Infantry
Battalion Command and Control (C2)
Facilities
The
Command Group
by LTC Daniel Klecker and CPT Jay Peterson
As outlined in FM 7-20, The Infantry Battalion, Appendix B, C2facilities available to the light infantry battalion task force include the main command post which encompasses the tactical operations center (TOC), combat trains, field trains and alternate command posts. Each of these facilities has a doctrinal purpose and suggested personnel and equipment to perform their crucial functions. At the battalion level, establishing a command group presents a doctrinally based, temporary C2node that provides the commander additional flexibility and capability to optimally complete his combat mission.
The command group is a temporarily task-organized group of key personnel and equipment, including the commander. The commander designates the command group to complete a specific task, usually to facilitate C2of the immediate battle. The task and purpose of the command group, its configuration, and duration of echelonment are all mission, enemy, terrain, troops, and time available (METT-T)-driven. The commander identifies these issues during his estimate; they are included in the command and control battlefield operating system (C2BOS) staff estimate, and confirmed during the staff decisionmaking process. Configuration is normally subject to specific unit standing operating procedures (SOPs). It is often locally referred to as a "tactical" CP (TAC) or an Assault CP.
This article discusses considerations and techniques for use of the command group. Techniques and procedures demonstrated by units training at the Joint Readiness Training Center (JRTC) are the basis for these observations. Generally, forced entry operations generate the best examples for discussion of command group issues, and will often be used for illustration purposes in this article.
Echelonment
of C2Nodes
The genesis of the decision for whether or not to echelon a command group forward during a given mission is the commander's estimate. During the commander's guidance, he will define the parameters of his intent to the staff, who will incorporate his guidance into a course-of-action development and ultimately into the operations order.
A technique to determine the exact configuration of the command group is by thorough analysis of echelonment of the C2BOS. This analysis becomes part of the C2continuous estimate. The staff incorporates this information into his course-of-action development (Figure 1) and deliberate wargaming. Another example is the BOS analysis for echelonment of command and control is the C2portion of a wargaming worksheet that aids in synchronizing C2.
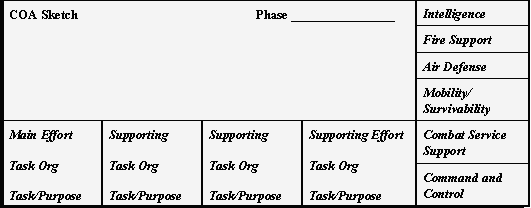
Figure 1. COA Development Tool (Generic)
Often overlooked in the process is the appreciation of the limitations of the austere command group, particularly during continuous operations. For forced entry operations, the command group, a temporary facility, should deploy for a short duration only. The command group must be capable of completing all necessary tasks of the main command post (CP), until the main CP can echelon forward and become operational. Such tasks include establishing and maintaining communications, security, combat information management, and targeting or synchronization processes. Operations that extend beyond 24 hours in duration normally exceed the optimal capabilities of the command group; the cumulative effects of sleep deprivation and stress affect its ability to provide adequate C2.
To best provide C2until the main CP is functional, the command group must have all appropriate combat information management tools. This may include tracking charts, maps and overlays. Upon establishment of the main CP, the command group can quickly and accurately transfer all necessary information to the TOC.
A useful technique is to create 8.5 x 11-inch replications of essential battle-tracking charts, laminate them, and place them in a three-ring binder. The unit can maintain all essential combat information management documents in this binder, to include blank copies of DA Form 1594, to facilitate maintaining a journal. The main CP updates the binder prior to the command group's departure from the TOC, and the command group maintains the binder's accuracy while forward. An appropriate suggestion is that the unit maintain a copy of this three-ring binder at each C2node.
Succession of C2Facilities
Each C2node should have the appropriate tools to perform its unique function; some of these mentioned earlier. While the echelonment of C2nodes should be a deliberate decision based upon due consideration of all factors of METT-T, similar situations will likely require similar C2capabilities. These tend to become somewhat predictable. Units should validate configurations of personnel and equipment, considering both mounted and dismounted options, and include the determined structures in the unit SOP. These templates are useful references and adjustable to a given situation. By including them in the unit SOP, subordinates anticipate actions earlier, improving their performance and efficiency.
The unit SOP should further address the displacement criteria for each C2node. There should be triggers for establishment of a command group, to include when to consider echelonment forward, and when the requirement for a separate node comes to an end. The unit SOP should also detail the succession of C2node priority, and the criteria for assuming C2. For example, during routine combat operations, the combat trains command post (CTCP) has the capability to assume the functions of the main CP should the primary be destroyed. Loss of communication with he main CP for a set time period should trigger the CTCP to assume the main CP functions. This demonstrates the types of concerns that can be predictable and incorporated into the unit SOP.
Alternate C2Nodes
The main effort will usually have the immediate attention of the command group. Alternate C2nodes have effectively provided better C2at other critical points on the battlefield, particularly during forced entry operations.
Sometimes referred to as "split TAC operations," a useful technique to consider is the operation of two, temporary command nodes until the complete maturation of all C2facilities. In this example, a primary command group (TAC 1) is in proximity to the main effort, while the battalion task force is securing an airfield and destroying enemy forces in zone. The battalion may temporarily establish an alternate command post (TAC 2) to provide C2of another concurrent and essential task. TAC 2 is under the supervision of the battalion executive officer and remains functional until their tasks are complete.
Another example of effective use of an alternate C2node is the early forward echelonment of essential logistics C2. This provides the unit the capability to oversee the arrival and marshaling of assets as they arrive into theater simultaneously with combat operations ongoing. Like the scenario illustrated above, the command group can provide C2for the immediate close battle involved with initial or forced entry operations (TAC 1). Key assets, such as the main command post with the TOC and key CSS elements, may be deployed by follow-on ground or air means. Recognizing the criticality of ensuring successful, timely arrival of these assets, the commander may elect to command and control these concurrent activities with an alternate C2node. He could configure TAC 2, under the supervision of his executive officer. Upon arrival of the main CP, TAC 2 may discontinue operations with the TOC assuming the battle.
The C2doctrine allows considerable latitude for commanders to tailor their command group to best fit any situation. Optimizing the location and configuration of the command group requires thorough estimates, deliberate planning and meticulous wargamming. Thoughtful consideration of the command group can significantly enhance C2and, ultimately, mission success.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

