Chapter 10
Defense Of The DSA
OVERVIEW AND PURPOSE
10-1. The CSS organizations are normally the units least capable of self-defense against a combat force. They are also often the targets of enemy action. Time and effort used to defend themselves degrade their ability to perform their primary support mission. Key support elements from the DSB are designated to evacuate the DSA to allow minimum support to the division troops should the enemy confront the DSA. The DSB should develop a displacement plan. However, all units must be able to defend against Level I activities (sniper or terrorist activities). They should be able to impede Level II attacks until assistance arrives. Assistance may come from an MP unit as a response force or a tactical combat force (TCF) located in the rear. No CSS unit can sustain a defense against a determined Level II or III attack, but it should plan and train to protect itself until a TCF arrives to repel the enemy attack.
10-2. The DSB units must defend themselves against attempts to disrupt their operations. They must be able to minimize destruction and to reinforce their units. The DSB units must also be able to gain time until response forces arrive. Units form base defense perimeters to defend against the threat. If enemy forces exceed base and base cluster defense capabilities, response forces are used. These forces will provide the initial force to close with and to destroy the enemy. If and enemy incursion exceeds the capability of response forces, tactical combat forces must be committed to neutralize the threat.
10-3. Responsiveness is a key to defeating enemy incursions in the rear area. Responsiveness requires the immediate reaction and rapid deployment of sufficient combat power and area damage control resources. These two forces destroy the enemy and ensure minimal damage to the area. Responsiveness is achieved through:
Effective command relationships and supervision.
Reliable communications.
Accurate intelligence.
Centralized planning and decentralized execution.
Organic mobility and fire power of response force.
Training and rehearsals.
Prior assessment of the capabilities of bases and facilities to withstand enemy attack. This assessment is based on a unit's degree of exposure and that unit's importance to the division's ability to sustain operations. This mission-essential vulnerability analysis assists the DSB commander. With this analysis, the commander is able to allocate resources to protect personnel, supplies, and facilities in consonance with their importance to the mission.
PLANNING AND EXECUTING DEFENSE OF THE DSA (BASE CLUSTER)
COMMAND, CONTROL, COMMUNICATION, CONPUTERS, INTELLIGENCE,
SURVEILANCE, RECONNAISSANCE (C4ISR)
10-4. The DSB commander is responsible for DSA security and its protection. As such he has control of all elements in the DSA for defense and positioning. Normally, the DSA is a base cluster with the DSB commander as the base cluster commander. The major elements in the DSA (ASMC, DSMC, signal field trains etc...) become unit bases. The senior individual in each base is the base commander. The DSB SOP will cover as many defense procedures as possible. Each base will be given specific responsibilities in the OPORD. Guidance for these responsibilities is given in this chapter.
10-5. The S2/S3 section of the DSB TOC is the base cluster operations center. Alternate BCOCs should also be designated. Possibilities include the DSMC and the DSMC in the DSA. In urban terrain, the DSB S2/S3 may have to establish subordinate base clusters and BCOCs within the DSA. One of these may be designated the alternate BCOC.
10-6. Each base will send a representative to the BCOC staff meetings or shift change briefings. In addition, the BCOC will issue a situation report on a regular basis, twice daily if possible. The report will provide intelligence updates, reporting requirements, and impending DSA movement orders.
BASE CLUSTER OPERATION CENTER (BCOC)
10-7. The DSB commander is responsible for integrating base defense plans into a base cluster defense plan. As discussed, this requires development of a rear operations communications system and coordination with field artillery, engineer, ADA, and MP units. As part of the terrain management function, the DSB S2/S3 assigns a defensive position and a sector to each base in the DSA. Bases on likely avenues of enemy approach are given a smaller sector. The S2/S3 ensures each base's sector of fire overlaps the adjacent base's sector. He does this by personally coordinating with base commanders, and confirming that tenant units are tied in at their respective boundaries. Infiltration routes for Level I threats, and main avenues of approach are covered by planning for fires, obstacles, patrols, OPs, or sensors. The DSB S2/S3 must carefully coordinate this planning with each base to avoid having troops engage friendly forces.
10-8. The DSA defense plan must be integrated into the plan for the entire division rear. This requires the BCOC to coordinate with the DISCOM S3 and ROC for the overall plan. It must also coordinate directly with other BCOCs in the division rear to plan mutually supporting fires and to prevent firing upon each other.
10-9. The S2/S3 keeps a sketch of the defensive plan. It shows base sectors of fire, locations of mines and obstacles, planned indirect fire coverage, OPs, patrol routes, and positions of automatic and anti-armor weapons.
10-10. These weapons will include those in the DSA for repair. If the firing system is operable, these weapons should be included in the DSA defensive scheme, and mechanics should work on them in their fighting positions.
10-11. Whenever possible, units should occupy the same location within the DSA relative to the other units every time the DSA moves. They should build a habitual relationship with the units on all sides of them. This will expedite coordination of sectors of fire. Since night vision devices are likely to be scarce, illumination plans must also be included in the overall DSA security plan. Details on sector defense planning are in FM 19-4.
10-12. In addition, the BCOC must plan for a quick reaction force (QRF) from assets in the DSB. This QRF will be called upon when a base's defenses cannot defeat the threat and MPs and combat forces from the division are not immediately available. As a minimum, the reaction force should include personnel equipped with machine guns, grenade launchers, rifles, FM radios, and vehicles. The DSB S2/S3 must carefully equip the reaction force. Removal of scarce assets such as machine guns from the defensive perimeter when the reaction force is assembled must be considered and integrated into the defense plan. During periods of increased readiness, the reaction force should be assembled for immediate response. It must be well-rehearsed and able to react precisely and immediately. Rally points, battle positions, and detailed procedures must be planned and practiced in advance. See the section on QRF in this chapter under MANEUVER.
10-13. The BCOC must ensure that all base commanders understand the different threat levels and the associated actions. The brigade staff must also be aware that the DSB is neither staffed nor equipped to continue support operations at normal levels while responding to increased levels of threat. Support will be degraded. How much it is degraded will depend on the level of the threat.
10-14. Level I threats are those which can be defeated by base or base cluster self-defense measures. They normally involve the activities of agents, saboteurs, and terrorists. Typical actions the BCOC will require in such situations include manning OPs fully, increasing guards and spot-checking vehicles, tightening base security, alerting defensive perimeter personnel, and increasing protection of key facilities. The degradation of support will depend on the actions directed by the individual BCOC in specific conditions. However, as a general planning guide, the DSB can estimate that the 75 percent of available assets will be engaged in support operations, while 25 percent defend.
10-15. Level II threats are those beyond base or base cluster self-defense capabilities. They can, however, be defeated by response forces, normally MPs with supporting fires. They normally involve:
Diversionary and sabotage operations by unconventional forces.
Raid, ambush, and reconnaissance operations by small combat units.
Special or unconventional wartime missions.
10-16. The BCOC would likely require strictly controlled access to all areas, reinforced perimeter defense, OPs prepared to withdraw, and the reaction force alerted.
10-17. A tactical combat force is required to defeat a Level III threat. Level III threats normally involve:
Airborne operations.
Heliborne operations.
Amphibious operations.
Penetration by enemy forces from the main battle area.
Ground force deliberate operations (for example, operational maneuver groups with linkup of smaller airborne and assault units).
Infiltration operations.
The OPs will be withdrawn, QRF forces committed, the DISCOM S3 and ROC notified, and support operations ceased. Artillery or air strikes normally precede such a threat.
10-18. The BCOC determines the level of threat and issues prearranged alerts to all bases. The BCOC also determines the probability of an air attack and issues air defense warnings.
10-19. The BCOC should also have planned in advance emergency move procedures. If the DSB is under imminent danger from a Level II or III threat, the BCOC will call for an emergency move of key DSA assets. Key elements should be identified in advance and prepared to move to a predesignated site with minimum notice. The commander designates key DSB elements as required. These will likely include C2, ATP, Class III, emergency medical treatment, and maintenance elements. Emergency destruction of equipment and supplies (excluding class VIII) is performed to avoid enemy capture. Priority items for destruction will probably include COMSEC items, fuel, ammunition, vehicles, communications equipment, and weapons.
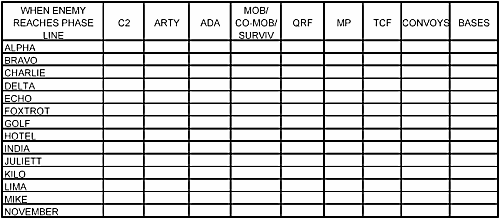
10-20. Other duties of the BCOC are to identify primary and secondary entry points into the DSA and designating preplanned landing zones for division rear reaction forces to use when required. The BCOC will also conduct regular (preferably daily) meetings or shift change briefings with base representatives to update the defensive plan. Below in Figure 10-1 is an example of an execution matrix, to assist the BCOC. To use this matrix the BCOC synchronizes the DSA actions in each category with the advance of the enemy forces. For every action of the enemy we have a reaction. It is like the playbook for the defense of the DSA. This matrix can be included with the support synch matrix to ensure everyone is on the same sheet of music.
Figure 10-1. DSA Execution Matrix
COMMUNICATIONS
10-21. Communications for DSA security will be conducted by wire, radio, signals, and personal contact. The primary means will be wire. Each base will be required to establish a wire linkup to the BCOC. The BCOC will operate a switchboard 24 hours a day. Other elements located in the DSA are responsible for laying wire from their CPs to the BCOC. The ADA and field artillery units in the DSA will have direct wire communications with the BCOC to provide early warning of enemy aircraft and to facilitate calls for fire.
10-22. Ideally, the DSB would also operate a separate rear operations radio net. If wire or BCOC FM communications are lost, units will monitor the DSB command net that will serve as the BCOC radio net. If communications by these means are lost, the tenant activities are responsible for sending a messenger to the BCOC to provide coordination.
10-23. In addition, units in the DSA cannot rely on wire and FM communications to relay alert status. Too much time would pass before every soldier received the message. The DSB should establish readily recognizable signals that are easy to initiate. For example, the warning for an NBC attack could be a pyrotechnic signal that could be relayed quickly with voice, hand and arm, or horn signals. Similar signals should be specified in the SOP for air and ground attacks or to change frequencies. Detailed information and instructions would follow by radio, wire, or messenger. The all-clear signal would only be passed via command channels.
MANEUVER
10-24. The only specific asset the DSB commander may have that is trained for and has the primary mission of rear area operations is the military police platoon. For details in planning for MP operations see FM 3-19.4 (19-4). With their ability to shoot, move, and communicate, MPs on the battlefield provide the commander both technical and tactical advantages. Commanders can rely on MPs to help keep enemy activity in the rear area from delaying his reinforcing units and disrupting C2.
10-25. MP elements are task-organized to accomplish their missions. Size and composition of a tasked element depend on mission needs and the tactical situation. MP teams have the experience, initiative, and ability to operate independently or as part of a larger unit.
10-26. Three-man teams are the building blocks of MP units. Each MP team has a vehicle, a crew-served weapon (an M60 machine gun, M2 .50 cal MG, or a MK-19 grenade machine gun), and a vehicle-mounted radio. The team leader observes and maintains communications. A second MP drives, and the third MP is the gunner and alternate driver. They are all capable of calling for indirect fire support and using light antitank weapons. The team is equipped with night-vision devices to detect NBC contamination and with equipment for secured radio communications. The MP teams fight mounted or dismounted to suit the tactical situation.
10-27. In the rear area, MPs are a critical part of the DISCOM and DSB commander's on-the-ground intelligence-gathering assets. They are the rear area scouts. MP teams are mobile over large geographical areas. As part of their battlefield circulation and control (BCC) mission, MPs routinely travel the battlefield road networks. As part of their area security mission, MPs routinely move off-road for area reconnaissance and other area security operations. They help find the enemy and identify his strengths and weaknesses. The MPs collect and disseminate vital information to help commanders see the battlefield. Information about conditions in the rear area and the presence and nature of the enemy helps a commander know when and where to concentrate combat power. The MP's mobility and communication assets allow them to detect and monitor activity throughout their broad AOs and report their findings quickly. Swiftly changing combat situations make timely and accurate information about the location of units, road conditions, and enemy activity imperative.
10-28. In the rear area, the MPs are a flexible economy-of-force organization that can significantly multiply the commander's combat power. MPs do this without increasing the commander's total force or diverting his combat resources from more critical operations. Because of their mobility and dispersion in the rear area, MPs are likely to be the first forces on the scene of a threat insertion in the rear area. If this occurs, MPs fight to preserve the security of the area. The MPs encountering enemy forces engage them with individual and crew-served weapons. They destroy enemy elements within their capability. Organized in small tactical elements, their experienced use of initiative, their mobility and firepower, and their communications ability enable the MPs to operate independently as well as fight as part of a larger force. As squads or platoons defending a base or countering small enemy incursions, MPs generate substantial short-term combat power for the tactical commander. Though MP elements are highly mobile and are equipped for and capable of limited combat missions, the commander should carefully consider mission priorities for these valuable assets because of their small size.
10-29. The MP platoon carries out four basic missions in support of the commander and the rear operations mission. These are:
Battlefield circulation and control. Expediting forward and lateral movement of combat resources to ensure a way is open to move reinforcing troops, fuel, food, and ammunition across the battlefield.
Area security. Helping the commander to provide security and protection in the rear area.
EPW operations. Collecting, evacuating, and interning EPW to relieve the tactical commander of the responsibility.
Law and order operations. Conducting these when necessary to extend the combat commander's discipline and control.
10-30. Any one of the above missions can easily require the entire MP platoon and more; therefore, it is important that the factors of METT-TC be considered when using the platoon. It is best to keep MPs mobile, acting as the eyes and ears of the commander. During offensive operations, the MPs will most likely be employed in BCC and EPW missions. In the defense, they will be employed in BCC as area security.
Movement
10-31. Maintaining security of the MSRs for swift and safe movement of units and resupplies is critical to combat mission success. To avoid locking too many MPs into this mission, the DSB must use the gun trucks (with caliber .50 weapons) and combat vehicles that are returning forward with supplies as security. If that is not possible, a good practice is to use no more than 50 percent of MP assets on BCC unless there is a major movement of forces.
CONVOY DEFENSE TECHNIQUES
10-32. The convoy commander must ensure that his troops are trained in convoy defense techniques. The payoff is reduced vulnerability to hostile action and successful mission accomplishment. The damage a convoy incurs when attacked depends on the adequacy of convoy defense training. It also depends on the adequacy of the briefing that convoy personnel receive before the operation.
10-33. Some elements of convoy defense training are routine. The key is to train to react rapidly to any situation. Successful accomplishment of your mission and your life depend on it. This section covers a broad range of convoy defense techniques to be employed against a variety of threats.
Air Attack
10-34. The air threat varies from UAV, cruise missiles, and armed helicopters to high-performance aircraft. Convoys face the greatest danger of an air attack while moving along open roads or during halts where there is little or no overhead cover.
10-35. An air attack is a type of ambush. Accordingly, many of the procedures used during a ground ambush also apply to the air attack. For example, the convoy commander must:
Prescribe alarm signals (unit SOP) (see FM 44-3 for more information on alarms).
Give instructions for actions to take when under attack.
Prescribe actions to take in the absence of orders.
Ensure that defense procedures are rehearsed.
Review the procedures with convoy personnel before the convoy moves out.
10-36. The convoy commander should remember that enemy pilots will seek out and try to surprise the convoy. They will fly at a low, terrain masking altitude. If they attack from higher than 350 meters, small arms fire will have no effect against them, but air defense weapons can be used against them effectively. Enemy pilots will also fly at high speed to make air defense weapons and small arms fire less effective.
Active Defense
10-37. The amount of fire a logistical convoy can bring to bear on attacking aircraft is extremely limited. It is limited to the number of vehicles with mounted machine guns and the individual weapons of operators and passengers. Although the convoy is not totally defenseless, it is no match for a skilled pilot in a modern ground attack jet aircraft. The convoy's capability to defend itself is slightly better against the slower and sometimes more vulnerable ground attack helicopter. At best, the convoy without air defense protection is extremely limited in its ability to defend against air attack.
10-38. The key to effective small arms fire against aircraft is volume. Put up a large volume of fire with small caliber weapons. Volume small arms fire comes from knowing the effectiveness of small arms fire on low-flying aircraft. Training ensures accuracy and builds confidence.
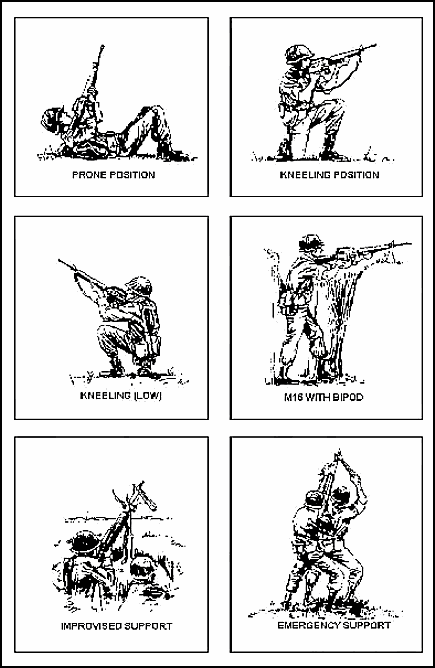
10-39. Firing positions. Except for the prone position, the riflemen's basic firing stances stay the same (Figure 10-2). Firing at aircraft from the prone position means the firer is lying on his back, aiming his rifle into the air. Maximum use of cover and concealment is essential. A crew served weapons gunner should fire from a protected position if possible. He needs to get the weapon up in the air. He can hold it up or use a support for his arms and the weapon. In a real emergency, another soldier can act as a hasty firing support.
Figure 10-2. Firing positions
10-40. Tips for small arms defense. The following are tips for small arms defense:
Shoot any attacking aircraft or unauthorized UAV.
Fire at the nose of an aircraft; fire at the fuselage of a hovering helicopter or slightly above the nose of a moving helicopter.
Fire in volume and everybody shoots.
Lead aircraft crossing your position (M16 and M60 lead jets the length of one football field).
Take cover if time allows.
Support your weapon if possible.
Lie on your back if caught in the open.
Aim mounted machine guns slightly above the aircraft nose for head-on targets.
Control small arms fire so attacking aircraft flies throughout it.
Passive Defense
10-41. For a logistical convoy, normally without significant air defense firepower, passive measures are most effective. The key is to prevent attacks by hostile aircraft.
10-42. Dispersion. The formation used by the convoy is a type of passive defense. The convoy commander must decide whether to use an open or closed column. The distance between vehicles must not be fixed. It should vary from time to time during a march. Factors influencing selection of the best vehicle distance include:
Mission.
Cover and concealment along the route.
Length of the road march.
Type of road surface.
Types of vehicles.
Nature of cargo.
Enemy threat (ground and air).
Available defense support.
Small arms potential.
10-43. Open column. Open column convoys generally maintain an 80 to 100 meter distance between vehicles. This formation offers an advantage of fewer vehicles damaged by air-to-ground rockets, cannons, or cluster bomb units. However, open columns make control more difficult for the convoy commander when it is necessary to give orders to stop, continue, disperse and seek concealment, or engage aircraft. The column may be more susceptible to attack. It is exposed for a longer period and, if attacked, its defense is less effective since its small arms fire is less concentrated.
10-44.. Close column. Close columns maintain a distance of less than 80 meters between vehicles. This formation has none of the disadvantages noted for the open column formation. However, presenting a bunched up target could be an overriding disadvantage. Where an air attack is likely, it may be wise for the convoy commander to move close column convoys only at night.
10-45. Camouflage and concealment. Camouflage and concealment techniques can make it more difficult for the enemy to spot the convoy. Not much can be done to change the shape of a vehicle moving down the road, but the type of cargo can be disguised or concealed by covering it with a tarpaulin. Bulk fuel transporters (tankers) are usually priority targets. Rigging tarps and bows over the cargo compartment conceals the nature of the cargo from the enemy pilot. The following are other effective passive measures:
The operator should look for a bush, tree, or some other means of concealment to break the shape as seen from the air (Figure 10-2).
Smooth surfaces and objects, such as windshields, headlights, and mirrors, will reflect light and attract the pilot's attention. Camouflage or cover all shiny items before the convoy moves out.
If vehicles are not already painted in a pattern to blend with the terrain and to break the outline, mud can be used to achieve this effect.
10-46. Air guard duties. Assign air guard duties to specific individuals throughout the convoy, and give each specific search areas. If the road march lasts more than an hour, soldiers should take shifts at air guard duty. Scanning for a long period dulls the ability to spot aircraft. Seeing the enemy first tips the odds in favor of the convoy, giving it time to react. See FM 44-3 for search and scan procedures.
10-47. Communications security. Today's communications equipment can be very useful for controlling convoys, but it can also help enemy pilots find you. Use the radio only when necessary and be brief. Enhanced situational awareness with new digital systems such as MCS, MTS, and FBCB2 also can be very useful for monitoring and controlling convoys.
Passive Reactions
10-48. When aircraft are spotted or early warning is received, the convoy commander has three options: stop in place, continue to march, or disperse quickly to concealed positions (Figure 10-3).
Figure 10-3. Dispersing vehicles seek cover for protection against air observation
10-49. If the convoy commander chooses to halt the convoy, the vehicles simply pull to the shoulder of the road in a herringbone pattern. This technique has several advantages:
It is harder for the enemy pilot to see the convoy when it is halted than when it continues to move.
It is easy to continue the march after the attack.
The volume and density of organic weapons will be higher than if the convoy disperses.
A disadvantage to this option is that a convoy stopped on the open road makes a good target and an enemy attack has a better chance of causing greater damage to the unit.
10-50. The mission and/or terrain may dictate that the march continue. If this is the case, convoy speed should be increased. Continuing the march offers the advantage of presenting a moving target, making it more difficult for the enemy to hit. However, detection is easier and volume and density of small arms fire are reduced.
10-51. A simple technique to disperse vehicles is to establish a method in the SOP that, in the event of an attack, odd-numbered vehicles go to the left and even-numbered vehicles go to the right. The key to dispersion is not to make two straight lines out of what was one long line and the vehicles must be staggered (Figure 10-4). This should not be much of a problem if the drivers have been trained to go to trees, bushes, folds in the ground, and so forth, that will give concealment. Once the convoy is dispersed, all personnel, except for vehicular-mounted weapon gunners, dismount and take up firing positions.
Figure 10-4. Vehicles moving to dispersed positions on road shoulders
10-52. Advantages of this option are that it is more difficult for the enemy pilot to detect the vehicles and get multiple hits. However, this method has several disadvantages:
It is easier for the enemy pilot to spot the convoy as it begins to disperse.
The volume and density of small arms fire are reduced.
It takes longer to reorganize the convoy after the attack.
Figure 10-5. Dispersed vehicles in concealed positions
Artillery Or Indirect Fire
10-53. Enemy artillery units or indirect fire weapons may be used to destroy logistical convoys or to harass and interdict the forward movement of supplies and personnel. Artillery fires are either preplanned fires or fires called in and adjusted on a target of opportunity by a forward observer. Of the two, the adjusted fires present the most complex problem as the artillery barrages can be adjusted to follow the actions of the convoy.
10-54. Active Defense. Active defensive measures against artillery are extremely limited but must not be overlooked. Active measures include:
Directing counter-battery fire if the direction and approximate distance to the enemy artillery can be estimated.
Directing small arms fire or artillery fires against the enemy forward FO if he can be located.
Coordinating air strikes against the enemy artillery.
10-55. Passive Defense. The formation in which the convoy moves can be a type of passive defense. See the discussion of open and closed convoys under passive defense for air attacks.
10-56. The convoy commander has three options when confronted with incoming artillery rounds: halt in place, continue to march, or disperse quickly to concealed positions. Regardless of the option selected, the actions to be taken and the signal directing the action should be covered in the unit SOP. The primary consideration is the immediate departure from the impact area.
10-57. The convoy should only be halted when the artillery concentration is ahead of the convoy. The convoy commander should look for an alternate route around the impact area and the convoy should remain prepared to move out rapidly.
10-58. The mission or terrain may require the convoy to continue. If this is the case, increase speed and spread out to the maximum extent the terrain will allow. Casualties can be reduced by avoiding the impact area, increasing speed, wearing protective equipment, using the vehicle for protection, and increasing dispersion.
Sniper Fire
10-59. Take extreme caution when sniper fire is received to ensure that any return fire does not harm friendly troops or civilians in the area. The best actions are passive. Ensure all personnel wear Kevlar helmets and available body armor at all times. All vehicles should move through the area without stopping. Escort personnel should notify the march element commander by giving a prearranged signal, like a smoke grenade thrown in the direction of fire, and attempt to locate and destroy the sniper by long-range fire if in a free-fire zone. Prevent convoy personnel from random firing by designating personnel to return fire. 10-60. The convoy commander may order additional fire or supporting forces into the area to destroy, capture, or drive off the sniper. Convoy personnel should be aware that a heavy volume of fire is frequently used by the enemy to slow down a convoy before an ambush. Remember all details so the incident can be reported to higher headquarters.
Ambush
10-61. This paragraph provides guidance in developing and employing counterambush tactics and techniques. The very nature of an ambush, a surprise attack from a concealed position, places an ambushed unit at a disadvantage. Combat situations may prevent a convoy from taking all the measures necessary to avoid being ambushed. Therefore, a convoy must take all possible measures to reduce its vulnerability. These are passive measures supplemented by active measures taken to destroy or escape from an ambush. For information on the types of ambushes, see FM 21-75.
10-62. No single defensive measure, or combination of measures, will prevent or effectively counter all ambushes in a situation. The effectiveness of counterambush measures is directly related to the state of training of troops and the leadership ability of the leaders.
10-63. The best defense is to avoid being ambushed. Take the following actions to avoid an ambush:
Select the best route for your convoy.
Make a map (digital) reconnaissance.
Make a ground reconnaissance.
Make an aerial reconnaissance.
Obtain current intelligence information (ASAS and UAV).
Use OPSEC to deny the enemy foreknowledge of the convoy.
Do not present a profitable target.
Never schedule routine times or routes.
10-64. Take the following actions to reduce the effectiveness of ambushes:
Harden vehicles.
Cover loads.
Space prime targets throughout the convoy.
Wear protective clothing.
Use assistant drivers.
Carry troops and supplies.
Use prearranged signals to warn the convoy of an ambush.
Use escort vehicles (military police, tanks, armored vehicles) or gun trucks.
Thoroughly brief all convoy personnel on immediate action drills.
Practice immediate action drills.
Maintain the interval between vehicles.
Move through the kill zone, if possible.
Stop short of the ambush.
Do not block the road.
Rapidly respond to orders.
Aggressively return fire.
Counterattack with escort vehicles.
Call for artillery support.
Call in TACAIR support.
Call for the reserve force.
10-67. In the event of ambush during night convoy operations under blackout drive, turn on service drive lights and increase speed to clear the ambush area. Be aware that drivers wearing night vision goggles will be temporarily blinded when service drive is turned on.
10-68. Road Not Blocked. Guerrillas are seldom able to contain an entire convoy in a single kill zone. This is due to the extensive road space occupied by even a platoon-size convoy and because security or lack of available forces may limit the size of the ambushing force. More often, a part of a convoy is ambushed, either the head, tail, or a section of the main body. That part of the convoy that is in the kill zone and receiving fire must exit the kill zone as quickly as possible if the road to the front is open. Vehicles disabled by enemy fire are left behind or, if blocking the road, pushed out of the way by following vehicles. Armored escort vehicles must not block convoy vehicles by halting in the traveled portion of the road to return fire.
10-69. Vehicles that have not entered the kill zone must not attempt to do so. They should stop and personnel should dismount, take up a good defensive position, and await instructions. Since escort vehicles may have left the road to attempt to overrun a hostile position, elements of the convoy should not fire on suspected enemy positions without coordinating with the escort forces.
10-70. Other actions that convoy personnel can take to neutralize the ambush force include:
Call for artillery fire on enemy positions.
Call for gunship or tactical air or army aviation fire on enemy positions.
Direct gun trucks and other vehicles mounted with weapons to lay down a heavy volume of fire on the ambush force.
Call for reaction forces.
Direct all nondriving personnel to place a heavy volume of fire on enemy forces as rapidly as possible as vehicles move out of the kill zone.
Vehicles must keep their distance to reduce the number of vehicles in the kill zone.
10-71. A motor transport convoy with a limited escort is seldom able to defeat a hostile force and should not attempt to do so. When part of the convoy is isolated in the kill zone, vehicles that have not entered the ambush area must not attempt to do so. They should stop, personnel should dismount and take up a good defensive position, and await instructions until supporting forces have cleared the ambush. Normally, a transport unit will not deploy to attack a hostile force unless it is necessary to prevent destruction of the convoy element. It relies on supporting air, artillery, escorts, and reaction forces.
10-72. Road Blocked. When an element of a convoy is halted in the kill zone and is unable to proceed because of disabled vehicles, a damaged bridge, or other obstacle, personnel will dismount, take cover, and return a maximum volume of fire on enemy positions. When dismounting, exit the vehicle away from the direction of enemy fire. Security/escort troops from vehicles that have passed through the ambush area dismount and lay down a base of fire on the ambush position. Reaction forces should be called in as soon as the ambush attack is launched. When a security escort is provided and a combat emergency arises, the escort commander has operational control of the security element to attack and neutralize the hostile force. Normally, the security force will take action to neutralize the ambush while the convoy escapes from the kill zone. In an ambush situation, immediate reaction and aggressive leadership are essential to limit casualties and damage to vehicles, cargo, and personnel. If immediate air or artillery support is available, personnel will be restricted to a specified distance from the road to avoid casualties from friendly fire. In this situation, personnel in the kill zone establish a base of fire, while others take up defensive positions away from their vehicles and wait while supporting fire is called in on the enemy positions. Fire in the kill zone may be from only one side of the road with a small holding force on the opposite side. To contain the convoy element in the kill zone, mines and booby traps are frequently placed on the holding force side. The security escort must take care in assaulting the main ambush force as mines and booby traps are commonly used to protect its flanks.
10-73. When the enemy is dislodged, the road must be cleared and convoy movement resumed as soon as possible. Wounded personnel are evacuated using the fastest possible mode. When disabled vehicles cannot be towed, their cargo should be distributed among other vehicles if time permits. When it is not feasible to evacuate vehicles and/or cargo, they will be destroyed upon order from the convoy commander. If at all possible, radios and other critical items will be recovered before the vehicles are destroyed. Under no circumstances will they be allowed to fall into enemy hands.
10-74. Mines and Booby Traps. Mines and booby traps are frequently part of an ambush. Command-detonated mines are often used to start an ambush. Mines will also be planted along the shoulder of the road for harassment and interdiction. A booby trap system may be used against personnel in vehicles and could consist of hand grenades. Claymore mines or artillery shells may be suspended from trees and command-detonated when a vehicle passes.
10-75. The following guidelines have proven effective in decreasing damage by mines in convoy operations:
Track the vehicle in front.
Avoid driving on the shoulder of the road.
Whenever possible, do not run over foreign objects, brush, or grass in the road.
Avoid fresh earth in the road.
Watch local national traffic and the reactions of people on foot. (They will frequently give away the location of any mines or booby traps.)
When possible, arrange for the engineers to sweep the road immediately before the convoy is scheduled to move over it.
Use heavy vehicles such as tanks to explode small mines when deployed in front of the convoy.
Harden vehicles.
Wear protective equipment.
Nuclear, Biological, Or Chemical Attacks
10-76. Chemical agents can be disseminated by artillery fire, mortar fire, rockets, missiles, aircraft spray bombs, grenades, and land mines. Always be alert because agents may already be present on the ground or in the air. Chemical agents are substances in either gaseous, liquid, or solid form. To protect against an NBC attack, you need to know how those agents may affect your body if they are used against you. Take defensive actions according to local directives and SOPs. For detailed information on defense against NBC warfare, see FMs 3-11.4 (3-4), FM 3-11.5 (3-5), and FM 3-11 (3-100).
Area Reconnaissance and Security
10-77. Area Reconnaissance and Security will always be a primary mission for MPs. Use of the S2's IPB will be important in identifying critical terrain that needs to be kept under frequent or constant surveillance, such as LZs, DZs, and axis of advance. The MP's ability to find, fix, and destroy Level I and Level II threats will greatly decrease the commander's requirement to employ combat forces in the rear. The early detection of heavy Level II and Level III threats by MPs will allow them to at least delay, if not defeat, the enemy before he reaches the DSB's logistics assets. Ensure the MPs are sufficiently equipped with antitank capability. Use them aggressively as rear area scouts in counter-reconnaissance missions to keep enemy reconnaissance out of the DSA. If the enemy force is more than the MP platoon can handle, the following contingencies should be planned for:
Re-prioritize artillery support to the rear area mission to slow the enemy until friendly combat forces make contact.
Redirect attack helicopters or close air support to slow down or stop the enemy.
Coordinate assets from division or corps to assist in backup for the rear operations battle.
QUICK REACTION FORCE
10-78. The DSB must ensure that quick reaction forces (QRF) are identified, trained and equipped to perform their mission of reaction to threats against the DSA both at bases and the base cluster. The S2/3 NCOIC is usually the chief of the QRFs. The ready reaction forces must be well rehearsed in:
Unit assembly.
Friendly and enemy force recognition.
Actions on enemy contact.
Delaying operations.
Call for fire (artillery, and rotary and fixed wing close air support).
Reconnaissance and surveillance operations.
Small unit tactics in-conjunction with the MPs and a tactical combat force.
Individual and crew served weapons, anti-tank weapons, mines, pyrotechnics, armored vehicle weapons systems and operations, night vision device, global positioning system, familiarization and operations.
Conduct of rehearsals.
Anti-fratricide measures.
Passage of lines.
Challenge and password.
Running password.
Hand and light signals.
Troop leading procedures.
Time distance factors (enemy avenues of approach).
EPW procedures.
10-79. The ready reaction forces must possess:
Friendly barrier plan.
Friendly sector sketch.
Pre-planned fires-field artillery / mortar / attack helicopter/CAS.
Casuality evacuation procedures.
10-80. The ready reaction forces must be briefed on:
Specifics of mission.
Communication procedures.
Special requirements/rules of engagement (ROE).
Completion of mission.
Quick recovery & reports.
Debriefing.
QRF TACTICS, TECHNIQUES, PROCEDURES (TTPs)
10-81. The QRF provides the commander with the capability to repel a Level II attack. The base commander determines the best use of the QRF as he monitors the battle. The QRF soldiers are not integrated into the perimeter and have no conflicting defensive requirements.
10-82. The QRF checklist is listed below:
Example of Team Composition (METT-TC driven).
NCOIC.
A/B team leaders.
Combat lifesaver.
Radio/commo operator.
Crew-served weapon operators (2 ea).
Force Protection Enhancement.
Hardened gun trucks.
FLAK vests.
Basic load of Class V (for vehicle and soldiers).
Night vision devices.
QRF BATTLE DRILLS
Battle Drill #1: Assemble The Force
Threat goes to Level II, or company comes under direct attack, the QRF soldiers immediately assemble at the unit CP with gun truck fully armed and prepared to engage the threat.
The QRF NCOIC establishes accountability and inspects soldier's ammunition load.
The QRF takes a defensive posture around the CP until told to mount gun truck, or move out on foot.
The QRF NCOIC takes all instructions from the company commander or ranking individual at the CP.
The QRF deploys in accordance with commander's or ranking individual's orders.
Battle Drill #2: Employment Of QRF
The QRF NCOIC receives deployment information and loads truck.
The QRF moves to specified location and positions gun trucks in over watch position as directed by QRF NCOIC to provide cover from direct enemy fire to protect the force during dismount.
Gun truck provides suppressive fire while dismounts move into position as directed by the QRF NCOIC.
Battle Drill #3: Engagement Of The Enemy
The primary mission of the QRF is to repel the enemy attack. The QRF will close with and attempt to destroy the enemy unless otherwise directed by the CP.
The QRF reinforces existing perimeter defensive positions and provides mass fire on known enemy locations.
The QRF NCOIC communicates situation (SALUTE Report) to CP via man pack radio and takes further instructions from the CP.
The QRF will not breach perimeter defense unless otherwise directed.
QRF engages enemy forces until successfully defeated.
Battle Drill #4: Command And Control
The QRF NCOIC takes charge of existing perimeter forces and dictates the flow of the battle via communication with the CP.
The QRF NCOIC coordinates with adjacent sector NCOICs to minimize the risk of fratricide.
Sub-element to which the QRF is deployed will take all instructions for engagement from the QRF NCOIC.
The QRF NCOIC directs all fires and rates of fires of all available fighting systems to effectively repel the enemy attack.
The QRF NCOIC coordinates with the CP any requirements for re-enforcements or munitions resupply via man pack radio.
Battle Drill #5: Consolidation And Recovery
Once attacking force is defeated and repelled, the QRF NCOIC conducts accountability and reports to the CP.
The QRF cross levels ammunition and reallocates soldiers along compromised perimeter in preparation for possible enemy counter offensive.
The QRF NCOIC assesses casualty situation and coordinates medical support with CP.
The QRF maintains area security and control until recalled by CP to stand down.
Once recalled by CP, QRF NCOIC conducts debrief with commander or ranking individual at CP.
The QRF conducts PMCS, cleans and services equipment, replenishes Class V basic load prior to QRF soldiers returning to duty positions.
The QRF NCOIC identifies any personnel and equipment replacements to CP prior to returning to duty position.
BASE OPERATIONS
10-83. The elements in the DSA are organized into bases for self-defense. Normally, each DSB company and each field train in the DSA will constitute a base. Miscellaneous small teams will be assigned to a base by the BCOC. The base commander is responsible for preparing the base defense plan and coordinating with the BCOC. Each base must be capable of defending itself and supporting other bases against a Level I threat and delaying a Level II threat until the reaction force arrives. If a base is faced with a Level II threat, it must take action to destroy the threat and prevent the capture of critical supplies and equipment. Base commanders are responsible for the establishing the following priorities of work:
Position antiarmor weapons, machine guns, and assign sectors of fire.
Position other defensive assets available (weapon systems for repair).
Establish local security and OP positions.
Establish the CP and wire communications.
Designate final protective line (FPLs) and final protective fire (FPFs).
Clear fields of fire and prepare range cards and sector sketches.
Coordinate with adjacent units,left, right, forward, and to the rear.
Prepare primary fighting positions.
Emplace obstacles and mines.
Mark or improve marking for target reference points (TRP) and other fire control measures.
Improve primary fighting positions such as overhead cover.
Prepare alternate positions, then supplementary positions.
Establish a sleep and rest plan.
Reconnoiter potential enemy infiltration routes, and friendly patrol routes.
Rehearse engagements, disengagement, and any reaction force plans.
Continue to improve positions.
10-84. Base commanders are responsible for the establishing the following specifics:
Coordinate with the base on each side to plan mutually supporting fires and to avoid troops engaging each other. If a problem exists in that area, the base commander will notify the BCOC.
Assign each individual a fighting position. Positions should provide overhead cover. Positions must also allow for interlocking sectors of fire.
Ensure proper individual fighting positions are prepared. Soldiers should use all available cover. Positions should provide frontal protection from direct fire while allowing fire to the front and oblique. Details on fighting positions are in FM 5-103.
Deploy crew-served weapons in fighting positions with primary and secondary sectors of fire. They cover the most likely enemy avenues of approach. Instructions for preparing positions for each type of crew-served weapon are also in FM 3-34.103 (5-103). The base commander must ensure each weapon has an adequate range card. Identify target reference points to be able to direct fire against approaching ground or air enemy forces. The commander must also ensure that dead space is covered with grenade launchers or mines.
Deploy all weapon-carrying vehicles on the base perimeter. As discussed previously, this includes combat vehicles in the DSA for repair.
Ensure vehicles are properly positioned. Natural cover and concealment are used as much as possible. Hull defilade positions or hide positions may be used with vehicles on the perimeter whenever possible.
Setup observation posts and listening posts. The DSB cannot constantly occupy a full perimeter and perform its mission. Early warning is imperative. Therefore, OPs are critical. OPs must provide a good view of the sector, which ideally overlaps with the adjacent OP sectors. The OPs and routes to them must provide cover and concealment. They should not be in positions that attract attention (such as isolated groups of trees) or on the very peaks of hills where positions would be silhouetted. Further guidance on OPs may be found in FM 3-19.4 (19-4) and FM 17-98.
Establish patrols when required.
Enforce noise and light discipline.
Ensure camouflage is used properly, guidance can be found in FM 5-20.
Plan and establish hasty obstacles.
Create a quick reaction force to respond immediately against a threat within the base. Ensure the force has covered and concealed routes to each sector on the perimeter.
Ensure soldiers know alert signals and proper responses to artillery and air attacks. Since soldiers are not continuously occupying the perimeter, they must be well trained to quickly respond to early warnings.
Prepare sector sketches and provide to the BCOC. These will be updated at regular BCOC meetings or shift change briefings. Sketches will include major terrain features, weapon positions and sectors of fire, dead space, OP positions, obstacles and mine fields, critical pieces of equipment, supplies, or facilities, and target reference points. See Figure 10-6 for examples of range cards, Figure 10-7 for weapons characteristic within the DSB, and Figure 10-8 for an example of a defensive sector sketch. Below is a checklist of those items needed in sector sketch preparation:
Draw your unit sector of engagement area.
Draw main terrain features in sector (s) and range to each.
Draw subunit positions.
Draw subunit primary and secondary sectors of fire.
Draw weapon positions with primary sectors of fire for each.
Draw machinegun final protective lines or principal direction of fire.
Draw locations of CP/OP.
Draw TRPs and RPs in sector.
Draw mines/obstacles.
Draw indirect fire target locations/final protective fire locations.
Draw and label dead space.
Draw patrol routes.
Draw locations, sector of fire of other weapons in your sector.
Place your unit ID, date time group (DTG) prepared, and magnetic north arrow on sketch.
Figure 10-6. Range Card
Weapon Caliber |
Effective Range/Maximum Range |
M9 Pistol (9-mm) |
Effective range: 50m |
M16A1 Rifle (5.56-mm) |
Effective range: 460m |
M16A2 Rifle (5.56-mm) |
Effective range: 550m |
M203 Genade launcher (40-mm) |
Effective range: 350m (area target);150m (point target) |
M249 Squad automatic weapon (5.56 link) |
Effective range: 900m |
M60 Machine gun (7.62) |
Effective range: 1,100m |
M2 HB Machine gun |
Effective range: 1,830m |
MK19 Grenade machine gun |
Effective range: 2,212m (area target);1500m (point target) |
M136 HE Antitank weapon (AT-4)(84-mm) |
Effective range: 300m |
Figure 10-7. Weapons Characteristics Within The DSB
Figure 10-8. Defensive Sector Sketch
DEFENSE OF SUPPLY POINTS
10-85. Whenever engineer assets are available, berms or deep-cut protective positions must be dug to protect fuel tankers and drums. Natural terrain concealment and camouflage nets are also used. Class I, II, and IV items are protected in deep-cut trenches if time allows, but construction of trenches for those items is a low priority. Traffic control must include measures to conceal movement at, to, and from supply points. At water points, control of spills and drainage is required to avoid standing pools of water, which reflect light. Proper fighting positions for individual and crew served weapons must be dug and integrated into the base defense. These include fighting positions for vehicles with mounted crew served weapons.
DEFENSE OF MAINTENANCE FACILITIES
10-86. In the company areas, individual positions are prepared near billeting areas and on the periphery of workstations. Proper fighting positions, bunkers, or other shelters are constructed next to key shop facilities for quick protection from artillery and air attacks. Use engineer assets when available to speed this process. These include fighting positions for vehicles with mounted crew served weapons or broken armored vehicles capable of firing their primary weapons systems. Ammunition should be acquired for these weapons systems and cached near the fighting positions.
INTELLIGENCE
INTELLIGENCE PREPARATION OF THE BATTLEFIELD (IPB)
10-87. IPB is a systematic, continuous process of analyzing the threat and environment in a specific geographic area. It is designed to support staff estimates and military decision making. By applying the IPB process, the commander can selectively apply and maximize his combat power at critical points in time and space on the battlefield. IPB facilitates:
Determining the threat's likely COA.
Describing the environment your unit is operating within and the effects of the environment on your unit.
10-88. The IPB consists of four steps:
Define the battlefield environment.
Describe the battlefield's effects.
Evaluate the threat.
Determine threat COAs.
10-89. The IPB process begins prior to and continues during the command's initial planning for an operation and is continuously updated during the operation. In step 1, the DSB S2:
Identifies characteristics of the battlefield which will influence friendly and threat operations.
Establishes the limits of the area of interest (AI).
Identifies gaps in current intelligence holdings.
10-90. Identifying for further analysis specific features of the environment or activities within it, and the physical space where they exist, that may influence available COAs or the commander's decisions. This focuses the command's initial intelligence collection efforts and the remaining steps of the IPB process. To focus the remainder of the IPB process, the S2 identities characteristics of the battlefield which require in-depth evaluation of their effects on friendly and threat operations, such as terrain, weather, logistical infrastructure, and demographics. Generally, the S-2 focuses more attention on areas within the command's area of operations (AO) and battle space than for the more broad areas of interest (AI). The AI is the geographical area from which information and intelligence are required to permit planning or successful conduct of the command's operation. Because the commander and staff need time to process information and to plan and synchronize operations, the command's AI is generally larger than its AO and battle space. The limits of the AI include the characteristics of the battlefield environment identified as exerting an influence on available COAs or command decisions. Additionally the AI is based on the amount of time estimated to complete the command's mission and the location and nature of the characteristics of the battlefield, which will influence the operation. During the planning process, the DSB S2 confers with the DISCOM S3 and ROC on recommendations for the command's battle space during development of friendly COAs. Defining the significant characteristics of the battlefield environment also aids in identifying gaps in current intelligence holdings and the specific intelligence required to fill them. Similarly, the S2 identifies gaps in the command's knowledge of the threat and the current threat situation. Once approved by the commander, the specific intelligence required to fill gaps in the command's knowledge of the battlefield environment and threat situation becomes the command's initial intelligence requirements. This effort, if successfully accomplished will result in saving time and effort by focusing only on those areas and features which will influence COAs and command decisions. If not properly executed, the DSB S2 will waste time and effort collecting and evaluating intelligence on features of the battlefield environment that will not influence success of the command's mission.
10-91. Step 2 evaluates the effects of the environment with which both sides must contend. The DSB S2 identifies the limitations and opportunities the environment offers on the potential operations of friendly and threat forces. This evaluation focuses on the general capabilities of each force until COAs are developed in later steps of the IPB process. This assessment of the environment always includes an examination of terrain and weather but may also include discussions of the characteristics of geography and infrastructure and their effects on friendly and threat operations. Characteristics of geography include general characteristics of the terrain and weather, as well as such factors as politics, civilian press, local population, and demographics. An area's infrastructure consists of the facilities, equipment, and framework needed for the functioning of systems, cities, or regions. Products developed in this step might include, but are not limited to:
Population status overlay.
Overlays that depict the military aspects and effects of terrain.
Weather analysis matrix.
Integrated products such as modified combined obstacle overlays (MCOOs).
10-92. Regardless of the subject or means of presentation, the S2 ensures that these products focus on the effects of the battlefield environment.
10-93. The best terrain analysis is based on a reconnaissance of the AO and AI. Identify gaps in knowledge of the terrain which a map analysis cannot satisfy. Use the gaps you identify as guide for reconnaissance planning. Because of time constraints, focus reconnaissance on the areas of most importance to the commander and his mission. For example, when conducting terrain analysis for a signal unit you might focus on identifying locations from which the unit's assets can best support the force commander while also identifying the best locations for the threat's EW assets that might target friendly signal systems. If engineer terrain support is unavailable, evaluate the terrain through a map analysis supplemented by reconnaissance. DMA produces specialized maps, overlays, and databases to aid in map based evaluations. Specialized DMA products address such factors as:
Cross-country mobility.
Transportation systems (road and bridge information).
Vegetation type and distribution.
Surface drainage and configuration.
Surface materials (soils).
Ground water.
Obstacles.
10-94. Ensure that the terrain analysis includes the effects of weather on the military aspects of the terrain. Consider the existing situation as well as conditions forecasted to occur during mission execution.
10-95. Also consider that terrain analysis is a continuous process. Changes in the battlefield environment may change the evaluations of its effects that result from terrain analysis. For example:
If built-up areas are reduced to rubble or lines of communication (LOCs) are destroyed by battle, you must reevaluate the mobility characteristics of the AO.
Similarly, if weather conditions change you must reevaluate the terrain's effect on military operations. Terrain analysis must always consider the effects of weather.
10-96. Terrain analysis consists of an evaluation of the military aspects of the battlefield's terrain to determine its effects on military operations. The military aspects of terrain are:
Observation and fields of fire - Observation is the ability to see the threat either visually or through the use of surveillance devices. Factors that limit or deny observation include concealment and cover.
Concealment and cover - Concealment is protection from observation. It can be provided by woods, underbrush, snowdrifts, tall grass, and cultivated vegetation. Cover is protection from the effects of direct and indirect fires. It can be provided by ditches, caves, river banks, folds in the ground, shell craters, buildings, walls, and embankments.
Obstacles - Obstacles are any natural or manmade terrain features that stop, impede, or divert military movement. Examples of obstacles to ground mobility are buildings, steep slopes, rivers, lakes, forests, deserts, swamps, jungles, cities, minefield, trenches, and military wire obstacles.
Key terrain - Key terrain is any locality or area the seizure, retention, or control of which affords a marked advantage to either combatant. An example of key terrain is a bridge over an unfordable river which gives access to the opposite shore without requiring an assault crossing. Another example is a level clearing in rough terrain which is the only accessible landing field for airmobile operations.
Avenues of approach (AA) - An AA is an air or ground route of an attacking force of a given size leading to its objective or to key terrain in its path. The identification of AAs is important because all COAs which involve maneuver depend upon available AAs. During offensive operations, the evaluation of AAs leads to a recommendation on the best AAs to the command's objective and identification of avenues available to the threat for withdrawal or the movement of reserves. During the defense, identify AAs that support the threat's offensive capabilities and avenues that support the movement and commitment of friendly reserves.
Weather - affects mobility and the functioning of virtually all items of equipment, as well as the performance of personnel. Terrain and weather are considered concurrently. Again, the DSB depends on the S2 channels to pass weather analysis information from the division weather team. The five aspects of weather that affect planning are temperature and humidity, precipitation, wind, clouds, and visibility.
10-97. Very high temperatures cause heat injuries and increased engine wear and failure. Very low temperatures increase cold weather injuries, damage to engines and cooling systems, lubrication problems, and fuel requirements. Cooler temperatures and humidity cause fog.
10-98. Precipitation affects mobility, visibility, and effectiveness of personnel and equipment. It also affects the quality of some stored material. Snow, even in small amounts, reduces the effectiveness of mines. DSB planners should consider precipitation of more than 0.1 inch per hour or 2 inches in 12 hours critical. Six inches of snow accumulation or drifts higher than 2 feet will have severe effects on mobility.
10-99. Wind usually favors the upwind force by blowing dust, smoke, sand, rain, or snow on the downwind force. It affects employment of NBC munitions, smoke, and conventional weapons.
10-100. Clouds affect air operations. This includes logistics air missions, but also our own close air support, as well as the enemy's ability to conduct airborne or air assault operations in the DSA.
10-101. Though poor visibility limits employment of airborne forces, agents and special purpose force operations often rely on it to reduce the effectiveness of our rear area security. Poor visibility hinders control and reduces effectiveness of reconnaissance, surveillance, and target acquisition.
10-102. Consider all of these factors when analyzing terrain, but always focus on the ones of most relevance to the specific situation at hand and the needs of the commander. Evaluate them in any order that best supports your analysis.
10-103. Remember that the terrain analysis is not the end product of the IPB process. Rather, it is the means to determine which friendly COAs can best exploit the opportunities the terrain provides and how the terrain affects the threat's available COAs.
10-104. In step 3 the DSB S2 NCO analyzes the command's intelligence holdings to determine how the threat normally organizes for combat and conducts operations under similar circumstances. When facing a well-known threat, the S2 can rely on his historical databases and well developed threat models. When operating against a new or less well known threat, he may need to develop his intelligence databases and threat models concurrently.
10-105. The S2's evaluation is portrayed in a threat model that includes doctrinal templates, which depict how the threat operates when unconstrained by the effects of the battlefield environment. Although they usually emphasize graphic depictions (doctrinal templates), threat models sometimes emphasize matrices or simple narratives.
10-106. Threat evaluation is a detailed study of the enemy forces. It considers their organization, tactical doctrine, equipment, and support systems. The DSB's interest for security purposes is in rear area threat evaluation. The DSB S2/S3 prepares a doctrinal template to reflect the enemy's air assault, airborne, operational maneuver group, and special purpose force employment doctrine. Other rear area threats (insurgents, guerrillas, terrorists, agents, and potential civil unrest) cannot be depicted in a doctrinal template. For these threats, an unconventional warfare situation map and population status overlay are prepared. The situation map shows probable operating areas, headquarters, encampments, and movement routes for unconventional forces. The rear area population status overlay shows areas with a high potential for civil unrest or with concentrations of enemy sympathizers. The overlay also shows where psychological operations would and would not be effective.
10-107. Once the threat evaluation is complete, this information is integrated with weather and terrain factors to determine how the threat is likely to operate in our rear areas. Again, the DISCOM S2 will evaluate the threat and advise the DISCOM S3. The DSB commander must ensure threat integration is coordinated with the DISCOM. Due to the limited resources available to the DSB commander to defeat the threat, he must identify specific areas of interest. These may include:
Landing zones and drop zones.
Key road junctions.
Forest paths.
Small groups of individuals attempting to move through or evade detection in the DSA.
Areas with insurgency sites.
Guerrilla/insurgency sites.
Terrorist operating or headquarters areas.
Target areas of interest are also identified along high-speed avenues of approach into the DSA.
Detailed information on IPB is in FM 34-130.
10-108. Step 4 integrates the results of the previous steps into a meaningful conclusion. Given what the threat normally prefers to do, and the effects of the specific environment in which he is operating now, what are his likely objectives and the COAs available to him? In step 4, the S2 develops enemy COA models that depict the threat's available COAs. He also prepares event templates and matrices that focus intelligence collection on identifying which COA the threat will execute. The enemy COA models are the products that the staff will use to portray the threat in the decision making and targeting processes. The S2 cannot produce these models, effectively predicting the threat COAs, unless he has:
Adequately analyzed the friendly mission throughout the time duration of the operation; identified the physical limits of the AO and AI; and identified every characteristic of the battlefield environment that might affect the operation. Identified the opportunities and constraints the battlefield environment offers to threat and friendly forces.
Thoroughly considered what the threat is capable of and what he prefers to do in like situations if unconstrained by the battlefield environment.
10-109. In short, the enemy COA models which drive the decision making process are valid only if the S2 NCO establishes a good foundation during the in the first three steps of the IPB process.
10-110. Like all other Army forces, the DSB must perform intelligence preparation of the battlefield (IPB). The sustainment planning considerations described in Chapter 8 are based on the DSB's knowledge of the enemy, (for example, his projected use of chemical munitions affects the DSB's stockage of MOPP gear) the weather, (fog may make aerial resupply impossible), and the terrain (lack of adequate road nets may mandate evacuation by air). Related to but distinct from the support, implications of IPB are the rear operations considerations. The DSB commander along with his staff, must analyze the terrain and weather and integrate this information with knowledge of the enemy. This enables the commander to identify probable target areas and activities. He can then predict probable courses of action to plan security operations.
RECONNAISSANCE AND SURVEILLANCE (R & S) PLANNING
10-111. Reconnaissance is an active mission concerned with enemy, terrain, and/or weather. It seeks out enemy positions, obstacles, and routes. Reconnaissance missions include:
Zone recon is conducted within a specific zone. The zone is defined by boundaries.
Area recon is conducted to obtain information concerning a specific location and the area immediately around it.
Route recon is conducted to obtain information on the route and terrain from which the enemy could influence movement along that route.
10-112. Surveillance is passive. It implies observing a specified area or areas from a fixed concealed position. Listening posts/observation posts (OPs) can provide 24-hour surveillance. OPs must be covered by indirect or direct fire.
10-113. R&S tasking matrix is a product used to display taskings, requests and coordinations necessary to answer the commander's priority information requirements (PIR). The matrix is made up of:
Named area of interest (NAI). Geographical area where information that will satisfy a specific information requirement can be collected.
Location. Grid coordinates or terrain features that identify the NAI.
Start/Stop. Beginning and end times for the R&S mission.
Specific information requirement. The exact information required during the R&S mission. Derived by the S2 from the commander's PIR. Issued in the form of a question. (Example: Is the bridge intact?)
Unit or asset. Each unit or asset capable of collecting the necessary information will be marked with an X. Each unit tasked to collect at a specific NAI will be marked with a circled X.
Report requirement. Describes specific reporting requirements. (Example: report every hour using SALUTE format). Figure 10-9 is an example of a R & S tasking matrix.
Figure 10-9. Reconnaissance and Surveillance (R&S) Tasking Matrix
SOURCES OF INFORMATION
10-114. The DSB's responsibility for security makes it imperative that the DSB TOC and DISCOM staff maintains a close relationship. Intelligence information possessed by the DISCOM with implications for security must be available to the DSB S2/S3. In addition, he receives information from DISCOM S2 channels. However, intelligence gathering should not be restricted to these sources. Local authorities, dislocated civilians, and local civilians are valuable intelligence sources. Information may also be obtained from base commanders within the DSA, military police, truckers, customers, elements of the MI battalion in the DSA, and any other elements moving into the area. In addition, information should flow laterally as well as vertically. For instance, while TMT company personnel must pass information like task force casualty estimates to the DSB S2/S3, they should also notify other DSB companies simultaneously whenever possible.
TERRAIN
10-115. The concept of OCOKA is used to analyze terrain. OCOKA refers to observation and fields of fire, concealment and cover obstacles, key terrain, and avenues of approach. The DSB commander will rely heavily on information from the DISCOM S2 for terrain analysis. The division is supported by a direct support terrain team that provides information to the G2 for IPB. The G2 passes it to the brigades and DISCOM HQ.
10-116. Line of sight is required in the DSA for radios, ground and air observers' vision, air defense target acquisition, and fields of fire for the DSA's direct fire weapons.
10-117. Concealment is protection from air and ground observation. Cover is protection from effects of fire. These considerations are closely related to observation and fields of fire. The DSB S2/S3 must determine what possibilities the terrain offers to both friendly and enemy forces. This analysis is vital to elements in the DSA in view of the limited weapons available and numerous personnel and items of equipment in the area. In built-up areas, DSA elements are likely to occupy buildings to maximize cover and concealment. Buildings significantly reduce heat signature. However, this technique is not effective in all areas of the world. Planners must take into account the soundness of buildings, availability of basements, and adequacy of the surrounding road net to accommodate traffic for CSS and self-defense operations.
10-118. Obstacles are natural and man-made features that stop, impede, or divert movement. Since one of the DSB's functions is to ensure freedom of movement for friendly forces in the rear, the DSB must be familiar with all existing obstacles and what the effects of removing, overcoming, or bypassing them would be. Weather effects on trafficability also act as obstacles.
10-119. Any feature that provides a tactical advantage is key terrain. Whether a particular feature is key or not varies with the tactical situation. However, features which may be key terrain features include bridges, fording sites, high ground, choke points, and road junctions. Not only must DSA elements optimize use of these features when available, but also they must recognize the enemy will frequently concentrate its efforts on these areas.
10-120. Avenues of approach are ground and air routes by which a force may reach an objective or key terrain feature. Considerations for avenues of approach in the rear are their capabilities to support movement of CS and CSS elements with their supported units and to allow rapid enemy movement into our rear. Commanders must avoid obvious armor and helicopter avenues of approach.
WEATHER
10-121. Weather affects mobility and the functioning of virtually all items of equipment, as well as the performance of personnel. Terrain and weather are considered concurrently. Again, the DSB depends on the G2/S2 channels to pass weather analysis information from the division weather team. The five aspects of weather that affect planning are temperature and humidity, precipitation, wind, clouds, and visibility.
10-122. Very high temperatures cause heat injuries and increased engine wear and failure. Very low temperatures increase cold weather injuries, damage to engines and cooling systems, lubrication problems, and fuel requirements. Cooler temperatures and humidity cause fog.
10-123. Precipitation affects mobility, visibility, and effectiveness of personnel and equipment. It also affects the quality of some stored material. Snow, even in small amounts, reduces the effectiveness of mines. DSB planners should consider precipitation of more than 0.1 inch per hour or 2 inches in 12 hours critical. Six inches of snow accumulation or drifts higher than 2 feet will have severe effects on mobility.
10-124. Wind usually favors the upwind force by blowing dust, smoke, sand, rain, or snow on the downwind force. It affects employment of NBC munitions, smoke, and conventional weapons.
10-125. Clouds affect air operations. This includes logistics air missions, but also our own close air support, as well as the enemy's ability to conduct airborne or air assault operations in the DSA.
10-126. Though poor visibility limits employment of airborne forces, agents and special purpose force operations often rely on it to reduce the effectiveness of our rear area security. Poor visibility hinders control and reduces effectiveness of reconnaissance, surveillance, and target acquisition.
THREAT EVALUATION
10-127. Threat evaluation is a detailed study of the enemy forces. It considers their organization, tactical doctrine, equipment, and support systems. The DSB's interest for security purposes is in rear area threat evaluation. The DSB S2/S3 prepares a doctrinal template to reflect the enemy's air assault, airborne, operational maneuver group, and special purpose force employment doctrine. Other rear area threats (insurgents, guerrillas, terrorists, agents, and potential civil unrest) cannot be depicted in a doctrinal template. For these threats, an unconventional warfare situation map and population status overlay are prepared. The situation map shows probable operating areas, headquarters, encampments, and movement routes for unconventional forces. The rear area population status overlay shows areas with a high potential for civil unrest or with concentrations of enemy sympathizers. The overlay also shows where psychological operations would and would not be effective.
THREAT INTEGRATION
10-128. Once the threat evaluation is complete, this information is integrated with weather and terrain factors to determine how the threat is likely to operate in our rear areas. Again, the brigade S2 will evaluate the threat and advise the brigade S3. He will perform threat integration for the entire rear area; the DSB commander must ensure threat integration for the DSA is coordinated with the brigade. Due to the limited resources available to the DSB commander to defeat the threat, he must identify specific areas of interest. These may include:
Landing zones and drop zones.
Key road junctions.
Forest paths.
Small groups of individuals attempting to move through or evade detection in the DSA.
Areas with insurgency sites.
Guerrilla/insurgency sites.
Terrorist operating or headquarters areas.
Target areas of interest are also identified along high-speed avenues of approach into the DSA.
Detailed information on IPB is in FM 34-10.
INTERNAL SECURITY
10-129. An effective base defense system must accomplish the following four tasks:
Security of the base. The base and base cluster commanders must establish the necessary defensive measures to ensure the security of their units. Each commander must apply METT-T analysis to determine requirements.
Detection. Detection is the early warning of enemy infiltration attempts. Detection devices include day and night observation devices as well as communications, intelligence, radar, and sensor equipment Chemical and radiological monitoring must also be used. Warning systems and procedures must be established and understood by all personnel. If an attack is unlikely, few people are involved in defensive operations. However, personnel will always man OPs and access points. If a threat is probable, defensive requirements will disrupt support operations. Alarms should be used to notify all personnel of alert postures. Warning devices include sirens, pyrotechnic and horns. The MPs may provide the base and base cluster commander's link for detection, early warning, and deployment against enemy attacks in the rear. Information gathered by MP elements dispersed throughout the rear area helps apprise commanders of enemy activity near bases. When the ROC determines the need, MPs respond to bases under attack.
Delay. The defense system must be able to hinder the threat's progress to permit defense forces to react. Obstacles covered by direct or indirect fires slow or canalize movement. The ROC can, with division G3 approval, authorize mine emplacement in the division rear. However, ROC must ensure a proposed minefield is coordinated with adjacent, higher, and subordinate units. It must also ensure limitations to friendly maneuver units are minimized and all requirements for reporting, marking, and recording are met.
Destruction. DSB units should place machine guns and lightweight antiarmor weapons to cover obstacles and avenues of approaches. Grenade launchers mounted on vehicles are effective fire suppression systems that can be quickly dispatched to threatened areas. Weapons systems evacuated to the DSA and BSA for repair should be used to prevent a breach of the perimeter. The equipment to be repaired weapon systems should be integrated into the defense plan.
10-130. Internal security of the DSA involves all soldiers. The ability to identify the threat and timely reporting to the TOC is the key to survivability in the DSA. The DSB TSOP covers, as a minimum, procedures for the following internal security measures:
Recon and surveillance plan.
Guard post operations.
Observation post (OP) operations.
Foot patrols.
Levels of alert (THREATCON).
Operational security (OPSEC).
Counterintelligence.
Standard signals for DSA response.
Essential elements of information.
Enemy prisoners of war.
STAND - TO.
Ready reaction force.
Movement of unit/personnel in the DSA.
DISMOUNT POINT
10-131. The following checklist is for outgoing vehicles to ensure that our soldiers are prepared for missions. Supervisors will ensure soldiers departing on missions retain this checklist to show gate guards.
______ ORGANIZATIONAL MAINTENANCE PMCS CERTIFICATION
______ FULL FUEL TANK
______ TWO FULL 5-GAL FUEL CANS SECURED
______ TWO FULL 5-GAL WATER CANS SECURED
______ A CASE OF EMERGENCY MREs ON BOARD
______ TWO QUARTS OF ENGINE OIL ON HAND
______ ONE QUART TRANSMISSION FLUID ON HAND
______ TA-50 TO INCLUDE SLEEPING BAGS ON HAND
______ INDIVIDUAL WEAPONS, MAGAZINES, AMMO ON HAND
______ CALL SIGNS AND FREQUENCIES FOR TWO DAYS
______ CHALLENGE AND PASSWORDS FOR TWO DAYS
| CHALLENGE | PASSWORD | |
| 1st Day | ____________ | ____________ |
| 2nd Day | ____________ | ____________ |
______ COMMS CHECK WITH CP CONDUCTED
______ LATEST ROAD CONDITIONS PROVIDED
CIRCLE ONE: GREEN AMBER RED BLACK
______ LATEST ROAD INTELLIGENCE
______ ROUTE TO TRAVEL/DESTINATION
ROUTE:_____________________
DESTINATION: _____________
______ SECURITY OF LOAD CHECKED
______ VEHICLE/TRAILER BUMPER NUMBERS
______ CAMOUFLAGE SYSTEM ON BOARD
______ MAP ON BOARD
______ SEAT BELTS USED
______ CP AWARE OF VEHICLE DEPARTURE
______ DATE TIME GROUP OF DEPARTURE___________
OTHER DEFENSIVE MEASURES
10-132. The DSB commander has additional assets available to him for the defense of the DSA. Weapons systems evacuated to the DSA for repair should be used to prevent a breach of the perimeter. The equipment to be repaired weapon systems should be integrated into the defense plan.
10-133. Planning and coordinating support with combat support units in the DSA and the DISCOM HQ, is essential for integrating all resources into an effective defensive plan. At a minimum the following operations are planned:
Fire support.
Air defense.
Engineer
Military police.
Close air support.
10-134. Despite the best planning efforts, situations may arise in which resources will not be available to meet requirements as outlined in doctrine and support plans. Improvisation, innovation, and creativity may be necessary to provide continuous support to the division troops.
FIELD ARTILLERY SUPPORT
10-135. The BCOC will develop the fire planning required to implement the execution of fire support for the DSA. The DSB S2/S3 will coordinate fires with the DSA FSO designated by the field artillery battalion commander. Together, they will plan targets for the DSA defense and help establish preplanned engagement areas for artillery and close air support. These fires will be coordinated with the brigade fire support coordinator, through the service battery or directly from the BCOC to the main CP. Targets are placed in the AFATDS systems for both DISCOM and division implementation. Artillery (and ADA) overlays must include displaced civilian camps, routes, and information on arts, monuments, and archives.
10-136. Calls for fire from the bases are made to the BCOC via field phones. If phones are not available, FM radio will be used. As previously mentioned, a direct line will link the BCOC and FA service battery CP. Calls will be made in accordance with procedures detailed in FM 3-09.30 (6-30). An aerial fire support officer may be on call to adjust fires as necessary. TC 25-4-1 gives details on planning and conducting fire coordination exercises.
AIR DEFENSE ARTILLERY SUPPORT
10-137. The DSA must be protected from enemy air strikes. ADA assets likely to be available in the DSA are Stingers/Avengers if the DSA is one of the main defensive priorities. The DSB S2/S3 will coordinate with the Stinger/Avenger section chief for DSA defensive fires. Assets are positioned to cover anticipated air avenues of approach. The DSB S2/S3 posts locations of the systems and air corridors covered on his sector sketch. The ADA based in the DSA will run a line to the BCOC. This will ensure early warning of all inbound aircraft. In addition, although not located in the DSA, the Patriot defensive umbrella should encompass the DSA. ADA operations are discussed in FM 44-3.
ENGINEER SUPPORT
10-138. When engineer assets are located in the DSA, they will be made available to the BCOC for survivability and countermobility operations. Therefore, the DSB S2/S3 must be prepared to take advantage of assets as they become available. Along with an engineer designated by the brigade engineer, he will plan barriers and minefield according to guidelines and principles presented in FM 3-34 ( 5-100) and FM 5-102.
MILITARY POLICE OPERATIONS
10-139. A direct support military police platoon is usually operating from the DSA. The battlefield missions performed by this platoon may include battlefield circulation control, area security, operation of the EPW point, and law enforcement.
10-140. Battlefield circulation control is performed along MSRs and in and around the DSA. MPs use traffic control points, mobile patrols, and temporary road signs to accomplish this mission. Coordination between MPs and the DSB TOC is essential to ensure movement in the area is controlled. Displaced civilian control and coordination with the local government must be included in planning.
10-141. The area security mission of the MPs is vital to rear operations. MPs employed in the brigade rear provide a light, mobile force that can move, shoot, and communicate. Their mobility makes it possible for them to detect the threat as they aggressively patrol road nets and key terrain features throughout the rear area. Their organic communications enable them to advise the rear CP, base clusters, bases, and moving units of impending enemy activity. MPs may also be used for convoy security and to protect static positions as required. However, when used in this manner, missions, which capitalize on MP mobility, are degraded.
10-142. The MPs conduct collection, evacuation, and internment operations to support their EPW mission. The EPW point holds EPWs captured by brigade units until they can be evacuated to the division central collection point. FM 3-19.40 (19-40) covers EPW operations in detail.
10-143. Law and order operations are only performed when the commander requires them and the tactical situation permits. This mission is usually the lowest priority during war.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|