FM 6-20-10: Tactics, Techniques, and Procedures for The Targeting Process
CHAPTER 2
TARGETING METHODOLOGY
The modern battlefield presents many targets of different types and vulnerabilities exceeding the number of resources available to acquire and attack them. The commander must determine which targets are most important to the enemy and, of those targets, which ones he must acquire and attack to accomplish his mission. The purpose of this chapter is to explain the decide, detect, deliver, and assess targeting methodology, which is designed to assist the commander in the decision-making process.
GENERAL
Targeting is a combination of intelligence functions, planning battle command, weaponeering, operational execution, and combat assessment. The decide, detect, deliver, and assess methodology facilitates the attack of the right target with the right asset at the right time.
A very important part of the targeting process is the identification of potential fratricide situations and the necessary coordination measures to positively manage and control the attack of targets. These measures are incorporated in the coordinating instructions and appropriate annexes of the OPLAN and/or OPORD.
The targeting process provides an effective method for matching the friendly force capabilities against enemy targets. Targeting is a dynamic process; it must keep up with the changing face of the battlefield. The tools and products described in this chapter must be continually updated on the basis of combat assessment and situation development.
DECIDE
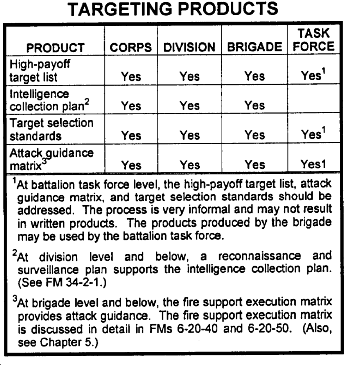
The decide function, as the first step in the targeting process, provides the overall focus and sets priorities for intelligence collection and attack planning. Targeting priorities must be addressed for each phase or critical event of an operation. The decisions made are reflected in visual products. The products areas follows:
- The high-payoff target list (HPTL) is a prioritized list of high-payoff targets (HPTs) whose loss to the enemy will contribute to the success of the friendly course of action.
- The intelligence collection plan answers the commander's PIRs, to include those HPTs designated as PIR. The plan, within the availability of additional collection assets, supports the acquisition of more HPTs. Determining the intelligence requirements is the first step in the collection management process. For a more detailed description, see FM 34-2.
- Target selection standards address accuracy or other specific criteria that must be met before targets can be attacked.
- The attack guidance matrix (AGM), approved by the commander, addresses which targets will be attacked, how, when, and the desired effects.
The products of the decide function are briefed to the commander. Upon his approval, his decisions are translated into the OPORD with annexes. Specific targeting products are required at echelons indicated in the table below.
Mission Analysis
At all echelons, the commander and his staff plan for future operations by analyzing one or more alternative COA. Each COA is based on the following:
- Mission analysis.
- Current and projected battle situations.
- Anticipated opportunities.
The process begins with receipt of a mission, whether assigned by higher headquarters or deduced by the commander. The commander, either with or without input from his staff, analyzes the mission, He considers tasks that must be performed and their purpose and limitations on the unit. The completed analysis is the basis for developing a restated mission. The restated mission is the basis from which to start the targeting process.
Intelligence Preparation of the Battlefield
The IPB provides much of the information for the intelligence estimate and the targeting process. IPB is the foundation for the rest of the targeting process. IPB includes electronic preparation of the battlefield (EPB). It is a continuous and systematic method for analyzing the enemy, weather, and terrain in a geographical area. This method evaluates enemy capabilities and predicts enemy COA with respect to specific battlefield conditions. Appendix A covers IPB with regard to the targeting process in greater detail. (Also see FM 34-130.)
Target Value Analysis and War-gaming
The battlefield environment, the effects of the environment on combatants, and the threat are considered in IPB analysis to arrive at an intelligence estimate. TVA yields HVTs for a specific enemy COA. Target spread sheets identify the HVTs in relation to a type of operation. The target sheets give more detailed targeting information for each specific HVT. The information on target spread sheets and target sheets is used during the IPB and the war-game processes. Both tools are developed by the G2 all-source production section. Both are discussed in detail in Appendix A.
TVA is a detailed analysis of the enemy in selected COAs. The TVA uses the following enemy characteristics:
- Doctrine.
- Tactics.
- Equipment.
- Organizations.
- Expected behavior.
The TVA methodology provides a relative ranking of target sets, or categories. It begins when the target analyst in the G2 or S2 places himself in the position of the enemy commander. The target analyst, in coordination with other staff members, war-games the operation.
During war gaming, alternative friendly COA are analyzed in terms of their impact on enemy operations and likely responses. The enemy battlefield functions that must be attacked to force the best enemy response are identified. The commander and his staff analyze the criticality of friendly battlefield functions with regard to a specific COA. The best places to attack HPTs in relation to the friendly COA are identified. These places are called target areas of interest (TAIs). TAIs are points or areas where the friendly commander can influence the action by lethal and/or nonlethal fires and/or maneuver. Decision points (DPs) or decision time phase lines are used to ensure that the decision to engage or not to engage occurs at the proper time. DPs and TAIs are recorded on the G3's decision support template (DST). The purpose of war gaming is to finalize individual staff estimates and to develop all of the following:
- Scheme of maneuver.
- Fire support plan.
- Friendly DSTs.
War gaming also identifies HVTs in priority that are critical to the success of the enemy mission. In addition, it identifies the subset of HVTs which must be acquired and attacked for the friendly mission to succeed. The subset is the HPTs.
The G3 or S3 normally leads the war game and role-plays the friendly COA. He establishes the technique and recording method for the war game. The G2 or S2 role-plays the enemy's most dangerous and likely COAs by using enemy doctrine and tactics. When available, the G5 or S5 war-games the civilian COAs. The deputy FSCOORD or FSO advises the G3 on using available fire support systems and records the needs for fire support. He also uses the war game to determine adequacy of fire support. He works with the G2 or S2 to ensure fill use of fire support target acquisition assets in the intelligence collection plan. The air liaison officer (ALO) and deputy or assistant aviation officer advise on availability and employment of air assets. They identify necessary airspace coordination measures. Other key staff officers who may not participate full time in the war game but who should be consulted consist of the following:
- Logistics officer for supportability considerations.
- Engineer officer for mobility, countermobility, and survivability considerations.
- Air defense officer (ADO) for force protection.
Input from the rest of the staff achieves a complete analysis of the impact of all BOSs. This ensures the AGM is synchronized with the DST, and selection of HPTs are supported by PIR and the intelligence collection taskings.
Target Selection
The staff war-games different COAs to develop the HPTs. As each friendly option is war-gamed by the staff the G2 or S2 identifies HVTs from which the staff nominates HPTs. The HPTs are targets which are critical to friendly success. Targets that can be acquired and attacked are candidates for the HPTL. Targets that need outside acquisition or attack are sent to higher headquarters. The key to HPTs is that they are critical to the enemy commander's needs (HVTs) and the friendly concept of the operation. They also support the friendly force commander's scheme of maneuver and intent. HFTs that need BDA are identified during the war game. The ACE collection manager helps identify and task the sensors needed for collection of the HPTs. The collection manager can determine the best sensor and its availability by referencing the intelligence synchronization matrix (ISM). Detailed discussion of the ISM is contained in FM 34-2.
Sensor/Attack Systems Matrix
The sensor/attack (atk) systems matrix is a targeting tool that can be used to determine whether the critical HVTs can be acquired and attacked. This matrix allows war-game participants to record their assessment of the ability of sensor systems to acquire and attack systems to attack HVTs at a critical event or phase of the battle.
|
Note: There is no horizontal linear relationship between the sensor systems and the attack systems. A more detailed discussion of specific sensor and attack systems is contained in Appendix B. |
Marginal information at the top of the matrix has blanks for the battlefield event being assessed and the associated HVTs. Blank spaces for entry, by G2 plans, of available sensor systems are on the left. On the other side are spaces for entry, by G3 plans, of available attack systems. The war-game participants annotate systems selected for use by marking the appropriate block with an S for sensor and A for attack.
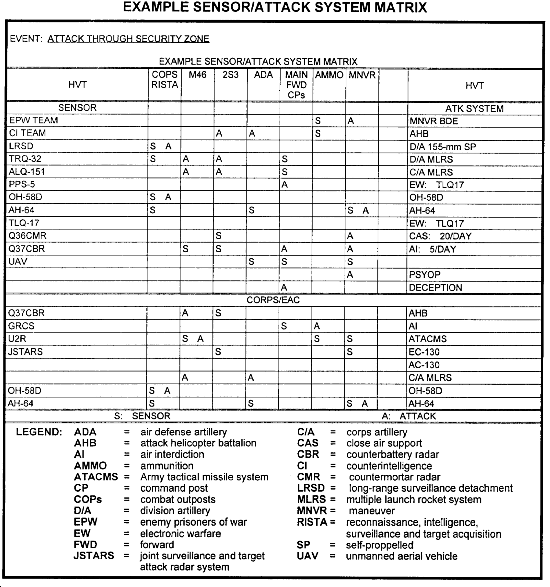
As the war game progresses from one phase to the next, the ability of sensor and attack systems to perform each task is determined. If they cannot, they must be moved or an alternate system selected. If no system is available within the command, support must be requested from higher headquarters. Following is an example of how the sensor/attack systems matrix may be used.
The example assesses the ability of sensor and attack systems of a heavy division to acquire and attack HVTs of a threat division in deliberate defense. The event is assessed in the friendly force attack through the enemy 15 kilometer (km) deep security zone.
The HVTs listed at the top can be detailed or general, depending on the time available and the needs of the commander. In this example, the G2 identified the RISTA and COPs of the security zone as HVTs. In the main defense echelon, he identified the 2S3 152-mm self-propelled gun/howitzers, M46 130-mm guns, AD systems, command posts, ammunition, and maneuver elements.
Positioning of sensor and attack systems in time and space is critical to get the necessary depth of coverage and to maintain survivability. As the attack progresses, moving the sensor and attack systems for continuous support of the maneuver units presents a synchronization challenge.
In this example, all of the HVTs can be acquired and attacked. However, attack of the ammunition stockpiles projected to be in the area must be done by air interdiction. This means the division must nominate the stockpiles as an HPT to corps to be included in the air tasking order (ATO). When or where the division will acquire this target is not known. However, coordination with corps is required now if attack of the target is critical to success.
The matrix lets the G2 identify possible taskings of assets like long-range surveillance teams. Their mission in the example is to acquire the RISTA and COPS in the security zone. The OH-58D scout helicopter may also be tasked for this purpose. The FSCOORD can direct the AN/TPQ-36 and AN/TPQ-37 Firefinder radars to acquire the 2S3 and M46 artillery systems. However, some enemy artillery may not be in range for the Firefinders. Support may be needed from corps or higher. The FSCOORD identifies which targets his echelon can attack and which he must send to corps.
The matrix separates division-controlled assets from corps and echelons above corps (EAC) assets which can sense or attack targets in the division area. This helps the G2 and FSCOORD coordinate with higher headquarters.
Information from the sensor/attack systems matrix helps the staff develop the HPTL and AGM and provide targeting input to the intelligence collection plan. HPTs are identified and the means to acquire them are determined. The effects desired are established. The attack systems to provide the desired effects are selected. Time of target attack is determined on the basis of the commander's concept of the operation, war gaming, and friendly system availability. Coordination measures are established to control potential fratricide situations. The HPTL, AGM, and intelligence collection plan are developed for each phase or critical event of the battle.
High-Payoff Target List
The HPTL depicted in the figure below identifies the HPTs for a phase in the battle in the order of their priority. The example is not a prescribed format. Target value is usually the greatest factor contributing to target payoff. However, other things to be considered include the following:
- The sequence or order of appearance.
- The ability to detect identify, classify, locate, and track the target. (This decision must include sensor availability and processing time-line considerations.)
- The degree of accuracy available from the acquisition system(s).
- The ability to engage the target.
- The ability to suppress, neutralize, or destroy the target on the basis of attack guidance.
- The resources required to do all of the above.
Targets are prioritized according to the considerations above within specific time windows. The targeting team sets priorities for the targets according to its judgment and the advice of the FSE target analysts and the FAIO. Target spread sheets give a recommended priority and attack sequence. If the target spread sheet or war gaming departs from the commander's guidance, it is noted on the proposed HPTL to inform the commander of the conflict. The target category of the HPT is shown, either by name or by number, on the list. The category name and number are shown on the target spread sheet. The number of target priorities should not be excessive. Too many priorities will dilute the intelligence collection acquisition and attack efforts. The approved list is given to the operations, intelligence, and fire support cells. It is used as a planning tool to determine attack guidance and to refine the collection plan. This list may also indicate the commander's operational need for BDA of the specific target and the time window for collecting and reporting it.
|
NOTE: Any format which serves the purpose of an HPTL maybe used. |
Intelligence Collection Plan
The G2 or S2 develops collection strategies that support the commander's concept of operations with available resources. Collection management orchestrates the intelligence system of systems to focus the intelligence effort in support of warfighting and operations other than war (OOTW). If BDA is needed, collection is planned to satisfy that requirement as well.
The collection plan provides a framework that collection managers use to determine, evaluate, and satisfy intelligence needs. Because of the diversity of missions, capabilities, and requirements, the collection plan has no prescribed doctrinal format. However, a dynamic collection plan should--
- Have as its basis the commander's priority intelligence requirements, to include those HPTs approved as PIRs.
- Help the commander see his area of interest.
- Provides synchronized coverage of the commander's area of operations.
- Have a five-dimensional battlefield approach: width, length, depth or altitude, time, and electromagnetic spectrum.
- Cover the collection capabilities of higher and adjacent units. Identify assets for acquiring and tracking HPTs and determining BDA on HPTs.
- Be flexible enough to allow response to changes as they occur.
- Cover only priority requirements.
- Be a working document.
- Contain precise and concise information.
The intelligence collection plan work sheet is a valuable aid in planning and directing the collection effort. For many needs, particularly those concerned with enemy capabilities and vulnerabilities, a written collection work sheet is advisable. The detail in which it is prepared, however, depends on the needs and coordination needed during the collection effort.
The selection of a format for the work sheet is based on the needs and resources available for collection management. However, the format selected must follow the logical sequence of collection management described in FM 34-2, Chapter 3. In addition, the plan must be easily adjustable to changing needs, situations, and missions. FM 34-2, Appendix A provides several recommended formats.
At division level and above, collection planning is complex. The PIRs of division and corps commanders often require in-depth analysis. Coordination of the overall collection effort is a major undertaking. For that reason, written collection work sheets prepared at these echelons are detailed.
At battalion and brigade, the collection plan work sheet is informal. It may consist of a list of available collection means plus brief notes on current intelligence requirements and specific formation to collect. The collection requirements are incorporated into the reconnaissance and surveillance plan. (See FM 34-2-1.)
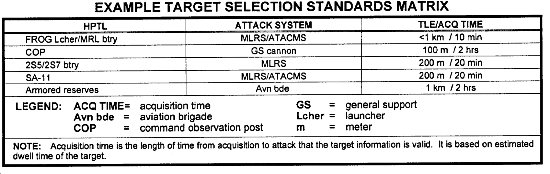
Target Selection Standards
TSS are criteria, applied to enemy activity (acquisitions and battlefield information), used in deciding whether the activity is a target. TSS break nominations into two categories: targets and suspected targets. Targets meet accuracy and timeliness requirements for attack. Suspected targets must be confirmed before any attack.
TSS are based on the enemy activity under consideration and available attack systems by using the following:
- Attack system target location accuracy requirements (target location error [TLE]).
- Size of the enemy activity (point or area).
- Status of the activity (moving or stationary).
- Timeliness of the information.
Considering these factors, different TSS may exist for a given enemy activity on the basis of different attack systems. For example, an enemy artillery battery may have a 150-meter TLE requirement for attack by cannon artillery and a 1 km requirement for attack helicopters. TSS are developed by the FSE in conjunction with the military intelligence personnel. Intelligence analysts use TSS to quickly determine targets from battlefield information and pass the targets to the FSE. Attack system managers such as FSEs, fire control elements (FCEs) or fire direction centers (FDCs), use TSS to quickly identify targets for attack. Commands can develop standard TSS based on anticipated enemy order of battle and doctrine matched with the normally available attack systems.
TSS are given to the G2 or S2 by the FSE. Intelligence analysts use TSS to identify targets that are forwarded to an FSE. Intelligence analysts evaluate the source of the information as to its reliability and accuracy, confirm that the size and status of the activity meet the TSS, and then compare the time of acquisition with the dwell time.
|
NOTE: Dwell time is the length of time a target is doctrinally expected to remain in one location. |
Accurate information from a reliable source must be verified before declaring it a target if the elapsed time exceeds dwell time.
The G2 or S2 knows the accuracy of acquisition systems, associated target location error (TLE), and the expected dwell times of enemy targets. He can then specify whether information he reports to the attack system manager is a target or a suspected target. Some situations may require the system to identify friendly and neutral from threat before approval to fire is given. High-payoff targets that meet all the criteria should be tracked until they are attacked in accordance with the AGM. Location of targets that do not meet TSS should be confirmed before they are attacked. The TSS can be graphically depicted in a TSS matrix as shown in the figure below.
The matrix lists each system that forwards targets directly to the FSE, FCE, or FDC. The effects of weather and terrain on the collection assets and on enemy equipment are considered. TSS are keyed to the situation. However, the greatest emphasis is on the enemy situation, considering deception and the reliability of the source or agency that is reporting.
Attack Guidance
Knowing target vulnerabilities and the effect an attack will have on enemy operations allows a staff to propose the most efficient available attack option. Key guidance is whether the commander wishes to disrupt delay, limit damage, or destroy the enemy. During war gaming decision points linked to events, areas (NAIs and TAIs), or points on the battlefield are developed. These decision points cue the command decisions and staff actions where tactical decisions are needed.
On the basis of commander's guidance, the targeting team recommends how each target should be engaged in terms of the effects of fire and attack options to use. Effects of fire can be to harass, suppress, neutralize, or destroy the target. The subjective nature of what is meant by these terms means the commander must ensure the targeting team understands his use of them. Application of fire support automation system default values further complicate this understanding.
- Harassing fire (JP 1-02) is fire designed to disturb the rest of enemy troops, to curtail movement and, by the threat of losses, to lower morale. The decision to employ harassing fires needs careful consideration. Harassing fire has little real effect on the enemy, subjects gun crews to an additional workload and increases the threat of counterbattery fires. Rules of engagement and/or the potential for adverse public opinion may prohibit the use of harassing fires. However, harassing fires may be a combat multiplier in some situations. Consider their use in military operations other than war, delaying actions, and economy of force operations.
- Suppression fires (JP 1-02) are fires on or around a weapons system, to degrade its performance below the level needed to fulfill its mission objectives. Suppression lasts only as long as the fires continue. The duration of suppression fires is either specified in the call for fire or established by standing operating procedures (SOP). Suppression is used to prevent effective fire on friendly forces. It is typically used to support a specified movement of forces. Use of one round volleys to suppress a target is normally insufficient to provide suppression for an action or move that lasts more than a few minutes. The FSCOORD needs to ask or calculate the when and how long questions.
- Neutralization fires (JP 1-02) are delivered to render the target ineffective or unusable for a temporary period. Neutralization fire results in enemy personnel or material becoming incapable of interfering with an operation or COA. Key questions the FSCOORD must ask are when and how long does the commander want the target to be neutralized. Most planned missions are neutralization fires.
- Destruction fires physically render the target permanently combat-effective or so damaged that it cannot fiction unless it is restored, reconstituted, or rebuilt. Setting automated fire support default values for destruction of 30 percent does not guarantee the achievement of the commander's intent. The surviving 70 percent may still influence the operation. Destruction missions are expensive in terms of time and material. Consider whether neutralization or suppression may be more efficient.
The decision of what attack system to use is made at the same time as the decision on when to acquire and attack the target. Coordination is required when deciding to attack with two different means (such as EW and combat air operations). Coordination requirements are recorded during the war-game process.
The attack guidance, as recommended by the targeting team, must be approved by the commander. This guidance should detail the following:
- A prioritized list of HPTs.
- When, how, and desired effects of attack.
- Any special instructions.
- HPTs that require BDA.
This information is developed during the war game. Attack guidance applies to both planned targets and targets of opportunity. Accordingly, attack guidance may address specific or general target descriptions. Attack guidance is provided to attack system managers via the attack guidance matrix.
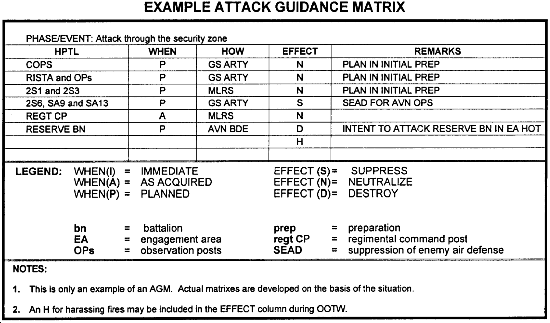
Attack Guidance Matrix
The AGM consists of columns for the following:
- Target categories.
- Specific HPTs.
- Timing of attack.
- How targets are attacked.
- Restrictions.
An example of an AGM is shown below.
HPT List Column
This column lists the prioritized HPTs identified during war gaming. They have priority for engagement.
WHEN Column
Timing the attack of targets is critical to maximizing the effects. During war gaming, the optimum time is identified and reflected in the WHEN column. A P indicates that the target should not be engaged now but should be planned for future firing (for example, a preparation, a SEAD program, or a countermobility program) or simply should be put on file. An A stands for as acquired. Such targets should be engaged in the sequence that they are received in the headquarters, with respect to the priority noted in the HPT list. An I indicates the attack must be immediate and is a special case. This designation should be limited to a very small percentage of targets and only for the most critical types. Too many immediate targets are disruptive and lower the efficiency of attack systems. Immediate attacks take precedence over all others and are conducted even if attack systems must be diverted from attacks already underway. Some examples of very important targets include:
- Missile systems capable of nuclear, biological, and chemical (NBC) attacks.
- Division headquarters.
- NBC weapons storage and support facilities.
Multiple rocket launchers may be considered for immediate attack depending on their demonstrated effectiveness against friendly forces and their tactical employment. The G3 or S3 and FSCOORD or FSO must establish procedures within the TOC that allow for immediate attack of targets.
HOW Column
The HOW column links the attack system to the HPT. It is best to identify a primary and backup attack system for attack of HPTs.
EFFECTS Column
Effects refers to the target attack criteria. The targeting team should specify attack criteria according to the commander's general guidance. Target attack criteria should be given in quantifiable terms (for example, as a percentage of casualties or destroyed elements, time, ordnance, and allocation or application of assets). Also, it can be noted as the number of battery or battalion volleys.
REMARKS Column
Some examples of how this column should be used are:
- Note accuracy or time constraints.
- Note required coordination.
- Limitations on the amount or type of ammunition.
- Any need for BDA.
This column should note which targets should not be attacked in certain tactical situations (for example, targets not to be attacked if the enemy is withdrawing).
As the operation progresses through time, the AGM may change. The AGM is a tool that must be updated on the basis of the changing enemy situation. It should be discussed and updated during routine staff planning meetings. Consider separate AGMs for each phase of a phased operation.
Formats
The formats for the HPTL, TSS, and AGM presented in the preceding paragraphs are examples only. Targeting personnel must understand all the considerations that are involved in building these targeting tools. However, experienced staffs may prefer to develop their own formats tailored for their situation. Alternative formats are provided in Appendix C.
DETECT
Detect is the next critical function in the targeting process. The G2 or S2 is the main figure in directing the effort to detect HPTs identified in the decide function. To identify the specific who, what, when, and how for target acquisition, the G2 or S2 must work closely with all of the following:
- Analysis and control element (ACE).
- FAIO.
- Targeting officer and/or FSO.
This process determines accurate, identifiable, and timely requirements for collection systems. The ACE targeting section is responsible for ensuring that the collection system asset managers understand these requirements.
Information needs for target detection are expressed as PIR and/or IR. Their relative priority depends on the importance of the target to the friendly scheme of maneuver and tracking requirements coupled with the commander's intent. PIR and IR that support detection of HPTs are incorporated into the overall collection plan of the unit.
Targets are detected by the maximum use of all available assets. The G2 or S2 must focus the intelligence acquisition efforts on the designated HPTs and PIR. Situation development information, through detection and tracking, will be accumulated as collection systems satisfy PIRs and IRs. The collection manager considers the availability and capabilities of all collection assets within his echelon and those available to subordinate, higher, and adjacent units. He must also consider joint or combined force assets. He translates the PIR and IR into specific information requirements (SIR) and specific orders and requests (SOR). If possible, he arranges direct dissemination of targeting information from the collector to the targeting cell or targeting intelligence to the fire support element.
Detection Procedures
It is essential that all TA assets be used effectively and efficiently. Duplication of effort among available assets must be avoided unless it is required to confirm target information. At corps and division, the ACE develops and manages the collection plan to avoid duplication. At the same time, the ACE ensures that no gaps in planned collection exist. This allows timely combat information to be collected to answer the commander's intelligence and TA requirements. This information lets analysts develop the enemy situation and identify targets.
Desired HPTs must be detected in a timely, accurate manner. Clear and concise taskings must be given to the TA systems that can detect a given target. Mobile HPTs must be detected and tracked to maintain a current target location. Target tracking is inherent to detection. The FS cell tells the G2 or S2 the degree of accuracy required and dwell time for a target to be eligible for attack. The G2 or S2 must match accuracy requirements to the TLE of the collection systems. If the target type and its associated signatures (electronic, visual, thermal, and so forth) are known, the most capable collection asset can be directed against the target. The asset can be placed in the best position according to estimates of when and where the enemy target will be located.
As the assets collect information for target development, it is forwarded to the intelligence analysts of the ACE. They use the information in performing situation and target development. When a target specified for attack is identified by the analysts, it is passed to the FSE. The FSE executes the attack guidance against the target. Close coordination among the intelligence staff and the FSE is essential to ensure that the targets are passed to an attack system that will engage the target. To ensure the exchange is timely, the FAIO must have access to the ACE. The FAIOs can coordinate with the G2s and FSEs to pass HPTs and other targets directly to the FCE at the division artillery (div arty) TOC or, if approved by the maneuver commander, directly to a firing unit. The result is an efficient attack of targets which have been designated in advance for attack. Some units have found it advantageous to locate the FAIO in the ACE with communications to the FSE. When the FAIO gets intelligence information which warrants attack, he notifies the FSE. This allows the FAIO to focus on intelligence information analysis and the FSE to manage the control of fires. The targeting officer at the maneuver brigade and the S2 at battalion perform FAIO functions.
Tracking is an essential element of the detect function of the targeting process. Tracking priorities are based on the commander's concept of the operation and targeting priorities. Tracking is executed through the collection plan. Not all targets will be tracked. However, many critical targets move frequently or constantly. As such, these HPTs require tracking.
Synchronization of Intelligence Collection
During the conduct of operations, the G2 or S2 monitors execution of the collection plan. He uses an ISM to ensure the intelligence system gives answers to intelligence requirements in time to affect the decisions they support. As HPTs are identified, he informs the appropriate FSE and cross-cues collection assets to support BDA as needed.
During delivery, near real time collectors and observers are cued to continue tracking targets during their engagement. Planned or cued BDA collection and reporting helps determine if the engagement produced the desired effects. If it did not, continued tracking supports immediate reengagement.
To facilitate hand-off of target and tracking responsibilities, the G2 or S2 coordinates with higher and subordinate units. Requirements for intelligence in a given area can then be directed to the unit with responsibility for that area. Operational graphics are very useful when tracking particular threat units or HPTs. Passing responsibility for the target as it crosses the graphic ensures that it is not lost in crossing.
Synchronization continues during the collection management process. The G2 or S2 uses the products of the targeting process to develop SIR and SOR that synchronize the collection effort with the decision points of the command. He plans and allocates time for collection, processing, and dissemination.
During execution, the collection manager monitors the collection and reporting to ensure synchronization. He prompts asset managers to meet time-lines, cross-cueing and retasking as necessary to keep intelligence operations synchronized with the operations of the command.
Essential Target Information
Targets and suspected targets may be passed to the targeting team by a number of means. It is important that the essential information be passed for proper analysis and attack to take place. As a minimum, the target report must include the following:
- Reporting agency.
- Date-time group (DTG) of acquisition by the sensor.
- Description of the activity.
- Size of the target.
- Target location and altitude.
- TLE.
- Dwell time.
- Status (stationary or moving).
The DTG is important as the dwell time of the target is analyzed. The dwell time of the target determines whether or not to attack on the basis of the likelihood of the target having moved.
The target description and size are compared with the AGM. Description should include posture (dug-in or in the open) and activity (moving or stationary). This information is used to determine the following:
- Attack means.
- Intensity of attack.
- Number of assets to be committed.
- Other technical considerations.
The target location must be given as accurately as possible within the confines of timeliness. The targeting team can request TLE for a target on the basis of the attack criteria. However, a sensor may report a target with a large TLE. The target will still be processed and the team will determine whether to engage the target and by what means.
DELIVER
The deliver function of the targeting process executes the target attack guidance and supports the commander's battle plan once the HPTs have been located and identified.
Attack of Targets
The attack of targets must satisfy the attack guidance developed in the decide function. Target attack requires several decisions and actions. These decisions fall into two categories--tactical and technical.
Tactical decisions determine the following:
- The time of the attack.
- The desired effect, degree of damage, or both.
- The attack system to be used.
On the basis of these tactical decisions, the technical decisions describe the following:
- Number and type of munitions.
- Unit to conduct the attack.
- Response time of the attacking unit.
These decisions result in the physical attack of the targets by lethal and/or nonlethal means.
Tactical Decisions
Time of Attack
The time of attack is determined according to the type of target-planned target or target of opportunity.
Planned Targets
Some targets will not appear as anticipated. Target attack takes place only when the forecasted enemy activity occurs in the projected time or place. The detection and tracking of activities associated with the target becomes the trigger for target attack. Once the designated activity is detected the targeting team does the following:
- The G2 verifies the enemy activity as the planned target to be attacked. This is done by monitoring decision points and TAIs/NAIs associated with HPTs.
- The G2 validates the target by conducting a final check of the reliability of the source and the accuracy (time and location) of the target. Then he passes the target to the FSE.
- The current operations officer checks the legality of the target in terms of the rules of engagement (ROE).
- The FSE determines if the attack system(s) planned is available and still the best system for the attack.
- The FSE coordinates as required with higher, lower, and adjacent units, other services, allies, and host nation. This is particularly important where potential fratricide situations are identified.
- The FSE issues the fire mission request to the appropriate executing unit(s).
- The FSE informs the G2 of target attack.
- The G2 alerts the appropriate system responsible for BDA (when applicable).
Targets of Opportunity
High-payoff targets of opportunity are processed the same as planned HPTs. Targets of opportunity not on the HPTL are first evaluated to determine when or if they should be attacked. The decision to attack targets of opportunity follows the attack guidance and is based on a number of factors such as the following:
- Activity of the target.
- Dwell time.
- Target payoff compared to other targets currently being processed for engagement.
If the decision is made to attack immediately, the target is processed further. The availability and capabilities of attack systems to engage the target are assessed. If the target exceeds the capabilities or availability of the unit attack systems, the target should be sent to a higher headquarters for immediate attack. If the decision is to defer the attack, continue tracking, determine decision point(s) for attack, and modify collection taskings as appropriate.
Desired Effects
Effects of fires can only be properly assessed by an observer or with an analysts. At brigade and TF, it is important that each target has a primary and alternate observer. The observers must understand the desired effects, when and for how long they are required. When in doubt about the commander's intent, ask--never assume. Emphasis on this issue during training will enhance the effectiveness and efficiency of fire support.
Attack System
The last tactical decision to be made is the selection of the appropriate attack system. For planned targets, this decision should have been made during the decide function of the targeting process. A check must be made to ensure that the selected attack system is available and can conduct the attack. If not, the targeting team must determine the best system available to attack the target.
The targeting team must always determine the attack system for targets of opportunity, subject to the maneuver commander's approval. All available attack assets should be considered. Attacking targets should optimize the capabilities of:
- Light and heavy ground forces.
- Attack helicopters.
- Field artillery.
- Mortars.
- Naval gunfire.
- Combat air operations (both CAS and AI).
- Offensive electronic warfare.
More information on attack assets is provided at Appendix B. The availability and capabilities of each resource is considered using the following:
- Desired effects on the target.
- Payoff of the target.
- Degree of risk in the use of the asset against the target.
- Impact on friendly operations.
In some cases, the target attack must be coordinated among two or more attack systems. Engagement of a target by lethal means along with jamming or monitoring may be of greater benefit than simply firing at the target.
Technical Decisions
Once the tactical decisions have been made, the FS cell directs the attack system to attack the target. The FS cell provides the attack system manager with the following:
- Selected time of attack.
- Effects desired in accordance with previous discussion.
- Any special restraints or requests for particular munitions types.
The attack system manager (FSCOORD, ALO, avn bde LO, NGLO, and so on) determines if his system can meet the requirements. If his system is unable to meet the requirements, he notifies the FS cell. There are various reasons an attack system may not be able to meet the requirements. Some are:
- System not available at the specified time.
- Required munitions not available.
- Target out of range.
The FS cell must decide if the selected system should attack under different criteria or if a different system should be used.
ASSESS
Combat assessment (CA) is the determination of the effectiveness of force employment during military operations.
CA is composed of three elements:
- BDA.
- Munitions effects assessment (MEA).
- Reattack recommendation.
In combination BDA and MEA, inform the commander of effects against targets and target sets. On the basis of this information, the threat's ability to make and sustain war and centers of gravity are continuously estimated. During the review of the effects of the campaign, restrike recommendations are proposed or executed. BDA is the timely and accurate estimate of damage resulting from the application of military force, either lethal or nonlethal, against a target. BDA in the targeting process pertains to the results of attacks on targets designated by the commander. Producing BDA is primarily an intelligence responsibility, but requires coordination with operational elements to be effective. BDA requirements must be translated into PIRs. BDA accomplishes the following purposes:
- At the tactical level, commanders use BDA to get a series of timely and accurate snapshots of their effect on the enemy. It provides commanders an estimate of the enemy's combat effectiveness, capabilities, and intentions. This helps commanders determine when or if their targeting effort is accomplishing their objectives.
- As part of the targeting process, BDA helps to determine if restrike is necessary. Commanders use this information to allocate or redirect attack systems to make the best use of available combat power.
The G3 through the targeting team, conducts MEA concurrently and interactively with BDA as a function of CA. MEA is an assessment of the military force in terms of the weapon systems and munitions effectiveness. This assessment is used as the basis of recommendation for changes to increase the effectiveness of the following:
- Methodology.
- Tactics.
- Weapon system.
- Munitions.
- Weapon delivery parameters.
The G3 develops the MEA by determining the effectiveness of munitions, weapons systems, and tactics. Munitions effect on targets can be calculated by obtaining rounds fired on specific targets by artillery assets. The targeting team may generate modified commander's guidance to the G4 concerning the following:
- Unit basic load (UBL).
- Required supply rate (RSR).
- Controlled supply rate (CSR).
The need for BDA for specific HPTs is determined during the decide function in the targeting process. BDA requirements should be recorded on the AGM and the intelligence collection plan. Commanders must be aware that resources used for BDA are the same resources used for target development and acquisition. The commander's decision must be made with the realization that an asset used for BDA may not be available for target development and acquisition. BDA information is received and processed by the ACE, the results of attack are analyzed in terms of desired effects. The results are disseminated to the targeting team. The targeting team must keep the following BDA principles in mind:
- BDA must measure things that are important to commanders, not make important the things that are easily measurable.
- BDA must be objective. When a G2 or S2 receives a BDA product from another echelon, he should verify the conclusions (time permitting). G2s and S2s at all echelons must strive to identify and resolve discrepancies between the BDA analyst at different headquarters.
- The degree of reliability and credibility of the assessment relies largely upon collection resources. The quantity and quality of collection assets influence whether the assessment is highly reliable (concrete, quantifiable, and precise) or has low reliability (best guess). The best BDAs use more than one collection discipline to verify each conclusion.
Each BDA has three components. They are:
- Physical damage assessment.
- Functional damage assessment.
- Target system assessment.
These three different assessments require different sensors, analytical elements, and time-lines. They are not necessarily subcomponents of each BDA report.
Physical Damage Assessment
Physical damage assessment estimates the quantitative extent of physical damage through munitions blast, fragmentation, and/or fire damage effects to a target. This assessment is based on observed or interpreted damage.
Functional Damage Assessment
Functional damage assessment estimates the effect of attack on the target to perform its intended mission compared to the operational objective established against the target. This assessment is inferred on the basis of all-source intelligence and includes an estimate of the time needed to replace the target function. A functional damage assessment is a temporary assessment (compared to target system assessment) used for specific missions.
Target System Assessment
Target system assessment is a broad assessment of the overall impact and effectiveness of all types of attack against an entire target systems capability; for example, enemy ADA systems. It may also be applied against enemy unit combat effectiveness. A target system assessment may also look at subdivisions of the system compared to the commander's stated operational objectives. It is a relatively permanent assessment (compared to a functional damage assessment) that will be used for more than one mission.
BDA may take different forms besides the determination of the number of casualties or the amount of equipment destroyed. Other information of use to the targeting team includes the following:
- Whether the targets are moving or hardening in response to the attack.
- Changes in deception efforts and techniques.
- Increased communication efforts as the result of jamming.
- Whether the damage achieved is affecting the enemy's combat effectiveness as expected.
Damage assessments may also be passive by compiling information in regards to a particular target or area. An example is the cessation of fires from an area. If BDA is to be made, the targeting team must give intelligence acquisition systems enough adequate warning for sensor(s) to be directed at the target at the proper time.
BDA results may change plans and earlier decisions. The targeting team must periodically update the decisions made during the decide function concerning the following:
- IPB products.
- HPTL.
- TSS.
- AGM.
- Intelligence collection plan.
- Operations plan.
On the basis of the BDA and MEA analysis, the G2 and G3 consider the level to which operational objectives have been achieved and make recommendations to the commander. Reattack and other recommendations should address operational objectives relative to the following:
- Target.
- Target critical elements.
- Target systems.
- Enemy combat force strengths.
A targeting checklist covering the decide, detect, deliver, and assess methodology is at Appendix D.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|