Bombs
Terrorists have frequently used homemade devices or IEDs to carry out their attacks against DOD personnel, facilities, and assets. The IEDs are ideal terrorist weapons. They are relatively inexpensive to make, and the components of many IEDs are common items that can be obtained from many sources and are difficult to trace. The IEDs can be large or small and be designed so that they are transported to the attack site in components for last-minute assembly. Such design concepts make detection more difficult and provide an additional increment of personal safety to the terrorists.
General
H-1. The use of IEDs can enhance the violence that gives terrorist groups their ability to intimidate or coerce a target population. The detonation itself creates a highly visual, newsworthy scene, even hours after the detonation occurs. Bombs can detonate anywhere, without apparent reason and without warning. The use of bombs in a terror campaign emphasizes the authorities' inability to safeguard the public and maintain law and order. Bombs are ideal weapons because they can be designed to give terrorists opportunities to escape from the scene of their crimes.
Concealing Bombs
H-2. Given the question, "Where have terrorists placed bombs in the past, and where should we look for them?" results in no easy answer. Table H-1 lists a few obvious locations that should be examined. Terrorists who use bombs as their weapons of choice can be very creative in designing and placing their weapons.
H-3. Bombs can be found anywhere people can place them. Without becoming paranoid and seeing a bomb under every rock and behind every tree, the practical answer to the above questions is: "Where they can be easily placed without the bomber being caught."
Damage and Casualty Mechanisms
H-4. The IEDs and other explosive devices inflict casualties in a variety of ways, including the following:
- Blast over pressure (a crushing action on vital components of the body; eardrums are the most vulnerable).
- Falling structural material.
- Flying debris (especially glass).
- Asphyxiation (lack of oxygen).
- Sudden body translation against rigid barriers or objects (being picked up and thrown by a pressure wave).
- Bomb fragments.
- Burns from incendiary devices or fires resulting from blast damage.
- Inhalation of toxic fumes resulting from fires.
H-5. It is impossible to calculate a single minimum safe distance from an IED or other explosive device. The safe distance varies with each device and its placement. As a rule, the farther away from a bomb, the safer the intended or collateral targets are. Blast effects, fragmentation injuries, and injuries resulting from flying debris diminish greatly as the distance between a bomb and possible targets increase. The amount of material in the device, the type of explosive material, the manner in which the device is constructed, and the location or the container in which it is placed all have a bearing on the specific destructive potential for each IED.
H-6. The following are four general rules to follow to avoid injury from an IED:
- Move as far from a suspicious object as possible without being in further danger from other hazards such as traffic or secondary sources of explosion (such as POL storage).
- Stay out of the object's LOS, thereby reducing the hazard of injury because of direct fragmentation.
- Keep away from glass windows or other materials that could become flying debris.
- Remain alert for additional or secondary explosive devices in the immediate area, especially if the existence of a bomb-threat evacuation assembly area has been highly publicized.
H-7. Some terrorists have used two especially devious tactics in the past to intensify the magnitude of casualties inflicted by bombing attacks. In some instances, they have detonated a small device to lure media attention and curiosity seekers to the site; a larger, more deadly device has detonated some time after the first device, thereby inflicting a large number of casualties.
H-8. Other terrorists have used a real or simulated device to force the evacuation of a facility only to detonate a much more substantial device in identified bomb-threat evacuation assembly areas. These attacks are especially harmful because the evacuation assembly areas often concentrate government or commercial office workers more densely than they are when dispersed throughout their usual workplaces.
Telephonic Threats
H-9. When receiving a telephonic threat, treat the call seriously. Often, an anonymous telephone call is made regarding a bomb or an IED. See Figure H-1 for information to record/obtain when receiving these calls.
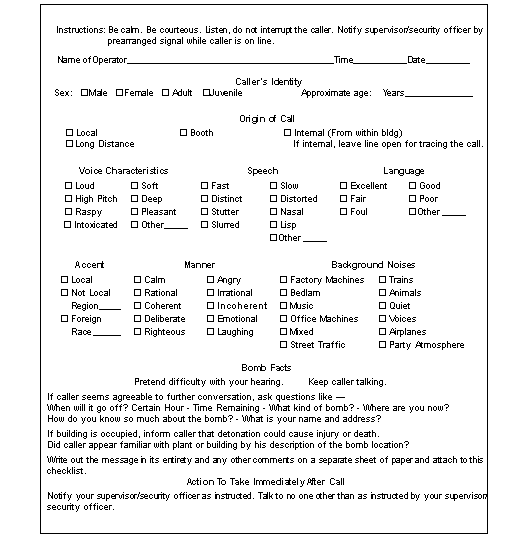

H-10. When an anonymous warning or threat is received, initiate the bomb-threat data card and notify the PMO, security police, security forces, or other law-enforcement/security offices immediately. Local SOPs will determine subsequent actions. Immediate action may include a search without evacuation, the movement of personnel within the establishment, a partial evacuation, or a total evacuation. The following criteria helps determine what immediate action to take:
- Factors favoring a search before the movement of personnel:—
- There is a high incidence of hoax telephone threats.
- Effective security arrangements have been established.
- Information in the warning is imprecise or incorrect.
- The caller sounded intoxicated, amused, or very young.
- The prevailing threat of terrorist activity is low.
- Factors favoring movement of personnel before searching:
Evacuation Drills
H-11. Evacuation and search drills should be performed periodically under the supervision of the installation's or unit's senior officer. The drills should be held in cooperation with local police if possible. Personnel in adjacent buildings should be informed of drills to avoid causing unnecessary alarm.
H-12. Evacuation procedures depend on the circumstances. Prepare, publicize, and rehearse evacuation plans in advance. Address alarm systems, assembly areas, routes to assembly areas, personnel-evacuation responses, building and area clearances, and evacuation drills.
Personnel-Evacuation Response
H-13. The bomb-threat alarm system should be easily distinguished from the fire alarm. When the alarm sounds, personnel should—
- Lock up or secure all classified materials.
- Conduct a quick visual search of their immediate working area.
- Open windows (wherever possible).
- Leave the building, taking only valuable personal belongings.
- Leave doors open and immediately proceed to the assembly area.
H-14. Opening the building will reduce internal damage due to blast effects. It will also somewhat mitigate the extent of debris flying out of or falling from the building should a detonation occur.
Assembly Areas
H-15. Choose the routes to the assembly area so that personnel do not approach the IED at any time. Preselect the routes to the assembly area, but devise a system to inform personnel of the location of the suspected IED and alternate routes. Routes prevent confusion and bunching and avoid potential hazards (such as plate glass, windows, and likely locations of additional IEDs).
H-16. Assembly areas should be preselected and well known to personnel. Establish a clearly defined procedure for controlling, marshaling, and checking personnel within the assembly area. If buildings or establishments are in a public area, coordinate the assembly areas with local police. Assembly areas are selected using the following criteria:
- Locate assembly areas at least 100 meters from the likely target or building (if possible).
- Locate assembly areas in areas where there is little chance of an IED being hidden. Open spaces are best. Avoid parking areas because IEDs can be easily hidden in vehicles.
- Select alternate assembly areas to reduce the likelihood of ambush with a second device or small-arms fire. If possible, search the assembly area before personnel occupy the space.
- Avoid locating assembly areas near expanses of plate glass or windows. Blast effects can cause windows to be sucked outward rather than blown inward.
- Select multiple assembly areas (if possible) to reduce the concentration of key personnel. Drill and exercise personnel to go to different assembly areas to avoid developing an evacuation and emergency pattern that can be used by terrorists to attack identifiable key personnel.
Building and Area Clearance
H-17. Establish procedures to ensure that threatened buildings and areas are cleared. Prevent personnel from reentering the building. Establish a cordon to prevent personnel from entering the danger area. Establish an initial control point (ICP) as the focal point for the PMO and for MP control.
H-18. Cordon suspicious objects to a distance of at least 100 meters, and cordon suspicious vehicles to a distance of at least 200 meters. Ensure that nobody enters the cordoned area. Establish an ICP on the cordon to control access; relinquish ICP responsibility to the PMO or local police upon their arrival. Maintain the cordon until the PMO, security police, security forces, or local police have completed their examination or stated that the cordon may stand down.
Searching for a Suspected IED
H-19. Searches are conducted in response to a telephonic threat or a report of an unidentified object on or near premises occupied by DOD personnel. The following types of searches may be used when searching for a suspected bomb or IED:
- An occupant search is used when the threat's credibility is low. Occupants search their own areas. The search is completed quickly because occupants know their area and are most likely to notice anything unusual.
- A team search is used when the threat's credibility is high. The search is very thorough and places the minimum number of personnel at risk. Evacuate the area completely, and ensure that it remains evacuated until the search is complete. Search teams will make a slow, thorough, systematic search of the area.
H-20. The following procedures should be followed if a search for explosive devices must be conducted before qualified EOD teams arrive:
- Make an audio check, listening for unusual sounds.
- Sweep the area visually up to the waist, then sweep up to the ceiling. Do not forget the tops of cabinets and cupboards.
- Perform a thorough and systematic search in and around containers and fixtures.
- Pass search results as quickly as possible to the leader responsible for controlling the search area. Do not use a radio; it may detonate the explosive.
H-21. Circumstances might arise in the case of a very short warning period. In other instances, a threat of a bomb against some facilities (if true) might necessitate the evacuation of a very large area. In these circumstances, searching for the presence of an explosive device to identify its location, appearance, and possible operating characteristics may be warranted.
H-22. Personnel who have not been trained in IED search and ID techniques should not search for explosive devices. Two types of errors are very common—the false ID of objects as IEDs and the incorrect ID of IEDs as benign objects. Depending on the devices used to arm and trigger an IED, the search process could actually result in an explosion.
Search Organization
H-23. The person controlling the search should have a method of tracking and recording the search results (such as a diagram of the area). Delegate areas of responsibility to the search-team leader, who should report to the person controlling the search when each area has been cleared. Pay particular attention to entrances, toilets, corridors, stairs, unlocked closets, storage spaces, rooms and areas not checked by usual occupants, external building areas, window ledges, ventilators, courtyards, and spaces shielded from normal view.
Discovery of a Suspected IED
H-24. When a suspicious object has been found, report its location and general description immediately to the nearest law-enforcement or supervisory person. Do not touch or move a suspicious object. Instead, perform the following steps:
- If an object appears in an area associated with a specific individual or a clearly identified area—
- Ask the individual/occupant to describe objects they have brought to work in the past few days.
- Ask for an accounting of objects.
- Ask for a verbal description/ID of objects.
- If an object's presence remains inexplicable—
- Evacuate buildings and surrounding areas, including the search team.
- Ensure that evacuated areas are at least 100 meters from the suspicious object.
- Establish a cordon and an ICP.
- Inform personnel at the ICP that an object has been found.
- Keep the person who located the object at the ICP until questioned.
- Avoid reentering the facility to identify an object that may or may not be an IED.
Reacting to an Exploded IED
H-25. The following procedures should be taken when an explosive/IED detonates at a DOD facility:
- For explosions without casualties—
- Maintain the cordon. Allow only authorized personnel into the explosion area.
- Fight any fires threatening undamaged buildings without risking personnel.
- Report the explosion to the PMO, security police, security forces, or local police if they are not on the scene.
- Report the explosion to the installation operations center even if an EOD team is on its way. Provide as much detail as possible, such as the time of the explosion, the number of explosions, the color of smoke, and the speed and spread of fire.
- Ensure that a clear passage for emergency vehicles (fire trucks, ambulances, and so forth) and corresponding personnel is maintained.
- Refer media inquiries to the PAO.
- Establish a separate information center to handle inquiries from concerned friends and relatives.
- For explosions with casualties—
- Select a small number of personnel to help search for casualties.
- Assign additional personnel the responsibility for maintaining the cordon to keep additional volunteers searching for casualties. Maintain the cordon until the EOD team verifies no further presence of bombs/IEDs at the site and the fire marshal determines that risk of additional injury to searchers from falling debris is acceptable.
- Prepare a casualty list for notification of next of kin; delay publication of the list until its accuracy is determined.
- Arrange for unaffected personnel to contact their next of kin immediately.
H-26. Civilian management officials and subordinate military commanders continue to have important personal roles to fulfill during a bomb/IED attack on DOD personnel, facilities, and assets. Perform the following procedures when reporting an attack:
- Pass available information to the operations center.
- Avoid delaying reports due to lack of information; report what is known. Do not take risks to obtain information.
- Include the following information in the report:
- Any warning received and if so, how it was received.
- The identity of the person who discovered the device.
- How the device was discovered (casual discovery or organized search).
- The location of the device (give as much detail as possible).
- The time of discovery.
- The estimated length of time the device has been in its location.
- A description of the device (give as much detail as possible).
- Safety measures taken.
- Suggested routes to the scene.
- Any other pertinent information.
H-27. Perform the following procedures when providing emergency assistance to authorities:
- Ensure that the PMO, security police, security forces, and other emergency-response units from local police, fire and rescue, and EOD teams are not impeded from reaching the ICP. Help maintain crowd control and emergency services' access to the site.
- Evacuate through the doors and windows of buildings.
- Assist the on-scene commander by obtaining a building diagram showing detailed plans of the public-service conduits (gas, electricity, central heating, and so forth), if possible. If unavailable, a sketch can be drawn by someone with detailed knowledge of the building.
- Locate, identify, and make witnesses available to investigative agency representatives when they arrive on the scene. Witnesses include the person who discovered the device, witnessed the explosion, or possesses detailed knowledge of the building or area.
H-28. Performing the above steps will provide substantial assistance to the crisis-management team and give other personnel constructive, supportive actions to take in resolving the crisis. Care must be exercised, however, that additional explosive devices are not concealed for detonation during the midst of rescue operations. These attacks add to the physical damage and emotional devastation of bomb/IED attacks.
H-29. The use of bombs and IEDs during terrorist attacks against DOD personnel, facilities, and assets is a common occurrence. The procedures outlined in this appendix are intended to help a DOD facility respond to an attack before an explosive device detonates. The procedures are also intended to help mitigate the consequences of an attack in case efforts to find an explosive device and render it inoperable are not successful. Incurring the costs to DOD facilities and installations of detecting an explosive device and terminating a terrorist incident before the device can detonate are almost always preferable rather than exercising plans and options to respond to a detonation. Several of the security measures discussed will help reduce the likelihood of a successful bomb/IED attack against DOD assets.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

