Chapter 3
Offensive Operations
The offense is characterized by violence, concentration of friendly forces, disruption of hostile forces, and rapid transitions between different types of operations. Smoke and obscurant use multiplies the commander's ability to project combat power at the critical time and place to defeat the enemy. Smoke and obscurant use will support any type of offensive operation at any level because smoke generally favors the attacker.
Historical Perspective
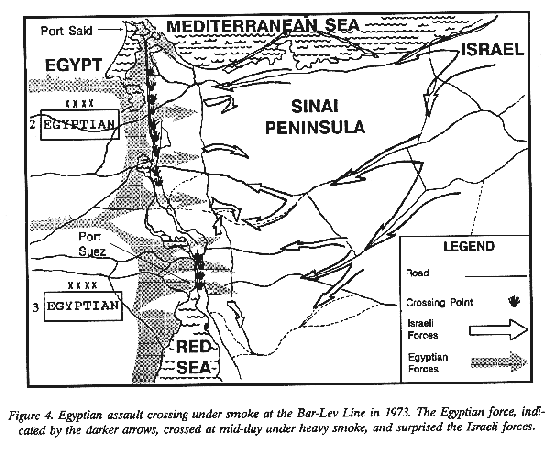
The most recent and perhaps most significant example of smoke in a combat multiplier role occurred during the 1973 Arab-Israeli War. On 6 October 1973, at 1400 prepared Israeli positions defending the west bank of the Suez Canal. The Egyptians initiated the attack by deploying 200 attack aircraft into the Sinai to destroy Israeli communications centers, airstrips, and artillery positions (Figure 4). Within moments, Egyptian artillery opened up with a massive barrage of high-explosive munitions and hours, Egyptian forces attacked blinding smoke. The Egyptians intended to degrade the ability of the Israelis to engage targets and adjust artillery fire with that blinding smoke. It accomplished its purpose with devastating results; it induced a feeling of total isolation among defending Israeli units. The fear caused by the addition of yellow smoke to the artillery preparation amplified the psychological effects of isolation. The defenders believed they were being gassed.
Minutes later Egyptian armored and artillery assets began to deploy forward to firing positions on their side of the canal. These units engaged the Bar-Lev strongpoints with direct fire while infantry units conducted a forced crossing in dinghies under the cover of canister-generated smoke. Air-mobile operations placed commando units 10 miles into the rear to disrupt reinforcing echelons. Egyptian engineer units emplaced bridges over the canal. Smoke from artillery, canister, and smoke generator assets supported the engineer effort.
These actions demonstrated the tremendous impact of smoke when synchronized with a combined arms assault. Within the first 24 hours of the attack, the Egyptians accomplished the almost impossible: They had moved five divisions, 100,000 men, 1,020 tanks, and 13,500 vehicles across the canal and established a bridgehead six miles into the Sinai. The Israeli forces lost 150 tanks, almost one-tenth of their total in the Sinai. The blinding smoke placed on the Bar-Lev strongpoints effectively reduced the Israeli ability to acquire targets and spot for attack aircraft.
The Egyptian Army was eventually driven back and sustained considerable losses. Nevertheless, their forced crossing of what the Israelis believed to be the largest tank ditch in the world was a complete success. The effect that smoke played in that operation was significant. While the crossing may have been effective without smoke, the Egyptian forces could have sustained far greater casualties, and the crossing could have taken far longer to complete without the cover of smoke.
Tactics
The National Training Center (NTC) is an area where smoke training is possible on a large force-on-force scale. MG E. S. Leland, former commander of the NTC, stated, "Smoke is a far more significant battlefield factor than I used to believe. It simply must be a major planning consideration in terms of both friendly employment and reaction to enemy use."
Key insights from the NTC for the offense include the following:
- Smoke favors the attacker.
- Smoke tightens attack formations.
- We must capitalize on thermal imager capability.
- We must plan command and control without visual cues.
- Training and rehearsal are the keys to success.
Smoke and obscurants integrated throughout the offensive framework provide major contributions to combat power in deep, close, and rear operations. In the offense, use smoke to--
- Support maneuver by--
-Providing tactical surprise and allowing the commander to set the terms of combat.
-Allowing the commander to mass forces unobserved.
Defeating enemy surveillance efforts.
-Supporting the deception plan.
- Provide additional firepower by--
-Changing friendly to enemy force ratios by using thermal imagers and millimeter wave acquisition devices such as radars to see through visual smokes and using smoke to isolate defending and second-echelon forces.
-Defeating enemy counterreconnaissance efforts.
-Enhancing friendly target acquisition efforts by silhouetting enemy vehicles with smoke and using smoke and obscurants we can see through but the enemy cannot. Disrupting enemy maneuver and reinforcement.
-Disrupting the enemy's ability to communicate.
- Protect the force by--
-Reducing friendly force vulnerability by concealing support forces from enemy observation and defeating enemy reconnaissance efforts.
-Concealing obstacle breaching.
-Defeating enemy weapons by defeating enemy target acquisition efforts, defeating enemy guidance systems, and negating standoff capability of enemy long-range direct fire weapons.
-Degrading or defeating enemy directed energy weapons.
Use
Smoke and obscurant use in the offense requires careful planning and execution to prevent interference with movement, assault operations, or target acquisition; to retain the element of surprise; and to avoid silhouetting or drawing undue attention to friendly forces.
Smoke use is not without risks. Our use of smoke must increase friendly force survivability without seriously degrading operational capabilities. It must decrease Threat force command, control, communications, and intelligence gathering capabilities (C3I).
In addition to the general employment techniques detailed in Chapter 1, techniques to minimize interference in the offense include the following:
- Use covered and concealed maneuver techniques. Assume the enemy can see through the smoke. Do not take unnecessary risks with the force.
- Time smoke delivery with decision points. Conduct a thorough IPB and time your use of smoke to key decision points in your tactical plan: for example, "When we reach Hill 285, we will call for A Battery to fire smoke and HE onto target XY1007 and sustain that fire to obscure enemy observation of our flanking of Objective White."
- Use unobscured weapons to over-watch. The overmatching elements should have target acquisition devices such as thermal imagers that can see through our own smoke and engage the enemy. This prevents surprise and enhances the ability to suppress enemy fire during the assault.
- Do not let your own smoke silhouette your forces. Never overrun your smoke cloud prior to the final assault. "Walk smoke in" towards enemy positions wherever possible. This ensures your forces remain concealed and confuses the enemy as to your exact location and intent.
- Plan to engage through or around the smoke. Plan to use weapon systems that can acquire and fire through the smoke. Plan limited visibility positions for those systems that smoke degrades (for example, position target acquisition assets on flanks or above smoke).
- Plan for enemy countermeasures. Enemy forces will counter your smoke use. Plan to intensify your counterreconnaissance and air defense efforts. The enemy may use countersmoke to confuse your command and control, so avoid reliance on visual signals. The enemy will increase use of indirect fire weapons when direct fire target acquisition is ineffective. Therefore, plan artillery counterbattery and countersmoke fire after crossing the line of departure/line of crossing (LD/LC).
- Plan for additional maneuver time under smoke. Smoke slows maneuver. Base the planning factor on METT-T and the proficiency of your unit to operate under smoke as shown in previous combat (or training) operations. Verify enemy locations (responsibility of reconnaissance). The enemy can use both our smoke and theirs to conceal movement to alternate positions or to break contact. Aggressive reconnaissance before and during the engagement will allow you to shoot and remain in contact.
Goal
The main focus of smoke in the offense is to defeat enemy RSTA efforts, conceal maneuver and support forces, and contribute to tactical deception operations. Our intent is to deny the enemy information about the disposition and composition of our forces, which provides surprise and security. It also allows the commander the flexibility to mass the forces required to conduct attacks. The next section presents the tactics for using smoke in offensive operations. Appendix A contains tactical decision aids for determining which smoke delivery means to use against the specific smoke targets covered by these tactics.
Phases
The phases of the offense are preparation, attack, exploitation, and pursuit.
Preparation
The preparation phase of offensive operations involves the concentration of attacking forces and associated support elements into contact with the enemy.
The overriding imperative in a movement to contact is initiative.
Use smoke to --
- Conceal movement of maneuver and support forces, allowing the commander to mass forces unobserved.
- Provide tactical surprise, allowing the commander to seize the initiative and set the terms of combat.
- Defeat enemy reconnaissance and counterreconnaissance efforts.
- Conceal obstacle breaching or crossing.
Smoke employment tactics in the preparation phase are the following:
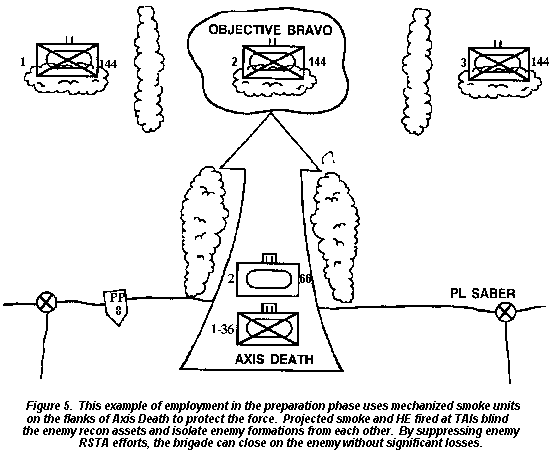
- Screening smoke. Use screening smoke to conceal maneuver and obstacle breaching or crossing. Use smoke in the main body area and along the flanks to conceal movement. You must carefully control the smoke to prevent silhouetting your units. Begin making smoke prior to crossing the line of departure to confuse the enemy as to the actual location and size of the force.
- Protecting smoke. Use protecting smoke as required to defeat enemy ATGMs and air defense systems.
- Obscuring smoke. Use obscuring smoke to defeat enemy reconnaissance and counterreconnaissance efforts. Use projected smoke means to deliver smoke mixed with high- explosive rounds before the enemy can pinpoint your units. Plan obscuring fire based on decision points for the enemy, isolating and confusing their reconnaissance forces.
- Marking smoke. Use smoke to mark enemy targets for rapid destruction or to reduce the potential for firing on friendly forces.
- Smoke for deception. Use this smoke to draw attention to areas of little or no importance. Create large area smoke away from the main body. Consider using smoke mixed with high-explosive rounds to conduct preparatory fire on dummy objectives.
Figure 5, illustrates smoke employment in the preparation phase.
Attack
A hasty attack will normally immediately follow a movement to contact. If the contact reveals an overwhelmingly superior enemy force, or our hasty attack is unable to either outflank or overcome the enemy defense, we will conduct a deliberate attack. In the attack phase, use smoke to--
- Provide tactical surprise, allowing the commander to seize the initiative early.
- Conceal movement of maneuver and support forces, allowing the commander to mass forces unobserved. Smoke must provide the commander with the ability to concentrate the maximum possible shock and violence against the enemy.
- Ruin the enemy commander's synchronization.
- Conceal obstacle breaching or crossing.
- Defeat enemy target acquisition, weapon guidance, and directed-energy weapon systems.
The overriding imperative in hasty attacks is agility. Therefore, smoke use in a hasty attack must assist the commander to fix and contain the enemy, deploy into combat formations, and maneuver additional forces to the flank and rear where the enemy is destroyed by fire or assault.
Smoke employment tactics in a hasty attack include obscuring smoke, screening smoke, marking smoke, protecting smoke, and deceptive smoke:
- Obscuring smoke. Use obscuring smoke to isolate the objective, defeat enemy target acquisition and guidance systems, and defeat reconnaissance and counterreconnaissance efforts. Use projected smoke means to deliver smoke mixed with high-explosive rounds in front of the objective; between enemy formations; and on identified forward observer, ATGM, and tank unit positions before the enemy can pinpoint your units as targets. Using projected smoke as countersmoke and to isolate the objective can significantly interfere with the enemy commander's synchronization.
- Screening smoke. Use screening smoke to conceal maneuver as you bypass small pockets of resistance and breach obstacles. Use it also along the flanks to protect the force and in the rear to conceal disposition and composition of reserves. Use self-defense and generated-smoke means to deliver smoke across danger areas and to the flanks of the force to limit enemy observation and engagement.
- Marking smoke. The tactics are the same as in the preparation phase.
- Protecting smoke. The tactics are the same as in the preparation phase.
- Deceptive smoke. The tactics are the same as in the preparation phase.
The overriding imperative for the deliberate attack is synchronization. Therefore, smoke use in the deliberate attack must assist the commander to fix and maneuver against the enemy and prevent the enemy from breaking contact. It must also force penetration of the enemy's defense and prevent reinforcement or counterattack by enemy reserves or second-echelon forces. Smoke employment tactics in a deliberate attack have the same names as for the preparation phase, but read on.
- Obscuring smoke. Use obscuring smoke to isolate the objective and complement countermobility efforts. Use it also to defeat enemy target acquisition and guidance systems and defeat reconnaissance and counterreconnaissance efforts. Use projected smoke means to deliver smoke mixed with high-explosive rounds in front of the objective, between enemy formations, on identified forward observers, and on ATGM and tank unit positions before the enemy can pinpoint your units as targets. Use smoke mixed with scatterable mines for countermobility behind enemy positions. Use it also between the enemy first-echelon, reserve, and second-echelon forces. The critical activity in planning obscuring fire in the deliberate attack is synchronization of all direct fire, fire support, smoke support, and engineer assets to create maximum combat power.
- Screening smoke. Use screening smoke to conceal maneuver as you cross the line of contact, bypass small pockets of resistance, or bypass or breach obstacles; along the flanks to protect the force; and in the rear to conceal disposition and composition of reserves. Use large-area generated smoke to conceal passage of lines and confuse the enemy concerning the disposition and composition of your force. Reconnaissance of enemy obstacles is critical to ensure timely employment of large-area smoke to conceal breaching or crossing of obstacles. Use self- defense and generated-smoke means to deliver smoke across danger areas and to the flanks of the force to limit enemy observation and engagement.
- Marking smoke. Use marking smoke to mark enemy targets for rapid destruction or to reduce the potential for firing on friendly forces. Use projected smoke means such as helicopter rockets to mark close and deep targets for engagement by close air support aircraft.
- Protecting smoke. If the enemy has known or suspected directed-energy weapon capability, concealing your force in a blanket of oil smoke will attenuate some of the energy. In the far term, using large-area projected smoke containing millimeter wave obscurants directly on the enemy positions will reduce our vulnerability to directed-energy weapons.
- Smoke for deception. Use supporting smoke to draw attention away from the main effort to areas of little or no importance. Use generated-smoke means (in a deliberate attack, the best means may be smoke pots and generators) to create smoke away from the main body. The deception story must be integrated into the overall tactical plan for smoke use to be effective.
Exploitation
Commanders should plan to follow every attack by bold exploitation to keep the enemy under pressure, compound their disorganization, and erode their will to resist. The overriding imperative in exploitation is depth. In the exploitation phase, use smoke to--
- Ruin the enemy commander's synchronization.
- Isolate enemy forces, allowing the commander to keep the enemy in contact and under pressure.
- Conceal movement of maneuver and support forces, allowing the commander to protect logistical units and convoys required to sustain the momentum of the exploiting force.
- Defeat enemy target acquisition, weapon guidance, and directed-energy weapon systems. This is particularly important as the exploitation force bypasses or contains small groups of enemy forces.
Smoke employment tactics in the exploitation phase use the same five types of smoke as follows:
- Obscuring smoke. Use obscuring smoke to complement countermobility efforts, defeat enemy target acquisition and guidance systems, and isolate enemy forces for piecemeal destruction. Use projected means to deliver smoke mixed with high-explosive rounds onto targets between enemy formations, onto enemy units as they attempt to regroup, and in front of enemy strongpoints as you bypass them. Use smoke mixed with scatterable mines behind moving enemy formations to impede their ability to break contact and to compound their disorganization.
- Screening smoke. Use this smoke to conceal maneuver and support forces and defeat enemy target acquisition and guidance systems. As protection of supplies and support units is essential to maintain the rapid tempo of the exploitation, priority of effort for smoke assets must go to sustainment activities. Use generated-smoke means to deliver smoke onto key logistics activities and to protect convoys. Use self-defense and generated-smoke means to conceal maneuver units as they bypass or harass enemy forces.
- Marking smoke. Use marking smoke to mark targets for destruction, identify bypass routes, and signal for battlefield activities. Use projected smoke means to deliver smoke onto identified enemy strongpoints or larger formations and to signal forces to consolidate on a particular objective or rally point. As exploitation force commanders rely heavily on air cavalry units for reconnaissance, helicopter-delivered smoke rockets will provide the best delivery system. Use generated-smoke means to mark bypass routes (for example, scouts could drop smoke pots at 100- to 200-meter intervals along a bypass route).
- Protecting smoke. The risk of nuclear weapon use increases when conventional means are ineffective in stopping our advance. If the enemy has known or suspected nuclear or directed- energy weapon capability, concealing your logistics activities in oil smokes may attenuate some of the energy.
- Supporting smoke for tactical deception. Use supporting smoke to keep the enemy off-balance and to draw attention away from critical sustainment activities. Use generated-smoke means to deliver smoke to multiple locations to the rear of the exploitation force to force the enemy to expend resources to target logistical activities.
Pursuit
As the enemy becomes demoralized and their formations begin to disintegrate, exploitation may develop into pursuit. Commanders attempt to annihilate the enemy force using a direct pressure force that keeps the enemy units in flight and an encircling force to envelop, cut off, and destroy or capture the fleeing enemy force. In the pursuit, use smoke to--
- Ruin the enemy commander's synchronization, denying the enemy time to reorganize a cohesive defense. If the enemy is able to establish a perimeter, smoke must help to defeat enemy target acquisition, weapon guidance, and directed-force towards the enemy to obscure energy weapon systems.
- Isolate enemy forces, allowing the commander to keep the enemy in contact and under pressure.
- Conceal movement of maneuver forces, allowing the commander to envelop the enemy force.
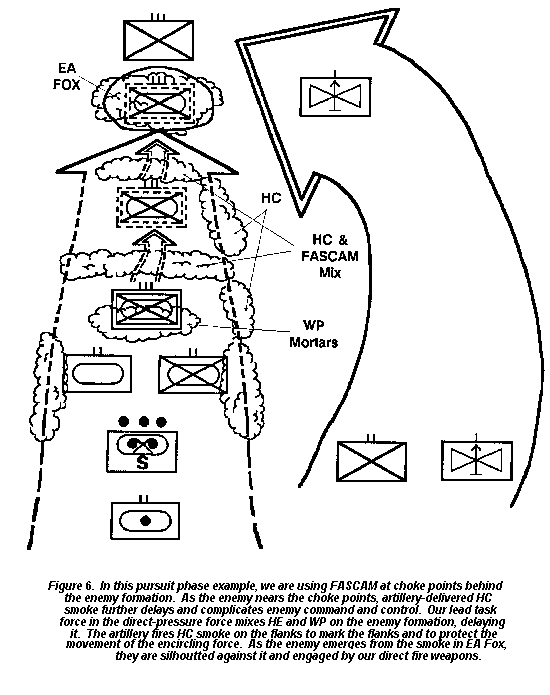
Smoke employment tactics in the pursuit include the following applications of the five basic smoke types:
- Obscuring smoke. The tactics are the same as in the exploitation phase. Additionally, use generated smoke from the direct pressure their observation while giving the encircling force freedom of maneuver. When in place, the encircling force could use generated smoke towards the enemy to obscure our forces, silhouette the enemy, and generally increase the enemy commander's synchronization problems.
- Screening smoke. Use screening smoke to conceal maneuver forces and defeat enemy target acquisition and guidance systems. Since the encircling force generally advances on parallel routes, screening smoke along the flanks of the encircling force can conceal their maneuver. However, since smoke draws attention, you may risk losing the element of surprise. Use self- defense and generated-smoke means to conceal maneuver units as they bypass or attack enemy forces.
- Marking smoke. The tactics are the same as in the exploitation phase.
- Protecting smoke. The tactics are the same as in the exploitation phase.
- Smoke for deception. Use this smoke to keep the enemy off balance and to support hasty attacks if the enemy is able to establish a perimeter. Use smoke generators to deliver smoke to multiple locations creating false passage points and to draw attention away from the main effort.
Figure 6, below, illustrates smoke employment in the exploitation and pursuit phases.
Attack Scenario
The following scenario illustrates possible smoke employment options in the offense, from the preparation through the pursuit phases. It depicts a mechanized infantry heavy brigade conducting the movement to contact. The brigade is the 2d Brigade, 54th Infantry Division (M).
Smoke delivery means include the direct support artillery battalion, battalion mortars, smoke generator platoon, VEESS, smoke pots, smoke grenades, and aviation assets on-call. Field expedient smoke delivery means include smoke pots strapped to armored vehicles with electrical ignition wires running inside the vehicle.
2d Brigade will conduct a movement to contact commencing at H-hour today. The commander's intent is to reestablish contact with the enemy, seize the brigade objective, and exploit any success onto the division objective. The brigade objective is Objective Fox. The brigade's follow-on objective is Objective Jack. The division objective is Objective Midas some 40 kilometers beyond the line of departure.
Intelligence indicates that the enemy is the 1st Guard Motorized Rifle Division, 2d Combined Arms Army, which relieved another motorized rifle division and is conducting a meeting engagement from the march. The enemy is marching by regiments, with three regiments in front and a combined arms reserve instead of a second echelon. Terrain is fairly open to the west of Hill 268 but is restricted to the east of Hill 352. The enemy has excellent observation and fields of fire from both hills. Figure 3-6 illustrates the disposition of forces as of H-1 hour.
At H - 24 hours, the commander issues the restated mission and his planning guidance. The brigade chemical officer, S2, and FSO go to the intelligence cell and begin target development.
The brigade chemical officer has completed his estimate at H - 18 hours and provides a draft target list to the FSO. While the brigade chemical officer briefs the commander, the brigade chemical NCO continues smoke target analysis in coordination with the smoke platoon leader.
At H - 15 hours, the brigade chemical officer, FSO, and smoke platoon leader finalize the smoke support plan. This includes a draft smoke support annex to the brigade OPORD.
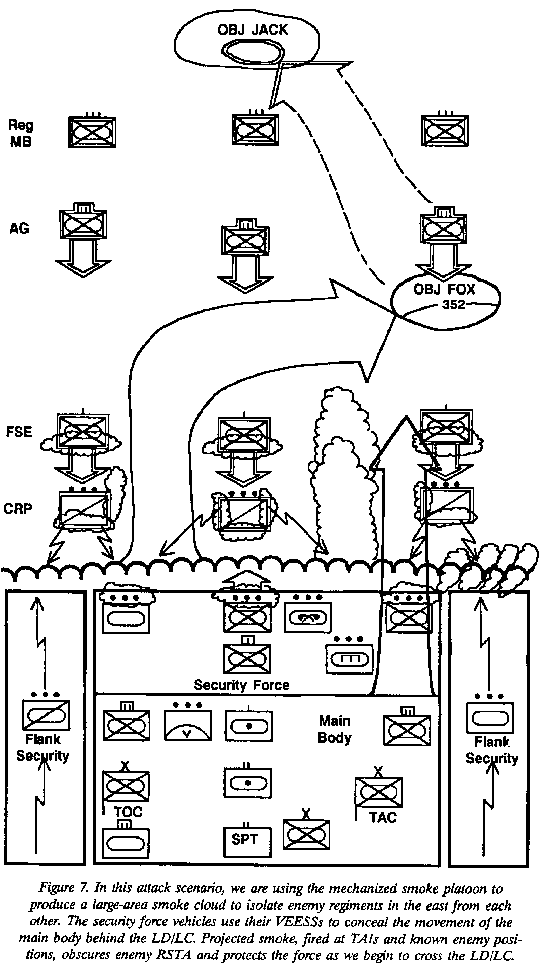
Preparation Phase(Movement to Contact)
Prior to H- hour the security force and flank security elements prepare expedient smoke devices using smoke pots strapped onto their vehicles. The fire support plan includes quick smoke to isolate the enemy combat reconnaissance patrols (CRPs), so WP and HC smoke ammunition is pre-positioned forward of the artillery battalion in the security force area.
The fire support plan also calls for aviation assets to use smoke rockets to mark the gaps between the enemy CRPs and FSEs. The S3 (air) has coordinated for the attack helicopter squadron to carry extra WP rockets in their first two sorties. The smoke platoon initially travels with the main body and has on-board capability to make smoke for 70 to 140 minutes.
At H- hour, our forces cross the line of departure.
Thirty minutes later, aviation reconnaissance sights the lead elements of the enemy CRP. When the CRP is within 3,000 meters of the security force, the artillery battalion fires HE and smoke (HC) in front of each CRP.
At H + 35 minutes, the security force sights the CRP through the smoke using thermal imagers. The security force then attempts to fix the CRP by engaging it with direct fire weapons through the smoke.
At H + 36 minutes, the security force will also locate and mark bypass routes. The security force ignites smoke pots and drops them off at 200-meter intervals to mark and conceal the bypass.
The smoke platoon moves toward the LD at H + 36 minutes. NOTE: The smoke platoon should always remain behind the security force.
At H + 38 minutes, the aviation reconnaissance and security force sight the enemy FSE. The FSE is moving forward to establish the FLOT along the screen line of the CRP.
At H + 39 minutes, the maneuver battalion mortars begin to fire HE and WP on top of and in between the CRPs. The artillery battalion shifts fire to the area between the FSEs and CRPs, obscuring with a mix of HE and HC.
The smoke generator platoon begins to make smoke at H + 40 minutes at the LD. In addition, the flank security force on the eastern flank ignites and dumps its smoke pots within 500 meters of the LD.
At H + 40 minutes, the security force combat vehicles initiate screening smoke with their VEESS. The artillery and mortar units increase their rate of fire.
At H + 45 minutes, the main body crosses the LD. The main body maneuvers to the west of the smoke along the bypass route (Figure 7).
Attack Phase
The movement to contact has developed into an actual engagement. The commander seizes the initiative and orders the brigade to attack toward Objective Fox. The main attack is in the west along Axis Andy. The supporting attack is in the east along Axis Tony. The brigade will consolidate on the objective and continue the attack towards the division objective.
At H + 46 minutes, the artillery shifts fire from the area between the CRP and FSE to the area between the FSE and advanced guard (AG), obscuring the target with a mixture of HE and HC. Also, the mortars shift fire from the CRP to between the CRP and FSE, obscuring with a mixture of HE and WP.
When the main attack has cleared the LD, the security force elements in the west turn off their VEESS. At the same time the supporting attack force engages the enemy FSE and AG with flanking fire.
At H + 50 minutes, the artillery shifts fire from the area between the FSE and AG to the area between the AG and the main body in the west, and onto the objective in the east. The artillery continues to fire a mix of HE and HC.
Also at H + 50 minutes, the mortars shift fire from the area between the CRP and FSE to the area between the FSE and AG, obscuring with a mix of HE and WP.
At the same time, the smoke platoon stops making smoke. This will ensure the objective itself is unobscured during the assault.
The main attack force is in position to make the assault on the objective at H + 55 minutes. The artillery shifts fire to the regimental main body beyond the objective, now firing only HE. The mortars shift fire onto the AG in the center and in the west, obscuring and isolating them with HE and WP mix.
At H + 1 hour, the main attack force assaults the objective. Artillery and mortars continue to fire on the enemy main body, isolating the objective from external support.
Exploitation Phase
The enemy resistance is crumbling. 2d Brigade has significantly disrupted the enemy's synchronization and has the initiative. Upon securing the brigade objective, the brigade rapidly consolidates and the commander orders them to continue the attack. The brigade's follow-on objective is to secure Objective Jack and destroy the remnants of the enemy division artillery group (DAG). The main attack is in the east along Axis Stef, with the supporting attack in the center along Axis Gay.
At H + 1.25 hours, the mortars begin to fire on the remaining regimental main bodies, obscuring them with a mixture of HE and HC. At the same time, the artillery begins to fire scatterable mines and HE and HC mix into the area behind the first-echelon regiments. This isolates the first echelon from the combined arms reserve and delays their retreat.
At H + 1.5 hours, the smoke platoon begins to make smoke in the west of the sector to isolate the remnants of the easternmost first-echelon regiments from the other first-echelon regiment. This further disrupts the enemy commander's synchronization, command, and control.
The main and supporting attack forces begun moving towards Objective Jack, keeping the enemy under pressure. They will bypass any enemy forces they encounter, with the brigade follow-on forces containing and destroying pockets of enemy forces bypassed by the main body.
At H + 1.75 hours, the mortars and artillery shift to fire behind the first-echelon regiments and onto Objective Jack, respectively. Both mortars and artillery will fire a mix of HE and WP for obscuration and lethality.
The mortars shift fire onto Objective Jack at H + 2 hours, and the exploitation force positions for the final assault on the objective.
At H + 2.10 hours, the mortars and artillery shift fire beyond Objective Jack. The main attack force assaults the objective, destroying the enemy DAG.
Pursuit Phase
By H + 2.25 hours, it is obvious that the enemy can no longer maintain their position, and 2d Brigade is capturing significant numbers of soldiers and equipment. The enemy resistance has crumbled. The enemy is now in full flight.
Upon securing the brigade follow-on objective, the brigade rapidly consolidates, and the commander orders them to conduct the pursuit. The direct pressure force moves rapidly forward along all available roads, bypassing small enemy pockets of resistance. The encircling force plans to move rapidly to the division objective and cut off the enemy retreat.
At H + 2.50 hours, aviation assets locate and mark the larger enemy formations with WP rockets. The mortars and artillery assets with the direct pressure force then fire successive belts of scatterable mines behind these larger formations. They also fire HE and HC mix onto the formations to further slow them and complicate command and control.
At H + 2.75 hours, the encircling force leaves its assembly area, moving rapidly along the western flank towards the division objective. By H + 3.5 hours, the encircling force has bypassed and outdistanced the entire enemy formation. The encircling force commander now establishes a hasty defense, blocking the enemy's escape route.
At H + 3.75 hours, the smoke platoon starts its third mission. The smoke platoon begins to make a smoke curtain across the enemy's escape route, while the artillery and mortars from the direct pressure force stop firing smoke. This allows the direct pressure force to engage the enemy with direct fire weapons that are unobscured while concealing the encircling force's preparations.
At H + 4.25 hours, the enemy is forced into an engagement area between the direct pressure and encircling forces. The smoke from the smoke generator platoon silhouettes the enemy force for attack by the direct pressure force. At the same time, the encircling force is able to engage enemy forces through the smoke or as they emerge from the smoke on the other side. The enemy is destroyed and forced to surrender.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|