|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 1
INTRODUCTION TO ELECTRONIC WARFARE
Critical Tasks: 01-5701.07-0001, 01-5701.07-0002, 01-5701.07-0003
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn about the history of electronic warfare (EW), some EW accomplishments, and the components of EW.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Define and explain EW. |
| CONDITION: | You will have this lesson. |
| STANDARD: | To demonstrate competency, you must achieve a minimum of 70% on the subcourse examination. |
| REFERENCES: | The material in this lesson was derived from the following publications: FM 34-1, FM 34-10, and FM 34-80. |
INTRODUCTION
In the early years of the 20th century, the navies of the world expanded their use of radio for command and control. They also began to search the spectrum to identify and locate other nations' ships. As the threat of a major war in Europe grew, so grew the efforts of ground forces to include radio in their modernization efforts. Radio became a means of communicating between ships and shore and between military units. By the end of this century's first decade, most major nations' fleets had continuous wave radios. Those radios allowed ships at sea to communicate with other ships and with shore stations. At about the same time, major military headquarters were provided radios to improve communications and provide a quick method of interfacing with national military commands. EW closely followed the development of radio.
1. Evolution of Electronic Warfare. Early EW was primarily a tool used to identify ships and military units. As nations improved their intelligence gathering systems, they also introduced methods to thwart their adversaries' means of collecting intelligence. Codes and ciphers were developed, and the periodic changing of call signs and frequencies was made a part of everyday communications. The disrupting of communications (jamming) and the creation of deceptive communications practices became a very sophisticated and artful practice.
a. World War I. During this period, EW was mostly limited to casual monitoring of radio and some attempts at wiretapping. Some radio direction finding was conducted; however, these early attempts were very crude, and the results were unreliable. The expanded use of codes and ciphers for diplomatic cables continued with the development of military radio use during and after World War I.
b. World War II. The period between the two world wars saw dramatic breakthroughs in the development of radio. The use of radio in the military became commonplace. Radios were found as far down as battalion level. Signal operations became more disciplined. Codes and ciphers provided transmission security, and call signs and frequencies were regularly changed. By the start of World War II, most nations had positions for EW functions within their staff elements. Jamming of radios became a component of EW, along with collecting, locating, and analysis. Some major breakthroughs in code breaking took place. Several countries, including Great Britain, Poland, the USSR, and the USA, were able to read the radio messages of other nations.
(1) By the end of World War II, radios could be found at company level. Transmission security continued to be a major item of concern, as the radio passed from the exclusive charge of the trained signal soldier to the less security-conscious front-line soldier.
(2) The use of deception became an integral part of planning. An interesting example of deception took place in England during the time of the Allied invasion of France. It was well known to the Allies that the German high command felt the main invasion would be at Calais. The Germans believed the landings in Normandy were only a ruse to draw its forces away from Calais. To keep the Germans thinking along those lines, the Allies set up a deception plan that included the communications structure of an entire army. The ruse worked so well that a large part of the German tank force remained in the Calais area, rather than being used against the Allies at Normandy. Deception operations, which are highly believable to an enemy, are likely to be more successful than less believable deceptions.
(3) Another example of deception was the Japanese attack on Pearl Harbor. The Japanese Fleet sailed across the Pacific in complete radio silence. At the same time, dummy radio nets in the home islands simulated the fleet's normal radio activity. This use of simulative electronic deception (SED) denied the U.S. the true location, intentions, and activities of the Japanese fleet.
(4) Code breaking was another major effort in this period. A successful example was Operation Magic (1937-1940), conducted by the U.S. against the diplomatic codes of Japan. This effort gave the U.S. information about Japanese military and national intentions. Later EW efforts against Japan led to the destruction of the Japanese carrier fleet at Midway. In Europe, the British success in breaking the German code system ULTRA allowed the Allies to read German high command and naval traffic. The success in defeating the submarine threat to Allied convoys crossing the Atlantic can be attributed, in part, to the breaking of the German codes.
(5) The development of radio detection and ranging (radar) affected the outcome of World War II. Radar was used for both the early detection and location of aircraft and naval surface forces. The development of systems and techniques to locate and identify radar sets grew into separate activities. They would eventually be given the names electronic intelligence (ELINT) and electronic security (ELSEC). Many years later, ELINT and ELSEC would play a major roll in the Persian Gulf War of 1991.
c. Korean War. During the Korean War, EW was used by both United Nations (UN) and North Korean forces. The Soviets supplied the North Koreans with ground-based radars that were used against American bombers. U.S. forces responded by jamming enemy radars with tin-foil strips, called chaff.
(1) Both sides intercepted and analyzed radio signals. UN forces jammed enemy communications nets. Enemy jamming capabilities were not as effective; however, they could locate UN positions through the technique of direction finding (DF).
(2) The Chinese used radio silence during their move into Korea in 1950. Thus, the UN forces Were denied data on the location and intentions of the Chinese.
d. Vietnam. Both sides used EW in Vietnam. ELSEC and deception became an integral part of U.S. battle planning. For the first time, EW units directly supported units at the brigade and separate regiment level.
(1) In North Vietnam, Chinese and Vietnamese air defense units caused the U.S. to use EW to protect its aircraft from radar-controlled; surface-to-air missile.
(2) In South Vietnam, both the U.S. Army and the Army of the Republic of Vietnam (ARVN) used EW support measures (ESM) to aid their ground forces. Captured enemy documents showed that the Viet Cong and the North Vietnamese Army were both very involved in collecting U.S. and ARVN communications.
(3) Vietnam also saw the first large-scale use of airborne platforms to collect enemy communications and locate enemy units. However, jamming was not a major factor in this war.
e. Operation Desert Shield/Desert Storm. The Persian Gulf War provides an example of battlefield deception. The undetected positioning of the coalition forces showed how an effective use of radio silence and deception can influence a battle's outcome. Modern EW technology was also used to seek out major communications facilities, determine their use, and provide targeting information for their destruction.
(1) ELINT was heavily used to locate and destroy the Iraqi air defense capability. U.S. Air Force systems suppressed radar sites. The coalition forces used jamming and lethal attacks with high-speed, anti-radiation missiles.
(2) The coalition forces used ESM to support the planning of deception operations. The U.S. Marine Corps portrayed an amphibious assault on Kuwait from the sea. EW was used to support rehearsed landings and to monitor the Iraqi forces' reaction (determining unit locations and monitoring radio traffic) to the deception.
f. The future.
(1) There is little to indicate that the use of EW will diminish in the post-Cold War era. In fact, the size of the world's armies grows smaller, the need for EW as a force multiplier will grow. The signal officer's role will become more difficult, as nations probe for weak spots in their adversaries' communications.
(2) Directed energy weapons will be used in future battles. Radio frequency and microwave energy weapons are the most likely to be developed to disrupt or destroy communications. They could potentially attack target emitters as super jammers to destroy electronic components. Non-nuclear electromagnetic pulse generators or transmitters are potential EW weapons. If constructed, these devices would generate an electromagnetic-pulse effect similar to that of a high-altitude nuclear detonation.
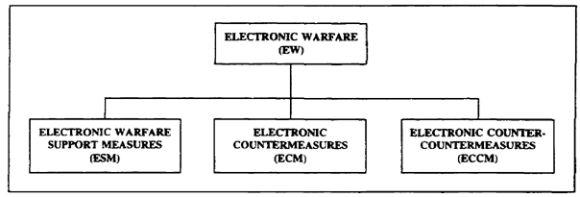
2. Electronic Warfare Components. EW is a command responsibility. It is a significant force multiplier when integrated and used with fire and maneuver. When used properly, it exploits enemy weaknesses, protects friendly freedom of action, and reduces security and communication vulnerabilities. EW significantly contributes to command, control, and communications countermeasures (C3CM). Figure 1-1 shows the three components of EW.
Figure 1-1. EW components
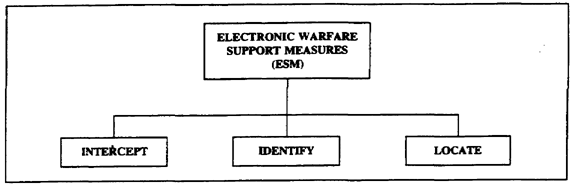
a. ESM provides the capability to intercept, locate, and identify enemy emitters (Figure 1-2). This information is needed for planning jamming, deception, electronic counter-countermeasures (ECCM), and targeting operations. It is integrated with the commander's overall fire and maneuver plan. The Assistant Chief of Staff G2, Intelligence (G2), who coordinates with the Assistant Chief of Staff G3, Operations (G3), has staff responsibility for ESM operations.
Figure 1-2. ESM components
(1) Interception operations provide EW planners with intelligence about the enemy's location, activity, possible future operations, and electronic disruption capabilities. This intelligence is passed to the G3 for planning electronic countermeasures (ECM) and operations. Special EW equipment is organic to military intelligence (MI) units at corps and division. This provides the means to intercept enemy electronic communications and non-communications emissions in the high frequency (HF), very HF, ultra HF, and super HF ranges. This interception capability provides combat information for the analysts to determine the pertinent intelligence the commander needs.
(2) Identification operations help to identify the size (personnel and equipment), type, echelon, and function of enemy units. This information has great significance in the commander's fire and maneuver plans. By identifying the enemy unit, the commander and his staff can better prepare combat operations. Signals analysts at the MI battalion operations center perform this function. They use automated support to collect, manage, analyze, and report intelligence data. This intelligence is provided to the commander and his staff for planning purposes.
(3) Location operations help planners to identify likely or possible enemy intentions. The data gathered can indicate if an enemy is in an offensive, defensive, or retrograde posture. The size of the area an enemy is occupying is a factor in determining the enemy unit's type and size. MI units at corps and division use airborne and ground-based sensors to locate enemy positions through DF of electronic emissions. The location and movement of enemy forces tells the commander and his staff what the enemy is doing or preparing to do. In addition to situation development, location intelligence is also used in planning the targeting of enemy positions.
b. ECM is offensive action taken to prevent or reduce an enemy's effective use of the electromagnetic spectrum. Effective ECM operations can degrade an enemy's combat effectiveness by degrading his electromagnetic operations. ECM, a staff responsibility of the G3, includes both electronic jamming and deception.
(1) Electronic jamming reduces or denies an enemy the effective use of his electronic equipment. Jamming can assist the ESM team by forcing an enemy to transmit in the clear and for longer periods. As a result, the ESM team can gather pertinent information about the enemy (intentions, location, size, etc.), which may assist the commander and his staff in preparing operational plans. Denying an enemy the use of the electromagnetic spectrum at key times causes chaos, disrupts combat operations, and reduces combat effectiveness.
(2) Electronic deception is used to cause an enemy to misinterpret what his electronic collection systems receive. It is usually conducted as part of a larger deception operation. It is associated with friendly electromagnetic radiations (SED and manipulative electronic deception (MED)) and with those of the enemy force (imitative electronic deception (IED)).
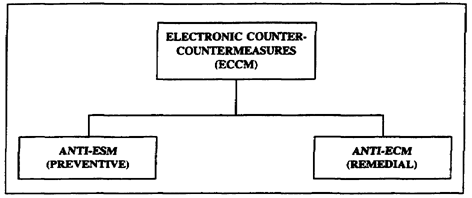
c. ECCM are defensive measures used to protect friendly command, control, and communications (C3) systems from enemy EW activities. It is closely related to signal security (SIGSEC). The main difference between the two is the type of information being protected from the enemy. ECCM protects friendly emitters from enemy EW assets. SIGSEC protects the information friendly forces transmit. ECCM allows friendly forces the continual use of the electronic spectrum by anti-ESM (preventive) and anti-ECM (remedial) activities (Figure 1-3). ECCM falls under the direction of the G3.
Figure 1-3. ECCM components
(1) Anti-ESM are actions taken to deny the enemy access to friendly force's electromagnetic transmissions. This is done by avoiding the enemy force's EW operations. To deny an enemy access to friendly electronic assets, several actions may be taken. An example is terrain masking, where a friendly radio station is placed, so an obstacle (such as a hill) is between it and the enemy. A second example is avoidance (using a directional antenna). A third example is emission control (operating at the lowest power needed, turning on the transmitter only when needed, and using random scheduling for communicating, if possible).
(2) Anti-ECM are used against jamming, but cannot be used against deception or ESM. Anti-ECM involve actions taken after discovering that the enemy is using EW against friendly forces. Effective anti-ECM methods are determining the cause of interference, recognizing the difference between jamming and natural interference, changing frequencies, or shutting down communications and switching to alternate frequencies.
3. Summary.
a. The use of EW followed the development of radio. As nations improved their intelligence gathering systems, they also introduced methods to thwart their adversaries' means of collecting intelligence. Codes and ciphers were developed. The periodic changing of call signs and frequencies became a daily part of communications. Jamming and the creation of deceptive communications practices became a sophisticated practice. EW has been used extensively since World War Ii.
b. EW contributes much to C3CM. There are three components of EW.
(1) ESM. Interception operations provide EW planners with intelligence about the enemy's location, activity, possible future operations, and electronic disruption capabilities. Location operations help planners to identify likely and possible enemy intentions. ESM identification operations help to identify the size, type, echelon, and function of enemy units.
(2) ECM. These offensive actions are taken to prevent or reduce an enemy's effective use of the electromagnetic spectrum. Electronic jamming reduces or denies an enemy the effective use of his electronic equipment. The objective of electronic deception is to deceive an enemy through his electronic systems.
(3) ECCM. These are defensive passive measures used to protect friendly (C3) systems from enemy EW activities. ECCM and SIGSEC are closely related.
(a) Anti-ESM are actions taken to deny the enemy access to friendly use of the electromagnetic spectrum.
(b) Anti-ECM are used against jamming. Anti-ECM cannot be used against deception or ESM.