Breaching Scenario and Special Planning Considerations
This appendix provides a scenario showing how the breaching tenets may be applied when conducting a breaching operation in open terrain, such as a desert. This example is not an attempt to give a single, doctrinally correct solution but simply to provide a method that a unit may use to task-organize and approach this very difficult mission. Also discussed in this appendix are considerations that may be needed when conducting a breaching operation in restricted terrain (a defile, urban terrain, or the jungle). The following paragraphs are an example of a worst-case scenario in which a TF is given the mission to conduct a breaching operation against a well-equipped, well-prepared enemy defense.
Sample Breaching Operation
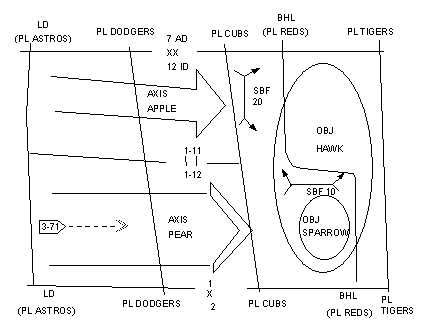
D-1. TF 1-12 is a mechanized infantry battalion that is task-organized with two tank companies from TF 3-71 (armored battalion). It just received a mission to secure OBJ SPARROW as part of a brigade attack to destroy a motorized infantry battalion (MIBN) (see Figure D-1) .
|
|
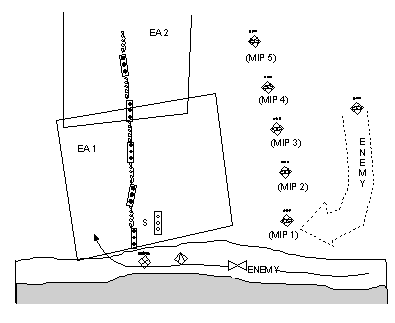
D-2. TF 1-12 received intelligence products, including the brigade SITEMP and a series of WOs, before issuing the actual OPORD. The TF staff, in particular the S2 and the engineer, revised and refined the brigade SITEMP based on their analyses of the terrain and the enemy (see Figure D-2).
|
|
D-3. Upon receipt of the brigade OPORD, TF 1-12 learns that—
- The brigade has task-organized it with an engineer recon team to augment its recon capability and its habitually associated engineer company. An additional engineer line platoon has been attached to the engineer company, giving the TF a total of three engineer line platoons.
- The brigade has given TF 1-11 the mission to fix enemy forces north of OBJ SPARROW to prevent them from repositioning.
- The brigade plans to disrupt the enemy's counterattack force by using area-denial artillery munition (ADAM)/remote antiarmor mine (RAAM) SCATMINEs along the high-speed route to OBJ SPARROW. The counterattack force has been located by intelligence sources.
- The brigade plans to have the engineer battalion (-) follow TF 1-12's assault force to assume control of the lanes. The engineer battalion will create additional lanes, if necessary, and upgrade/maintain the lanes and marking pattern to facilitate the passage of TF 3-71.
- The brigade has tasked it to seize OBJ SPARROW and occupy SBF 10 with at least two platoons to fix enemy forces north of OBJ SPARROW.
- The brigade has tasked it to create two lanes in the obstacle system to support the passage of TF 3-71 through the created lanes.
D-4. Based on the commander's guidance, the TF staff developed three COAs. The third COA was chosen based on war gaming. It required a company team (assault force), consisting of one tank platoon (the platoon has two tank plows mounted) and two mechanized infantry platoons, to seize OBJ SPARROW. The staff decided that two lanes were necessary in the obstacle system, vicinity grid AA123456, based on the specified task given by the brigade. Because of the lane requirement and the obstacle type expected to be encountered, the staff decided that the breach force must consist of at least two tanks with MCBs, two tanks with MCRs, and two MICLICs. The breach force must also have two engineer platoons to create, proof, and mark the lanes and to provide redundancy of assets. The staff considered the threat to the breach force to be—
- The infantry platoon and AT weapons on the southern flank.
- The southern motorized infantry platoon (MIP), which the support force may not be able to suppress because its forces are masking the breach force.
- The MIP-size counterattack force.
D-5. In this COA, the staff task-organized one tank platoon and one mechanized infantry platoon to the breach force (in addition to the MCBs and MCRs) to provide local security and redundant suppression. The staff determined from its terrain and enemy analyses that the support force's mission is to suppress the four southern MIPs to facilitate reduction operations. To accomplish this, the staff task-organizes two company teams to the support force. Each company team in the support force has one tank plow to reduce any obstacles it encounters en route to the SBFs (see Figure D-3).
|
|
|
|
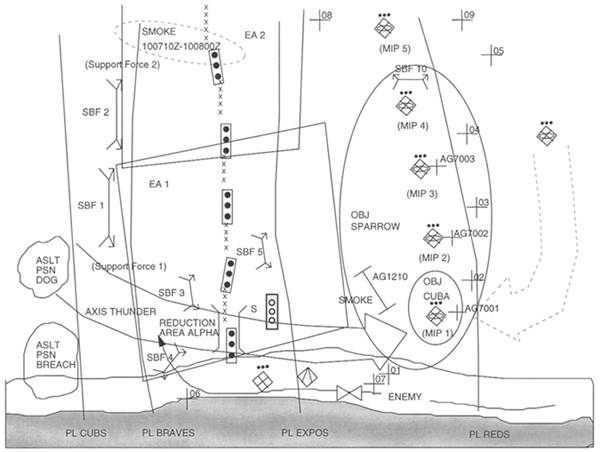
D-6. The staff further refines the COA by developing an initial plan to achieve the following breaching fundamentals, to include assigning tasks to the various subordinate forces (see Figure D-4):
- Suppress .
- Support force 1 will occupy SBF 1 and initially orient its fires on MIPs 1 and 2. When the breach force is committed, it will shift its fires to orient on MIPs 2 and 3. Fires will be lifted on the order of the assault-force commander.
- Support force 2 will occupy SBF 2 and orient its fires on MIPs 3 and 4. Fires will be lifted on the order of the assault-force commander.
- The breach-force security element will occupy SBF 3 and orient fires on MIP 1. The security element is responsible for local security at the point of breach.
- The fire-support element (FSE) will ensure that CFZ 1 is activated as the breach force moves to the point of breach.
- The support force will call for and adjust artillery targets AG7001 through AG7003 when the lead elements of the support force cross PL CUBS.
- Obscure .
- The support force will call for and adjust smoke target AG1210 when the lead elements of the support force cross PL CUBS. The support force will adjust this target only if the smoke is ineffective.
- The smoke platoon (task-organized to the TF for this mission) will employ its generators to the north of support force 2. Smoke operations begin when support force 2 crosses PL CUBS.
- Secure . The breach force (security element) will occupy SBF 4 and orient fires on the infantry platoon and AT weapons on the south wall.
Figure D-4. Graphics Developed During COA Development (Overlaid on SITEMP)
- Reduce .
- The breach-force reduction element will move from assault position (ASLT PSN) BREACH when the commitment criteria in reduction area ALPHA has been met. In this scenario, it will create, proof, and mark (initial lane-marking pattern) two lanes in the obstacle system, at least 800 meters apart, within reduction area ALPHA. This considers the enemy's use of artillery-delivered SCATMINEs to close the lanes.
- The breach-force security element will occupy SBF 5 with one platoon orienting fires on MIPs 2 and 3 to provide enemy suppression when one lane is created in the tactical obstacles.
- Assault .
D-7. During COA analysis, modifications are made to the original COA. This includes task-organizing an engineer platoon to the assault force to help reduce protective obstacles and mark lanes for the assault and follow-on forces (see Figure D-5 ).
|
|
|
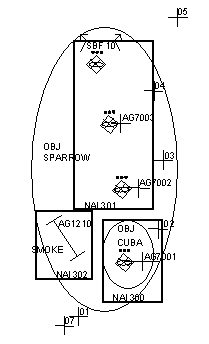
D-8. Additionally, the staff develops a decision point for committing the breach force and a plan to collect the necessary information to support the decision point (see Table D-1 ). Figure D-6 shows the location of each NAI.
|
Breach force must have a minimum of one engineer platoon, 1 MICLIC/MCB, and 6 M1s/M2s. |
||
|
|
D-9. The commander specifies the following C 2 structure of the mission based on the scheme of maneuver in the COA he approved:
- The assault force will be comprised of Team A/3-71 (mechanized heavy).
- The breach force will be comprised of Team B/3-71 (tank heavy) and A/55th Engineer Battalion. The Team B commander will be the breach-force and security-element commander. The engineer commander will be the reduction-element commander.
- The support force will be comprised of Team C/1-12 (mechanized heavy) and Team D/1-12 (tank heavy). The support-force commander will be the TF S3.
D-10. Preparation for the breaching operation involves numerous rehearsals, beginning at the lowest levels and culminating into a full-dress, combined-arms rehearsal. S2 reports that the TF received the confirmed location of the tactical obstacles in the vicinity of the point of breach. The report indicated that the minefields are comprised of three rows of buried SB-MV mines (Italian AT mines), with a uniform 4.5 meters spacing between mines and 70 meters between rows. One row of concertina wire is positioned 40 meters to the rear of each tactical minefield. Additionally, the enemy has emplaced protective minefields, which are comprised of AP mines only, 400 meters in front of each platoon position. The enemy has tanks and infantry fighting vehicles (IFVs) overwatching tactical and protective obstacles. Reports indicate that the enemy has not prepared dismounted positions.
NOTE: The assault-force commander decides to conduct a mounted assault based on information from the intelligence report and the terrain analysis he conducted. The terrain analysis indicates that tank plows will effectively reduce the enemy's protective obstacles.
D-11. This information is quickly relayed to subordinate units and all rehearsal sites reflect these obstacles. The commander pays particular attention to the status and location of reduction assets throughout preparations for the attack. This results in an MCB being removed from an inoperable M1 at the unit maintenance collection point (UMCP) to an operable M1 in the assault force.
D-12. The TF crosses the LD at 95 percent strength (all MCBs, MICLICs, and MCRs are operational). Before crossing PL DODGERS, the TF scouts report that three of the four vehicles in NAI 300 have been destroyed by Copperhead munitions. The commander reminds the S3 that destroying the remaining vehicles is his first priority.
D-13. As the support force crosses PL CUBS, the TF S3 reports that he has lost two M2s to indirect fires and one M1 to maintenance and is beginning to occupy SBFs 1 and 2. Artillery units begin suppressive fires and begin to build obscuration smoke. As the support force begins to suppress the enemy with direct and indirect fires, the breach and assault forces occupy ASLT PSNs BREACH and DOG, respectively, and conduct final preparations as necessary. The tactical operations center (TOC) informs the commander that CFZ 1 will be activated when the breach force is committed. The breach-force commander reports that all reduction assets are operable, and the TF scouts report that the final vehicle in OBJ CUBA has been destroyed. The TF S3 reports that obscuration and suppression have been achieved and that combat power is 6 M1s and 13 M2s.
D-14. Having met the commitment criteria, the commander orders the breach force to AA123456 to begin obstacle reduction. The breach-force commander initially moves his security element to SBFs 3 and 4. The reduction-element commander also moves forward with his platoon leaders to recon the obstacle and confirm/refine the plan to reduce the obstacle. Once the security element is set in SBFs 3 and 4, the reduction element moves forward to reduce the obstacle. When the first lane is created and proofed, the breach-force commander moves a portion of the security element from SBF 3 to SBF 5. The assault-force commander begins movement from the assault position to the far-recognition marker that has been reported by the reduction-element commander. Upon reaching the far-recognition marker, the assault-force commander can observe the final-approach marker and the marked lane.
D-15. The assault force moves through lanes in the tactical obstacles and sets its platoons in the SBFs. It immediately begins to create two lanes in the protective obstacles with the MCBs. When the lanes are complete, the assault-force commander maneuvers the two tank platoons to SBF 10, while the mechanized company team continues to suppress the remaining enemy vehicles. The engineer platoon remains at protective obstacles to mark lanes in preparation for passing follow-on forces.
D-16. The engineer battalion S3 is immediately behind the assault force. He takes control of the reduction element that has created, proofed, and marked two lanes in the tactical obstacles by this time. The S3 moves a portion of the reduction assets away from the lanes to counter any SCATMINEs that the enemy may use to close the lanes. The S3 prepares to assist with TF 3-71's passage through the lanes. When the assault force reports that it has created a safe route to PL REDS, the brigade commander orders TF 3-71 to pass through TF 1-12 and continue the attack.
Considerations for Restricted Terrain
D-17. The breaching tenets discussed in Chapter 1 apply to breaching operations in restricted terrain; however, the application of these tenets is different from a breaching operation conducted in open terrain. The following considerations should be made when breaching in restricted terrain:
- OBSTINTEL collection is critical when conducting breaching operations in restricted terrain. It is essential that the breach force knows what types of obstacles are in place and knows the exact composition of any complex obstacle. With this information, the breach-force commander can ensure that the reduction assets necessary to reduce the obstacle are available and placed in the right order in the movement formation. The breach force's ability to move reduction assets within the formation may be extremely limited due to the terrain's constricting nature.
- Recon assets tasked to obtain OBSTINTEL should be prepared to recon different types of obstacles than would normally be found in open terrain. For example, in urban or mountainous terrain, the enemy may use rubble obstacles, such as the rock drop . Additionally, recon assets are much more likely to encounter field-expedient or booby-trapped obstacles when conducting operations in restricted terrain. Recon assets used to collect OBSTINTEL must be able to recommend reduction methods to be used by the breach force when reducing the obstacle.
D-18. The proper application of the following breaching fundamentals is essential to the success of breaching operations conducted in restricted terrain. As with other breaching tenets, breaching fundamentals are normally applied differently in restricted terrain than in open terrain.
- Suppress . The need to prevent or degrade enemy fires and observation of friendly forces remains unchanged when breaching in restricted terrain. However, unlike a breaching operation conducted in open terrain in which the support force can suppress the enemy with long-range fires, massed indirect fires, and smoke, suppression will normally be achieved through close-in fighting. Forces tasked with suppressing the enemy may find it necessary to seize terrain at or on the far side of the obstacle to achieve their mission. In all probability, the fighting to achieve enemy suppression will be decentralized. Therefore, the ability to use indirect fires will be restricted due to the close proximity of friendly and enemy forces.
- Obscure . When trying to obscure the enemy with indirect fires, the same problems exist as when trying to suppress the enemy. Using mortars (because of their ability to fire high-level trajectory), smoke pots, and smoke grenades may be more effective. The potential for degrading friendly-force operations when using obscurants is greater because of the close-in nature of the fighting that occurs in restricted terrain.
- Secure . The responsibility to secure the reduction area may normally be given to the support force when conducting breaching operations in restricted terrain. Because the support force may find it necessary to seize terrain on the far side of the obstacle to suppress the enemy, securing the reduction area may be accomplished at the same time. When this situation occurs, the amount of maneuver forces within the breach force may be less than what is normally necessary when breaching in open terrain.
- Reduce . The ability to create more than one lane and to move reduction assets around each other may be severely restricted when breaching in restricted terrain. For this reason, accurate OBSTINTEL and a well-thought-out, well-rehearsed reduction plan are critical.
- Assault . As discussed earlier, the number of lanes available to the assault force may be less than what is actually needed. For example, a battalion-size assault force may be restricted to using a single lane through an obstacle due to the restricted terrain. For this reason, the assault-force commander must ensure that the sequencing of forces through the lane is appropriate to achieve the mission.
- Mass . Although mass remains a critical tenet for breaching operations in restricted terrain, the ability to achieve mass may be difficult and time-consuming. The assault force will attempt to achieve a 3:1 combat-power ratio. However, due to the restricted nature of the terrain and the limited number of lanes that may be created, the assault force may take longer to get that much combat power to the far side of the obstacle. Units must consider ways to minimize the risk to the assault force as it builds its combat power on the far side of the obstacle.
- Synchronize . The reverse-planning process described in Chapter 1 remains the key to successful breaching operations in restricted terrain. However, effective C 2 , particularly the controlling of personnel and equipment around the point of breach, is critical for successful operations. The terrain's restricted nature magnifies mistakes made in bringing the proper reduction assets forward to the obstacle or in sequencing forces through created lanes. These mistakes result in increased time for the enemy to react to the breaching operation through repositioning and other means. For this reason, a well-rehearsed force is critical. All subordinate units must understand their mission, the overall timing of the operation, and how their actions relate to missions of other subordinate units.
Considerations for Military Operations in Urbanized Terrain
D-19. Military operations in urbanized terrain (MOUT) is defined as all military actions that are planned and conducted on a topographical complex and its adjacent natural terrain where man-made construction is the dominant feature. Urbanized terrain affects the tactical options available to the commander and requires a thorough knowledge of unique terrain characteristics, detailed planning down to the smallest unit level, and sound leadership at all levels. The complexities of the urban environment, such as line-of-sight (LOS) restrictions, inherent fortifications, limited intelligence, densely constructed areas, and the presence of noncombatants, restricts current military technology. US forces do not possess the overwhelming technology advantages in an urban environment as in other environments.
D-20. A three-dimensional view of the terrain is essential to gain a complete understanding of observation and AAs. The close fight (inside the building) is difficult and decentralized, with control of the movement from room to room most often in the hands of squad and platoon leaders. Success in the movement from building to building is a combined-arms fight, which requires the active involvement of a battalion command post. Seeing the terrain in a three-dimensional view will identify opportunities for employment of all the battalion's combat power and enable the battalion to set the conditions for successful platoon and company assaults.
Planning
D-21. Close-quarters clearing techniques are designed to be executed by standard four-man breach and clearing teams. Therefore, the size of the breach organization will be significantly smaller than those involved when fighting occurs in open terrain. The reduction element must work with the breach leader to formulate the assault plan and to ensure that all planning considerations are completed.
D-22. The reduction element is responsible for the following tasks during the planning phase:
- Accessing all intelligence data on potential breach points.
- Helping the command element select the best method of entry (mechanical, shotgun ballistic breach, or explosive). (See Figures D-7 through Figure D-10 )
- Assembling and preparing tools and equipment and constructing explosive entry charges and diversionary charges if required.
- Briefing team members.
- Rehearsing.
- Conducting a back brief of team members.
- Conducting a precombat inspection (PCI).
D-23. The commander, breacher, and other essential personnel assemble and analyze all available information, data, and intelligence pertaining to the intended target. This involves examining the design construction and material makeup of the structure to determine the best primary and alternate points of breach.
|
|
|
|
|
|
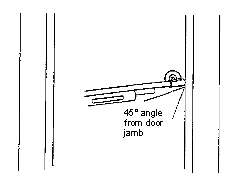
|
Method of Entry
D-24. Once the point of breach has been identified, the reduction element leader continues to assemble and analyze all available information, data, and intelligence pertaining to the target structure. This involves a detailed examination of each point of breach's design, construction, and material makeup to determine the best primary, secondary, and tertiary breaching method. Again, tactics to be employed may dictate or rule out specific entry points.
Obstacle Intelligence
D-25. Collecting the following OBSTINTEL is critical during MOUT:
- What type of mission is it?
- Are drawings or blueprints of the structure available?
- Are photographs of the point of breach and adjacent structures available?
- Can R&S personnel give a detailed description of the point of breach?
- Can counterintelligence personnel provide any information?
- Are there any human intelligence sources (agents, friendly forces, evacuees, prisoners, tourists, workers, businessmen, travelers) that can provide information relating to the point of breach?
- What type of shielding is available at potential breach points (natural or man-made)?
- How close will the assault force be positioned to the breach points?
- Do drawings of the target (if available) include gas, power lines, and other similar hazards?
- Is there a history of booby-trap use?
- Will the weather affect charge adhesion methods?
Breaching Fundamentals
D-26. The proper application of the following breaching fundamentals is essential to ensure success in breaching conducted during MOUT. As with other breaching tenets, the breaching fundamentals are normally applied differently in urbanized terrain than in open terrain.
- Suppression . Maneuvering to achieve suppression of the enemy will be decentralized. Therefore, the ability to use indirect fires will be restricted due to the close proximity of friendly and enemy forces and civilians.
- Obscure . The potential for degrading friendly-force operations with obscurants is greater due to the close-in fighting that occurs in built-up terrain. Hand-emplaced smoke will likely be the most effective.
- Secure . Breach and clearing teams secure a foothold near the point of breach. Local security must consider all possible locations for the enemy to hide.
- Reduce . Redundant systems are critical during MOUT. The reduction element is responsible for preparing equipment/charges for emplacement, searching for improvised explosive devices (IEDs), and verifying target intelligence.
- Assault . The actual attack of the objective using close-quarters battle techniques should be conducted according to the assault plan. The unit should be prepared to conduct additional planned and unplanned breaches.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|