Chapter Four
Relevant Information and Intelligence (RII) (cont)
Battlespace Awareness. JSTARS, UAV Aviation, and USN Orion P-3C can all provide Situational Awareness in Peace Enforcement operations.
TFE employed helicopter aviation and supporting JSTARS, UAV and P-3 assets during operations to track EAF units, police forces, political leaders, PIFWCs (Persons Indicted for War Crimes), organized groups of demonstrators, and unruly mobs. These assets were focused on COMEAGLE's CCIR (Commander's Critical Information Requirements) and on the potential and actual hotspots identified by the G-2. These systems were supplemented with HUMINT collectors, both active and passive. The aerial assets could be used during operations to provide battlefield visualization in support of current operations.
JSTARS. The Joint Surveillance Target Attack Radar System (JSTARS), an IMINT collector, first deployed to support OJE on 14 December 1995. During ground operations on 13 January 1996, the U.S. bde of TFE employed a Ground Station Module (GSM) which received JSTARS information. Such use represented the first time a JSTARS GSM had been tasked down to a BDE in a real-world deployment. Initially, the GSM monitored large sectors, making analysis of specific areas difficult. As a result, the S2 narrowed the focus of the JSTARs by orienting the system on Named Areas of Interest (NAI) for specified periods of time. He also provided the operators, who also performed limited analysis, PIR and likely patterns to observe.(48)
However, it was discovered that JSTARS has certain limitations in a peace operations environment which preclude its employment as a "stand alone" collection asset. The non-linear, and for the most part, non-violent nature of peace operations means that civilian traffic may mix with FWF military movements, the FWF armed forces may sometimes use civilian vehicles, and even coalition vehicles may be intermingled with FWF and non-combatant vehicular traffic, making positive identification difficult. TFE found that it was indeed difficult to distinguish the significance of large convoys, which were detected by the Moving Target Indicator (MTI). Although the Synthetic Aperture Radar (SAR) was used to further refine images of vehicles within the convoy, definite confirmation of the types of vehicles could not be obtained to the degree of detail required. The SAR was used to identify some trenchlines within the zone of separation (ZOS), but identification of the positions requires close observation and analysis. The SAR imagery does not provide the degree of resolution required for easy recognition of a target.(49)
Although JSTARS exhibited these limitations, the brigade experienced several successes with the system. TFE identified large movements out of the town of Odzak. After the S2 was alerted of the movements, Civilian and Military Operations personnel were sent to that location to determine the reasons. The reason was the fact the Serbs did not want to live in Odzak after the area had been transferred to the HVO (Bosnian Croat Defense Forces). In addition, JSTARs confirmed a ferry site in the vicinity of Odzak. The site was designated as an NAI for a period of several days, and the MTI detected the movement across the river. JSTARS identified two-three tanks in an assembly area by a Fixed Target Indicator (FTI) and confirmed, to some degree, by a SAR photograph. JSTARS also identified a rail-loading operation of armored vehicles at a railhead near Odzak. JSTARS seems to have its greatest utility during the initial phases of peace enforcement operations which are characterized by open hostile opposing forces which must be separated and stood down.
UAVs. TFE used UAVs, such as Predator and Pioneer, extensively for monitoring important areas of interest such as the Zone of Separation, EAF cantonment areas, gravesites, troop movements, para-military and police activities, and civil demonstrations.(50)On 29 June 1997, UAVs complemented ground reporting in monitoring FWF political leadership during a political crisis within one of the FWFs.
The Republika Serpska President, Madame Plavsic, had been detained by authorities at the airport in Belgrade, and then deported to Republika Serpska where she was subsequently met by elements of the RS Police upon her arrival there. A rift between the supporters of Mme. Plavsic in the northern portion of RS and the supporters of ousted ex-president and indicted war criminal Radovan Karadzic had widened and threatened to deteriorate rapidly with a change in government not an unlikely outcome. The MND-N commander was concerned that Mme. Plavsic's freedom of movement might have been restricted and controlled by rogue elements of the RS Police. Mme Plavsic was located at a hotel in Bijeljina by SFOR soldiers; a meeting was arranged with a senior field-grade SFOR officer. After the meeting, SFOR granted Mme. Plavsic's request for an RS military helicopter to fly her to her support base in the town of Banja Luka, where VRS Army III Corps MPs and an anti-terrorist unit would guarantee her safety. The request was granted out of concern that the RS President's safety among her own police forces was in question.
The motorcade's movement to the helipad and the subsequent flight to the Rupes Military Academy at Banja Luka were televised to the Main CP from beginning to end by the Predator UAV, allowing SFOR to track her every movement. Had any rogue RS Police attempted to interfere, SFOR would have known immediately: a visible demonstration of information dominance.
USN Orion P-3C and Army Aviation. During an operation intended to prevent a clash of non-combatants from opposing FWFs on 11 July 1997, TFE used the USN Orion P-3C aircraft, helicopter aviation to track groups of demonstrators. The Association of the Women of Sebrinica (WOS) attempted to execute a bus ride and vigil to the Dulici Dam outside of Zvornik on the RS side of the Zone of Separation (ZOS) -- the location of a suspected mass grave site of the victims of the genocidal slaughter of the citizens of Sebrenica captured and subsequently killed by Bosnian Serb Army in the summer of 1995. The plan called for the group to cross the ZOS and hold a rally at the dam with busloads of WOS members and anyone else who decided to attend. The RS Police Chief of Zvornik had already announced that he would not provide security for the group. Local Bosnian Serbs in the vicinity of Dulici had fore knowledge of the planned bus ride, and crowds armed with rocks and pitch forks began to form at the suspected mass grave site at the same time that the group was boarding transportation.
The MND-N Commander's intent was to prevent any open hostilities from erupting that would be detrimental to the peace process. Accordingly, SFOR forces in MND-N would take all possible measures to keep the two sides from coming into contact. The RISTA assets available in support of the operation were the P-3 and the helicopter aviation units: the Predator was on a mission outside of the division sector. For this mission, ground elements were postured and directed based on the aerial intelligence obtained by P-3 and the helicopter pilots. The Division forward command post, the Tactical Action Center (TAC), was able to accurately track the location of center of mass and front-line trace of the moving groups of demonstrators, give descriptions of their composition, disposition, and potential courses of action, thus providing a clear Relevant Common Picture (RCP) throughout the MND-N AOR.
AH-64 Gun Camera Video as an IO Tool. TFE used Digitized footage from the Apache attack helicopter gun camera to enforce compliance among the FWF armed forces and document violations of the DPA. The photographs produced from the footage were declassified and occasionally handed over the FWF to compel them to comply with instructions to withdraw weapons or move forces. These photos were "date-stamped" and showed the exact location with grid reference and, of course, had the signature "cross hairs" of the gun system, providing an "unsubtle but highly effective means of compelling compliance."(51)Gun camera footage from aviation reconnaissance of the ZOS downlinked in real time to the freeze-frame-capable Mobile Intelligence Tactical Terminal (MITT) provided the friendly force irrefutable evidence to show the FWFs any acts of non-compliance.(52)By showing proof, the peace operations force demonstrated information dominance and avoided having to resort to lethal means to enforce compliance.
Other RISTA systems employed by TFE included Aerial Reconnaissance Low (ARL), Lofty View UAV, while SFOR employed NATO-level RISTA assets such as NATO E3S and US E-2Cs. ARL, a fixed-wing U.S. Army airframe packaged with COMINT and IMINT sensors, deployed in support OJE on 28 January 1996. This aircraft primarily provided images for TF Eagle requirements. In one mission, COMEAGLE demonstrated the presence of NATO intelligence by having the FWF leadership view themselves via live ARL video down-link to the Joint Military Commission (JMC) meeting they attended.(53)Lofty View, a short-range UAV, operated from Sepurine Air Base, Croatia, occasionally supported TFE by providing video images that were downlinked in real time to TFE headquarters.(54)
Daily, the G-2 develops plans for Predator, P-3, and helicopter aviation to obtain the Commander's CCIR and to cover potential hot-spots. Therefore, what was available on any given day was a function of the IPB analysis done the day before, and on what assets are available after higher headquarters RISTA needs are filled. During the AWS demonstration, for example, the MND-N Commander would have employed the Predator UAV extensively, but it was on an SFOR mission out of sector.
TFE primarily used the RISTA assets of P-3 and UAV as well organic and attached helicopter aviation assets to maintain situational awareness during operations. Both the UAV and P-3 provided real-time televised imagery that facilitated command and control. Helicopter aviation was always available, even when P-3 and Predator were out of the Division sector. The helicopter pilots were rapidly responsive intelligence collectors on developing situations who provided important SITREPs over FM radio communications. The combination of these systems enabled the Division to achieve Information Dominance over the FWF organizations or groups under scrutiny, resulting in TFE achieving situational dominance.
Using Modern INFOSYS to Build RII.
Exploiting Human Intelligence (HUMINT)
| "In
noncombat operations, HUMINT, open sources, and other government agencies provide
timely information to augment the unit's more traditional battle-focused intelligence
collection effort." --FM 100-6, Information Operations |
HUMINT is the category of intelligence derived from information collected and provided by human sources. During OJE/OJG/OJF, U.S. intelligence units employed a suite of technical intelligence-gathering means, reflecting U.S. strengths in such systems. Other partner nations, namely the British and French, fielded specialized capabilities in HUMINT in the Allied Military Intelligence Brigade, which complemented the U.S. technological means of collection.(55)This example of cooperation demonstrates the advantages that accrue from multi-national operations. FM 100-8, The Army in Multinational Operations, directs intelligence operations officers to carefully research and employ all available assets across the MNF.(56)
In peace operations, information gathered by patrols, observation posts, and roadblocks provides a substantial amount of information for MI analysts to evaluate.(57)While every soldier is an intelligence collector, specialized units maintain greater exposure to the local populace and governmental and military elements of the FWF, and are better positioned to gather HUMINT. The information gathered from traditional means is compared to HUMINT to support intelligence analysis. Joint Doctrine for peace operations notes "the best sources of information may be CA and PSYOP personnel."(58)In MND-N, the units best-suited to collect HUMINT in TFE were the Multi-Discipline Counter-Intelligence (MDCI) personnel organized into Force Protection Teams (FPTs). Although gathering information is not their primary task, several elements are well-positioned to provide information and intelligence, to include HUMINT, such as: Tactical PSYOP Teams (TPTs), Civil Affairs Direct Support Teams (DSTs), and the special forces Joint Commission Observers (JCOs).
In MND-N, the TPTs were actively engaged with the local populace through dissemination missions and coordinating with key communicators through the sector on a routine basis. The PSYOP soldiers actively debriefed the G-2 on pertinent information gleaned in their missions.(59)TPTs spent a great deal of time disseminating PSYOP print products to the local populace and were keenly positioned to provide relevant reporting on points of interest in the civilian communities of the battlespace.
"CA forces, if used correctly, can complement the intelligence collection process, especially HUMINT."(60)CA doctrine recognizes that the nature of CA operations which requires CA personnel to develop and maintain a close relationship with the civilian populace puts them in a favorable position to collect information.(61)CA operations are closely tied to the intelligence functions and operations associated with the overall tactical mission. CA personnel have an intricate and important intelligence role during both the intelligence cycle and the operational planning sequence. CA personnel support HUMINT through referrals to intelligence personnel for interpreters, and civilians with special skills. However, CA personnel must avoid appearing to be intelligence agents, or risk degradation of their primary mission.(62)
Task Force Eagle's Counter-Intelligence FPTs were composed of CI Agents, interrogators, and military or contracted civilian linguists. These teams were formed from the division MI Battalion and corps/theater MI Brigades. Their primary mission was to collect tactical HUMINT to satisfy the supported commander's primary intelligence requirements (PIRs). Through sustained collection efforts, the FPTs were able to substantially increase the volume of RII from HUMINT sources.(63)In the first year of OJE, tactical FPTs generated over 3,000 Force Protection Information Reports (FPIRs), a major percentage of the task force collection effort.(64)
Joint Commission Observer (JCO) teams composed of Army Special Forces and U.S. Navy SEALs were excellent sources of HUMINT. The JCOs supported SFOR objectives by performing liaison functions between SFOR and the EAFs. Deployed throughout the AO, and living in towns and villages among the local populace, the JCOs provided "ground truth" of EAF and FWF military and civilian attitudes, intentions, and actions. In emergencies, the JCOs served as a direct link between COMSFOR and the EAFs. The nature of the JCO mission brought the teams into contact with numerous political and social groups, local leaders, police, and military elements of the FWF. One TFE Military Intelligence Battalion Commander estimated that over 80 percent of all useful intelligence reporting resulted from FPT and JCO collection efforts.(65)
Exploiting Open-Source Intelligence (OSINT)
| "In
noncombat operations, HUMINT, open sources, and other government agencies provide
timely information to augment the unit's more traditional battle-focused intelligence
collection effort." --FM 100-6, Information Operations |
The MI Battalion document exploitation team played an integral role in Information Operations (IO) as the TFE OSINT Cell. The information it produced was especially important in a PKO and during municipal elections in which numerous political parties participated. The news media comprised important elements of the information environment during Operation JOINT GUARD (OJG). The international press covered SFOR operations, diplomatic and political events, and other newsworthy events extensively. Perhaps more importantly, local and regional media not only reported on events, but some also actively supported the agendas of the various political parties and presented their broadcasts accordingly. The local populace were avid consumers of these broadcasts and often responded to the messages presented. Therefore, it was critical for the TFE commander and staff to be aware of news broadcasts and to conduct information operations aimed at promoting the truth and countering misinformation. The OSINT Cell's operations proved to be an effective conduit for focused, analyzed reporting on the public media.
The OSINT Cell monitored TV and radio broadcasts and produced translated, edited transcripts. The cell published three products:
- The "Night Owl" was a daily news digest of report summaries from broadcasts throughout the AOR. It was an unclassified publication disseminated to military elements within TFE and to other military and non-government organizations (NGO) by request.
- Intelligence briefs were special assessments of media broadcasts which focused on short-term trends or themes identified by OSINT analysts. It was published three times a week and provided directly to the TFE G2.
- The "Nut Shell" was a special assessment of media broadcasts which focused on specific long-term trends identified by OSINT analysts over several weeks or months. The Nut Shell was published every three to four months, as required.
These products shared the same purpose and characteristics:
- To provide an accurate depiction of open-source information available to the local populace.
- To assist commanders and staffs in anticipating the public response to various TFE operations.
- To help commanders and analysts gain an increased appreciation for the political, cultural and social environment as reflected by the media.
- To present information "as is" to the greatest degree possible to accurately depict public sentiment. Transcripts were edited only to facilitate understanding and improved readability.
The OSINT Cell's reporting often provided indicators to the TFE staff of events that would require a tactical response by TFE forces. It also proved to be a valuable tool for use in the TFE Information Operations effort. FM 100-6 states that "C2Protect includes countering an adversary's propaganda campaign to prevent it from affecting friendly operations, options, public opinion, and the morale of friendly troops." The OSINT cell provided the supported command with both timely and historical records of messages presented to the local populace. Commanders and the TFE Information Operations Working Group (IOWG) used the cell's reporting to plan IO themes and to gauge their effectiveness after implementation.
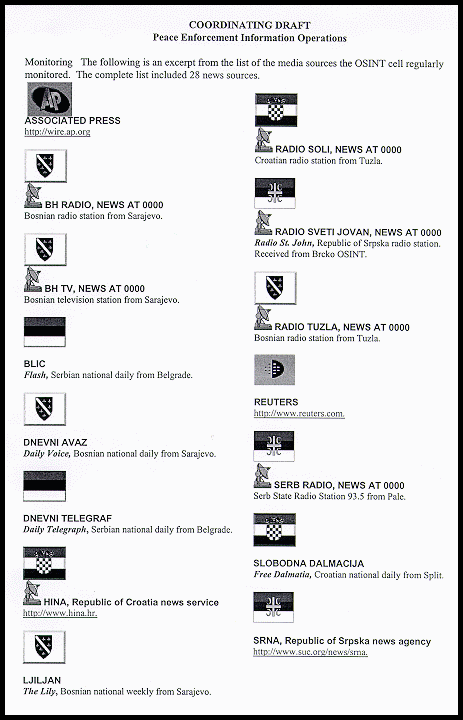
Monitoring. Following is an excerpt from the list of the media sources the OSINT cell regularly monitored. The complete list included 28 news sources.
The G2 focused the cell's monitoring, analysis and reporting functions by tasking the cell with standing reporting guidance as well as specific guidance to meet mission-oriented collection requirements. Below is an example of the standing reporting guidance. It provided the cell with specific events or locations of interest (similar to SIR) as well as specific indicators (similar to SOR).
The G2 adjusted his OSINT reporting guidance based upon guidance he received from the TFE Commander, the IOWG, and all-source analysts in the ACE. Representatives of the OSINT Cell also attended G2 shift change briefs and staff "huddles" to ensure that they were aware of emerging mission requirements. The OSINT cell disseminated its products in either paper or digitized form according to the users' requirements. The Night Owl was distributed in paper copies locally and in digitized copies via the internet to military and NGOs outside the headquarters. Hundreds of Night Owl articles were included in the TF Eagle RII databases, and users of the newsletter included the U.S. Embassy in Sarajevo.(66)
1. Headquarters, U.S. Army Training and Doctrine Command, Force XXI Operations, TRADOC PAM 525-5 (Fort Monroe, VA: TRADOC), 1 August 1994, Chapter 3.
2. Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6, op. cit. p. 4-0.
3. Ibid. p. 4-3.
4. Ibid. p. 4-1.
5. Office of the Chairman of the Joint Chiefs of Staff, Joint Publication 3-07.3, Joint Tactics, Techniques, and Procedures for Peacekeeping Operations, Washington, DC, 29 April 1994, p. V-6. See also Headquarters, Dept. of the Army, Military Operations in Low-Intensity Conflict, Field Manual 100-20 (Washington, DC: USGPO), 5 December 1990, p. 4-6.
6. HQDA, Military Operations in Low-Intensity Conflict, Field Manual 100-20 (Washington, DC: USGPO), 5 December 1990 p. 4-7.
7. Information provided here on the composition of the MI Task Force was originally published in Center for Army Lessons Learned, B/H CAAT V Initial Impressions Report - Task Force Eagle Transition (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), May 1997, p. 11.
8. The WARLORD is a U.S. intelligence processing system employed in TFE operations. WARLORDs were placed at all brigade-level headquarters of those participants in OJE/OJG/OJF. The information on the WARLORD system is divided into categories of SECRET, NOFORN, SECRET-Releasable to NATO, SECRET-Releasable to IFOR/SFOR. To ensure that no compromise of classified material occurred, a three-step process was employed, which ensured that non-U.S. personnel were not allowed access to the WARLORD workstation. For more information, see Center for Army Lessons Learned, Operation JOINT ENDEAVOR- Initial Impressions Report - Initial Operations (Fort Leavenworth, KS: CALL), May 1996, p. 66.
9. Headquarters, Department of the Army, Intelligence and Electronic Warfare Operations, Field Manual 34-1 (Washington, DC: USGPO), 27 September, 1994, p. 6-2.
10. Headquarters, Dept. of the Army, Decisive Force: The Army in Theater Operations, op. cit., p. 8-15.
11. Headquarters, USAREUR, Operation JOINT ENDEAVOR, USAREUR Headquarters After-Action Report, op. cit., p. 81.
12. Headquarters, Dept. of the Army, Decisive Force: The Army in Theater Operations, Field Manual 100-7, op. cit., p. 8-5.
13. Again, the term RISTA, rather than ISR, is employed here to emphasize the role of Target Acquisition systems in developing RII.
14. Headquarters, USAREUR, Operation JOINT ENDEAVOR, USAREUR Headquarters After-Action Report, op. cit., p. 84.
15. Headquarters, Dept. of the Army, Staff Organization and Operations, Field Manual 101-5 (Washington, DC: USGPO), 31 May 1997, p. 1-3.
16. The commander states his information requirements as priority intelligence requirements (PIRs) and friendly force information requirements (FFIRs). He also determines what information about the friendly force must be kept from the enemy, which are essential elements of friendly information (EEFIs). The commander's critical information requirements (CCIRs) are comprised of PIR, FFIR, and EEFI.
17. Chairman of the Joint Chiefs of Staff, Operational and Academic Research Topics, 19 August 1997, downloaded from http://www.dtic.dla.mil:80/mil-ed/97jrt/index.html
18. Headquarters, TRADOC, Information Operations Division, Brochure, Information Operations (Fort Monroe, VA: TRADOC), 22 January 1997, p. 11.
19. Center for Army Lessons Learned, B/H CAAT2 Initial Impression Report - Operation JOINT ENDEAVOR - Continuing Operations (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), September 1996, p. 67.
20. Headquarters, Department of the Army, Intelligence and Electronic Warfare Operations, Field Manual 34-1 (Washington, DC: USGPO), 27 September, 1994, p. 6-2.
21. Headquarters, Department of the Army, Decisive Force: The Army in Theater Operations, Field Manual 100-7, op. cit., p. 8-5.
22. Headquarters, Training and Doctrine Command, Concept for Information Operations, TRADOC Pamphlet 525-69 (Fort Monroe, VA: TRADOC), 1 August 1995, p. 10.
23. Headquarters, Dept. of the Army, Decisive Force: The Army in Theater Operations, Field Manual 100-7, op. cit., p. 8-15.
24. Headquarters, Dept. of the Army, The Army in Multinational Operations, Field Manual 100-8, op. cit., p. 1-3.
25. Ibid. p. 2-10.
26. Ibid.
27. For a discussion on the role of the USIA in information operations, refer to Chapter Three, PSYOP, page 13.
28. William S. Cohen, Annual Report to the President and the Congress (Washington, DC: USGPO), April 1997, p. 232.
29. Larry K. Wentz, ed., Lessons from Bosnia: The IFOR Experience, Command and Control Research Program (National Defense University, Washington, DC: NDU Press), 1997, pp. 67-68.
30. For a complete listing of other systems, see William B. Buchanan, U.S. European Command Support of Operation JOINT GUARD (21 December 1996 - 20 December 1997) (Unclassified, Distribution Limited, Alexandria, VA: Institute for Defense Analysis, IDA Paper P-3389), 1998, p. III-19.
31. Headquarters, Dept. of the Army, Military Operations in Low-Intensity Conflict, Field Manual 100-20, op. cit., p. 4-6.
32. Yu Lin Whitehead, Maj., U.S. Air Force, "Information as a Weapon: Reality versus Promises," Airpower Journal, Vol. XI, No. 3, Fall 1997, p. 50.
33. David L. Grange, Maj. Gen., U.S. Army, and Col. James A. Kelley, U.S. Army, "Information Operations for the Ground Commander, Military Review, March-April 1997, p. 9.
34. Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6, 27 August 1996, Washington, DC, p. 6-19.
35. Ibid, p. 4-1.
36. Ibid.
37. Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6, 27 August 1996, Washington, DC, p. 2-10.
38. Ibid.
39. Gary B. Griffin, Lt. Col., U.S. Army, The Directed Telescope: A Traditional Element of Effective Command, Combat Studies Institute, U.S. Army Command and General Staff College (Fort Leavenworth, KS: CGSC Press), July 1991, pp. 1, 5, and 8.
40. Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6, 27 August 1996 (Washington, DC; USGPO), p. 1-10.
41. For a more detailed account, see William B. Buchanan, U.S. European Command Support of Operation JOINT GUARD (21 December 1996 - 20 December 1997) (Unclassified, Distribution Limited, Alexandria, VA: Institute for Defense Analysis, IDA Paper P-3389), 1998, pp. III-24 and III-25.
42. Larry K. Wentz, ed., Lessons from Bosnia: The IFOR Experience, op. cit, p. 70.
43. See Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6, op. cit., p. 5-0.
44. Slobodna Bosna (Free Bosnia), Bosnian national semi-monthly, 5-11 December 1998, Sarajevo, as translated in The Tuzla Night Owl, Task Force Eagle, G-2 OSINT, Vol 3, Issue 342, December 8, 1998, p. 5.
45. Office of the Chairman of the Joint Chiefs of Staff, Joint Publication 3-07.3, Joint Tactics, Techniques, and Procedures for Peacekeeping Operations (Washington, DC: USGPO), 29 April 1994, p. V-6. See also, Headquarters, Dept. of the Army, Military Operations in Low-Intensity Conflict, Field Manual 100-20 (Washington, DC: USGPO), 5 December 1990, p. 4-6.
46. See CALLCOMS observation 10007-17500, "Video Cameras as information operations tools during peace enforcement operations." Published in B/H CAAT 9 Initial Impressions Report: Operation JOINT GUARD, Task Force Eagle Operations (Fort Leavenworth, KS: CALL, Unclassified, Distribution Limited), March 1998, p. A-55.
47. Headquarters, Dept. of the Army, Information Operations, Field Manual 100-6 (Washington, DC: USGPO), 27 August 1996, p. 3-9.
48. See Center for Army Lessons Learned, CALLCOMS Observation 10011-59136 (Unclassified, Distribution Limited).
49. Larry K. Wentz, ed., Lessons from Bosnia, Command and Control Research Program, National Defense University (Washington, DC: NDU Press), January 1998, pp. 100-102. See also CALLCOMS Observation 10011-59136, "JSTARS Employment at Brigade Level," Center for Army Lessons Learned.
50. Larry K. Wentz, ed., IFOR C 4ISR Experiences, a report prepared for the National Defense University, Command and Control Research Program, working draft, as of 15 January 1998, p. 46. Downloaded from the CCRP Website at http://www.dodccrp.org/bosnia.htm#REPORTS/BRIEFINGS
51. This photograph digitization capability was the result of an investment in commercial software and off-the-shelf equipment costing less than $1,000. See Kenneth Allard, "Information Operations in Bosnia: A Preliminary Assessment," Strategic Forum, Number 91, November 1996, Institute for National Strategic Studies, National Defense University, p. 5.
52. Headquarters, USAREUR, Operation JOINT ENDEAVOR, USAREUR Headquarters After-Action Report, op. cit., p. 88.
53. Ibid., p. 87.
54. Headquarters, USAREUR, Operation JOINT ENDEAVOR, USAREUR Headquarters After-Action Report, op. cit., p. 87.
55. Ibid., p. 77.
56. Headquarters, Department of the Army, The Army in Multinational Operations, Field Manual 100-8, op. cit., p. 4-2.
57. Headquarters, Department of the Army, Intelligence and Electronic Warfare Operations, Field Manual 34-1, op. cit., p. 6-2.
58. Joint Warfighting Center, Joint Task Force Commander's Handbook for Peace Operations, Fort Monroe, VA, 28 February 1995, p. 30.
59. Center for Army Lessons Learned, B/H CAAT IX, Initial Impressions Report (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), March, 1998, p. A-124, CALLCOMS file number: 10003-79460.
60. Headquarters, Dept. of the Army, Civil Affairs Operations, Field Manual 41-10 (Unclassified, Distribution Limited), op. cit., p. 6-3.
61. Ibid., p. 6-2.
62. Ibid.
63. Center for Army Lessons Learned, B/H CAAT Elections Initial Impressions Report (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), March 1998, pp. A-98.
64. Center for Army Lessons Learned, B/H CAAT V Initial Impressions Report - Task Force Eagle Transition (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), May 1997, p. 14.
65. Center for Army Lessons Learned, B/H CAAT Elections Initial Impressions Report (Unclassified, Distribution Limited, Fort Leavenworth, KS: CALL), March 1998, pp. A-132.
66. Headquarters, USAREUR, Operation JOINT ENDEAVOR, USAREUR Headquarters After-Action Report, op. cit., p. 197.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

