FM 34-45: Tactics, Techniques, and Procedures for Electronic Attack
Chapter 5
Detect
This Chapter discusses the deployment of ES systems and the collection and dissemination of ES data in support of EA. For EA to be successful on the battlefield, the commander must understand the role of ES and how to coordinate the ES effort in support of EA.
ELECTRONIC SUPPORT DATA
5-1. ES assets collect information for three purposes:
5-2. Currently database development relies heavily on exploiting signal internals, which include what is said that specifically identifies the target and gives target intent. Future ES systems, like PROPHET, will detect and collect signal externals. Signal externals only identify that an emitter is active and is located at a specific grid coordinate. If the ES system is designed to identify what kind of unit is associated with the peculiar characteristics of the emitter, then you will know a little about the unit but not the specifics of its purpose, capabilities, and intent. More detailed analysis, often at echelons higher than that supporting the EA asset, is required to provide this information. 5-3. DETECT is composed of three functions:
|
DEPLOY ELECTRONIC SUPPORT AND ELECTRONIC ATTACK ASSETS
5-4. Deploying assets is naturally divided into the three basic categories of platforms:
5-5. ES assets are not deployed in the same manner as EA systems. ES systems deploy in various formations to create a baseline which will provide area coverage for specific missions. For example, the "Lazy W" configuration is used for a wide coverage along a front where enemy positions are unknown. Systems will deploy to high ground for best LOS, while still remaining in proximity to adjacent systems in order to maintain system parameters and good baseline for DF and cueing operations. Targets from the HPTL will be found, identified, located, and targeted for a predesignated mission. In the defensive, ES assets are used primarily to identify targets on AAs into the AO. 5-6. EA assets deploy to cover specific areas in response to targeting requirements. EA assets will move to high ground to achieve optimal LOS; generally valleys, passes, roads, and bridges are ideal target areas because they create choke points in which EA is most effective. EA assets will not deploy in the same area unless a high number of targets require two systems or more to cover them. |
GROUND AND AIR ASSETS CAPABILITIES
5-7. Air and ground assets have unique capabilities to consider when employing. Employ air and ground assets to complement their capabilities. The collection manager must ensure that the ISM is configured to efficiently fulfill the requirements. Use of EAC assets should never be the sole source of ES. Because EAC ES assets are not organic to the ground commander, they lack the responsiveness and flexibility to collect within a specific area and cross-cue other sensors. |
Ground Capabilities
|
Air Capabilities
|
AIRBORNE PLATFORMS
5-8. Airborne deployment falls into three functions. These assets are heavy maintenance items and are generally used during specified periods to provide EA capability on targets not in range of ground assets. |
Select Restricted Operation Zone (ROZ)
5-9. The ROZ determines the flight path from which the airborne platform will perform its mission. This function has five steps:
|
Coordinate ROZ Selection
5-10. This function covers the coordination for air space with the BCD. Pilots will request a ROZ with the MI battalion S3. This request will specify the air space and request it 72 hours in advance. The S3 will then coordinate the request with the Joint Forces Air Component Commander (JFLAC)/A2C2 for the ROZ. This JFLAC/A2C2 at the Corps will then pass the request onto the BCD. The BCD will coordinate with air space managers who decide whether this request is acceptable or if an alternate ROZ is granted due to air space limitations. |
Review Air Threat Report
5-11. The pilots and crew perform this step. The aviation brigade will receive intelligence on the current threat to air assets and confirm the intelligence with the ACE. The pilots and crew will review this report before the mission. This report may cause the use of alternate ROZs because of a high threat. New intelligence and requirements update steps 2 and 3 continuously. |
GROUND MANPACK PLATFORMS
5-12. Manpack collection teams can be deployed alone or in conjunction with other elements. Independently deployed assets will have the additional responsibility of team security and added supply considerations. |
Ground Manpack System
5-13. Manpack collection systems provide the commander with unique capabilities when conducting initial entry, stability operations, and support operations. Found in both light and special operations forces (SOF) units, manpack systems have characteristics not found in vehicle systems. Manpack systems are characterized by the following:
5-14. Limitations of manpack systems:
|
Special Considerations
5-15. Special considerations must be made for small low-level voice intercept (LLVI) teams which will be deployed close to the FLOT if not beyond it. These teams are dependent upon stealth for battlefield survival. The teams will usually be inserted by air, either air assaulted in or jumped in. Slow movement due to the weight of these small systems will make security escorts hard to plan and coordinate. For these sites, situational awareness is imperative. Evasion plans are briefed and planned with rally points and extract points fully detailed. If contact is made, team members will move as a group or as individuals back to the predesignated points. |
GROUND PLATFORMS
5-16. Current ground systems have to completely shut down in order to change position. The commander must decide on how much of the baseline he is willing to lose for the duration of the movement. A commander can move all or part of the assets. Jumping a part of the baseline at a time allows the commander to maintain coverage of the targets, but this is a slow process. 5-17. In the case of the "Lazy W" configuration, a commander can start movement by jumping the two rear operating systems. Once these systems are in place and operational, the commander would then jump the other three systems. The other option is to move all systems at the same time. The commander can negate the loss of target coverage by coordinating with other assets. |
Ground Systems Augmented With Air Assets
5-18. The commander must carefully plan and coordinate for the use of organic aerial assets. The aerial assets add tremendous flexibility to the baseline. Aerial assets—
5-19. Deploying ground platforms consists of three interrelated functions:
5-20. Coordinate ES and EA Position Selection. This function is comprised of three actions:
- Convex, which provides good LOBs against targets that are located to the sides of the baseline of systems (Figure 5-2). - Concave, which is best, is used when the targets are straight in front of the baseline (Figure 5-3). - "Lazy-W," which is the most often used configuration because it offers good DF when the target's location in relation to the baseline is unknown (Figure 5-4). |

Figure 5-1. Stand Alone Operations
5-21. Select ES and EA Operational Sites. This function identifies primary, alternate, and supplementary sites as well as provides for preparing site sketches. Communication, target LOS, and range of targets are essential to operations and are part of site selection. Range will always be dependent upon terrain, vegetation, emitter power, distance between receiver and collector, and numerous other factors. The SIGINT team will use the signal-to-noise ratio to ensure EA systems are within range of their respective targets. Also considerations for baselines are imperative in choosing these sites. All possible sites must provide support for the baseline to effect accurate locations and overall coverage of the battlefield. |

Figure 5-2. Convex Baseline
|

Figure 5-3. Concave Baseline
|
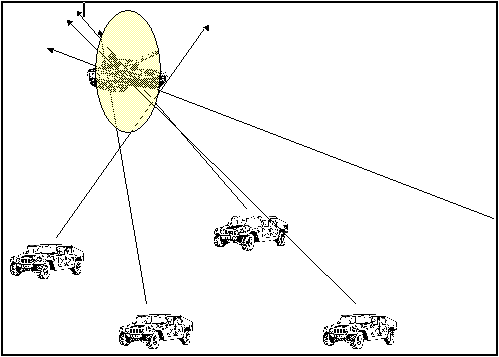
Figure 5-4. "Lazy W" Baseline
5-22. Occupy and Prepare Selected ES Sites. This step is comprised of five tasks:
|
COLLECT ELECTRONIC SUPPORT DATA
5-23. Collection of ES (communications intelligence [COMINT]) data falls into two categories: voice and digital or analog data. This data will be used to identify and target receivers for EA. |
COLLECT VOICE DATA
5-24. This function has six subfunctions that when combined and analyzed provide intelligence on targets and nodes for the effective use of EA against these nodes. |
Intercept Signal
5-25. ES systems will search across the spectrum for enemy communications (either voice encrypted or clear). |
Target Acquisition
5-26. Collection for target acquisition is the process where the ES system has been given specific tasking to locate a particular target. It can be as simple as finding a particular frequency to provide orientation data for an EA system. Or it can be as complex as searching the full spectrum for a particular entity that has met the criteria for EA. The ES system then tips that frequency and location to an EA system for attack. The length of time that it takes the ES system to fulfill the tasking is directly tied to the amount of technical data that is supplied with the tasking. The ES system that has been tasked to provide tip-off data is also usually tasked to monitor the effectiveness of the attack. The tasking for this type of mission originates in the ACE and is refined by the GS or DS company POC prior to being sent to the system. |
Gist Signal
5-27. The operator will provide the gist of the communication; callsign, ID nets (for example, artillery, infantry). |
Locate Target
5-28. This subfunction will be performed either by the system which is netted or by the POC team using numerous LOBs. |
Analyze the Signal and Build a Database
5-29. This subfunction will be performed primarily in POC and above by 98Cs to build net diagrams for the precise delivery of EA to delay, disrupt, divert, or deny spectrum to enemy. |
Report Collection Results
5-30. Operators will report collection data as soon as possible to expand the SIGINT base. |
COLLECT DIGITAL OR ANALOG DATA
5-31. This function has seven steps that somewhat mirror the subfunctions of collecting communications data. |
Intercept Digital Analog Signal
5-32. Operator will scan and identify signal (for example, digital artillery nets). |
Record Digital/Analog Signal
5-33. Operator will record the signal and make notes about the type of signal. |
Identify Emitter Parametrics
5-34. Operators identify signal strength and width. |
Identify Emitter Function
5-35. This step is completed by the POC team or higher through enemy historical data and threat models. |
Locate Digital or Analog Target or Build Digital or Analog Database
5-36. This step is also performed by analyzing data at the SIGINT team level. |
Report Digital or Analog Collection Results
5-37. This step is performed by the operator along with sending the recording back to the SIGINT team. |
COLLECTION FOR DATABASE DEVELOPMENT
5-38. The collection manager develops clear, precise, and valid tasking to support targeting. In order to maximize collection, the EWO will coordinate with the collection manager to ensure the EW target annex is integrated into the collection plan for ES. Information obtained from this collection will help update local and national databases in order to perform situation development. 5-39. Collection will be geared to support the PIR and IR and the current operation. The collection manager can follow one of several methodologies when developing the EW target list (EWTL). These methodologies vary from EW support to targeting to collection for threat database development. 5-40. The collection manager can focus tasking by threat operating systems. The collection manager plans collection based on the operating system that he feels will be most beneficial to support PIR (for example, artillery, maneuver units, reconnaissance units). 5-41. Tasking is based on known frequency, callsign, net characteristics, or signal characteristics. Characteristics can determine the importance of a net. Example: If an artillery command observation post (COP) were known to operate on a specific frequency, that frequency is included in the tasking. Tasking is based on geographical location. Signals may be of particular interest if DF places it in an area that is of specific interest. |
SEARCH TECHNIQUES
5-42. There are three main techniques of acquiring target emitters. They are spectrum searches, band or sector searches, and point searches. These techniques are best used combined, not independently. The techniques employed will depend on the mission, the number of assets, and their capabilities. |
SPECTRUM SEARCH
5-43. A spectrum search entails a detailed mapping of the entire spectrum that is exploited by a particular system. This search provides an overview of the amount and type of activity and where in the spectrum it is located. No detailed processing is done on signals. The amount of time to identify the signal and produce an LOB or fix is kept to a minimum. This search technique is best used to first establish what activity to exploit. Spectrum search allows a single asset to locate and exploit emitters to fulfill mission requirements. In a multiple asset system, one position should always conduct a spectrum search to acquire new targets. |
BAND OR SECTOR SEARCH
5-44. A band or sector search follows the same guidelines as a spectrum search but is limited to a particular segment of the exploitable spectrum. By limiting the size of the search band, the asset can improve the odds of acquiring a signal. This technique is used only in multiple asset or position systems. This search will allow for the development of new targets. |
POINT SEARCH
5-45. The point search technique is used when a list of specific targets is provided for monitoring or exploitation. This technique allows for in-depth, long-term exploitation of signals in a defined environment. Point search should be used only after a thorough map of the environment is completed and in conjunction with a spectrum, band, or sector search. This technique is used to tip-off preplanned targets to EA assets. |
CROSS CUE
5-46. When an ES asset acquires an EA target (for example, preplanned or target of opportunity), the ES asset is responsible for tipping the target information to the EA asset. 5-47. The EA ground systems have the capability to use either an omnidirectional antenna or a log periodic antenna (LPA). The difference is that the LPA increases the effective radiated power and the power is focused along a general azimuth. In order to use the LPA, the EA system operator must know the approximate target location prior to the start of the EA mission. This is one way the ES system supports EA missions. 5-48. The EA aerial systems have only omnidirectional antennas. With both types of EA systems, the ES assets provide support by providing target acquisition, target tip off, target monitoring, and jamming effectiveness. |
TA TEAM
5-49. The TA team will verify and assist the ES assets in target detection. The TA team will take the notification of a target from the ES asset and verify the target with the AGM or EWTL. If it is a valid target, the TA team will notify the ES asset in order to pass the target to the EA assets. 5-50. Along with tasking the EA assets, the ES assets are tasked to monitor the target in order to quickly identify information that would lead to valid targeting. Because information is time sensitive, quick reporting is vital. 5-51. The minimum information that needs to be passed to the EA assets are frequency, location of target, and signal characteristics (if available). This enables the EA assets to acquire the target and position their antennas in the correct azimuth. |
PROCESS SIGNALS INTELLIGENCE DATA
5-52. The processing of SIGINT data will create and redefine the baseline of intelligence necessary for the commander to envision the threat, both current and future. The data produced by this process will provide support to targeting, SIR, and numerous other products to the commander. The processing of SIGINT data takes place at all levels of ES, from the ES asset operator to the SIGINT team and collection manager. The focus of the manual is on EA but it provides a brief overview of the process of intelligence as it applies to EA. 5-53. ES assets will transmit collection data via tactical reports (TACREPs) to the TA team. The data will include signal type, target identification, and gist of target activity. 5-54. The TA team will process the ES data, fusing the data to develop a battlefield picture and provide support in either a GS or DS mode. The TA team will provide limited processing using support from the SIGINT team via ASAS, doing limited work on simple voice matrixes, and using the OB and the EOB. These tools, along with intelligence disseminated by the ACE, provide a source for intelligence support to units supported in a DS mode. 5-55. The SIGINT team will further process ES data, having feeds from both the TA teams and, under certain circumstances, the ES assets. The data processed will depend upon numerous factors. Upon support from higher to decrypt communications data and intelligence feeds, the SIGINT team will also use the OB, EOB, and doctrinal templates to determine threat intent and actions. 5-56. The SIGINT team and the TA team will provide target data to FS channels. Using the ISM, these teams provide priority to targeting requirements to ensure intelligence is provided in a timely manner to engage HPTs. These targets may be engaged by either lethal or nonlethal fires. |
SITUATION DEVELOPMENT
5-57. It is crucial that information pass between elements as quickly and as accurately as possible. Information development data will be passed from the ACE, down to the ES and EA assets, in the form of technical data and tasking. Technical information that is developed at the ES asset is also passed directly to the EA asset (as well as to the ACE) to help with database development. 5-58. Once the ES system has acquired the target, the operator must disseminate the information to the EA system. This is done most frequently with voice communications. The data needs to include the frequency, location, and signal characteristics. The ES system operator also notifies higher headquarters that the target was acquired and that the necessary data was transmitted to the EA system. If the ES system fails to acquire the target, the ES system operator must notify higher so that the tasking can be shifted or changed. |
ELECTRONIC ATTACK EFFECTIVENESS
5-59. During an EA mission, the ES asset will monitor the target to provide feedback to the EA asset and to provide the analytical element with an effectiveness report. The purpose of feedback is to keep the EA asset apprised of the status of the target. The immediate notice of changes to the frequency, location, or signal characteristic is vital to the success of the EA mission. 5-60. When a mission is completed, the ES or EA asset will send the analytical element a detailed effectiveness report in the form of a jamming effectiveness report (JER) or multiple assets effectiveness report (MAER), which will be sent digitally or by voice. This report will include the effects on the target from the perspective of that ES or EA asset. It includes but is not limited to frequency, location, signal characteristics, effects observed, and duration. (See Appendix D.) |
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

