|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 3
JAMMING, FREQUENCY CONTROLS, AND ELECTRONIC DECEPTION
Critical Tasks: 01-5701.07-0001, 01-5701.07-0002, 01-5701.07-0003
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about the concepts and methods of jamming and the frequency control methods applied to electronic warfare (EW). You will also learn about the methods of deception used to confuse or distract enemy forces.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Define and describe the methods of jamming, frequency control mechanisms, and the methods of electronic deception. |
| CONDITION: | You will have this lesson. |
| STANDARD: | To demonstrate competency, you must achieve a minimum of 70% on the subcourse examination. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 24-33, FM 34-1, FM 34-10, and TC 34-41. |
INTRODUCTION
Offensive EW is the means commanders use to attack enemy electronic systems. It combines the use of jamming and electronic deception. It provides combat information to elements able to physically attack enemy systems and equipment. Offensive EW is conducted in three mission areas (degrade, disrupt and deceive, and defend). Jamming disrupts and degrades enemy electronic systems. Deception misleads or deceives enemy analysis of the capabilities and intentions of friendly forces.
1. Jamming Concepts. Jamming is the deliberate radiation or reradiation of energy to prevent or degrade the reception of information by a receiver. The jamming function is tied directly to the information provided by the EW support measures (ESM) component of the EW program. The tactics for using jamming vary with the tactical situation and the commander's plan of action. Conceptually, the jamming transmitter is placed between the signal transmitter and the receiver to which the transmission is directed. However, the ability to place the jammer between the transmitter and the receiver is seldom possible. Thus, many jammers have enough power to compensate for the additional range needed to jam signals effectively.
a. Three methods of communications jamming are commonly used on the battlefield. Each is used to attack a different signal or signals.
(1) Spot jamming is directed against a single or specific frequency, while allowing adjacent frequencies to remain free of the effects of the jamming. It applies the full radiated power of the jamming transmitter against enemy signals, one frequency at a time.
(2) Barrage jamming targets multiple frequencies. It may be used over a large portion of the frequency spectrum or the entire amplitude modulation or frequency modulation band. Barrage jamming needs high power to operate. It cannot distinguish between enemy and friendly frequencies.
(3) Sweep jamming is used to block several preselected sequential frequencies. It moves from one frequency to another, remaining on each frequency for a predetermined period. It can affect both friendly and enemy frequencies.
b. Various types of signal modulation can be used during jamming. These modulation types are selected based on their effectiveness against the transmission being attacked. In some cases, the jammer's signal generator can produce only a limited number of signals. In other cases, the generator can produce a large number of signals or sounds. Some of the most commonly used modulation types are discussed below.
(1) The stepped tone signal is a series of varying tones normally sent in an ascending or descending order.
(2) The bagpipe signal is like the sounds produced by a bagpipe.
(3) The gulls signal is similar to the sounds made by sea gulls.
(4)The spark signal is like that made by a spark gap Morse transmission.
(5) Other popular and effective signals can be applied to the jammer's carrier. They include random Morse keying (on-off keying), random noise, static, and playback of previously recorded transmissions.
c. Reradiation jamming normally uses special equipment. Normally directed against non-communications emitters, there are some applications of reradiation against communications receivers. The most widely used method uses the delayed retransmission of a recorded transmission. To conduct this form of jamming, a very slight delay is used when rebroadcasting the recorded signal. The following are other forms of reradiation jamming:
(1) A repeater can intercept, alter, amplify, and retransmit signals.
(2) Transponders are systems that automatically send a predetermined signal in response to the reception of a given signal.
(3) Reflection jamming uses devices, such as corner reflectors and chaff, to confuse electronic systems by producing false signals or images. It is sometimes called mechanical jamming.
d. The are three major systems for executing jamming missions. They are ground-based systems, airborne platforms, and expendable jammers. Determining the delivery vehicle is based on several factors. These include:
(1) Target link distance. This is the distance between the enemy transmitter and receiver.
(2) Jammer-to-receiver distance. This is the distance from the jammer to the intended receiver.
(3)Terrain factors. The line-of-sight factor between the jammer and the target receiver is important. A hill or mountain can mask the jamming signal.
(4)Effective radiated power quotient. This is the computation of the effective radiated power of the jammer and the enemy transmitter. It is used to determine the jammer radiated power requirement needed to defeat the transmitter.
(5) Signal compatibility. This is the compatibility of the modulation, bandwidth, and enemy signal type.
(6) Environmental factors. The weather, terrain, and vegetation affect the considerations that apply to jammer selection.
2. Control Mechanisms. These are established to ensure the success of all jamming missions, the protection of friendly communications, and the direction of jamming against high-value targets (HVT).
a. Positive control mechanisms ensure that the mission may be stopped at any time.
(1) The positive control list is a publication of authorized frequencies that can be jammed.
(2) On-off control is a centralized method of controlling jamming. It provides for the immediate initiation or stopping of jamming missions.
b. Negative control mechanisms protect specific frequencies from being jammed, except as authorized on a jamming restriction list. This method of control is executed through the development of separate listings of frequencies that are under any of the three classifications of frequencies.
(1) Taboo frequencies are never to be jammed for any reason. However, they can be time-controlled, and the jamming restrictions may be removed during particular time periods.
(2) Protected frequencies are those frequencies used or designated for use by friendly forces for a planned or on-going operation. These frequencies are published in a protected frequency list.
(3) Guarded frequencies are listed as enemy-used frequencies exploited by friendly force ESM or signals intelligence (SIGINT). Guarded frequencies can only be jammed when the potential operational gain outweighs the value of the information they provide.
c. A combination of negative and positive controls can be used to keep jamming missions under control.
3. Electronic Deception. This is normally used to cause enemy analysts to misread the situation and provide their commander with misleading information and intelligence that appears to be accurate. The three types of electronic deception are manipulative electronic deception (MED), simulative electronic deception (SED), and imitative electronic deception (IED). The signal officer plans and executes both MED and SED. IED is primarily conducted by military intelligence (MI) personnel.
a. MED involves altering the electromagnetic profile of friendly forces.
(1) MED tries to influence or alter enemy EW and SIGINT estimates of the situation. It does this by changing the technical characteristics of specified friendly communications to create false impressions.
(2) MED can include false traffic levels, false peaks, routing, electronic cover, and controlled breaches of communications security. It can also use non-communications devices.
(3) The deployment of various types of radar to mislead analytic assessments of the location of airfields, air defense batteries, and field artillery units can aid in applying MED effectively.
(4) To be effective, MED must be developed by those with a complete knowledge of the operational concepts and procedures of friendly communications.
b. SED can counter an enemy's EW ability to accurately read the battlefield. It does this by misleading the enemy about friendly force composition, deployment, and capabilities.
(1) The indication of additional friendly forces on or approaching the battlefield is an example of SED. By matching the communications and non-communications emitters of a friendly unit and duplicating the type and volume of radio traffic normally found in that unit, an enemy can be misled into believing there are more friendly forces on the battlefield than actually exist.
(2) The introduction of new or different electronic systems can indicate to an enemy that new systems or type units are available.
(3) Another method of conducting SED is to create a false electronic signature which indicates that a friendly unit has moved. Such deception, coupled with suppressed communications at the unit's actual location, can alter an enemy's estimate of friendly intentions.
c. IED can be conducted against both communications and non-communications emitters.
(1) The function of IED may vary in the methods and techniques used. IED injects false and misleading information directly into an enemy's communications nets. Thus, the activity may vary in scope, based on the sensitivity and sophistication of the techniques used.
(2) The scope of IED may include nuisance intrusion, deceptive jamming, planned message intrusion, and cryptographic intrusion. Nuisance intrusion requires language ability, a compatible radio, and little technical support. However, deceptive jamming, planned message intrusion, and cryptographic intrusion need skilled operators to prevent the enemy from detecting the level of success that friendly EW and SIGINT are having in exploiting enemy communications.
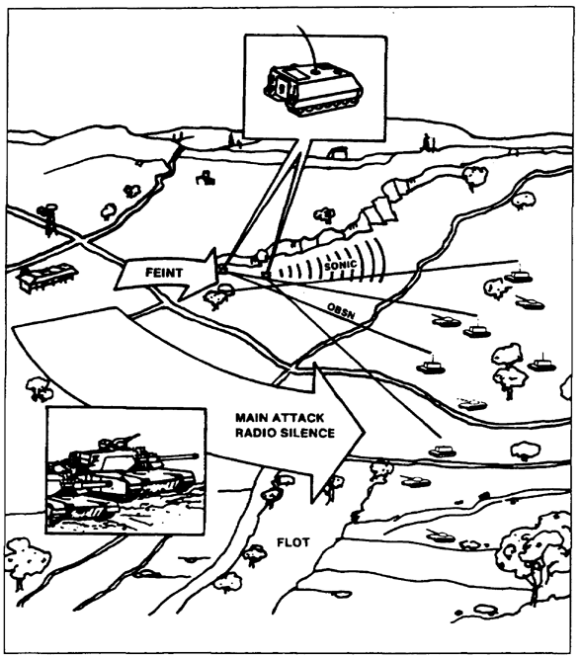
d. The use of electronic, physical, and sonic (noise) deception techniques is depicted in Figure 3-1. The main attacking force of tanks and armored personnel carriers (APC) uses radio silence and noise discipline. A small deception portrays a large frontal attack. The two APCs have a small physical signature. Loudspeakers and equipment broadcast recorded tank and APC noise. With that and the tree line to hide in, the two APCs indicate a larger force. Thus, the enemy is fed false data.
Figure 3-1. Deception scenario.
4. Summary. In this lesson, you learned about the concepts and methods of jamming, the frequency control methods applied to EW. You also learned about the methods of deception used to confuse or distract enemy forces.
a. Jamming is the deliberate radiation or reradiation of energy to prevent or degrade the reception of information by a receiver. Three methods of communication jamming are commonly used on the battlefield. Each is used to attack a different signal or signals.
(1) There are several methods of communications jamming. Spot jamming is directed against a single or specific frequency, while allowing adjacent frequencies to remain free of the effects of the jamming. Barrage jamming is targeted against multiple frequencies. Sweep jamming is used to block several preselected frequencies.
(2) Various types of signal modulation can be used during jamming. Some of the common modulation types are stepped tones, bagpipes, gulls, and spark.
(3) Reradiation jamming normally uses special equipment and is directed against non-communications emitters.
(4) The three major systems for jamming missions are ground-based systems, airborne platforms, and expendable jammers. Several factors determine the delivery vehicle. They include target link distance, jammer-to-receiver distance, terrain factors, effective radiated power quotient, signal compatibility, and environmental factors.
b. Control mechanisms are established to ensure the success of all jamming missions, the protection of friendly communications, and the direction of jamming against HVT. Positive control mechanisms ensure that the mission may be terminated at any time. Negative control mechanisms protect specific frequencies from being jammed, except as authorized on a jamming restriction list.
c. Electronic deception is normally used to cause the enemy analysts to misread the situation and provide his commander with information and intelligence which, while in appearance is accurate, is actually misleading. The three types of electronic deception are MED, SED, and IED. The signal officer plans and executes both MED and SED. IED is primarily an MI function.