target information to the aviation brigade FSE.
Fire Support Element. The FSE recommends to the G3 required changes to the artillery task organization and priority of fires to support the aviation brigade. It may recommend a mix of DS, reinforcing, or GS-reinforcing artillery, or it may assign the aviation brigade priority of fires for a specific mission. METT-T will influence the method chosen.
The FSE also may recommend changes to the division HPTL, attack guidance matrix, and target selection standards. Depending on the time available, the FSE may direct repositioning FS assets to support the overall mission, as well as provide SEAD support for the aviation brigade's mission. Artillery units support the operation with preplanned fires and on-call missions. Electronic warfare assets degrade the effectiveness of enemy air defense by jamming key C2 nets.
The FSE coordinates additional fires for the aviation brigade as requested by the brigade FSO. The FSE also coordinates SEAD for targets outside the division's boundaries, but capable of ranging air corridors.
The opening of a corridor is a major operation requiring a heavy commitment of resources. Only a limited number of corridors can be established in a given period of time. Therefore, the division FSE must coordinate with adjacent and subordinate units to ensure all division suppression operations are mutually supportive and capitalize on enemy vulnerabilities.
Division artillery systems can destroy accurately located enemy AD targets. Artillery may also engage suspected enemy AD targets. Smart munitions and advanced sensors can reduce the problem of target location if the location is within the sensor's area.
Use of artillery smoke in SEAD operations can be both an advantage and a disadvantage. Smoke can hide aircraft from enemy AD weapons that use visual acquisition. However, it is ineffective as a countermeasure against electronic sensor-guided AD systems. It can also obscure targets and prevent friendly aircraft from identifying enemy AD weapons. Smoke is a limited resource; its use must be planned and coordinated carefully.
The MLRS, if available to the light division, is an effective weapon for SEAD. The dispersion of MLRS bomblets makes it an excellent weapon against thin-skinned AD weapons and radars. MLRS can create corridors at the FLOT or engage several targets with its multiple aim point capability.
Jamming enemy AD system C2 nodes has two objectives. First, it can force enemy firing units to activate their radars to acquire targets rather than relying on the C2 system, and thus expose themselves to acquisition and attack. This is useful, however, only if systems are poised to attack when the enemy activates its radars. Second, jamming also degrades C2 systems during friendly air operations. This type of suppression requires close coordination of flight and jamming schedules. Because of the limited number and capabilities of division jammers, the EW staff officer in the FSE synchronizes jamming of SEAD targets with the total division ECM effort.
An Example
This section provides an example of how a division plans and executes SEAD in support of an aviation brigade cross-FLOT operation. The division commander has decided to attack a regiment identified as the enemy's counterattack force to prevent its use against the division as it attacks. The division is conducting offensive operations as part of a corps deliberate attack. The division is not the corps main attack.
The enemy opposing the division occupies deliberate defensive positions and consists of elements of an infantry division at approximately 40 percent combat effectiveness. Air parity exists in the theater with either side capable of achieving local air superiority for short periods. Ninety-six hours earlier, the division received this mission:
- To conduct a relief in place.
- To attack, on order, as the corps supporting attack, to penetrate the enemy defense.
- To be prepared to pass an armored division to exploit in the enemy's rear.
The division is at 98 percent combat effectiveness. It completed the relief in place 24 hours before as part of a regeneration of the corps' combat power. The corps' FRAGO to attack is received 18 hours prior to H-hour.
Once the enemy infantry regiment is identified as a HPT, the intelligence system focuses on it to detect its location and movement. The intelligence staff uses analysis of the terrain, weather, and enemy doctrinal and situational templates to develop possible enemy COAs. The G2 establishes NAIs and TAIs. The NAIs will confirm or deny the enemy's COA while the TAIs will become the EAs for the attack on the regiment. These areas are highlighted in the collection plan with additional assets allocated to ensure redundancy of collection to increase timely information on the enemy regiment's movement.
The division commander assigns the cross-FLOT attack mission to the aviation brigade. The G3 establishes priorities and allocates resources to the aviation brigade to conduct the attack. These included priority of fires. The aviation brigade conducts detailed planning and preparation for the mission, including SEAD planning.
The aviation brigade A2C2 element coordinates air corridors to attack the enemy regiment to avoid concentrations of enemy air defense. The A2C2 element considers existing low-level transit routes (LLTRs) in effect or projected to take effect. This allows planners to take advantage of scheduled AF jamming and operations conducted in support of AF missions. Planners also consider the terrain, projected weather, and aircraft survivability capabilities. The brigade S2 and FSO conduct their planning and preparations based on these air corridors.
The aviation brigade A2C2 element provides the division A2C2 element the proposed air corridors, which it coordinates with the committed maneuver brigade's S3 air and corps A2C2 element. The division A2C2 element synchronizes these corridors with the concept of operations and scheme of maneuver. The G3 air recommends approval to the G3 and the division commander approves them.
The aviation brigade S2 recommends changes to the aviation brigade commander's PIR and IR. He requests enemy AD locations from higher and adjacent units and provides target information to the FSO to plan attack of these targets.
The aviation brigade FSO develops the SEAD program from targets received from the S2. He tasks supporting FS assets and requests support from division for targets beyond the brigade's capabilities. Jamming assets are tasked to suppress C2 systems of the enemy AD assets facing the division.
The aviation brigade FSO coordinates the positioning and munition requirements for the SEAD with the DIVARTY. He coordinates ECM targets through the EW staff officer in the main CP FSE.
The SEAD targets are verified prior to launching the attack. The field artillery intelligence officer in the ASPS is also a key source for target updates.
To simplify C2 for executing SEAD, the FSO plans SEAD as individual targets, groups, and series. These targets are included in an execution matrix which is provided, along with the SEAD program, to units scheduled to fire the SEAD. Using an execution matrix, the FSO for the air battle captain directs execution of the SEAD. Attack helicopters engage targets of opportunity or these targets are transmitted as an immediate suppression or fire-for-effect mission to the FSO. (See Figure 5-18.)
The aviation brigade commander reviews the updated plan and gives the execution order to the air mission commander. As part of the final preparation, the air mission commander conducts a rehearsal with the aviation brigade FSO, artillery units, ECM assets, and his subordinate commanders participating.
During the mission, the air mission commander directs the execution of SEAD targets as the mission progresses and calls for fire at targets of opportunity for the duration of the mission, including the recrossing of the FLOT.
On completion of the cross-FLOT mission, the aviation brigade commander and staff conduct an analysis to determine its effectiveness. The SEAD planning process continues, to ensure maximum planning before any future commitment of assets to further cross-FLOT operations.
ARMY AIRSPACE COMMAND AND CONTROL
Successful division operations and engagements may depend on the effective use of airspace over the AO. Within this airspace, a high density of friendly weapons systems and aerial vehicles with overlapping operating envelopes and flight profiles must contribute to combat effectiveness without interfering with one another, hindering the efforts of friendly combatants, and causing fratricide.
Division A2C2 consists of all actions required to synchronize airspace use. The division A2C2 element performs these actions under the supervision of the G3 air. The A2C2 element coordinates airspace user requirements with the commander's plan for effective airspace use over the division's AO. The A2C2 element is a separate cell in the division main CP, normally located near the division FS cell. Its primary tasks include--
- Identifying and resolving airspace user conflicts.
- Coordinating and integrating airspace user requirements within the division's AO and with other services and adjacent units.
- Maintaining A2C2 information displays and maps.
- Developing and coordinating airspace control SOPs, plans, and annexes to division OPORD and OPLANs, and disseminating airspace control orders, messages, and overlays.
- Approving, staffing, and forwarding to corps requests for airspace control measures requiring airspace control authority (ACA) approval and special use airspace.
To accomplish these tasks, A2C2 elements must continuously update the G3 air and A2C2 displays and maps. This coordination helps synchronize combat power within the limited airspace over the division's AO.
Airspace Control Measures
To meet the requirements of simplicity and flexibility, the A2C2 element methodology stresses procedural control. Procedural control is conducted through the use of airspace control measures and standard operational procedures (air, axis, air corridor). Figure 5-19 depicts airspace control measures available to provide procedural control. Airspace control measures requiring ACA approval are forwarded through the corps A2C2 element for approval as shown in Figure 5-20.
To separate rotary- and fixed-wing aircraft, weapons control status of weapons free. Aircrews the air component commander (airspace control authority) designates an airspace control measure in the form of a coordinating altitude. (See Figure 5-21.) Rotary-wing aircraft normally operate below the coordinating altitude, and fixed-wing aircraft, above it. The coordinating altitude assigned to rotary-wing aircraft may be below the altitude assigned to fixed-wing aircraft, thus creating a buffer zone. The following paragraphs discuss airspace control measures the division uses.
A weapons free zone (WFZ) (Figure 5-22) is an AD zone established for the protection of key assets or facilities of the joint force other than air bases. Air defense artillery systems within a WFZ are normally maintained at a must avoid active WFZs, or coordinate with the designated control authority prior to entry or prior to transit through a WFZ.
A high-density airspace control zone (HIDACZ) may be requested by a maneuver force commander and must be approved by the ACA. This airspace control measure reserves airspace. It also controls which airspace users have access to the zone. (See Figure 5-23.) By establishing a HIDACZ, the commander forces other airspace users to operate elsewhere or under the conditions and restrictions approved by the authority. The establishing (requesting) commander must control all airspace use within the HIDACZ. In addition, the commander controls the weapons control status within this area.
A restricted operations zone (ROZ), also known as an airspace restricted area, is airspace of defined dimensions developed for a specific mission or requirement. (See Figure 5-24.) A ROZ restricts some or all airspace users from the area until the end of the mission. A ROZ supports DZs, search and rescue operations, special electronic mission aircraft orbits, and UAV launch and recovery sites. A ROZ may facilitate AD operations in a given area by preventing friendly aircraft from entering airspace. The commander's A2C2 element requests a ROZ through the appropriate A2C2 element to the ACA. The ACA Coordinates requirements for temporary ROZs and evaluates their impact on other airspace users. Controlling authority requirements for the ROZ are similar to those required for a HIDACZ, with the exception of the ADA weapons status.
A minimum risk route (MRR) is a temporary route of flight which presents the minimum known hazards to low-flying aircraft transiting the combat zone. It normally extends from the air route structure in the communications zone (COMMZ) through the Army, corps, and division area, across the FLOT, and terminates near the FSCL. The MRR is synonymous with low-level transit route (NATO term).
A low-level transit route (LLTR) (see Figure 5-25) is a temporary corridor of defined dimensions which allows the low-level passage of friendly aircraft through friendly air defenses and controlled or restricted airspace. The ACA specifies the number of LLTRs (active and on-call) to accommodate air operations. Division and corps nominate the actual trace on the ground which the LLTR follows. The A2C2 element, with AF coordination and assistance, plans it. The routing accommodates transiting aircraft but avoids critical areas and assets defended by ADA. It also stays clear of areas of anticipated intense combat operations (for example, an axis of main attack). Additionally, airspace planners establish the route trace to avoid--
- Concentrations of FA units.
- Significant groups of FS targets.
- Landing and drop zones, FARPs, landing sites, and airfields.
- Known enemy ADA systems.
- Other planned or active special use airspace (for example, ROZs, and special corridors).
- Friendly ADA firing batteries or units.
A standard use army aircraft flight route (SAARF) (Figure 5-26) is a route established below coordinating altitude to aid movement of Army aviation. Normally in the corps and division rear AO, it is a recognized Army airspace control measure that does not require joint approval by ACA. The develops SAAFRs to safely route Army helicopters conducting CS and CSS missions. They are intended primarily for single aircraft or for small flights of aircraft operating routinely between base clusters in the DSA and in corps rear area.
An air corridor is a restricted air route for use by Army aircraft and to prevent friendly forces from firing on friendly aircraft. Air corridors are standard Army operational procedures. They do not require ACA approval as they are employed within the terrain flight environment, normally in the division AO and deep operations area. Air corridors are temporary, established as required to route combat elements of the division and corps aviation brigade between assembly areas, holding areas, battle positions, FARPs, and target engagement areas. (See Figure 5-27.)
Air corridors can serve as control measures during air assault operations, and as routes for air assault forces during the air movement phase. Helicopters conducting air movement operations within the corps and DRA can use them. Standard measures for air corridors include air control points (ACPs), communications check points, magnetic azimuths of the routes of flight, PZs, LZs, and initial points (IPs).
The aviation LO, in coordination with the A2C2 element, selects the ground trace of an air route and depicts it graphically on the OPORD overlay. Terrain, enemy AD, and ground maneuver plans influence the need for and location of air corridors.
Command Post Functions
The division A2C2 element functions under the staff supervision of the G3. The G3 air supervises the operations of the A2C2 element. The A2C2 element is staffed for 24-hour operations.
The A2C2 element at the main CP is the focal point for all airspace control activities related to division operations. Close coordination is maintained between the TAC CP, the rear CP, and the A2C2 element at the main CP. This ensures airspace requirements generated by changes to the tactical situation are met timely and effectively.
No formal A2C2 element exists at the TAC CP. Selected TAC CP staff and liaison elements perform airspace control as collateral functions. The division A2C2 element comprises the G3 air element, ADA element, aviation element, and ALO.
The A2C2 element often includes an MI brigade LO and an ATS LO. The A2C2 element constantly coordinates with the--
- FSE.
- Aviation brigade.
- ADA battalion.
- ATS unit assigned to the division.
- G2 section.
- G4 section and, when required, the air and naval gunfire liaison company (ANGLICO).
- A2C2 elements and brigade S3 airs.
The A2C2 staff sections and liaison elements are represented only within the main CP.
Personnel assigned A2C2 accomplish two primary tasks. First, they assist in coordinating their parent units' assets, provide technical expertise, and serve as liaison between the commander, his headquarters, and their parent units. Second, they synchronize airspace requirements of their parent units with other airspace users of the combined arms team and services. As an additional task, A2C2 staff often obtain and pass battle damage assessment information from A2C2 channels to the G2 staff.
Personnel performing A2C2 staff functions require an in-depth knowledge of A2C2 doctrine and procedures, corps and division airspace control plans, and division airspace control SOPS. This requires personnel be assigned full-time staff duties in the A2C2. It is recommended that personnel receive formal training (for example, the Air-Ground Operations School).
Tactical CP
The G3 operations cell responds to airspace conflicts in close operations as required based on information provided by committed forces and the main CP A2C2 element. The operations section maintains and displays unit locations down to battalion level. Committed forces provide their OPLAN and OPORDs, graphics, and FRAGOs to the operations section. The FS cell receives and maintains locations of artillery and AD units and their coverage and range fans. The air liaison officer has information concerning sorties--how many, when, and where. He also has information on MRRs, CPs, and IPs that are in effect. The A2C2 element at the main CP provides the TAC CP with effective or planned air corridors affecting the close area of operation. By using standardized overlays, the G3 operations cell can readily identify airspace conflicts or likely conflicts. The G3 operations cell can then request the A2C2 element to resolve the conflict with affected units. In time-critical instances, the TAC CP may issue directives to resolve an immediate conflict and then pass overall synchronization to the A2C2 element at the main.
Main CP
The A2C2 element at the main CP is the focal point for A2C2 in the division. It synchronizes airspace use for current deep, close, and rear operations and provides input and technical expertise to the plans cell for future operations.
Various organizations and CPs provide the information required to synchronize the use of the division's airspace. The A2C2 element keeps this information on one A2C2 map. The G3 air must keep up to date on branches and sequels to the current deep, close, and rear operations.
Support of current deep, close, and rear operations begins with the planning, coordination, and approval of airspace control measures implemented by the division or the ACA. In the case of LLTRs and MRRs, the A2C2 receives input from committed unit S3 airs, correlates the information, and provides it to the corps A2C2 element. This is done routinely in cycles--every 8, 12, or 24 hours. Recommendations are based on the division's and brigade's missions, concepts of operations, and intent. The objective is to preclude airspace control measures from restricting ground operations--especially artillery, mortar, and AD operations. War-gaming the concept of operations and branches and sequels should indicate artillery, AD, and Army aviation locations to avoid. On-call airspace control measures should also be developed to support various branches and sequels.
During operations, the A2C2 element must anticipate activating airspace control measures to preclude airspace conflicts. Members of the A2C2 element must review the air control order as it is received to identify conflicts. For example, GS AD assets positioned in a LLTR may require repositioning.
Artillery units positioned in a division air corridor or positioned so that their trajectory crosses an air corridor may have to reposition to fire SEAD missions in support of aircraft using the corridor. In each case, there are other options besides repositioning. These include establishing airspace coordination areas for the artillery or changes to weapons control status for AD units. The A2C2 element informs the G3 of conflicts which cannot be resolved at division level or through coordination with the corps A2C2 element.
Rear CP
The rear CP does not have an A2C2 element. The rear CP G3 operations cell responds to airspace conflicts as required. The rear CP G3 operations cell coordinates with the A2C2 element in the main CP which plans, coordinates, and monitors A2C2 for rear operations.
During rear operations, tactical changes may require changes to airspace control in the rear. A Level III response to a rear area threat primarily affects LLTRs, SAAFRs, and other air corridors that transit through the rear.
Division A2C2 Operations
Figure 5-28 shows items of information that each A2C2 staff element requires to perform its functions. The staff elements using this information are shown by duty position.
In the forward AO where the division conducts close and deep operations, enemy actions may determine airspace use requirements. Division and corps aviation units maneuver over the battlefield, operating below the coordinating altitude and using terrain flight and standardized movement techniques. Attack helicopter battalions, air cavalry troops, and aviation companies in air assaults conduct combat operations as a unit. They respond to the tactical directives of an aviation C2 system. As such, policy and procedures concerning air traffic management, identification of airspace users, and flight following differ from those for aircraft operating in the division and corps rear areas or COMMZ, or in a controlled airspace. Aviation elements of corps and EAC normally conduct CSS missions as small elements or individual flights. As such, they operate under established procedural control rather than under their parent C2 system. When operating in the MBA, these aircraft coordinate with the unit over which they are transiting.
Fire Support
Fires from mortars, cannon and rocket artillery, and missiles pose hazards to friendly aircraft activities. The highest probability of conflict between aircraft and surface-to-surface indirect fire occurs at relatively low altitudes in the immediate vicinity of firing units and target impact areas.
To reduce potential conflicts between surface-to-surface indirect fires and aircraft, the FSE provides firing battery locations and FS plans and activities to the A2C2 element. The A2C2 element disseminates this information to all aviation, ATS, and TACAIR elements. The FSE disseminates airspace control measures to firing units for establishing airspace coordination areas. Additionally, the interface between the FSE and the element ensures they coordinate planned artillery fires and UAVs with air operations and planned air activities with ground operations. This is essential to deconflict fires, air operations, and ground operations.
Air Defense Artillery
In forward area air defense (FAAD), the primary goal of airspace control is to avoid engaging friendly aircraft while imposing as few constraints as possible on both aircraft and FAAD systems. Achieving this goal involves developing procedures for FAAD and aircraft as well as a system to support timely dissemination of information.
The ADA representative in the A2C2 element provides the location and coverage of organic and supporting AD units for use by the A2C2 element to determine, coordinate, and recommend airspace control measures to the division commander and corps A2C2 element. He disseminates active and on-call airspace control measures to the air battle management operations center (ABMOC) in the division ADA battalion. The ABMOC issues the required instruction to affected ADA units.
Army Aviation
The Army aviation representative to the A2C2 element provides locations of Army airfields, forward operating bases, and FARPs. He determines, coordinates, and recommends SAAFRs and air corridors to the division commander for approval. He disseminates A2C2 information from the corps and brigade S3 airs to the aviation brigade as well as to supporting medical evacuation (MEDEVAC) units.
Air Liaison Officer
The ALO provides locations of contact points and initial points to the A2C2 element. He also provides times of preplanned or immediate CAS missions for use by the element to deconflict airspace use. The ALO also provides technical advice on employing aircraft and ensures ACA-approved airspace control measures are displayed on the A2C2 map and incorporated in A2C2 planning and coordination.
Air Traffic Service LO
The ATS LO representative provides A2C2 elements with current status of flight coordination centers (FCCs), navigational aids (NAVAIDs), and ATS terminal support at airfields or LZs. The ATS LO ensures critical changes in airspace information affecting Army aircraft operating in the DRA are transmitted to aircraft through the FCCs.
G2 Section
The G2 representative provides the A2C2 element with weather data and known and suspected locations of enemy units and air defense. This aids in planning and coordinating airspace control measures.
G4 Section
The G4 section provides the A2C2 element locations of forward support battalions (FSBs) and bases in the division rear. The A2C2 element uses the information to plan, determine, and coordinate SAAFRs in the division's AO. The G4 also informs the A2C2 of air resupply missions for incorporation in the overall A2C2 mission.
A2C2 Planning
Plans and associated control measures for A2C2 should be limited to those necessary to ensure conformity with the tactical plan and aircraft safety. They should make maximum use of procedural control measures. The scheme of maneuver and commander's intent determine and govern their design.
Planning will be as detailed as the situation and time allows. The urgency of the situation and time available will dictate whether to produce an A2C2 annex. It should include only information which clarifies or amplifies what is in the unit SOPs, or specifies actions and procedures necessary to synchronize airspace use. In many situations, the fast-paced and dynamic tempo of combat operations may cause the A2C2 staff to use an A2C2 overlay and to issue verbal directives to subordinate forces.
The use of the field SOPs, airspace control orders, and airspace control plan standardizes procedures, reduces the amount of coordination, and provides implementing instructions. The need for an A2C2 annex is thus minimized in many situations.
A2C2 in Battle
Once the battle is in progress, the A2C2 element at the main CP continues to monitor subordinate and parent units and modify plans as required. Effective coordination, rapid exchange of information, timely decision making, and rapid issuance of orders promote agility and initiative.
A2C2 actions during the battle are the same as those performed during the planning phase. During the battle, emphasis is on--
- Anticipating and reacting to changes in the tactical situation.
- Anticipating future requirements based on the progress of the battle.
- Facilitating the ability of the commander to influence the battle with air assets. This means identifying potential airspace conflicts and taking immediate action to resolve them.
Organization of the A2C2 system enhances coordination and exchange of information and permits the A2C2 element to respond to changing requirements. Electronic communications and messengers disseminate information, airspace control orders, and requests for special restrictive measures.
Airspace use and information displays maintained by the A2C2 element include an airspace utilization and situation map and status boards and charts. Information is keyed to the CCIR. Matters pertaining to airspace use, or requirements of forces for airspace use, must receive prompt attention by the A2C2 element and the current operations cell. Because commanders can employ air assets with a relatively short lead time, coordinating and integrating airspace requirements with the ongoing ground battle requires immediate attention. Current operations actions are also required when--
- Conflicts develop in the DRA.
- Corps directs a specific operation such as a deep operation.
- Changes to the corps OPORD affecting the use or uses of airspace are a response to the tactical situation.
- Conflicts cannot be resolved at a lower echelon.
The division A2C2 element maintains data on ATS facilities, current and planned restrictive measures, and special joint use requirements. It recommends solutions to the G3 for conflicts that command guidance, orders, and SOPs cannot resolve. The division A2C2 element also maintains data on the AD situation for use by other TOC elements. The G2 and AD channels provide data on hostile air activity to the A2C2 element in the main CP. The A2C2 element assists the commander by making recommendations concerning the impact the ADA weapons control status will have on air operations.
The supporting ATS unit and the A2C2 element develop plans for ATS assistance to aircraft within the AO and to units conducting tactical operations. The ATS units operate under control of the G3. The ATS unit supporting the division is linked with the A2C2 system, the host nation ATS, and the TACS. The ATS system supports aircraft of other units and component forces operating in the division AO. It also supports aviation brigade units conducting tactical operations, and is the interface between aircraft in flight and the A2C2 element at the main CP.
Electronic warfare is the means through which the division commander protects his own electronic systems while attacking those of the enemy. It exploits, disrupts, and deceives the enemy C2 system. It also protects friendly use of communications and noncommunications systems. This enhances the agility and initiative of the division, while limiting that of the enemy. The three functions of EW are--
- Electronic support measures (ESM).
- Electronic countermeasures (ECM).
- Electronic counter-counter measures (ECCM).
Electronic support measures are an intelligence-producing function to support ECM; ECM is a nonlethal attack means; and ECCM is an element of force protection. Electronic warfare may be offensive or defensive, is an essential element of combat power, and occurs during both offensive and defensive operations.
Electronic support measures and ECM are offensive components of EW. Electronic support measures search for, intercept, locate, and identify sources of radiated electromagnetic energy. They produce combat information for ECM, fire, maneuver, or threat avoidance. Electronic countermeasures prevent or reduce the enemy's effective use of electronic systems through jamming and electronic deception.
Electronic counter-countermeasures are the defensive portion of EW. They protect the friendly use of the electromagnetic spectrum and location of critical installations and systems. They consist of anti-ESM and anti-ECM. Anti-ESM prevents the enemy from intercepting, locating, and identifying friendly electronic systems. Anti-ECM precludes jamming or electronic deception of friendly forces.
Roles and Relationships
The G3 integrates and synchronizes EW into division operations. The EW staff officer, located in the FSE, is responsible to the G3 for planning and coordinating EW. He is specifically responsible for planning and coordinating ECM. He coordinates ESM requirements with G2 operations and ECCM requirements with the ADSO. He coordinates electronic deception and integrates it into the deception plan. He is responsible for preparing both the EW estimate and EW annex to the division OPORD.
The G2 has staff responsibility for conduct of ESM. The G2 operations plans, coordinates, and integrates ESM in division operations. He coordinates ESM requirements with the EW staff officer and the TCAE of the MI battalion.
The SIGINT/EW officer in the ASPS conducts the EPB in coordination with both G2 operations and the TCAE. He also coordinates guarded frequencies with the EW staff officer to preclude their jamming.
The TCAE maintains the status of EW assets, collects technical data in support of EW, and assesses the effectiveness of division EW operations. The TCAE also conducts the mission management of EW assets.
The division signal officer is responsible for ECCM. The ADSO, located at the main CP, plans, coordinates, and integrates ECCM in division operations. He coordinates with the EW staff officer, G2 operations, and G3 operations to determine and disseminate taboo and protected frequencies and identify negative effects of ECM on division operations.
The division FSCOORD in the FSE integrates ECM into the division FS plan. He coordinates with the EW staff officer to ensure ECM use is consistent with the division commander's concept and intent for fire support and the capabilities and availability of ECM assets.
Planning Considerations
The EW staff officer, G2 operations, ASPS, TCAE, and ADSO consider EW priorities as they plan and coordinate EW in support of division operations. Priorities include protection of friendly C3 systems, attack of critical FS capabilities, degrading of (or locating for destruction) enemy critical AD elements, and disruption of his critical C3 links.
Planners must also consider the following. In ECM, they consider target link distances (distance between the enemy transmitter and receiver), distance between the jammer and enemy receiver, radio line of sight, antenna polarization, jammer power and enemy transmitter power, bandwidth compatibility, and terrain, weather, and vegetation. In ESM, they must consider system accuracy and distance to the target. A minimum of three lines of bearing (LOBS) is required to accurately locate a target through direction finding. Planners must consider enemy capability to conduct electronic deception against the division. In ECCM planning, they must consider the protection inherent in the division communications equipment and procedures, enemy capabilities, and division capability to quickly locate and attack enemy jammers.
The G3, G2, and FSCOORD coordinate the planning of division EW operations. Based on the division commander's planning guidance, the G2 recommends the task organization of IEW assets to the G3. This task organization incorporates support to division deep, close, and rear operations as well as to committed maneuver brigades. The task organization incorporates ESM support to situation and target development and to ECM, and ECM targeting according to the division's HPTL and attack guidance matrix. The ADSO conducts ECCM planning. Planning begins with identifying essential friendly emitters and sensitive communications to protect. Friendly electronic emitters, signatures, and profiles are evaluated based on their vulnerabilities to enemy radio electronic combat and SIGINT capabilities. ECCM are then planned to overcome these vulnerabilities.
The G2 integrates ESM planning in the overall IPB process. While both terrain and weather both impact on friendly and enemy use of the electromagnetic spectrum, ESM planning begins during the threat evaluation phase of the IPB process. The ASPS in the main CP conducts an EPB. This process identifies the electronic template of the enemy force, is part of the overall situation development, and is the initial step in developing ESM support requirements for ECM.
ESM assets confirm or deny the EPB. This supports development of situational, event, and decision support templates during the threat integration phase of the IPB process. The EW staff officer and the TCAE also use this information to identify and plan targets for attack by ECM.
Electronic countermeasures planning incorporates the results of IPB and EPB into the commander's concept and intent through the targeting process. HPTs are identified for ECM, The staff officer identifies HPTs, and uses the HPTL, attack guidance matrix, and division synchronization matrix to plan the attack. He coordinates ECM taskings with the TCAE, FSE, G3 operations, and signal officer.
The EW staff officer coordinates with the TCAE to ensure assets are properly positioned and available to accomplish ECM taskings. He coordinates with the FSE to ensure ECM targets are valid and require attack. He coordinates with G3 operations to ensure ECM targets are attacked according to the synchronization matrix. He coordinates with the signal officer to ensure ECM targets are not on the protected, or guarded frequencies, list. This ensures ECM operations do not interfere with friendly operations or target frequencies that are providing significant intelligence.
The EW officer also coordinates with the G3 and ADSO in the main CP to plan EW support of deception operations. At division level, electronic deception consists primarily of manipulative or simulative electronic deception. Manipulative electronic deception alters the friendly electromagnetic profile or deliberately transmits false information. Simulative electronic deception simulates nonexisting units or capabilities or units and capabilities at false locations.
The ADSO conducts ECCM planning at the division level. Threat evaluation and integration during the IPB process indicate the enemy's capability to conduct radio electronic combat against the division. The ADSO, in coordination with the G3, determines critical friendly emitters to protect. He plans ECCM to protect them through assignment of taboo and guarded frequencies; frequency allocation; use of meaconing, intrusion, jamming and interference (MIJI) reports; terrain masking; and attack of enemy jammers.
Electronic warfare planning differs little between offensive and defensive operations. The primary difference is proximity of systems to the FLOT, Figure 5-29, and Figure 5-30, portray typical offensive and defensive EW arrays. In both the offense and defense, EW assets are employed as part of MI company teams and leapfrog from position to position to maintain coverage.
An Example
The division receives a warning order and corps OPORD to conduct an attack as part of a corps operation. The G2 continues to update the IPB as part of the preparation for the attack. The IPB, and the division commander's restated mission and planning guidance, are the bases for developing the concept of operations and commander's intent.
During the IPB process, the ASPS developed an EPB which identified critical enemy communications and noncommunications emitters, capabilities, locations, and supporting technical data. The G3, G2, FSE, and signal officer integrate this information into the division OPORD.
The G2 identifies enemy units, locations, dispositions, and probable COAs through the use of ESM. He verifies them through other intelligence assets. This precludes the enemy from deceiving the division through electronic deception.
The G3, with the G2 and FSCOORD, determines the HPTs and attack guidance which the commander approves. During the decide phase of the targeting process, the G3, with the EW staff officer, FSE chief, and G2, determines that the enemy division's system for FS and AD are HPTs. The G3 also determines ECM will be part of FS means during the attack. He provides this decision to the EW staff officer to plan and coordinate ECM with the G2, FSE, and signal officer.
The EW staff officer coordinates with the G2 ASPS and TCAE to ensure required technical data is available to support the ECM missions. If not, the EW staff officer ensures ESM collection tasks are planned and conducted to provide this data. He coordinates with the FSE to plan the ECM attack in conjunction with other FS assets. The EW staff officer also coordinates with the signal officer to ensure that frequencies to be jammed are not taboo, protected, or guarded and ECM will not impact negatively on friendly operations.
The G3 develops a deception plan during the development of the division's attack plan. The EW staff officer, with the battlefield deception element and ADSO, develops the electronic deception portion of this plan and includes it in the deception annex to the division OPORD. This plan consists of simulative electronic deception to assist in the portrayal of the division main effort in a false location.
The ADSO coordinates with G2 ASPS and determines the enemy's capability to conduct EW against the division. He reviews the division and MSC CP locations to determine their susceptibility to jamming and recommends alternate locations for those that are high risk. He coordinates with the G2 and FSE chief to expeditiously locate enemy jammers and engage by lethal attack those having a significant impact on division operations.
The FSE chief and EW staff officer identify the timing and sequencing of ECM targets to maximize attack effectiveness by massing both lethal and nonlethal attack assets. The FSE provides the EW staff officer an execution matrix to assist him in the coordination, timing, and synchronization of ECM assets with the TCAE.
During the attack, the G3 ensures synchronization of EW with the overall plan. The EW staff officer monitors and informs the G3 of the status of EW assets and actions. He also monitors current operations and coordinates positioning and tasking of ECM assets with the TCAE. He ensures ECM assets are properly positioned to attack targets according to the scheme of maneuver and the FS plan.
The G2 ensures ESM assets are available and in position to support the situation and target development and provide ESM support to ECM. The ASPS EW and SIGINT officer coordinates requirements with the TCAE and G2 operations cell. The FSE chief coordinates with the EW staff officer. This ensures all ECM assets engage targets according to the execution matrix. The ADSO monitors the status of friendly communications. The intelligence system locates enemy jammers that are negatively affecting the division's communications and provides them as targets to the FSE for engagement by lethal attack.
Deception is an important combat multiplier. It enhances the conditions which allow the commander to effectively mass forces at decisive times and locations. It should be a consideration in every division operation.
The ultimate goal of division-level deception operations is to manipulate enemy behavior and create opportunities for exploitation. Battlefield deception enables the commander to conduct economy of force operations, mass at a decisive point, and conserve and protect the force. Well-planned and executed deceptions, not luck, achieve surprise and its benefits.
Planning Considerations
Deception operations cannot be planned independently of tactical operations. The primary consideration in any deception is the corps mission and deception plan. Deceptions, whenever possible, should be centralized. Like missions and OPORDS, deception must be synchronized from the top down. Failure to do this can result in wasted combat power and possible disaster. Higher and, when necessary, adjacent headquarters should be aware of division deception operations. Failure to coordinate can damage other units' operations or deceptions.
A deception must be plausible. The enemy must believe the division's actions are in accordance with its doctrine and the division can do what the deception indicates. Enemy intelligence collection channels must be fed information in a coordinated redundant effort. The division may have to pass the same information repeatedly through multiple channels to ensure the enemy collects the deception. The enemy must see a picture consistent with our capabilities and his beliefs.
Deceptions should be adaptable and flexible. As the plan changes, the deception may also be forced to change. The division must portray the deception for as long as it is feasible and beneficial. For this to happen, the overall plan, including the deception, must have built-in flexibility.
Integration is vital to successful deceptions. A deception must not only be part of the overall plan, it must extend into the plan's every facet. That is, aside from being part of the operations, it must be part of the logistics, FS, AD, signal, and engineer portions as well.
The division can expect the enemy to know its norms. The enemy will seek to find where the division places class I, III, and V depots, for example. He will look for medical treatment and maintenance facilities, and FS units. These signatures provide him a basis for true intent. Without full integration into all plans, the deception will quickly lose credibility.
The target of any deception is the enemy decision maker. He has the authority to react to the deception. It does no good to design elaborate deceptions if the enemy is incapable of either collecting, analyzing, or reacting to the information, or if the deception is contrary to normal operating procedures.
Feedback is important in any deception. Means to verify the deception must be established. The division's normal intelligence infrastructure or specially established means can normally accomplish this. It may not always be possible to verify the deception, and for this reason, all plans, including deception plans, must be flexible.
Finally, the division must consider cost of a deception in terms of resource expenditure. For a deception to appear real, the division must dedicate adequate resources. The cost depends on the type of deception (demonstration, display, feint, or ruse) and its objective. The division must also measure costs in risk and flexibility. For example, it may be very risky for the success of the division's main effort to rely solely on the success of a planned demonstration. Should the demonstration not produce the expected enemy reaction, it could cause the main effort to fail. Flexibility is built into the plan by using branches, sequels, or executable deceptions.
The goal of any deception is to cause the enemy to act contrary to his interests and beneficial to the division's. The division's goals are to--
- Condition the target's beliefs.
- Influence the target's actions by misleading him and persuading him to adopt a specific course of action.
- Benefit from his actions through surprise, superior combat power, and improved survivability.
The five components of battlefield deception are the objective, target, story, plan, and event. The objective is what the division wants the enemy to do. The target is the enemy decision maker. The story is what the division portrays to the enemy. The plan is the concept of how the story is portrayed. Events are specific actions performed as part of the plan. Since deception is inherent in planning and concurrent with current operations, the division G3 has overall responsibility for deception (with support from other staff agencies).
If the intent is to induce the enemy to do something the division can exploit, the commander and staff must address deception early in the planning process. Deception designed after the division has developed, wargamed, and decided on a COA is wasted. It becomes an afterthought, ill planned because of lack of time, and ill resourced because all division assets have been allocated in the war game of the chosen COA.
In providing his deception guidance, the division commander should consider--
- What he wants the enemy to do.
- How the division can best make the enemy do it.
- What forces and material will be dedicated to the effort.
- What enemy behavior is expected.
- How the division can benefit from that behavior.
These guidelines require the deception to do more than just alter or reinforce enemy perceptions. It must manipulate enemy behavior and then exploit it.
The staff uses this guidance to develop a deception plan or COA in the same manner as it develops and analyzes other COAs. The G2 provides normal input, identifying enemy weaknesses and vulnerabilities, and enemy collection assets that can detect the deception. Done properly, a deception should be part of a COA. Like any COA, deception development must involve the entire staff with OPSEC measures developed and implemented.
Operations Flexibility
Operations flexibility is a technique the division uses to plan and prepare for two or more related COAs, rather than optimizing one. This inherently builds flexibility into the operation. It causes the enemy to become vulnerable to manipulation and exploitation. The division selects one COA for execution and another related COA for portrayal to the enemy. Both COAs (one shown and one hidden) seek to obtain a specific reaction. Thus, if the enemy reacts to the visible (deceptive) COA, the concealed COA will be able to exploit him.
Conversely, if the enemy rejects the visible COA, reacting instead to the concealed COA or yet another, the division may still be able to exploit him by executing the visible COA. The key to this type of deception is that no matter what the enemy does, whether he reacts to the deception or not, the commander still has an executable COA. This technique differs from a demonstration or a ruse, which normally lack any significant combat power and are not usable for exploitation.
The deception process relies greatly on signature management. Signature management is the use of--
- Deception assets (decoys, dummies, and signature replicating devices) to augment or mask signatures.
- OPSEC assets and techniques to diminish signatures.
- Real assets and techniques to augment or diminish COA signatures.
In short, it is the selective management of key activities to directly or indirectly control the enemy's behavior.
The division uses signature management to reduce the visibility of key activities associated with the COA it intends to execute (the COA it wants to hide). It does this through the judicious use of OPSEC techniques and assets and in the manner it conducts its real operations. For instance, a reserve force for the intended COA may go to radio silence or coordinate a passage of lines face to face. This may hide the existence and intent of the unit. An engineer unit might lay a deliberate minefield at night. Logistics supply points might be hidden in a built-up area. These techniques reduce signatures and avoid detection.
Simultaneously, key signatures associated with the deceptive COA are highlighted through more visible activities. For example, the reserve force mentioned above could support the deception COA. It could coordinate a passage of lines along a major avenue of approach via radio. Logistics supply points could be poorly camouflaged or even left out in the open. Dummy logistics assets, such as blow-up rubber 55-gallon drums, or empty ammunition crates, can augment the signature. The engineer unit may lay a hasty minefield during daylight hours with soldiers and equipment, or in some other manner designed for enemy detection.
In the end, operations flexibility gives the division commander an inherently deceptive OPLAN and enhances his ability to execute it on the battlefield. It requires the commander's guidance on deception early in the planning process. It requires a coordinated staff effort, including war gaming.
Deception Execution
All staff agencies, but especially the G2 and G3, must carefully control and monitor deception execution. For this purpose, the corps battlefield deception element can be extremely helpful.
The corps may attach members of the battlefield deception element to the division. They may operate as a team, split team, or single person configuration across the AO. They advise and assist units on the deception execution. They may also function as the eyes and ears for both the G3 and G2. They can assist the G3 in timely and proper execution of deception events. They may also help provide the G2 intelligence on enemy reactions to the deception.
At times, the corps battlefield deception element may assist the division by becoming a part of the deception. Resource availability within the division, or the lack thereof, may require the division to request it to provide people and assets to replicate C3 signatures. The corps battlefield deception element has the capability to do this; however, it should be used only as a last resort. Its primary responsibilities are planning, monitoring, and assisting; its personnel and equipment assets are limited.
To properly evaluate deception activities, the division must determine their impact on the enemy. This requires reliable feedback, an important aspect of any deception. Without feedback, the division can never be confident the enemy decision maker is intentionally reacting to the deception in ways contrary to his better interest. The division G2 plays a major role in this regard.
The division obtains the necessary feedback in one of three ways. It can use its already established intelligence gathering infrastructure, or it can establish a special means with which to collect information about the deception. This involves using many of the same assets used routinely to collect intelligence, the difference being the focus of the effort. It can also use a combination of the two methods above. In any case, the division must obtain reliable feedback to determine if the deception is working or has been compromised, or if the plan requires adjustments to improve its effectiveness or plausibility.
The division may require only a reasonable assurance that intended signals reached the decision maker and had their intended effect. This will not always be possible to confirm. The division must rely on information available and knowledge of the enemy to determine his reaction to the deception. However, if the plan is flexible, the criticality of feedback is somewhat lessened. This is not to say feedback then becomes unimportant. It is always one of the most important aspects of deception.
The termination of a deception can be as critical as its execution. The concept of playing out the deception should be a double-edged sword for the enemy. The division should continue the deception for as long as possible with the intent of never allowing the enemy to know he has been deceived, or phase out the deception in such a manner that the enemy views it as a perfectly plausible activity. If the enemy discovers the deception for what it is, he may become the exploiter instead of the exploited. He may also review the signals he received throughout the operation and view them skeptically, reducing the division's ability to deceive him in future operations.
The enemy may employ tire support to create opportunities for maneuver forces to exploit. The division should establish conditions for decisive combat maneuver through destruction of the enemy's FS system.
Counterfire consists of fries targeted throughout the battlefield that attack the enemy's entire FS system. Counterfire assists the division to achieve and maintain agility and initiative. It gains freedom of action and protects the force. It also deprives the enemy of freedom of action.
The division commander must realize that counterfire is not solely the responsibility of the division artillery commander. Counterfire requires integration of intelligence, fire support, and maneuver. It is a concurrent operation the division commander and staff must coordinate and synchronize within the framework of the offensive or defensive mission.
Components of Counterfire
Counterfire maybe proactive or reactive. Proactive counterfire is the detection and attack of enemy nonfiring, as well as firing, systems before they engage friendly forces. It is linked with the targeting effort. Reactive counterfire is, as the name implies, a response to the enemy's engagement of the division.
Proactive counterfire requires the intelligence system to identify, locate, and accurately target elements of the enemy FS system. The corps normally conducts the proactive portion of counterfire. It has the intelligence and attack systems to identify, locate, and attack the enemy's fire support before its commitment, arrival, and employment against the division. Still, the division may conduct proactive counterfire against enemy FS systems within range of organic and supporting intelligence and FS systems.
Reactive counterfire requires integration of intelligence, target acquisition, FS, maneuver, and C2. The intelligence system must use the IPB to predict likely locations of enemy FS systems. Using this prediction, the division positions and tasks intelligence sensors and target acquisition assets to confirm the IPB and provide target information. Fire support assets engage enemy FS systems on the basis of this information. Maneuver elements provide information from reconnaissance and surveillance. They also may engage enemy target acquisition assets located on or near the FLOT. The C2 system provides the reporting network for counterfire and identifies priorities for protect ion of the force.
Roles and Relationships
The division commander is responsible for counterfire throughout the division AOR. His counterfire responsibilities include--
- Developing, planning, and describing his vision, concept, and intent for counterfire within the total division mission.
- Segmenting the battlefield through maneuver boundaries or assignment of AORs. This delineates responsibilities for counterfire within the division zone.
- Prioritizing the counterfire effort within the division's zone.
- Allocating resources within the context of the overall division mission.
- Synchronizing the division counterfire effort.
The division has a more reactive counterfire focus than the corps. The division also requires greater emphasis on rapid execution of counterfire.
Within the division, key staff members for counterfire operations are the G2, G3, and DFSCOORD. The G2 develops and updates the IPB, tasks sensors and units to acquire target information, and disseminates information to the G3 and FSE. The G3 integrates and prioritizes Counterfire into the concept of operations. He allocates resources in the context of the overall mission. The DFSCOORD integrates Counterfire into the division's FS plan.
The engineer and G4 are also involved in the counterfire process. The engineer may be required to provide survivability support to the artillery. The G4 orchestrates class V support for the FS systems, including attack helicopters.
Planning Considerations
Division planning considerations for counterfire include--
- The corps counterfire plan.
- Capabilities of friendly and enemy fire support.
- Capabilities of friendly and enemy target acquisition.
- Command and control capabilities.
Division must understand its role within the corps counterfire plan. The corps counterfire plan is defined through the corps commander's concept and intent. Corps FS and artillery support plans further define corps and division roles. Corps delineates responsibilities, establishes priorities, and allocates resources based on the corps mission and the part Counterfire plays in the mission.
Within the division, the first Counterfire consideration is the enemy's capabilities. The G2 provides this information as part of the IPB and targeting process. These considerations include the enemy's mission, and whether the division is facing the enemy main effort. Both impact on the division's counterfire requirements and plan. His considerations are not only enemy mortars and artillery, but also enemy electronic warfare, and fixed- and rotary-wing assets. He includes ranges, echelon, and types of artillery in the estimate. Less counterfire is required against towed artillery than against self-propelled artillery. Range and echelon affect not only the enemy's capability to engage the division in depth, but also where the enemy positions his artillery on the battlefield.
Munitions capabilities of the enemy FS system are also a consideration in the counterfire planning. Weapons that fire improved conventional munitions are a greater threat than those capable of firing only standard high explosive (HE) munitions.
The G3 and DFSCOORD must consider the capabilities of friendly weapons systems. The corps 155-millimeter and corps 203-millimeter howitzers can fire 30 kilometers with RAP munitions. However, these munitions don't have the effectiveness of the dual-purpose improved conventional munitions (DPICMs). The DPICM's maximum range is 18 kilometers for the 155-millimeter howitzer and 23 kilometers for the 203-millimeter howitzer. The MLRS is normally the counterfire weapon of choice. It has a maximum range of 30 kilometers, but a minimum range of 8 kilometers. If it is positioned well forward to range deep into the enemy formation, it may not be capable of ranging counterfire targets on or near the FLOT.
Enemy target acquisition capabilities also impact the division's counterfire planning. The division must plan to attack and destroy enemy artillery reconnaissance elements and command OPs through an aggressive counterreconnaissance effort. The division also must strictly employ and enforce ECCM to negate or limit enemy direction-finding capabilities. If the enemy artillery target acquisition threat is great, friendly artillery must move frequently to survive. The division must locate and destroy enemy counterfire radars to enhance survivability of mortars and artillery.
Similarly, the commander and staff must consider the division's target acquisition capabilities. These capabilities include the Q-36 Firefinder radar, IEW systems, UAVs, forward observers, and COLTS employed with the maneuver forces. Each of these provides a different degree of accuracy and speed of targeting data. The division must also consider threats to each of these. For example, operations against an enemy with a sophisticated EW capability require cueing guidance for counterfire radars to preclude their identification, location, and destruction.
The C2 organization of friendly artillery is also a consideration. The division must decide whether to centralize or decentralize execution of counterfire by the artillery. Augmenting the division with a corps artillery and target acquisition detachment provides additional flexibility. Centralization facilitates massing of artillery and precludes duplication of effort. It also enhances use of counterfire radars, (See Figure 5-31.) However, centralization places a heavy burden on the headquarters responsible for executing artillery counterfire. If the division has a reinforcing corps FA brigade, it may be assigned to execute artillery-delivered counterfire (but the overall responsibility to execute the division's counterfire efforts still remains with the DIVARTY commander). This allows the corps FA brigade to focus on counterfire while the DIVARTY headquarters focuses on artillery support to committed forces.
Techniques
The corps should delineate counterfire responsibilities between the corps and division. This allows each echelon to focus on a specific area of the battlefield and prevents duplication of effort.
Counterfire planning begins with the targeting process during COA development and war gaming. The targeting cell identifies high-value targets and refines them into HPTs for the division. It recommends what targets to attack, how to detect and engage them, and how to determine the results (battle damage assessment). The targeting cell does this as part of the total targeting process of the division and not as a separate action.
Generally, the division conducts reactive counterfire against enemy mortars and artillery. The corps normally engages enemy artillery and other FS assets. However, maneuver brigades may have counterfire responsibility against mortars and artillery of committed regiments, while the division conducts counterfire against enemy division artillery.
The commander prioritizes counterfire targets within the division zone. Normally, enemy fire support facing the division's main attack or main defensive effort will receive the priority for counterfire. However, when the division employs a unit in an economy of force role, it may receive priority for counterfire.
Once the commander decides what to attack with counterfire his staff can plan how targets will be detected. Again, the IPB process is the first step. Using the situational and event templates from the IPB process, the G2 and FSE focus IEW sensors and target acquisition assets on likely positions of enemy tire support. The division may use the engineer terrain team or TerraBase software to develop visibility diagrams. 'These are used to position observers or assistant fire support officers (AFSOs) to observe enemy artillery positions and request fire against them.
The staff may use these same templates and diagrams to position and orient counterfire radars and GSR. The counterfire radars identify and provide locations of mortars, artillery, and rocket units as they are tiring. Call for tire zones should be established in the counterfire radars around likely enemy firing positions. Ground surveillance radars may provide combat information on enemy firing units occupying likely firing positions. They also may provide a degree of battle damage assessment indicating units are displacing after a likely firing position has been engaged. They also may cue other target acquisition assets such as the AFSO.
Similarly, with direction finding, ESM assets may locate key FS headquarters for lethal attack or jamming. ESM assets also may be used to identify and locate artillery reconnaissance elements or command OPs as part of the division counterreconnaissance effort.
The division uses a variety of techniques to execute counterfire. One, the counterfire program, is used when there is little movement of enemy fire support assets and sufficient time available to identify, locate, and target them. It is used to disrupt enemy fire support systems at critical times, such as during a counterattack or a penetration.
Another technique is strictly reactive counterfire. This involves attacking enemy FS assets during or immediately following enemy engagement of friendly forces. A cueing agent normally initiates this technique. He directs the counterfire radar to radiate, acquire the target, and transmit a fire mission to its reporting headquarters.
The use of counterfire radars requires several decisions. First, the division examines the threat to decide if radars will operate in a continuous or command-cued manner. If threat of acquiring the radars is low, then the commander may direct continuous cueing. If the threat is high, the division normally employs command cueing. Command cueing requires cueing agents to direct the radar to radiate. These agents are normally battalion or brigade FS officers, but may include FIST chiefs or even individual forward observers.
The controlling headquarters assigns zones of search to individual radars. Each radar may establish up to nine zones of search. These zones are--
- Critical friendly zones (CFZs).
- Call for tire zones (CFFZs).
- Artillery target intelligence zones (ATIZs).
- Censor zones.
The CFZs are established around the highest priority friendly locations. Typical CFZs include maneuver assembly areas, headquarters, and other troop concentrations. The CFZ provides the most responsive priority of fires from radars.
The CFFZs designate locations beyond the FLOT that are likely enemy artillery or mortar positions. Enemy fires from a CFFZ result in the second most responsive priority of fires from the radar.
The ATIZs allow the commander to monitor a likely enemy firing position, but give higher priority to other locations. Enemy fires from within an ATIZ may be evaluated for attack, but do not automatically generate a fire mission as do the CFZ and CFFZ.
Censor zones designate areas from which the commander does not want to attack targets. This zone is often used to prevent overlap and duplication.
Counterfire radars may be digitally linked to one of several artillery headquarters. One technique is to assign a Q-36 radar to each DS artillery battalion. This provides the maneuver brigade commander a reactive counterfire capability he would not otherwise have. It allows the brigade commander to orient the radar and establish zones of search that best support his concept of operations. Concurrently, the two Q-37 radars may be linked to DIVARTY headquarters to provide reactive target acquisition at division level. The division may use this technique if maneuver brigades have the counterfire responsibility against regimental artillery and mortars.
A second technique is to have all counterfire radars report to DIVARTY headquarters. This allows DIVARTY to centrally command and control radars and artillery counterfire It also enables DIVARTY to maintain continuous coverage of the division sector by leapfrogging counterfire radars. However, the complexity of this technique may cause DIVARTY to lose visibility of other functions. Additionally, if the division does not have sufficient GS or GS-reinforcing artillery, then radars may quickly overload available artillery at division level.
Counterfire radars may report to a reinforcing artillery brigade, if one is assigned. This allows DIVARTY to monitor counterfire execution while focusing on its other functions. Even if the reinforcing artillery brigade has the counterfire mission, the DIVARTY commander maintains overall responsibility. He augments the reinforcing FA brigade with assets from the target acquisition battery to enable the FA brigade to accomplish this mission effectively.
The division may employ maneuver forces against enemy FS systems. This may include use of small maneuver elements to engage reconnaissance, surveillance, and target acquisition elements (such as artillery reconnaissance or command OPs). The division may employ attack helicopters against artillery groupings at regiment, division, or army level.
The division may employ a joint attack of artillery. This is similar to a JAAT but is targeted specifically against enemy artillery.
The division may employ a mix of these techniques. (See Figure 5-32.) Ground maneuver forces may attack target acquisition elements while EW assets jam key fire support nets. The division may use mortars against target acquisition assets or fire direction centers (FDCs) while artillery, attack helicopters, and CAS aircraft engage artillery.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|