|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 4
STAFF RESPONSIBILITY FOR ELECTRONIC
COUNTER-COUNTERMEASURES
| CRITICAL TASKS: | 01-5701.07-0003 01-5771.07-0002 01-5879.07-9001 |
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about the staff responsibilities for electronic counter-countermeasures (ECCM) planning, operations, and analysis and electronic warfare (EW) vulnerabilities analysis.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Identify the staff responsibilities for electronic counter-countermeasures. |
| CONDITION: | Given the material in this lesson. |
| STANDARD: | To demonstrate competence, you must achieve a minimum of 70 percent on the subcourse examination. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 24-1, FM 24-33, FM 34-1, FM 34-10, FM 34-25, FM 34-60, and FM 34-80. |
INTRODUCTION
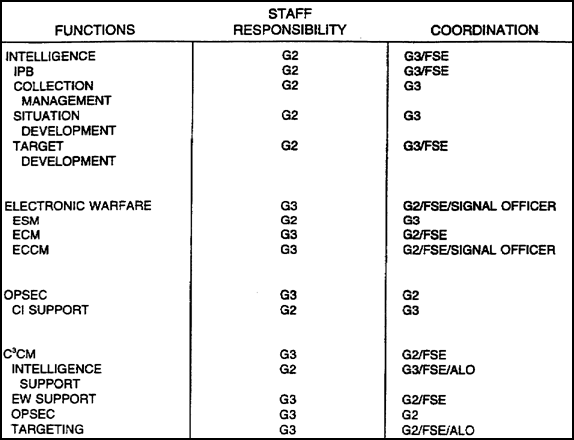
1. Staff Functions and Responsibilities. The G2/S2 and the G3/S3 have the main staff responsibility for coordinating intelligence and EW (IEW) efforts. They ensure IEW actions satisfy the commander's requirements. They plan and manage IEW operations on the battlefield in coordination with the signal officer. IEW staff responsibilities are listed in Figure 4-1.
Figure 4-1. IEW staff responsibilities.
a. The G2/S2 provides the G3/S3 with information concerning enemy forces for ECCM planning and operations. This information may include intelligence on enemy capabilities, intentions, or weaknesses. It is used to develop and implement effective ECCM operations. The G2/S2 is also responsible for monitoring the unit's signals security posture.
c. The signal officer, in coordination with the G3/S3, develops and plans the integration of ECCM into the overall operational plan. Specifically, the signal officer:
(1) Enforces proper use of ECCM on communications channels.
(2) Helps the G3/S3 develop and provide ECCM training.
(3) Prepares the ECCM and restricted frequency list appendices to the signal annex of operations plans (OPLAN) and operations orders (OPORD).
2. The Electronic Counter-Countermeasures Planning Process. The four ECCM planning categories are deployment, employment, replacement, and concealment.
a. The deployment category has two subcategories. They are geometry and system design.
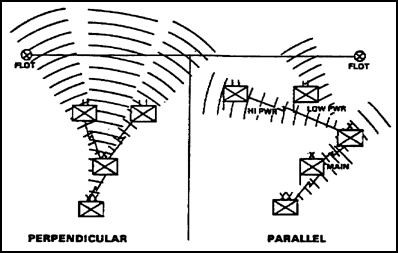
(1) We must analyze the terrain and determine methods to make the battlefield's geometry work in our favor. Figure 4-2 shows this concept. When deploying units and communications systems perpendicular to the forward line of own troops (FLOT), we open ourselves to enemy EW. Our transmissions are aimed in the enemy's direction, so he can pick them up. When possible, we must install our terrestrial line-of-sight communications parallel to the FLOT. This prevents enemy EW units from intercepting the primary strength of our transmissions. Dispersing the command posts so the natural terrain masks antennas and emitters helps reduce enemy EW efforts. Using tactical satellite systems helps to reduce enemy EW efforts.
Figure 4-2. Geometry of the battlefield.
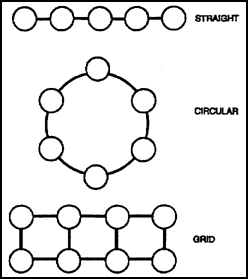
(2) In designing communications systems, we must establish alternate routes of communications. With enough routes, the loss of one or more will not seriously degrade the overall system. Figure 3 shows the three possible routing configurations. The straight-line method provides no alternate routes. The circular method allows one alternate route of communications. The grid method allows as many alternate routes as can be planned practically.
b. Enemy forces can extract vital information from friendly communications patterns. Thus, friendly forces should not have any sort of communications pattern. Traffic leveling (keeping transmission traffic fairly constant) should also be practiced. The frequency of messages being sent can tell enemy analysts what type of mission friendly forces are likely planning or doing. Introducing false messages on a random basis can prevent an enemy from detecting operations. This is especially true during periods when actual message traffic decreases. Properly using and enforcing signal operation instructions (SOI) can help eliminate communications patterns. Whatever method is used needs to be carefully planned and fully integrated into the unit's OPLANs and OPORDs. Consider the type of equipment used and its location, power, and operating methods when planning ECCM. To make communications more secure, use:
Figure 4-3. Deployment configurations.
(1) Low power until you must use high power.
(2) Frequency hopping to deny interception from enemy forces.
(3) Null steering and adaptive antenna techniques to mask radiation patterns.
(4) Spread spectrum techniques to suppress interference and provide multiple access for other users.
c. The replacement category involves establishing alternate communications routes. These must be planned and exercised before engaging an enemy. This can stop them from setting up a database on primary friendly communications. It can also help to maintain the primary communication means available to the tactical commander. Replacement actions must be carefully planned, coordinated, and integrated into the units OPLAN or OPORD.
d. Communications equipment and personnel should be concealed as much as possible. Terrain features and man-made obstacles should be used to conceal equipment, without degrading communications. Concealment provisions must be included in OPLANs and OPORDs.
3. Electronic Warfare Vulnerabilities Analysis. The signal systems analysis and EW vulnerability process are part of the overall counter-signals intelligence (C-SIGINT) process. This four-phase process provides the commander with knowledge of the enemy capabilities to assess them against his OPLANs. The phases are threat assessment, vulnerability assessment, countermeasures options development, and countermeasures evaluation.
a. Threat assessment is the key in planning C-SIGINT operations. Enemy technical and operational capabilities and intentions are examined to determine their impact on friendly C3 equipment.
b. The vulnerability assessment is conducted to determine where enemy forces can inflict the most damage. The identified weaknesses are ranked according to their potential impact on friendly operations.
c. During countermeasures options development, specific options are identified for controlling, eliminating, or exploiting the weaknesses identified during vulnerability assessment. Countermeasures are needed to effectively counter enemy exploitation of friendly C3 systems.
d. The effectiveness of the applied countermeasures is evaluated during countermeasures evaluation. This provides the commander the information he needs to decide if they should be used in other operations.
4. Summary.
a. Staff Functions and Responsibilities.
(1) The G2/S2 and the G3/S3 have the main staff responsibility for coordinating intelligence and electronic warfare (IEW) efforts.
(2) The G2/S2 provides the G3/S3 with information concerning enemy forces for ECCM planning and operations. He is also responsible for monitoring the unit's signals security posture.
(3) The G3/S3 has primary staff responsibility for ECCM. He is also responsible for including ECCM training in the unit training program.
(4) The signal officer develops and plans ECM integration into the overall operational plan. He does this in coordination with the G3/S3.
b. The ECCM planning process. The four ECCM planning categories are deployment, employment, replacement, and concealment.
(1) The deployment category has two subcategories (geometry and system design). We must analyze the terrain and determine methods to make the battlefield's geometry work in our favor. In designing communications systems, we need alternate communications routes.
(2) Friendly forces should not have any sort of communications pattern.
(3) Alternate communications routes must be planned and exercised before engaging an enemy.
(4) Communications equipment and personnel should be concealed as much as possible.
c. EW vulnerabilities analysis. The signal systems analysis and EW vulnerability process are part of the overall C-SIGINT process. This process has four phases. They are threat assessment, vulnerability assessment, countermeasures options development, and countermeasures evaluation.
GO TO: