Chapter 4
|

The purpose of the offense is to defeat, destroy, or neutralize the enemy. Infantry brigades normally conduct offensive operations in restrictive terrain under day or night conditions in support of division or corps operations. Brigades may also conduct offensive operations independently. Offensive operations are rapidly executed, violent operations against over-matched opponents that seek weaknesses and exploit success. The brigade attacks as part of a synchronized division, corps, or joint task force plan by fixing the enemy while maneuvering to defeat him. The concept of establishing a base of fire with one force and maneuvering with another is fundamental to offensive maneuver based warfare. These two distinct forces have separate missions. The base of fire force uses indirect and direct fire to reduce the enemy's capability to interfere with the movement of the maneuver force and, within its capabilities, to destroy the enemy. The mission of the maneuver force is to close with and defeat the enemy. The maneuver force is normally assigned the main effort to accomplish the brigade's purpose. Many historical examples reveal the unique characteristics of infantry operations, which are marked by stealth, resourcefulness, a high degree of discipline, innovation, and the will to operate in terrain and environments where they are least expected.
Section I
FUNDAMENTALS OF BRIGADE OFFENSE
The offensive is the commander's primary means of gaining the initiative and limiting the ability of the enemy to recover from the initial shock of the attack. Through constant offensive pressure on the enemy, he is best able to force the enemy to conform to his intent and retain his own freedom of action. A thorough understanding of enemy doctrine is critical to success in all offensive operations.
4-1. CHARACTERISTICS OF OFFENSIVE OPERATIONS
Successful offensive operations are characterized by concentration, surprise, tempo, flexibility, and audacity. (FM 100-5 discusses these characteristics in detail.)
a. Concentration. When concentrating the effects of forces for the attack, the brigade commander must avoid set patterns or obvious movements that would indicate the timing or direction of the attack. He designates, sustains, and shifts the main effort as necessary. Mobility, speed, security, and OPSEC are essential to concentrate forces successfully. Concentration also requires the close cooperation and integration of CS and CSS elements. Success depends on the ability to concentrate unexpectedly and achieve combat superiority at a decisive place and time.
b. Surprise. Achieve surprise by striking the enemy at a time or place, or in a manner, for which he is unprepared. Avoid the enemy's strengths and attack his weaknesses. Strike him when and where he least expects it through night attacks, infiltrations, or rapid insertion of airborne or air assault forces.
c. Tempo. Tempo is the rate of speed of a military action. By controlling the tempo (friendly and enemy) of the operation the commander maintains the initiative. Commanders seek a tempo that puts pressure on the enemy to effectively keep him off balance and unable to respond. A quick tempo demands an ability to make quick decisions, to execute operations to deny the enemy a pause, and to exploit opportunities according to the commander's intent. Tempo can be either fast or slow. Commanders adjust the tempo to achieve synchronization. Speed is preferred in order to keep the enemy off balance, but establishing the conditions for decisive actions may require the tempo to be slowed as the pieces are set in place. Once ready, the tempo is increased, and the action takes place rapidly. Tempo provides the necessary momentum for attacks to achieve their objectives. Tempo is a combination of speed and mass that creates pressure on the enemy. Commanders build the appropriate tempo into the operations through careful planning. Commanders identify the best avenues for attack, plan the battle in depth, provide quick transition to other phases of the offense, and concentrate and combine forces effectively.
d. Flexibility. The plan of attack must foresee developments, reflect the uncertainties of offensive combat and provide for the exploitation of opportunities that arise during the course of operations. Subordinates must understand the brigade commander's intent so well that they can properly exploit battlefield opportunities even when communications fail. The commander must be capable of changing quickly from offense to defense (and vice-versa), conducting continuous operations, and fighting on an integrated battlefield. He must be able to cope with diversions from the original plan such (as changes in direction or location of the main effort. The understanding of doctrine and commander's intent coupled with the use of SOPs, drills, and mission orders are the keys to flexibility.
e. Audacity. Audacity is the willingness to take bold action to achieve decisive results. The audacious commander's actions, though quick and decisive, are based on a reasoned approach to the tactical problem and on his knowledge of soldiers, terrain, and enemy. The brigade maneuvers to maintain a positional advantage over the enemy, seeks to attack the enemy on the flank or rear, and exploits success once achieved. Audacious commanders throughout history have used the "indirect approach." To defeat a numerically superior opponent, they strike at an unexpected time and place.
4-2. ORGANIZATION OF OFFENSIVE BATTLES
As a means to organize thoughts and information, the commander views tactical offensive battles as operations in depth. These operations consist of three interrelated parts as follows:
- Deep operations.
- Close operations.
- Reconnaissance and security actions.
- Main effort.
- Reserve action.
- Rear operations.
a. All operations are interdependent on each other, and all are equally important. To defeat the enemy, the commander applies combat power within the construction of deep, close, and rear operations and protects his forces.
b. The brigade normally plans and conducts deep operations within its battlefield framework and may participate in the execution of deep operations as part of the division or corps deep fight.
4-3. OFFENSIVE OPERATIONS PLANNING
Planning for possible operations is a continuous process on the part of the brigade commander and staff. A continuing analysis of METT-T is conducted as part of the estimate process. The four general phases of offensive operations are preparation, attack, exploitation and pursuit.
a. Reconnaissance and security are key precursors to all offensive operations. Reconnaissance is undertaken to obtain information about the activities and resources of the enemy. It also provides fresh information on the terrain to reduce the unknown and facilitate the rapid execution of the main or supporting effort. Reconnaissance provides information on enemy dispositions and helps guide attacking forces against enemy weaknesses. The brigade uses the eyes and ears of every soldier to supplement existing information on the enemy and terrain. Reconnaissance by air, ground, and intelligence units is continuous and aggressive before and during offensive operations. Information must be evaluated, interpreted, and disseminated rapidly or its value is lost.
b. Security operations are designed to deny information to the enemy and provide friendly reaction time, maneuver space, and protection to the main body. Security operations include screening, guarding, covering, and area security. (See Chapter 2 for a discussion of reconnaissance and security and Chapter 5 for reconnaissance and security operations.)
c. Available maneuver forces, engineers, FA, ADA, attack helicopter, CAS, and EW assets must be synchronized at the decisive point and time to ensure tactical success. This requires that the brigade mission be analyzed and translated into specific objectives that through control of an area or destruction of an enemy force, lead to defeat of the enemy. Designing main and supporting efforts and tasks to forces in the attack contributes to mission understanding and clarifies responsibilities of attacking battalions. The brigade plan must designate a--
- Main effort.
- Supporting effort(s).
- Follow-and-support force, if any.
- Reserve.
d. The brigade commander weights the main effort by--
- Assigning tasks and purposes to supporting effort units to create the conditions for main effort success.
- Allocating additional ground maneuver forces.
- Prioritizing combat multipliers such as fires, close air support, engineers, air defense, intelligence assets, and CSS.
- Narrowing the zone.
- Selecting favorable terrain.
- Striking assailable enemy flanks.
- Supporting with direct fires.
- Using follow-and-support elements.
- Prioritizing employment of attack helicopters.
- Limiting the number of tasks assigned to the main effort.
- Establishing priorities of fire.
- Assigning priority targets.
e. The supporting effort contributes to the success of the main effort by--
- Fixing enemy forces to facilitate the main effort.
- Controlling terrain that facilitates maneuver of the main effort.
- Destroying enemy forces that would otherwise hinder the main effort.
- Deceiving the enemy as to the location of the main effort.
- Preventing or delaying enemy concentration to defeat the main effort.
f. Follow-and-support forces are committed forces that follow a force conducting an offensive operation normally an exploitation or a pursuit. They usually reinforce and support the main effort-they are not the reserve. Follow-and-support forces must be able to keep up with the attacking echelon and maintain close liaison and coordination. Follow-and-support units are assigned missions that would slow the attacking forces advance such as securing lines of communications, destroying pockets of resistance, securing key terrain and blocking movement of enemy reinforcements.
g. Follow-and-assume forces are committed forces that follow a force conducting an offensive operation. The follow-and-assume force is prepared to continue the offensive when the lead force is fixed, attrited, or otherwise unable to continue.
h. Reserves are uncommitted forces that are kept available to be used at the decisive location and time to exploit success or to ensure mission accomplishment. The purpose of the reserve is to provide flexibility and retain the initiative through offensive action. The best use of the reserve is to capitalize on an exposed enemy weakness or unexpected advantage by a decisive attack. The size of the reserve is determined by the commander during his estimate of the situation. In general, the more vague the situation, the larger the reserve. The reserve is positioned to--
- Exploit success.
- Permit rapid movement to points of probable employment.
- Weight the main effort by destroying or blocking enemy counters to it.
- Provide security to unoccupied terrain within the brigade sector.
- Provide the greatest protection from hostile observation.
- Provide fire and support consistent with mission requirements.
The commitment of the reserve signals a loss of flexibility for the brigade and should be reported immediately to higher headquarters. Reserve planning guidance should be detailed enough to provide the reserve force commander a clear understanding of the brigade commander's intent, commitment criteria, and priorities. This guidance should be clear enough to enable the reserve force commander to develop effective plans and rehearse for the most likely contingencies. The commander must plan to reestablish a reserve at the earliest opportunity after the original reserve is committed. The commander, himself, decides whether or not to commit the reserve.
4-4. CONDUCT OF OFFENSIVE OPERATIONS
During execution, the momentum of the attack must be maintained. The force closes quickly on the objective with the greatest combat power. Halts on intermediate objectives should normally be avoided because they slow the attack and increase vulnerability.
a. As the attack progresses, the commander may shift the weight of the attack to take advantage of tactical success, avoiding suspected enemy strength and taking advantage of more favorable routes or situations as they are discovered by reconnaissance elements.
b. As the assault begins, units close quickly on the objective before the enemy can react. Direct-fire weapons from overwatch units must be integrated with indirect-fire weapons. Weapon systems lift and shift their fires as fires are masked. Obstacles must be quickly overcome by breaching and bypassing.
c. As soon as the objective is seized, supporting weapons adjust to protect consolidation and reorganization. To eliminate the enemy from the objective, the unit may have to systematically clear it using the appropriate control measures. The unit forms a hasty defense, establishes security, plans fires, and conducts reconnaissance. Preparations are made for follow-on missions. Key personnel, wounded or killed in action are replaced. The WIAs, KIAs, EPWs, and equipment are evacuated. Supplies, ammunition and equipment are redistributed, and the C2 facilities relocate.
The basic forms of maneuver in the offense are envelopment, turning movement, infiltration, penetration and frontal attack.
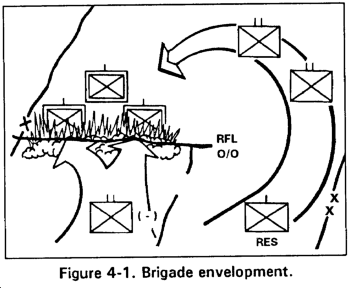
a. Envelopment. An envelopment seeks to apply friendly strength against an enemy weakness. To accomplish this, the commander fixes the enemy from the front. He then maneuvers a force around the enemy's front and strikes his flank or rear. He forces the enemy to fight him as he advances along lightly defended or undefended avenues of approach. Envelopment requires the enemy to have an open flank weakness in his positions, or a gap in his lines, which affords the enveloping force an exploitable weakness.
(1) The brigade may use the envelopment as a form of maneuver for its own attack or it may take part in one as part of a larger force. In an envelopment, the brigade makes a supporting attack with one or more battalions. The remaining units maneuver against the enemy's flank to destroy him or seize objectives in his rear. As part of a larger unit's envelopment, the brigade may have the envelopment role or a supporting role (Figure 4-1).
(2) Envelopments require task-organizing the brigade based on METT-T and the commander's intent. The holding or fixing forces must have sufficient combat power to keep the enemy fully engaged during the movement of the enveloping force. The supporting and enveloping forces may launch the attack at the same time or at staggered times. The attacker always plans preparatory fires but does not always fire them. Normally, the brigade also retains a reserve; its size is based on the estimate of the situation. The reserve follows the enveloping force to exploit success or to respond to an unforeseen contingency.
(3) Variants of the envelopment are the double envelopment and the encirclement. In the double envelopment the commander seeks to pass around both enemy flanks at the same time. This action requires close coordination and precise timing. An encirclement occurs when the enemy loses control of all ground routes of evacuation and reinforcement. This variant offers the best opportunity for fixing the enemy in position, it usually permits his capture or destruction.
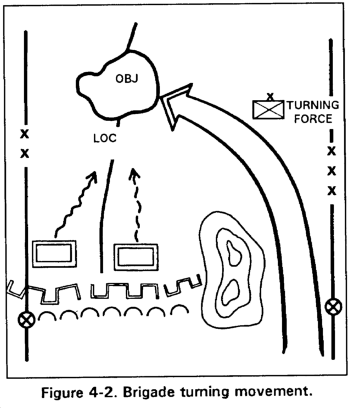
b. Turning Movement. Brigades normally participate in turning movements as part of a larger force operation. In executing a turning movement, the brigade passes around the enemy force (avoiding his main forces) to secure an objective deep in the enemy's rear (Figure 4-2). This maneuver forces the enemy to abandon positions or divert major forces to counter the attack. Airborne and air assault forces are well suited for conducting turning movements because of their air mobility. Deep fires become more important in this type of maneuver to protect the maneuver force and to attack the enemy, especially when unaccompanied by artillery.
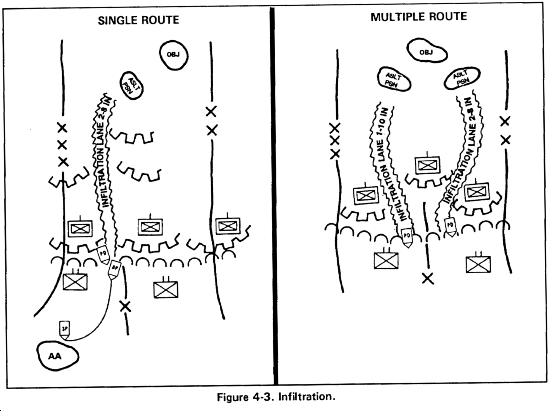
c. Infiltration. In the offense, infiltration is the concealed movement of all or part of the attacking force through enemy lines to favorable positions in the enemy rear. Because infiltration alone can rarely defeat an enemy defense, it normally takes place with some other form of maneuver.
(1) The commander will rarely infiltrate all of his brigade. However, he may require some elements to move through gaps in the enemy's defense to--
Attack lightly defended positions.
Occupy an overwatch position from which to support the main effort by fire.
Seize or secure key terrain.
Conduct ambushes, destroy vital facilities, or harass and disrupt the enemy's defenses.
Identify targets or to obtain intelligence.
(2) Infiltration is most feasible during limited visibility, over restrictive or difficult terrain through areas unoccupied by the enemy, or through areas not covered by enemy observation and fire. These conditions often allow undetected movement of small elements when movement of the entire force would present more risk. It requires resourcefulness, a high degree of discipline, expert land navigational skills, and innovation (Figure 4-3).
(3) Infiltrations are conducted in five phases: patrol, prepare, infiltrate, consolidate, and execute.
(4) Infiltration requires extensive reconnaissance that identifies the enemy disposition across the area to be infiltrated identifies infiltration lanes, locates assault positions, identifies enemy weaknesses, and observes enemy activity.
(5) Based on the initial reconnaissance, friendly forces organize into appropriate sized elements and move through and around enemy positions. They may use single or multiple lanes. The choice depends upon the size of the force to be infiltrated, the detail of information on enemy dispositions and terrain the time, and the number of lanes available. (For more information on the employment of infiltration, see FM 7-20.)
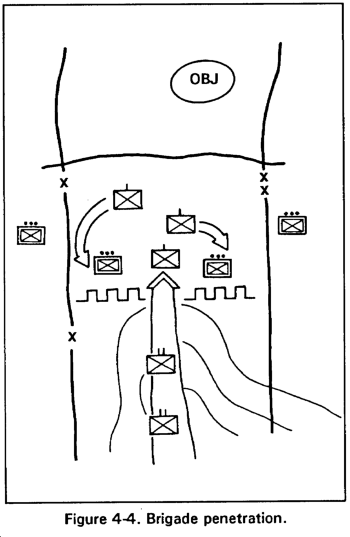
d. Penetration. The purpose of a penetration is to break through prepared enemy positions by concentrating overwhelming combat power on a narrow front. Units penetrate when enemy flanks are not assailable and when time does not permit some other form of maneuver (Figure 4-4). A successful penetration requires the concentration of all combat multipliers, to include use of limited visibility, stealth and covered and concealed terrain. Infantry brigades ideally penetrate the enemy by infiltrating through the enemy positions during limited visibility. The brigade attacks the enemy at the point of penetration from an unexpected direction achieving surprise and concentration of combat power. Penetrations have three stages: initial rupture of enemy positions, roll-up of the flanks on either side of the gap, and exploitation to secure deep objectives.
(1) A penetration requires a massing of forces and fires against a narrow portion of the enemy defense before he can move forces to halt the attack. Fires (including smoke) on the defensive position help suppress and isolate forces at the point of attack to deprive the enemy of mutual support and defensive fires. Once the enemy is overwhelmed at the point of attack, infantry holds the shoulders of the penetration and assists other forces as they pass through the gap to secure the objective.
(2) The initial stages of the penetration often favor small-unit operations. Infantry forces remain under decentralized control until they concentrate just before the attack. Suppression of the enemy is critical at this stage since infantry on the move is vulnerable to enemy fires.
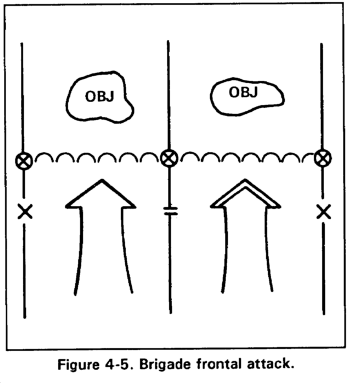
e. Frontal Attack. The purpose of a frontal attack is to overrun and destroy or capture a weakened enemy, or to fix an enemy force in position to support another attack. A frontal attack is the least desirable form of maneuver, and the brigade normally conducts it as part of a larger force. The frontal attack strikes along the enemy front within the zone of the brigade (Figure 4-5). During the attack, the brigade commander seeks to take advantage of the enemy position. Subordinate units try to seize their objective from a direction other than the front if the terrain and enemy situation permit.
The brigade commander selects the initial attack formation that offers the best chance of success. However, the brigade subordinate commanders must be flexible to change their formations and organizations rapidly to conform to changing situations. Maintaining mutual support between maneuver elements should be a key consideration, and the piecemeal commitment of forces should be avoided. Commanders must understand time-spice relationships when planning movement. The figures within this paragraph provide a planning distance. The actual distance used is based on METT-T. The brigade may employ any of several basic formations in offensive operations.
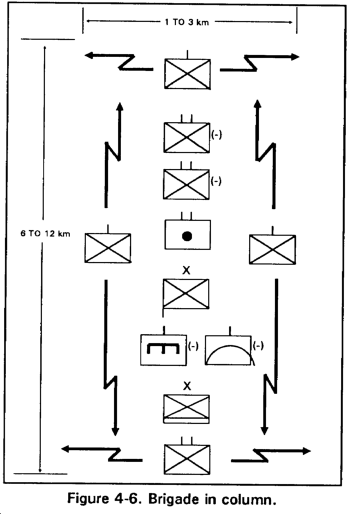
a. Brigade in Column. The commander may opt to use a column of battalions for the initial attack--
- To attack on a narrow front, at night, or during limited visibility, if terrain or enemy defenses require it.
- To provide the depth necessary for a sustained attack when the strength, composition, and location of the enemy reserves so dictate.
- To retain the initiative and permit flexibility.
- To keep the following battalions in position to move through or around the lead elements to maintain the momentum of the attack.
- To provide a degree of security by keeping the following battalions in position to counter threats from the flanks.
Forces in column can concentrate only a part of their fires to the front; thus they are subject to piecemeal commitment and slower deployment to the front. The brigade requires multiple routes in their zone if they are to attack effectively from columns. Passage of the brigade through an area in column requires more time than other formations (Figure 4-6).
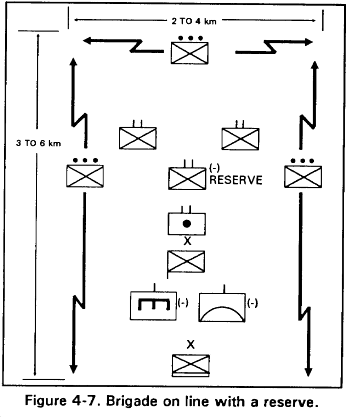
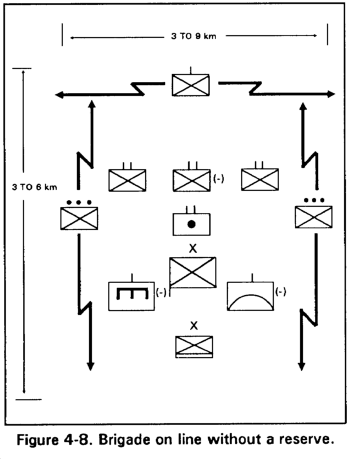
b. Brigade on Line. A brigade may be on line with or without a reserve.
(1) With a reserve. This formation consists of two or more battalions of the brigade on line with the remaining forces designated as the brigade reserve (Figure 4-7). The reserve provides flexibility and security because it is a major force that can exploit the success of, or assume the mission of, a leading battalion. This formation allows the brigade to attack on a broad front. This formation may be used--
Against defensive positions when great depth in the attack is unnecessary.
In the initial attack against an enemy position known to be so thin and weak that it can be ruptured by an attack on a relatively wide front.
In the envelopment when the assailable flank is of the extent that the brigade can envelop on a broad front.
(2) Without a reserve. When the requirement for speed outweighs that of security, this formation may be used with two or more battalions abreast without a reserve (Figure 4-8). Another use is to exploit a friendly nuclear or chemical attack on an extended front. Reconnaissance across the brigade front is essential to provide knowledge of enemy dispositions and areas of nuclear or chemical contamination. This enables forces to reposition as necessary to maintain the momentum of the attack. The terrain must be suitable for this formatting and the enemy situation must not initially dictate a reserve. This formation needs adequate maneuver space and avenues of approach and sufficient gaps or weak spots in the enemy line. The brigade must also be capable of delaying decisive action by the enemy reserves through the employment of fire support, screening forces, or appropriate maneuver. Once contact is made, the commander may designate the least committed unit to provide an on-order reserve.
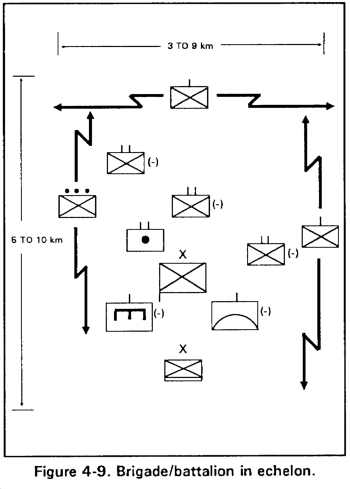
c. Brigade in Echelon. This formation is used when advancing in a wide zone, when a flank threat exists, or when the envelopment of an enemy force is planned. The echelon formation provides good flank security and depth, but flexibility and ability to develop combat power to the front is more limited than in some other formations (Figure 4-9).
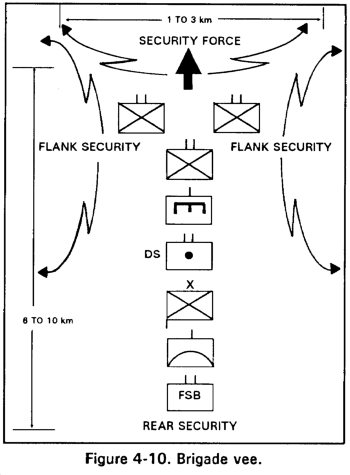
d. Brigade Vee. When two or more battalion TFs of the brigade are on line, any remaining battalion TFs may be designated as the brigade reserve. The reserve can exploit success, assume the mission of the leading TF, or counter enemy threats to the brigade mission. The brigade vee (Figure 4-10) may be employed when great depth in the attack is not required, such as in the limited objective attack. It may also be used in the initial attack against a weak enemy, vulnerable to defeat by an attack on a reactively wide front. In the envelopment, this formation can be used when the brigade can envelop an assailable flank on a broad front. The lead TFs receive the priority of fire support.
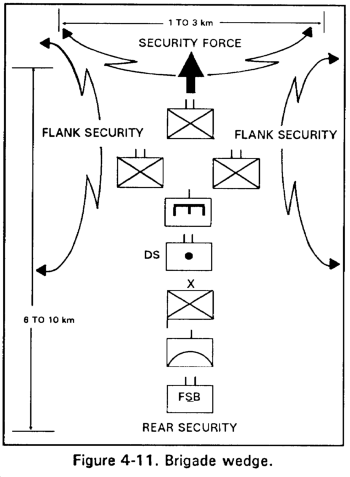
e. Brigade Wedge. Like the brigade vee, the brigade wedge (Figure 4-11) offers the commander flexibility and security in all directions. It is often used when the enemy situation is vague, and contact is imminent. The wedge facilitates control and permits sustained effort by reserving two task forces for maneuver against the enemy.
NOTE: Size, composition, and distance of operation from the main body for advance, flank, and rear security will vary according to the commander's estimate of the situation.
Section II
TYPES OF OFFENSIVE OPERATIONS
The brigade prepares for offensive operations that support the scheme of maneuver. The types of operations may be conducted in sequence in a successful battle, beginning with a movement to contact to locate the enemy and ending with the destruction of the enemy through pursuit. The four general forms of the tactical offense are--
Movement to contact.
Attack.
Exploitation.
Pursuit.
Brigades may conduct both hasty and deliberate attacks.
A movement to contact is an attack to gain or reestablish contact with the enemy. It is used when the tactical situation is not clear or when the enemy has broken contact.
a. The brigade is normally assigned an axis of advance or zone of action and an objective. Although a movement to conflict may result in taking a terrain objective, the primary focus should be on the enemy force.
b. A movement to contact must maintain the commander's freedom of action upon contact if the commander is to maintain the initiative. The following principles apply to a movement to contact:
- Lead with a small, mobile, self-contained force to locate and fix the enemy.
- Task-organize the brigade to be able to deploy and attack rapidly in any direction.
- Maintain mutual supporting distances to facilitate response.
- Use aggressive movement.
- Use decentralized execution.
c. The key fire support task during a movement to contact is to provide immediate responsive fires to the maneuver units initially making contact. Consider the following options:
- Establish priority of artillery fires and assign priority targets to forces most likely to make the first contact.
- Assign COLTs to increase the number of trained observers looking into likely engagement areas.
- Establish quick-fire channels to provide lead elements a direct link to the field artillery battalion.
d. Aircraft that provide CAS, air interdiction and airlift of troops and supplies can also provide information on the terrain to be traversed. They can detect enemy units, obstacles, or movement in the area in which the brigade can conduct a movement to conflict. Intelligence units at division or corps and USAF aircraft with long-range surveillance equipment may locate the enemy before contact.
e. Consider establishing priority of artillery fires and assigning priority targets to forces most likely to make the first contact, assigning COLTs to increase the number of trained observers looking into likely engagement areas, and establishing quick-fire channels to provide lead elements with a direct link to the field artillery battalion.
f. Air defense systems protect the brigade movement by moving ADA with security forces to selected sites forward, to the flanks, and to the rear of the main body. Dispersed formations reduce vulnerability to nuclear or chemical attack, but they also complicate C2 and mutual support. However, reconnaissance and liaison between units can reduce these problems. The brigade's CSS units must also be capable of uninterrupted movement.
g. The brigade main CP normally displaces as far forward as possible before starting movement then displaces as required to provide continuous support. The tactical CP operates forward with the main body to ease decision making and transition to other missions.
h. In organizing for a movement to contact, the brigade commander must anticipate contact with the enemy during movement. He considers requirements for maneuver and fire support upon contact. The infantry brigade uses one of three techniques to conduct a movement to contact--the approach march, the search and attack, and the reconnaissance in force.
(1) The approach march technique is one technique used for conducting a movement to contact. It is used when direct contact with the enemy is imminent. The brigade is fully or partially deployed. It is used to develop the situation early to provide an advantage before decisive engagement. The brigade is assigned an axis of advance or a zone, and march objectives are assigned to orient movement. The focus of the movement to contact remains enemy, not terrain. The brigade may not be required to seize, hold or occupy the objectives. The march objective can be any terrain feature that is easy to find and that is a possible enemy location. If the unit does not contact the enemy before it reaches the last objective, it establishes a hasty defense and seeks guidance from higher headquarters. The brigade usually establishes advance, flank, and rear guards to protect the main body.
(a) Advance guard. The main body normally furnishes the lead element and controls the advance guard. The advance guard is organized to fight through small concentrations of enemy forces. It makes sure the main body can deploy uninterrupted into attack formations. Required CS, such as engineers and artillery, are integrated into the advance guard. The R&S elements and systems assist in detecting the enemy before actual contact.
(b) Flank and rear guards. Flank and rear guards protect the main body from ground observation and surprise attack. These guards must have enough combat power to defeat enemy forces or to delay an enemy attack long enough to allow the main body to deploy. They operate under control of the brigade. The flank guard travels on routes parallel to the main body and within range of supporting artillery. It moves by continuous marching or by successive or alternate bounds to occupy key positions on the flanks of the main body. The rear guard follows the main body and provides rear security to the brigade. If adjacent or following units secure the flanks or rear of the brigade, the size of the brigade flank and rear guards can be smaller.
(c) Main body. The main body contains the bulk of the brigade's combat power. The main body must be capable of conducting either a hasty attack or a defense. The march formation of the main body must permit the greatest flexibility during movement and upon contact with the enemy.
(2) The search and attack technique is used when the enemy is operating in small, dispersed elements or when the task is to deny the enemy movement in an area. The battalion is the basic operational unit in search and attack operations. The brigade assists by ensuring the availability of adequate supporting fires, mobile transportation assets, timely and accurate intelligence, and reserve forces. Search and attack operations are accomplished by organizing the brigade into find fix, and finish forces; each has a specific task and purpose. The finish force is the main effort. Some considerations for conducting search and attack operations include:
(a) The IPB process is critical to the conduct of search and attack. The brigade does not usually have the luxury of conducting a police call type search of the zone. The S2 must focus the brigade's search efforts on likely enemy locations. The enemy situation template must be continuously refined as new information becomes available.
(b) The brigade commander task organizes the finish force first ensuring that it has enough combat power based on the anticipated size of the enemy. The finish force may move at some distance behind the find force, or it may be at a PZ and air assault to the objective once it is located. The air assault technique is dependent on the availability of LZs near the objective, weather, and availability of aircraft. The finish force must be responsive enough to have reached the objective before the enemy can displace. The S2 must provide the commander with his estimate of how long it will take the enemy to displace.
(c) The fix force isolates the enemy once the find force finds it. It blocks both escape and reinforcement routes. Indirect fires are incorporated into the fix plan. The fix force is placed to block routes identified by the S2. Depending on the mobility of the enemy and the likelihood of the find force being compromised, the fix force may have to be emplaced before the find force enters the AO.
(d) The size of the find force will be dependent on the degree of certainty associated with the enemy template. The more vague the situation is, the larger the find force will be. The find force will consist of infantry, air, and electronic assets. It usually uses zone reconnaissance techniques to reconnoiter NAIs identified by the S2. The brigade fix-and-finish plan must consider the possibility of the find forces being compromised.
(e) Units may be rotated through the find, fix, and finish roles, but the main effort remains the finish force. Rotating roles may require a change in task organization and additional time for rehearsal.
(f) Available fire support must provide flexible, rapid support throughout the area of operation. This includes the ability to clear fires rapidly. In order to clear fires rapidly, units must track and report the locations of the unit's subordinate units. The capability must exist to mass fires quickly in support of the main effort. Because of the uncertainty of the enemy situation the commander avoids command or support relationships that prevent shifting assets when necessary. Supporting fires should be flexible and destructive. They should also enhance the ability of a highly mobile attack force to destroy an enemy force located and fixed by other forces.
(g) The brigade commander provides the necessary control, but he allows for decentralized actions and small-unit initiative to the greatest extent possible. This includes establishing the proper graphic control measures to control movement and the synchronization of all brigade assets to enhance combat power.
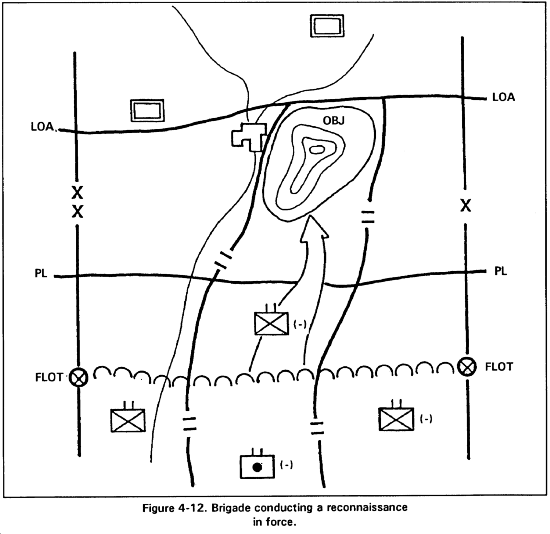
(3) Reconnaissance in force is a movement to contact technique used to obtain information and to locate and test enemy disposition, strengths, and reactions. Although its primary purpose is reconnaissance, the reconnaissance in force may discover weaknesses in the enemy dispositions which, if promptly exploited, would permit tactical success. The brigade commander may conduct his own reconnaissance in force or conduct a reconnaissance in force at the direction of a higher headquarters.
(a) When deciding to reconnoiter in force, the commander considers the following:
His knowledge of the enemy situation.
Urgency and importance of additional information.
Efficiency and speed of other intelligence collection agencies.
Extent to which his plan of action may be divulged by the reconnaissance in force.
Possibility that the reconnaissance may lead to a general engagement.
(b) The reconnaissance in force is planned and executed as an attack with a limited objective (Figure 4-12). The objective should be of such importance than when threatened, it forces the enemy to react. Securing a terrain objective is not the purpose--gaining the most information of the enemy is. The plan should address the possible withdrawal or extrication of the reconnoitering force if necessary. When possible, the objective should contribute to an envelopment or penetration of enemy defenses, thereby facilitating future operations.
(c) The reconnoitering force is normally at least battalion size. However, the size of the force depends on the mission and situation. The force must always be strong enough to make the enemy react. The brigade commander normally retains sufficient maneuver forces to exploit enemy weaknesses or extract his committed forces. The composition of the reconnoitering force may include:
Infantry battalion (+ ).
Artillery battery.
Engineer platoon.
ADA platoon.
Additional MI assets (GSR teams, interrogation teams, and so forth).
Army aviation (aero scouts).
Additional signal assets.
i. In a division's movement to contact the brigade may move as part of the division main body, or it may provide units for the division's advance, flank, or rear guards. It may control some division security forces or act as the covering force for the division. When assigned as a division covering force, the brigade is usually reinforced with aviation, artillery, engineers, and CAS (when available). Suppression of enemy air defense must be a top priority if CAS missions are planned. The brigade commander must provide clear guidance on bypassing to maintain momentum of movement while securing the main body. (See FM 71-100 for more information on division movement to contact.) The brigade commander forms his forces for movement on either a single axis or multiple axes.
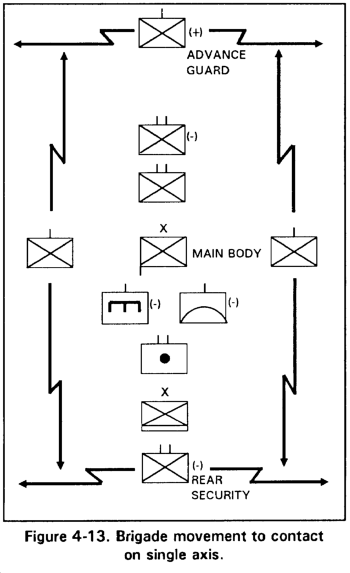
(1) Single axis. The single axis is used for ease of control or when terrain permits movement on only one axis. The disadvantages are that it takes longer to deploy, increases column length and permits the enemy to achieve the greatest delay with the least force (Figure 4-13).
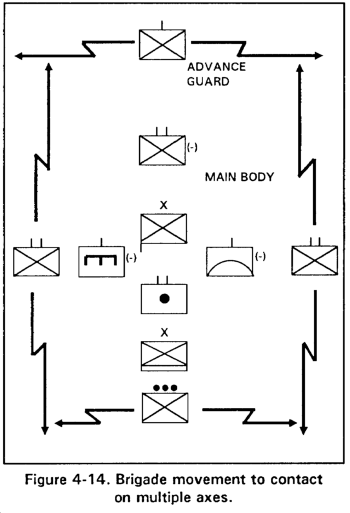
(2) Multiple axes. Multiple axes are normally a movement to contact because they allow greater flank security and mutual support. Forces can deploy more quickly from multiple axes and can present multiple threats to the enemy. However, multiple axes do complicate C2 (Figure 4-14).
j. A meeting engagement is normally the result of a movement to contact. It is the initial contact that occurs when a moving force makes contact with a moving or stationary enemy force. The main characteristics of a meeting engagement are a limited knowledge of the enemy and limited time for the commander to develop the situation. A meeting engagement is a decision point where the commander decides to retain the initiative and attack or where he takes up a hasty defense. The action ceases to be a meeting engagement when the situation has been developed and other actions are undertaken such as a hasty attack or defense. However, if the advance guard or leading battalion can defeat the enemy force, the movement to contact continues. The brigade commander must clearly state his intent and let subordinates know how much initiative they may use in reacting to a meeting engagement.
k. The goal, once contact is made, is to overcome the enemy quickly and decisively before he can effectively react. To do this, the commander must have his force prepared for contact, must have good information as to the situation (either through good reports or personal observation), and must immediately issue instructions for action. If the enemy force is also moving, speed in both decision making and execution is important.
Attacks can be hasty or deliberate. The principal difference is that in a deliberate attack there is more time available for planning and preparation.
a. Hasty Attack. A hasty attack is normally conducted following a movement to contact or a meeting engagement. The brigade attacks with the resources it has immediately available and with a minimum of reorganization to maintain momentum or to take advantage of the enemy situation. Attacking units may bypass local obstacles and pockets of resistance that do not threaten overall success, according to the higher commander's intent. The reduction of bypassed enemy units then becomes the responsibility of the higher commander. The commander must consider the inherent danger that bypassed enemy units can inflict on trail CS and CSS assets.
(1) Fire support planning for the movement to contact and the hasty attack is a continuous process. The FSCOORD must control the displacement of artillery so that fire support to committed units is not interrupted. The division attacks deep targets, suppresses enemy air defense, and provides counterfire. Specific considerations are as follow:
Plan fires on likely counter attack routes.
Use preparation fires to fix the enemy in coordination with the unit's assault force.
Synchronization direct and indirect fires at the point of penetration for the final assault. Consider requesting additional fire support assets from the division artillery.
Choose only those targets that are critical and attack the targets ruthlessly. Elaborate plans will fail.
Consider FASCAM to block counterattack routes and smoke to screen friendly movement.
Recommend other radar zones to prioritize the engagement of enemy artillery that can affect the brigade's operations.
(2) The commander must quickly identify the critical points in the battle where deep fires are most useful. In the movement to conflict and hasty attack, tactical air support and deep fires can be used to interdict the movement of enemy counterattack forces, to isolate the enemy at times and places critical to the brigade, and to destroy the enemy's artillery units, CPs, and logistic units.
(3) When opposing forces are moving, the initial advantage in hasty attacks belongs to the force that first fixes and contains the enemy, deploys into combat formations, and maneuvers additional forces to the flank and rear from where the enemy can be destroyed by fire or assault. The reaction is RDRD: return fire, deploy, report and develop the situation.
(4) Preparation time is short, and orders must be brief during the hasty attack. The brigade commander should be well forward to influence the battle. Although tactical CPs need to be close to their commanders for assistance in battle direction and information flow, their movement must not interfere with attack formations.
(5) Commanders ensure visual contact is maintained with leading units. When one battalion follows another, the trailing battalion is responsible for maintaining contact. The main CP should monitor the leading force's command net. If the hasty attack is not succeeding, the commander may elect to establish a defense on the best defensible terrain until greater combat power can be achieved.
(6) The most critical control measures are objectives, phase lines, checkpoints, axes of advance, and boundaries. Intermediate objectives may be used to coordinate the essential movements of attacking forces. On-order objectives are used to orient following forces and reserves quickly, this increases the flexibility of tactical maneuver.
(7) When the maneuver force attacks, the attacking battalions should receive FAAD priority.
(8) Engineers should provide breaching support to maneuver forces, protect flanks by creating obstacles on avenues of approach, and assist in organizing captured ground against counterattacks. Engineers should plan for situational obstacles on the flanks and upon consolidation on the objective.
b. Deliberate Attack. A deliberate attack is characterized by thorough, detailed planning; specific task organization; rapid concentration of forces; exploitation of enemy weaknesses; and violent execution. It may involve overcoming strong enemy forces in established positions. A deliberate attack is undertaken after thorough reconnaissance, acquisition and development of targets, and analysis of all other factors affecting the situation. This type of offensive operation requires a sudden, violent concentration of combat power in an area where there is a high probability of surprise and success.
(1) This type of attack is usually necessary against a well-organized enemy who cannot be turned or bypassed. Normally, the scheme of maneuver for the deliberate attack employs three elements--assault, support, and breach. The assault is the main effort.
(2) In organizing for a deliberate attack, the brigade commander must make the most of his available combat power. If given additional forces, he must integrate them with brigade forces to create the most potent force. The following considerations based on METT-T apply to the conduct of a deliberate attack:
(a) An enemy oriented deliberate attack requires knowledge of the enemy location. Otherwise, it is a movement to contact. A sizeable reconnaissance effort will usually be required.
(b) Use terrain to avoid enemy fires and to exploit gaps in his defenses. This dictates the development of a comprehensive reconnaissance plan.
(c) Use smoke to conceal movement.
(d) Use artillery and mortars (including smoke) to suppress adjacent enemy positions. Concentrate fires at the breach point.
(e) Plan redundant breaching assets.
(f) Attack adjacent positions by fire or maneuver. The support element must isolate the objective.
(g) Mark the breach lane. Use a breach OIC to control passage through the breach.
(h) Preparation fires may be used, but they forfeit surprise. If fires are used, the assault must quickly follow the preparation. Consider echeloning fires from larger (artillery) to smaller (mortar) systems.
(i) Position the brigade reserve within the formation to permit rapid movement to the point of probable employment and to provide security.
(j) After securing the brigade objective, reorganize rapidly and prepare to continue the attack on order. Make the greatest use of supporting fires and use minimum forces to retain control of objectives. Disperse the remaining units to defend against an enemy counterattack or to prepare to continue the attack. Designate elements to maintain contact with the enemy to keep him off balance and to obtain information.
(k) If the brigade is required to continue the attack issue a FRAGO to subordinate units with instructions on the following:
Designation of main effort and how it is to be supported.
Resupply of units.
Passage of lines within the brigade.
Shift in direction of movement.
This is the bold continuation of an attack to increase success and take advantage of weakened or collapsed enemy defenses. Its purpose is to prevent reconstitution of enemy defenses, prevent enemy withdrawal, secure deep objectives, and destroy enemy C2 facilities, logistics, and forces.
a. The exploitation is initiated when an enemy force is having difficulty maintaining its position. Although local exploitations may appear insignificant, their cumulative effects can be decisive. Depending on the situation and its task organization, the brigade can exploit its own success, it can be used as an exploiting force for a higher echelon, or it can follow and support another exploiting force. Exploiting forces can have the mission of securing objectives deep in the enemy's rear, cutting lines of communications, surrounding and destroying enemy forces, denying escape routes to an encircled force, or destroying enemy reserves.
b. The commander must be ready at all times to use every opportunity afforded by the enemy for exploitation. These are indicated by an increase in prisoners captured; an increase in abandoned materiel; and the overrunning of artillery, command facilities, signal installations, and supply dumps.
c. The transition from the deliberate attack to the exploitation may be abrupt or so gradual it is hardly distinguishable. After transition, units should make every effort to continue the advance without halting. Bypass enemy resistance when possible and make the most of available fire support when appropriate targets are presented. Fire support, target acquisition systems, and observers are positioned well forward with lead elements. Key fire support considerations are as follows:
- Plan fires to support hasty attacks.
- Consider using CAS and attack helicopters, which are well suited for exploitation.
- Coordinate with the FSO to establish FSCM between exploiting and converging forces.
- Keep the FSO advised of locations of lead elements to facilitate positive clearance of fires.
- Use FASCAM to delay or fix the enemy. Ensure the FSO considers the loss of maneuver space.
d. Once the exploitation begins, carry it out to the final objective. The enemy should be given no relief from offensive pressure. Should the lead force be unable to continue the mission, follow-and-assume forces must rapidly assume responsibility. Enemy troops encountered are not engaged unless they are a threat to the brigade or cannot be bypassed. This decision rests with the next higher commander; however, freedom of action is normally delegated to commanders in the exploitation.
e. Follow-and-support units clear the bypassed areas and expand the zone of exploitation. Follow-and-support forces are normally battalion or higher formations employed primarily in exploitation and pursuit operations to facilitate maintaining the momentum of the attack. They may also be used in a penetration. A force with a follow-and-support mission is not a reserve but a committed unit. Follow-and-support forces assist attacking units by relieving them of tasks that would otherwise slow their advance. Follow-and-support units can undertake the following:
- Destroy bypassed pockets of resistance.
- Relieve elements of the attacking force that have been left to block or contain enemy forces.
- Secure the flanks of a penetration to prevent the enemy from closing it.
- Expand the penetration by breaking through other enemy defenses.
- Secure lines of communications.
- Secure key terrain overrun or bypassed by the attacking unit.
- Protect key installations.
- Guard prisoners of war.
- Reinforce or assume mission of leading force.
- Widen breach lanes.
- Clear MSRs.
f. When augmented with additional CSS assets, these follow-and-support forces may also be assigned to control and process refugees and collect and manage casualties.
g. Decentralized execution is characteristic of the exploitation; however, the commander maintains enough control to prevent overextension of the command. Minimum control measures are used. Tactical air reconnaissance and Army aircraft maintain contact with the enemy movements and keep the commander advised of enemy activities. Close air support aircraft, deep FA fires, and attack helicopters can attack moving enemy reserves, withdrawing enemy columns, enemy constrictions at choke points, and enemy forces that threaten the flanks of the exploiting force. Security of ground supply columns must be considered and an aerial resupply may be necessary. Exploiting forces take advantage of captured supplies whenever possible.
The pursuit normally follows a successful exploitation. The primary function of pursuit is to complete the destruction of the enemy force. As a successful exploitation develops and the enemy begins to lose the ability to influence the situation the brigade may be ordered to execute the pursuit. In the pursuit the brigade may point its advance toward a physical objective; however, the mission is the destruction of the enemy's main force.
a. Friendly forces in the exploitation are alert for indicators of an enemy collapse that would permit a pursuit operation. There are several indicators of a weakening enemy:
- Continued advance without strong enemy reaction.
- An increased number of captured prisoners, abandoned weapons, and unburied dead.
- A lessening of hostile artillery fire.
- A lack of enemy countermeasures.
b. The pursuit is ordered when the enemy force can no longer maintain its position and tries to escape. The commander exerts unrelenting pressure to keep the enemy force from reorganizing and preparing its defenses. The brigade may be a part of a corps or division pursuit, functioning as either the direct-pressure or encircling force.
c. The mission of a direct-pressure force is to prevent enemy disengagement and subsequent reorganization of the defense and to inflict the most casualties. Leading elements contain or bypass small enemy pockets of resistance that are then reduced by follow-and-support units. At every opportunity, the direct pressure force envelops, cuts off, and destroys enemy elements, provided such actions do not interfere with its primary mission. The enemy is not allowed to break contact.
d. The mission of an encircling force is to get behind the enemy and block his escape so that he can be destroyed between the direct-pressure and encircling forces. The encircling force advances along or flies over routes paralleling the enemy's line of retreat to reach defiles, communication centers, bridges, and other key terrain ahead of the enemy main force. When conditions permit, brigades attempt a double envelopment of retreating enemy main forces or their subordinate elements. Hostile rear guards or forces on flank positions are not permitted to divert the main force from its mission. Air assault and airborne units are effective as enveloping forces. If the encircling force cannot outdistance the enemy, it attacks the enemy main body on its flank. If the enemy's main force establishes itself on a position from which it cannot be easily dislodged, the pursuing commander launches a hasty attack to restore fluidity.
e. Fire support systems are placed well forward with the lead elements of the direct-pressure force. Such positioning facilitates the delivery of fire support for both the direct-pressure and encircling force. Fire support performs two key tasks in the pursuit: slowing the retreat of enemy forces and preventing resupply and reinforcement of enemy force fires. Brigade CSS assets should follow the direct-pressure force to enhance their security. During a pursuit, the brigade may also serve as the division follow-and-support force. (See paragraph 4-10 on exploitation.)
Section III
OTHER OFFENSIVE OPERATIONS
Some offensive operations require special planning by virtue of their unique purpose or the circumstances in which they are conducted.
4-11. FEINTS AND DEMONSTRATIONS
The purpose of feints and demonstrations is to deceive the enemy by giving a false impression of the commander's intent. (FM 90-2 discusses tactical deception in detail.)
a. Feint. The purpose of a feint is to draw the enemy's attention away from the area of the main attack. Feints must be of sufficient strength and composition to cause the desired enemy reaction. It is normally conducted by brigade and smaller units. They must appear real, therefore some contact with the enemy is required. This operation is most effective when it appears to pose a definite threat to the enemy, when the enemy has a large reserve that he has consistently committed early, or when there are several feasible courses of action open to the brigade commander. A properly planned and executed feint can cause the enemy to--
- Reposition main forces.
- Commit reserves too early.
- Shift supporting fires from the area of concentration.
- Reveal his defensive positions and fires.
- Become confused and indecisive.
b. Demonstration. A demonstration is an attack or show of force in an area where a decision is not being sought. Its purpose is to deceive the enemy without making contact. Forces use fires, movement smoke, EW assets, and communications equipment in support of a deception plan to help conduct a demonstration.
Raids are operations involving swift penetration of hostile territory to secure information to confuse the enemy, or to destroy his installations. Plans are made for the withdrawal of personnel at the completion of the mission.
a. Usually, raids coincide with other offensive operations either in a supporting or supported role. They are characterized by swift, violent action terminating in a planned withdrawal upon completing the assigned mission. Raids are usually planned at brigade level and executed at battalion level. Raids are usually conducted during limited visibility. The approach route should be different from the withdrawal route, which security elements must ensure is open.
b. The raiding force usually carries everything it requires to sustain itself during the operation. If not, resupply is normally by aircraft. Factors governing the amount of logistic support accompanying a raiding force include the--
- Type and number of enemy vehicles and weapons.
- Movement distance to the raid objective area.
- Length of time the raid force is to remain in enemy territory.
- Expected enemy resistance.
Section IV
LIMITED VISIBILITY OPERATIONS
The brigade often attacks at night or under other conditions of limited visibility. This offers the advantage of surprise, reduces enemy target acquisition and effectiveness of weapons, and reduces mutual support between adjacent enemy positions.
4-13. NIGHT/LIMITED VISIBILITY ATTACKS
Night/limited visibility attacks are an integral part of the brigade offensive operations; they are routine operations for infantry. The brigade may conduct offensive night operations to--
- Continue an attack that began in daylight.
- Seize or secure key terrain for future operations.
- Achieve surprise.
- Penetrate strong enemy defenses.
- Offset enemy air superiority.
a. Types. There are two basic types of limited visibility attacks--nonilluminated and illuminated. However, illumination is normally planned for every limited visibility attack so that it can be readily available if the enemy detects the attack. Permission to fire illumination may be retained at brigade or allocated to battalions. This depends on how the light may affect adjacent units.
(1) Nonilluminated attack. The infantry brigade normally conducts nonilluminated attacks to exploit its technological advantage. Nonilluminated, nonsupported attacks offer the best chance of gaining surprise. Care must be taken to avoid converging forces and fires. The penetration form of maneuver is one way of accomplishing this. For brigades that do not have NVDs, a linear assault is one technique. Another option is to infiltrate close to the enemy and then assault under illumination.
(2) Illuminated attacks. Illuminated, supported attacks are almost like daylight attacks. They may be most effective when speed is essential, when there is limited time for reconnaissance, or when the enemy is weak or disorganized. Once illumination is begun, it should be continued until the objective is secured. Sufficient ammunition must be available. The illumination rounds may be fired to impact on the ground, providing both light and markings to orient on the objective. They may also be placed behind the objective and in the air causing the enemy to be silhouetted.
(3) Combination. Illumination after a nonilluminated attack objective is secured may be used to support consolidation and reorganization. The brigade could also conduct both an illuminated and a nonilluminated attack at the same time but in different areas.
b. Basic Considerations. The following specific actions need to be taken if a night offensive operation is to succeed.
- Leaders may have to move forward.
- Keep the plan simple.
- Organize forces properly.
- Distribute organic night vision equipment.
- Conceal the preparations.
- Control the maneuvering forces.
- Coordinate the support elements.
- Schedule rehearsals during daylight and limited visibility.
- Schedule additional preparation time.
- Perform a detailed reconnaissance and consider the use of guides.
c. Additional Considerations. Plan, prepare, and conduct night operations the same as those conducted in daylight. However, the following considerations also apply:
(1) More time is necessary to execute movements and emplace weapon systems.
(2) A clear definition of objectives and routes to them is essential.
(3) Intermediate objectives are necessary for control and to aid in maintaining direction.
(4) Smoke can further degrade enemy, as well as friendly, capabilities.
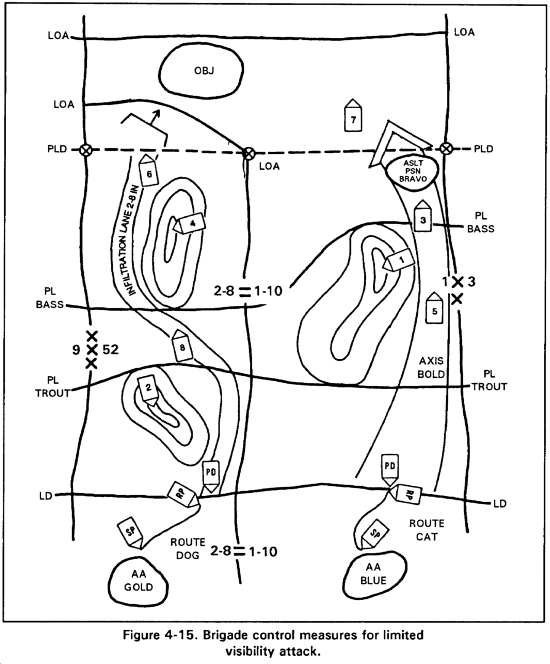
(5) Night attack control measures are normally quite restrictive (Figure 4-15). All control measures should be easily identifiable. The commander may use additional control measures to assist in C2. These may include the following:
(a) Point of departure. The PD is the exact place where units cross the LD. Normally, there will be more than one for each unit.
(b) Release points. A release point is a clearly defined control point on a route where the commander releases control of subordinate units to their commanders.
(c) Probable line of deployment. The PLD is the line at which the brigade commander intends that his brigade be completely deployed before beginning the assault. If the attack is not discovered at the PLD, the brigade advances with stealth until discovered or ordered to assault. If obstacles must be breached, the PLD should be located on the enemy side of the obstacles whenever tactically feasible. This precludes deploying at the PLD or narrowing ranks to pass through gaps in obstacles and then redeploying.
(d) Limit of advance. This is easily recognized terrain feature beyond which attacking units will not advance. The limit of advance is a critical control measure since fire support elements are free to fire at targets beyond the CFL.
(6) Navigational aids and combat surveillance equipment may aid movement. Attack helicopters or AC-130s can provide excellent navigational guidance.
(7) Rehearsals on terrain and under light conditions similar to those expected in the attack are necessary.
(8) Reconnaissance is necessary in both daylight and during reduced visibility. Use reconnaissance to gain information about the terrain and the enemy. The following are examples of things to observe:
Location of enemy positions.
Nature of obstacles, barriers, and bypasses.
Presence and number of enemy searchlights and night vision devices.
Unoccupied sectors, gaps between sectors, or sectors held by weak enemy forces.
Landmarks to coincide with graphic control measures.
Terrain features that offer concealment.
Routes to the LD, attack positions, PLD, objective, and limit of advance.
Distance between checkpoints and phase lines.
Location of TRPs.
Structures or terrain on that horizon that can be used for guiding the direction of movement.
(9) Offensive operations at night may or may not have indirect-fire weapons support. In determining the feasibility of a preparation weigh its probable effects on maneuver versus the effect of surprise stemming from an attack by stealth When not firing a preparation plan on-call fires for use in the event the element of surprise is lost. Plan fires to cover the attacking force if it must withdraw and to isolate the area of the attack. Also use indirect fires to aid in deception plans.
(10) Battlefield illumination aids in maintaining direction of movement and it facilitates coordination and control of maneuver forces and target acquisition. However, it reduces the element of surprise and the use of night vision devices. Carefully coordinate the use of illumination to avoid detrimental effects in adjacent brigade areas.
Smoke is employed under proper METT-T conditions when it significantly increases friendly survivability without degrading operational capability. Smoke and obscurants are combat multipliers that can support the movement and positioning of forces on the battlefield and cover the logistical support of forces before, during, and after engagements with the enemy. Obscurants can conceal friendly operations, support battlefield deception activities, interfere with enemy target acquisition and fire-control systems, and disrupt enemy command and control. The smoke/decontamination platoon can provide smoke coverage from 0.5 to 1.7 km if smoke is to be 50 to 150 meters wide. The smoke screen can conceal ground maneuver, breaching, and recovery operations. Smoke can also be used for deception at night to counter enemy infrared sights.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|