|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 1
OVERVIEW OF ELECTRONIC WARFARE
CRITICAL TASK: 01-5701.07-0002
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about the components of electronic warfare (EW).
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Describe the EW components. |
| CONDITION: | Given the material in this lesson. |
| STANDARD: | To demonstrate competence, a minimum of 70 percent on the subcourse examination must be achieved. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 24-18 and FM 24-33. |
INTRODUCTION
EW is a unique kind of combat. It occurs in the battlefield's electromagnetic dimension. EW prevents or reduces the effective use of enemy electronic equipment. It also ensures the continued use of friendly equipment and systems. To be an effective signal leader, you must know and practice EW in the execution of your professional duties.
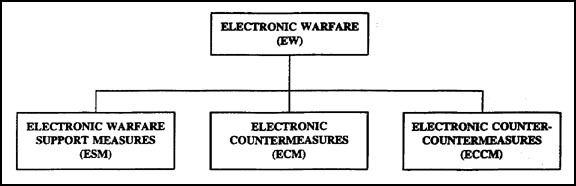
1. Electronic Warfare Components. EW is a major force multiplier when integrated and employed with fire and maneuver. Used properly, it exploits enemy weaknesses, protects friendly forces' freedom of action, and reduce security and communication vulnerabilities. EW has three components (Figure 1-1). They are electronic countermeasures (ECM), electronic counter-countermeasures (ECCM), and EW support measures (ESM).
Figure 1-1. EW components.
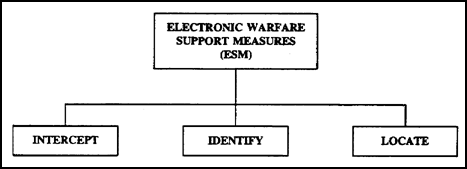
a. ESM provides the capability to intercept, identify, and locate enemy emitters (Figure 1-2). This crucial information is required for planning jamming, deception, ECCM, and targeting operations. It is integrated with the overall fire and maneuver plan.
Figure 1-2. ESM components.
(1) Interception operations provide information about enemy locations, activities, future operations, and electronic disruption capabilities that are used to plan ECM and ECCM operations. This capability provides combat information for the analysts to determine the pertinent intelligence the commander needs.
(2) Identification operations help to identify the size (personnel and equipment), type, echelon, and function of enemy units. This information has significance in fire and maneuver plans. By identifying enemy units, the commander can better prepare combat operations.
(3) Location operations help identify likely or possible enemy intentions. The data gathered can show if an enemy is in an offensive, defensive, or retrograde posture. The location and movement of enemy forces indicates what the enemy is doing or preparing to do. Gathered information is also used to plan the targeting of enemy positions.
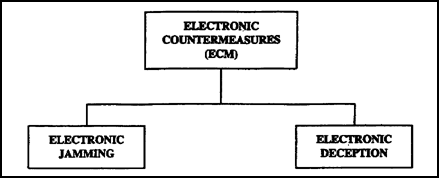
b. ECM are offensive actions taken to prevent or reduce an enemy's effective use of the electromagnetic spectrum. Figure 1-3 shows the components of ECM.
Figure 1-3. ECM components.
(1) Electronic jamming reduces or denies an enemy the effective use of his electronic equipment. It can help ESM efforts by forcing the enemy to send in the clear and for longer periods. ESM personnel can then gather vital information about the enemy's intentions, location, size, and other pertinent data. Denying the enemy use of the electromagnetic spectrum at key times causes chaos, disrupts his operations, and reduces his effectiveness.
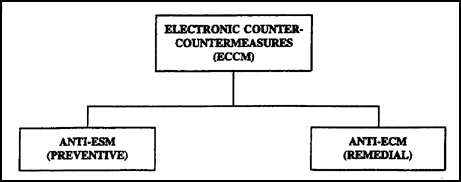
c. ECCM are defensive measures used to protect friendly command, control, and communications (C3) systems from enemy EW activities. ECCM allow friendly forces the continual use of the electronic spectrum. The components of ECCM are shown in Figure 1-4.
(1) Anti-ESM are actions taken to deny the enemy access to friendly electromagnetic transmissions. This is done by avoiding enemy EW operations. To deny an enemy access to friendly electronic assets, several actions may be taken.
Figure 1-4. ECCM components.
(a) An example is terrain masking, where a friendly radio station is placed so a hill is between it and the enemy.
(b) Another example is avoidance by using a directional antenna.
(2) Anti-ECM are used against jamming. They cannot be used against deception or ESM. This involves actions taken after learning the enemy is using EW against friendly forces. Effective anti-ECM methods are:
(a) Determining the cause of interference.
(b) Recognizing the difference between jamming and natural interference.
(c) Reporting incidents of ECM so the jammer can be located and destroyed.
(d) Using techniques to overcome ECM.
- Continue to operate normally to encourage jammer retargeting.
- Improve the signal-to-jamming ratio by adjusting the receiver, increasing transmitter power, adjusting the antenna, and setting up a retransmission capability.
(e) Changing frequencies.
(f) Shutting down communications and using alternate frequencies. This is done as a last resort.
2. Signal Security (SIGSEC). SIGSEC is closely related to ECCM. The main difference between the two is the type of information being protected from the enemy. ECCM protect friendly emitters from enemy EW. SIGSEC protects the information friendly forces send. Its major function is to keep an enemy from exploiting friendly electromagnetic spectrum use. SIGSEC techniques are covered in the next lesson.
3. Summary.
a. The EW components are ESM, ECM, and ECCM.
(1) ESM. Interception operations provide EW planners with intelligence about the enemy's location, activity, possible future operations, and electronic disruption capabilities. Identification operations help identify the size (personnel and equipment), type, echelon, and function of enemy units. Location operations help planners identify likely and possible enemy intentions.
(2) ECM. These offensive actions are taken to prevent or reduce effective enemy use of the electromagnetic spectrum. Electronic jamming reduces or denies the enemy effective use of his electronic equipment. The objective of electronic deception is to deceive the enemy through his electronic systems.
(3) ECCM. These defensive measures are used to protect friendly C3 systems from enemy EW activities.
(a) Anti-ESM are actions taken to deny the enemy access to friendly force's electromagnetic spectrum.
(b) Anti-ECM are used against jamming.
b. ECCM and SIGSEC are related. The major function of SIGSEC is to keep an enemy from exploiting friendly electromagnetic spectrum use.
GO TO: