APPENDIX J
Defensive Formation
Section I. GENERAL |
|
Jungle defensive operations are based on the same fundamentals of the defense used in other type operations. Some of the fundamentals may acquire a special significance in the jungle. The basic factors of observation and fields of fire, cover and concealment, obstacles, key terrain, and avenue of approach should always be considered carefully.
Three defensive formations will be presented here: the perimeter, the triangle, and the "Y." Platoon-size elements will be the primary consideration, although the techniques mentioned are adaptable to larger units. It should be noted that all three defensive postures have definite advantages as well as inherent disadvantages. Units should vary their type of defensive posture in order to avoid establishing a pattern.
Section II. FORMATIONS |
|
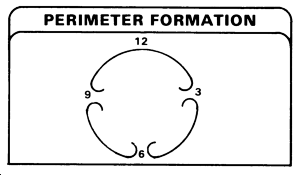
PERIMETER DEFENSE
The first of the defensive formations is the perimeter. All elements are generally configured in a circular formation, and the terrain is used to the maximum advantage.
|
CONTENTS SECTION I. General II. Formations |
|
Advantages are:
|
It is mutually supported by observation/communication, and patrols are easily coordinated. Disadvantages are:
|
The basic technique used to establish this defensive formation is the clock system. This involves the platoon using the direction of movement as 12 o'clock, with one squad occupying from 8 to 12, one squad occupying from 8 to 4, and the last squad occupying from 4 to 12. The headquarters element would normally be located in the center of the formation to facilitate control. It is generally suggested that automatic weapons be placed to cover the most likely avenues of approach. At least one machinegun should be kept with the headquarters, under the control of the unit leader, for deployment against a specific threat.
TRIANGLE DEFENSE
The second of the defensive formations is the triangle defense. This formation is a modification of the perimeter.

|
Advantages are:
|
Disadvantages are:
|
This defensive formation is best established by having the commander move forward with one element and establish a base line. Again, 12 o'clock is used as the direction of movement. The baseline could be established by the first squad, running from 8 to 12. Once this base line is established and the squad is prepared to provide support, the next squad moves forward and occupies the straight line position from 8 to 4; finally, the last squad moves forward and occupies the straight line position from 4 to 12. The headquarters element will normally locate in the center of the formation. If three machineguns are available, one will be placed at each comer in such a manner to allow flexibility in providing final protective fires down either of its two sides. If only two machineguns are available, one may be placed to cover the two sides deemed most vulnerable to attack. The second machinegun should be kept with the headquarters element under control of the unit leader. Firing positions should be pre pared at all three comers.
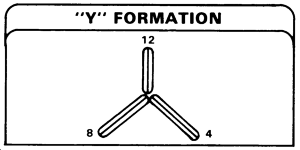
"Y" DEFENSE
The third defensive formation is the "Y." This formation, like the triangle, may be utilized as an offensive formation, usually in an ambush. Depending upon the situation, it can be a very effective defensive formation.
|
Advantages are:
Disadvantages are:
|
The recommended technique for emplacement of this formation is for the unit leader to take one element and the headquarters forward and establish the center of the sector. This establishes the 12 o'clock position. The remaining elements stay in security positions. Since all legs of the "Y" are mutually supporting, the commander has the option of having all soldiers on each leg face the same direction, or he may alternate fire teams. Once the decision is made regarding which method is to be used, subsequent legs of the "Y" must conform to the initial one. Once the lead squad is emplaced, the next squad moves forward to the center point and is closely directed into the 8 o'clock position. After the second element is in position, the third element moves forward to the center point and is closely directed into the 4 o'clock position. If three machineguns are available, one is positioned at each leg, with possible final protective fires across the fronts of adjacent legs. If only two are available, they are positioned at the center point to provide fire down the legs. This positioning of two is not preferred because it does not allow for dispersion; plus, the machineguns are bunched and extremely vulnerable to indirect fire.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

