|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
PLANNING CONSIDERATIONS
Critical Task: B-100-000
OVERVIEW
LESSON DESCRIPTION:
This lesson addresses staff planning, techniques, and procedures that support armored battalion/TF planning for the deliberate attack. It also addresses engineer considerations in support of armored battalion/TF attack planning and execution.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | You will identify the planning considerations for an armored battalion/TF deliberate attack and the fundamentals of the deliberate attack. You will also identify the key functions of the engineer battalion commander and his staff and the combat-engineer company commander during the planning and execution of the deliberate attack. Finally, you will identify how and why engineer assets are apportioned to armored battalions/TFs. |
| CONDITION: | You will use the materials contained in this lesson. |
| STANDARD: | You will correctly answer all questions on the practice exercise at the end of the lesson. |
| REFERENCES: | The materials contained in this lesson were derived from FM 5-34, FM 5-100, FM 71-100, FM 100-5, FM 5-71-100, ST 100-9, and other materials approved by the US Army Engineer School.
Refer also to Appendix C (extract pages 3-19 through 3-54 from FM 71-2). |
The objective of offensive operations is to break through the enemy's main defensive zone and into the rear area to destroy artillery positions, command posts, logistics support areas, ADA positions, and lines of communication. Friendly forces sometimes encounter a well-prepared enemy defensive position that cannot be eliminated with a hasty attack.
When this happens, the entire force will pause and take sufficient time to prepare for and conduct a deliberate attack.
Major changes are taking place in the engineering community that affect the capability of combat engineers to support the combined-arms team during offensive operations. Changes under the divisional engineer structure include improved C2, improved logistics organization, and an experienced engineer commander at almost every maneuver command level. Army operations doctrine emphasizes offensive operations as the key to victory. Force mobility is the key to quick and decisive offensive operations, and combat engineers must understand how to enhance the overall mobility of the force.
PLANNING OFFENSIVE OPERATIONS
2-1. Considerations. Offensive operations include hasty attacks, deliberate attacks, and variations of both. Appendix C covers the various types of offensive operations, but this lesson will focus on deliberate attacks. A deliberate attack requires time for collecting and evaluating enemy information, reconnoitering, planning, and coordinating. The attack may be made from positions in contact or through a forward unit following a passage of lines. Task organization may be changed to fit the concept of operation. The commander must provide the necessary CS for each CO/TM and establish proper C2 relationships between units. The commander should designate support, breaching, and assault forces and position them in the attack formation for anticipated breaching operations.
In planning a deliberate attack, the commander and staff follow these principles of C2:
- Adhere to the 1/3 - 2/3 rule. Commanders should use only one-third of the time available for planning and allow two-thirds of the time for preparation.
- Follow troop-leading procedures to use available time efficiently.
- Issue warning orders to initiate reconnaissance, movement, and subordinate-unit planning and preparation.
- Conduct detailed reconnaissance and IPB to determine the precise location, orientation, disposition, and intent of the enemy.
- Use a reverse-planning process to develop detailed plans from the objective area back to the line of departure (LD) or the assembly area.
- Designate a main attack.
- Task-organize maneuver units to support the main effort for each phase of the operation.
- Ensure that coordination and synchronization of maneuver, CS, and CSS assets are built into the plan and support the main attack.
- Deliver the order from a vantage point that overlooks the terrain of the operation and ensure that the order contains a clear statement of the mission and the intent.
- Conduct rehearsals of the fire-support plan and, to the extent possible, practice the movement plan.
- Conduct continuous reconnaissance and schedule a final intelligence update just before the attack.
2-2. Concept of the Attack. A simple, complete concept of operations is the basis of all tactical offensive actions. The concept should permit rapid transition between offensive phases. Corps and divisions make use of five complementary elements in fighting their offensive battles:
- A main attack with supporting attacks as required.
- Reserve operations in support of the attack.
- A reconnaissance and security operation forward and to the flanks and rear of main and supporting attacks.
- A continuous deep operation in vital parts of the zone of attack.
- Rear-area operations needed to maintain offensive momentum. While some deep and rear-area activities conducted by higher echelons affect (and must therefore be coordinated with) brigade and subordinate units, the latter normally do not conduct separate deep and rear-area operations. These rear echelons, however, seek and anticipate uncommitted enemy forces that could affect mission accomplishment. They also provide all-around security, to include protection of logistics trains in the rear area.
![]() a. Close operations. The commander organizes elements of the offensive framework for complementary functions in conducting his attack. In the close operation, reconnaissance and security forces (covering forces and advance, flank, or rear guards) locate the enemy and find gaps in his defenses, protect the friendly force from surprise, develop the situation, and give the commander time and space in which to react to the enemy (see Figure 2-1). The main and supporting efforts maneuver around or through enemy defenses to occupy objectives that permit the defeat of defending forces.
a. Close operations. The commander organizes elements of the offensive framework for complementary functions in conducting his attack. In the close operation, reconnaissance and security forces (covering forces and advance, flank, or rear guards) locate the enemy and find gaps in his defenses, protect the friendly force from surprise, develop the situation, and give the commander time and space in which to react to the enemy (see Figure 2-1). The main and supporting efforts maneuver around or through enemy defenses to occupy objectives that permit the defeat of defending forces.
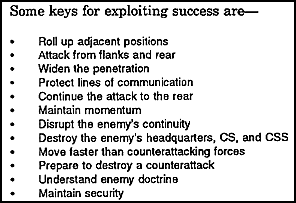
Figure 2-1. Exploiting success
![]() b. Deep operations. Deep operations isolate enemy defenses, disorganize enemy reserves, disrupt enemy support, and complicate the reconstitution of the defense during withdrawal.
b. Deep operations. Deep operations isolate enemy defenses, disorganize enemy reserves, disrupt enemy support, and complicate the reconstitution of the defense during withdrawal.
![]() c. Rear-area operations. Rear-area operations ensure freedom of action for committed and uncommitted forces and protect needed CS and CSS support from disruption.
c. Rear-area operations. Rear-area operations ensure freedom of action for committed and uncommitted forces and protect needed CS and CSS support from disruption.
2-3. Deliberate-Attack Mission Planning. In contrast to hasty attacks, deliberate attacks are fully synchronized operations that employ every available asset against the enemy's defense. Because such synchronization requires careful planning and extensive coordination, deliberate attacks take time to prepare. During this time, the enemy can improve his defenses, disengage, or launch a spoiling attack of his own. Therefore, deliberate attacks should be reserved for those situations where the defense can neither be outflanked nor overcome with a hasty attack.
Whether hasty or deliberate, a successful attack depends on concentrating the maximum possible shock and violence against the enemy force. The objective is to shatter the enemy's nerve, ruin his combined-arms synchronization, and destroy his unit's cohesion and the willingness of his soldiers to fight. The most successful attacks leave defending units incapable of further resistance. Deliberate attacks normally include large volumes of supporting fires, main and supporting attacks, and deception measures. Detailed information about the enemy must be collected from higher, lower, and adjacent units through patrolling, reconnaissance by fire, aerial photographs, prisoners, line-crossers, electronic warfare, radar, sensors, and other means.
![]() a. Preparation. Detailed information about terrain can be collected from many of the same sources as that about the enemy. Leaders at all levels should look at the actual terrain in daylight. If the attack is to be conducted at night, they should also look at the terrain at night. The likelihood that terrain can be seen or reconnoitered in detail more than a few kilometers into enemy territory is remote. Detailed planning of maneuver and fires will usually be restricted. Planning for subsequent actions will normally be more general. For example, the maneuver of forces and fires may be stated in broad terms, and units may simply receive orders to prepare to exploit success.
a. Preparation. Detailed information about terrain can be collected from many of the same sources as that about the enemy. Leaders at all levels should look at the actual terrain in daylight. If the attack is to be conducted at night, they should also look at the terrain at night. The likelihood that terrain can be seen or reconnoitered in detail more than a few kilometers into enemy territory is remote. Detailed planning of maneuver and fires will usually be restricted. Planning for subsequent actions will normally be more general. For example, the maneuver of forces and fires may be stated in broad terms, and units may simply receive orders to prepare to exploit success.
Bringing subordinate commanders together to issue the order is an important advantage that is not usually available in a hasty attack. The operation must be explained in detail so that there are no doubts about who is to do what and when it is to be done.
If the order is issued at a forward location, the battalion/TF commander indicates points of interest on the ground as well as on the map. With all commanders present, coordination among CO/TMs is started immediately and is often completed before they disperse.
The battalion/TF commander and staff supervise preparation and execution of the plan. The commander and selected assistants must be well forward in the attack so as to exercise control. Success of the operation depends on the commander's immediate reaction to the situation as it develops. He must literally see in order to effectively suppress and move.
![]() b. Time. Time is the biggest difference between hasty and deliberate attacks. For a deliberate attack, time must be made available for the collection and evaluation of enemy information, reconnaissance, planning, and coordination. The battalion/TF may itself be reorganized and will often change internal organization to optimize each force for the task it will be assigned. New units may be attached to or placed in support of the battalion/TF or subordinate units. Time must be available to thoroughly familiarize replacements with the situation, mission, SOPs, and signal operation instructions (SOI). Time is used for careful assignment and coordination of missions of tank, mechanized infantry, attack helicopter, artillery, antitank (AT), mortar, engineer, bridging, surveillance, air defense, maintenance, medical, supply, and signal assets. Each contributes to the commander’s ability to see, suppress, and move. Each must be used to the best advantage.
b. Time. Time is the biggest difference between hasty and deliberate attacks. For a deliberate attack, time must be made available for the collection and evaluation of enemy information, reconnaissance, planning, and coordination. The battalion/TF may itself be reorganized and will often change internal organization to optimize each force for the task it will be assigned. New units may be attached to or placed in support of the battalion/TF or subordinate units. Time must be available to thoroughly familiarize replacements with the situation, mission, SOPs, and signal operation instructions (SOI). Time is used for careful assignment and coordination of missions of tank, mechanized infantry, attack helicopter, artillery, antitank (AT), mortar, engineer, bridging, surveillance, air defense, maintenance, medical, supply, and signal assets. Each contributes to the commander’s ability to see, suppress, and move. Each must be used to the best advantage.
![]() c. Replacements. Replacements must have time to become familiar with the –
c. Replacements. Replacements must have time to become familiar with the –
![]() (1) Situation.
(1) Situation.
![]() (2) Mission.
(2) Mission.
![]() (3) SOPs.
(3) SOPs.
![]() (4) Communication and electronics.
(4) Communication and electronics.
![]() d. IPB. The engineer is the terrain expert and works closely with the Intelligence Officer (US Army) (S2) in the initial phases of the IPB process. The engineer will advise the maneuver commander on the terrain's capability to support the plan and how the commander can best use the terrain to his benefit.
d. IPB. The engineer is the terrain expert and works closely with the Intelligence Officer (US Army) (S2) in the initial phases of the IPB process. The engineer will advise the maneuver commander on the terrain's capability to support the plan and how the commander can best use the terrain to his benefit.
Study Appendix C, page C-21 for a more thorough grasp of this subject.
![]() e. R&S planning. The S2 prepares a detailed R&S plan based on information generated during the IPB process. He coordinates this with the Operations and Training Officer (US Army) (S3) to confirm or deny the S2’s templating. Specific taskings are given to CO/TMs, scout platoons, ground surveillance radar (GSR) sections, and any other element that has an R&S capability.
e. R&S planning. The S2 prepares a detailed R&S plan based on information generated during the IPB process. He coordinates this with the Operations and Training Officer (US Army) (S3) to confirm or deny the S2’s templating. Specific taskings are given to CO/TMs, scout platoons, ground surveillance radar (GSR) sections, and any other element that has an R&S capability.
Study Appendix C, page C-21 through C-24 for a more thorough grasp of this subject.
![]() f. Reporting. The S2 establishes reporting by an established time schedule. The size, activity, location, unit, time, and equipment (SALUTE) format is used for accurate reporting. Information collected must be quickly disseminated to all elements of the TF and higher headquarters.
f. Reporting. The S2 establishes reporting by an established time schedule. The size, activity, location, unit, time, and equipment (SALUTE) format is used for accurate reporting. Information collected must be quickly disseminated to all elements of the TF and higher headquarters.
![]() g. Dissemination of information. Dissemination within the battalion/TF is usually made by personal contacts, oral reports, radio net monitoring, and briefings. Dissemination to higher and adjacent units is usually accomplished through reports, summaries, and intelligence estimates and analyses.
g. Dissemination of information. Dissemination within the battalion/TF is usually made by personal contacts, oral reports, radio net monitoring, and briefings. Dissemination to higher and adjacent units is usually accomplished through reports, summaries, and intelligence estimates and analyses.
![]() h. The command estimate. The estimate of the situation, in its broadest sense, is a mental, problem-solving process. The difficult part is to select the best way to accomplish the mission. An estimator should use some logical and rational system to assist him in determining the best way to accomplish the mission. (This concept is discussed in detail in Lesson 3.)
h. The command estimate. The estimate of the situation, in its broadest sense, is a mental, problem-solving process. The difficult part is to select the best way to accomplish the mission. An estimator should use some logical and rational system to assist him in determining the best way to accomplish the mission. (This concept is discussed in detail in Lesson 3.)
2-4. Scheme of Maneuver. The scheme of maneuver is the central expression of the commander's concept of the operation. The scheme of maneuver must be flexible enough to take advantage of developing information. Attack plans will often have two or more initial options. A final choice, based on the latest intelligence, will not be made until just before the attack.
![]() a. The scheme of maneuver addresses actions on the objective and synchronization of the close assault. Actions on the objective are an important aspect of attack planning. The commander must develop a plan to isolate and destroy individual enemy units by achieving overwhelming combat-power ratios at the decisive point and time. The plan must enable the commander to bring as much combat power to bear as possible by synchronizing maneuver elements and fires. Maneuver units must arrive at their attack-by-fire positions or commence the assault simultaneously to achieve the desired combat-power ratios and avoid a "piecemeal" attack. Fires must be planned to enhance combat-power ratios. Reverse planning from actions on the objective is an excellent method for enhancing synchronization of the attack. It serves to clarify the commander's intent and prevent overemphasis on movement. To isolate enemy units from one another, the commander may use direct and indirect fires, including smoke for obscuration, and maneuver to fix units or to prevent reinforcement.
a. The scheme of maneuver addresses actions on the objective and synchronization of the close assault. Actions on the objective are an important aspect of attack planning. The commander must develop a plan to isolate and destroy individual enemy units by achieving overwhelming combat-power ratios at the decisive point and time. The plan must enable the commander to bring as much combat power to bear as possible by synchronizing maneuver elements and fires. Maneuver units must arrive at their attack-by-fire positions or commence the assault simultaneously to achieve the desired combat-power ratios and avoid a "piecemeal" attack. Fires must be planned to enhance combat-power ratios. Reverse planning from actions on the objective is an excellent method for enhancing synchronization of the attack. It serves to clarify the commander's intent and prevent overemphasis on movement. To isolate enemy units from one another, the commander may use direct and indirect fires, including smoke for obscuration, and maneuver to fix units or to prevent reinforcement.
![]() b. Normally, the TF scheme of maneuver for a deliberate attack employs three elements: main attack, supporting attack, and reserve.
b. Normally, the TF scheme of maneuver for a deliberate attack employs three elements: main attack, supporting attack, and reserve.
![]() (1) Main attack. The mission of the main attack is to penetrate the enemy's defenses and secure the objective. The main attack emphasizes the indirect approach.
(1) Main attack. The mission of the main attack is to penetrate the enemy's defenses and secure the objective. The main attack emphasizes the indirect approach.
![]() (2) Supporting attack. The mission of the supporting attack is to fix or suppress an enemy force not being directly assaulted by the main attack. The supporting attack accomplishes its mission by emphasizing fire rather than maneuver. The fires of the supporting attack must be combined with indirect fires to achieve the maximum effectiveness. The supporting attack allows the main attack to be successful.
(2) Supporting attack. The mission of the supporting attack is to fix or suppress an enemy force not being directly assaulted by the main attack. The supporting attack accomplishes its mission by emphasizing fire rather than maneuver. The fires of the supporting attack must be combined with indirect fires to achieve the maximum effectiveness. The supporting attack allows the main attack to be successful.
![]() (3) Reserve. The reserve is an uncommitted force used during the critical place and time to ensure mission success. Reserves are positioned to weight the main effort. They exploit success, reinforce or maintain momentum, deal with enemy counterattacks, provide security, complete the destruction of enemy forces, secure deep objectives, or open the next phase of a campaign or major operation by seizing objectives beyond the defended area.
(3) Reserve. The reserve is an uncommitted force used during the critical place and time to ensure mission success. Reserves are positioned to weight the main effort. They exploit success, reinforce or maintain momentum, deal with enemy counterattacks, provide security, complete the destruction of enemy forces, secure deep objectives, or open the next phase of a campaign or major operation by seizing objectives beyond the defended area.
![]() (a) The TF normally retains a reserve to complete the destruction of the enemy’s position or exploit the success of the attack. The reserve may be used initially to overwatch the main attack.
(a) The TF normally retains a reserve to complete the destruction of the enemy’s position or exploit the success of the attack. The reserve may be used initially to overwatch the main attack.
![]() (b) A brigade conducting a deliberate attack may often retain a two-or three-company battalion/TF in reserve initially. The commander and staff of a battalion/TF so designated face a planning task more complex than the task of planning a main or supporting attack.
(b) A brigade conducting a deliberate attack may often retain a two-or three-company battalion/TF in reserve initially. The commander and staff of a battalion/TF so designated face a planning task more complex than the task of planning a main or supporting attack.
![]() (c) The reserve commander needs to know the brigade concept in great detail, including when and where the brigade commander feels the reserve may be committed. He also needs the concepts of the leading battalions/TFs so that should the reserve be committed through or around any of them, he will have information as to their scheme of maneuver and plan for fire support. When the attack is under way, representatives of the reserve should be in the command post of the leading battalions/TFs. Many brigades require the commander of the reserve to join the brigade command group. Such an SOP provides the advantage of permitting the reserve commander to see the attack develop as the brigade commander sees it and have a forewarning of commitment. With face-to-face-contact with the higher unit commander, no time will be lost nor any misunderstanding of the mission as might be the case if orders are transmitted electronically or by messenger.
(c) The reserve commander needs to know the brigade concept in great detail, including when and where the brigade commander feels the reserve may be committed. He also needs the concepts of the leading battalions/TFs so that should the reserve be committed through or around any of them, he will have information as to their scheme of maneuver and plan for fire support. When the attack is under way, representatives of the reserve should be in the command post of the leading battalions/TFs. Many brigades require the commander of the reserve to join the brigade command group. Such an SOP provides the advantage of permitting the reserve commander to see the attack develop as the brigade commander sees it and have a forewarning of commitment. With face-to-face-contact with the higher unit commander, no time will be lost nor any misunderstanding of the mission as might be the case if orders are transmitted electronically or by messenger.
![]() (d) In a fast-moving operation, the reserve may move continuously behind a designated force. Deliberate attacks, however, are likely to be relatively slow. The reserve should plan to move on at least two routes so as to have combat units well forward. The commander should also plan dispersal areas where portions of the TF can obtain cover or concealment if held up even momentarily. Movement on multiple routes and provision for dispersal are ways of providing security for the TF and making it more difficult for the enemy to detect the direction of the brigade's main effort.
(d) In a fast-moving operation, the reserve may move continuously behind a designated force. Deliberate attacks, however, are likely to be relatively slow. The reserve should plan to move on at least two routes so as to have combat units well forward. The commander should also plan dispersal areas where portions of the TF can obtain cover or concealment if held up even momentarily. Movement on multiple routes and provision for dispersal are ways of providing security for the TF and making it more difficult for the enemy to detect the direction of the brigade's main effort.
Study Appendix C, pages C-25 through C-28 for a more thorough grasp of this subject.
2-5. Integration and Coordination of Combat, CS, and CSS Assets.
![]() a. Follow-and-support forces. Follow-and-support forces are normally battalions/TFs or higher formations employed primarily in exploitation and pursuit operations to facilitate maintaining the momentum of the attack. They may also be used in conducting a penetration. A force with a follow-and-support mission is a committed unit.
a. Follow-and-support forces. Follow-and-support forces are normally battalions/TFs or higher formations employed primarily in exploitation and pursuit operations to facilitate maintaining the momentum of the attack. They may also be used in conducting a penetration. A force with a follow-and-support mission is a committed unit.
Follow-and-support forces assist attacking units by relieving them of tasks that would otherwise slow their advance. These tasks include –
- Destroying bypassed pocket of resistance.
- Relieving elements of the attacking force that have been left to block or contain enemy forces.
- Securing the flanks of a penetration to prevent the enemy from closing it.
- Expanding the area of the penetration by breaking through other enemy defenses.
- Securing lines of communications.
- Securing key terrain overrun or bypassed by the attacking unit.
- Protecting key installations.
- Guarding prisoners of war.
When augmented with additional CSS assets, follow-and-support forces may also be assigned missions such as refugees control and casualty collection and management.
When operating as a follow-and-support force, TF movement techniques are similar to those used in the movement to contact. Plans are coordinated with the unit that the TF follows, and the tactical command post (CP) initially moves with that unit's tactical CP. The TF main CP monitors the command net of the unit that it is following.
![]() b. CO/TMs. Within the main or supporting attack, the TF commander assigns CO/TMs one of the following four basic missions to support the TF scheme of maneuver:
b. CO/TMs. Within the main or supporting attack, the TF commander assigns CO/TMs one of the following four basic missions to support the TF scheme of maneuver:
![]() (1) An attack to seize/secure a terrain objective. If the mission is to seize an objective, the company must clear it of enemy forces. Securing means not only gaining possession of the objective but deploying in a manner that prevents its destruction or loss to enemy action. The commander must clearly state the purpose to be achieved by seizing or securing the objective.
(1) An attack to seize/secure a terrain objective. If the mission is to seize an objective, the company must clear it of enemy forces. Securing means not only gaining possession of the objective but deploying in a manner that prevents its destruction or loss to enemy action. The commander must clearly state the purpose to be achieved by seizing or securing the objective.
![]() (2) An overwatch. A unit assigned an overwatch mission supports the movement of other elements by placing direct fire or adjusting indirect fire on enemy forces that could engage the supported unit. The commander must designate the element to be overwatched and assign fire-control measures. The range of enemy antiarmor systems normally requires the overwatch element to reposition frequently. The commander may designate a series of overwatch positions or specify positioning instructions for the overwatch element. Overwatch positions are usually shown graphically as checkpoints.
(2) An overwatch. A unit assigned an overwatch mission supports the movement of other elements by placing direct fire or adjusting indirect fire on enemy forces that could engage the supported unit. The commander must designate the element to be overwatched and assign fire-control measures. The range of enemy antiarmor systems normally requires the overwatch element to reposition frequently. The commander may designate a series of overwatch positions or specify positioning instructions for the overwatch element. Overwatch positions are usually shown graphically as checkpoints.
![]() (3) An attack by fire. This mission requires engaging an enemy force with direct fire to destroy, fix, or suppress it. Commanders can assign positions and sectors of fire or other fire-control measures.
(3) An attack by fire. This mission requires engaging an enemy force with direct fire to destroy, fix, or suppress it. Commanders can assign positions and sectors of fire or other fire-control measures.
![]() (4) A reserve force. The TF commander determines the size, composition, and location of his reserve. The commander prioritizes missions for planning and coordination based on likely contingencies.
(4) A reserve force. The TF commander determines the size, composition, and location of his reserve. The commander prioritizes missions for planning and coordination based on likely contingencies.
![]() c. Scout platoon. During the preparation for the deliberate attack, the primary mission of the platoon is reconnaissance to gather intelligence on the enemy's defensive locations, orientation, and dispositions. Zone reconnaissance to facilitate the movement of the main attack, supporting attack, and reserves is a secondary mission. During the attack, the scout platoon's mission is to report enemy repositioning and counterattack. It prepares to screen to the front of the battalion/TF upon consolidation of the objective.
c. Scout platoon. During the preparation for the deliberate attack, the primary mission of the platoon is reconnaissance to gather intelligence on the enemy's defensive locations, orientation, and dispositions. Zone reconnaissance to facilitate the movement of the main attack, supporting attack, and reserves is a secondary mission. During the attack, the scout platoon's mission is to report enemy repositioning and counterattack. It prepares to screen to the front of the battalion/TF upon consolidation of the objective.
![]() d. Antiarmor company. AT elements are normally positioned to provide overwatch and support by fire onto the objective and the potential enemy counterattack routes.
d. Antiarmor company. AT elements are normally positioned to provide overwatch and support by fire onto the objective and the potential enemy counterattack routes.
![]() e. Field artillery (FA). The TF commander employs FA to help his CO/TMs move forward. In the deliberate attack, preparation fires and/or series of targets are often planned and delivered on the objective according to a predetermined time schedule. The commander plans fires to suppress, isolate, and blind the enemy forces. These fires are smoke and high explosive (HE). Also, a short-duration family of scatterable mines (FASCAM) is used to help isolate and impair the enemy's ability to counterattack.
e. Field artillery (FA). The TF commander employs FA to help his CO/TMs move forward. In the deliberate attack, preparation fires and/or series of targets are often planned and delivered on the objective according to a predetermined time schedule. The commander plans fires to suppress, isolate, and blind the enemy forces. These fires are smoke and high explosive (HE). Also, a short-duration family of scatterable mines (FASCAM) is used to help isolate and impair the enemy's ability to counterattack.
![]() (1) A TF conducting the brigade's main attack will normally have priority of the brigade's direct-support artillery battalion, organic mortars, and aviation support. The commander and his staff develop the scheme of maneuver and the supporting fires concurrently. The fire-support officer (FSO) plans, prepares, distributes, and continually updates the TF fire-support plan.
(1) A TF conducting the brigade's main attack will normally have priority of the brigade's direct-support artillery battalion, organic mortars, and aviation support. The commander and his staff develop the scheme of maneuver and the supporting fires concurrently. The fire-support officer (FSO) plans, prepares, distributes, and continually updates the TF fire-support plan.
![]() (2) The FSO recommends and the commander approves those fire-support tasks that make the greatest contribution to the attack. The FSO determines priorities and taskings for the battalion mortar platoon in conjunction with the overall fire-support plan.
(2) The FSO recommends and the commander approves those fire-support tasks that make the greatest contribution to the attack. The FSO determines priorities and taskings for the battalion mortar platoon in conjunction with the overall fire-support plan.
![]() (3) The priority task for fire support in the attack is the suppression of antiarmor systems that inhibit maneuver.
(3) The priority task for fire support in the attack is the suppression of antiarmor systems that inhibit maneuver.
![]() (4) Other fire-support tasks in the attack include –
(4) Other fire-support tasks in the attack include –
![]() (a) Preparation fires. Preparation fires, including preplanned close air support (CAS), can suppress, neutralize, and destroy enemy positions on the objective.
(a) Preparation fires. Preparation fires, including preplanned close air support (CAS), can suppress, neutralize, and destroy enemy positions on the objective.
![]() (b) Obscuration and screening fires. Fires using smoke assist breaching efforts, cover friendly maneuver, and aid in deception efforts,
(b) Obscuration and screening fires. Fires using smoke assist breaching efforts, cover friendly maneuver, and aid in deception efforts,
![]() (c) Counterbattery fires. When manual breaching is anticipated, the FSO should coordinate for counterbattery fires, which are planned by higher headquarters.
(c) Counterbattery fires. When manual breaching is anticipated, the FSO should coordinate for counterbattery fires, which are planned by higher headquarters.
![]() (d) Illumination fires. Illuminating fires are always planned for night attacks but are usually held on the order of the TF commander.
(d) Illumination fires. Illuminating fires are always planned for night attacks but are usually held on the order of the TF commander.
![]() (e) Priority targets. Priority targets are normally allocated to weight the main attack.
(e) Priority targets. Priority targets are normally allocated to weight the main attack.
![]() (f) Assault fires. Assault fires are usually executed in the following sequence:
(f) Assault fires. Assault fires are usually executed in the following sequence:
- Suppression fires to prevent the enemy from observing and engaging friendly elements and conceal the movement of companies.
- Concentrated fires to destroy enemy fighting positions near the initial objective.
- Subsequent fires that concentrate on deeper objectives.
![]() (g) Fires during consolidation. Fires are placed on retreating enemy forces and on deeper positions. Targets are planned on likely enemy counterattack routes or placed on enemy withdrawal routes to force his destruction or capture.
(g) Fires during consolidation. Fires are placed on retreating enemy forces and on deeper positions. Targets are planned on likely enemy counterattack routes or placed on enemy withdrawal routes to force his destruction or capture.
![]() f. Mortars. Mortars move well forward with the main effort. Although they can provide HE suppression, their primary mission is smoke placed in front of the objective and between the TF and the enemy to conceal friendly movement and isolate the enemy by obscuring enemy weapon systems. Once on the objective, the mortars position to provide general support to the battalion/TF defense.
f. Mortars. Mortars move well forward with the main effort. Although they can provide HE suppression, their primary mission is smoke placed in front of the objective and between the TF and the enemy to conceal friendly movement and isolate the enemy by obscuring enemy weapon systems. Once on the objective, the mortars position to provide general support to the battalion/TF defense.
![]() g. Air force. CAS missions are planned and flown at the request of the battalion/TF. The number of sorties received depends on the number allocated by brigade. The deliberate-attack planning process requires detailed planning, integration, and coordination of CAS within the battalion/TF scheme of maneuver. Tank and artillery positions are the priorities of CAS in the deliberate attack.
g. Air force. CAS missions are planned and flown at the request of the battalion/TF. The number of sorties received depends on the number allocated by brigade. The deliberate-attack planning process requires detailed planning, integration, and coordination of CAS within the battalion/TF scheme of maneuver. Tank and artillery positions are the priorities of CAS in the deliberate attack.
![]() h. ADA. During the deliberate attack, ADA assets are positioned well forward to support the main effort. ADA coverage for the main effort is focused against likely air avenues of approach and is concentrated at choke points and river-crossing sites.
h. ADA. During the deliberate attack, ADA assets are positioned well forward to support the main effort. ADA coverage for the main effort is focused against likely air avenues of approach and is concentrated at choke points and river-crossing sites.
![]() i. CSS. The combat trains normally do not accompany the battalion/TF during the deliberate attack. They remain in a location and readiness pasture that allows them to move forward rapidly to planned locations from which to affect CSS upon consolidation on the objective.
i. CSS. The combat trains normally do not accompany the battalion/TF during the deliberate attack. They remain in a location and readiness pasture that allows them to move forward rapidly to planned locations from which to affect CSS upon consolidation on the objective.
2-6. Mobility, Countermobility, Survivability.
![]() a. Mobility. Engineer elements are employed well forward with the main attack to enhance mobility. Normally, reconnaissance is done by troops who are to breach obstacles, accompanied by an engineer who will assist in the assessment of obstacles. They accompany the breaching force and assist in reduction and crossing of obstacles encountered. In the deliberate attack, stealthy prebreach of obstacles by engineers or dismounted infantry is a preferred technique.
a. Mobility. Engineer elements are employed well forward with the main attack to enhance mobility. Normally, reconnaissance is done by troops who are to breach obstacles, accompanied by an engineer who will assist in the assessment of obstacles. They accompany the breaching force and assist in reduction and crossing of obstacles encountered. In the deliberate attack, stealthy prebreach of obstacles by engineers or dismounted infantry is a preferred technique.
![]() b. Countermobility. Short-duration FASCAM can be planned behind an enemy unit to seal withdrawal routes or counterattack routes.
b. Countermobility. Short-duration FASCAM can be planned behind an enemy unit to seal withdrawal routes or counterattack routes.
![]() c. Survivability. Survivability provides concealment and shelter from the effects of enemy weapons. Engineers have the technical knowledge, skills, and equipment to help other units develop and improve survivability.
c. Survivability. Survivability provides concealment and shelter from the effects of enemy weapons. Engineers have the technical knowledge, skills, and equipment to help other units develop and improve survivability.
ENGINEER CONSIDERATIONS
This section deals with planning and executing an offensive operation. It does not cover all of the tactical issues dealing with the TF in the offense but looks instead at the interface that must occur between the TF and the engineer company during offensive operations.
The engineer company provides a significant offensive capability to the force. The engineer company is the primary agent of obstacle breaching and fortification reduction available to the TF or the engineer battalion. The engineer company normally fights as part of a TF or with the engineer battalion during the offense.
The offense's main purpose is to defeat, destroy, or neutralize the enemy force. The fundamental characteristics of offensive operations are surprise, concentration, tempo, and audacity. These characteristics are all subcomponents of initiative.
2-7. Engineer Planning for the Deliberate Attack. Engineer planning requires a detailed engineer battlefield assessment (EBA). Enemy templating is crucial to the rapid movement of the force and the successful breaching of enemy obstacle systems. The combat-engineer battalion headquarters assists the brigade staff during situation analysis, prepares the EBA, and assists with detailed analysis and estimates during course-of-action (COA) development. It continually refines the EBA and war-games to assess all possible outcomes and develop necessary counters. Locating engineer units within the force and pre-positioning necessary materials allows either rapid exploitation of success or rapid transition to defense. Engineer considerations in a deliberate attack are support well forward, obstacle responsibility, flank security, and logistical sustainment.
![]() a. Support well forward. The primary offensive engineer function is mobility. There is insufficient engineer effort available in a rapidly moving offensive operation to accomplish more than just incidental survivability tasks. Consequently, most of the division engineers are task-organized in command relationships with forward elements. Generally, the leading TFs of the main-effort brigade and their supporting brigades receive a combat-engineer battalion. This battalion is oriented on mobility, rapid breaching, and assault support. It has assets to provide countermobility obstacles to protect the maneuver force's flank. The main-effort brigade is normally reinforced with an additional combat-engineer company from the following or supporting brigade(s). This combat-engineer company provides additional mobility capability.
a. Support well forward. The primary offensive engineer function is mobility. There is insufficient engineer effort available in a rapidly moving offensive operation to accomplish more than just incidental survivability tasks. Consequently, most of the division engineers are task-organized in command relationships with forward elements. Generally, the leading TFs of the main-effort brigade and their supporting brigades receive a combat-engineer battalion. This battalion is oriented on mobility, rapid breaching, and assault support. It has assets to provide countermobility obstacles to protect the maneuver force's flank. The main-effort brigade is normally reinforced with an additional combat-engineer company from the following or supporting brigade(s). This combat-engineer company provides additional mobility capability.
![]() b. Obstacle responsibility. Countermobility is also important. Plans include situational obstacles to cover dangerous counterattack and flank-attack routes into the maneuver force's area of operations. Situational obstacles are planned as a way to handle contingencies. As a part of the war-gaming process, the engineer on the battle staff identifies areas for situational obstacles. Penetrations always require dynamic obstacles to help hold the flanks, and deep attacks require preplanned flank obstacles to block potential counterattack routes. The combat engineer also plans on a transition to the defense as the natural sequel to all offensive operations and preplans the necessary situational obstacles. Situational obstacles are controlled with the use of obstacle zones and belts.
b. Obstacle responsibility. Countermobility is also important. Plans include situational obstacles to cover dangerous counterattack and flank-attack routes into the maneuver force's area of operations. Situational obstacles are planned as a way to handle contingencies. As a part of the war-gaming process, the engineer on the battle staff identifies areas for situational obstacles. Penetrations always require dynamic obstacles to help hold the flanks, and deep attacks require preplanned flank obstacles to block potential counterattack routes. The combat engineer also plans on a transition to the defense as the natural sequel to all offensive operations and preplans the necessary situational obstacles. Situational obstacles are controlled with the use of obstacle zones and belts.
![]() (1) Engineers with each leading brigade retain some type of situational mining capability. This could be the third company of the combat-engineer battalion, augmented by all obstacle sections within the battalion.
(1) Engineers with each leading brigade retain some type of situational mining capability. This could be the third company of the combat-engineer battalion, augmented by all obstacle sections within the battalion.
![]() (2) Artillery-delivered scatterable mines are always preplanned. The engineer at each level (TF, brigade, and division) plans and coordinates the employment of all artillery- scattered mines. Because artillery support for situational mining in the attack may be limited, engineers cannot prestock mines near firing points when required to move forward rapidly. Mission ammunition loads must be predominantly designed to suppress, neutralize, and obscure. If artillery-scattered mines are critical to the obstacle plan, engineers may dedicate vehicles to haul the ammunition for the artillery.
(2) Artillery-delivered scatterable mines are always preplanned. The engineer at each level (TF, brigade, and division) plans and coordinates the employment of all artillery- scattered mines. Because artillery support for situational mining in the attack may be limited, engineers cannot prestock mines near firing points when required to move forward rapidly. Mission ammunition loads must be predominantly designed to suppress, neutralize, and obscure. If artillery-scattered mines are critical to the obstacle plan, engineers may dedicate vehicles to haul the ammunition for the artillery.
![]() (3) The combat-aviation brigade provides a significant situational-obstacle capability. Engineer rapid-demolition teams consist of a combat-engineer squad with preconfigured demolitions materials. These teams, which wait at a forward area rearm/refuel point (FARP) or helicopter pickup point, are able to rapidly destroy a bridge or crater a road. Helicopter-delivered Volcano minefields are planned but not loaded onto helicopters until needed. A combat-engineer squad is required, with the stockpile of Volcano mines, to load aircraft at a FARP. Preferably, these engineer forces would be provided by a supporting corps combat-engineer unit, but they could be provided by the following brigade.
(3) The combat-aviation brigade provides a significant situational-obstacle capability. Engineer rapid-demolition teams consist of a combat-engineer squad with preconfigured demolitions materials. These teams, which wait at a forward area rearm/refuel point (FARP) or helicopter pickup point, are able to rapidly destroy a bridge or crater a road. Helicopter-delivered Volcano minefields are planned but not loaded onto helicopters until needed. A combat-engineer squad is required, with the stockpile of Volcano mines, to load aircraft at a FARP. Preferably, these engineer forces would be provided by a supporting corps combat-engineer unit, but they could be provided by the following brigade.
![]() (4) Normally, the assault-and-obstacle platoon carries mines for rapid surface mining during offensive operations. The combat-engineer company will use the Volcano mine system and will require additional haul assets from the supported unit.
(4) Normally, the assault-and-obstacle platoon carries mines for rapid surface mining during offensive operations. The combat-engineer company will use the Volcano mine system and will require additional haul assets from the supported unit.
![]() c. Flank security. All placement of flank and hasty defense obstacles will be controlled with the use of obstacle belts and groups as subsets of the obstacle zones. Their location will be determined in the IPB and EBA processes. These control measures will be placed on the maneuver graphics and passed to the support elements to make them aware of potential obstacle locations.
c. Flank security. All placement of flank and hasty defense obstacles will be controlled with the use of obstacle belts and groups as subsets of the obstacle zones. Their location will be determined in the IPB and EBA processes. These control measures will be placed on the maneuver graphics and passed to the support elements to make them aware of potential obstacle locations.
![]() d. Logistical sustainment. Logistical sustainment requires conversion of tracked-vehicle-capable lanes and gaps into moderate-speed, wheeled-vehicle routes as soon as possible. Each forward brigade require one good, all-weather main supply route (MSR) in order to sustain its fight Forward ammunition supply points (ATPs) and ammunition transfer points (ATPs) require protection and concealed road nets capable of withstanding heavy wheeled-vehicle traffic and occasional tracked-vehicle traffic. Replacement of assault bridging and improving breach lanes are necessary to accelerate and ease wheeled-vehicle passage. Wheeled combat-engineer battalions from the corps engineer group provide this support to the division. Regimental engineers do not have the capability to accomplish these missions.
d. Logistical sustainment. Logistical sustainment requires conversion of tracked-vehicle-capable lanes and gaps into moderate-speed, wheeled-vehicle routes as soon as possible. Each forward brigade require one good, all-weather main supply route (MSR) in order to sustain its fight Forward ammunition supply points (ATPs) and ammunition transfer points (ATPs) require protection and concealed road nets capable of withstanding heavy wheeled-vehicle traffic and occasional tracked-vehicle traffic. Replacement of assault bridging and improving breach lanes are necessary to accelerate and ease wheeled-vehicle passage. Wheeled combat-engineer battalions from the corps engineer group provide this support to the division. Regimental engineers do not have the capability to accomplish these missions.
2-8. Reconnaissance. Reconnaissance is always conducted to verify, extend, and modify the engineer picture of the battlefield developed during the EBA. The combat-engineer battalion S2 develops the list of engineer priority-intelligence requirements. These requirements are met through direct tasking of engineer companies and by passing these requirements to the brigade S2 for incorporation into the brigade's collection plan. The S2 is also the expert on the threats engineer organizations, equipment, capabilities, doctrine, tactics, techniques, and procedures. The engineer-brigade S2 is the main source for this detailed information.
A combat-engineer scout squad normally accompanies the maneuver scout platoon during reconnaissance. The combat-engineer squad, along with the scouts –
- Conducts reconnaissance of predicted obstacle areas.
- Conducts reconnaissance of unexpected obstacles encountered, and develop precise locations of the obstacles.
- Gathers detailed information on the obstacles such as mine types, spacing, and depth of tank ditches.
- Identifies attack positions for the breaching force and likely lane locations.
Scouts concurrently determine details of the overwatching battle positions and identify attack-by-fire positions for the support force.
2-9. Attack. The division engineer supports the brigades with reinforced combat-engineer battalions. These battalions are augmented with one combat-engineer company from the follow-on brigade. The brigade engineers normally organize their forces as follows:
![]() a. The lead brigade's combat-engineer battalion provides up to two reinforced combat-engineer companies to support leading TFs. Normally, each TF receives one combat-engineer company, and reinforcements come from that battalion's organic company.
a. The lead brigade's combat-engineer battalion provides up to two reinforced combat-engineer companies to support leading TFs. Normally, each TF receives one combat-engineer company, and reinforcements come from that battalion's organic company.
![]() b. The remaining organic company, now just a headquarters, receives the battalion's three obstacle sections and acts as the maneuver brigade's obstacle reserve.
b. The remaining organic company, now just a headquarters, receives the battalion's three obstacle sections and acts as the maneuver brigade's obstacle reserve.
![]() c. The combat-engineer company, under the operational control (OPCON) of the lead brigade, is given the missions of accepting obstacle handover from the leading TFs and improving obstacle lanes during the attack. The OPCON combat-engineer companies will hand over the obstacles to the follow-on TFs when they arrive.
c. The combat-engineer company, under the operational control (OPCON) of the lead brigade, is given the missions of accepting obstacle handover from the leading TFs and improving obstacle lanes during the attack. The OPCON combat-engineer companies will hand over the obstacles to the follow-on TFs when they arrive.
The follow-on brigade is organized with a combat-engineer company in support of each of its leading TFs. These companies move platoons in front of their TFs to take obstacle handover and help the TF passage. The combat-engineer battalion's third company is in direct support (DS) to the combat-engineer battalion of the main-effort brigade.
2-10. Formation Movement. Combat engineers move as a part of a larger maneuver formation. The lead elements move under the control of the formation commander. Combat-engineer elements farther back and engineer-equipment support elements generally move in column, keeping station on the formation to their front.
![]() a. Lead combat-engineer squad. The lead combat-engineer element in a moving formation is a combat-engineer squad, which moves with the forward security element. Its mission is to identify terrain difficulties and obstacles, find a bypass, mark routes, report to the maneuver and combat-engineer commanders, and continue the mission.
a. Lead combat-engineer squad. The lead combat-engineer element in a moving formation is a combat-engineer squad, which moves with the forward security element. Its mission is to identify terrain difficulties and obstacles, find a bypass, mark routes, report to the maneuver and combat-engineer commanders, and continue the mission.
![]() b. Lead combat-engineer platoon. The combat-engineer platoon moves with four M113s and one combat-engineer vehicle (CEV) in a platoon-movement formation within the maneuver-team formation. The platoon does not tow trailers, except for mine-clearing line charge (MICLIC) launchers, if armored vehicle-launched MICLICs (AVLMs) are not available. Armored vehicle-launched bridges (AVLBs), Volcano tracks, and armored combat earthmovers (ACEs) do not have the mobility to terrain drive. They move behind the maneuver CO/TM, normally one terrain feature back, guiding on the trail element. They move under the control of their platoon leader. Their mission is to conduct the initial breaching operations. They mark the breach, report its location, and continue the mission. The trailers can be left in the maneuver-unit field trains and brought forward by the engineer and maneuver CSS vehicles.
b. Lead combat-engineer platoon. The combat-engineer platoon moves with four M113s and one combat-engineer vehicle (CEV) in a platoon-movement formation within the maneuver-team formation. The platoon does not tow trailers, except for mine-clearing line charge (MICLIC) launchers, if armored vehicle-launched MICLICs (AVLMs) are not available. Armored vehicle-launched bridges (AVLBs), Volcano tracks, and armored combat earthmovers (ACEs) do not have the mobility to terrain drive. They move behind the maneuver CO/TM, normally one terrain feature back, guiding on the trail element. They move under the control of their platoon leader. Their mission is to conduct the initial breaching operations. They mark the breach, report its location, and continue the mission. The trailers can be left in the maneuver-unit field trains and brought forward by the engineer and maneuver CSS vehicles.
![]() c. Lead combat-engineer company. Two reinforced combat-engineer platoons are forward with lead maneuver teams. An additional combat-engineer platoon (minus) and the additional assault section move under company-command group control behind the lead teams in the vicinity of the TF command group. The obstacle section from the forward combat-engineer company is attached to the trail engineer company. Its mission is to pass the maneuver battalion through the obstacle, improve the marking system, report, and continue the mission.
c. Lead combat-engineer company. Two reinforced combat-engineer platoons are forward with lead maneuver teams. An additional combat-engineer platoon (minus) and the additional assault section move under company-command group control behind the lead teams in the vicinity of the TF command group. The obstacle section from the forward combat-engineer company is attached to the trail engineer company. Its mission is to pass the maneuver battalion through the obstacle, improve the marking system, report, and continue the mission.
![]() d. Lead combat-engineer battalion. The battalion command group moves behind the lead TF. The third engineer company, minus its assault sections but with additional obstacle sections, moves in the center of the brigade. It can install rapid obstacles. This third company retains a blade team (two ACEs and a supervisor) from its assault sections. The blade team works forward to improve breaches and allow rapid recovery of AVLBs. The DS engineer company, under the engineer battalion commander's control, moves by bounds near the center of the brigade, accepts obstacle handover from forward engineers, and helps the following brigade to pass.
d. Lead combat-engineer battalion. The battalion command group moves behind the lead TF. The third engineer company, minus its assault sections but with additional obstacle sections, moves in the center of the brigade. It can install rapid obstacles. This third company retains a blade team (two ACEs and a supervisor) from its assault sections. The blade team works forward to improve breaches and allow rapid recovery of AVLBs. The DS engineer company, under the engineer battalion commander's control, moves by bounds near the center of the brigade, accepts obstacle handover from forward engineers, and helps the following brigade to pass.
Study Appendix C, pages C-12 through C-18, for a more thorough grasp of this subject.
2-11. Breaching Obstacle Systems. The four types of breaching are in-stride, deliberate, assault, and covert. The command at each level must choose the breaching option based on the best information available and on the mission. Reconnaissance plays a major role in breaching. The size of the enemy force protecting the obstacle often determines the commander's decision on which type of breaching will be done. Each task requires two lanes through an obstacle system for mounted forces. If dismounted, each infantry platoon requires one lane. When planning the lane and breaching equipment requirements, the commander must have 50 percent redundancy in breaching equipment to handle unexpected problems and battle losses.
![]() a. In-stride. The in-stride breach is used by the maneuver brigades and TFs to quickly overcome unexpected or lightly defended tactical obstacles. Brigade and TF commanders plan and prepare their forces for an in-stride breach by task-organizing subordinate TFs or CO/TMs with the forces needed to conduct independent breaching operations. The actual breach is conducted at the subordinate level. The subordinate commander designates specific support, breaching, and assault forces based on his task organization. He is also responsible for synchronizing the suppress, obscure, secure, reduce (SOSR) breaching fundamentals through his own detailed breach planning or well-rehearsed immediate-action drills. The in-stride breach tactic enables a TF to seize and maintain the initiative through simple, decentralized, independent breaching operations conducted under the responsive C2 of CO/TM commanders.
a. In-stride. The in-stride breach is used by the maneuver brigades and TFs to quickly overcome unexpected or lightly defended tactical obstacles. Brigade and TF commanders plan and prepare their forces for an in-stride breach by task-organizing subordinate TFs or CO/TMs with the forces needed to conduct independent breaching operations. The actual breach is conducted at the subordinate level. The subordinate commander designates specific support, breaching, and assault forces based on his task organization. He is also responsible for synchronizing the suppress, obscure, secure, reduce (SOSR) breaching fundamentals through his own detailed breach planning or well-rehearsed immediate-action drills. The in-stride breach tactic enables a TF to seize and maintain the initiative through simple, decentralized, independent breaching operations conducted under the responsive C2 of CO/TM commanders.
![]() b. Deliberate. The deliberate breach is a maneuver designed to cross an obstacle and continue the mission. A unit conducts a deliberate breach when the required force allocation ratios for support, breaching, and assault forces are beyond the capability of a task-organized subordinate unit. The deliberate breach is characterized by thorough reconnaissance, detailed planning, extensive preparation, and explicit rehearsal. One or more subordinate units are specifically tasked to perform the roles of support, breaching, and assault forces. The deliberate breach is centrally planned and executed.
b. Deliberate. The deliberate breach is a maneuver designed to cross an obstacle and continue the mission. A unit conducts a deliberate breach when the required force allocation ratios for support, breaching, and assault forces are beyond the capability of a task-organized subordinate unit. The deliberate breach is characterized by thorough reconnaissance, detailed planning, extensive preparation, and explicit rehearsal. One or more subordinate units are specifically tasked to perform the roles of support, breaching, and assault forces. The deliberate breach is centrally planned and executed.
![]() c. Assault. The assault breach allows a force to penetrate a enemy's protective obstacles and destroy the defender in detail. It provides a force with the mobility needed to gain a foothold in the enemy defense and exploit success by continuing the assault through the objective. The assault breach is conducted by CO/TMs and platoons assigned the mission of assaulting an objective as part of a larger force's attack. The nature of combat during the assault phase requires a different application of the SOSR breaching fundamentals than those used during in-stride and deliberate breaches. The TF commander still provides the CO/TM or platoon with the support, breaching, and assault assets it needs to accomplish the mission. However, he also task-organizes his own support force to suppress the enemy during the breaching and to isolate the assault-objective area.
c. Assault. The assault breach allows a force to penetrate a enemy's protective obstacles and destroy the defender in detail. It provides a force with the mobility needed to gain a foothold in the enemy defense and exploit success by continuing the assault through the objective. The assault breach is conducted by CO/TMs and platoons assigned the mission of assaulting an objective as part of a larger force's attack. The nature of combat during the assault phase requires a different application of the SOSR breaching fundamentals than those used during in-stride and deliberate breaches. The TF commander still provides the CO/TM or platoon with the support, breaching, and assault assets it needs to accomplish the mission. However, he also task-organizes his own support force to suppress the enemy during the breaching and to isolate the assault-objective area.
![]() d. Covert. The covert breach is a special breaching operation used by dismounted forces during limited visibility. It is silently executed to achieve surprise and minimize casualties. The covert breach relies on stealth; quiet, manual lane-reduction techniques; and dismounted maneuver. The TF commander conducts a covert, breach when his mission specifies infiltration through the enemy to attack an objective deeper in the enemy's sector. The commander may also use the covert breach during an assault when the need for surprise outweighs the need for overwhelming suppression. The covert breach may support a mounted attack by creating and securing lanes designed for follow-on mechanized forces.
d. Covert. The covert breach is a special breaching operation used by dismounted forces during limited visibility. It is silently executed to achieve surprise and minimize casualties. The covert breach relies on stealth; quiet, manual lane-reduction techniques; and dismounted maneuver. The TF commander conducts a covert, breach when his mission specifies infiltration through the enemy to attack an objective deeper in the enemy's sector. The commander may also use the covert breach during an assault when the need for surprise outweighs the need for overwhelming suppression. The covert breach may support a mounted attack by creating and securing lanes designed for follow-on mechanized forces.
2-12. Obstacle Handover. All combat engineers with follow-on forces move in front of their unit to accept obstacle-lane responsibility, improve lanes within capabilities, and pass their unit through and hand over the obstacle lanes to following forces. The platoon conducting the initial breach is responsible for conducting it according to the tactical marking system and passing responsibility for the obstacle lane to the following DS combat-engineer company within its battalion. In turn, the following DS combat-engineer company hands over the obstacle to the lead company of the following combat-engineer battalion (the combat-engineer battalion with the following brigade). Clearly marked lanes are essential. As soon as possible, an engineer force either marks the obstacle and lanes, bypasses them according to FM 5-34 with permanent fencing, or renders the obstacle safe (clears minefields and installs semipermanent bridging).
2-13. Summary. This lesson addressed the planning considerations for an armored battalion/TF deliberate attack and the fundamentals of the deliberate attack. A deliberate attack requires time for collecting and evaluating enemy information, reconnoitering, planning, and coordinating. The key areas of deliberate-attack planning fundamentals are time, IPB, R&S, and the command-estimate process. The integration and coordination of CS and CSS are important elements of the deliberate-attack planning process. This lesson also discussed the command-estimate process and the techniques of the deliberate attack. R&S are critical in planning the deliberate attack. Remember, reconnaissance is continually conducted to collect information on which the commander plans, makes decisions, and issues orders.
In this lesson, you learned that major changes are taking place in the engineering community that affect the way engineers will be used in the combined-arms team. You also learned the engineer considerations for planning and executing a deliberate attack. That is, the key functions of the engineer-battalion commander and his staff and the combat-engineer company commander during the planning and execution of the deliberate attack. Finally, you learned how and why combat-engineer assets are apportioned to the TFs.
GO TO:

