FM 6-20-10: Tactics, Techniques, and Procedures for The Targeting Process
APPENDIX A
INTELLIGENCE PREPARATION OF THE BATTLEFIELD AND TARGET VALUE ANALYSIS
IPB considers terrain, weather, enemy doctrine, and current enemy actions to arrive at enemy COAs. TVA is a methodology which concurrently identifies potential HVT sets within a given tactical situation. It further develops the HVTs to produce the HPTL, TSS, and the AGM.
THE IPB PROCESS
IPB can be best described as the process of understanding the battlefield, the enemy, and the options presented. The objective of IPB is the early identification of probable courses of enemy action. It is a continuous, systematic, labor-intensive process. It begins with analysis of enemy doctrine and capabilities in a geographical area, the terrain, and the effects of weather on that terrain. The products of IPB are graphic overlays and templates used to visualize and predict enemy intentions.
Evaluating the threat in the IPB process uses doctrinal templates that convert enemy order of battle (OB) to graphics. The graphics aid in TVA and initial identification of potential HVTs. HVTs are assets the enemy commander needs for successful completion of his mission. Situation templates help in refining HVTs for specific battlefields and enemy COA. Concurrent with development of the situation template is an examination of enemy decision points and/or critical nodes as a part of each COA. The examination shows what might happen if the enemy commander's plan fails and what actions make up his failure options. Evaluation of enemy COA leads to identification of critical enemy functions in each COA and the HVTs associated with each function. Applying the IPB process helps the commander selectively apply and maximize his combat power at critical points in time and space. It does this by describing the battlefield environment, how the environment affects his unit and his adversary, and what the likely COA will be. Situational templates support the development of event templates. Event templates help identify critical enemy activities. It also identifies NAIs where specific enemy activities or events will help confirm or deny the adoption of a particular COA. Potential HPTs are identified. HPTs are those HVTs that must be attacked to give the commander a significant advantage in defeating the enemy. This work is further analyzed in the war-gaming process.
The single-source analysis element of the ACE at corps and division main CPs perform the initial EPB in support of the G2 IPB effort. The initial EPB is passed to the MI unit technical control element. The ACE expands and correlates the EPB with technical data such as call signs and frequencies. The EPB examines the association of specific emitters with identified units. It also checks the electronic line of sight from these emitters to potential locations for friendly EW assets. The result of EPB is the identification of targets that are important to the enemy operation which can be influenced with available EW assets. An example is a specific analysis of enemy air defense systems that can effect aviation operations throughout the zone of action. It could result in a terrain-based product showing enemy radar profiles and the effect of geography and line of sight on engagement profiles.
IPB TARGETING PRODUCTS
The IPB process provides the commander and his staff with a basis for fire and maneuver decision making. In other words, a framework for deciding where and when to employ limited resources to achieve decisive results. It is a starting point for, and integral to, the targeting process. Enemy capabilities are evaluated from a doctrinal standpoint and in relation to the specific battlefield and friendly mission to produce the following graphic products:
- Doctrinal template.
- Situation template.
- Event template.
- DST.
Using these, the commander and staff can identify HVT and HPT as they enter the battle area.
Doctrinal Template
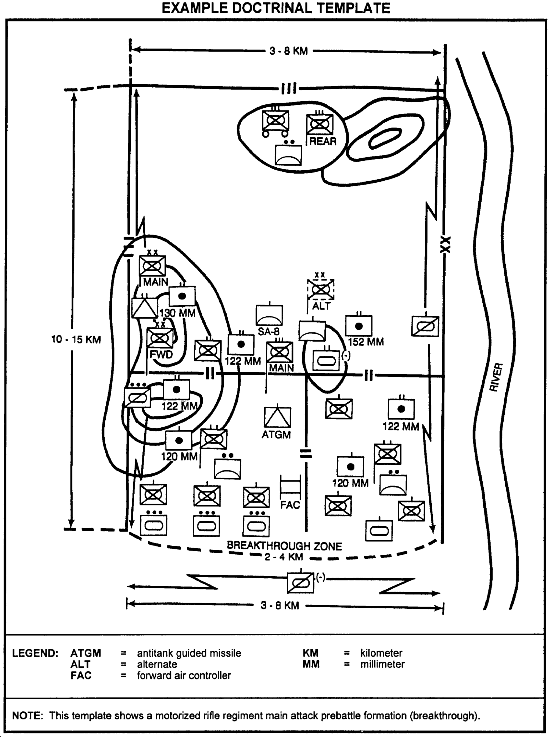
Situation template development begins with the doctrinal template. The template shows how enemy doctrine dictates their approach to a particular tactical situation, without terrain and weather constraints. A doctrinal template depicts unit composition, width, depth, organization, formation, and disposition. It aids analysts in determining the location of threat units, weapons, equipment, and boundaries when assessing the actual enemy force. It can also identify gaps in intelligence for the collection plan.
To the target producer, the primary importance of the doctrinal template is that it provides the basis for initial HVT category identification. It shows him the critical assets for each type of operation at each echelon of command by doctrine. From these he can draw his initial HVT categories.
Files of doctrinal templates can be developed to show enemy tactical doctrine for a variety of maneuvers on the basis of the current situation. They can be varied by echelon of unit depicted, and by COA or type of operation. (Example: a regiment or brigade conducting a hasty river crossing operation.) An example of a doctrinal template for a motorized rifle regiment (echelon) in prebattle formation (COA) is shown in the figure below.
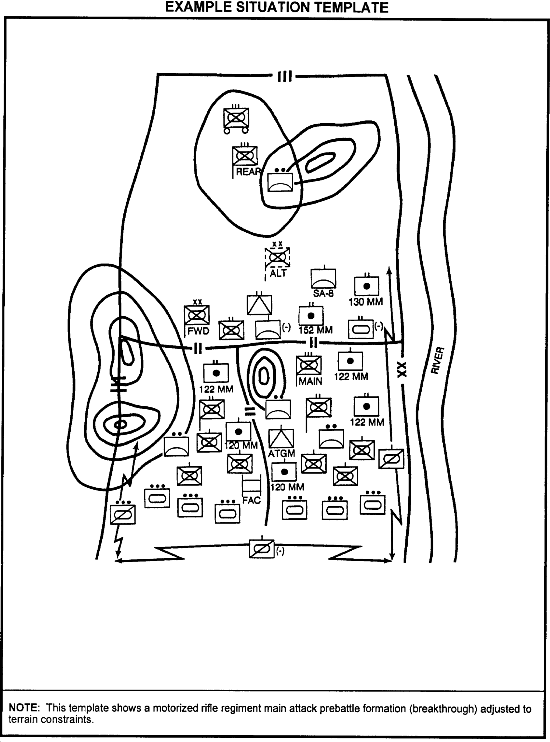
Situation Template
When adjusted for terrain and weather, the doctrinal template becomes a situation template. It shows how enemy forces might deviate from doctrinal tenets to accommodate the realities of geography or weather-generated obstacles. (The figure below shows the same motorized rifle regiment adjusted to terrain constraints.)
The situation template focuses on the enemy's activities within specific mobility corridors of an avenue of approach. It graphically represents how his formations might have to adjust to move, shoot, and communicate within the corridors.
When considering the intentions of the enemy, the analyst also war-games the enemy through COA, friendly reaction, and counteraction. The war-gaming process causes the situation template to change as the analyst projects the enemy arrays at various points in time and phases of the battle.
Event Template
Event templates identify and analyze significant battlefield events and activities which provide indicators of enemy COA. It facilitates comparing what we know the enemy can do with what he is doing, and thus predict what he will do next.
The S2 or G2 uses event template techniques to select critical areas on the battlefield for the collection plan, while eliminating less vital areas. It also allows for best use of collection assets by watching critical areas at critical times, rather than wasting assets during the wrong periods. (See the figure below.) (See explanation of NAI and time-phase lines (TPL).)
The event template also provides the S3 or G3 with useful information as he plans the battle. By projecting the most likely enemy COA, he can plan where, when, and what to shoot, jam, communicate, and maneuver against and what results to expect.
The event template is a critical step in the development of the final product of IPB--the DST.
The event template depicts NAI along each avenue of approach and mobility corridor and the relationship of events between separate avenues of approach and mobility corridors. It is used to analyze the sequence of events that should occur for each enemy COA and how they relate to one another. The event template is developed by war-gaming each enemy COA from the point where friendly or enemy activity begins to the final objectives.
An NAI is an area along an avenue of approach or mobility corridor where enemy activity (or lack of it) will confirm or deny a COA. Designating NAIs allows for observation of all the viable enemy options without wasting coverage on areas of little importance. NAIs frame significant military events not only by location, but by time.
TPLs are the analyst's estimate of the rate of advance (enemy or friendly) and help trace estimated FLOTs at any given time. During actual operations, TPLs are adjusted to reflect actual enemy and/or friendly movements in the given situation. From the targeting perspective, they help determine when HVTs and HPTs will be vulnerable to attack.
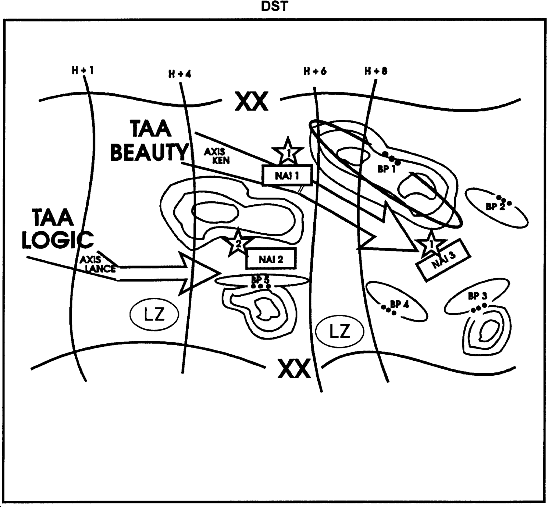
Decision Support Template
The DST is essentially a combined intelligence and operations estimate in graphic form. It relates the detail of the event template to decision points (DPs) that are significant to the commander. It identifies critical battlefield areas (including TAIs) and events and activities that require tactical decisions by time and location. (See explanations of TAI and DP.)
Although the DST is a total staff effort, it is essentially a product of the targeting triad--the S2 or G2, S3 or G3, and FSE and/or FSCOORD. It is updated throughout the war-gaming process.
A TAI is an engagement area where the interdiction of an enemy force by fire, maneuver, or jamming will reduce or deprive it of some capability. TAIs are usually avenues of approach or mobility corridors. Unlike the NAI, which is designated for watching enemy activity, the TAI is an area in which we wish to interdict enemy activity to cause him to abandon a particular COA. (Destruction is seldom a requirement for interdiction to be effective.) Examples of TAIs are--
- Bridges.
- Road junctions.
- Choke points.
- Drop zones and landing zones.
- Known fording sites.
- FARPs and rear area refueling and rearming points.
TAIs can indicate where HVTs and HPTs might be most vulnerable to attack. TAIs are normally associated with DPs.
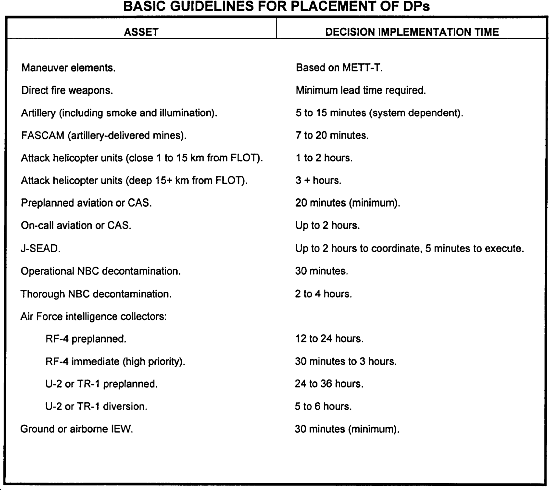
DPs are identified after TAIs are selected. They identify events, areas, and points on the battlefield, and where and when tactical decisions are required by the friendly commander. (They do not indicate what decision will be made.) They are selected according to options and assets available to the commander. Because they are time-sensitive, their determination must anticipate enemy movement rates and distances and times required to implement decisions. (See the table below.)
DSTs depict--
- TAIs.
- DPs.
- TPLs.
- Avenues of approach and mobility corridors.
- Objectives.
- Current enemy situation (from the current situation map [SITMAP] and situation templates).
The figure below shows an example of a DST.
THE TARGET VALUE ANALYSIS PROCESS
Given a selected COA and the input generated by the IPB process, target priorities can be developed. The TVA process identifies potential HVT sets associated with critical enemy functions that could interfere with the friendly COA or that are key to enemy success. The target priorities are used by both fire support and intelligence systems in their target attack and collection plans. The G2, G3, and FSCOORD participate in this process.
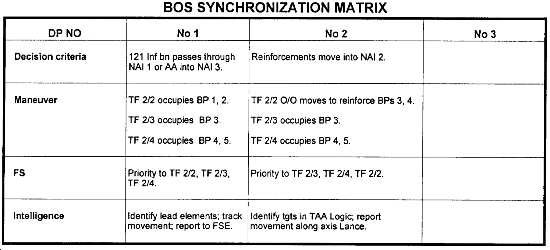
The DST is often associated with a BOS synchronization matrix. The battle staff then plans appropriate support from each BOS to support the commander's DPs and scheme of maneuver. An example of a partial BOS synchronization matrix is shown in the figure below.
TVA offers the combined arms commander the means to:
- Provide focus for his target acquisition effort.
- Identify priorities for the engagement of enemy targets that will facilitate the success of his mission.
- Identify effects criteria.
- Permit planning for identified contingencies based on enemy options available when the enemy operation fails.
- Better estimate friendly unit capabilities.
TARGET VALUE ANALYSIS SOURCES AND PRODUCTS
The TVA process draws on IPB products and other sources in the production of HVTs. Target spread sheets and target sheets provide the initial sources for TVA. The ultimate products of TVA are the HTPL, TSS, and the AGM.
High-value targets
Those assets the enemy commander requires for the successful completion of his mission are HVTs. The loss of HVTs would be expected to degrade important battlefield functions. HVT identification begins as early as the development of the doctrinal template.
Refinement takes place during the development of the situation template and the war-gaming process that goes along with it.
High-payoff targets
HVTs which, if successfully attacked, would contribute substantially to friendly operations are called HPTs. HPTs are developed from HVTs when the various COA are war-gamed. Developed on the basis of METT-T, their selection does not depend on unit ability to acquire or attack them. If it is beyond unit capability, they can be passed to the next-higher echelon as a priority intelligence requirement.
TARGET SPREAD SHEETS
Target spread sheets are an integral part of TVA. The majority of target spread sheets used today were prepared for a Warsaw Pact force in a european mid-to-high intensity conflict. However, the all-source production section (ASPS) target analyst can produce his own tailored to the threat he faces. Target spread sheets contain many IPB products already developed and can help in developing other IPB products during war-gaming.
The standard target spread sheet should contain the following as a minimum:
- Doctrinal template and resume. (See the discussion.)
- Failure option statement. (See the discussion.)
- Relative value matrix. (See the discussion.)
- Attack rationale column. (See the discussion.)
- Specific high-value targets. (See the discussion.)
The figures shown below are examples of the front and back sides of a target spread sheet. On one side of the spread sheet will be information about enemy forces at regiment, division, army, and front with respect to operations the forces are expected to conduct. On the other side will be a summary of information about the enemy's doctrine and tactics. This side explains how he is expected to fight, what he intends to accomplish, and what alternatives he has if he fails to accomplish his primary mission. The major sections shown on the example are:
- Title and sheet number (A).
- Doctrinal template (B).
- Doctrinal resume (C).
- Failure option statement (D).
- Relative value matrix (E).
- Attack rationale column (F).
- Specific HVTs (G).
Title and Sheet Number
These specify the tactical situation and enemy unit echelon for which the sheet was developed. The number refers to that specific situation-echelon combination for ease of access.
Doctrinal Template
This shows the major subunits of the enemy organization being considered deployed to scale, without regard to the effects of terrain and weather. Fire support personnel can use the template to begin planning acquisition coverage and likely areas of interest. However, the template is only a guide.
Doctrinal Resume
The doctrinal resume is a synopsis of the major features of the operation. This portion indicates the objectives of the enemy force and the tactical principles that govern how the unit is supposed to fight.
Failure Option Statement
The failure option statement lists the doctrinal courses of action the enemy can take if he fails in the situational option described. Analysts consider this as they war-game the enemy battle plan. Keep in mind that the options are doctrinal and could vary, depending on factors influencing the actual situation.
Relative Value Matrix
The relative value matrix lists 13 standard target sets or categories covering the major battlefield functions. All targets may be categorized in one of these groups. The 13 target sets are based on the battlefield functions discussed below.
C3
C3 stands for command, control, and communications centers. Generally, these are targets that affect maneuver or combined arms C3. Examples include regimental, divisional, and army CP and traffic control points.
FIRE SPT
This refers to fire support targets. It covers the entire threat fire support system. Subsets include fire support command and control (C2), weapons, TA, and ammunition logistics. Weapons include cannons, guns, missiles, and fixed-and rotary-winged (attack aviation) aircraft.
MANEUVER
These targets are maneuver tactical subunits in various postures. They are motorized rifle and tank companies, assembly areas, march columns, assault aviation, and advanced guard units.
ADA
This set covers air defense system targets. These include missile unit headquarters and processing centers, radar sites, and short-range air defense platoons.
ENGINEER
This refers to all engineer-type targets. Examples include bridging, ferry units, crossing sites, snorkeling sites and movement support elements.
RSTA
This group covers reconnaissance, surveillance, and target acquisition assets. RSTA refers to the concept that all intelligence and TA assets are under the control of one manager at each major unit level. Target types include ground surveillance radars, reconnaissance patrols, and airborne sensor systems.
REC
Radio-electronic combat (REC) is commonly known in Western circles as offensive electronic warfare. Some dedicated collection TA assets are listed here instead of under RSTA. The REC targets include communications and noncommunications jammers, radio-radar direction finding (DF) stations, and airborne jammers. There are 23 REC HVT types.
NUKE/CHEMICAL
This set covers nuclear (NUKE) and chemical support elements and major weapon firing positions. Nuclear and chemical targets are always treated as special cases because of the destructive and disruptive nature of the weapons that they support.
CLASS III POL
This target set covers petroleum, oil, and lubricants (POL) support. It is critical because of the level of mechanization of some forces and the projected rates of advance for second-echelon forces. Targets include transport and pipeline units and POL points.
CLASS V AMMO
This refers to ammunition support targets. These include ammo storage sites, depots, and distribution points.
CLASS IX MAINT
This is the set that covers the maintenance and repair capability. The targets include regimental maintenance units, vehicle collection points, and mobile repair facilities.
LIFT
Lift refers to general transport units in threat forces. While there is only one target category, special consideration should be given to heliborne transport.
LOC
This set covers lines of communication (LOC) for which no special target types are designated. However, any target that would interfere with the ground or air LOC, if attacked, is a candidate. Such targets include choke points, bridges, tactical airfields, and railheads.
RELATIVE WORTH
In the relative value matrix, the target sets are rank-ordered according to their relative worth to the enemy operation. The right side of the matrix has a relative value column which indicates the target sets that are considered high-value for the situation. It presents their relative value with respect to each other by use of a simple bar chart. A set with three blocks filled in is not 25 percent higher-value than a set with only two blocks filled in. The blocks are only to indicate the ordering of sets compared with one another. The target sets that are not considered high-value are not assigned a bar value.
DISRUPT, DELAY, LIMIT
The left side of the matrix consists of three columns labeled "DISRUPT," "DELAY," and "LIMIT." An X in a column associated with a target set indicates that a benefit may be accrued by attacking the target with one of these particular goals in mind.
Elements of a target set could conceivably be attacked to disrupt, delay, and limit depending on the target and the situation. This part of the relative value matrix is a general guide to desired effects against a target. It may remind planners that a target need not be neutralized or destroyed to be rendered ineffective.
Disrupt, delay, and limit are not to be confused with attack guidance terms such as suppress, neutralize, and destroy. Disrupt, delay, and limit are the effects that the attack on a specific target set will have on the echelon being faced. The targeting cell determines the effect desired. This determination is based on the combined arms commander's concept of operation. The amount of ammunition to use or the intensity of the attack (suppress and so forth) is not tied to the relative worth of a target set. The intensity of attack is based on the target vulnerability and what must be done to the target to achieve the effect desired.
An X in the DISRUPT column indicates that it is beneficial to attack a target with the goal of disrupting the function of the target. This could be achieved by continuous suppression, neutralization, or destruction of the target by lethal means. In other cases, it could involve offensive EW for some target types. The enemy function represented by the target is considered unacceptable on the battlefield and must be removed.
An X in the DELAY column indicates it is beneficial to attack the target to delay its arrival on the battlefield. For instance, a commander could opt to use less ammunition and slow a second-echelon force for a given period. This would free his remaining fire support assets for a greater effort in close-in or rear operations. The delay would allow his maneuver forces to recover and refit. Then when the second echelon finally arrived at the FLOT, a coordinated attack could be launched. In this case, the unacceptable aspect of the target is its time of arrival. The implication is that the combined arms team can defeat such a target if given enough time to prepare.
An X in the LIMIT columm indicates that a benefit can be gained if the target approach is limited. The desired effect in this case is diversion of the enemy unit to another part of the battlefield. This either puts the target in a part of the battlefield where it can be better handled or puts the enemy on unsuitable terrain.
There is one target set that always has the same relative value at division level and above. Nuclear and chemical support targets threaten any combat operation. The effects of nuclear and chemical weapons are often difficult to completely predict. These weapons complicate the planning process and threaten the commander's concept. Obviously, such weapons should be attacked with extreme vigor whenever they are found on the battlefield.
Attack Rationale Column
The result of the attack on each HVT and secondary effects on other target sets are determined during war-gaming. This information is recorded in the target spread sheet attack rationale column. This column gives commanders a general guide of the benefits derived from attacking targets in a particular target set. This column shows the desired objectives for attack of the targets in the set. Descriptions are connected to their set by lines. A solid line indicates the primary results of attacking targets in the set from which the line is drawn. These lines should be traced from left to right. Some descriptions are further attached to other sets by dotted lines. They indicate that a secondary benefit is achieved for that set when the primary set is attacked. These lines are traced from the attack rationale column back to the target set (right to left).
There are two type styles used in the attack rationale column. Normal type indicates that the associated set should be attacked in a specific sequence. The attack sequence should be the same as the listing on the right side of the sheet. This is why the lines cross to place the sets in the proper attack order on the right side. Generally, the targets in these sets will give the greatest benefit if attacked in the sequence indicated by the order of the descriptions. Descriptions in italics indicate that for the enemy posture considered the sets always have the same value throughout the operation.
Combined arms commanders should be familiar with the rationale for attack of targets to provide complete and accurate target attack guidance. Artillery personnel should be very familiar with the attack rationale so they can correctly advise the combined arms commander on attack guidance. This will ensure the guidance is within the TVA guidelines while providing optimum effects on the enemy formation.
Targeting personnel can use the attack rationale column to help develop the HPTL and attack guidance. The target sets that are sequentially ordered should be prioritized and scheduled accordingly. Target sets whose attacks would provide great secondary benefit should be considered before single benefit sets with the same value.
Specific High-Value Targets
Specific assets within each target set are noted by the G2 or S2 as HVTs. For each set there are usually some HVTs, although the set itself might be given a low relative worth. The targeting team uses the right side of the spread sheet in recommending attack guidance and developing the HPTL for the operation.
Each target is listed by the target sheet number and its name. Personnel using the spread sheet to formulate detailed attack guidance should not include all of the specified HVT. They should use only those in the higher-value categories. For example, when we are conducting pursuit operations, the enemy engineer targets are a low value category. Mechanized minelayers, however, are HVTs because, if allowed to function, they can emplace minefields that could cause pursuing forces to lose contact. Targeting personnel will consider all of the HVTs in the context of the situation and the commander's directives before developing the HPTL.
TARGET SHEETS
The decision on which HVTs should or could be attacked requires knowledge of their individual vulnerabilities, locations, signatures, and functions. Also considered is the effect that an attack on them will have on the parent enemy unit. This information, when consolidated, is called a target sheet. Locally produced target sheets should contain the following major sections:
- Target category.
- Target sheet number and title.
- Function.
- Description.
- Signature.
- Degradation effect.
- Some form of graphic representation.
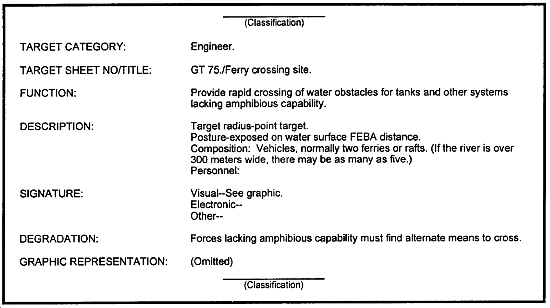
The construction of target sheets is simple and much of the information is readily available, although from varied sources. An example of a target sheet is shown below.
The target category indicates to which of the 13 sets the target belongs. A sheet number and title should be assigned to the target so it may be referenced in the future. The sheet number can be used to cross-reference the target sheet with the spread sheet. The title refers to the type and function. The function of the target details the specific operations and tasks that the target is expected to do. It includes the primary and secondary functions of the target and indicates any relationship to other target categories or types.
The description details the number and type of vehicles and equipment in a position and the approximate number of people with the target. It details--
- Usual distance from the current forward edge of the battle area (FEBA).
- Expected posture of the target with respect to camouflage and orientation.
- Type and amount of terrain occupied.
The description is useful in considering the types of attack systems and munitions to be used.
The signature describes all possible signatures to include visual, electronic, auditory, and infrared. This portion is especially useful to target acquisition and intelligence collection managers. The effects on the parent or associated intelligence unit when the target can no longer function are discussed. This is called the degradation portion.
The final part of the target sheet should be a graphic representation of the target. This aids in identifying the target and in analyzing its vulnerabilities. It may be used to help determine the effects desired against the target.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|