Chapter 6
Area Security
MP conduct AS operations to protect critical functions, facilities, and forces. They synchronize efforts with base and base cluster defense planners within a specific AO to ensure that support and sustainment operations are not interrupted. The HN, when capable, retains responsibility for security of all areas outside US bases. However, US commanders are always responsible for the defense and security of US forces and bases regardless of HN support. AS is conducted by MP across the full spectrum of army operations to protect the force, impose order, and ensure freedom of movement. MP activities that support AS include reconnaissance operations, ADC, base and air base defense (ABD), response force operations, and critical site asset and high-risk personnel security.
RECONNAISSANCE OPERATIONS
6-1. MP plan and conduct area and zone reconnaissance, screening and surveillance missions, and counterreconnaissance.
6-2. MP conduct reconnaissance and screening missions to obtain information about the activities and resources of an enemy or potential enemy or to secure data concerning the characteristics of a particular area. MP reconnaissance, screening, and surveillance efforts include area, zone, and route reconnaissance and counterreconnaissance. These missions may be conducted primarily in the rear area, but may occur anywhere sustaining operations are conducted. Refer to Chapter 5 for more information about route reconnaissance. MP employ NBC detection equipment to determine the absence or presence and extent of NBC contamination. Refer to Appendix J for more information about NBC reconnaissance.
AREA RECONNAISSANCE
6-3. Area reconnaissance is performed to obtain detailed information concerning the terrain or enemy activity within a prescribed area, such as a town, ridgeline, woods, or any terrain critical to the operations. MP conduct area reconnaissance to help guard against unexpected enemy attack in the rear area. Area reconnaissance and surveillance are vital to maintaining AS and contribute to the commander's intelligence collection plan. MP area reconnaissance is a composite of actions. It is initiated from observations and reports gathered over time by MP patrols and information gained through coordination with HN police and other friendly forces. Refer to FM 7-8 .
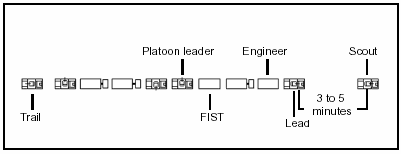
6-4. Reconnaissance patrols may differ slightly, depending on the type of reconnaissance to be performed. However, all reconnaissance patrols have a reconnaissance and security team. The size of the patrol is determined by METT-TC. Other considerations to determine the size of the patrol include—
6-5. MP leaders plan area reconnaissance based on the IPB and the commander's critical information requirements. Information on enemy activity and likely avenues of approach is coordinated with military intelligence (MI). MP monitor likely enemy avenues of approach and LZ and DZ in critical areas to give early warning of rear-area enemy activity.
6-6. MP area reconnaissance plans include areas near facilities that are designated as critical by the commander, such as—
6-7. When leading an area reconnaissance patrol, in addition to using troop-leading steps and following the general principles for making a reconnaissance, the patrol leader—
Conducts a leader's reconnaissance of the objective area to confirm or change the plan.
Returns to the ORP, completes the plan, and briefs the soldiers.
6-8. The security elements leave the ORP before the reconnaissance element. The security element leader places security teams at the ORP and on enemy avenues of approach into the objective area. The reconnaissance element conducts the reconnaissance by moving to several vantage points around the objective.
6-9. The reconnaissance element leader may have a small reconnaissance team move to each vantage point instead of having the entire element move as a unit from point to point. This reduces the chances of being spotted.
6-10. After the objective has been reconnoitered for the details outlined in the order, all elements return to the ORP. Teams share their information, consolidate it, and report it, then return to the patrol HQ or continue to the next mission.
ZONE RECONNAISSANCE
6-11. A zone reconnaissance is a directed effort to obtain detailed information concerning all routes, obstacles (to include chemical or radiological contamination), terrain, and enemy forces within a zone defined by boundaries. A zone reconnaissance is normally assigned when the enemy situation is vague or information concerning cross-country trafficability is desired. Zone reconnaissance techniques include the use of moving elements, stationary teams, or a series of area reconnaissance actions. Refer to FM 7-8 and FM 17-98 .
6-12. The four methods used to conduct a zone reconnaissance are—
Box Method
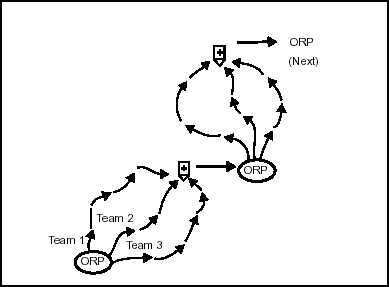
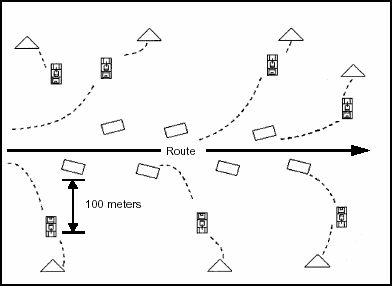
6-13. To use the box method (Figure 6-1), the leader sends his reconnaissance and security teams from the ORP along the routes that form a boxed-in area. He sends other teams along routes through the area within the box. All teams meet at a linkup point at the far side of the box from the ORP.
Figure 6-1. Box Method of Zone Reconnaissance
Fan Method
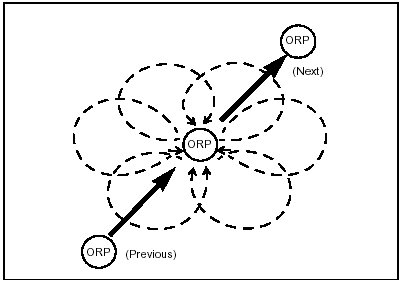
6-14. To use the fan method (Figure 6-2), the platoon leaders selects a series of ORPs throughout the zone. At the first ORP halt and set up security. After confirmation of the patrol's location, the platoon leaders selects reconnaissance routes out from and back to the ORP.
NOTE: These routes form a fan-shaped pattern around the ORP. They must overlap to ensure that the entire area has been reconnoitered.
Figure 6-2. Fan Method of Zone Reconnaissance
6-15. Once the routes have been selected, send out reconnaissance elements along the routes. Do not send out all the elements at once. The platoon leader keeps a reserve at the ORP. He sends elements out on adjacent routes to keep from making contact in two different directions.
6-16. After the entire area (fan) has been reconnoitered, report the information then move the patrol to the next ORP. Repeat this action at each successive ORP.
Converging-Routes Method
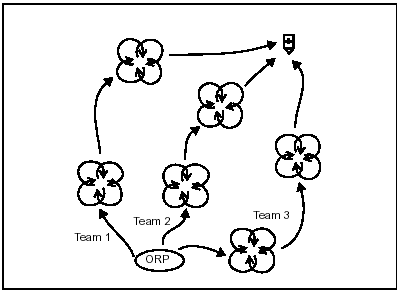
6-17. To use the converging-routes method (Figure 6-3) (which incorporates the fan method), select an ORP and reconnaissance routes through the zone and the rendezvous point.
NOTE: The rendezvous point is a place where patrol members link up after the reconnaissance.
Figure 6-3. Converging Routes Method of Zone Reconnaissance
6-18. Halt the patrol at the ORP and set up security. Confirm the patrol's location. Designate a route for each reconnaissance element, a location for the rendezvous, and a linkup time at the rendezvous point. Send a reconnaissance element to reconnoiter each route (usually using the fan method). The leader moves with the center element.
6-19. At linkup, the patrol secures the rendezvous point as it did the ORP. While at the rendezvous point, information gained by each member is exchanged with all the other members. This provides backup to ensure that all information is passed onto higher HQ. The patrol then returns to friendly lines or continues on to another mission.
Successive-Sector Method
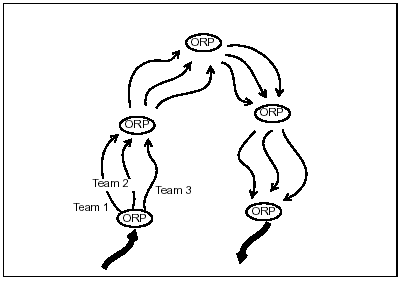
6-20. To use the successive-sector method (Figure 6-4), build on the converging-routes method. Select an ORP and a series of reconnaissance routes and rendezvous points. Use the converging-routes method from each ORP to each rendezvous point.
Figure 6-4. Successive Sector Method of Zone Reconnaissance
6-21. Each rendezvous point becomes the ORP for the next phase. Designate reconnaissance routes, a linkup time, and the next rendezvous point when the patrol links up at the rendezvous point. Continue this action until the entire zone has been reconnoitered.
6-22. Regardless of the type of method used, report the information through proper MP channels as soon as possible. Commanders rely on fast, accurate reconnaissance information to plan successful operations.
SCREENING MISSIONS
6-23. Screening missions are defensive in nature and largely accomplished by establishing a series of OPs and conducting patrols to ensure adequate surveillance of the assigned sector. Division cavalry units normally conduct security missions that include a screen for maneuver units during offensive operations.
6-24. MP conduct screening missions for friendly forces in the rear area to provide early warning of enemy approach and to provide real-time information and reaction time for stationary units. In the event of a Level III threat, MP may come under the OPCON of a TCF, which is also referred to as a combined-arms maneuver unit. In this role MP may provide limited security missions, such as a screen to the flank or rear of the main body, with the primary mission of providing early warning and disrupting or destroying enemy reconnaissance vehicles.
6-25. Generally, MP are tasked to observe specific avenues of approach or, more precisely, NAI. The area to observe should be identified in either the reconnaissance and security plan that the platoon leader receives or in the OPORD from higher HQ. If the platoon does not receive an IPB product, the higher OPORD must specifically state where it must focus the screening operation. If the platoon is assigned multiple requirements, the higher HQ must prioritize them.
SURVEILLANCE
6-26. On order, MP maintain continuous surveillance of all the assigned NAIs or enemy reconnaissance avenues of approach into a particular sector. This is accomplished by setting up a series of OPs. MP may conduct active mounted patrols to extend their observation limits or to cover dead space and the area between OPs. Refer to Chapter 4 for more information about setting up OPs/LPs.
6-27. Once the platoon leader understands what his surveillance requirements are, he task organizes the platoon and any assigned assets to achieve the most effective surveillance of the avenue or NAI.
6-28. Unlike a scout platoon, MP focus on providing early warning of enemy reconnaissance elements rather than gaining and maintaining contact with the enemy's main body or destroying it. During screen missions, it is important to understand that an MP platoon by itself does not have enough assets to both acquire and kill an enemy reconnaissance larger than the engaging element. Generally, other assets will be given the specific mission of killing these forces. If MP are ordered to engage enemy forces, they do so by engaging at the maximum effective range of their organic weapons. If available, the platoon leader also plans for and uses CAS and indirect fire.
6-29. During surveillance the platoon's ability to report is critical. Effective early warning requires detailed planning for uninterrupted communications. The platoon leader considers communication distances and significant terrain features to identify potential wireless communication problems. If problems exist, he requests support from the higher HQ.
COUNTERRECONNAISSANCE
6-30. MP contribute to the commander's concept of operations by conducting security and reconnaissance missions designed to detect, disrupt, and impede enemy reconnaissance elements. Counterreconnaissance is not a distinct mission; rather, it is a combination of measures taken by friendly forces to reduce the threat's ability to gather information. It contains both active and passive elements and includes combat action to destroy or repel enemy reconnaissance units.
6-31. Counterreconnaissance prevents enemy reconnaissance forces from observing the main body of friendly forces by defeating or blocking the enemy forces. In the execution of counterreconnaissance, MP operate either offensively or defensively using whatever tactics best accomplish the mission. The principal techniques used are—
6-32. MP must task organize to defeat enemy reconnaissance forces. Enemy reconnaissance capabilities in any given situation must be compared to the MP unit's capabilities to determine if additional maneuver or CS assets are required.
6-33. Conventional reconnaissance elements are usually squad-size or smaller. However, special-purpose reconnaissance forces can consist of mechanized forces up to company size. In all counterreconnaissance operations, the goal is to acquire, identify, and kill the enemy reconnaissance force after it has penetrated the initial screen line. Defeating such forces usually requires combined-arms forces, but this is dependent on the type, size, and capabilities of the reconnaissance element.
6-34. MP platoons are not organized or equipped to fight for extended periods or to destroy enemy armor vehicles. MP employ AT weapons, such as AT-4s, for defensive purposes (self-protection and breaking contact). However, MP teams are highly skilled at reconnaissance and surveillance and providing early warning of enemy activity.
6-35. A scout platoon acquires and identifies enemy reconnaissance forces along a screen line, which is a control measure usually named as a phase line, and is an established forward of the main body. MP conduct their counterreconnaissance efforts in a similar manner in the rear area or anywhere sustainment operations are taking place.
6-36. In most cases, the scout platoon cannot be expected to acquire, identify, and defeat enemy reconnaissance elements. As a CS asset, MP can assist a scout platoon by locating the enemy reconnaissance element, freeing the scouts or TCF to perform the killing function of counterreconnaissance on larger mechanized enemy reconnaissance elements. MP activities that contribute to counterreconnaissance include—
6-37. Conventional threat reconnaissance elements push far out in front of their combat unit to gain intelligence on their rear area objective. Unconventional threats such as terrorists, criminals, or gangs may try to observe installations, deep-water ports, or other facilities to obtain information. Conventional threat reconnaissance efforts are concentrated on gaining intelligence on the capability of friendly forces. Unconventional threats try to obtain information to plan sabotage or criminal activity, or to simply disrupt the efforts of friendly forces.
6-38. MP leaders plan measures to counter enemy reconnaissance by coordinating with various staff sections and agencies that include—
MI for information on enemy capabilities, likely rear area targets and objectives, likely enemy reconnaissance avenues of approach, and the commander's critical information requirements (CCIR).
The PM and criminal investigation division (CID) for HN police information on local gangs, known criminals, and criminal activity.
6-39. To assist commanders with their counterreconnaissance efforts, friendly forces such as MP, CID, engineers, and MI conduct physical security surveys and vulnerability and risk assessments of bases and base clusters, deep-water ports, and air bases. They advise commanders of these facilities on security measures designed to prevent the threat from gaining access to friendly forces and facilities.
6-40. During AS missions, MP conduct security activities around NAI; critical assets, such as communications nodes; and air bases. MP perform area and zone reconnaissance of all terrain that dominates critical facilities. They concentrate their efforts on locating enemy reconnaissance forces. MP deny the enemy the opportunity to observe friendly forces by reporting their location, maintaining surveillance, and assisting in their destruction if required.
6-41. Enemy reconnaissance forces are not likely to use primary reconnaissance avenues of approach to gather information on friendly forces. MP teams are more likely to come in contact with enemy reconnaissance forces operating on trails, rough terrain, and dead space that allows mounted movement. They use the cover of darkness for their operations. MP must make maximum use of NVDs and illumination to help detect their movement. They put the devices on key terrain and along avenues of approach to critical bases, and cover the area with crew-served weapons. Enemy reconnaissance teams are most vulnerable during the day. MP concentrate daytime mounted or dismounted operations on locating their base camp or hide positions. Once they are discovered, if ordered to do so, MP can lay ambushes on likely routes to destroy them. Refer to Chapter 4 for more information about ambush patrols.
6-42. Mounted MP patrols use overlapping search techniques to make it difficult for enemy reconnaissance teams to reach their objectives without being exposed. Overlapping searches provide random coverage not easily predictable by simple observation.
6-43. If contact is made, MP may be directed to maintain contact or surveillance until enough force can be assembled to counter the threat. They disrupt their movement and delay them until a large enough force is available to defeat them. If directed to disrupt or delay, they clearly identify the enemy before engaging them; there are generally numerous friendly forces operating in the rear area. MP must consider fratricide preventive measures. Refer to Appendix F for more information about fratricide avoidance.
6-44. MP make good use of terrain and maximum use of weapon systems. They use harassing fire from mounted crew-served weapons (MK19/M2), but do not become decisively engaged. They deceive the enemy with heavy harassing fire from crew-served weapons. If available, MP destroy the threat with indirect fire. MP make the threat believe he has encountered a defense. The enemy must not realize these actions are only delaying tactics.
AREA DAMAGE CONTROL
6-45. ADC is basic to successful rear-area operations. ADC measures are taken before, during, and after hostile actions or natural or man-made disasters to minimize effects and reduce damage. All commanders try to limit the impact of enemy actions and reestablish unit operations as quickly as possible. Commanders at each level plan ADC operations.
6-46. ADC operations integrate the functions of many specialized units. Engineers plan and coordinate ADC operations at the site. Medical teams help sort and treat mass casualties and assist in initial evacuations. Army aviators help evacuate casualties and provide emergency resupply, communications relay operations, area damage assessment, and C2 actions. MP expedite and control battlefield movement into, around, or through damaged or contaminated areas. Signal elements reestablish the signal system. HN civil efforts, like clearing rubble and providing facilities and services, can greatly aid ADC.
6-47. The amount of MP support needed for ADC depends on the extent of the damage, the importance of the affected area, and the effect of the damage on the movement of troops and logistical supplies. Enemy attacks on key military facilities can leave them unprotected. Heavy damage in urban civilian areas can disrupt local government services.
NOTE: Protecting civilian facilities is a HN responsibility. However, MP preserve law and order in such an area if so doing protects friendly forces and resources.
6-48. Route and area reconnaissance are key to determining the trafficability of the routes into, out of, and around affected areas; obtaining a damage assessment, and having early warning of the continued presence of the enemy. MP determine the level and extent of NBC contamination and identify the location of critical points affected by damage.
6-49. The enemy's damage to the terrain determines the degree and kind of MP support needed and where to place the priority of effort. Downed trees, urban rubble, damaged or destroyed bridges, cratered roads, and contaminated road networks affect circulation control. If the roads can be traveled, MP provide circulation control operations locally in the affected area. However, damage to an area may be so great that roads must be closed and MSR traffic rerouted.
6-50. MP give priority of movement to ambulances transporting wounded and engineers clearing debris. They maintain law and order in the affected area by employing measures to stop looting and unlawful behavior, according to the ROE and the use of force requirements. They disseminate key information such as the location of first aid stations, emergency shelters, and other emergency facilities.
6-51. Security patrols may be needed around key facilities. MP may need to set up an OPs/LPs to observe sectors of the affected area. The OP/LP teams can watch for enemy agents trying to exploit the effects of a conventional attack through arson, sniper fire on firefighters, or other disruptive acts. The OPs/LPs also watch for theft, pilferage, or arson against military property.
6-52. MP ADC operations may be either part of an ongoing operation or a separate requirement. During ADC, MP—
Note and report the development of critical points caused by damage to bridges, tunnels, and the like.
Prevent sabotage, looting, and pilferage in the damaged area.
Protect property, contain panic, and enforce emergency restrictions.
Direct persons to first aid stations, emergency shelters, and other emergency operations.
Post temporary signs to prevent entry into unsafe buildings or redirect activity to temporary locations.
Operate mounted and dismounted mobile patrols, checkpoints, and roadblocks to—
BASE DEFENSE
6-53. Base defense is the local military measures, both normal and emergency, required to nullify or reduce the effectiveness of enemy attacks on, or sabotage of, a base to ensure that the maximum capacity of its facility is available to friendly forces.
6-54. The base commander organizes and controls the forces assigned to a base to best capitalize on their capabilities. These forces may be joint or single-service forces operating in the joint rear area (JRA). If a base, base cluster, or air base comes under attack, the base commander responds within his capability. Defense fundamentals, as they pertain to the defense of the bases, include the following:
Understand the enemy. Defenders must be familiar with the capabilities and limitations of the enemy forces, weapons, equipment, and tactics.
Use situational awareness. Intelligence operations are key to assembling an accurate picture of the battle space.
Use the defender's advantages. The defender's advantages may permit a numerically inferior force to defeat a much larger one. These advantages include—
- The ability to fight from cover.
A more detailed knowledge of the local terrain and environment.
The ability to prepare positions, routes between them, obstacles, and fields of fire in advance.
The ability to plan communications, control measures, indirect fires, and logistic support for contingency operations.
The ability to deceive enemy forces about friendly defensive capabilities, dispositions, and execution of operations.
Concentrate at critical times and places. Conduct the defense of a base along interior lines, permitting the timely and secure movement of forces to engage the most critical threats. The commander must mass combat power at points of decision by economizing in some areas, retaining a reserve, and maneuvering to gain local superiority at critical points.
Conduct counterreconnaissance and counterattacks. Fixed bases have well-established perimeters that usually have limited depth. Counterreconnaissance and counterattack add depth to the battle, outside the perimeter, allowing the base to continue its primary mission with minimal interference.
Extend counterreconnaissance patrols 3 to 5 kilometers outside the perimeter, based on terrain. This reduces the risk of fratricide, especially at night.
Coordinate critical defense assets. Synchronization of indirect fires, air defense resources, tactical aircraft, engineers, dismounted troops, armored vehicles, naval surface fire support, and helicopters can produce a combined-arms effect.
Balance base security with political and legal constraints. This fundamental is especially critical in a low-intensity conflict environment.
Know the law of war and ROE. Base commanders and their subordinates must comply with ROE. In joint-service operations, reconcile inconsistencies with ROE.
6-55. A base or base cluster has certain inherent capabilities which allows it a degree of defense. Each base has a BDOC that plans, coordinates, and supervises base defense operations. The BDOC initiates contingency planning that enables the base to—
Increase the manning posture of the base as the threat level increases.
Defend against heavier enemy forces until the response force is committed.
Support the fire and movement of the response force operating outside the base.
6-56. Each base cluster has a BCOC to monitor base defense plans and establish the base cluster response force. The BCOC—
Provides C2 of resources for planning, coordinating, and supervising the defense of the base cluster.
Maintains communications with the BDOC within the cluster, MP, and the supporting RAOC.
6-57. MP leaders plan for the interface of their support into the base plan. The plan requires—
Secure and redundant communications systems at all guard locations (a landline, radio links to the BDOC, and a telephone hookup to the center switch).
6-58. All plans and overlays depicting MP support are forwarded through normal MP channels to the BCOC.
6-59. Any threat to the bases must be dealt with swiftly. Few sustainment units can continue their mission while under attack by even a low-level threat.
6-60. Sustaining operations rely on MP to stay apprised of enemy activity near bases. MP forward early warnings of enemy activity to the operations cell at the rear CP. The rear-operations cell immediately notifies the subordinate RAOC and the base and base clusters. It may also alert the response force.
6-61. If a base or base cluster comes under attack, the base commander responds within his capability. However, interruptions of base sustainment operations must be kept to an absolute minimum. If a threat exceeds a base's ability to defeat it, the base commander requests response force support.
DANGERBase defense forces must be aware of the disposition of other friendly forces in front of them. Fire discipline between the response force, mobile reserve, and TCF is imperative. Positive control must be maintained at all times. |
AIR BASE DEFENSE
6-62. The Army is responsible for defending air assets from ground threats outside the boundary of the air base and its area of responsibility (AOR). ABD forces are tasked to defend particularly critical air bases. They may be forces operating in the area specifically on call for ABD or they may be the rear-area response force.
6-63. Air Force security forces (AFSF) are responsible for the internal security of US air bases. HN and US Army forces are primarily responsible for external defense of US air bases. Given the size of an air base and the high priority as a threat target, providing ABD as a dedicated asset requires a force larger than a company. MP do not have the force structure to be dedicated solely to ABD operations. However, an echelon commander could decide to redirect MP mission priorities to ABD and deploy his limited MP assets to serve as part of a larger composite force, such as a TCF. Or an MP response force may be required to respond to threats beyond the base's capabilities.
6-64. MP operating as part of a larger ABD force may provide support that includes —
Setting up roadblocks and checkpoints to limit access to the base.
Occupying OPs/LPs and fighting positions on key terrain and likely avenues of approach to the air base.
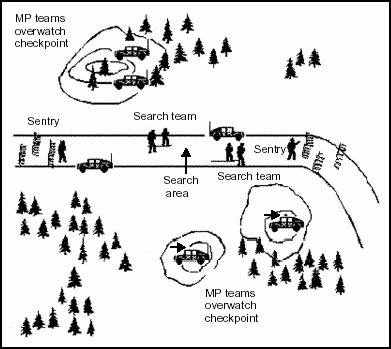
6-65. A typical ABD layout consists of a base perimeter that surrounds the runway and the facilities that support air base operations. The tactical perimeter of a base is the outer most ABD tactical AOR. It is where defense forces cover, patrol, or occupy likely avenues of approach to the base and other key terrain. Figure 6-5 shows a typical ABD layout.
Figure 6-5. Typical ABD Layout
6-66. Commanders develop unit SOPs and contingency plans for ABD. SOPs should address C2 and fire support issues that are different for ABD. However, AS plans for ABD provide for increased security patrols and static security measures around an air base the same as they would for other critical facilities.
6-67. The depth of the defense area surrounding the air base depends on METT-TC and other defensive planning factors. MP activities that support ABD are concentrated in the tactical perimeter and on key terrain adjacent to the tactical perimeter.
FIRE SUPPORT
6-68. Organic AFSF fire assets typically available are the M29 81-millimeter mortar, the MK19, and the M2 .50 caliber machine gun (MG). These fire systems are incorporated into the base defense plan for both the security force (SF) and MP. This ensures compatibility with all ABD measures in the surrounding area and mutual support to other bases when practical.
6-69. The use of mortars and other indirect-fire weapons located in the defense area is coordinated through a 5-man FDC located at the air base BDOC. The AFSF primarily uses its mortars for illumination, suppression of enemy indirect-fire weapons, and suppression of enemy surface-to-air missile (SAM) capability. AFSF weapons controlled by the FDC vary. The number of weapons available depends on the size of the air base.
6-70. CAS is obtained from aircraft at the base. Aircraft may be sent aloft to provide CAS or targets may be assigned to aircraft already airborne. CAS provides suppressive fire or increased detection capabilities. Among the CAS aircraft that may be available, the AC-130 Spectre gunship and the A-10 Thunderbolt II both have night-flying capability. Both have compatible frequency modulated/modulation communications equipment. Both are especially effective for use against targets considered danger close to ABD forces. However, they are very susceptible to SAM.
DANGERABD forces must be aware of the disposition of other friendly forces in front of them. Fire discipline between AFSFs response forces, mobile reserves, and the TCF is imperative. Positive control must be maintained at all times. |
COMMUNICATIONS
6-71. Joint communications for all forces supporting ABD must be compatible. Communications must be secure, have redundancy, and possess the ability to integrate all security forces.
6-72. Effective coordination must be an ongoing process. Call signs, frequencies, and SOI are exchanged between all joint, combined, and coalition forces supporting ABD.
MILITARY POLICE RESPONSE TO AIR BASE DEFENSE
6-73. Air bases are normally located in the rear area. Threats that are beyond the capability of the base may require the deployment of an MP response force. In general, the response force responds to an air base the same as any other base or base cluster. However, as a joint service operation there are C2 and fire support differences. Company and platoon tactical SOPs for ABD should be developed to help speed the response time.
6-74. The response force leader coordinates with the Air Force defense force commander (DFC) for the current tactical situation and threat. When committed, the MP response force may transition to the operational control of the DFC. This ensures that MP actions do not interfere with air sorties being generated by the air base commander.
6-75. The DFC is in charge of all aspects of ABD operations. He provides guidance on where the response force is needed and informs the response force leader of the tactical situation. The response force leader directs the tactical operations of MP elements, keeping the DCF informed. If a TCF must be called to defeat a Level III threat, all units, Air Force and Army, are under the OPCON of the TCF commander until the threat is defeated.
6-76. For the local ground defense of their base, the Air Force provides a BDOC which operates similar to an Army BDOC. It is responsible for combat intelligence, combat operations, logistics, and personnel administration. It collects the ground combat intelligence within the ABD area.
6-77. The AFSF maintains a mobile reserve force. The mobile reserve's purpose is to mass enough firepower to destroy threat forces within the air base boundary or, at least, delay the threat until a larger force can be assembled. The mobile reserve is usually a mounted force. It is under the direct control of the BDOC. The mobile reserve tries to contain any direct landing by threat forces on the airfield. It responds to penetrations of the defense area by forces that have managed to elude external defense forces.
6-78. If the enemy penetrates deeply into the defense area, the response force leader can request that the BDOC commit the mobile reserve to battle. This may prevent the premature commitment of the TCF. Contact points and AAs are established around the base to assist in integrating the mobile reserve during combat operations outside the ground defense area.
6-79. The response force must keep the enemy from destroying resources on the ground and interrupting or stopping air operations.
Night Operations
6-80. Air bases are most vulnerable when visibility is limited. In response to the threat, the bulk of both internal and external ABD operations must be dedicated to detecting threat forces during periods of limited visibility. The large gaps between defensive positions facilitate enemy infiltration through external defenses. To narrow these gaps during limited visibility, external defensive efforts may have to be set up closer to the perimeter. External defensive efforts should integrate the extensive use of—
Water Obstacles
6-81. Many air bases border water obstacles. Air bases located next to rivers, lakes, or oceans provide unique ABD problems. Threat efforts directed against an air base from the water include infiltration, reconnaissance, and standoff-weapons attacks. As a result, water obstacles that penetrate the defense area may require ABD forces to set up continuous battle positions between the water and any critical air base facility near the water. ABD obstacle plans should include fences, mines, and sensor employment along the portion of the perimeter that borders water. Planned fires are coordinated to defeat watercraft. Floating expedient barricades may have to be assembled. Warning buoys should also be anchored offshore. Underwater approaches provide excellent avenues to air bases. They must be considered during ABD planning. Joint support from the Navy and the Coast Guard may also be needed.
Urban Terrain
6-82. Air bases bordered by urban areas pose a special challenge for ABD operations. Increased security is a necessity. MP must be aware of underground approaches, such as sewers, that could bypass defensive positions. Threat forces, saboteurs, and special-purpose forces will use these avenues of approach to gain access to the air base.
6-83. Infiltrating groups will be very difficult to detect because they avoid direct confrontation and usually move at night. These teams have the greatest potential for disrupting air operations throughout the rear area.
CHECKPOINTS AND ROADBLOCKS
6-84. Checkpoints and roadblocks are set up to control the movement of vehicles, personnel, and material and prevent illegal actions or actions that aid the enemy. They are used to prevent trafficking in contraband and stop the movement of known or suspected belligerents. Checkpoint and roadblock operations contribute to the commander's information and intelligence collection process. Additionally, they assist friendly forces in detecting and establishing the behavioral patterns of the local populace.
6-85. When conducted improperly, checkpoints and roadblocks can foster resentment toward US forces. MP minimize the negative impact that checkpoints and roadblocks may have by treating local nationals with dignity and respect. Whenever possible, checkpoints and roadblocks should be conducted with interpreters, HN police, or other HN authorities.
6-86. In most stability and support operations there exists the potential for threat forces to attempt to exercise some level of force against US forces. Checkpoints and roadblocks may become prime targets for threat forces (both traditional and nontraditional). METT-TC determines the level of self-protection needed at a checkpoint or roadblock. However, MP leaders must always plan force protection measures that allow their forces to quickly implement adequate self-defense when threatened.
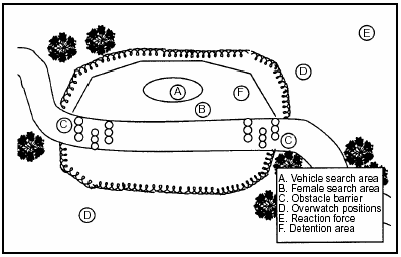
6-87. Checkpoints and roadblocks must be designed so that potential threat forces are discouraged from attempting to disrupt its operation or try to inflict casualties. MP use armored vehicles whenever possible to support the dismounted troops operating the checkpoint or roadblock. The MP security element assigned to protect the site should have an antiarmor capability. The vehicle search area should be located in an area that provides blast protection.
Checkpoints
6-88. Checkpoints are part of a police action. As such, the ROE and the use of deadly force must be clearly understood by all soldiers participating in the operation. MP use the minimum intrusion and imposition necessary to accomplish the mission and protect the force. They allow for a vehicle escape route and plan to destroy a hostile element who uses it. If the checkpoint is completely sealed off, an enemy will have to penetrate it by attempting to run over the barricades. This puts the search team in a position to have to defend itself and fight back.
6-89. MP establish and operate two types of checkpoints—deliberate and hasty.
6-90. Deliberate Checkpoint. A deliberate checkpoint is a fixed position set up on a main road in a rural or built-up area. It can be classified as either a heavy - or light-traffic checkpoint , depending on how much traffic is expected to pass through it. A heavy-traffic deliberate checkpoint normally requires a platoon. An MP squad can only operate a light-traffic checkpoint for a short duration (12 hours or less).
6-91. To operate a heavy-traffic checkpoint, task organize the platoon into—
A HQ element. The HQ element is responsible for C2 and maintaining communications with subordinate elements and higher HQ.
A security element. The security element is an MP squad that provides early warning to the search and assault element, watches for and reports suspicious activity, and monitors traffic flow up to and through the checkpoint. The security element should have an antiarmor capability to protect the site from an enemy armor threat.
A search element. The search element is an MP squad that halts vehicles at the checkpoint, guides them to the designated search point, conducts personnel and vehicle searches, and directs cleared vehicles on through the checkpoint.
An assault element. The assault element is an MP squad responsible for destroying (consistent with the ROE) any hostile element that forces its way past the search team. The squad leader places his soldiers beyond the search point and emplaced zigzag obstacles and barriers. The soldiers prepare and occupy fortified fighting positions. When confronted by a threatening vehicle, the search element gets out of the way and allows the vehicle to pass. The vehicle passes through the escape lane, and the assault element makes the decision whether to engage or not. If the assault element has to engage, the battle will occur away from the checkpoint. This reduces the possibility of fratricide to friendly forces or injury to innocent civilians.
6-92. In smaller checkpoint operations, a squad can be organized in a similar fashion. MP elements use handheld portable radios, if available, or wire communications. However, much of the needed signals at a checkpoint or roadblock can be easily accomplished using arm and hand signals.
6-93. A deliberate checkpoint is organized into sections (Figure 6-6). The physical layout and detail of preparation depend on the amount of traffic that will pass through it and the duration of its operation. Normally, a deliberate checkpoint will require engineer support to construct obstacles, barriers, escape lanes, and possibly fighting positions. All checkpoints consists of—
Figure 6-6. Deliberate Checkpoint
6-94. Hasty Checkpoint. MP set up hasty checkpoints to achieve surprise. They are temporary and should be moved often. The materials used to construct these checkpoints are carried by the platoon. The platoon or squad uses its vehicles, reinforced with concertina wire, as the obstacle. MP may employ tire deflation devices or road spike stripes. These devices are more effective than concertina wire and may be less intrusive in peace operations. They are commercially available or can be locally fabricated.
6-95. MP position the vehicles to partially block the route (Figure 6-7). MP conduct the search in the area between the vehicles. MP are positioned at each end of the checkpoint. They cover them by mounted or dismounted automatic weapon positions. MP conceal a reaction force (at least one team) nearby to react in case the site is attacked.
Figure 6-7. Hasty Checkpoint
6-96. MP establish hasty checkpoints where they cannot be seen by approaching traffic until it is too late to withdraw. Good locations to set up hasty checkpoints include—
6-97. Vehicle Searches. Two members of the search team position themselves at both rear flanks of the vehicle undergoing a search, putting the occupants at a disadvantage. These soldiers maintain eye contact with the occupants once they exit the vehicle and react to any threat attempts by the occupants during the vehicle search.
6-98. The actual search is conducted by two MP armed with pistols only. One MP conducts interior searches and the other performs exterior searches. They instruct the occupants to exit the vehicle during the interior search and instruct the driver to watch the vehicle search. Once the interior search is complete, they escort the driver to the hood of the vehicle and instruct him to open it. Once the engine compartment has been examined, they instruct the driver to open the other outside compartments (tool boxes, gas caps, trunks, and so forth). The driver removes any loose items that are not attached to the vehicle for inspection. Members of the search team rotate positions to allow for mental breaks.
6-99. MP use MWD teams, mirrors, and metal detectors to thoroughly search each vehicle for weapons, explosives, ammunition, and other contraband. Depending on the threat level, the vehicle search area provides blast protection for the surrounding area.
6-100. Personnel Searches. MP may be required to conduct personnel searches at the checkpoints. Every attempt should be made for HN authorities to conduct, or at least observe, searches of local nationals. Additionally, MP leaders must plan for same-gender searches. Personnel searches are conducted only when proper authorization has been obtained, usually from higher HQ, according to the ROE, Status of Forces Agreement (SOFA), or HN agreements. This does not preclude MP from searching individuals that pose a threat to US or other friendly forces.
6-101. MP may have to detain local nationals who become belligerent or uncooperative at the checkpoints. The OPORD and the ROE must address the handling of such personnel. In any case, self-protection measures should be planned and implemented according to the orders from higher HQ.
6-102. Searches of local nationals should be performed in a manner that preserves the respect and dignity of the individual. Special consideration must be given to local customs and national cultural differences. In many cultures it is offensive for men to touch or even talk to women in public. Searchers must be polite, considerate, patient, and tactful. MP leaders must make every effort not to unnecessarily offend the local population. Such situations can have a very negative impact on peace operations and can quickly change popular opinion toward US and other friendly forces.
6-103. Each captive is searched for weapons and ammunition, items of intelligence value, and other inappropriate items.
NOTE: When possible, conduct same gender searches; however, this may not always be possible due to speed and security considerations. Therefore, perform mixed gender searches in a respectful manner using all possible measures to prevent any action that could be interpreted as sexual molestation or assault. The on-site supervisor carefully controls soldiers doing mixed-gender searches to prevent allegations of sexual misconduct.
6-104. MP conduct individual searches in search teams that consist of the following:
A searcher. A searcher is the MP that actually conducts the search. He is in the highest-risk position.
Security. Security includes at least one MP to provide security. He maintains eye contact with the individual being searched.
An observer. The observer is a MP leader that has supervisory control of the search operation. He also provides early warning for the other members of the team.
6-105. The two most common methods that are used to conduct individual searches are the frisk search and the wall search.
Frisk search. This method is quick and adequate to detect weapons, evidence, or contraband. However, it is more dangerous because the searcher has less control of the individual being searched.
Wall search. This method affords more safety for the searcher because the individual is searched in a strained, awkward position. Any upright surface, such as a wall, vehicle, tree, or fence may be used.
6-106. If more control is needed to search an uncooperative individual, the search team places the subject in the kneeling or prone position.
6-107. Strip searches should only be considered when the individual is suspected of carrying documents or other contraband on his person. This extreme search method should be conducted in an enclosed area and by qualified medical personnel when available.
Additional Checkpoint Considerations
6-108. The effective use of all task organization elements is vital to the success of checkpoint operations is. Roles and responsibilities must be well defined and rehearsed. Additional considerations when conducting checkpoint operations include—
Preparing and emplacing signs in the local language instructing drivers what to expect and do at the checkpoint (for example, "You are entering a military checkpoint. Prepare to stop your vehicle, and have your identification papers ready for inspection.").
Determining if it is necessary to apprehend or detain those who see the checkpoint ahead and turn around to avoid it. If it is, HN police are responsible for this mission, if they are available. If they are not available, it may be necessary to position a respond force close to the approach route to block or detain vehicles that try to avoid the operation.
Clearing and maintaining control of all buildings and terrain that dominate the checkpoint.
Staying alert for any change of scenery around the checkpoint. A parked car that was not there before, crowds gathering for no apparent reason, or the media waiting for an event are all indicators that something may happen.
Using artificial illumination for night operations, arrange the lighting to keep those passing through the checkpoint in the light and our forces in the shadows as much as possible.
6-109. If HN personnel are used to assist, commanders ensure that they do not represent a national, ethnic, or religious group of faction feared and hated by the majority of the local population.
6-110. Leaders avoid setting patterns by moving the checkpoint location and changing the method of operation at random.
6-111. MP can gain valuable police, criminal, and combat information while operating checkpoints. They use a checklist to standardize the information collection effort. The following information is included in the checklist:
The number and type of vehicles stopped. Report identifying markings, license plate number, and any signs displayed on the vehicle.
The number of passengers in the vehicle. Report the nationality, the ages, and the sex mixes of passengers.
A description of arms, ammunition, explosives, and sensitive items found and confiscated from the vehicle.
Possible or actual sightings of weapons, explosives, or threat forces by the passengers.
The condition of passengers (general health, dress, attitude).
6-112. When conducting checkpoint operations, MP will need the support of the following:
6-113. Sometimes MP are tasked to operate a checkpoint to assist convoys of friendly forces. These checkpoints are set up at the entrance to the controlled route and will have a vehicle holding area to accommodate large convoys. Refer to Chapter 5 for more information about holding areas.
6-114. At the convoy checkpoints, MP check convoy vehicle movement credits issued by the local movement control unit to ensure that the convoy is moving on the correct route at the correct time. When convoys are ahead of schedule, MP hold them near the checkpoint in a vehicle holding area until it is their scheduled time to pass. They allow convoys that are behind schedule to proceed if route traffic permits and assist drivers who have taken the wrong route.
Roadblocks
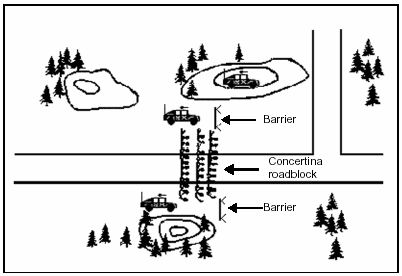
6-115. Roadblocks are set up to stop, slow, or limit movement of vehicles along a route. They are used to limit access to certain areas or roads. A roadblock can be established separate from a checkpoint or used to channel vehicles and personnel to a checkpoint.
6-116. MP use their vehicles with concertina wire, barbed wire, and warning signs as a roadblock (Figure 6-8). If available, armored vehicles make excellent roadblocks. Place a roadblock where unauthorized vehicles or enemy personnel cannot bypass it. If possible, position it so that obstacles like cliffs, swamps, or rivers restrict movement to its flanks or around it. Build man-made obstacles to tie in with and reinforce natural obstacles.
Figure 6-8. Roadblock
6-117. When using a roadblock to channel traffic to a checkpoint, place it where drivers cannot see the roadblock until after they have passed all possible turnoffs. When using a roadblock to close off a road, place it at an intersection to let drivers change to another route with little delay.
6-118. Select a defendable site for the roadblock. Cover the roadblock with automatic weapons. Ensure that defensive positions—
Include a fighting position for the crew-served weapon to provide overwatch for the roadblock.
Have fields of fire that cover the approaches to the roadblock to keep it from being breached.
Are not accessible to an attacker and provide cover and concealment.
Are placed at an intersection to let drivers change to another route with little delay.
Are placed near an area where drivers can turn their vehicles around easily.
RESPONSE FORCE OPERATIONS
6-119. MP response forces may respond to threats to a base, a base cluster, or an air base and possibly respond to downed aircraft. MP are normally the commander's designated force to respond to attacks beyond the capabilities of a base or base cluster. The objective of response force operations is to eliminate the threat or make the enemy disengage without requiring the premature commitment of the TCF. MP are organized and equipped to defeat Level II threats. These threats exceed base and base cluster self-defense capabilities but do not require the commitment of a TCF.
6-120. With prior coordination and appropriate supporting fires, MP can defeat the following:
Small combat units conducting raids, ambushes, and reconnaissance operations.
Unconventional forces conducting diversionary and sabotage operations.
Special warfare intelligence collection and operational missions.
6-121. MP response forces are prepared to delay and disrupt Level III threats, protect the flank of a TCF, or allow a base time to establish defenses in greater depth.
Plan
6-122. METT-TC, the number of MP available, and the commander's intent determine the size of a response force. Normally, an MP response force requires at least a full-strength platoon. However, response force operations conducted in built-up areas or in support of ABD may require a much larger force. MP platoons are not organized and equipped to fight for extended periods. The commander task organizes a platoon for response force operations. A response force should have increased antiarmor capability, integrate available fire support, and have CAS available. The result is a force capable of causing an enemy to break off its attack. The response force can then fix and destroy the threat using close combat techniques and the application of artillery, Army aviation, and CAS.
6-123. MP must know the terrain and be able to use it against the enemy. They mass combat power quickly to destroy the enemy or delay them until a TCF can arrive. The rear CP fire support element, along with the main CP fire support cell, establishes procedures by which MP can call for fire support.
6-124. The response force identifies the location of the bases within their AO, and must know which bases are the most critical and which are the most vulnerable. They include this information in the local IPB. In coordination with the rear CP operations cell and the affected RAOC, they position the response force where they can best—
Detect enemy incursions (near the DZ, the LZ, and the like).
Consolidate quickly in response to threatened key assets in the rear area.
6-125. The response force leader must have the following readily available:
Methods for contacting the BDOC or the BCOC, to include call signs and frequencies.
Call signs and frequencies for supporting artillery and Army aviation units tasked to respond.
Call signs and frequencies for the TCF, RAOC, and the rear CP.
Locations of the nearest medical treatment facility (MTF), NBC decontamination site, and ammunition supply point (ASP).
6-126. Continuous communication with the base and base clusters is the key to knowing how and when an MP response force is needed. Bases and base clusters establish 24-hour communications with the RAOC, if they are located in the corps rear area, or the rear CP, if they are located in the division. This liaison and interface allows timely response and information dissemination.
6-127. The response force will be effective only if it can react swiftly and is thoroughly familiar with the base defense plan. They coordinate all response force actions for a base through its BDOC. (Go through the BCOC for base clusters.) They coordinate the following with BDOC:
Positions of critical internal assets, external coordination points, and no-fire areas.
Engineer support, if needed, to help prepare defensive positions or for ADC.
6-128. In coordination with the main CP fire support cell, the operations cell sets procedures by which MP can call for fire support.
Execute
6-129. Base response force operations rely heavily on MP tactical skills. The choice of action is based on METT-TC and the base commander's tactical assessment. Once a situation develops that requires a response force, there are several options available to disrupt or eliminate the threat. Response force options include the following:
Attack into the enemy's flank using the base for fire support.
Use ambushes along likely escape avenues if it is obvious that the attacking force is not strong enough to overrun the base.
Augment the base's defense forces and provide support from within a base.
6-130. Once the MP company commander receives the mission to direct response force operations, the company's main efforts shift to supporting the response force. The commander conducts a mission analysis and begins the TLPs, culminating in issuance of an OPORD and a FRAGO. Refer to Chapter 2 for more information about TLPs.
6-131. The company HQ coordinates for support that includes communications, air evacuation, and logistical support (Class I, III, V, and IX). The company operations section coordinates with follow-on forces and other support that includes the following:
6-132. Once the platoon leader receives the mission to conduct response force operations he initiates TLPs. Normally, the PSG assembles the response force at a prearranged AA near the base under attack.
6-133. The base commander gives the response force an objective and a tactical AO. He may designate a small force to assist the response force. This force would be under the OPCON of the response force leader.
6-134. Normally, the response force acts as a maneuver element against the enemy. Once the platoon leader develops a COA he designates the ORP and selects a scheme of maneuver. The response force moves to the ORP, establishes security, and reports its status to higher HQ. Once the response force has established communications with the friendly forces under attack, the platoon leader reconnoiters the area and assesses the situation. Based on the situation and guidance from higher HQ the platoon leader may decide to—
6-135. If the decision is made to call for fire to destroy or make the enemy break off the attack, the platoon leader follows the procedures set by the main CP fire support cell. When available, MP can call for and adjust indirect fire provided by artillery. Another option is CAS, if there is a tactical air control party or army aviator trained in joint air attack team operations. Refer to Chapter 3 for more information about call for fire and fire support. Also refer to FM 6-20 .
6-136. If the response force is ordered to attack and destroy the enemy, the platoon leader immediately prepares the response force for a hasty attack.
6-137. Plan a Hasty Attack. A hasty attack is an immediate action taken without extensive preparations, with the resources at hand and, if by so doing, the attacking element can maintain momentum or take advantage of the enemy situation.
6-138. The platoon leader uses fire support to complement the scheme of maneuver. The goal is to kill as many enemies as possible and suppress the rest to keep them from seeing or shooting the maneuver element as it closes on the objective. The attack plan includes the use of all available direct and indirect fire. The response force leader mainly plans and directs the fire of his organic weapons (MG, M203, AT-4, and MK19). The fire element's makeup depends on how much direct-fire support is needed and what support is to be provided. The initial employment of the fire element includes the following:
Positioning crew-served and M249 weapons on or near the line of departure (LD), when the objective and route to it can be seen and covered by fire.
Positioning some crew-served and M249 weapons on or near the LD and some with the moving element, when the objective can be seen and covered by fire from the LD, but only a part of the route is visible, or when the entire route is visible from the LD, but the objective is not visible or is out of range from the LD.
6-139. Plan control measures at the objective and initial employment of the fire element. If time is available before moving to the assault position, make a second reconnaissance to see if the plan needs changing.
6-140. Conduct the Attack. The platoon leader moves to where he can lead the force and influence the fight. He moves a fire element into the over watch position and has the attacking element move from the LD to the assault position, using covered and concealed positions. If en route to the objective, the patrol should—
Receive indirect fire. Move quickly out of the impact area to a preset point.
Meet obstacles, breach, or bypass them. Report their location if the obstacles might affect follow-on units. Take special care when crossing a danger area like a field, roadway, or creek. Refer to Chapter 3 for more information about moving in contact.
Meet direct enemy resistance before reaching the objective and return fire. Call for and adjust fire on the enemy.
6-141. The platoon leader coordinates action so that the response force hits the enemy with its full combat power. He maneuvers the force to strike the enemy's flank or rear. The response force engages the hostile element with the appropriate level of force. He uses overpowering force on armed combat forces. While in contact—
Immediately assume the best available covered positions, when moving, and at the same time, return fire in the direction of the enemy.
Locate actual or suspected enemy positions and engage them with well-aimed fire.
Distribute fires evenly over the objective when no individual positions have been identified.
Make visual or verbal contact with soldiers on the left or the right. (Platoon members and team leaders make frequent visual contact with the squad leaders. Squad leaders make frequent visual contact with the platoon leader. Relay all arm and hand signals from the platoon chain of command.)
6-142. When resistance is destroyed, the attacking force continues quickly onward to the assault position. They deploy on line just before reaching the assault position. To maintain the momentum, the attacking force passes through the assault position and attack the objective. They halt at the assault position only to allow all the soldiers to come on line to attack at once. The assault position should be as close to the objective as possible to prevent needless exposure to enemy fire.
6-143. As the moving element attacks, the fire element in its overwatch position will cover the attacking element by shooting at the enemy. Before the attacking element moves beyond support range, the fire element moves up to a position from which it can continue its support and shoot at the enemy.
6-144. With the fire element in overwatch, the platoon leader (commander) gives the command or signal to open fire. The fire leader will control the method and the rate of fire. He and the gunners watch the progress of the attacking element and engage targets that threaten it. When crew-served weapons are close together, the fire leader anticipates the masking of their fire and moves the weapons one at a time. When those weapons are separated, each gunner displaces when its fire is masked or when it can no longer support the attacking element. The platoon leader (commander) times the displacement of weapons in a fire element so that the attacking element has continuous fire support.
6-145. Maneuvering begins when the attacking element makes contact with the enemy. As the attacking element maneuvers near the objective, the fire element in overwatch suppresses the enemy with a high rate of fire.
6-146. When the attacking element reaches the objective and closes with the enemy, the fire element walks its fire across the objective in front of the maneuvering element. Then it shifts its fire to supplementary targets (rear of the objective, escape routes) or lifts its fire to keep from endangering the attack element. Soldiers in the element closing with the enemy move singly, by pairs, by teams, by squads, or by a combination of these, using as much cover as possible. As they close, they fire on selected targets to suppress the enemy. Automatic rifles are fired in short bursts across the forces' front. Rifles, M203s, hand grenades, bayonets, and MG are used to overcome pockets of resistance. The advance continues past the objective far enough to shoot at any withdrawing enemy. Firing continues until the enemy is killed or captured or withdraws.
6-147. Once the threat is eliminated, the platoon leader reconsolidates the response force and assembles it at a secure rally point. Refer to Chapter 3 for more information about consolidating and reorganizing.
6-148. Conduct an Attack on Urban Terrain. In military operations in built-up areas, a response force must be able to find, isolate, and evict the enemy concealed in hardened structures. Normally, responding to a threat in a built-up area will call for a larger response force and should be supported by armored fighting vehicles. When attacking and clearing a building in an urban area, try to—
Determine and isolate the area around the objective. In urban terrain it is often hard to pinpoint the enemy's position.
Number the area's buildings and use those numbers as reference points to control movement and for clearing operations.
Retain a reserve force to have the flexibility essential for urban combat.
6-149. Refer to FM 90-10-1 for information about attacking on urban terrain.
Respond to Downed Aircraft
6-150. MP are often required to respond to downed aircraft. This specialized mission requires close coordination with aviation assets. In the event of a downed aircraft, the primary mission is to safeguard the aircraft, render first aid to the crew, evacuate the wounded, and secure the crash site. Normally, this requires MP to be airlifted to the crash site.
6-151. MP leaders plan for downed-aircraft rescue operations as a contingency mission. The primary concern is the safety of personnel onboard the aircraft. The MP leader establishes preplanned lift packages for a mounted or dismounted platoon-size downed-aircraft response force. When organized for downed-aircraft operations, the force must meet the following requirements:
Be prepared to defend the site against Levels I and II threats.
Have internal medical support to treat and evacuate injured personnel.
6-152. Engineer support may be necessary to clear lanes to the downed aircraft and medical evacuation (MEDEVAC) LZs.
6-153. Once the response force arrives at the crash site, the platoon leader immediately establishes security and notifies higher HQ of the exact location, the type of aircraft, and the number of wounded or killed personnel. Medical personnel treat the injured and prepare them for evacuation. The platoon leader selects and secures a MEDEVAC LZ. Once all the injured personnel have been evacuated, the response force continues to secure the crash site until relieved.
6-154. Security at the crash site involves MP preventing the handling or disturbance of the wreckage, theft of any parts, or compromising evidence such as gouges or marks on the ground made by the aircraft. Other security measures include—
Preventing all unauthorized access to the site. This includes media and local authorities.
Prohibiting removal of deceased persons until properly identified by military authorities.
Keeping spectators and the media at a reasonable distance from the site for safety.
6-155. All requests for information will be referred to the Public Affairs Office (PAO). MP at the scene will not release information about the crash to the media.
ENEMY DELAY
6-156. A delay is an operation in which a force under pressure trades space for time by slowing down the enemy's momentum and inflicting maximum damage on the enemy without, in principle, becoming decisively engaged. Normally a delay operation is unlikely to be conducted in a sustainment area. However, bypassed enemy forces could create a situation where a MP response force may be required to delay a threat to buy time for a base to establish defenses in greater depth or to delay an enemy until the arrival of the TCF. MP deliberately conduct a delay only when directed to do so by higher HQ. In that case, higher HQ determines the size of the MP force. In the delay, the destruction of the enemy force is secondary to slowing his advance to gain time.
PLAN
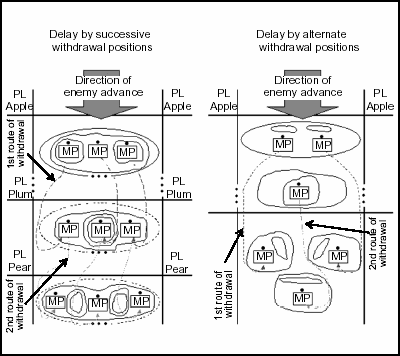
6-157. The platoon delays either from successive positions or from alternate positions. When delaying from successive positions, the delaying force will fight rearward from one position to another, holding each position for a given time or until it becomes decisively engaged.
6-158. When delaying from alternate positions, the delaying force will fight rearward with the force deployed so elements can provide overwatch and subsequent maneuver. While the forward element is fighting, the rear element prepares to assume the action. The forward element disengages. It passes through or around the rear element to prepare to assume the action from a position in greater depth. Use the following methods to delay the enemy (Figure 6-9):
Figure 6-9. Methods of Delaying the Enemy
6-159. The platoon leader develops a plan of action using the factors of METT-TC and the commander's concept and intent. He gives priority to—
Gearing the terrain analysis to the enemy's intent, avenues of approach, and likely positions and targets.
Gaining information from aggressive area patrol and reconnaissance.
Having alternate communications, both sound and sight, ready to be used in case radio communications are disrupted.
Forecasting time. The response force must consider how fast the enemy will close, how long will it take to move off a position, and how long to get to and occupy the next position. In delaying actions, timing can be critical.
6-160. In the OPORD to subordinate leaders, includes the—
Trigger points identifiable on the ground. ("Squad leader, I plan to initiate fires when the enemy reaches the railroad track.")
PLs and delay lines. Include the length of time to delay on or forward of the given position or PL.
Indirect-fire plan (smoke, high explosives [HEs] munitions, artillery-delivered scatterable mines).
Responsibility for adjacent-unit coordination (passage and the like).
Fire control measures, engagement areas, targets, and rate of fire.
Disengagement criteria. ("Squad leaders, I plan to start disengagement when the enemy has three armor vehicles across the railroad tracks.")
Plan for moving after disengagement (signals, breakpoint, use of smoke, and the like).
Subsequent delay positions and routes and the sequence of disengagement.
6-161. Most of the firepower will be oriented toward the enemy. However, flank and rear security must be provided. The platoon leader plans fire support in front of and on both flanks of the positions. He plans fire to cover the disengagement and movement to subsequent positions. He has fire concentrate on breaking up the enemy's advance at long range.
6-162. Higher HQ will resupply, rearm, and refuel the delaying element. On a platoon action, the platoon sergeant is crucial in ensuring that the platoon has the required support to continue a delaying action. The OPORD provides for a central point where the teams or squads can recover.
EXECUTE
6-163. If directed to delay the enemy, the platoon leader moves to a position where he can best control the action. The platoon leader makes good use of the terrain to mask all movements and provide vantage points for observation and harassing fire.
6-164. The enemy will try to bypass a delaying force. The platoon leader tries to keep the enemy in front of or on an oblique angle to the delaying force's position. He prepares positions as thoroughly as time permits, and reconnoiter routes to subsequent positions.
6-165. When selecting delay positions, look for the following:
Clear observation and fields of fire onto the avenues of approach.
Positions offering mutual support and interlocking and flanking fires where possible.
Short, covered, concealed, and trafficable routes to rearward positions.
6-166. If the delaying force has time they—
Emplace obstacles to slow the enemy while they move to rearward positions.
Block obvious routes rearward and direct the force to use more hidden routes.
Consider preparing ambush sites along the routes to slow enemy pursuit.
Have soldiers familiarize themselves with the routes to these positions.
Place the OPs/LPs, and other security means far enough forward to warn the platoon, particularly if the enemy is using a secondary avenue of approach.
Control Fire
6-167. Fire control is extremely important. The platoon engages the enemy at maximum range with all weapons systems. They fire on a prearranged signal or event (trigger point). They aim for leaders and C2 vehicles and avoid premature firing. The platoon leader considers not firing until the enemy reaches a preset point on the ground. Then he uses ambush-type fires to quickly destroy lead enemy elements. This also keeps the enemy from learning the friendly force's size and location.
6-168. If the enemy force cannot evade, it will make every effort to envelop and destroy the delaying force. Avoid presenting an exposed flank to the enemy. Use contact points to help ensure flank coordination.
6-169. Each time the delaying force moves back, it will have less time to plan and prepare. Speed, firepower, and maneuver become more important. The platoon leader calls for added fire support or assistance from higher HQ if decisive engagement or envelopment seems likely.
6-170. If additional elements arrive, the platoon leader uses them to augment the element in contact, employing them on the left and right of the element in contact. The platoon leader ensures that as the element in contact moves back, the left and right elements know to also move, but not at the same time. As the element in contact moves back, the flank screens can open harassing fire. Drawing enemy attention to flank elements will allow the element in contact to disengage more easily.
6-171. The platoon leader keeps higher HQ informed of the situation. Forward elements must not become so heavily engaged that they cannot be withdrawn effectively. If contact with higher HQ is lost, the platoon leader uses initiative. He bases each move on METT-TC, the events on the battlefield, and the tactical commander's intent.
Disengage
6-172. Deciding when to disengage is difficult. If the delaying forces remain too long, they risk decisive engagement or envelopment. If they move too soon, they may give up ground unnecessarily and risk pursuit. The decision of which element to move is based on METT-TC. Move the least heavily engaged element first. To disengage—
Direct supporting elements to engage enemy forces forward of the disengaging element.
Give priority fire, if available, to the disengaging element to rapidly increase its firepower.
Begin an orderly movement to successive or alternate positions.
Place the fire far enough forward to avoid impeding personnel leaving the protected positions.
Move into subsequent positions from the rear and send a SITREP to higher HQ.
Tell the elements left in contact to disengage and take their next positions.
6-173. If it becomes necessary, replace key leaders, give crew-served weapons a priority of manning, evacuate casualties, and redistribute ammunition. Refer to FM 17-95 for more information on defensive tactics used for delays.
BATTLE HANDOVER TO A TACTICAL COMBAT FORCE
6-174. When the combined efforts of the base and base cluster defense force and the MP response force are unable to jointly defeat an enemy threat, the operation becomes the responsibility of the TCF. Coordination is essential to determine when, where, and how the response force gives up responsibility for the fight and the TCF takes over. The MP response force and the base-defense force will then hand over the fight to the TCF by conducting a battle hand over.
6-175. A battle handover (Figure 6-10) is a coordinated operation between two units that transfers responsibility for fighting an enemy force from one unit to another in close-in battle. It is designed to sustain continuity of the combined-arms fight and protect the combat potential of both forces involved. Battle handover is usually associated with conducting a passage of lines. MP leaders must establish clear tactical SOPs that allow their forces to quickly establish the necessary coordination to preclude a loss of momentum in the attack. In a battle handover, the MP response force will pass rearward through the TCF lines while handing over the fight or the TCF will move forward through the MP response force lines to engage the enemy.
Figure 6-10. Planning Considerations for a Battle Handover
6-176. However the fight is handed off, coordination between the MP response force commander and TCF commander is critical. Use a BHL (refer to FM 17-95 and FM 17-98 ) and contact points as control measures to set both forces' responsibilities. Both the TCF commander and the response force leader coordinate the BHL location. The BHL is shown on the operations overlay and in the OPORD as a PL or a boundary. It identifies ground as "owned" by the TCF or by the response force. It sets the location where control of the battle passes from one commander to the other. It is where the TCF can use direct fire and observe indirect fire.
6-177. The handover occurs at the time or event coordinated by the TCF commander. The TCF commander decides the method of handover based on METT-TC. Generally, one of the following methods will be used:
The response force passes rearward through a stationary TCF.
The response force sets up a final blocking position, with elements of the TCF conducting an attack to destroy the enemy.
6-178. Coordination for battle handover normally flows from the TCF commander to the response force leader. Coordination normally includes—
6-179. The most important task for the response force is to maintain contact and continue to engage the enemy. The enemy must continue to see the level of activity that has been established. If the enemy perceives that the handover is occurring, he will attempt to seize the opportunity to destroy the response force.
PASS A RESPONSE FORCE THROUGH A STATIONARY TACTICAL COMBAT FORCE
6-180. The TCF commander coordinates with the response force leader at a designated contact point. The rear CP operations cell dictates the contact point location and notifies both units.
6-181. The contact point should be located forward (50 to 200 meters) of the BHL. It should be near or on easily identifiable terrain features. At a prescribed time, liaison parties from both forces will meet. Normally, a response force representative is sent to the contact point. At the contact point, the TCF commander or his representative briefs the response force representative. Response force teams may remain in the vicinity of the BHL if passage is imminent. TCF security forces screen along the BHL and monitor the response force command net.
6-182. The actions of the elements on the BHL are critical. At the BHL, the TCF scouts, or others assigned the BHL action, pick up the fight from the passing response force elements. If the response force is in contact, its maneuver elements are bound behind the BHL, preferably to a covered and concealed location. At the same time, the TCF elements on the line relieve the pressure on the response force elements.
6-183. At the passage point, where the response force passes through TCF units, response force teams identify passing response force units. They ensure that the passing vehicles are displaying the correct visual recognition signal. TCF scouts on the BHL notify the forward TCF teams by a prearranged signal that contact has been made and friendly forces are at the BHL. Response force elements continue to delay forward of the BHL. Once behind the BHL and covered from enemy direct fire, the response force should—
Confirm that the proper visual recognition signal is still displayed on all vehicles.
Move quickly, in the directed formation, through the passage points and along designated routes to the RP.
6-184. Stationary TCF elements overwatch this movement. The only time the TCF fires is when positive enemy identification is made. At the completion of the handover, response forces may either be released by the operations cell to resume other priority missions or tasked to remain in OPCON to the TCF and continue the fight.
PASS A TACTICAL COMBAT FORCE THROUGH A DELAYING FORCE
6-185. This technique is similar to the response force passing through the stationary TCF. The response force will have more information on the terrain and enemy situation than the TCF.
6-186. The response force leader sets up contact points, passage points, and routes. At the least, he provides guides. The guides meet the TCF at the contact points and lead them along routes to the passage points and/or RPs near the LD and LC.
6-187. The response force maintains normal radio traffic. The TCF and response force operations elements temporarily collocate. The TCF commander assumes control of the battle handover at this time. TCF company teams may maintain listening silence on their TCF command net. The response force guides notify their commander when the TCF begins moving forward from the contact points. As the TCF company teams deploy across the BHL, the response force leader and the TCF commander transfer responsibility for the battle.
6-188. The TCF fire support officer (FSO) may collocate with the response force forward observer (or the individual appointed to act as forward observer for the artillery unit in the AO). Fire missions are approved by the RAOC supporting the response force until the battle handover has occurred. After that, any fire missions for the response force are cleared through the TCF FSO. Response force units provide direct-fire overwatch according to the TCF commander's scheme of maneuver. It is coordinated directly by the TCF commander and the response force leader at collocated command groups.
6-189. Response force direct-fire support depends on the TCF commander's attack plan and the battle handover. However, the stationary unit lifts and shifts its direct fire as coordinated by the collocated command groups.
BLOCK FOR A TACTICAL COMBAT FORCE
6-190. When defending from a battle position, the response force positions its elements to achieve the TCF commander's intent. The response force sets up blocking positions to keep the enemy from escaping. It selects battle positions where it can control, maneuver, and concentrate direct fire on the enemy. As blocking positions are set up, the TCF maneuvers to attack the enemy's flank. The TCF commander and the response force commander set up a contact point for coordination and conduct a reconnaissance of this point, time permitting. The TCF commander and response force leader coordinate C2 and exchange the following information:
What targets must be destroyed to allow the TCF to close on the enemy.
The time, location, or activity to pass control of the battle.
6-191. The TCF and blocking force coordinate so that the TCF flanks the enemy. The response force suppresses the enemy from the front allowing time for the TCF to maneuver into position.
6-192. The TCF commander specifies tasks for the response force to achieve the TCF scheme of maneuver. The response force normally will have to orient its weapon systems on the enemy avenue of approach using TRPs or engagement areas (EAs). The response force may be tasked to—
Control the terrain or block an avenue of approach by holding the battle position against the enemy assault.
Reorient weapons systems on a secondary avenue of approach from supplemental positions or avenues of escape for the threat.
6-193. Refer to FM 17-95 for more information about battle handover.
CRITICAL SITE, ASSET, AND HIGH-RISK PERSONNEL SECURITY
6-194. MP are often tasked to perform security operations that require integration and prioritization from other MP CS operations. During security operations, MP focus their efforts on measures designed to safeguard resources by conducting special security activities that prevent unauthorized access to installations, equipment, materiel, and documents; and safeguard against espionage, sabotage, damage, and theft. An MP security operation includes protection of CPs, convoys, ASPs, deep-water ports, rail, pipelines, and high-risk personnel.
COMMAND POST SECURITY
6-195. CPs are priority targets for enemy attack, and their security can be crucial to the success of military operations. CPs at division, corps, and EAC are designated critical sites and assets. When CPs relocate, MP provide in-transit security. The amount and type of security provided to an established CP depends on whether the CP is dispersed or massed, large or small. In all cases, the focus of MP security efforts is on providing early warning of threat activity. MP possess mobility and communications assets that make them most valuable in operating AS patrols around the CP. Elements do not share a common defensive perimeter in a dispersed CP. Each cell provides its own local security and access control. MP conduct screening operations to provide early warning of enemy activity. In a massed CP where elements share a common perimeter, MP may contribute to perimeter defense with other elements that are collocated at a base.
Division Main CP Security
6-196. All Army of Excellence (AOE) divisions have a main, rear, and tactical CP. Division XXI currently has a division main and tactical CP and a security operations center (SOC). The best use of MP assets to secure any division CP is to employ MP teams to conduct AS around the location of the CP. MP provide early warning of enemy activity by conducting area reconnaissance and surveillance (R&S) of likely enemy avenues of approach to the CP. This security measure also provides the CP with standoff protection from direct enemy fire.
Division Band
6-197. When assigned to augment security operations, the division band should be employed intact, facilitating the commander's ability to quickly return it to its primary mission. The MP commander ensures that the bandmaster and his soldiers know the tactical situation and the defensive plan for the CP when they are assisting in CP security. The band may—
Corps Command Post Security
6-198. Normally, the corps CPs are echeloned into a tactical CP, a main CP, and a rear CP. The corps main CP is generally located in the general vicinity of the division rear boundary. Traditionally, the corps main CP is massed and is a large organization with attendant mobility and signature problems. The corps tactical CP is small, mobile, survivable, and normally located well forward in the vicinity of a division main CP.
6-199. MP security is provided to both the corps main and tactical CPs. How MP elements deploy depends on the CP dispersion, the particular situation, and the METT-TC. The MP company provides corps CP security. If the CP is massed, one platoon secures the tactical CP and the remainder of the company secures the main CP. Or, depending on the METT-TC,—
One squad provides access control within the corps tactical operations center (CTOC).
The remaining squads operate the OPs/LPs and the security patrols.
6-200. The main security efforts and emphasis of MP are on early warning and screening. Both internal access and screening force measures provide CP security. These measures are enhanced by—
6-201. When a corps main CP is dispersed in cells, focus MP efforts on screening force measures. Allocate MP based on the location of the function and the METT-TC.
CONVOY SECURITY
6-202. MP leaders plan and conduct convoy security (specifically convoy escort) using several different methods to secure them as they move through their AO. Primarily, MP secure vehicle movement by maintaining security in the area that a convoy will pass through. MP also conduct route security on a specific route for a designated period during which multiple convoys move unimpeded.
6-203. The main threats to convoys are mines and ambushes. Convoys are vulnerable to sniper fire, long-range fire from artillery, mortar, threat aircraft, and AT-guided missiles. They are also vulnerable to remotely controlled mines and demolitions. Armored vehicles are better suited to provide convoy escort protection. Leaders carefully evaluate the threat before assigning a convoy escort mission to HMMWV-equipped units.
6-204. When MP conduct convoy escort security missions, platoons normally escort the convoy through their AO and pass responsibility for escort to adjacent platoons as the convoy moves from one platoon's AO to another. However, some situations may require a platoon to escort a convoy from its SP to its final destination.
6-205. Whatever method is used to secure the convoy, MP platoons executing the escort mission operate under the control of the convoy commander. The relationship between the MP platoon and the convoy commander provides for unity of command and effort, if combat operations are required during the course of the mission.
Plan
6-206. The platoon leader plans for security of the convoy in all directions and throughout the length of the convoy. This requires MP teams to be dispersed throughout the convoy formation. When available, locate engineer assets toward the front to respond to obstacles. If a fire-support team (FIST) is attached, locate it near the platoon leader.
6-207. The platoon uses the column formation (Figure 6-11) due to its inherent speed and ease of movement.
Figure 6-11. MP Platoon Escorting a Convoy
6-208. The platoon leader develops a convoy security plan that includes the following:
Enhanced security at critical points such as, bridges, tunnels, key intersections, and other danger areas.
Emergency actions to be taken during ambushes, a sniper attack, an air attack, or an artillery attack.
Coordination with the response force responsible for the AO.
6-209. The platoon leader assigns selected teams to remain with the convoy to provide close-in security, if attacked, and other teams to maneuver toward the enemy to deliver a high volume of fire. Use a scout vehicle to travel ahead of the convoy (3 to 5 minutes) to alert the convoy commander of enemy activity, obstacles, or anything that might disrupt the convoys movement.
6-210. If a tracked armored vehicle is not available to lead the escort, the platoon leader assigns one team as the lead security element. Hardening of all vehicles used for convoy escort missions must be SOPs.
6-211. The platoon leader coordinates with the convoy commander to ensure that all convoy personnel are briefed and fully understand the convoy security plan. If time permits, the platoon leader conducts a joint rehearsal with the convoy commander and all security elements. At a minimum, the rehearsal should cover reactions to an ambush and air and artillery attacks.
React to Ambush
6-212. A well-planned ambush can have a devastating effect on a convoy. The reaction to an ambush must be quick, overwhelming, and decisive. The platoon executes its reaction to an ambush as a drill, taking special care to prevent fratricide. Actions to be taken include the following:
When the ambush is initiated, security vehicles direct their action toward the enemy (Figure 6-12). Selected teams move to covered positions between the convoy and the enemy to suppress the enemy with the highest possible volume of fire and obscure the enemy's view with smoke. At least one team should remain with the convoy and continue close-in security. The platoon leader sends the appropriate reports to higher HQ.
Figure 6-12. Security Vehicles' Actions During an Ambush
The convoy commander continues to control the convoy and maintains radio contact with the security force (MP platoon leader). Vehicles not yet in the kill zone are stopped before they enter. Vehicles in the kill zone are moved out of the zone at the highest possible speed.
The scout vehicle immediately selects a safe area for the convoy commander to move vehicles. The vehicles use a Light Vehicle Obscuration Smoke System (LVOSS) or other smoke to mask movement if possible. This safe area will be the linkup location when the convoy resumes.
The convoy vehicles, if armed, return fire only until the security force positions itself between the convoy and the enemy.
The damaged or disabled vehicles are abandoned and pushed off the route if they are not mission essential.
The MP platoon leader submits SPOTREPs. Based on his assessment of the situation he can call for fire or CAS, or request the response force.
Once the convoy is clear of the kill zone, the MP platoon leader chooses one of the following COAs based on the composition of the escort and the strength of the enemy:
6-213. Normally, MP equipped with HMMWVs move out of the kill zone as soon as the convoy is clear. ASV-equipped security forces may continue to suppress the enemy or execute an assault. The platoon leader decides when to break contact.
6-214. Mines . Command-denoted mines are usually to signal the start of an ambush. When ambush fire comes from one side of the road, the enemy will most likely deploy a second, smaller force on the opposite side. They will deploy mines and obstacles between themselves and the convoy to contain US forces. The ambush force often uses mines to protect its flanks. To avoid damage from mines, drivers must—
Avoid running over foreign objects, brush, or grass in the road.
Watch local traffic and the reactions of people on foot, which may give away locations of mines and booby traps.
6-215. Artillery Attack . If a convoy comes under artillery fire, vehicles must not stop. The convoy continues forward as quickly as possible to clear the area.
6-216. Air Attack . If the convoy comes under air attack, vehicles are dispersed, and soldiers attempt to find cover for the vehicles. Personnel begin firing all available weapons in an antiaircraft effort.
6-217. Obstacles . Obstacles are a major threat to convoys. Obstacles can be used to harass the convoy by delaying it. If the terrain is favorable, it may stop the convoy altogether. In addition, an obstacle or series of obstacles can be used to channel or stop a convoy to set up an ambush. The purpose of a route reconnaissance ahead of a convoy, is to identify obstacles and either breach or find bypasses. The convoy takes actions to reduce or bypass the obstacle. A convoy becomes more vulnerable when it is stopped and its escort force is occupied with tasks required to overcome or bypass the obstacle. For these reasons, security becomes critical, and actions at the obstacle must be accomplished quickly. Security personnel take the following actions at an obstacle:
Direct (convoy commander) a halt when the lead security vehicle identifies an obstacle.
Establish dismounted security and provide security throughout all activities directed by the convoy commander (such as conducting a reconnaissance and breaching the obstacle).
Ensure that all convoy vehicles are aware that the enemy may have buried mines in the area, especially on the road flanks.
6-218. Halts . When a convoy has to halt for short breaks it assumes a herringbone formation (Figure 6-13). Security forces take up protective positions 360-degrees around the convoy and orient their weapons outward. They remain alert and establish dismounted local security. The convoy pulls into the protected area in the center of the perimeter. Stagger the convoy vehicles off the road, if there is no threat of enemy mines, but position them so they can easily pull back onto the road.
Figure 6-13. Herringbone Formation
6-219. When the convoy is ready to resume, the convoy vehicles reestablish the column formation, leaving space for the security vehicles. Once the convoy is in column, the security vehicles join the column, leaving local security dismounted.
6-220. Once all elements are in column, local security personnel mount and the convoy continues.
CONVENTIONAL AMMUNITION SUPPLY POINT SECURITY
6-221. When an MP platoon has been tasked to provide security for an ASP, the platoon establishes internal and external security. The platoon secures the ASP against enemy or criminal activity so that the ASP is able to maintain normal operations. MP leaders coordinate with ASP personnel to verify communications, distress and duress signals, defense plans, and fratricide prevention.
Internal Security
6-222. When MP conduct internal security, they establish a dismount point and allow only authorized personnel access to the ASP. Access is granted according to the local SOP and access and entry control rosters. MP conduct perimeter patrols ensuring that they do not set a pattern and maintain communications with platoon HQ.
External Security
6-223. When tasked to provide external security for an ASP, MP establish an OP/LP for early warning. They establish a TCP at the intersection of the MSR and the ASP access road. The TCP maintains free traffic flow, screens the traffic entering the access road, and controls stragglers and refugees. To further enhance external security, MP employ movement sensors, establish defensive positions, maintain communications with the platoon HQ, and emplace obstacles and physical security measures.
DEEP-WATER PORT SECURITY
6-224. The very nature of a terminal operation generates some different, and frequently more demanding, aspects of physical security. Ports and harbors are prime targets for enemy and criminal activities. The perimeter areas of these facilities are more vulnerable because of the extensive distance and the exposed beach or pier areas. Terminal areas may include fully developed piers and warehouses or may be an unimproved beach where logistics over the shore (LOTS) or roll-on/roll-off (RORO) operations are conducted.
Security Measures
6-225. When MP provide security for cargo in a port, the main effort is to provide security from the perimeter of the port outward. Security measures focus on aggressive patrolling and reconnaissance designed to detect, report, or destroy enemy threats before they disrupt port operations. Measures may also include—
Developing police information and intelligence designed to identify criminal threats operating near the port.
Conducting mounted or dismounted patrols, with MWD if available, around the port perimeter.
Providing a response force to react to incidents inside the port's perimeter.
Providing observation and early warning of threat ground and air attacks.
6-226. When providing security for cargo, MP concentrate their efforts on providing AS in the area used to move cargo from the port to its final destination.
6-227. Inside a port's perimeter, MP security forces limit access to cargoes by—
Operating random mounted or dismounted patrols (with MWD if available).
Using the combined patrols as a response force for incidents inside the perimeter.
6-228. The priority is safeguarding the most critical cargoes waiting to be transferred to land transport. To safeguard stored cargo MP—
Waterside Security
6-229. If the restricted area is a pier or other maritime environment, access from the water must be controlled as well as from the land. Entry on the landward side of a pier can be limited with fencing, pass control, and aggressive patrolling, but the part of the pier that protrudes over the water is accessible from the sides and below. Methods for securing the pier along its water boundaries include—
DANGERPorts pose special dangers for MP foot patrols. MP leaders must ensure that soldiers are thoroughly briefed on the hazards of patrolling too close to the water's edge. |
6-230. While most of the barriers described above will stop or impede access to facilities from boats or swimmers, nets are among the most effective. Well-marked, partially submerged objects are also effective; however, there may be legal prohibitions against the emplacement of barriers that may constitute a hazard to navigation. The barriers should be emplaced only after coordination with and approval by the appropriate legal and HN authorities. Sometimes it is best to just close off the waterside of a pier. A floating boom will keep small boats out. Suspending a cable or chain link net from the bottom of the boom will deny access underwater.
6-231. MP establish at least two security zones on a facility's waterside: the reaction zone and the keep-out or exclusion zone. MP in these zones notify vessels, craft, and swimmers that they are entering restricted waters and should alter their course. MP may stop and search intruders if necessary. Security zones should be extended at least 1,000 meters from the nearest protected asset; however, in some port areas, a security zone this large is not possible. In such cases, other measures, such as boat patrols, must be increased to mitigate the possibility of attack. The two zones are defined as the—
Reaction zone. The reaction zone extends from the high water mark to a distance beyond the maximum range of anticipated waterborne threats is the reaction zone. Inside the reaction zone, MP will stop and challenge intruders.
Keep-out zone. This is the zone closest to the protected assets. The keep-out zone extends from the cargo asset to the maximum range of anticipated threat weapons. MP prevent the entry of all unauthorized craft or vessels into this zone. The tactical response force boat, in this case, may be employed if necessary.
Cargo Security During the Transfer
6-232. To keep cargo secure during transfer from one transport method to another, MP control the traffic moving in and out of cargo handling areas by—
Erecting field-expedient barriers and using truck trailers or other large vehicles to constrict the traffic flow if permanent barriers are not in place.
Limiting entry to mission-essential personnel, vehicles, and equipment, as designated by the port authority.
6-233. If gates are used by other than cargo vehicles, a turnout should be available. Cargo vehicles can pull into it while they are being checked. The turnout must be large enough to handle the volume and size of traffic being inspected. A wooden deck or platform at, or slightly higher than, the level of the truck bed hastens checking; it makes it easier to see the cargo. The platform should be as long as the vehicles being inspected. An empty flatbed trailer could be used.
6-234. Cargo is less likely to be diverted when close observation of cargo documentation and container safety is enforced. Containerized cargo is less likely to be stolen or sabotaged if closely watched as they are filled and sealed. Cargo can be pilfered before the seal is applied. An unsealed container can be moved to a stacking area or someone may apply a false seal, break the seal later, remove cargo, and then apply a legitimate seal. At access control points security personnel—
Inspect inbound and outbound containers. Look for signs of damage or unserviceability.
Inspect containers for the presence of seals and/or locks and hinges. Check their serviceability.
Verify that the document's transport number, container number, and seal number match those numbers on the transportation control and movement document (TCMD).
NOTE: Check seals by handling them, not simply by visually checking them.
TRAIN SECURITY FOR CARGO MOVED BY RAIL
6-235. Military resources moving by rail are often vulnerable to theft, pilferage, and sabotage. Depending on the threat, the cargo's sensitivity, vulnerability, and MP availability, the echelon commander may require MP to protect cargo moving by rail.
6-236. Most train operating crews consist of four or five people-the engineer, a conductor, a fireman, a senior brakeman, and a brakeman or flagman. This crew controls the train. The conductor is the train commander unless a transportation railway service officer is assigned to the train. The train commander is responsible for the train's operation and security. He makes all decisions affecting the train. MP integrate their security efforts with the security efforts of the train's crew. MP watch for and report any discrepancies or interruption to normal procedures at any time during the movement. Information about the movement is usually sent along the movement route by the chief dispatcher through a telephone circuit.
Safety Considerations
6-237. Many regions use electric trains. These trains use aboveground, high-voltage lines and travel at greater speeds. When these high-speed trains pass parallel to a stopped cargo train and MP security forces are dismounted, the train can create a vacuum strong enough to pull a security force member under the wheels of the passing train. Some of the slower-moving trains are referred to as floaters. They travel at much slower speeds than the express trains, cause less vibration, and are much quieter. These trains may not be heard until they are too close to react. All trains pose a risk to MP working in and around them.
6-238. Track switches are another danger to MP while they are dismounted. Track switches are used to alter the course of a moving train or car onto another rail line. Track switches are remotely controlled and operated. A member of the rail crew activates some switches manually at some sites. The inherent danger to dismounted MP is getting a foot caught or crushed as the track is being switched.
Security Force
6-239. Normally, an MP squad is an adequate force to secure railway shipments of sensitive freight, but additional MP may be needed for movement of critical cargo. When required, MP conduct railway security to prevent pilferage, detect enemy activity directed against the train and, within their capabilities, defend the train against enemy attack. In addition to MP, the shipper may send specially trained personnel with highly sensitive cargo. The number of MP in a train security force depends on the—
6-240. When planning rail cargo security, MP—
Review the unit SOP to determine guard force security clearance and weapons qualifications requirements and the use of force and rail security operations training.
Make a map reconnaissance of the route. If time permits, they conduct an aerial reconnaissance. Bridges and tunnels are especially vulnerable.
Coordinate with the HN and other agencies, such as the military traffic management command (MTMC) and movement control team (MCT).
Plan actions at scheduled stops or relief points, deploying MP according to these plans.
Plot the locations of MP units and other friendly forces along the route and note their radio frequencies and call signs.
Obtain an intelligence report covering the route to indicate sites where sabotage may occur, or attacks may be expected, and if thefts and pilferage are likely.
6-241. MP prepare and maintain a record, by car number, of guarded cars in the train. MP may be required to ride in—
NOTE: If only one security car is used, it should be near the center of the train; if more than one is used, space the cars to provide the best protection for the train.
Security Measures
6-242. The shipper is responsible for the security of all carload freight until it is turned over to the transportation railway service (TRS).
6-243. Railway cars are sealed after loading. A seal shows that a car has been inventoried and inspected. The standard method of sealing a railway boxcar door (in addition to padlocks or wires) is by a soft metal strap or cable seal that contains a serial number.
6-244. Maintaining rigid accountability of all the seals is necessary to prevent the undetected replacement of an original seal with another. While sealing does not prevent pilferage, a broken seal is a good indicator that the car and its contents have been tampered with.
6-245. When military vehicles are shipped by railcar, sensitive and high-value items must not be secured in the vehicles. Container express (CONEX) and military-owned demountable containers (MILVANs) are ideal for shipping these and other small items on flatcars since they greatly reduce the chance of pilferage. These containers must be locked and sealed and, if possible, placed door-to-door for additional security.
6-246. Cars containing freight that is likely to be pilfered, high-priority cargo, or special shipments are grouped in the train to permit the most economical use of MP security forces. When flatcars or gondolas are used to transport sensitive or easily pilfered freight, the MP leader positions a security element where it can continuously observe and protect these cars.
6-247. The security force commander conducts a joint inventory and inspection of the seals and locks with the MCT or transportation officer on DD Form 1911 . The security force commander maintains possession of this document and uses it when transferring custody.
6-248. The MP leader ensures that each seal is checked at every scheduled stop (time permitting) and—
Reports broken seals immediately to help pinpoint the time and place of possible thefts.
Dismounts and conducts 360-degree security when the train is stopped.
Notes and reports irregularities in procedures, the presence and/or actions of unauthorized personnel, and deficiencies and incidents that occur.
Conducts a joint inspection of the cars when relieved by another security force while en route. The relief force signs for the train ( DD Form 1911 ). The record is kept on the guarded cars.
6-249. Security personnel obtain a receipt for the secured cars when they arrive at their destination. The receipt is attached to the trip report that includes the following:
Any additional information required by local SOP or command directive.
Any recommendations for correcting deficiencies or for improving future security on the trains.
6-250. Dock workers unload the cars as soon as possible when arriving at unloading points to reduce the opportunity for loss through pilferage and sabotage. MP assets are normally not available for security of freight in railway yards; however, MP must be prepared to conduct stabling and staging operations.
6-251. Stabling operations are conducted when numerous train shipments are held in a rail yard or other locations, such as a marshalling area, for extended periods pending arrival at the final destination. Stabling operations require continuous security that may include establishing perimeter patrols, access control, and a quick-reaction force to respond to internal and external threats.
6-252. Staging operations are not extended like stabling operations. They occur when parts of a shipment enter a secured or unsecured off-load site. The site may be large enough to accommodate the entire shipment or only several rail cars at a time. Security forces may be split and required to maintain security at two locations. Additional security forces may be required based on the METT-TC. Refer to FM 55-20 for more information about security of rail cargo.
PIPELINE SECURITY
6-253. Pipeline systems are widely used in a theater of operations to transport bulk petroleum products or other liquids. Such systems are open to a number of security threats from the point of entry to the point of final delivery. Pipeline systems are composed of storage and dispersing facilities, pump stations, terminals, and extended pipelines. They also include discharging facilities for tankers at ports or other water terminals.
6-254. The type and extent of risk to a pipeline varies with the level of conflict in the AO. In a communications zone (COMMZ), the chief hazard is likely to be pilferage. Pipelines can be tapped by loosening the flange bolts that join sections of pipe or cutting holes in the hose line. The risk rises if gasoline is scarce and expensive on the civilian market. Sabotage is a security hazard during all levels of conflict. It is committed by any method such as simply opening pipe flanges, cutting hose line, or setting fires and causing explosions to destroy portions of the line.
6-255. In areas of greater conflict, the likelihood of sabotage and interdiction increase. Pipeline systems are vulnerable to air attacks, especially at—
6-256. Deploy MP in the best manner to provide coverage to the most vulnerable portions of the pipeline which are at the greatest risk to enemy, terrorist, partisan, and ground attack. MP are best able to provide pipeline security by conducting mounted and dismounted patrols; establishing a LP/OP for early warning; and establishing defensive positions around terminals, pump stations, and aboveground pipeline sections. They patrol isolated areas and remote pumping stations and—
Detect, report, and respond to attacks on or sabotage of the pipeline.
Monitor critical parts of the pipeline on a routine but random basis.
Monitor ground sensors and other intrusion detection devices. These are often used at pump stations and elsewhere along the pipeline to detect and identify threats to the system.
Check line pressure devices in the pipeline and pumping facilities. These devices monitor the flow and detect breaks in the line, which may indicate pilferage of gasoline or other petroleum products.
6-257. Dedicated MP are rarely enough in number for surveillance of an entire pipeline system. Available supporting forces, in the course of their normal duties, assist in observing and reporting items of intelligence for further investigation. Examples of suspicious activities in the pipeline area might include the unusual presence of commercial tank trucks, the appearance of gasoline drums or cans, or the increased use of motor vehicles in fuel-scarce areas.
HIGH-RISK PERSONNEL SECURITY
6-258. Security of high-risk personnel is the responsibility of the US Army Criminal Investigation Division Command (USACIDC). However, due to a limited number of CID special agents, in any theater of operation, MP are often tasked to provide close-in security of protected persons.
Security Considerations
6-259. Normally, the MP company commander designates a platoon leader as the officer in charge (OIC) of the security detail. The platoon leader is given full responsibility for all phases of the security mission, to include the coordination. This allows for a single point of contact for the conduct of the mission. The platoon leader prepares a comprehensive plan to ensure the safety of the designated person. Once the platoon leader receives the designated person's itinerary, he selects an advance team and conducts a reconnaissance of the route and locations the designated person is scheduled to visit.
6-260. Normally, the platoon leader uses organic vehicles and equipment to conduct the mission. If special equipment is required, he makes the necessary coordination through his higher HQ. Personnel selected for the mission are thoroughly briefed on the security plan and their conduct and demeanor during the mission. The security plan should include the following:
Restrictions on individuals approaching the protected person.
Evacuation procedures if the protected person is attacked and the threat cannot be immediately reduced.
Emergency actions to be taken in the event of an ambush or indirect fire.
6-261. Depending on the threat level, selected members of the security team are armed with a M4, a M16, or a M203. When dismounted with the protected person, they provide standoff security out to the maximum effective range of their weapons. Shotguns should be considered shotguns if there is a threat of attack in a congested area where there is danger of injuring innocent persons if long-range weapons were used. Members of the team that are selected to physically escort the protected person should be armed with sidearms only. This allows them to have both hands free to react to close-in threats.
6-262. The security plan must be flexible to allow for itinerary and weather changes and mechanical failures. Once the platoon leader has finalized the security plan, he assembles the security team and conducts detailed rehearsals.
Security During the Visit
6-263. Protection may be accomplished by establishing a series of protective cordons around the protected person. The protective measures used must allow the person freedom of movement and must not interfere with the conduct of his duties. Irritating conduct must be avoided at all times.
6-264. MP must remain alert at all times and provide constant security to the protected person. MP provide security by—
Restricting the circulation of unauthorized personnel around the protected person.
Taking positions where they can observe everything and everyone near the protected person.
Securing the facility of the protected person, but not entering if the protected person does.
6-265. When required to secure a designated person while moving, the mode of transportation must be guarded at all times. Vehicle security normally requires a protected vehicle to transport the designated person, security vehicles to react to threats, and an advance team to travel ahead of the motorcade to provide early warning of threats or hazards before the main body is affected.
6-266. Regardless of the method of transportation, each situation must be evaluated to determine the degree of security that is practical and necessary. Good judgment on the part of the OIC will be necessary in solving the various situations that may exist. Refer to FM 3-19.30 for more information about the security of designated personnel.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|