|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 2
CONDUCTING OFFENSIVE OPERATIONS
TASK:
Identify the types and characteristics of tactical offensive operations.
CONDITIONS:
Given the subcourse material for this lesson, a training scenario and extracts, as applicable, the student will complete the practice exercise at the end of this lesson.
STANDARD:
The student will demonstrate his comprehension and knowledge of the task by identifying the types and characteristics of the tactical offensive operations; and identifying the considerations and techniques for planning, preparing, and conducting attacks; and identifying the types and characteristics of and planning considerations for special purpose operations.
GENERAL
Aggressive initiatives on the part of subordinate commanders is an outstanding element which contributes to the success of offensive operations. Other attributes of success in the offensive include:
- Rapid shifts in the main effort to take advantage of opportunities.
- Momentum.
- The deepest, most rapid destruction of enemy defenses possible.
The ideal attack should resemble what Liddel Hart called the "expanding torrent." It should move fast. It should follow reconnaissance units or successful probes through gaps in enemy defenses. By shifting its strength quickly, it will widen penetrations and reinforce its successes. By this means, the ideal attack carries the battle deep into the enemy's rear. The ideal attack rapidly destroys or brings under control those forces or areas that are critical to the enemy's overall defensive organization. This occurs before the enemy can react to the attack.
This lesson will introduce you to the critical elements of tactical offensive operations. You will learn about planning, preparing, and conducting attacks. Finally, the lesson will consider the unique considerations needed for planning special purpose operations. The lesson begins with a discussion of the types and characteristics of tactical offensive operations.
Learning Event 1:
IDENTIFY THE TYPES AND CHARACTERISTICS OF TACTICAL OFFENSIVE OPERATIONS
In any offensive campaign, the commander should try to collapse enemy defenses as quickly as possible. At the same time, he must protect his forces from unnecessary losses. Offensive campaigns should seek to retain the initiative. They should attempt to strike enemy weaknesses and to attack the enemy in great depth. A good offense will create fluid conditions which prevent the enemy from organizing a coherent defense.
As part of either offensive or defensive campaigns and major operations, corps, divisions, and smaller tactical level units may be given missions that require movement to contact, hasty attack, deliberate attack, exploitation, or pursuit. A battalion task force movement to contact will be discussed first.
MOVEMENT TO CONTACT
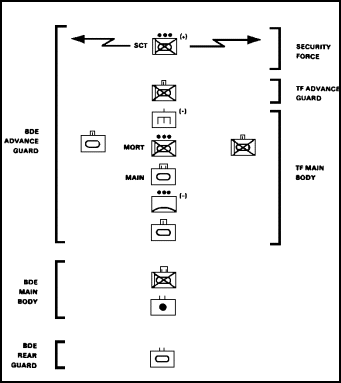
The battalion task force conducts a movement to contact to make or regain contact with the enemy and to develop the situation. Task forces conduct movement to contact independently or as part of a larger force (Figure 8). The battalion task force will normally be given a movement to contact mission as the lead element of a brigade attack, or as a counterattack element of a brigade or division. Movement to contact terminates with the occupation of an assigned objective or when enemy resistance requires the battalion to deploy and conduct an attack to continue forward movement.
A task force given a movement to contact mission is assigned a zone of action or an axis of advance and an objective at a depth sufficient to ensure contact with the enemy. Movement to contact is conducted in a manner that allows the task force to maneuver to fully develop the situation, maintain freedom of action, and, if possible, defeat the enemy once contact is made. Key planning considerations for the movement to contact are:
FIGURE 8. BATTALION TASK FORCE MOVEMENT TO CONTACT
AS PART OF A BRIGADE ATTACK.
Movement
Task force movement is oriented on the objective and along any assigned axis of advance. The task force moves consistent with the following factors:
- Speed required by brigade.
- Available avenues of approach.
- Requirements to maintain mutual support between maneuver units, security, and fire support to the security force.
- Making contact with the smallest element possible.
- Reacting to contact faster than the enemy.
Task Organization
The task force is organized with a security force, advance guard, main body, and flank and rear guards.
Security force
- The security force is normally established with the battalion scout platoon. Engineers and forward observers are attached to the scout platoon and the security force as necessary. Normally, the screening force has initial priority of indirect fires. The mission of the security force is to determine the size, activity, location, and depth of the enemy force. Decisive engagement is avoided, but once found, the enemy must be kept under surveillance and his activity reported.
- The security force is assigned area reconnaissance missions. It must cover the frontage of the task force axis of advance.
- The security force must be far enough ahead of the advance guard (usually 2 to 6 kilometers) to provide adequate warning and sufficient space for them to maneuver. However, the security force must not be so far ahead that the advance guard cannot rapidly assist in disengaging from the enemy should that become necessary. The advance guard keys its movement on the movement of the security force.
- When the enemy force is discovered, the security force calls for and adjusts fires on the enemy. Once the lead elements close on the enemy, the screening force places fires on the enemy's positions in depth or on forces maneuvering against the main body.
Advance guard
- The advance guard for a task force movement to contact is usually a company team. Its composition is METT-T dependent. In open terrain, a tank-heavy team is preferred. At night, a mechanized-infantry-heavy team is preferred. The engineers follow or are attached to the lead elements. When a task force is moving in parallel columns, the two lead companies are task organized accordingly. The mission of the advance guard is to provide security for the main body and facilitate its uninterrupted advance. This is done by rapidly developing the situation upon encountering the enemy's force, destroying reconnaissance or delaying enemy forces, and reducing obstacles.
- The advance guard is the task force commander's initial main effort. Priority of fires is shifted to the advance guard once it is committed.
- In planning the movement to contact, each contingency operation should revolve around the actions of the advance guard. The lead elements must be well trained and well rehearsed on battle drills, especially those involving obstacle reductions and actions on contact.
Main body
- The main body remains 1 to 2 kilometers behind the advance guard lead element, keying its movement to that of the advance guard. The main body remains close to the advance guard to provide responsive support when it is committed.
- The main body of the task force contains the bulk of the combat elements and is arrayed to achieve all-round security. It is flexible enough to maneuver rapidly to a decisive point on the battlefield to destroy the enemy. The tactical CP follows the advance guard; the main CP moves behind the lead element of the main body.
- The use of standard formations and battle drills allows the battalion commander to rapidly shift combat power on the battlefield. Companies employ the appropriate movement techniques within the battalion formation.
Flank and rear guards
- Flank security is normally accomplished with platoon-size elements from one or more of the companies in the main body providing a flank guard under company control. These elements are located at a distance from the main body that would allow the task force time and space to maneuver to either flank. In open terrain, this distance may extend from 2 to 3 kilometers. Indirect fires are planned on major flank approaches to enhance security.
- The trailing company of the main body provides a rear guard to protect the task force rear.
- Security is also attained by rapid forward movement which gives the enemy less time to react or to reposition forces to attack the task force.
Integration of combat support and combat service support elements
- Antiarmor. Antiarmor platoons are used as flank and rear security or are positioned to overwatch the advance guard.
- Scout platoons. The scout platoon is normally the battalion task force security force. When not performing as the security force, the scout platoon is employed in a flank screen or required to maintain contact with an adjacent battalion task force.
- Field artillery. Priority targets and family of scatterable mines (FASCAM) are allocated to the security force and advance guard. Direct support field artillery is provided by the brigade or division. Field artillery units are positioned by brigade to provide continuous indirect fires for the moving battalion task force.
- Mortars. The task force mortars are placed under the operational control of the advance guard to provide responsive fires and smoke to support initial actions on contact.
- Air Force. Close air support (CAS), if available, is employed to interdict enemy counterattack forces or destroy defensive positions.
- GSR. GSRs are employed on flank avenues of approach to provide early warning to the battalion task force. If movement occurs during limited visibility, GSRs may be used to guide the advance guard and elements of the main body toward the objective.
- Air defense Artillery. ADA assets are generally employed to provide area coverage for the task force, and to cover movement through restricted areas. However, some ADA assets may be placed in direct support of the advance guard.
- Engineers. Priority of engineer support is to mobility. Elements of the supporting engineer unit are employed with the security force to reconnoiter obstacles. Engineers travel with the advance guard to assist in mobility of the advance guard and main body. AVLBs move to the rear of the advance guard to be in position to provide responsive support to the maneuver of the main body. FASCAM is planned to support the security force and the advance guard.
- Combat trains. The task force may form unit trains for an extended movement to contact. Otherwise, it forms into echeloned combat and field trains. The combat or unit trains move as part of the task force main body. The combat trains consist of the command post, support platoon, and medical platoon. All other assets not essential for tactical support are located at the field trains.
- Support platoon. The task force support platoon moves with the main body during the movement to contact. The support platoon priority of support is to Class III and Class V. Communications are maintained with the battalion combat trains command post (CP) and field trains CP to monitor the fight and responsively switch support to a redesignated main effort.
- Medical platoon. Priority of effort of the medical platoon is to the evacuation of wounded.
- Maintenance platoon. The maintenance platoon detaches a trail party to the battalion task force rear guard. The trail party to the battalion task force rear guard. The trail party recovers or repairs damaged equipment or coordinates its collection with the FSB. All other maintenance assets locate with the field trains and prepare to provide support once the situation allows.
MEETING ENGAGEMENT AND ACTIONS ON CONTACT
The meeting engagement is normally the result of a movement to contact. A meeting engagement is the initial contact that occurs when a task force not completely deployed for battle encounters an enemy force on which little information is known. The enemy may be moving or stationary. The task force commander wargames contingencies to define how much initiative he will allow subordinate commanders in reacting to a meeting engagement. The goal, once contact is made, is to quickly and decisively overcome the enemy before he can effectively react. To do so, the battalion commander keeps his force in a position to maneuver immediately to the contact, gather and report information, and issue instructions.
The security force makes the initial contact. They must quickly determine the size and activity of the enemy force and avoid being fixed or destroyed--if possible, the security force avoids detection.
If the enemy is moving, the screening force determines the direction of movement and the size and composition of the force. The screening force forward observer (FO) places fire on the lead enemy companies. Speed of decision and execution is critical when the enemy is moving. When two forces converge, threat doctrine calls for his force to immediately conduct a hasty attack from the line of march and attempt envelopment.
If the enemy is stationary, the security force determines if enemy positions are prepared and reinforced by obstacles or minefields. The security force attempts to identify individual antitank weapon positions, and the enemy's flanks and gaps in his positions.
The advance guard quickly moves to overpower and destroy platoon-size and smaller security forces and combat outposts. Larger forces normally will require deployment of the main body. The advance guard protects the main body and allows the task force the freedom to maneuver by fixing larger than platoon-size enemy forces.
In developing the situation, the advance guard commander maintains pressure on the enemy by fire and maneuver. He probes and conducts a vigorous reconnaissance of the enemy's flanks to determine his exact location, composition, and disposition. The information gained by the security force and advance guard is used to develop a task force plan of action.
The task force commander has several action on contact options based on the enemy's situation and his mission.
Bypass.
If rapid forward movement is required, and if bypass of enemy forces has been authorized by the brigade commander, the task force can bypass. If the size and mobility of the bypassed force represents a threat, the enemy force must be fixed or contained until released by brigade follow-on forces or reserve.
Hasty ambush.
Ambush is effective against a moving force that is not aware of the presence of the task force. Instead of immediately opening fire, the advance guard (and possibly the entire task force) moves into hasty firing positions oriented on an engagement area. When most of the enemy formation is in the engagement area, the enemy is attacked by massed fires and maneuver.
Hasty attack.
Task force planning and standing operating procedure (SOP) reactions to contact define the criteria for conducting hasty attacks or for slowing the advance to prepare a deliberate attack. Preparations for a deliberate attack are initiated when the enemy is in strong, prepared positions with extensive obstacles, bypass is not authorized, and a hasty attack is not possible or has failed.
Defense.
The task force may defend after making contact with a stronger force or as a prelude to a deliberate attack. The task force defends initially from hasty positions, employing spoiling or counterattacks as possible to slow and disrupt the enemy advance.
HASTY ATTACK
The hasty attack is conducted either as a result of a meeting engagement or when bypass has not been authorized and the enemy force is in a vulnerable position. Hasty attacks are initiated and controlled with fragmentary orders (FRAGOs). There are two categories of hasty attack depending on the disposition of the enemy--an attack against a moving enemy force and an attack against a stationary enemy force.
Attack against a moving force.
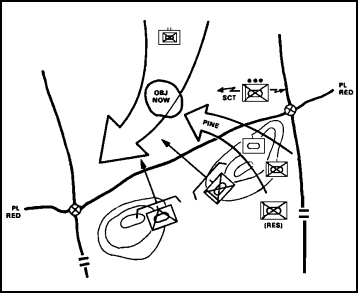
When two opposing forces converge, the side that wins is normally the one that acts fastest and maneuvers to positions of advantage against the opponent's flank. Task force contingency planning and SOP reactions to contact facilitate the execution of a hasty attack. The advance guard attacks or defends, depending on the size and disposition of the enemy force. The task force commander maneuvers trailing or adjacent teams against the enemy's flank or rear, while attacking by fire and interdicting enemy units attempting to do the same (Figure 9).
FIGURE 9. HASTY ATTACK AGAINST A MOVING ENEMY FORCE
Tanks normally lead the attack; BFVs and TOWs overwatch and support the maneuvering tanks by fire.
FASCAM, smoke, and other supporting fires may be used to disrupt enemy maneuver and cover that of the task force.
The scouts and advance guard provide initial information on the enemy force and develop the situation.
The lead company team defends from hasty positions to fix the enemy element.
A company team seizes high ground to provide overwatch and flank security.
The trail team(s) counterattacks the enemy flanks supported by field artillery, antiarmor company, and CAS.
Task organization is not changed.
Attack Against a Stationary Force.
A hasty attack against a stationary force (composed mainly of individual fighting positions and hasty protective obstacles) is initiated after scouts or lead company teams reconnoiter the enemy's positions to find flanks or gaps that can be exploited. This must be done quickly to gain the initiative. The task force coordinates maneuver elements and supporting fires to avoid a piecemeal commitment of combat power.
The task force commander coordinates the actions of his subordinates through FRAGOs and previously issued contingency plans and control measures. He clearly states the time, direction, and objectives of the attack. He develops the situation to find and secure or clear approaches to the enemy's flank or rear.
Dismounted infantry assaults supported by direct and indirect fires may be necessary to defeat the enemy. Tanks support by fire and begin their assault timed to arrive on the enemy position at the same time as the dismounted infantry. Dismounted infantry clears the position before resumption of mounted movement.
Integration of Combat, Combat Support, and Combat Service Support Elements.
Maneuver
- Scout platoon. During the hasty attack, the scout platoon quickly determines enemy locations and dispositions. It is then deployed to the battalion's most critical flank in a screen role, or beyond the objective to provide early warning of enemy reinforcement.
- Antiarmor company. Antiarmor platoons are deployed quickly to positions that provide overwatch to the main attack.
Fire support.
- Field artillery. Priority of support is to maneuvering elements.
- Mortars. Mortars are placed under the control of the FSO to provide general support to the battalion. Priority of support is to smoke operations to facilitate maneuver.
- Air Force. Immediate CAS is requested to support the battalion's main attack.
Intelligence.
GSRs are deployed to cover possible avenues of approach into the flank(s) of the attacking battalion.
Air defense artillery.
ADA assets move closely as possible to the attacking company team to provide protection from enemy air.
Mobility, countermobility, survivability,
- Engineers. During the hasty attack, engineers move with the lead company team to assist in breaching obstacles and provide mobility support to follow-on company teams.
- NBC. Chemical (nonpersistent) agents are planned to interdict threat counterattacking forces.
Combat service support.
- Combat trains. At the initiation of the hasty attack, the combat trains deploy to a location that will not interfere with the maneuver of battalion task force company teams, or the elements of follow-on units. The combat trains CP eavesdrops on the operation, anticipates logistical requirements, and prepares to "push" them forward.
Medical platoon.
The aid station establishes operations near an MSR or easily identifiable spot and prepares to triage and evacuate wounded.
DELIBERATE ATTACK
Task force deliberate attacks differ from the hasty attack to that they are characterized by precise planning based on detailed information, thorough preparation, and rehearsals. Deliberate attacks normally include large volumes of supporting fires, main and supporting attacks, and deception measures.
The tank or mechanized infantry battalion will normally conduct a deliberate attack as the main or supporting effort of a brigade attack, or as the brigade reserve.
A deliberate attack requires time for collecting and evaluating enemy information, reconnoitering, planning, and coordinating. The attack may be made from positions in contact or through a forward unit following a passage of lines. Attachments and task organization may be changed to fit the concept of operation. The commander must provide the necessary combat support for each company team and establish proper command and control relationships between units. The commander should designate support, breaching, and assault forces and position them in the attack formation for anticipated breaching operations.
Detailed plans for fire and maneuver are completed for an area that has been reconnoitered. Planning for actions beyond the limit of reconnaissance is less restrictive, with maneuver of forces and firepower planned in broader terms to provide flexibility and allow initiative.
Planning the deliberate attack.
- Adhere, as a minimum, to the 1/3 - 2/3 rule.
- Follow troop-leading procedures to use available time efficiently.
- Issue warning orders to initiate leader reconnaissance, movement, and subordinate unit planning and preparation.
- Conduct detailed reconnaissance and IPB to determine precise locations, orientations, dispositions, and intent of the enemy.
- Use a reverse planning process to develop detailed plans from the objective area back to the LD or assembly area.
- Designate a main attack.
- Task-organize maneuver units to support the main effort for each phase of the operation.
- Ensure that coordination and synchronization of maneuver, CS, and CSS assets is built into the plan and supports the main attack.
- Deliver the order from a vantage point that overlooks the terrain and ensure that the order contains a clear statement of mission and intent.
- Conduct rehearsals of the fire support plan and, to the extent possible, the movement plan.
- Conduct continuous reconnaissance and schedule a final intelligence update just before the attack.
TECHNIQUES FOR THE DELIBERATE ATTACK
The commander employs those techniques that will avoid striking the enemy's main strength. He uses deception to deceive the enemy as to the point of the main attack; he uses surprise to take advantage of his initiative in determining the time and place of his attacks; and he uses the indirect approach to strike the enemy on the flanks and rear.
Battalion task forces penetrate enemy company defenses to isolate and destroy elements of platoon size or smaller. The battalion task force completes the defeat of the enemy company in detail. Throughout the attack, the task force remains ready for enemy counterattacks and prepared to exploit success.
The coordinated attack is usually conducted in four phases. The task force will--
Close on the objective.
- Isolate the site for penetration.
- Breach or penetrate to gain a foothold into the position.
- Exploit the penetration.
- Close on the objective. The commander uses terrain or limited visibility or both to avoid enemy fires and to exploit weaknesses or gaps in the enemy defense. Envelopment is the preferred form of maneuver. When natural cover and concealment is unavailable, the commander uses smoke, suppression, and speed to minimize exposure to enemy weapons systems. Enemy "fire sacks" are avoided.
- Isolate the site for penetration. Regardless of the form of maneuver used to close on the objective, a penetration is usually required during the deliberate attack.
The commander masses overwhelming combat power at the point of initial penetration.
Artillery and mortar fires (including smoke) are used to suppress adjacent enemy positions and isolate the objective.
Overwatch is positioned where direct fire weapons can support the assault and prevent enemy reinforcement.
Envelopment is the preferred form of maneuver at every echelon. The enemy is attacked from a favorable direction based on his strength and orientation. Deliberate attacks are normally conducted against prepared defenses and require the infantry to dismount in the assault. The stronger the defenses, the more deliberate and methodical the attack and the greater the reliance on dismounted infantry.
- Breach or penetrate to gain a foothold.
Infantry dismounts outside the range of enemy direct fire weapons systems and moves forward by covered and concealed routes under the protective fires of tanks and BFVs positioned in overwatch.
The penetration of the enemy position is made on a narrow front. Bypass of obstacles is preferred to breach. The breach must lead to an exploitable weakness or gap in the enemy's defenses.
The infantry uses breaching and assault techniques similar to those used in the assault of a complex obstacle, and will reduce trench lines, bunkers, fortified positions, and the antitank weapons in them.
- Exploit the penetration.
Tanks will frequently follow the dismount elements and support from close overwatch. Tanks then move to exploit the initial breach as quickly as possible.
Bradleys use the long-range stabilized fire of the 25-mm gun and TOW to provide effective overwatch fires. Bradleys will leave overwatch when the antitank defenses are destroyed and assist in exploiting the breach and holding the shoulders of the penetration.
Reconnaissance elements use the penetration to reposition as required and obtain information on enemy positions in depth.
Reserves widen and deepen the penetration, and prepare to repulse counterattacks.
Once the objective is cleared, the mounted attack is continued to subsequent objectives or the task force begins consolidation and reorganization.
The battalion task force must integrate and coordinate combat, combat support, and combat service support to capitalize on them as combat multipliers.
Maneuver. Normally, the task force scheme of maneuver for a deliberate attack employs three elements: main attack, supporting attack, and reserve.
- Main attack. The mission of the main attack is to penetrate the enemy's defenses and secure the terrain to be seized. The main attack emphasizes the indirect approach.
- Supporting attack. The mission of the supporting attack is to fix or suppress an enemy force not being directly assaulted by the main attack. The supporting attack accomplishes its mission by emphasizing fire rather than maneuver. The fires of the supporting attack must be combined with indirect fires to achieve the maximum effectiveness.
- Reserve. The task force normally retains a reserve to complete the destruction of the enemy's position or to exploit the success of the attack. The reserve may be used initially to overwatch the main attack.
- Scout platoon. During the preparation for the deliberate attack, the primary mission of the platoon is reconnaissance missions to gather intelligence on enemy defensive locations, orientation, and dispositions. Zone reconnaissance missions to facilitate the movement of the main, supporting, and reserve units are a secondary mission. During the attack, the scout platoon's mission is to report enemy repositioning and counterattack. It prepares to screen to the front of the battalion task force upon consolidation of the objective.
- Antiarmor company. Antitank elements are normally positioned to provide overwatch and support-by-fire onto the objective and potential enemy counterattack routes.
- Fire Support.
- Field artillery. The task force commander employs field artillery to aid his company teams in moving forward. In the deliberate attack, preparation fires and/or series of targets are often planned and delivered on the objective in accordance with a predetermined time schedule. The commander plans fires to suppress, isolate, and blind the enemy forces in and about the axis of advance and objective area. These fires are both smoke and HE. In addition, short duration FASCAM is used to help isolate and impair the enemy's ability to counterattack.
- Mortars. Mortars move well forward with the main effort. Although they can provide HE suppression, their primary mission is smoke placed in front of the objective and between the task force and the enemy to conceal friendly movement and isolate the enemy by obscuring enemy weapon systems. Once on the objective, the mortars position to provide general support to the battalion task force defense.
- Air Force. Close air support missions are planned and flown at the request of the battalion task force. The number of sorties received is dependent on the number allocated by brigade. The deliberate attack planning process requires detailed planning, integration, and coordination of CAS with the battalion task force scheme of maneuver. Tank and artillery positions are the priorities of CAS in the deliberate attack.
- Air Defense Artillery. During the deliberate attack, ADA assets are positioned well forward to support the main effort. ADA coverage for the main effort is focused against likely air avenues of approach and concentrated at choke points and river crossing sites.
- Mobility, Countermobility, Survivability.
- Combat Service Support. The combat trains normally do not accompany the battalion task force during the deliberate attack. They remain in a location and readiness posture that allows them to move forward rapidly to planned locations from which to effect CSS upon consolidation on the objective.
- Mobility. Normally, reconnaissance is done by troops who are to breach obstacles, accompanied by an engineer who will assist in the assessment of obstacles. Engineer elements are employed well forward with the main attack to enhance mobility. They accompany the breaching force and assist in reduction and crossing of obstacles encountered. In the deliberate attack, stealthy prebreach of obstacles by engineers or dismounted infantry is a preferred technique.
- Countermobility. Short duration FASCAM can be planned behind an enemy unit to seal withdrawal routes or counterattack routes.
EXPLOITATION
The exploitation is conducted to take advantage of success in battle. Exploitation prevents the enemy from reconstituting an organized defense or conducting an orderly withdrawal. It may follow any successful attack. The task force normally participates in the exploitation as part of a larger force. The keys to successful exploitation are speed in execution and maintaining direct pressure on the enemy.
Opportunities for exploitation are indicated by-
- An increase in the number of enemy prisoners.
- An increase in abandoned materiel.
- The overrunning of artillery, command facilities, signal installations, and supply dumps.
- A decrease in enemy resistance.
- A breakdown in enemy command and control as evidenced by confusion and a loss of cohesion.
Exploiting force missions include--
- Securing objectives deep in the enemy rear.
- Cutting lines of communication.
- Surrounding and destroying enemy units.
- Denying escape routes to an encircled force.
- Destroying enemy reserves, CS, and CSS units and assets.
The task force conducting an exploitation moves rapidly to the enemy's rear area using movement to contact techniques, avoiding or bypassing enemy combat units, and destroying lightly defended and undefended enemy installations and activities. Bypassed enemy forces are reported to brigade headquarters for destruction by followand-support forces. The task force is usually assigned an objective deep in the enemy rear based on the higher commander's intent. This objective may be one that will contribute significantly to the destruction of organized resistance or one for orientation and control.
- If the mission is to seize or secure a deep objective, the task force avoids engagements and moves to the objective as quickly as possible.
- If the objective is assigned for orientation and control, the task force seeks targets anywhere in its zone of action or along its axis of advance. In this case, the exploitation is executed as a tank sweep.
The exploitation continues day and night for as long as the opportunity permits. The initial plan must ensure that adequate stocks of fuel, spare parts, ammunition, protective clothing, decontaminants, medical supplies, and food are available to the task force. The momentum of the exploitation must not be slowed because of lack of support. Aerial resupply may be requested during the exploitation.
PURSUIT
The pursuit normally follows a successful exploitation. It differs from an exploitation in that a pursuit is oriented primarily on the enemy force rather than on terrain objectives. While a terrain objective may be designated, the enemy force is the primary objective. The purpose of the pursuit is to run the enemy down and destroy him.
The task force participates in the pursuit as part of a larger force. The pursuit is conducted using a direct-pressure force, an encircling force, and a follow-and-support force. The task force may comprise or be part of any of these forces.
- The direct-pressure force denies the enemy units the opportunity to rest, regroup, or resupply by repeated hasty attacks to force them to defend without support or to stay on the move. The direct-pressure force envelops, cuts off, destroys, and harasses enemy elements.
- The encircling force moves with all possible speed to get in the enemy rear, block his escape, and, with the direct-pressure force, destroy him. The enveloping force advances along routes parallel to the enemy's line of retreat to establish positions ahead of the enemy main force.
- The follow-and-support force is organized to destroy bypassed enemy units, relieve directpressure force elements, secure lines of communication, secure key terrain, or guard prisoners or key installations.
Engineers in exploitation and pursuit operations should be well forward in the columns to aid the movement of the force. Breaching equipment must be well forward in anticipation of encountering and breaching destroyed bridges, road craters, abatis, and interdiction mining.
This concludes this learning event. You should now be familiar with the types and characteristics of tactical offensive operations. This includes the methods for movement to contact and the attacks that can be initiated against the enemy. You should also be familiar with the methods to continue an attack by exploitation and/or pursuit of the enemy force.
The next learning event will introduce you to the considerations and techniques for planning, preparing, and conducting offensive operations.
Learning Event 2:
IDENTIFY THE CONSIDERATIONS AND TECHNIQUES FOR PLANNING, PREPARING, AND CONDUCTING ATTACKS
When a commander of a force receives an offensive mission, he immediately issues a warning order to alert his subordinate elements. He must then plan and prepare for the attack. First, he must make an estimate of the situation and identify the objectives. Then he considers the tasks required to gain the objectives. And finally, he must issue the attack order. Only with proper planning, preparation, and conduct of the attack will the commander be able to control the area or defeat the enemy.
This learning event will introduce you to the significant aspects of offensive operations; aspects that must be considered to properly plan, prepare for, and conduct an attack.
CONSIDERATIONS IN PLANNING THE ATTACK
As the commander makes his estimate of the situation, he must consider various factors vital to the success of the mission. Factors that he should consider are:
- Mission.
- Enemy.
- Terrain and weather.
- Troops.
- Time.
Each of these factors will be discussed in detail in the following paragraphs.
Mission
Offensive operations should allow subordinate commanders the greatest possible freedom. Whenever possible, subordinate elements should be assigned an objective and zone without further restrictions. Some operations require greater control and coordination. In these cases, it may be necessary to give the subordinate elements more detailed orders for the attack.
In all cases, commanders need to anticipate likely developments during an attack. They must bear their superior's mission and intentions and make preparations to continue beyond their objectives.
Enemy
The commander must also consider the dispositions, equipment, doctrine, capability, and probable intentions of the enemy. Because of the strength of established defenses, commanders should aggressively seek gaps or weak points in the enemy's defenses. Commanders plan to penetrate enemy security area, overcome obstacles, avoid the strengths of established defenses, and destroy the coherence of the defenses. This requires an active intelligence collection. Enemy reserves must be identified and located. Air defenses and air capabilities are a vital part of the intelligence estimate.
Terrain and Weather
Attacking commanders should select avenues of approach that:
- Permits rapid advance.
- Allows for maneuver by the attacking force.
- Provides cover and concealment.
- Permits lateral shifting of reserves.
- Allows for good communication.
- Resists obstruction by enemy obstacles.
- Orient on key terrain.
Weather conditions that affect mobility, concealment, and air support should be exploited when possible.
Battalion task forces and company teams advance from one covered and concealed position to the next. To sustain momentum, tanks and mechanized task forces must move forward; so must field and air defense artillery, engineers, and combat service support units.
Terrain chosen for the main effort should allow rapid movement into the enemy's rear area; however, an initial maneuver over difficult terrain may be desirable if the enemy can be surprised. Commanders should reconnoiter the terrain where the main effort is to be conducted. Special attention should be given to obstacles. The commander must plan to negotiate or avoid urban areas, rivers, extreme slopes, thick forests, or soft ground between their units and their objective. Such terrain when parallel to the axis of advance can be used to protect the attacker's own flanks. Key terrain along the axis of advance must be either seized or controlled by fire. When present, decisive terrain becomes the focal point of the attack. Weather and visibility conditions can have significant effects on offensive operations. Ground conditions will increase or reduce the number of avenues available for maneuver and will affect speed of movement for all forces.
Troops
Dismounted infantry opens approaches for armor and mechanized forces by attacking through heavy cover or by penetrating antiarmor defenses. Air assault or airborne units can seize objectives in depth to block enemy reserves or secure choke points. Armor units move rapidly through gaps to disorganize the defense in depth. Field and air defense artillery, and engineers all perform critical functions and must be used to support all elements of the attacking force. Aviation units must engage the full range of enemy ground targets.
Time
Commanders should remember the warning of Clausewitz's: "Time not used by the attacker benefits the defender." Offensive actions become harder to conduct as the defender organizes the ground and brings up more troops. Nonetheless, the attacker must take the time necessary to synchronize and to concentrate all available combat power for the attack.
General Patton, who stressed the efficient use of time in all his operations, carefully distinguished haste from speed.
"Haste exits," he wrote, "when troops are committed without proper reconnaissance, without the arrangement for proper supporting fire, and before every available man has been brought up. The result of such an attack will be to get the troops into action early, but to complete the action very slowly. "Speed is acquired by making the necessary reconnaissance, providing the proper artillery and other tactical support, including air support, bringing up every man and then launching the attack with a predetermined plan so that the time under fire will be reduced to the minimum. At the battalion level four hours spent in preparation for an attack will probably ensure the time spent under fire not exceeding thirty minutes. One hour spent in...preparation...will most certainly ensure time under fire lasting many hours with bloody casualties."
Once an attack is underway, time remains critical. The attack can succeed only if it achieves its objective before the enemy recovers his balance, identifies the threat, and masses forces and fires against it. Time is therefore vital to the attacker; he must prolong the enemy's surprise, confusion, and disorganization for as long as possible.
PLANNING FOR ATTACKS
Commanders use mission orders to describe the overall mission of the force, their own intent, the concept of operation and the missions of their subordinate units. Commanders should minimize restrictions they impose on the freedom of action of subordinates. Commanders should consider the factors discussed below when planning for attacks.
Situation and Available Resources
In designating objectives, the commander must consider the mission, the enemy's situation (including enemy dispositions in depth), troops available and their combat effectiveness, the terrain, the weather, and the time-space relationships.
After selecting his objectives, he develops the scheme of maneuver, allocates available forces, and plans for fire support, combat support, and combat service support.
Plan the Scheme of Maneuver
The scheme of maneuver seeks to gain an advantage of position over the enemy, to close with him rapidly, to overrun him if possible, and to destroy his ability to resist. The commander determines the specific form of maneuver or the combination of forms as part of his estimate of the situation. He selects a scheme of maneuver that facilitates seizing the objective rapidly and positioning the force for subsequent operations.
Surprise, attacking the enemy weakness, and exploitation of the enemy are desirable characteristics of any scheme of maneuver.
Surprise the Enemy.
Surprise and an indirect approach are desirable characteristics of any scheme of maneuver. When a geographically indirect approach is not available, the commander can achieve a similar effect by doing the unexpected--striking earlier, in greater force, with unexpected weapons, or at an unlikely place.
Attack the Enemy's Weakness.
Commanders concentrate attacking forces against enemy weaknesses. The commander can weigh the main attack by positioning reserves, by assigning a narrower zone to the main attack force, by assigning priority of fires to the main attack, or by a combination of all these. The main attack normally receives priority of effort from close air support, attack helicopters, combat engineers, electronic warfare (EW), combat service support (CSS), and nuclear, chemical, biological (NBC) and defense units.
Exploitation of the Enemy.
The scheme of maneuver identifies where the main effort is to be made. All of the force's available resources must operate in concert to assure the success of the main effort.
However, commanders must avoid becoming so committed to the initial main effort that they neglect other opportunities. The commander selects a scheme of maneuver that facilitates positioning for subsequent operations. The plan of attack must also contain provisions for exploiting success whenever it occurs. Commanders must plan to overcome the enemy's resistance completely and to exploit successes relentlessly. The plan should facilitate rapid dispersal of concentrated units and the introduction of fresh forces to support exploitation whenever necessary.
Plan the Use of Available Forces and Combat Support
In addition to the main attack force, you must develop plans for the use of fire support, combat support, and combat service support units. The units may assist the attacking force by providing direct and indirect fire, rear area operations, and forward area assistance.
Rear Operations.
Rear operations are of concern in all division and corps level offensive operations. They are of particular concern to divisions and larger units, which must allocate forces and other resources to maintain freedom of action and continuity of operations during and following an attack. Lines of communication, reserves, and displacing support elements are the logical targets of the enemy's own deep operations.
Deep Operations.
Deep operations must be synchronized with the scheme of maneuver. Deep operations support tactical offensive operations by isolating the battlefield from reinforcing or counterattacking enemy reserves; disrupting the enemy's combined arms cooperation and operational command and control; and destroying or degrading his sustaining support. Enemy reserves, fire support elements, command and control facilities, and other high value assets beyond the line of contact are potential targets for attack. The primary tools for deep operations are:
- Tactical air support.
- Long-range artillery.
- Attack helicopter units.
- Electronic warfare systems.
- Special forces.
- Ranger units.
- Air assault units.
- Airborne units.
- Armored and mechanized units.
Separately, or in combination, these means can block the reinforcement of the enemy defenses. They can also protect the attacking force against counterattack and disorganize enemy fire support, air defense, and logistic support.
Combat Support.
Commanders develop a fire support plan that assists and complements the maneuver plan. The fire support plan provides fires in direct support of committed maneuver elements and in general support of the entire force. The commander can influence the action by shifting air, artillery, engineer, and EW assets during the attack.
When authorized for use in the attack, nuclear or chemical weapons employment may permit small forces attacking at high speeds to achieve the same success as larger forces supported with conventional fires. Nuclear or chemical fires may so reduce the enemy's strength that multiple, simultaneous attacks are possible.
Reserve Forces.
The reserve is the commander's principal means of influencing the action decisively once the operation is under way. The reserve reinforces success in the attack or maintains attack momentum.
PREPARING FOR ATTACKS
Time is essential and must be carefully managed. Commanders should use no more than one-third of the available preparation time for planning and issuing orders. Subordinates must be given time to conduct necessary reconnaissance and coordination and to follow troop-leading procedures throughout the force. Warning orders are vital in preparing attacks.
Attack Orders
Attack orders embody the commander's intent and concept of operation. They include measures for coordinating and controlling operations. Control measures describe and illustrate the concept, maintain separation of forces, concentrate efforts, assist the commander in the command and control of his forces and add flexibility to the maneuver plan. As a minimum, they include a line of departure, a time of attack, and an objective. In addition they may assign zones of action, axes of advance, directions of attack, routes, phase lines, checkpoints, and fire control measures. Such control measures support the commander's concept and allow maximum freedom of action for subordinate commanders.
Whenever possible, commanders should issue face-to-face orders. Subordinate commanders must know what the command as a whole is expected to do, what is expected of them, and what adjacent and supporting commanders are expected to do. Subordinate commanders and staffs must have pertinent information and as much time as possible to prepare their plans.
Coordination with Combat Support and Combat Service Support
Coordination begins immediately on receipt of a mission and is continuous throughout the operation. When time allows, the commander and his staff should review plans of subordinates, giving additional guidance as needed to ensure an overall coordinated effort.
Commanders must integrate support plans with tactical plans during their preparations for offensive operations. They must also ensure that their CSS operators are kept fully informed during the battle.
In the offense, CSS facilities should be positioned as close as possible to the tactical units they support. Only CSS elements that provide essential support (trucks with ammunition and petroleum, oil, and lubricants (POL), for example) should move forward just prior to the attack. If possible, these movements should take place at night.
When the plan calls for the attacking unit to pass through a defending unit, CSS planners should seek assistance from the defending unit.
Prior to the attack, units move rapidly into attack positions. This movement must be thoroughly coordinated and planned in detail to avoid confusion and delay. Concentration of the force should take place quickly and should make maximum use of cover and concealment, signal security, and deception. Actions that would alert the enemy to the coming attack must be avoided or masked to preserve surprise.
The attacking force organizes to cope with the environment to attack across obstacles and rivers, during snow or rain, at night, or to exploit nuclear or chemical strikes. Engineers, nuclear, chemical, and biological reconnaissance units, and air defense artillery and aviation assets must be employed to support maneuver throughout the attack.
CONDUCTING ATTACKS
Both attack and exploitation often begin with a forward passage of lines, an operation in which one friendly unit moves forward through positions held by another. Such a passage must be well coordinated to ensure minimum congestion and confusion. When possible, passage should be through elements that are not in contact.
Forward Passage of Lines
Specific details of the forward passage are coordinated between the respective subordinate unit commanders. Normally, the overall commander assigns boundaries to designate areas through which subordinate elements will move. Such boundaries usually correspond to those of the passed force. The passed force mans contact and passage points. It also provides information pertaining to the enemy, minefields, and obstacles; and it provides guides to assist the passing unit.
To ensure continuous support without increasing battlefield clutter, the passed unit may provide the passing unit initial logistical support. Once started, the passage is completed as quickly as possible to minimize the vulnerability of the two forces. The passing force must assume control of the battle as soon as its lead elements have moved through the passed force. Artillery supporting the passed force and its own direct fires should be integrated into the fire support plan of the passing unit.
Support of the Attacking Force
To support the assault, a coordinated effort is required to suppress enemy field artillery, air defense, radio electronic combat means, and command and control systems. The enemy forces in depth that pose the greatest threat to the attacking force are his reserves, nuclear and chemical capability, fire support units, and the enemy's command and control system.
These enemy forces in depth are dealt with as follows:
- Jamming by combat electronic warfare intelligence units.
- Attacks by artillery or air.
- Blocked by other maneuver forces during the assault.
Conduct of the Attack
Commanders concentrate all available firepower on the defender's positions at the beginning of the assault. As attacking troops begin their assault, these fires are then shifted to targets beyond the objective. Dismounted assault forces should move as close behind their own fires as possible. Armored forces should assault under overhead artillery fire.
Initiation of the Attack.
The attack must be violent and rapid to shock the enemy and to prevent his recovery before the defense has been destroyed. The attacker must minimize his exposure to enemy fires by using maneuver and counterfire, avoiding obstacles, and maintaining security. The attacker must maintain command and control, and remain organized for the fight on the objective.
Culmination of the Attack.
The attack culminates in a powerful and violent assault on the objective. The purpose of the assault is to destroy an enemy force or to seize the ground it has occupied. Synchronized fires, maneuver, and combat support are imperative to achieve superior combat power at the point of the assault. Artillery preparation, suppressive fires, isolation of the enemy force, concentration of combat power, and overrunning the enemy all combine to destroy the defending force.
Reaching the Objective.
As the attacker reaches his objective, he must overcome enemy resistance with violent concentrated firepower and a rapid advance. Speed during this phase of the attack is essential to reduce casualties and to avoid becoming stalled in the enemy's fields of fire. The assault must move completely across the objective. Fortified positions on the objective are then attacked from the flank, or rear, after the assaulting force has passed around them.
Maintaining Control.
When a hasty attack fails and a commander decides to resort to a deliberate attack, he must ensure that the force does not become disorganized or vulnerable to conventional counterattack or nuclear and chemical attack during the preparatory period. Positive command and control is imperative. Portions of the force must take up hasty defense positions; other parts of the force are directed to assembly areas. Rapid dispersal is essential, but it must be orderly enough to allow attack to continue after the briefest possible period of reorganization, consolidation, planning, and coordination.
Exploitation.
The exploitation follows immediately either by continuing the attack with the same force or by passing another force through. Infantry attacks on fortified defenses are normally exploited by armor and mechanized forces.
OTHER TACTICAL CONSIDERATIONS
Other tactical factors which commanders must consider include:
- Flank security.
- Smoke operations.
- Protection from air attack.
- Breaching obstacles.
- River crossing operations.
- Attacks during limited visibility.
Flank Security
The attacking force should ignore the threat to its flanks. This threat increases as the attack progresses. Responsibility for flank security must be assigned to attacking units or to designated security forces. To maintain forward momentum, it may be necessary to dispense temporarily with flank protection. The speed of attack itself offers a degree of security, because it makes defensive reactions less effective.
Obstacles overwatched by air or ground cavalry or other security forces can improve flank security. When flank obstacles are emplaced, the commander should be mindful of how they affect both his own maneuver options and those units following his.
Smoke Operations
During offensive operations, smoke may be used to degrade enemy observation. Place smoke on or near enemy positions to blind gunners and observers. Deliver smoke between friendly and enemy forces to screen friendly maneuvers. Use care to ensure that smoke does not impair the effectiveness of the friendly forces.
You may also use smoke to deceive the enemy as to your intentions. For example, use smoke to attract the enemy's attention to one part of the battlefield, while friendly units attack from another.
Protection from Air Attack
Attacking forces are highly vulnerable to enemy air attack. If the enemy dominates the air, attacks will have to use concealment carefully. In that event, cloud cover or limited visibility conditions, in conjunction with well-planned, ground based air defense efforts are a great advantage to an attack.
In a rapid attack, air defense units must seek aggressive control over the airspace from which the attack can be threatened. While short-range air defense (SHORAD) units provide close-in protection of critical assets such as command and control nodes, artillery, and key mobility features (bridges and defiles, for example), high-to-medium altitude air defense (HIMAD) assets must be repositioned to reach out and destroy enemy aircraft before they enter the zone of the attack.
Breaching Obstacles
The attacker should expect to encounter obstacles when facing an organized defense. Natural obstacles should be bypassed, breached, or crossed with the assistance of engineer units in support of the attack.
An attacking force should bypass obstacles whenever possible. If these obstacles cannot be bypassed, they should be breached at once.
Assault breaches usually occur under enemy fire. The assault force usually has little time for reconnaissance. When possible, combat engineers moving with the leading companies perform the breach while tanks and infantry overwatch. Because engineers cannot be everywhere, all units must be trained, organized, and equipped to conduct hasty breaches of minefields and other obstacles. In an assault breach, rapid breaching devices clear lanes to the minimum width necessary to allow combat forces to continue the advance.
Combat engineers may conduct a deliberate breach if time permits detailed reconnaissance and planning. Normally, in a deliberate breach, they will clear obstacles completely.
River Crossing Operations
Commanders plan to quickly cross rivers and streams in the path of their advance. A river crossing requires special planning and support. The size of the obstacle and the enemy situation will dictate how to make the crossing. Regardless of how the river is to be crossed, attackers try to do so without losing momentum. Only as a last resort should an attacking force pause to build up forces and equipment.
Attacks During Limited Visibility
Darkness and other periods of limited visibility offer great advantages to the attacker. Attacks may be conducted at such times:
- To achieve surprise.
- To exploit success.
- To maintain momentum.
- To rupture strong enemy defenses.
- To offset enemy air superiority.
Night combat has become increasingly feasible and effective due to the development of improved night vision devices. Because it lights the battlefield for both sides, artificial illumination should be used only when night vision devices are not available in sufficient quantities, or when ambient light levels are very low.
When ambient light levels are high, passive night vision devices will overcome many of the limiting effects of darkness. However, limited visibility will still reduce detection and engagement ranges, the length of bounds, and the ability to move on covered and concealed routes.
Snow, rain, fog, or smoke present special problems in navigation, target acquisition, and identification. Special training, use of appropriate sensors, and careful planning can overcome these difficulties.
Night attacks against strongly defended positions should cover relatively short distances. Leaders at all levels should have the opportunity to reconnoiter the area of the attack as far forward as possible during good visibility. Wire will often be the primary means of communication until the assault begins or surprise is lost. Visual aids for recognition may assist in control of forces. Objectives will usually be smaller than normal, but they must be of sufficient prominence to ensure easy location.
You should now be familiar with the factors which must be considered when planning, preparing, and conducting an attack. In the next learning event, you will become familiar with the types, characteristics, and planning considerations for special purpose operations.
Learning Event 3:
IDENTIFY THE TYPES AND CHARACTERISTICS OF AND PLANNING CONSIDERATIONS FOR SPECIAL PURPOSE OPERATIONS
The material presented up to this point pertains to all types of offensive operations. There is, however, an additional category known as special operations. Special purpose operations have special planning considerations which will now be discussed.
Special operations include:
- Reconnaissance in force.
- Attacks from a defensive posture.
- Counterattacks.
- Diversionary operations.
- Offensive reliefs.
- Raids.
Each type of special purpose operation will be discussed in detail in the following paragraphs.
Reconnaissance in Force
Reconnaissance in force is a limited objective operation by a considerable force. It is used to obtain information and to locate and test enemy dispositions, strengths, and reactions. Even when the commander is executing a reconnaissance in force primarily to gather information, he must be alert to seize any opportunity to exploit tactical success. If the enemy's situation must be developed along a broad front, the reconnaissance in force may consist of strong probing actions to determine the enemy situation at selected points. The enemy's reactions may reveal weaknesses in his defensive system. Because reconnaissance in force is primarily an information-gathering operation, commanders must carefully evaluate the risks involved. They must make advance provisions either to extricate the force or to exploit success.
Attacks from a Defensive posture
Attacks from a defensive posture include spoiling attacks and counterattacks. Spoiling attacks are mounted to disrupt an expected enemy attack before it is launched. A spoiling attack attempts to strike the enemy while he is most vulnerable,during his preparations for the attack in assembly areas, attack positions, or on the move prior to crossing his line of departure. In most respects, a spoiling attack is conducted like any other attack and may be either hasty or deliberate. Frequently, the circumstances in which it is conducted will preclude full exploitation, and the attacking force will either halt on its objective or withdraw to its original position. When the situation permits, a spoiling attack should be exploited as in any other attack.
Counterattacks
Counterattacks can be conducted by either a reserve or by lightly committed forward elements. They are conducted to defeat an attack after it has been launched, the enemy's main effort identified, and an assailable flank created. Counterattacks are conducted like other attacks, but because they must be synchronized with the overall defensive effort, their timing is especially important. Like spoiling attacks, counterattacks usually revert to a defensive posture after local exploitation rather than to full exploitation and pursuit. In some cases, the counterattack may be the first step in reverting to offensive operations by the larger defending force. Counterattacks may also be more limited "counterattacks by fire." These are tactical level actions which consist of positioning a force where advantageous flanking or rear fires may be brought against the enemy. Enemy positions are not assaulted.
Diversionary Operations
Diversionary operations include feints and demonstrations. A feint is a supporting attack designed to divert the enemy's attention from the main effort. It is normally executed by brigades and smaller units.
Feints are usually shallow, limited-objective attacks conducted before or during the main attack. A demonstration is a show of force in an area where a decision is not sought. A demonstration threatens attack, but does not intentionally make contact with the enemy.
Offensive Relief
An offensive relief is conducted to pass fresh troops into the attack in order to maintain offensive momentum. Such reliefs are most common as the force enters the exploitation or pursuit. However, relief may also be necessary during the attack itself if previously committed units have suffered such severe losses that they are unable to reach their objectives. Offensive reliefs may be conducted as reliefs in place, but ideally are conducted without a significant pause in offensive tempo.
Raid
A raid is a limited objective attack into enemy territory for a specific purpose other than gaining and holding ground. Raids are typically conducted to destroy key enemy installations and facilities, capture or free prisoners, or disrupt enemy command and control or support functions. The raiding force always withdraws from the objective area after completing its mission and, unless it is a stay-behind unit, will normally recover to friendly lines.
CONCLUSION
This concludes this subcourse on Offensive Tactical Doctrine, Part I. This subcourse has familiarized you with the tactical doctrine pertaining to the offense. It has presented both the fundamentals of offensive operations and the procedures for conducting an offense.
If you have any questions relating to the material presented, go back and review the text now. When you are ready, take the practice exercise.
GO TO: