|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 2
DEFENSIVE ELECTRONIC WARFARE
AND SIGNAL SECURITY TECHNIQUES
| CRITICAL TASKS: | 01-5701.07-0002 01-5701.07-0003 |
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about preventive and remedial electronic counter-countermeasure (ECCM) techniques. You will also learn about signal security (SIGSEC) techniques.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Describe preventive and remedial ECCM and SIGSEC techniques. |
| CONDITION: | Given the material this lesson. |
| STANDARD: | To demonstrate competence, a minimum of 70 percent on the subcourse examination must be achieved. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 24-18 and FM 24-33. |
INTRODUCTION
A commander's ability to conduct a battle successfully depends on his ability to see battlefield activity. A commander and his staff need timely and accurate information about friendly and enemy forces. That information is carried over communication systems maintained by signal personnel. Applying ECCM help protect those systems and increase the chance of winning.
1. Preventive Electronic Counter-Countermeasures. The two major areas of preventive ECCM are systems design and operational techniques. The enemy tries to gain information about an opposing force through electronic surveillance. He uses direction-finding receivers to pinpoint the locations of radar, radio transmitters, and other devices that produce electromagnetic signatures. We thwart enemy electronic warfare (EW) efforts by taking preventive measures.
a. Systems design includes ECCM-designed circuits. Most military radios have unique design features incorporated into their circuitry. A radio operator cannot normally control the effectiveness of design features. Examples include:
(1) A radio's low power setting. Lower output power reduces transmission range.
(2) Secure voice equipment, such as VINSON. This provides electronic signal encryption.
(3) Automatic power adjustments. These limit the radiated power to a level sufficient for effective communications. They reduce a radio's electronic signature. This feature is used in mobile subscriber equipment. Specifically, the radio access unit and the mobile subscriber radiotelephone terminal use it.
(4) Frequency hopping. This is very effective in reducing the effects of enemy jamming. It is also effective in denying the enemy information about your location. The Single-Channel Ground and Airborne Radio System (SINCGARS) radios employ frequency hopping.
(5) The spread spectrum technique. This suppresses interference by other frequency users (friendly and enemy). It provides multiple access (user sharing) and ends multipath interference (self jamming). This technique spreads signals across a very wide frequency band of the operating spectrum, causing the transmitted signal to be hard to distinguish from normal levels. The Enhanced Position Location Reporting System and the Joint Tactical Information Distribution System uses it.
b. Operational techniques provide methods for preventing an enemy from detecting friendly communications.
(a) Place an antenna to allow the terrain to mask it from the enemy. Masking an antenna from an enemy normally only reduces the signal's range in the enemy's direction.
(b) Relocate the antenna frequently. This makes the timely locating and targeting of stations more difficult. When you cannot move an antenna, remote it as far as possible from the radio.
(c) Use directional antennas when possible. Using bidirectional or unidirectional antennas is preferred over omni-directional antennas.
(d) Use low power settings when possible. Higher power levels increase a signals range, making it easier for an enemy to locate the transmitter.
(e) Select the correct antenna to support the operating nets power requirements.
(2) Radio operator procedures are the key to the success of preventive ECCM techniques. Using correct procedures reduces an enemy's ability to intercept, disrupt, or destroy friendly communications. The usable data an enemy intercepts is lessened by:
(a) Reducing operator-distinguishing characteristics and procedures. Enemy sign analysts can identify operators and stations that use unique or otherwise distinctive phrases or procedures. Call sign and frequency changes are useless when an operator compromises his station's identification by violating procedures after changes occur. Unique operator-distinguishing procedures often develop through operator design (unique method of opening a net). Others occur with a gradual development of a habitual approach or technique.
(c) Using authentication. A constant threat is the chance that an enemy may intrude into a radio net. The most effective means of countering deceptive entry is authentication. Authentication procedures are found in the supplemental instructions of the signal operation instructions (SOI).
(d) Encrypting essential elements of friendly information (EEFI). EEFI encompass the tactical situation, enemy contact, and operations orders. They include operations plans, equipment status reports, and personnel status reports. Message encryption is done using communications security (COMSEC) devices authorized for the classification level of the material being sent. A listing of the material types to be encrypted is in the SOI's supplement.
(3) Using null steering. This masks the radiation pattern to degrade the effects of jamming. It also provides an improved signal-to-noise ratio.
2. Radio Maintenance. ECCM depend on proper radio maintenance and alignment. A radio operator's skill and effectiveness affect the ability to protect transmissions and provide effective ECCM. These include initial procedures and reviewing equipment technical manuals for operating instructions. They also include setting up the radio set and reviewing cable connections and control settings. An operator should operate his radio according to his unit's radio requirements. These procedures should include:
a. Inspecting the set for completeness.
b. Inspecting the radio's condition. Look at the condition of knobs, dials, switches, and controls. Also inspect plugs, receptacles, and connectors.
c. Reviewing dial, switch, and control settings.
d. Following start-up and shutdown procedures contained in equipment manuals.
3. Single-Channel Techniques. Single-channel radio procedures that help defeat enemy EW efforts are specific operator procedures and actions based on the means of transmissions. The means normally used include radiotelegraph, radiotelephone, and radio teletypewriter (RATT). Good training, operator expertise, and operator adherence to signal discipline help to defeat enemy EW operations.
a. Radiotelegraph is the most reliable means available to send data and the easiest to detect. It uses normal communications procedures. It also uses procedure signs (prosigns) and operating signals to reduce the time needed to set up and maintain effective data transfer. Reducing transmission time is the most effective anti-EW support measure (anti-ESM) technique.
(1) When properly used, prosigns convey information, requests, orders, and instructions. To reduce the effectiveness of enemy EW, operators should not use unauthorized prosigns. This could allow enemy analysts to identify or isolate a station or operator.
(2) Operating signals are three-letter signals beginning with the letter Q or Z. RATT operators use them to expedite communications. Operating signals must be encrypted as part of an encrypted message. Examples are QSA, QSY, ZEV, and ZKJ.
b. Radiotelephone provides rapid, short-range, person-to-person communications among mobile and air units. However, it has little defense against enemy electronic countermeasures (ECM). It also has little defense against message exploitation unless a security device is used. There are several basic rules for radiotelephone that provide some security and signal protection.
(1) Use the following to help provide transmission security:
(a) No violation of radio silence.
(b) No needless chatter among operators.
(c) Transmit on directed nets only with permission.
(d) No excessive tuning or testing.
(e) No sending of an operator's personal name.
(f) Only authorized use of plain language.
(g) No association of classified and unclassified call signs.
(h) No association of address groups and call signs.
(i) Only authorized procedure words (prowords) used.
(2) Prowords are the voice equivalent of prosigns. Using prowords reduces the duration of transmissions.
(3) There are two correct methods for using call signs. The complete call sign is used when entering a net. It is also used when requested by the net control station (NCS) or another station in the net. The abbreviated call sign is used once the net is entered. The NCS directs the use of abbreviated call signs on the net. An example of a complete call sign is Q3O47. The abbreviated call sign is O47. Abbreviated call signs allow operators to more quickly identify themselves and stations they are calling. This is a defensive EW technique.
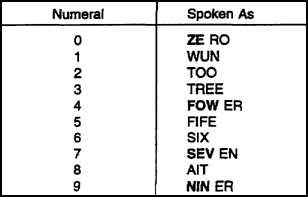
(4) Correctly using the phonetic alphabet is needed to reduce transmission time. This also ensures there is no confusion by the receiving operator. Table 2-1, contains the authorized phonetic alphabet. Table 2-2, contains the numerical pronunciation guide.
c. RATT uses frequency shift keying (FSK). FSK uses direct action from a keyboard, perforated tape, or electronic memory storage. It can use clear (unencrypted) or encrypted traffic. It is a dependable means of communication that integrates defensive EW techniques. Sending a long logistics report by single-channel radio invites enemy direction finding.
Table 2-1. Phonetic alphabet.
Table 2-2. Numerical pronunciation guide.
This is because the operator is on the radio too long. Sending it by RATT reduces transmission time, increases accuracy, and provides a hard copy for the receiver. Another EW advantage of RATT is the radiation signature it produces. Using a doublet antenna, operators can direct the radiation pattern in an azimuth away from an enemy.
4. Multichannel Techniques. Commander use line-of-sight (LOS) multichannel communication radio, troposcatter, and satellite relay.
a. Common myths about the security of multichannel communications can cause operators to violate basic COMSEC practices.
(1) Many think a multichannel radio is always secure. Many also think multichannel radio signals can only be intercepted from positions forward of the sending directional antenna, or within or on the immediate fringes of areas the signal beam spans, or from forward of the transmission path. However, these notions are no true.
(2) Multichannel radio signals can be intercepted by very accurate enemy sensors. However, multichannel does have some defensive EW characteristics. At a signal site, individual subscriber's circuits are assigned to a particular channel and electronically superimposed onto one carrier frequency and transmitted using one radio. In addition, the LOS radiation pattern is narrow and directional, instead of omni-directional. Also, each channel is secured, using a crypto-secure device.
b. Too many operators use the nonsecure orderwire to discuss classified matters. Examples are movement time, locations, and other operations-related information. Use the orderwire only for systems and circuit alignment. Also set up a separate engineering channel for operators.
c. Operating with misconceptions causes preventive ECCM techniques to have limited value. An enemy's successful penetration of multichannel nets allows him to focus his attention on carefully guarded information. Do not be the one who leaks information.
1. Remedial Electronic Counter-Countermeasures. These are actions taken in response to enemy jamming. Remedial ECCM techniques reduce the effectiveness of enemy jamming efforts (Figure 2-1). These techniques apply to jamming and unidentified or unintentional interference that disrupts friendly communications. Remedial ECCM techniques do not apply to other actions that might disrupt or destroy friendly communications.
a. Jamming may be either obvious to the operator or extremely subtle and difficult to detect. An enemy may use modulated or unmodulated signals. He may use spot, barrage, or sweep jamming. Spot jamming directs the jammer signal against a single frequency. Barrage jamming directs the jamming signal against a frequency band, disrupting many frequencies. Sweep jamming directs the jamming signal up and down a frequency band; it does not lock onto a specific frequency or group of frequencies.
Figure 2-1. Remedial ECCM techniques.
(1) Obvious jamming is normally easy to detect. Modulated signals are commonly encountered. They are identified quite readily by the signal's actual modulation. Examples of obvious jamming include:
(a) Random noise. This is synthetic radio noise that is random in amplitude and frequency. It is similar to normal background noise and used to degrade all types of signals.
(b) Stepped tones (bagpipes). These are sent at increasing and decreasing pitch. They resemble the sound of bagpipes and are normally used against single-channel AM or FM voice.
(c) Spark. This is an easily produced signal, which is very effective in disrupting all types of signals. Its sound resembles short duration, high intensity signals repeated at a rapid rate.
(d) Gulls. These are generated by a quick rise and then a slow fall of a variable radio signal, which is similar to a sea gull's call. They produce a nuisance effect and are usually effective against voice transmissions.
(e) Random pulse. This involves pulses of varying amplitude, duration, and rate. It is used to disrupt RATT, radar, and all types of data transmissions.
(f) Wobbler. This is a single frequency modulated by a slowly varying tone resembling a howling sound. It is a nuisance to voice radio communications.
(g) Preamble jamming. This is the broadcasting of synchronization tones over the operating frequency of a radio net that uses voice security devices. It often causes radios to be locked in the RECEIVE mode.
(h) Recorded sounds. These can be any audible sound of a varying nature. Examples are music, screams, applause, whistles, machinery noise, and laughter. They are used to distract voice radio operators and disrupt communications.
(2) Subtle jamming is not obvious to the radio operator because no sound is heard. The receivers are blocked and unable to receive an incoming signal, even though everything seems normal. Subtle jamming affects the squelch mode of FM radios. It places a tone on the receiver squelch circuit that blocks out weaker signals on the frequency. The operator believes the radio is functioning properly, but no signal is present on the assigned operating frequency.
(3) Unintentional jamming may be a big problem to communicators. Atmospheric conditions, malfunctions of the radio, and other radios (enemy or friendly) cause it. Other sources include electric, electronic and electromagnetic devices.
b. Once you realize an enemy is conducting jamming operations, you should report the jamming. You should then:
(1) Continue to operate.
(2) Improve the signal-to-jamming ratio.
(3) Adjust the receiver. This includes adjusting the beat frequency oscillator, adjusting the bandwidth, adjusting the gain or volume control, and fine tuning the frequency.
(4) Increase your transmitter's power output.
(5) Adjust, change, or move the antenna.
(6) Set up a retransmission station.
(7) Change the frequency.
(8) Use a different satellite.
(9) Use an alternate communications means.
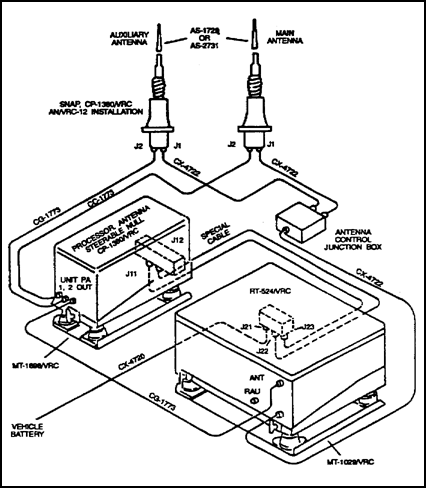
2. Transmission Protection. This requires the preoperational selection of antenna placement, transmitter power selection, and frequency usage be in concert with preventive ECCM principles. Additional transmission protection can be provided for single-channel radios. These include the AN/VRC-12 family of radios and the SINCGARS. Using steerable null antenna processor (SNAP-1) allows efficient jam-free reception. This occurs even when the operator does not know the location of the jamming or communications transmitter. An example is the OL-275/VRC used with the AN/VRC-12 and SINCGARS radios.
a. The OL-275/VRC SNAP-1 consists of a CP-1380/VRC steerable null antenna processor and a J-3792/VRC interconnecting box. It also includes a CX-13179/U special purpose electrical cable assembly (Figure 2-2).
Figure 2-2. OL-275( )/VRC steerable null processing group.
b. The OL-275/VRC (Figure 2-3) uses the equipment listed below.
(1) Two AS-1729 or two AS-2731 antennas.
(2) Two antenna cables CG-1773.
(3) Two control cables CX-4722.
(4) Mount MT-1898.
(5) COMSEC equipment TSEC/KY-8, TSEC/KY-38, or TSEC/KY-58.
(6) Radio set AN/GRC-160, radio set AN/GRC-164, and AN/VRC-12 radios.
Figure 2-3. OL-275( )/VRC installation.
c. The SNAP-1 combines signals received from two separate antennas to create a radio reception pattern containing a null. The SNAP-1 effectively becomes the antenna control system and must interface and operate with the radio. The SNAP-1 also:
(1) Automatically blocks an unwanted signal from the radio receiver. It does this without interfering with the desired signal coming from a different direction.
(2) Operates on-the-move or stationary, using current vehicular mounted radios.
(3) Can automatically block signals, even when the operator does not know the jammer's location or when the jammer is moving.
(4) Permits normal cipher and plain text voice and data communications over associated COMSEC and radio.
(5) Allows passing of the desired signal. This occurs even when the friendly transmitter is not equipped with SNAP-1.
(6) Uses standard Army VHF-FM antennas.
PART C - SIGNAL SECURITY MEASURES
1. Signal Security. A close relationship exists between ECCM and SIGSEC. When an enemy does not have access to or knowledge of EEFI, his effectiveness is reduced. SIGSEC's major function is to deny an enemy the ability to exploit friendly electromagnetic spectrum use. Its techniques include emission security and control, transmission security, cryptographic security, and physical security.
2. Emission Security and Control. This involves preventing an enemy from targeting friendly communications. If enemy EW units do not know a friendly unit is present, they cannot target it. Denying an enemy the ability to detect friendly units is possible when friendly radio operators—
a. Turn on emitters only to meet minimum requirements.
b. Use the minimum amount of power needed to pass information.
c. Mask antenna locations.
d. Use directional antennas.
3. Transmission Security. The type of information sent and how it is sent affect an enemy's ability to exploit friendly communications. Reducing transmissions is the key to transmission security. Keep transmission duration to 15 seconds when possible. Enemy analyst can exploit unneeded chatter and discussions that mention locations, equipment names, communications problems, and unit morale.
4. Cryptographic Security. This deals with codes, keylists, and COMSEC devices.
a. Using a security device denies enemy linguists the ability to exploit message texts. However, enemy EW units can still locate the transmitter. They can associate the location and net structure to the type unit, mission, and intentions.
b. When an enemy cannot gain information from a radio station, he may try to jam or destroy it.
c. Codes and keylists should always be those included in the SOI. Homemade codes offer no challenge to an experienced cryptoanalyst. However, they do offer an excellent source of information. They also provide operators with a false sense of security.
d. Chattering causes communications compromise. By talking around a subject and using unauthorized nicknames, enemy analysts receive excellent opportunities to gain EEFI.
5. Physical Security. Common sense measures and adherence to unit operational policies are the keys to good physical security practices. These include protection of SOI materials and keylists.
1. Preventive Measures.
a. The two major areas of preventive ECCM are systems design and operational techniques.
(1) Most military radios have unique design features incorporated into their circuitry.
(a) Null steering masks the radiation pattern to degrade the effects of jamming.
(b) The spread spectrum technique suppresses interference by other frequency users (friendly and enemy). It provides multiple access (user sharing) and ends multipath interference (self jamming).
(2) Operation techniques provide methods for preventing an enemy from detecting friendly communications.
(a) Site selection, radiated power, and antenna selection are the most important considerations in radio system installation.
(b) Radio operator procedures are the key to the success of preventive ECCM techniques.
(c) Frequency hopping is very effective in:
- Reducing the effects of enemy jamming.
- Denying the enemy information about your location.
b. ECCM depend in part on proper radio maintenance and alignment. A radio operator's skill and expertise affect the ability to protect transmissions and provide effective ECCM.
c. Single-channel radio procedures that help defeat enemy EW efforts are specific operator procedures and actions based on the means of transmissions.
d. Radiotelegraph is the most reliable means for sending information. It is also the easiest to detect. It has little defense against enemy ECM. It also has little defense against message exploitation unless a security device is used.
e. Commanders can use LOS multichannel communications radio, troposcatter, and satellite relay.
(1) Common myths about the security of multichannel communications cause operators to violate basic COMSEC practices. Multichannel radio signals can be intercepted by enemy sensors.
(2) Do not use the nonsecure orderwire to discuss classified matters. Use it only for systems and circuit alignment. Designate a separate engineering channel for operators.
2. Remedial Measures.
a. Remedial ECCM are taken in response to enemy jamming. Remedial ECCM techniques reduce the effectiveness of enemy jamming efforts.
b. Transmission protection requires the preoperational selection of antenna placement, transmitter power selection, and frequency usage be in concert with preventive ECCM principles. Using steerable null antenna processors (SNAP-1) allows efficient jam-free reception. This occurs even when the operator does not know the location of the jamming or communications transmitter.
3. Signal Security Measures. ECCM and SIGSEC are closely related. SIGSEC's major function is to deny an enemy the ability to exploit friendly electromagnetic spectrum use. SIGSEC techniques include emission security and control, transmission security, cryptographic security, and physical security.
a. Emission security and control involves preventing an enemy from targeting friendly communications.
b. The type of information sent and how it is sent affect an enemy's ability to exploit friendly communications. The key is to minimize transmissions.
c. Cryptographic security deals with codes, keylists, and COMSEC devices.
d. Common sense measures and adherence to unit operational policies are the keys to good physical security practices.
GO TO: