|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 1
FUNDAMENTALS OF OFFENSE
TASK:
Identify the fundamentals of the offense.
CONDITIONS:
Given the subcourse material for this lesson, a training scenario and extracts, as applicable, the student will complete the practice exercise at the end of this lesson.
STANDARD:
The student will demonstrate his comprehension and knowledge of the task by identifying the purposes, characteristics, and phases of offensive operations; and identifying the forms of maneuver and the framework for tactical offensive operations.
REFERENCE:
FM 100-5
GENERAL
This lesson will introduce you to the fundamentals of offensive operations. It will help you to develop an understanding of the role of the offense in military operations. The learning events contained in this lesson will show you the purpose, characteristics, and phases of offensive operations. You will learn about forms of maneuver and the elements which comprise the offensive framework.
Learning Event 1:
IDENTIFY THE PURPOSE, CHARACTERISTICS, AND PHASES OF OFFENSIVE OPERATIONS
This learning event will provide you with an understanding of some of the purposes for conducting an offensive campaign. You will see that commanders may conduct attacks for many different reasons. However, no matter what the original intent, successful offensive campaigns all share common characteristics. You must recognize these traits. To succeed in an attack, you must also be familiar with the phases of offensive operations.
To properly understand these fundamentals, you must be able to recognize and use them in the perspective of a real battlefield situation. This learning event will begin, therefore, by describing a real battle from history. This will provide you with an historical perspective.
HISTORICAL EXAMPLE
From the Revolutionary War to the present, the U.S. Army has a long history of successful offensive campaigns. Sherman, Jackson, MacArthur, Bradley, and Patton are names which stand out from a long list of American leaders who were expert in the attack.
Of all the American generals, perhaps General Ulysses S Grant was the outstanding expert in offensive operations. Although he could fight direct and bloody actions when necessary, he was also a master of maneuver, speed, and the indirect approach. His operation south of Vicksburg in the spring of 1863 has been called the most brilliant campaign ever fought on American soil. It exemplifies the qualities of a well-conceived, violently executed offensive plan. A deeper look at this battle will help construct a perspective for the basics of a good offensive.
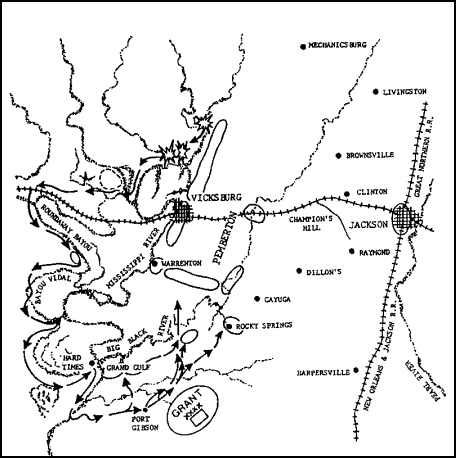
General Grant moved his army south of the fortress of Vicksburg after 6 months of fruitless fighting had taken place north of it. He also crossed to the eastern bank of the Mississippi early in May. He brilliantly masked this difficult move from Confederate observation by a series of demonstrations and raids. By moving south of Vicksburg (Figure 1A ) and crossing the Mississippi, Grant succeeded in turning the Confederate defense.
FIGURE 1A. THE VIGKSBURG CAMPAIGN.
He also placed the Union Army within reach of the Confederate rear. Grant's action was risky because it separated him from his base of operations. It placed him in enemy territory against an army of equal strength.
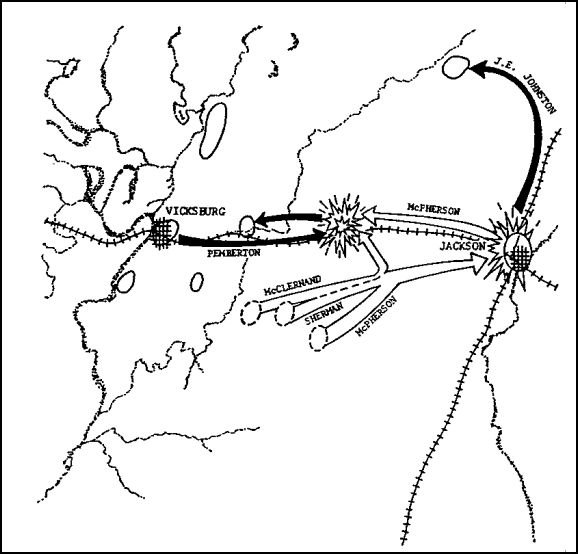
In spite of this, Grant retained the initiative. He did not move north on the most obvious approach to his objective. Instead, Grant avoided the defenses south of Vicksburg. He used the Big Black River to protect his flank as he maneuvered toward Jackson, Mississippi. By threatening both cities, Jackson and Vicksburg, Grant prevented the Confederates from uniting their forces against him. By swinging to the east of the fortress (Figure 1B ), he interdicted its main line of support.
FIGURE 1B. THE VICKSBURG CAMPAIGN (CONTINUED).
His speed of movement and his refusal to establish conventional lines of supply added to the effect of his attack. Grant's actions succeeded in completely confusing the Confederates and frustrating their attempts to strike at his rear.
Grant set a pace of operations so rapid that the Confederates could not follow his activities. In doing so, he defeated the forces of Confederate Generals Johnston and Pemberton in five successive engagements. His troops covered 200 miles in 19 days, capturing the city of Jackson and driving the defenders of Vicksburg into their trenches.
Grant's 4,000 casualties were only half as great as those of the enemy. Six weeks later, the 30,000-man garrison of Vicksburg surrendered. This action gave the Union uncontested control of the Mississippi. In effect, it divided the Confederacy.
Campaigns of the future will require the same speed, surprise, maneuver, and decisive action as campaigns during General Grant's time. Modern commanders will have the advantage of sensors and long-range weapons. As attackers, they will be able to rapidly move their ground and air units and to concentrate forces and fires at the time and place of their choosing. Modern commanders who can harness these advantages will be able to collapse the enemy's defenses rapidly and in depth.
As the historical example suggested, there can be many reasons for conducting offensive operations. The paragraphs which follow discuss the most common purposes for offensive tactics.
PURPOSES OF THE OFFENSE
Commanders of military units conduct offensive operations to:
- Defeat enemy forces.
- Secure key or decisive terrain.
- Deprive the enemy of resources.
- Gain information.
- Deceive and divert the enemy.
- Hold the enemy in position.
- Disrupt an enemy attack.
Because offensive operations involve movement, they require the attacker to expose himself. Therefore, the attacker usually must have a local superiority in combat power at the point of the attack. This, and the need to have enough forces available to exploit success, imply a commanders willingness to accept risk elsewhere on the battlefield. Therefore, a successful attack must be pressed relentlessly. An attack which is properly pressed will prevent the enemy from recovering from the initial shock. He will be unable to regain his equilibrium. Furthermore, if an attack is sufficiently pressed, it will prevent the enemy from reconstituting a cohesive defense. It may also limit his ability to launch a counterattack.
Defeating Enemy Forces
Offensive operations may have as their objective the destruction of an enemy force. However, inflicting physical damage is often incidental to offensive success. Rather, an attacking force can achieve large gains by destroying the coherence of the enemy's defense. It will also gain by fragmenting and isolating enemy units in the zone of attack, and by driving deep into enemy territory to secure operationally decisive objectives. Historically, the most successful offensive operations have produced more enemy prisoners than casualties. This fact reflects the corrosive impact of offensive shock on the enemy's will to resist.
Successful attacks normally share a number of common elements. Successful offensive efforts will most likely result from attacks that:
- Avoid the enemy's main strength.
- Turn the enemy out of his defensive position.
- Isolate the enemy from support.
- Cause the enemy to fight in an unintended direction on ground he has not prepared.
Interestingly, many of the famous commanders of history have consistently attempted to produce such conditions. They did so in order to shift to the defender the disadvantages of fighting while exposed and surprised. Field Marshal Viscount Slim put it concisely:
| Hit the other fellow As quick as you can, Where it hurts him most, When he isn't looking. |
There will be times when only more direct attacks are possible. Even General MacArthur, a master of maneuver, was forced to use frontal attacks to seize Buna and Gona in New Guinea during World War II. Frontal attacks are almost always costly in lives and materiel. Thus, commanders should only undertake them when no other approach is possible to accomplish the mission.
Related Purposes
Most attacks seek the outright defeat of the opposing force. However, it is also useful to conduct offensive operations for related purposes.
Seizing Key Terrain
Attacks can be mounted to seize key terrain for use in defense or subsequent attacks. Attacks may also be useful to secure or protect vital lines of communication. An example of this type of attack would be the Israelis capture of the Mitla Pass in 1967. Control of the Mitla Pass provided the Israelis the springboard for their subsequent drive to the Suez Canal.
Depriving the Enemy of Resources.
Another reason to conduct an attack may be to secure critical war-supporting resources. An example of this is Germany's effort in 1941 to seize Great Britain's oil fields in the near east.
Gaining Information.
Sometimes, it may be useful to launch an attack simply to force the enemy to disclose his strength, dispositions, or intentions. Such a reconnaissance in force may develop into a major attack if the initial probe discloses an exploitable weakness in the enemy's defenses.
Deceiving and Diverting the Enemy.
Another purpose of attacking is to deceive or distract the enemy. In conjunction with other deceptive measures, diversionary attacks can delay the enemy's identification of and reaction to the main effort. Such attacks may actually induce him to shift forces away from critical areas.
Holding the Enemy in Position.
An attack also may be designed to fix an enemy force in position. This is done to prevent enemy interference with maneuvers of other friendly forces. Feints and demonstrations are also special forms of diversionary attacks used by commanders.
Disrupting an Enemy Attack.
Finally, once hostilities are begun, a defending force may use attacks to disrupt an expected enemy attack. Attacks of this type, if properly conducted, can upset enemy preparations and, in so doing, buy time and information. Spoiling attacks, as they are known, like a reconnaissance in force, may develop into a major offensive operation if the attack reveals an exploitable weakness. Raids are a special form of spoiling attacks. Raids are designed to destroy installations or facilities critical to the enemy's operations. Raids may be mounted prior to, or in conjunction with, other offensive operations to confuse the enemy or divert his attention.
Commanders may undertake offensive operations, for one or more of these purposes. Whatever their purpose, successful attacks have elements in common. These characteristics of offensive operations will be discussed next.
CHARACTERISTICS OF OFFENSIVE OPERATIONS
All successful offensive operations are characterized by surprise, concentration, speed, flexibility, and audacity.
Surprise
Commanders achieve surprise by striking the enemy at a time or place, or in a manner, for which he is unprepared. Surprise delays enemy reactions; it overloads and confuses his command and control systems. Surprise also reduces the effectiveness of his weapons, and induces psychological shock in soldiers and leaders. By radically reducing the enemy's combat power, surprise allows the attacker to succeed with fewer forces than he might otherwise require.
Surprising the enemy once hostilities have begun has never been easy. Modern surveillance and warning capabilities have made it even more difficult. However, a commander can still achieve surprise. He can do this by operating in a manner contrary to the enemy's expectations. For example, he can order an attack over a more difficult, and therefore less obvious, avenue of approach. By ordering an attack in adverse weather, he can also attain surprise. An example of successful application of the characteristic of surprise is Germany's precipitate defeat of France in 1940. The Germans achieved surprise by attacking with their armored and mechanized forces through the Ardennes Forest. Military thinkers had considered this region to be "impassable" for large mechanized forces. Four years later, the Germans surprised the American Army by attacking over the same ground in the dead of winter.
By radically altering the structure or tempo of the battle, a commander can also achieve surprise. For example, the insertion of airborne, air-mobile forces or special operating forces deep in the enemy's rear can sharply and suddenly increase the enemy's sense of threat. The action may sow fear into and confusion and in the extreme case induce outright paralysis. This technique has achieved these effects in the past. On the night of 5 June 1944, prior to the Normandy invasion, large scale British and American airborne attacks had just such an effect on defending German forces.
Deep ground attacks can also achieve surprise simply through the rapidity with which they move. They can cause enemy rearward forces to confront an unanticipated threat. An example of this form of surprise is the Israeli attack in the Sinai in June 1967.
Manipulating the enemy's expectations through deceptions, feints, and ruses can also attain surprise. Egypt's attack across the Suez Canal in 1973 owed its success, in part, to a succession of demonstrations and maneuvers conducted in the months prior to the attack-actions. These demonstrations led the Israelis to believe that preparations for the actual attack were merely part of the same pattern. A more recent example is the British use of deception in the Falkland Islands to achieve surprise over the Argentinian forces defending Port Stanley.
Surprise can radically degrade enemy combat power. However, the effect is usually only temporary. One has only to recall the experience of the U.S. Army in 1944 during the Battle of the Bulge to see the validity of this point. At that time, after initially suffering a crippling blow, American forces regrouped. Within a matter of days, they launched a counterattack that caused the Germans to give up the assault, go over to the defensive, and finally to retreat.
Unless enemy's forces or their leaders are inherently fragile or demoralized, sooner or later they will recover from the initial shock. History affords countless examples of armies which have recovered from initial surprise and achieved victory. To reap the benefits of surprise, an attacking commander must ruthlessly exploit its initial shock effect. He must allow the enemy no time to regain his equilibrium.
As you can see, surprise can be a vital ingredient of a successful offensive operation. However, surprise can never be guaranteed. Even when achieved, it rarely lasts. While always seeking surprise, the commander must also hedge against the loss of surprise. He must continue to plan to aggressively exploit surprise whenever it is achieved.
Surprise is only one of the characteristics of offensive operations. The characteristic known as concentration forms the next topic of discussion.
Concentration
Surprise undoubtedly contributes to offensive success. However, concentration of effort is invariably essential to achieve and exploit this success. Virtually all modern offensive operations have been characterized by sudden concentrations followed by rapid, deep exploitations. Examples of this characteristic are:
- The German attack through France in 1940.
- The Soviet attack into Manchuria in 1945.
- The American counter-offensive in Korea in 1950.
- The Israeli seizure of the Sinai in 1967.
All of the above examples illustrate the rapid concentration of combat power to penetrate or envelop, then shatter the enemy's defenses. In all but the Manchurian case, the attacker enjoyed little overall numerical superiority. Each victor succeeded by achieving overwhelming local superiority, then preserving that initial advantage by rapid and relentless exploitation.
Modern technology has made the process of concentration both more difficult and more dangerous. Advances in air and ground mobility enable the attacker to concentrate more rapidly; however, they also enable the defender to react more quickly. Moreover, the lethality of modern weaponry, especially of nuclear weapons, radically increases the threat to concentrated formations.
A commander, planning an attack, must work to overcome these difficulties. He must manipulate both his own troop concentrations and those of the enemy. First, he must disperse his forces in order to stretch the enemy's defenses and to avoid presenting lucrative targets for the enemy's deep fires. He must then concentrate rapidly along converging axes to overwhelm enemy forces at the point of attack. Next, the commander must plan to disperse his forces once again. By doing this, he can exploit his initial success and shatter the enemy's in-depth defenses.
Achieving this pattern of rapid concentration and dispersal requires flexible leaders and agile units. It also requires careful synchronization of combat, combat support, and combat service support activities. Commanders at all levels must designate a main effort and focus resources to support it. They must then be prepared to shift it rapidly without losing internal cohesion as the attack unfolds. Units making the main attack must be able to adjust to changing circumstances without the time consuming and potentially confusing need to reorganize. They must be allocated enough combat support and combat service support to make these rapid adjustments. At the same time, the commander must retain control of sufficient assets to be able to shift his main effort to a supporting attack if it becomes more promising.
Special efforts must be devoted to concealing concentrations from the enemy until it is too late for him to react effectively. This is true at every level, but it is especially important at division and higher levels. Units must avoid or mask patterns of movement which might reveal the direction or timing of the attack. Monitoring of logistical build-ups, patrolling activities, communications, and indirect fires must take place to preclude visible changes in the attacking forces normal operating pattern. Such changes might alert the enemy to an impending attack. A commander must always keep in mind that successful concentration for an attack requires speed, security, and deception.
On the AirLand battlefield, concentration requires the careful prior coordination of other service support. This is especially true for air support. Tactical air operations will be vital at every stage of the attack. Examples of the kinds of tactical air support that will be required are:
- Offensive and defensive counter air strikes to protect the concentration from detection and attack.
- Reconnaissance and interdiction to delay and disrupt enemy counterconcentrations.
- Close air support to weight the main effort and to sustain the momentum of the attack.
Airpower's flexibility makes it a powerful instrument of rapid concentration. However, its full advantages cannot be realized unless ground and air operations are effectively synchronized.
An attacking commander needs the advantage of both concentration and surprise. Another major characteristic that he will need in his offense is speed.
Speed
In offensive operations, the attacker must move rapidly. Speed is essential to success. It promotes surprise and keeps the enemy off balance. Speed also contributes to the security of the attacking force and prevents the defender from taking effective countermeasures. When properly exploited, speed can confuse and immobilize the defender until the attack becomes unstoppable. In addition, speed can compensate for a lack of mass. It can provide the momentum needed for attacks to achieve their aims.
Attacking forces move fast. They follow reconnaissance units or successful probes through gaps in enemy lines. Attacking forces must shift their strength quickly to widen penetrations, roll up exposed flanks, and reinforce successes. The attacker tries to carry the battle deep into the enemy rear. His objective is to break down the enemy's defenses before he can react. Enemy forces must never be permitted to:
- Recover from the shock of the initial assault.
- Gain time to identify the main effort.
- Have the opportunity to mass forces or supporting fires against the main offensive effort.
Through careful planning, a commander can build speed into offensive operations. Commanders must identify the best avenues for attack. They must plan the battle in depth. They must also provide for quick transitions to exploitation and pursuit, and concentrate and combine forces effectively. Violent execution of the plan by fire and maneuver units is the key to the use of speed in offensive operations. However, speed also depends on:
- Full understanding of the commander's intent.
- Availability and positioning of engineers.
- Use of air and ground cavalry.
- Maintenance of effective air defense.
- Responsive logistic support of the force.
- Effective use of military intelligence (MI) and electronic warfare (EW) assets.
- Effective command and control.
- Effective air support.
In addition to speed, concentration, and surprise, a commander must have flexibility in his offense. This characteristic will be discussed next.
Flexibility
The attack must be flexible. The commander must foresee developments as far ahead as possible. However, he must also expect uncertainties and be ready to exploit opportunities. On a fluid battlefield, in order to preserve synchronization, initial planning must be detailed. Subordinates must understand the commander's aims so well that they can properly exploit battlefield opportunities. They must be able to do this even when communications fail. The corps or division must coordinate and support all arms. They must also control operations that may cover 50 to 80 kilometers daily and frequently change direction. In such an environment, brigades and battalions must sustain themselves and maintain the ability to change direction quickly. They must achieve this without losing either unit concentration or synchronization.
Commanders must plan to use routes which permit the maximum possible opportunities for maneuver around strongpoints. For flexibility, plans for a major offensive operation must provide:
- Alternative routes from the main approach.
- Plans for reversion to the defense and for exploitation.
- Control measures that facilitate changing the direction or location of the main effort.
- Provisions for combat at night or in limited visibility.
Commanders must also be aware of the roles of nuclear and chemical weapons, even if plans for the attack do not call for their use. They must plan to protect their force from the effects of these weapons in the event they are used by the enemy. Planning for maximum dispersal, using multiple routes, and having reserves assume major missions are all basic to an attack.
We have discussed surprise, concentration, speed, and flexibility as characteristics of successful offensive operations. A fifth characteristic is audacity.
Audacity
Historically, audacity has always been a feature of successful offensives. More attacks have been defeated due to a lack of audacity than for any other reason. General George S. Patton, Jr. warned the overly cautious around him, "Never take counsel of your fears. The enemy is more worried than you are. Numerical superiority, while useful, is not vital to successful offensive action. The fact that you are attacking induces the enemy to believe that you are stronger than he is." In short, the key tenets of the AirLand Battle doctrine also apply to any successful attack. These tenets are: initiative, agility, depth, and synchronization.
With the characteristics of the offense at his disposal, the commander must understand the various phases of offensive operations.
PHASES OF OFFENSIVE OPERATIONS
Offensive operations tend to occur in roughly sequential phases. However, the length and nature of each phase, and whether it occurs at all, will vary from situation to situation. The four general phases of offensive operations are preparation, attack, exploitation, and pursuit.
Preparation
The preparatory phase of an offensive operation involves the concentration of attacking and support forces and their movement into contact with the enemy. This phase may also include diversionary actions and the delivery of preparatory fires. The extent and nature of the preparatory phase will depend on whether or not opposing forces are already in contact and on the posture of the enemy.
A central feature of the preparatory phase is the movement to contact. Movement to contact is conducted to gain or reestablish contact with the enemy. It is normally associated with mobile operations in which both sides are contesting the initiative. However, movement to contact occurs at some level in virtually all attacks where forces are not in immediate proximity. Some of its characteristics are:
- Rapid movement along multiple axes.
- Decentralized control.
- Rapid deployment of combined arms formations from the march to attack or to defend.
In a fluid situation where both opponents have freedom of maneuver, movement to contact will frequently produce a meeting engagement. In this engagement, each side attempts to seize the initiative and either overwhelm the other or force it to go on the defensive. The Soviets consider this a likely result, especially in nuclear and chemical warfare. Because of this belief, they frequently practice rapid attack from the march.
More often, movement to contact occurs when a defending enemy has disengaged or is attempting to do so. In this case, the objective of the movement to contact is to force the enemy to battle before he can reestablish a cohesive defense.
Movement to contact, even in less fluid conditions, will be necessary whenever opposing forces are beyond immediate observation. In a division attack, for example, battalions or even brigades may need to conduct a movement to contact prior to deploying for attack if the situation to their front is ambiguous and enemy positions have not been clearly located. Such situations are especially characteristic of wide envelopments.
In either case, the critical elements of the movement to contact are:
- Security to the front and flanks.
- Smooth and rapid deployment into the attack when contact is made.
- Prior coordination of both ground and air supporting fires to produce the fastest possible build-up of combat power superiority at the point of contact.
A commander must recognize that seizure of the initiative is the overriding imperative. Seizing the initiative will require aggressive action by leaders at every level without waiting for detailed orders.
At this point, the discussion pertaining to the preparation phase of offensive operations is concluded. In the next phase, the student will be introduced to the attack phase of the offensive operation.
Attack
Movement to contact, unless contact reveals an overwhelmingly superior enemy force, will normally be followed immediately by a hasty attack. The hasty attack will be launched with the forces at hand and with a minimum of preparation. The object of the hasty attack is to destroy the enemy before he is able to either concentrate or establish a defense. Such an attack may also be employed to seize a fleeting opportunity or to regain the initiative quickly after a successful defense. In the defense, hasty counterattacks may recapture lost positions before the enemy has had time to consolidate his success. In World War II, German units, down to platoon level, were renowned for the rapid and effective ways in which they could mount such hasty counterattacks.
At higher echelons, hasty attacks are often anticipated through the use of contingency plans. Large formations attack from the march using hasty attacks by subordinate units or covering forces.
A hasty attack, regardless of its purpose or the echelon at which it is conducted, purchases agility at the risk of losing synchronization. In order to minimize this risk, units conducting hasty attacks must make maximum use of standard formations and well understood and rehearsed battle drills. Supporting arms and services must be able to react quickly, using prearranged procedures. The more closely combat and combat support units have worked together prior to the attack, the easier and more successful such implicit coordination will be. Hasty attacks place a premium on habitual relationships among supporting and supported units at every level.
Deliberate attacks, in contrast to hasty attacks, are fully synchronized operations which employ every available asset against the enemy defense. Because such synchronization requires careful planning and extensive coordination, deliberate attacks take time to prepare. During this time, the enemy can improve his defenses, disengage, or even launch a spoiling attack of his own. Deliberate attacks should, therefore, be reserved for those situations where the defense can neither be outflanked nor overcome with a hasty attack.
A successful attack, either hasty or deliberate, depends on concentrating the maximum possible shock and violence against the enemy force. The objective is to shatter the enemy's nerve, to ruin his combined arms synchronization, and destroy his units cohesion and the willingness of his soldiers to fight. Most successful attacks leave defending units unable to resist further.
In addition to preparation and attack,commanders must understand the exploitation phase of offensive operations. This phase will be discussed next.
Exploitation
Complete annihilation of a defending enemy force as a result of an attack rarely occurs. More often, the enemy will attempt to disengage. He will withdraw whatever he can, and reconstitute an effective defense as rapidly as possible. In large-scale operations, the enemy may attempt to draw forces from less active areas or bring forward reserves not yet committed. As a rule, every attack not restricted by higher authority or by lack of resources should be boldly exploited. Exploitation is designed to keep the pressure on the enemy, compound his disorganization, and erode his will to resist. The ultimate objective of the exploitation is to disintegrate the enemy forces to the point where they have no choice but to surrender or flee.
Exploitation is integral to every attack. However, it is especially important in a deliberate attack in which concentrations for the attack may require accepting risk elsewhere. Failure to exploit success aggressively may permit the enemy time to detect and exploit that weakness. Such a failure could allow him to regain both the initiative and the advantage.
You now have a basic understanding of three of the four phases of offensive operations. The next paragraphs will discuss the fourth phase of offensive operations, pursuit.
Pursuit
If it becomes apparent that enemy resistance has completely broken down, attack or exploitation may give way to pursuit. Annihilation of the opposing force is the object of the pursuit. It is conducted as a series of encirclements in which successive portions of the fleeing enemy are intercepted and either captured or destroyed. In modern war, large scale pursuits are rare. They do, however, occur. For example, in 1950 the U.S. Eighth Army pursued North Korean forces to the Yalu River in Korea after the Inchon landing and the breakout from the Pusan perimeter. The pursuit, like the exploitation, is normally characterized by broad decentralization of control and rapid movement. Unlike the exploitation, however, the pursuit can rarely be anticipated. Forces are not normally reserved for it.
Exploitations and pursuits test the audacity and endurance of both soldiers and their commanders. Typically, an attack will disorganize the attacker nearly as much as the defender. Attacking forces will be tired. Units will have suffered losses of men and equipment. As the exploitation or pursuit unfolds, lines of communication will become increasingly tenuous. Extraordinary efforts will be required to sustain the momentum of the attack and thus turn tactical success into an operational or even strategic victory.
Historical examples exist which reveal all four phases of the offense occurring in the sequence just described. However, most often, offensive operations deviate from this pattern in one way or another Attacks, and especially counterattacks,may take place with little preparation. They may follow the unintended collision of forces at a time and place neither had foreseen. The battle of Gettysburg resulted from just such an unintended collision.
Successful attack may give way directly to pursuit, bypassing exploitation altogether. Such a pattern was typical of engagements in Vietnam. In these engagements, enemy forces attacked by U.S. forces simply sought sanctuary in Laos or Cambodia.
In conventional war, in contrast, pursuits are rare. Exploitation is more likely to end short of annihilation, to be curtailed by insufficient sustaining capability or by deliberate strategic restriction.
Some offensive operations intentionally exclude one or more phases. Spoiling attacks and feints, for example, rarely envision full exploitation. However, unusual circumstances may convert either into a full-scale attack. Demonstrations seek no real contact whatever. They are, in effect, no more than an elaborate preparatory phase designed to deceive the enemy into expecting an attack.
Finally, phases may run into each other with no abrupt and discernible break. This is especially true of the exploitation and pursuit phases. Nevertheless, these phases constitute significantly different problems. Therefore, each must be dealt with differently in planning and execution.
This concludes learning event 1. In the next learning event, you will learn the various forms of offensive maneuver and the framework for tactical offensive operations.
Learning Event 2:
IDENTIFY THE FORMS OF MANEUVER AND THE FRAMEWORK FOR TACTICAL OFFENSIVE OPERATIONS
Knowing the purposes, characteristics, and phases of offensive operations gives you a foundation on which to build your knowledge of offensive operations. To apply this knowledge, you must also understand the forms of maneuver and the framework for tactical offensive operations. This learning event covers these topics. Forms of maneuver are discussed first.
FORMS OF MANEUVER
As similar phases are common to all offensive operations, similar forms of maneuver are common to all attacks. These forms of maneuver include envelopment, the turning movement, infiltration, penetration, and frontal attack. Although frequently used in combination, each form attacks the enemy in a different way, and each poses different challenges to the attacking commander.
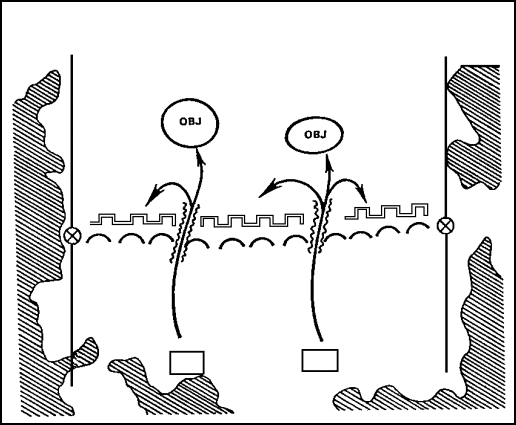
Envelopment
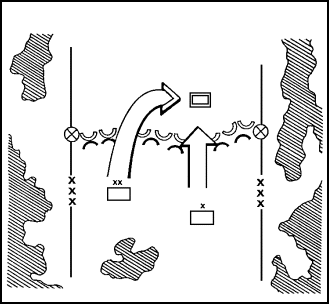
The basic form of maneuver in any doctrine which seeks to apply strength against weakness is envelopment ( Figure 2). Envelopment avoids the enemy's front, where his forces are most protected and his fires most easily concentrated. Instead, the attacker fixes defender's attention forward, by supporting or diversionary attacks. The attacker then maneuvers his main effort around or over the enemy's defenses to strike at his flanks and rear. Flank attacks are a variant of the envelopment. In flank attacks, the enemy's own forward movement provides the attacker with access to the enemy's flank and rear.
Single envelopments are directed against only one flank of the defending forces. Double envelopments attack both flanks. Either variant can develop into an encirclement if the attacking force is able to sever the defender's lines of communications (LOCs) and prevent his reinforcement or escape.
For an envelopment to succeed, the attacker must discover or create an assailable flank. In meeting engagements and counterattacks, this may be the actual flank of the enemy force. In less fluid conditions, it is more likely to be a gap or weak point in the enemy's defense. Such gaps can be created by conventional, nuclear, or chemical fires. They can also be created by penetration prior to envelopment.
FIGURE 2. ENVELOPMENT.
Typically, envelopment requires less initial combat power than other forms of maneuver. This is because the attacker does not need to push through heavily defended, prepared positions. However, envelopment places a premium on agility since success depends on reaching the enemy's vulnerable rear before he can shift his forces and fires.
Envelopment is only one of the forms of maneuver. The next paragraph will introduce you to the form of maneuver known as the turning movement.
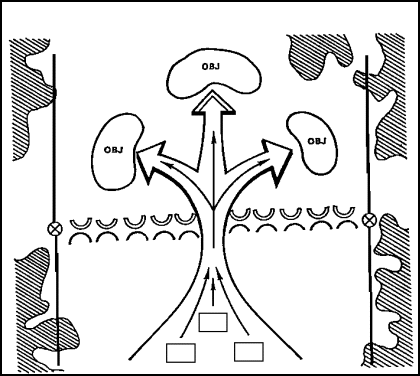
Turning Movement
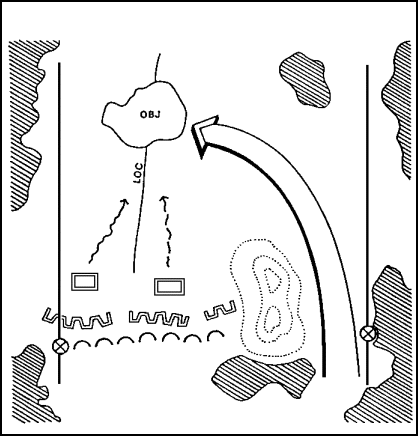
The turning movement (Figure 3) is a variant of the envelopment. In the turning movement, the attacker tries to avoid the defense entirely. Instead, the attacker seeks to secure key terrain deep in the enemy's rear and along his lines of communication. Faced with a major threat to his rear, the enemy is thus "turned" out of his defensive positions. Proper execution of this movement forces the enemy to attack rearward at a disadvantage. A classic example of a turning movement was General MacArthur's invasion at Inchon during the Korean War.
FIGURE 3. TURNING MOVEMENT
Amphibious, airborne, and air assault forces are uniquely valuable for conducting turning movements. However, because they will have to fight beyond the supporting distance of other ground forces, they will require heavy and continuous air and/or naval support.
In addition to the envelopment and the turning movement, you must become familiar with the form of maneuver known as infiltration. The paragraphs which follow will introduce you to this form of maneuver.
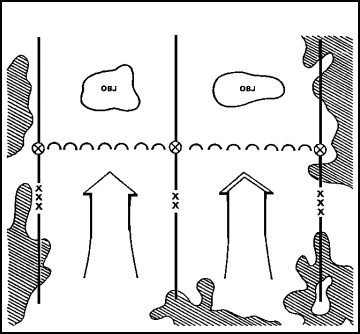
Infiltration
Another means of reaching the enemy's rear without fighting through prepared defenses is infiltration ( Figure 4). Infiltration is the covert movement of all or part of the attacking force through enemy lines to a favorable position in his rear. Successful infiltration requires above all the avoidance of detection and engagement. That requirement limits the size and strength of the infiltrating force. Because this is true, infiltration can rarely defeat the defense by itself. Rather, it is normally used in conjunction with some other form of maneuver.
FIGURE 4. INFILTRATION
Infiltration is most feasible when the terrain is rough or when visibility is reduced. It is useful in areas poorly covered by observation and fire. It may also be used to;
- attack lightly defended positions.
- attack stronger positions from the flank or rear.
- Secure key terrain in support of the main effort.
- disrupt the enemy rear positions.
Penetration
The next form of maneuver is known as penetration. Penetration (Figure 5) is used when enemy flanks are not assailable and when time does not permit the use of some other form of maneuver. It attempts to rupture enemy defenses on a narrow front. It thereby tries to create both assailable flanks and access to the enemy's rear.
Penetration typically comprises three stages:
- Initial rupture of enemy positions.
- Roll-up of the flanks one either side of the gap.
- Exploitation to secure deep objectives.
The penetration itself is vulnerable to flank attack, especially in its early stages. Therefore, penetrating forces must move rapidly, and follow-on forces must be close behind to secure and widen the shoulders. Fire support must concentrate on suppressing enemy defenses quickly, then shift to protect the flanks of the attack.
Depending on the forces available, commanders may attempt penetration on one or several axes. When feasible, multiple penetrations are desirable. This is because they disperse the enemy's fires and complicate the commitment of his reserves.
FIGURE 5. PENETRATION
You should now be familiar with envelopment,the turning movement, infiltration, and penetration. The last form of maneuver to be discussed here is the frontal attack.
Frontal Attack
The frontal attack (Figure 6) strikes the enemy on a wide front over the most direct approaches. For deliberate attacks, it is the least economical form of maneuver. This is because it exposes the attacker to the concentrated fire of the defender. Simultaneously, it limits the effectiveness of the attacker's own fires.
The frontal attack is the simplest form of maneuver. It is useful for overwhelming light defense, covering forces, or disorganized enemy forces. A frontal assault is often the best form of maneuver for a hasty attack or for a meeting engagement in which speed and simplicity are paramount. It is also a good form to use to exploit the effects of nuclear or chemical fires. Frontal attacks may be used during exploitation or pursuit. Subordinate elements of large formations may use frontal attacks when conducting an envelopment or penetration.
The forms of maneuver have changed very little in modern history. Potential adversaries, as well as American leaders, understand and practice the forms of maneuver. Successful offensive operations depend less on the choice of the forms used than on their creative combination. Success will especially depend on the skill and audacity with which they are executed.
Now that you know the forms of maneuver, you must understand the context, or tactical framework, within which offensive operations are conducted.
FIGURE 6. FRONTAL ATTACK.
TACTICAL OFFENSIVE FRAMEWORK
Military history repeatedly shows that the basis of all tactical offensive actions is a simple, complete concept of operation. This concept must permit rapid transition between offensive phases.
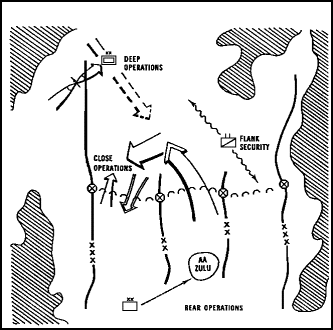
In fighting their offensive battles, corps and divisions use these five complementary elements:
- A main attack with supporting attacks as required.
- Reserve operations in support of the attack.
- A reconnaissance and security operation forward and to the flanks and rear of main and supporting attacks.
- A continuous deep operation in vital parts of the zone of attack.
- Rear area operations necessary to maintain offensive momentum.
Higher echelons such as division or corps may conduct some deep and rear operations which could affect brigade and subordinate units (Figure 7). They should, therefore, coordinate their activities with the units that might be affected. Brigades and battalions do not normally conduct separate deep and rear operations. As a rule, these echelons look for and anticipate enemy uncommitted forces which may affect the ability to accomplish the mission. Subordinate echelons also provide all-round security to include protection of logistic trains in the rear.
FIGURE 7. THE OFFENSIVE FRAMEWORK.
Close Operation
In the close operation, reconnaissance and security forces (covering forces and advance, flank, or rear guards) perform the following functions:
- Locate the enemy and find gaps in his defenses.
- Protect the force from surprise.
- Develop the situation.
- Give the commander time and space in which to react to the enemy.
The main and supporting efforts maneuver around or through enemy defenses to occupy objectives that permit the defeat of defending forces.
Reserves
The commander then positions his reserves to weight the main effort. Reserves are used to:
- Exploit success.
- Reinforce or maintain momentum.
- Deal with enemy counterattacks.
- Provide security.
- Complete the destruction of enemy forces.
- Secure deep objectives.
- Open the next phase of a campaign or major operation by seizing objectives beyond the defended area.
Deep Operations
Deep operations are used to:
- Isolate enemy defenses.
- Disorganize enemy reserves.
- Disrupt enemy support.
- Complicate the reconstitution of the defense during withdrawal.
Rear Operations
Rear operations assure freedom of action of committed and uncommitted forces and protect necessary combat support and combat service support from disruption.
Corps, divisions, and maneuver brigades can perform any type of tactical offensive operation. Divisions, brigades, and battalions may also be employed as security forces, as reserves, or, in some cases, as elements of deep or rear operations.
Maneuver battalions and companies attack, defend, delay, or move as part of their parent units operation. They form their own security elements and reserves as needed.
All elements of an attacking force must be able to move quickly and change orientation rapidly. They must be able to mass and disperse on the move and accept new missions without loss of time or momentum. Synchronization must be preserved in spite of rapid movement, battle losses, and changes in the main effort. Units in all elements of offensive tactical operations must be prepared to defend when they are finally halted.
CONCLUSION
The purposes, characteristics, and phases of offensive operations are all important to your study of tactical doctrine. Along with the forms of maneuver and the tactical framework, they form the basis for tactical offensive operations. In lesson 2, you will learn about the actual conduct of offensive operations. Before you begin lesson 2, take the practice exercise. It will help you measure how much you have learned so far.
GO TO: