Appendix F
AUTOMATED FDC
While the means of technical fire direction is different, the basic operation of an automated FDC is similar to that of a manual FDC.
F-1. Personnel
Duties of the FDO and chief fire direction specialist are the same as in a manual FDC. The equivalent USMC billet description is operations chief.
a. Senior Fire Direction Specialist. The senior fire direction specialist (computer)operates the computer that is the primary means of determining firing data. He is responsible for the transmission of fire commands(voice or digital) to the howitzer sections. The equivalent USMC billet description is operations assistant.
b. Fire Direction Specialist(USMC--Fire Control Man).
(1) Recorder. The recorder maintains the record of fire, recording information as directed by the FDO. The recorder may also be required to operate the computer that is the backup means of determining firing data.
(2) HCO and VCO. The HCO and VCO maintain a firing chart and follow each mission. The HCO and VCO check the coordinates on the firing chart and provide target altitude as required. The HCO and VCO maybe required to operate the backup computer as well.
F-2. Fire Order
The FDO considers the same factors when determining a fire order in an automated or manual FDC. The order in which the fire order is announced and the elements of the fire order are also the same. The biggest difference between the fire order for an automated FDC and for a manual FDC is the SOP. On the basis of the computer's ability to determine individual piece firing data and the computer programs, certain elements would be standardized differently.
a. Adjusting Element/Method of Fire of the Adjusting Element. On the basis of the computer's ability to compute firing data based on individual piece locations, muzzle velocities, and aimpoints, the use of base piece is not necessary (a base piece should be selected for ease of transition from automated to manual). Depending on the computer's programming, it may automatically select an adjusting piece in sequential order, or the operator may have to input an adjusting piece. Method of fire of the adjusting element would be included in the SOP, which may or may not be a programmed computer default.
b. Basis for Corrections. The SOP for this element should reflect the primary means of computing firing data.
c. Distribution. As in a manual FDC, the observer or FDO will announce the sheaf to fire. In a manual FDC, the normal sheaf is parallel. In an automated FDC, the normal or default sheaf will be the default sheaf programmed into the computer.
d. Ammunition Lot and Charge. The SOP for this element will allow the computer to select the lot and charge to fire on the basis of its programmed selection routines. Safety constraints, availability of registration corrections, and muzzle velocity information, are additional considerations when determining the SOP.
e. Target Number. The SOP for this element is normally the next available, as in manual gunnery. The computer may or may not be programmed to automatically assign a target number.
F-3. Fire Commands
Fire commands for automated gunnery are exactly the same as for manual gunnery. Depending on the computer systems in use, fire commands may be transmitted by voice or digitally.
F-4. Establish a Manual Backup for Automated Operations
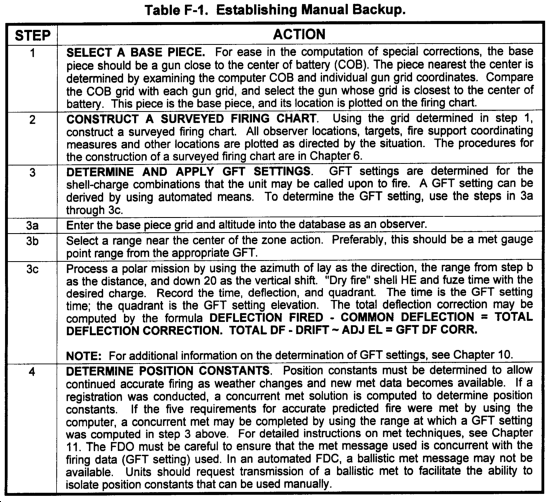
a. Concept. The manual backup should be set up to allow the automated(BCS and BUCS primary)FDC to continue operations should the computers fail. Manual backup should be established as a form of "position improvement" and should not impede setup or processing with automated means. The manual backup also serves as a basis of rapidly "checking" the automated solution. The basis for the manual backup is that a piece will be designated as the base piece. The location of this piece is plotted on the firing chart. GFT settings are derived by using this piece and reflect its muzzle velocity and TGPCs. Once the FDC converts from automated to manual operations, all adjustments are conducted with the base piece. All ranges are measured from base piece to the center of the target and all data computed reflects base piece muzzle velocity and location. When the observer requests fire for effect, the adjusted data from base piece is converted to data for the remaining pieces by applying special corrections, or terrain gun position corrections. These corrections take into account the differences in piece locations(displacement)and the differences in shooting strength(comparative VEs). TGPCs can be determined by using automated means or the Ml7 plotting board.
b. Establishment of the Manual Backup. The manual backup is established in five steps as follows:
- Select a base piece.
- Construct a surveyed firing chart.
- Determine and apply GFT settings.
- Determine comparative velocity errors for the remainder of the guns.
- Determine position constants.
Table F-1 elaborates on these steps.
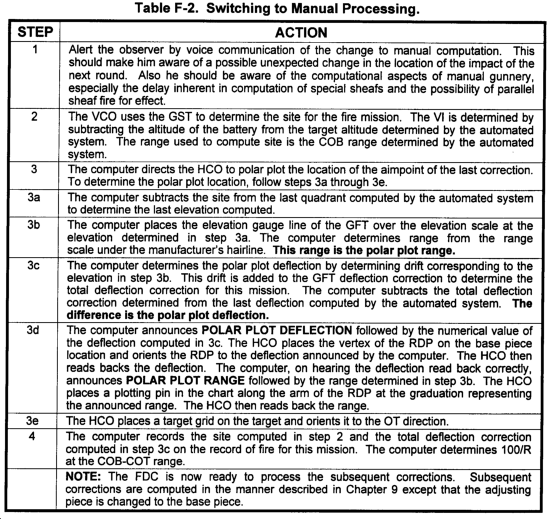
F-5. Convert a Mission in Progress From Automated to Manual Processing
a. General. Should automated means fail, a battery must continue to process fire missions. With a manual backup established, the FDC continues operations with minimal delay.
b. Procedure. If during the processing of a fire mission the computer fails, the mission is switched to manual processing. If the observer's total corrections are applied to the firing chart, a significant difference in point of impact in the target area may be noticed because of the difference in automated accuracy. To make the transition as smooth as possible, the steps in Table F-2 are used.
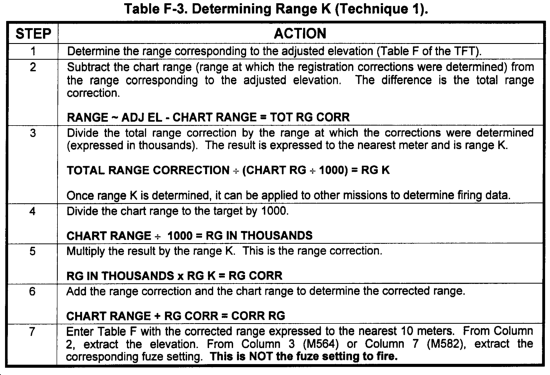
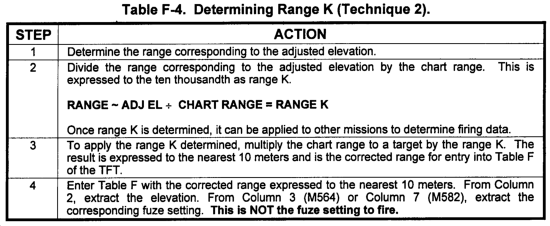
F-6. Range K and Fuze K
a. The proportion of correction to range and fuze setting that results from a registration or the solution of a met message is referred to as range K or fuze K. Once determined, range K and fuze K may be used to apply the determined corrections at lesser or greater ranges than that at which the corrections are determined. This procedure allows the application of a "GFT setting" to a TFT.
b. Range K can be determined and applied by using two techniques. These techniques are discussed in Tables F-3 and F-4.
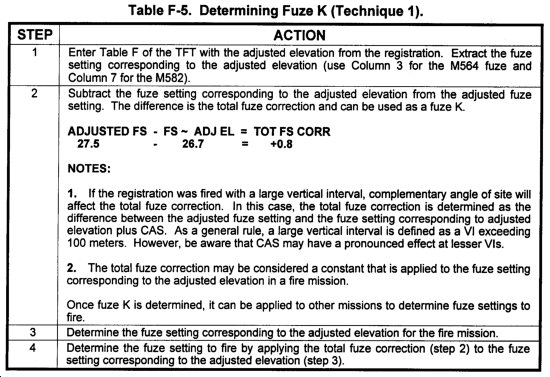
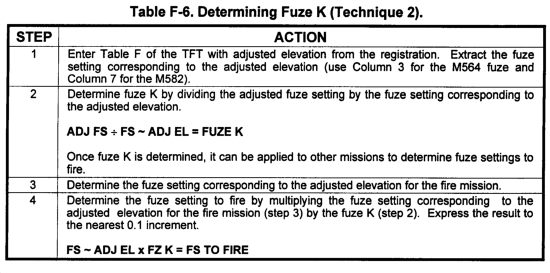
c. Fuze K can be determined and applied by using two techniques. These techniques are discussed in Tables F-5 and F-6.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|