|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 2
ELECTRONIC WARFARE OPERATIONS
Critical Tasks: 01-5701.07-0001, 01-5701.07-0002, 01-5701.07-0003
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about using electronic warfare (EW) on the battlefield.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Define and explain electronic warfare on the battlefield. |
| CONDITION: | You will have this lesson. |
| STANDARD: | To demonstrate competency, you must achieve a minimum of 70% on the subcourse examination. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 11-30, FM 24-1, FM 24-18, FM 34-1, FM 34-10, FM 34-23, FM 34-80, TC 34-1, and TC 34-41. |
INTRODUCTION
EW is used to exploit, disrupt, and deceive enemy command, control, and communications (C3), while protecting friendly use of communications and non-communications systems. It is a significant force multiplier when integrated and used with fire and maneuver. It is also a significant contributor to C3 countermeasures (C3CM). Offensive C3CM is the integrated use of jamming, physical destruction, and military deception to disrupt enemy C3. Defensive C3CM includes EW and operations security to protect friendly C3 and deny an enemy information of intelligence value.
1. Divisional Military Intelligence Battalion. The mission of the divisional military intelligence (MI) battalion is to provide dedicated intelligence and EW (IEW) support to the division. The battalion is organic to the division. It operates under the command and direction of the division commander and his staff. The battalion responds to missions assigned by the division Assistant Chief of Staff, G2 (Intelligence) and Assistant Chief of Staff, G3 (Operations and Plans).
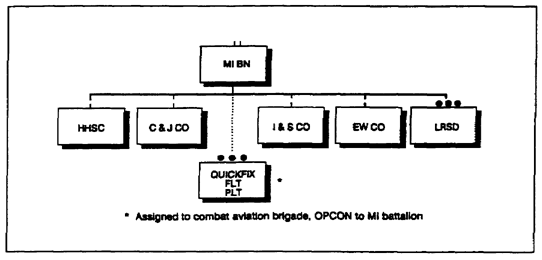
a. The MI battalion in a heavy division has four companies (Figure 2-1). It is authorized approximately 300 personnel at full tables of organization and equipment (TOE).
Figure 2-1. MI battalion organization (heavy division)
(1) The headquarters, headquarters and service company (HHSC) provides command and control (C2) for all elements, including those under the battalion's operational control. It manages battalion assets in support of IEW operations, and supplies technical control and analysis for EW operations. Personnel and equipment to support three IEW support elements are assigned to the HHSC-one for each maneuver brigade in a three-brigade division.
(2) The collection and jamming (C&J) company provides communications intelligence (COMINT) collection, low-level analysis, and communications jamming support for the division.
(3) The intelligence and surveillance (I&S) company provides ground surveillance for the division. It also provides enemy prisoner of war (EPW) interrogation and limited counterintelligence (CI) capabilities.
(4) The EW company provides EW support measures (ESM) to the division. It intercepts, locates, and identifies sources of radiated energy on the battlefield in support of the EW plan. It also conducts initial analysis and prepares reports to support the commander's priority intelligence requirements (PIR) and information requirements (IR).
(5) The long range surveillance detachment (LRSD) collects information by human intelligence (HUMINT) means within the division's area of operations and interest. For planning purposes, this area extends to a depth of 50 kilometers beyond the forward line of own troops.
(6) The QUICKFIX flight platoon provides aerial COMINT collection, direction finding, and jamming support to the division.
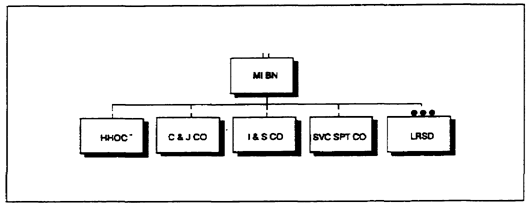
b. The MI battalion assigned to an airborne or air assault division has four companies (Figure 2-2). At full TOE, this battalion is authorized approximately 360 personnel.
Figure 2-2. MI battalion organization (airborne/air assault divisions).
(1) The headquarters, headquarters and operations company (HHOC) provides C2 for all battalion elements. The HHOC is the home of the QUICKFIX flight platoon.
(2) The C&J company performs communications and non-communications intercept and direction finding operations. It also performs communications jamming.
(3) The I&S company provides ground surveillance, interrogation, and CI support. In an airborne division, it also has remotely-monitored, battlefield sensor system assets. These provide additional ground surveillance capability.
(4) The service support company provides maintenance (vehicular and signal), food service, and signal support to the battalion.
(5) The LRSD collects information by HUMINT means within the division's area.
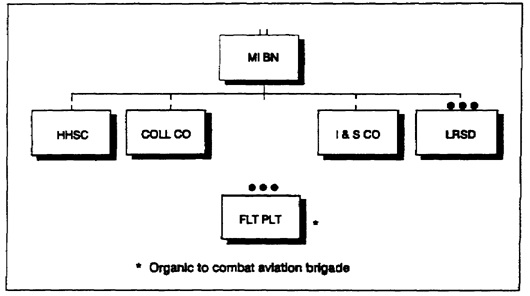
c. The MI battalion assigned to a light division is organized with the same philosophy as its parent division. It is easy to transport and relies on additional assets from higher echelons for support during combat operations. The battalion receives corps augmentation for ground-based jamming and electronic intelligence support. When the division is in a low intensity conflict environment, additional CI and EPW interrogation augmentation is provided. This battalion has three companies (Figure 2-3). It is authorized approximately 295 personnel at full TOE.
Figure 2-3. MI battalion organization (light division).
(1) The HHSC provides C2 for all elements within the battalion and supporting units. It provides administrative, logistics, maintenance, and communications support for the battalion.
(2) The collection (COLL) company provides COMINT collection, line-of-bearing (LOB) information, and analysis support for the division.
(3) The I&S company provides counterintelligence, EPW interrogation, and ground surveillance support for the division.
(4) The LRSD collects information by HUMINT means within the division's area of operations and interest.
(5) The flight platoon provides aerial support to complement ground-based EW systems.
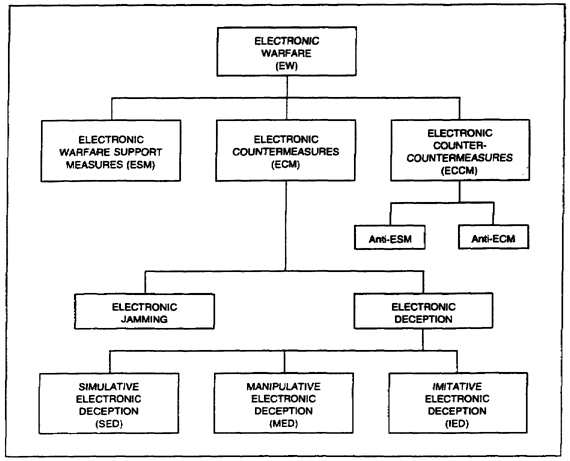
2. Electronic Warfare Battlefield Operations. When integrated into the overall operational scheme of maneuver, EW is a formidable force multiplier. It exploits enemy electronic capabilities and protects friendly use of the electromagnetic spectrum. Figure 2-4 depicts the various functions of EW. ESM acquires information about the enemy. Electronic countermeasures (ECM), the offensive component, prevent or reduce an enemy's use of the electromagnetic spectrum. Electronic counter-countermeasures (ECCM), the defensive component, are actions taken to retain friendly use of the spectrum.
Figure 2-4. EW functions.
a. The interception, location, and identification of enemy electronic equipment can provide the tactical commander with vital intelligence about enemy intentions, capabilities, and disposition. The type and quantity of equipment being used provides important data for EW technicians to analyze and determine what types of units are opposing friendly forces. This information, combined with the equipment's location and frequency of use, provides information on possible enemy intentions.
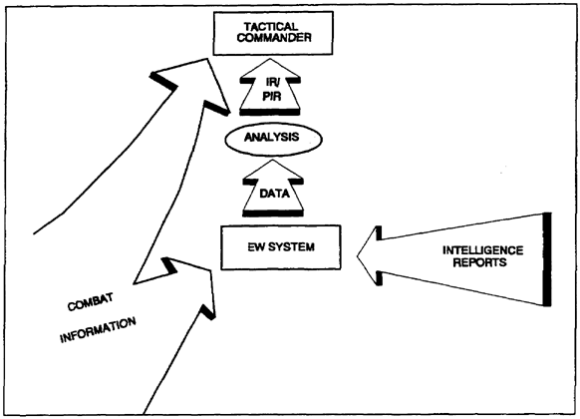
b. EW provides the tactical commander with accurate information that is used to make estimates, reach decisions, prepare orders, and execute operational plans. This information must reach the commander in enough time to be used in the overall tactical scenario. The commander receives two types of data (intelligence reports and combat information). This is shown in Figure 2-5.
Figure 2-5. EW provided data
(1) Intelligence is data which results after analysis has been conducted on gathered information (combat and other intelligence reports). It has immediate or potentially significant importance to military planning and operations. It is given to the tactical commander in the form of responses to his PIR and information requirement (IR).
(2) Combat information is information given directly to the tactical commander before it is analyzed or evaluated. It is also given to the EW team for analysis. This highly perishable information can have immediate impact on current combat plans and operations. Its importance is such that it cannot be delayed for the normal intelligence analysis. Combat information which is not of critical importance is integrated with other intelligence reports received by the EW system. It is then analyzed for responses to the commander's PIR and IR.
3. Offensive Electronic Warfare Operations.
a. ESM allows the commander to know the type of enemy force he is facing. It is the EW component that produces combat information and intelligence reports. This supplies the ESM team with the crucial information needed to answer the commander's PIR and IR. It also allows the EW staff to plan ECM, ECCM, and targeting operations.
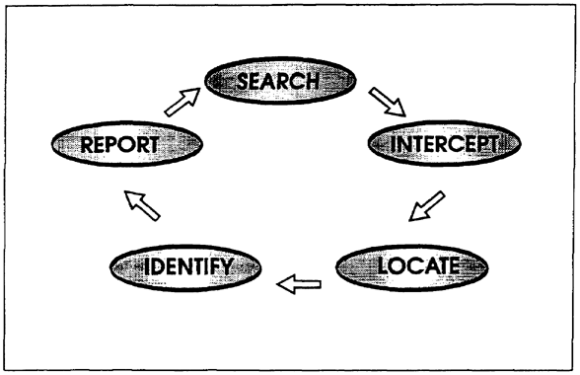
(1) The five major ESM components are search, intercept, locate, identify, and report. These five components are part of a continuous process (Figure 2-6). They are carried out using special EW equipment.
Figure 2-6. ESM components.
(2) In the search component, the ESM team uses special EW equipment to search for enemy electronic transmissions. The intercept component occurs when the ESM team actually records the transmissions for further analysis. Acquiring LOB on the transmissions helps to locate the transmitter. It also helps to identify where the equipment is located. Identifying the emitter occurs when all information from the previous components are combined and analyzed. This intelligence is given to the commander and his staff in various EW reports.
b. ECM are actions taken to prevent or reduce effective use of the electromagnetic spectrum by enemy forces. ECM operations can degrade an enemy's combat effectiveness by degrading his electromagnetic operations. ECM is the staff responsibility of the G3. It includes electronic jamming and deception.
(1) Electronic jamming reduces or denies an enemy the effective use of his electronic equipment. It also permits exploitation by friendly ESM teams. It allows them to gather vital information about enemy intentions, location, size, and other data which could help the commander and his staff in preparing operational plans. Denying an enemy the use of the electromagnetic spectrum causes chaos and disrupts his effective combat operations. This greatly reduces his combat effectiveness.
(2) Electronic deception causes an enemy to misinterpret what his electronic systems receive. Normally, it is conducted as part of a larger deception operation. It involves actions associated with friendly electromagnetic radiations (manipulative electronic deception (MED)) and simulative electronic deception (SED)), and with those of the enemy (imitative electronic deception (IED)). Electronic jamming and deception are discussed in greater detail in the next lesson of this module.
4. The Electromagnetic Environment.
a. That battles are won depends in large part to the degree of C2 the commander exercises. Radio is the primary means for carrying out C2. The battlefield's electromagnetic dimension is where a unique form of warfare occurs. Friendly units strive to exploit the use of the electromagnetic spectrum, while denying its use to an enemy.
b. A battlefield is an extremely violent and exceedingly dense signal environment, with many devices producing signals. A single U.S. division engaged in combat will have over 3,000 communications emitters working. In addition, thousands of enemy emitters and non-communications emitters (radars, jammers, etc.) are propagating signals. This vast amount of electronic equipment causes a saturated frequency spectrum.
c. Communications systems are threatened by physical damage and enemy jamming. Friendly emitters may be targeted by enemy intercept or direction finding. Once an enemy gets an electronic fix, he can quickly target friendly forces with artillery and air assets. A battlefield saturated with signals is not very user-friendly. There is much interference and many unpredictable outcomes due to this messy environment, this electromagnetic "soup." Our forces must be able to operate with minimum communications. They must plan to continue operations without radio. Alternate means (messenger, visual signals, etc.) must be practiced to enhance combat effectiveness. Another practice is to reduce the dependence on radio. Too many voice messages relate to aspects of operations that should be addressed during the planning stage. Proper planning and coordination result in fewer calls being made to inquire about what is to be done. To effectively counter EW in combat, we must make it a continuing part of our combat preparations.
5. Summary. In this lesson, you learned about using EW on the battlefield.
a. EW is used to exploit, disrupt, and deceive enemy C3, while protecting friendly use of communications and non-communications systems. It is a major force multiplier when integrated and used with fire and maneuver. It contributes much to C3CM. To be effective, it must be fully integrated with the commander's operational plans.
b. The divisional MI battalion provides dedicated IEW support to its division.
c. The five major ESM components are search, intercept, locate, identify, and report.
d. ECM are offensive actions that include both electronic jamming and deception.
(1) Electronic jamming reduces or denies enemy forces the effective use of its electronic equipment.
(2) Electronic deception is used to cause an enemy to misinterpret what is received by his electronic systems.
e. ECCM are defensive actions taken to retain friendly use of the spectrum.