CHAPTER 4
OFFENSIVE OPERATIONS
An SBCT dictates the nature, scope, and tempo of offensive operations. While the manner in which an SBCT orchestrates offensive operations throughout the full spectrum of conflict will be different in many respects to legacy forces, the doctrinal characteristics of offensive operations remain unchanged. The command and control systems (specifically the INFOSYS) and a capability to access higher echelon information databases allow the SBCT commander to visualize and anticipate opportunities, conduct rapid decision-making, and direct the execution of decisive combat. The C2 INFOSYS, reach capability, and organic force structure allow the SBCT to conduct offensive operations throughout its assigned area of operations.
Section I. CHARACTERISTICS OF THE OFFENSE
While the characteristics of offensive operations remain unchanged, the SBCT's unique capabilities allow it to conduct offensive operations with greater precision and rapidity than other organizations in the past. In past military operations, US ground forces conducting combat operations spent precious lives and extraordinary amounts of munitions and time to develop situations to the point where they had enough clarity to develop the best solution to the tactical problem. The sensors and INFOSYS within the SBCT will allow the commander to visualize the battlefield better than his counterparts, both past and present; however, they will not eliminate casualties or render obsolete dismounted combined arms infantry assaults. The SBCT's fight will ultimately result in a personal human endeavor wherein fear, uncertainty, and chance still play a part.
4-1. SURPRISE
Surprise is defined as attacking the enemy at a time or place or in a manner for which he is not physically or mentally prepared (FM 3-0). The successful integration of surprise into any offensive operation provides an initial tactical advantage over the enemy by delaying his reactions, confusing his command and control efforts, and forcing him to make decisions for which he is unprepared. Combat actions are particularly complex as the SBCT confronts its opponents at relatively close ranges in restrictive terrain. While satellites, UAVs, and other technological ISR assets may not be readily available to the enemy, global and national news, intelligence from sympathetic countries, local nationals, and discrete reconnaissance and surveillance by belligerents may be available to the enemy. These provide excellent sources of information that could undermine the SBCT's attempts at surprise. The SBCT commander and staff must perform a thorough analysis of EEFI and PIR and guard them in order to preserve the element of surprise while conducting tactical deception and IO to veil intended combat actions.
a. The SBCT has several capabilities that lend themselves to achieving surprise. First, the tremendous potential for the cavalry squadron (RSTA) to gain accurate and timely information on the enemy allows the commander to take advantage of enemy weaknesses and to disrupt enemy movement, allowing combat forces to gain surprise. Second, the mounted speed of the three maneuver battalions provides the SBCT commander the option to rapidly position combat power, limiting the enemy's ability to react. Finally, the SBCT's ability to attack over various classifications of terrain through any type of weather, day or night, will keep the enemy off-balance.
b. The SBCT can achieve surprise in several ways. IO and tactical deception are a key foundation to encourage the enemy to relax or to gain a false sense of the tactical environment. The SBCT must use tactical deception through feints and demonstrations as a precursor to actual offensive operations. The key to successful deception is to show the enemy what he expects to see. It is not necessary to completely fool the enemy. Often, surprise is achieved by causing the enemy to hesitate physically or in his decision-making, allowing the SBCT to retain the initiative by concentrating forces and adjusting tempo as the tactical situation requires.
4-2. CONCENTRATION
Concentration is defined as the ability to mass the effects of combat power (FM 3-0). While the SBCT commander must concentrate overwhelming effects on the defending enemy force as part of the decisive operation, he must be tactically cautious in massing combat forces to do so. An enemy may stand and fight large formations in open, rolling terrain, or he may rely instead on mines, indirect fire, or some type of terrorist (or other asymmetric) action. It is likely that the SBCT's opponent will seek close combat in urban or severely restricted terrain where it is difficult for US forces to employ fires and bring infantry forces to bear in overmatching numbers. To counter this threat, commanders must plan to defeat the enemy when and where the SBCT is least vulnerable. Most importantly, the commander must optimize the SBCT's ability to operate in a dispersed manner, utilizing its mounted speed to quickly mass forces in operations driven by rapid decision-making based on accurate and timely information from the cavalry squadron (RSTA).
a. The cavalry squadron (RSTA), combined with access to other ISR and higher echelon information databases, clarifies the situation in severely restrictive and urban terrain. This clarification allows the SBCT to conduct maneuver and mass forces and effects at the decisive point to achieve overmatching combat power against the enemy. The ability to mass fires and effects resides throughout the SBCT. It starts with the ability of the cavalry squadron (RSTA) to gain contact (electronic or physical) with the enemy. Near real-time information, not only on enemy disposition, composition, and strength but also on the trafficability of routes into the objective, allows the SBCT to place precision fires and effects on the enemy, jam his communications, isolate any forces attempting to withdraw or reinforce while also allowing the infantry to conduct the decisive operation. Unrestricted maneuver, with assistance from the engineers when needed, allows the infantry to quickly mass the effects (concentration) of direct fire without massing formations for too long.
b. The SBCT has the flexibility to concentrate fires at the lowest level and the ability to fight as a combined arms team at the company level. Concentration of direct fires in a combined arms infantry assault in any terrain is the final component of decisive combat. This is the SBCT's strength.
4-3. TEMPO
Tempo is defined as the rate of military action (FM 3-0). Following the use of surprise to gain the initiative, the attacker controls the tempo in order to maintain relentless pressure on the enemy. Relentless pressure forces the enemy to make decisions for which he is unprepared, to conduct maneuver for which he has not rehearsed, and prevents him from recovering from the initial shock of an attack. The ability to conduct decision-making during execution originates with the development of branches and sequels during planning. The data and information provided by the cavalry squadron (RSTA), combined with the other ISR assets, the INFOSYS, and the mounted speed of the infantry, allows the SBCT commander to execute branches and sequels at predetermined decision points during the course of a battle. The key to maintaining the appropriate tempo is to anticipate enemy reaction during planning and quickly maneuver forces during execution to seize the opportunity it presents.
a. The SBCT's tempo will fluctuate. Tempo will be slow as the cavalry squadron (RSTA) focuses its reconnaissance and surveillance effort to confirm and or deny the PIR for the attack. At the same time, the SBCT can use other ISR assets and access to ARFOR and national assets to compliment the cavalry squadron (RSTA)'s efforts. In combination, these two capabilities provide the SBCT S2 with the ability to clarify the situation for the commander with great accuracy.
b. The SBCT commander must exercise tactical patience as reconnaissance and surveillance is conducted. Once he attains the clarity necessary to allow the appropriate decision, he issues necessary FRAGOs and is able to increase the operational tempo as he transitions the SBCT to the attack.
c. While clarity and SU are necessary to conduct decision-making, the SBCT commander cannot be overly reliant upon technology to the point he expects, and waits for, "perfect" intelligence. The commander must guard against hesitation while waiting for perfect SU or to set the conditions for attack without error or casualties. This situation occurs when the commander and staff attempt to fight the plan instead of a freethinking enemy. To drive the tempo of an offensive operation, the SBCT commander makes tactical decisions quickly, taking prudent risk to seize opportunities as they are presented.
d. At times, and under exceptional circumstances, the reconnaissance and surveillance efforts of the cavalry squadron (RSTA) may not yield the degree of clarity the commander desires to transition into offensive operations with maneuver forces. This is most likely to occur if the enemy adopts something similar to a security zone. The cavalry squadron (RSTA) is not organized to fight for intelligence; therefore, an effective enemy security zone may deny the SBCT commander the fidelity he desires for an attack. In such circumstances, the commander adjusts the tempo of the operation to conduct a reconnaissance in force with his maneuver battalions. The reconnaissance in force maintains tempo while providing the clarity the commander needs to begin maneuvering forces to attack the enemy's decisive points.
4-4. AUDACITY
Audacity is defined as the state of being bold with a reasoned disregard of normal constraints. The willingness and ability of the SBCT commander to execute offensive operations with audacity is a key component to success. Audacious action normally occurs when an unexpected opportunity arises during the course of an attack. Subordinate commanders must be prepared to act quickly within the SBCT commander's intent to exploit these opportunities by refocusing combat power, committing reserves, increasing the tempo, or whatever maneuver decision is required to overwhelm the defender. It is entirely possible and in fact likely that the path to success will lie on an avenue unanticipated in the plan. In the past, armies have relied upon the "genius" of the commander to anticipate and seize unforeseen opportunities. The SBCT commander will still have maintain this feel for the battle. However, the cavalry squadron (RSTA), the robust ISR capability available to him, and C2 INFOSYS capability will aid him to an unprecedented degree in this personal responsibility to visualize the upcoming battle.
Section II. FORMS OF MANEUVER
The SBCT commander selects the form of maneuver based on his analysis of the factors of METT-TC to develop a course of action. The forms of maneuver are—
- Envelopment.
- Turning movement.
- Infiltration.
- Penetration.
- Frontal attack.
4-5. ENVELOPMENT
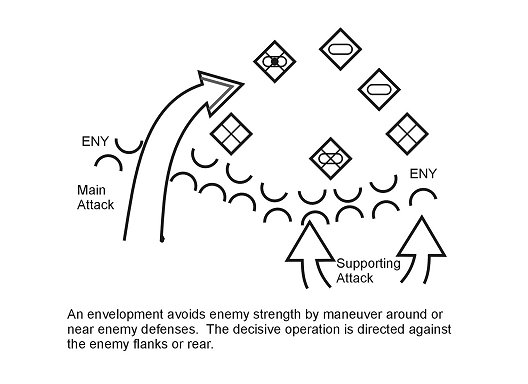
The envelopment (Figure 4-1) is the preferred form of maneuver. It seeks to apply strength against weakness, striking a moving or stationary enemy from an unexpected direction (an assailable flank). If an assailable flank does not exist, the SBCT creates one by using another form of maneuver. The preponderance of the SBCT's combat power avoids the enemy where his force is most protected and where his fires are concentrated. The cavalry squadron (RSTA), or other ISR assets, allows the SBCT to develop the situation out of contact. The SBCT can then maneuver out of contact and envelop the enemy on its own terms. Another option is for the SBCT to fix the enemy with one force (task organization is METT-TC dependent) then attack the enemy with a preponderance of the remaining available force.
Figure 4-1. Envelopment.
4-6. TURNING MOVEMENT
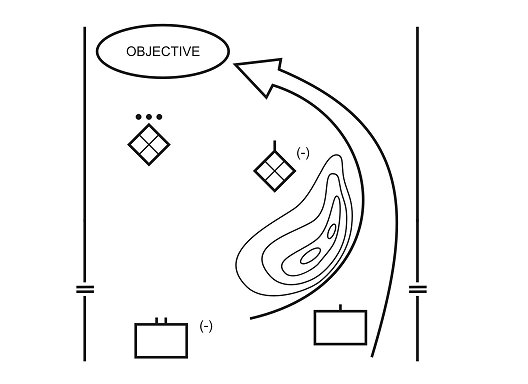
A turning movement (Figure 4-2) is used to destroy or force the withdrawal of a defending enemy. The SBCT passes around and avoids the enemy's main force and secures an objective in the enemy's rear area along his line of communications, causing him to abandon his prepared defensive positions to address this threat. Turning movement allows the SBCT to fight a repositioning enemy on terms and conditions that are favorable to the SBCT. The SBCT normally will conduct a turning movement as part of a higher headquarters' operation.
Figure 4-2. Turning Movement.
4-7. INFILTRATION
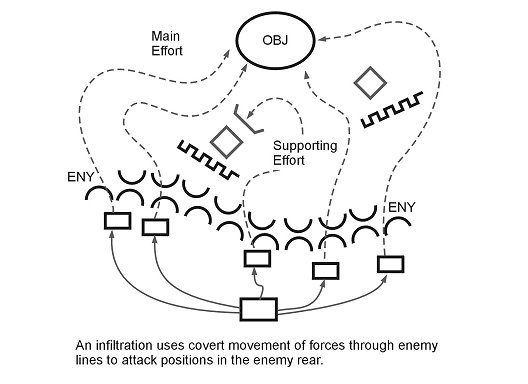
Infiltration (Figure 4-3) is the covert movement of all or part of the attacking force through enemy lines to an objective in the enemy's rear area. Infiltration normally is used before an attack that is using another form of maneuver. An infiltration may be used to reconnoiter the enemy force or objective, to attack the enemy from an unexpected location, or to seize terrain to support a future attack. The SBCT normally infiltrates ISR assets or infantry to obtain information or to support the attack by destroying vulnerable key targets or seizing key terrain. Planning for an infiltration must be detailed and synchronized.
Figure 4-3. Infiltration.
4-8. PENETRATION
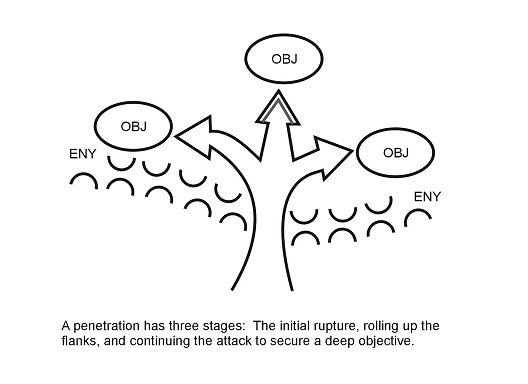
The penetration (Figure 4-4) ruptures the enemy defense along a narrow front to create an assailable flank, gain a foothold in the enemy's defense, or gain access to the enemy's rear area. The SBCT's ability to rapidly mass combat power at the point of penetration while achieving surprise as to the intended location of the point of penetration is critical to success.
Figure 4-4. Penetration.
4-9. FRONTAL ATTACK
The frontal attack is used to attack the enemy across a wide front and along the most direct approach. It is used to overrun and destroy a weakened enemy or fix the enemy. The SBCT may conduct a frontal attack against a stationary or moving enemy force. Unless a frontal attack is executed with overwhelming speed and combat power against a weaker enemy, it will seldom be decisive.
Section III. FORMS OF TACTICAL OFFENSE
The SBCT conducts, or participates in, movements to contact, attacks, exploitations, and pursuits across the full spectrum of conflict. The SBCTs cavalry squadron (RSTA) and INFOSYS do not negate the need to conduct traditional movements to contact. However, the actual techniques used during a movement to contact may be modified to fit the capabilities found within the SBCT. Attacks, exploitations, and pursuits may be conducted sequentially or simultaneously throughout the SBCT's AO.
4-10. MOVEMENT TO CONTACT
A movement to contact is an offensive operation designed to develop the situation and gain or reestablish contact with the enemy. It is used when the tactical situation is unclear or when contact with the enemy has been lost. The SBCT's cavalry squadron (RSTA) and other ISR assets may reduce the need to conduct a movement to contact as SU allows the commander to determine where significant enemy forces are located. However, enemy information operations may degrade the accuracy of the commander's SU. In this instance, the SBCT will conduct a movement to contact. A movement to contact develops the situation and maintains the SBCT commander's freedom of action once contact has been gained. The SBCT may conduct a movement to contact as part of a higher unit's movement to contact, or the SBCT commander may direct a movement to contact any time during an operation. The following are fundamentals of a movement to contact:
- Focus all efforts on finding the enemy.
- Make initial contact with the ISR assets or with the cavalry squadron (RSTA).
- Task-organize the SBCT and use movement formations to attack rapidly throughout the area of operation.
- Plan to facilitate flexible response throughout the AO.
- Maintain contact once contact is made.
The SBCT commander develops an ISR plan that ensures all ISR assets are employed to answer the PIR and facilitate his decision-making. The cavalry squadron (RSTA), augmented by other ISR assets and the SBCT's ability to access higher echelon sensors, observes NAIs throughout the SBCT's AO and area of interest. The cavalary squadron (RSTA)'s efforts may allow the commander to transition the SBCT from a movement to contact to an attack or a defense prior to the infantry battalions making contact with the enemy. The SBCT may apply one of the following techniques when conducting a movement to contact: approach march or search-and-attack.
a. Approach March Technique. The approach march technique is the traditional, linear technique for conducting a movement to contact. The technique is an advance of a combat unit when direct physical contact with the enemy is expected and desired. Using this technique, the SBCT will normally organize into a security force, advance guard, main body, flank guards, and rear guard. When the SBCT participates as part of a divisional or corps movement to contact (using the approach march technique) in an MTW, it will likely fill the roles of security force, flank guards, or rear guard. The commander visualizes how the SBCT will be deployed when contact with the enemy is made. Based upon this visualization and the answers to his PIR, he may move the SBCT in a single column or in multiple columns.
(1) Security Force. This force focuses more on reconnaissance and surveillance than on combat. The SBCT staff develops its reconnaissance and surveillance plan to ensure the appropriate combination of the cavalry squadron (RSTA) and other ISR assets is available to observe NAIs throughout the AO, answer the PIR, and facilitate the commander's decision-making. When possible, the SBCT infiltrates the ISR assets throughout the AO. The cavalry squadron (RSTA) and other ISR assets shape the AO for the SBCT commander and may allow for a timely and efficient transition to an attack or a defense prior to the advance guard making contact with the enemy.
(2) Advance Guard. The advance guard is a task-organized unit or detachment that precedes a formation to protect the main body from ground observation or surprise by the enemy. The advance guard develops the situation to protect the deployment of the main body when it is committed. The SBCT commander, through his analysis of the factors of METT-TC and his SU during execution, will determine how far forward of the main body the advance guard will operate. The advance guard must operate within the supporting range of the main body in order to not be too vulnerable, but it should operate far enough forward to successfully accomplish its mission. The advance guard provides its own advance guard, flank guards, and rear guard. When the SBCT is moving along multiple axes, each lead infantry battalion serves as an advance guard. The SBCT may assign the following tasks to the advance guard:
- Reinforce the reconnaissance and surveillance efforts of the security force.
- Destroy enemy security forces within its capabilities.
- Destroy or repel all enemy reconnaissance forces.
- Bypass or breach obstacles along the main body's axis of advance.
- Fix, suppress, or block enemy forces to develop the situation for the main body.
(3) Main Body. The main body will contain the preponderance of the SBCT's combat power. Based on the commander's intent and concept, the main body keeps a sufficient distance from the advance guard to maintain flexibility. Although some level of security might be felt because of the COP and units to the front, flanks, and rear, the main body must still maintain local security and be prepared to rapidly deploy and attack the enemy. Depending on his visualization, answers to the PIR, and the fidelity of other information, the SBCT commander may designate a portion of the main body as the reserve. The reserve gives the SBCT commander flexibility to react to unforeseen circumstances.
(4) Flank and Rear Guards. SBCT forces screen or guard the flanks and rear of the SBCT if adjacent units are not protecting the SBCT's flank or rear. Flank and rear guard responsibilities typically reside with the main body force. The flank security forces must be task organized to provide information and early warning, to repel anticipated enemy attacks or to delay enemy attacks long enough for the main body to react. The SBCT commander may task-organize ISR assets to the main body force to enhance the ability of the flank and rear guards to accomplish their missions during movement.
b. Search-and-Attack Technique. A search-and-attack is a decentralized movement to contact, requiring multiple, coordinated patrols to locate and destroy the enemy. It is most often used when operating within noncontiguous areas of operation during an SSC. The SBCT conducts this form of the movement to contact to destroy enemy forces, deny the enemy certain areas, to protect the force, or for information collection. Execution of the search-and-attack will typically be by company-sized elements in battalion-sized AOs. During a search-and-attack, the SBCT task-organizes its subordinate units into finding, fixing, and finishing forces, and may task its subordinate units to conduct the following missions:
- Locate enemy positions or habitually traveled routes.
- Destroy enemy forces within its capability or to fix and or block the enemy until reinforcements arrive.
- Maintain surveillance of a larger enemy force through stealth until reinforcements arrive.
- Search urban areas.
- Secure military or civilian property or installations.
- Eliminate enemy influence within the AO.
(1) Finding the Enemy. Much time may be required to develop relevant information on the enemy. The SBCT must leverage its cavalry squadron (RSTA) and other ISR assets to enhance the commander's understanding. The cavalry squadron (RSTA) may arrive in the AO prior to the remainder of the SBCT. Information on enemy activities in the AO gained through the cavalry squadron (RSTA)'s reconnaissance and surveillance efforts will help the SBCT commander focus the search-and-attack. The commander may subdivide the SBCT's AO to allow the cavalry squadron (RSTA) to conduct a zone reconnaissance while the infantry battalions, with attached ISR assets, conduct a search-and-attack.
(2) Fixing the Enemy. The SBCT will task its subordinate units with one of the following actions after the commander has developed his SU:
- Block enemy escape and or reinforcement routes for another unit to attack. The blocking unit maintains contact and positions its forces to isolate or fix the enemy so another unit can attack. The INFOSYS will be critical for the attacking unit to destroy the enemy and prevent fratricide of the blocking unit.
- Conduct an attack. This occurs if it is in line with the commander's intent and concept. The attacking force must be able to generate sufficient combat power for a decisive operation.
- Maintain surveillance. The unit avoids detection and reports enemy composition, disposition, and activities.
(3) Finishing the Enemy. Once the enemy force has been fixed, the SBCT may task its subordinate units to conduct one of the following:
- Conduct an attack.
- Block an escaping enemy for another unit to attack.
- Continue reconnaissance and surveillance activities with a refined CCIR.
- Employ lethal or non-lethal fires and effects.
4-11. ATTACK
An attack is a type of offensive operation characterized by coordinated movement supported by fires and effects. Attacking is the primary means of destroying or defeating an enemy force, of seizing or securing terrain, or both. Attacks take place along a continuum defined at one end by the issuance of a FRAGO that directs the execution of deliberate offensive operations by forces immediately available to the conduct of deliberate offensive operations. The other end of the continuum is defined by published, detailed orders with multiple branches and sequels, detailed knowledge of all aspects of the enemy's disposition, a force that has been task-organized specifically for the mission, and the conduct of extensive rehearsals. Most attacks fall within the continuum as opposed to its extreme ends. The cavalry squadron (RSTA), other ISR assets, INFOSYS, and reach capability allow the SBCT to apply the best of these extreme ends during planning and execution to facilitate quick decision-making while still maintaining a good doctrinal foundation for a successful attack.
a. Situational Understanding. The SBCT commander takes every opportunity to gain and refine data and tactical information regarding the enemy. He uses his cavalry squadron (RSTA) and other ISR assets to gather data and information and process it into the relevant information and intelligence that eventually feed into his understanding. Relevant information and intelligence gathered during planning is especially useful to determine the feasibility and acceptability of a developed course of action. If the SBCT commander feels that he lacks appropriate knowledge of the situation, he may not continue with an attack. Instead, he may conduct a movement to contact or refine his ISR effort.
b. Intelligence, Surveillance, and Reconnaissance Effort. The SBCT commander ensures that the ISR effort is continuous throughout the operations process (plan, prepare, execute, and assess) for an attack. The enemy's attempts to modify his defenses will be detected. This early detection allows the SBCT commander to adjust his scheme of maneuver as the enemy situation becomes clearer. The SBCT commander uses all available ISR assets (HUMINT and technological) separately or in combination with the cavalry squadron (RSTA)'s efforts to provide the inputs to develop his SU. The two fundamental employment techniques for reconnaissance that support an attack are reconnaissance-pull and reconnaissance-push.
(1) Reconnaissance-Pull. The objective of reconnaissance-pull is to find weaknesses in enemy dispositions that can be exploited by the main body. The cavalry squadron (RSTA) and other ISR assets are deployed over a broad area of operations that allows them to identify enemy weaknesses to exploit and enemy strengths to avoid. Once these have been identified, the SBCT commander exploits the situation by choosing a course of action that allows his decisive operation (main effort) to attack the enemy's weaknesses and penetrate gaps in the enemy's defense. He then commits forces to widen the gap and envelop the enemy. The cavalary squadron (RSTA) and other ISR assets continue to move, avoiding enemy strengths and "pulling" the SBCT deep into the enemy's rear area of operations.
(2) Reconnaissance-Push. The objective of reconnaissance-push is to identify the obstacles and enemy forces that the main body must overcome to assault the objective in a previously chosen location in accordance with the order that deployed the cavalry squadron (RSTA) (typically WARNO2). Once the cavalry squadron (RSTA) has made contact with the enemy, it develops the situation within its capabilities. If the objective is the enemy force, the cavalry squadron (RSTA) orients on it to maintain contact and determine the enemy's disposition.
c. Special Purpose Attacks. The SBCT commander can execute an attack to achieve different results or for special purposes. The SBCT will normally execute special purpose attacks in an MTW or SSC. The commander's intent and an analysis of the factors of METT-TC determine the specific form of special purpose attack. These forms of the attack share the same planning, preparation, and execution considerations as other offensive operations. These subordinate forms of an attack are—
- Raids.
- Counterattacks
- Spoiling attacks.
- Feints.
- Demonstrations
(1) Raids. A raid is an attack that involves swift, temporary penetration of enemy territory for a specific mission. The SBCT conducts raids to capture prisoners, installations, or enemy materiel; to destroy enemy installations or materiel; to obtain specific information of a hostile force; to liberate captured friendly personnel or materiel; or to deceive or harass enemy forces. A raid is a small-scale attack that always ends with a planned withdrawal. Raids require detailed reconnaissance and surveillance planning and may rely on infantry battalion reconnaissance platoons or ISR assets rather that the cavalry squadron (RSTA) (METT-TC dependent). The SBCT normally assigns raids to subordinate forces. The raiding force may operate within or outside its normal area of operation. The raiding force moves to its objective by infiltration (mounted or dismounted), quick violent attack, or by air. Specific planning considerations for a raid include the following:
- Conduct detailed reconnaissance and maintain constant surveillance of the raid objective to ensure the enemy situation remains unchanged and within the capabilities of the raiding force.
- Position fire support systems to provide responsive fires and effects during the approach, actions on the objective, and the withdrawal.
- Establish clear abort criteria for the raid. These may include loss of personnel, equipment or support assets, or changes in the enemy situation on or near the raid objective.
- Develop contingency plans (branches) for enemy contact prior to and after actions on the objective.
- Plan casualty evacuation and raiding force extraction during the approach, actions on the objective, and the withdrawal.
(2) Counterattacks. A counterattack is executed from a defense to defeat an attacking enemy force or retake key terrain and regain the initiative. The counterattacking force ultimately conducts the decisive operation in the defense when committed; therefore, it should become the main effort upon its commitment. The SBCT commander may plan counterattacks as part of the SBCT's defensive plan. The SBCT may be the counterattacking force for a higher headquarters' defensive plan, if that higher organization lacks sufficient mobility and firepower in its subordinate units.
(3) Spoiling Attacks. A spoiling attack is executed from a defense to disrupt the enemy's attack preparations and is executed in the same manner as an attack. Spoiling attacks focus on the enemy's critical systems and forces that would have the greatest impact on the SBCT. These systems and forces include, but are not limited to, command and control systems, ISR assets, fire support forces, and any identified unconventional threat. Spoiling attacks are conducted as often as necessary to deny the enemy adequate attack preparation. The SBCT, with it organic cavalry squadron (RSTA) and other ISR assets, normally conducts spoiling attacks as part of a higher headquarters.
(4) Feints. A feint is intended to deceive the enemy and draw attention and combat power away from the main effort and force the enemy to employ his reserves away from the main effort or remain in position, attract enemy supporting fires away from the main effort, force the enemy to reveal defensive fires or weaknesses, or to gain surprise. Feints must be of sufficient strength and composition to cause the desired enemy reaction. Feints must appear to be real; therefore, some contact with the enemy is required. The SBCT may execute a feint as part of a higher headquarters' attack or may include a feint as part of its own deception plan. Planning for a feint follows the same sequences as any other attack. Special planning considerations include the following:
- Assign attainable objectives.
- Ensure the feint is resourced to appear as the main effort or as a credible threat to the enemy.
- Establish clear guidance regarding force preservation.
- Ensure adequate means of detecting the desired enemy reaction.
- Designate clear disengagement criteria for the feinting force.
- Issue clear follow-on missions to the feinting force.
(5) Demonstrations. A demonstration is used for deception. The SBCT executes it with the intention of deceiving the enemy; however, no contact is intended. A demonstration must be made clearly visible to the enemy without being obviously deceptive to the enemy. Demonstration forces use fires and effects, movement of maneuver forces, smoke, electronic warfare (EW) assets, and communications equipment to support the deception plan. Specific planning considerations include the following:
- Establish a means to determine the effectiveness of the demonstration.
- Establish a limit of advance (LOA) for the demonstration forces that allow the enemy to see the demonstration without being able to effectively engage it with direct or indirect fires.
- Establish other security measures necessary to prevent engagement by the enemy.
- Employ demonstrations to reinforce enemy expectations and contribute to the main effort's success.
- Develop contingency plans (branches) for enemy contact and to avoid decisive engagement with the enemy.
- Issue clear follow-on missions to the demonstration force.
4-12. EXPLOITATION
Exploitation is the bold continuation of an attack to increase success and take advantage of weakened or collapsed enemy defenses. Its purpose is to prevent reconstitution of enemy defenses; prevent enemy withdrawal; secure deep objectives; and destroy enemy C2 facilities, logistics, and forces. The SBCT commander configures his CCIR to facilitate decision-making and to help recognize the existence of this transition point within the offensive framework. The cavalry squadron (RSTA) and infantry battalions will continue to conduct tasks similar to those executed during the attack, and it is only in the condition of the enemy that there will be any noticeable difference. The SBCT commander and staff must maximize the ability to rapidly develop plans that facilitate seamless continuation of the offense as it transitions from attack into exploitation. Thus, ISR efforts for future operations must be tied to, and conducted simultaneously with, ongoing offensive operations. Once the exploitation begins, the enemy is given no relief from offensive pressure. In traditional (linear) combat, should the lead force be unable to continue the mission, follow-and-support forces rapidly assume responsibility. Within nonlinear combat, it is more likely that the SBCT must employ attacks against disorganized enemy units throughout an AO. As the SBCT destroys more enemy forces, it gains greater freedom of movement within the AO. The SBCT commander task-organizes HUMINT ISR assets to directly support the infantry battalions. Increased access to EPWs, noncombatants, and document and or electronic exploitation produces a cascading effect that yields greater clarity on disposition of the remaining enemy.
a. Form of Exploitation. The exploitation may take the form of an MTC or a series of attacks during hasty operations. The commander will usually issue a series of FRAGOs that designate—
- Movement formation.
- The positions of each battalion within that formation.
- Any required modification to task organization.
- Bypass criteria.
- Revised or new contol measures that assist the maneuver such as objectives, boundary changes, LOA, and FSCM.
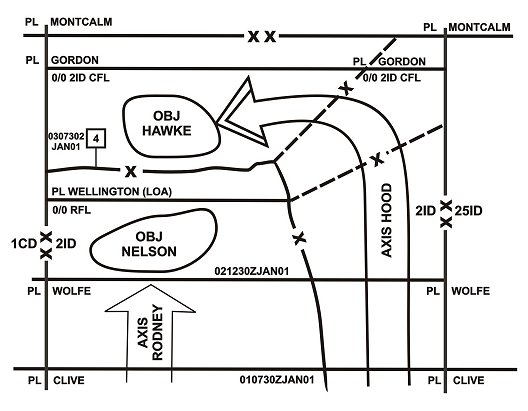
b. Control Measures. The commander uses control measures to retain his tactical options to converge on the most important axis or to redirect his exploitation effort on a new axis. These control measures should be flexible and capable of rapid adjustments to reflect changing conditions. For an example of control measure used during exploitation operations, refer to Figure 4-5. The commander balances the need to prevent fratricide with the need to allow his battalion commanders the ability to take advantage of opportunities.
Figure 4-5. Exploitation control measures in a contiguous AO.
c. Initiation of an Exploitation. The exploitation is initiated when an enemy force is having difficulty maintaining its position. Although local exploitations may appear insignificant, their cumulative effects can be decisive. Depending on the situation and its task organization, the SBCT can exploit its own success, it can be used as an exploiting force for a higher echelon, or it can follow-and-support another exploiting force. The commander must be ready at all times to use every opportunity afforded by the enemy for exploitation. Updated intelligence is crucial to accurately predicting the exact conditions required to transition from an attack to an exploitation. Such indicators include—
- Higher headquarters reports the threat of use of WMD by enemy forces.
- An increase in prisoners captured.
- An increase in abandoned materiel.
- The overrunning of artillery, command facilities, signal installations, and supply dumps.
- Enemy reconnaissance intensifies.
- Enemy fires decrease in intensity and effectiveness.
- Units become intermingled.
- Reports confirm the capture or absence of enemy leaders.
d. Transition. The transition to the exploitation may be abrupt or so gradual it is hardly distinguishable. The commander's primary concern when initiating an exploitation resulting from a successful attack is to shift his force into the appropriate combat formation and task-organize it with additional capabilities and resources to take advantage of a short window of opportunity. The SBCT would normally maneuver on a wide front and may move on two axes. When moving on two axes, each battalion must be task-organized to operate independently. After transition, units should make every effort to continue the advance without halting. They bypass enemy resistance when possible and make the most of available fire support when appropriate targets are presented. Fire support, target acquisition systems, and observers are positioned well forward with lead elements. Key fire and effects considerations are as follows:
- Plan fires and effects to support the attacks.
- Incorporate CAS and attack helicopters, which are well suited for exploitation.
- Establish FSCM between exploiting and converging forces.
- Keep the ECOORD advised of locations of lead elements to facilitate positive clearance of fires.
- Use families of scatterable mines (FASCAM) to delay or fix the enemy.
- Consider the loss of maneuver space.
- Position fire support assets well forward.
- Plan for continous fires and effects.
e. Follow Through. Once the exploitation begins, it is carried out to the final objective. The enemy should be given no relief from offensive pressure. Should the lead force be unable to continue the mission, follow-and-support forces must rapidly assume responsibility. Enemy forces encountered are not engaged unless they are a threat to the SBCT or cannot be bypassed. This decision rests with the next higher commander; however, freedom of action is normally delegated to commanders in the exploitation.
f. Follow-and-Support Forces. Follow-and-support forces clear the bypassed areas and expand the area of exploitation. Follow-and-support forces are normally battalion or higher formations employed primarily in exploitation and pursuit operations to facilitate maintaining the momentum of the attack. They may also be used in a penetration. A force with a follow-and-support mission is not a reserve but a committed unit. Follow-and-support forces assist attacking units by relieving them of tasks that would otherwise slow their advance. Follow-and-support forces can —
- Widen or secure the shoulders of the penetration by breaking through other enemy defenses.
- Block the movement of enemy reinforcements.
- Destroy bypassed pockets of resistance.
- Relieve elements of the attacking force that have been left to block or contain enemy forces.
- Secure the flanks of a penetration to prevent the enemy from closing it.
- Open and secure lines of communications.
- Secure decisive terrain overrun or bypassed by the attacking unit.
- Protect key installations or areas.
- Guard prisoners of war.
- Reinforce or assume mission of leading force.
- Widen breach lanes.
- Clear MSRs.
- Contol dislocated civilians.
When augmented with additional CSS assets, these follow-and-support forces may also be assigned to control and process refugees and collect and manage casualties.
g. Decentralized Execution. Decentralized execution is characteristic of the exploitation; however, the commander maintains enough control to prevent over extension of the command. Minimum control measures are used. Aerial reconnaissance and Army attack or reconnaissance aircraft maintain contact with the enemy movements and keep the commander advised of enemy activities. Close air support aircraft, fires and effects assets, and attack helicopters can attack moving enemy reserves, withdrawing enemy columns, enemy constrictions at choke points, and enemy forces that threaten the flanks of the exploiting force. Security of ground supply columns must be considered and an aerial resupply may be necessary. Exploiting forces take advantage of captured supplies whenever possible.
4-13. PURSUIT
A pursuit is an offensive operation designed to catch or cut off an enemy force attempting to escape, with the aim of destroying it (FM 3-90). The pursuit normally follows a successful exploitation and the enemy attempts to conduct a retrograde, The primary function of pursuit is to complete the destruction of the enemy force. As a successful exploitation develops and the enemy begins to lose the ability to influence the situation, the SBCT may be ordered to execute the pursuit. In the pursuit, the SBCT may point its advance toward a physical objective; however, the mission is the destruction of the enemy's main force. The SBCT's ability to share and rapidly disseminate information facilitates the transition into pursuit. Most enemy forces will attempt to flee the area or blend into the local population; however, some enemy forces, motivated by ideology or ethnic and or religious convictions, may hold out. To complete the destruction of those enemy forces attempting to flee the AO, the SBCT designates direct pressure and encircling forces. The commander's analysis of the factors of METT-TC determines the composition of these forces. Infantry, supported by elements of the cavalry squadron (RSTA) or other ISR assets, have the superior tactical mobility to conduct pursuit operations against those enemy forces fleeing the AO.
a. Indicators of the Enemy's Collapse. Friendly forces in the exploitation are alert for indicators of an enemy collapse that would permit a pursuit operation. There are several indicators of a weakening enemy:
- Continued advance without strong enemy reaction.
- An increased number of captured prisoners, abandoned weapons, and unburied dead.
- A lessening of enemy artillery fire.
- A lack of enemy countermeasures.
b. Initiating a Pursuit. The pursuit is ordered when the enemy force can no longer maintain its position and tries to escape. The commander exerts unrelenting pressure to keep the enemy force from reorganizing and preparing its defenses. The SBCT may be a part of a higher headquarters, functioning as either the direct-pressure or encircling force. The commander organizes and conducts pursuit operations by designating subordinate commands to produce the effects of a direct pressure force and an encircling force.
(1) Direct Pressure Force. The mission of a direct-pressure force is to prevent enemy disengagement and subsequent reorganization of the defense and to inflict the most casualties. Leading elements contain or bypass small enemy pockets of resistance that are then reduced by follow-and-support units. At every opportunity, the direct pressure force envelops, cuts off, and destroys enemy elements, provided such actions do not interfere with its primary mission. The enemy is not allowed to break contact.
(2) Encircling Force. The mission of an encircling force is to get behind the enemy and block his escape so that he can be destroyed between the direct-pressure and encircling forces. The encircling force advances along or flies over routes paralleling the enemy's line of retreat to reach defiles, communication centers, bridges, and other key terrain ahead of the enemy main force. When conditions permit, the SBCT attempts a double envelopment of retreating enemy main forces or their subordinate elements. Enemy rear guards or forces on flank positions are not permitted to divert the main force from its mission. If the encircling force cannot outdistance the enemy, it attacks the enemy main body on its flank. If the enemy's main force establishes itself on a position from which it cannot be easily dislodged, the pursuing commander launches an attack to restore fluidity. The SBCT commander should consider augmenting the encircling force with ISR assets such as UAVs and remote-sensing systems. The cavalry squadron (RSTA)'s HUMINT capability should be augmented from the SBCT's MICO to conduct "pursuit" operations when enemy forces are attempting to blend into the civilian population.
c. Control Measures. The commander uses control measures to retain his tactical options to converge on the most important axis or to redirect his pursuit effort on a new axis. These control measures should be flexible and capable of rapid adjustments to reflect changing conditions. For an example of control measure used during pursuit operations refer to Figure 4-6. Centralized planning and decentralized execution characterize the pursuit. The commander balances the need to prevent fratricide with the need to allow his battalion commanders the ability to take advantage of fleeting opportunities.
Figure 4-6. Pursuit control measures.
d. Fires and Effects. Fire and effects assets are placed well forward with the lead elements of the direct-pressure force. Such positioning facilitates the delivery of fire and effects support for both the direct-pressure and encircling force. Fires and effects assets perform two key tasks in the pursuit: slowing the retreat of enemy forces and preventing resupply and reinforcement of enemy force fires. CSS assets should follow the direct-pressure force to enhance its security. During a pursuit, the SBCT may also serve as a higher headquarters follow-and-support force. (See Paragraph 4-12 on exploitation.)
Section IV. OFFENSIVE PLANNING CONSIDERATIONS
The SBCT's unique ISR and the capability to access higher echelon database to retrieve information may alter the manner in which it actually plans, prepares for, and executes an attack and may result in some unique planning considerations (Figure 4-7).
Figure 4-7. Planning considerations.
4-14. FORCE ORGANIZATION
The commander task-organizes forces within the SBCT after he chooses a scheme of maneuver. The task organization allocates sufficient combat power to allow subordinate units to accomplish their assigned purposes. The structure of the SBCT and its INFOSYS reduces the number of unknowns and allows the task organization to be tailored to meet the specific threat.
a. The cavalry squadron (RSTA) primarily executes reconnaissance and surveillance for the SBCT. In instances where the enemy situation remains vague, additional forces are allocated to assist in the reconnaissance effort. The ISR assets of the MICO may be attached to or operate in direct support of the cavalry squadron (RSTA) to facilitate the reconnaissance effort. The S2x section, under the direction of the SBCT S2, has access to higher intelligence collectors and is able to garner those capabilities to help in the ISR effort. When the enemy mounts an effective security zone that denies the cavalry squadron (RSTA) the ability to provide the tactical information that the SBCT commander needs to make decisions during execution, he may direct an infantry battalion to conduct a movement to contact or limited attacks through the enemy security zone. From the SBCT commander's perspective, these operations constitute a reconnaissance-in-force and feed sufficient information to build a level of understanding needed to facilitate decision-making by the commander and obtain decisive combat action.
b. Across the full spectrum of conflict, the SBCT commander carefully considers security force requirements. Unlike an MTW, an SSC will rarely have clearly defined flanks and rear areas. Forces must be allocated to protect critical assets within the SBCT AO against conventional and unconventional attacks. Force organization reduces the amount of dedicated security through a COP and mutual support. Additionally, the cavalry squadron (RSTA) and other ISR assets will provide passive security through the conduct of their operations.
c. The SBCT can conduct both linear and nonlinear operations within contiguous or noncontiguous areas of operations. The mounted speed of the subordinate units within the SBCT allows the SBCT to conduct nonlinear operations while maintaining the ability to provide mutual support. This flexibility allows the SBCT to conduct battalion-level operations against multiple objectives within the SBCT's areas of operation.
d. The SBCT commander has greater latitude in the designation and composition of his reserve. Reserves should be designated at appropriate levels to address unforeseen events. The amount of combat power allocated to the reserve depends primarily on the level of uncertainty about the enemy. The increased ability of the SBCT to gain a better degree of understanding about the enemy should allow the commander to tailor the reserve to meet the specific threats and opportunities. At times the situation may allow the SBCT to retain only a small, but tailored, force as the reserve because there is little likelihood of catastrophic failure or all of the infantry battalions are conducting significant operations simultaneously. At other times, the SBCT commander may determine that his degree of SU allows him to tailor subordinate forces to a level that will ensure their success and therefore he does not designate a reserve.
4-15. INTELLIGENCE, SURVEILLANCE, AND RECONNAISSANCE
Intelligence, surveillance, and reconnaissance is a broad category of assets designed to support planning, intelligence development, decision-making, and targeting. The ISR effort is a combined-arms maneuver operation that employs the cavalry squadron (RSTA) and other ISR assets to observe, by visual or other detection methods, NAIs and TAIs in order to collect data, information, or combat information. Intelligence encompasses the products shared on the COP and in databases, as well as the processes used to collect, process, and analyze data and relevant information. Surveillance involves the systematic observation of a particular NAI by visual, electronic, photographic, or other means. Target acquisition by specialized and non-specialized ISR assets provides detection, identification, and location of targets in sufficient detail to permit the effective employment of fires and effects.a. The increased capabilities of the SBCT in intelligence acquisition and rapid precision fires and effects dictate that ISR assets be tightly integrated into a single operation to facilitate mission accomplishment.
b. The S2 integrates IPB and other MDMP products into his analysis of all intelligence and information coming into the main CP from the cavalry squadron (RSTA), other ISR assets, and higher echelon intelligence assets and databases. The S2 attempts to answer the PIR, recommends refined PIR for the commander to consider, confirms probable enemy COAs and intentions, and explains enemy actions in relationship to the current friendly operation. The product of this process is available on a shared database facilitating the ability of the SBCT commander and his subordinate commanders to make timely and effective decisions regardless of their location on the battlefield. Ultimately, reconnaissance and surveillance operations set the conditions for the success of the unit in the close fight.
c. The SBCT conducts reconnaissance and surveillance using organic and supporting HUMINT and technical assets. The data, information, and combat information collected from these assets, when combined with intelligence provided by the higher echelon assets, help the SBCT commander visualize a nearly complete picture of the enemy and environment within the SBCT's battlespace. Specifically, the SBCT employs an appropriate number of its ISR assets throughout its AO in order to identify favorable terrain and determine the enemy's composition, disposition, activities, strengths, and possible vulnerabilities.
d. The INFOSYS allow information to be passed from the cavalry squadron (RSTA) and other ISR assets to decision-makers and targeting cells in a timely manner. The ISR order (and collection plan) is published early in the MDMP process (not later than WARNO2), with sufficient enemy detail and operational coordination to focus the SBCT's ISR effort. This information allows the SBCT to—
- Seize and maintain the initiative.
- Develop and disseminate effective maneuver and fires and effects plans prior to contact.
- Detect, identify, and destroy high payoff targets early.
- Allow follow-on forces to maneuver rapidly, and without obstruction, to the objective.
- Keep uncommitted forces available as long as possible in preparation for action at decisive points.
- Recognize and exploit fleeting opportunities presented by discovered enemy weaknesses.
- Share a common operational picture.
- Reduce the risk of surprise by enemy operations.
4-16. INTELLIGENCE, SURVEILLANCE, AND RECONNAISSANCE FUNDAMENTALS
Successful ISR operations depend on the following fundamentals:
- Maintain a continuous ISR effort.
- Focus ISR assets on answering PIR and or IR.
- Integrate the staff in ISR planning.
- Maximize ISR assets.
- Collect, process, and disseminate information rapidly and accurately.
a. Maintain a Continuous ISR Effort. Reconnaissance and surveillance is a continuous process. In order to accomplish this, the employment of reconnaissance and surveillance forces and or assets needs to be cycled to provide for continuous reconnaissance and surveillance and rest and maintenance periods. ISR assets are normally not held in reserve. However, with the increase in ISR assets available to the SBCT, commanders must give consideration to their mission, duration, rest, resupply, and subsequent mission requirements. When the SBCT does not have adequate organic resources to achieve or sustain the required reconnaissance and surveillance effort, it requests integration of other ISR assets from division, corps, joint task force, and national systems to cover areas, or time periods, when assistance is needed.
b. Focus ISR Assets on answering PIR and IR. The PIR identifies the critical enemy information needed by the commander to support his battlefield visualization and decision-making. The PIR and the staff's IR provide focus to the collection plan and prevent the wasteful employment of ISR assets. The PIR filter information available to the commander and support his decisions that will affect overall mission accomplishment. The IR are requirements for intelligence to fill a gap in the commander's knowledge and understanding of his battlespace. In addition to the PIR, there will also be higher commander's PIR and subordinate units' IR that may influence the focus of the SBCT's collection plan. The collection plan should focus on collection of information to support the PIR and provide observation of the decision points on the battlefield. The increase in the number of ISR collection assets available to the SBCT increases the importance of a focused and synchronized collection plan. The amount of data and information gained from the increased number of assets may quickly overwhelm the S2 section with superfluous reports that prevent relevant information from getting to the decision makers in a timely manner. Focusing the reconnaissance and surveillance effort ensures that only the PIR and specific IR are answered; therefore, ISR collection assets are not wasted looking for information that is not relevant to the commander's decisions.
c. Integrate the Staff in ISR Planning. The S2 and S3 rely upon the entire staff to assist in the planning and execution of reconnaissance and surveillance by providing—
- Subject matter expertise.
- ISR assets.
- CS and CSS support.
- Communications, connectivity, and information management planning.
- IR submissions.
d. Maximize ISR Assets. The SBCT maximizes the capabilities of its ISR assets by ensuring that collection requirements specify what needs to be collected, where it needs to be collected, who collects it, and when it needs to be collected and reported in order for the SBCT to successfully accomplish the mission. The cavalry squadron (RSTA) and other ISR assets compliment each other with their different capabilities. For example, a joint surveillance target attack radar system (JSTARS) may have gaps in its area coverage because of terrain features that interrupt line of sight. Once these gaps are identified, they are covered by another asset such as a UAV. Each asset's strength compensates for another asset's weakness. Cross-cueing—using one system to trigger another—is a way to maximize the capabilities of ISR assets. JSTARS only indicates that something is moving. This indication may trigger the employment of a UAV to positively identify the target.
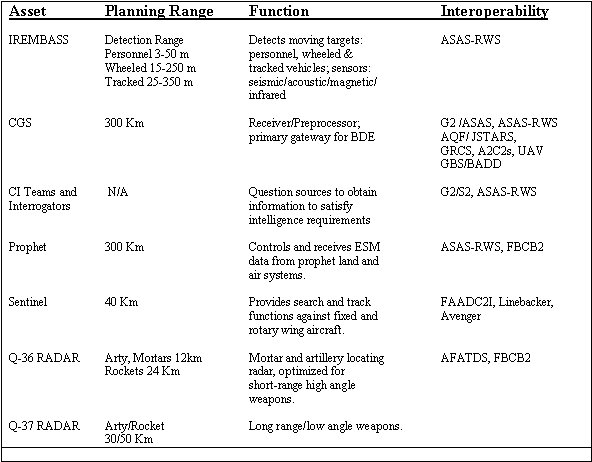
e. Collect, Process, and Disseminate Information Rapidly and Accurately. The INFOSYS within the SBCT enhance both the accuracy of the intelligence collected and the timeliness with which it can be processed and disseminated. Once data or information arrives at the collection manager, it is processed and disseminated to users such as the SBCT commander, key staff officers, and the fires and effects coordination cell. This is accomplished through the INFOSYS. Combat information goes directly (unprocessed) to the SBCT commander for his consideration. In order to conduct reconnaissance and surveillance continuously, the SBCT supplements its organic ISR collection assets with intelligence from higher headquarters and additional maneuver, fires and effects, or force protection assets. These assets provide the SBCT with a variety of options to draw upon, each with its own capabilities. Table 4-1 shows the ISR collection assets that are generally direct support to an SBCT.
Table 4-1. ISR collection assets.
4-17. SCHEME OF MANEUVER
The SBCT directs its decisive operation (or main effort) against an objective, ideally an enemy weakness, to cause the collapse of the enemy. By doing so, the SBCT sustains the initiative and reduces its own vulnerabilities. The SBCT commander seeks to identify an assailable flank, poorly defended avenue of approach, or a smaller unit lacking mutual support that he can exploit to gain a tactical advantage. When attacking a well-prepared enemy defense, the commander normally plans to isolate, then destroy, vulnerable portions of the enemy defense throughout the depth of the zone of attack.
a. The commander and staff develop the plan using a reverse planning process from actions on the objective to the assembly area. They incorporate plans for exploiting success and unforeseen opportunities that may develop during execution. Emphasis is placed on synchronizing maneuver, fires and effects, and support throughout the reconnaissance and surveillance effort and the attack. Reconnaissance and surveillance facilitates maneuver, allowing combat forces to move on specific routes to objectives, without significant enemy contact. The composition, disposition, and strength of the enemy force drive the type of attack that the SBCT conducts (see Paragraph 4-11).
b. The staff considers the enemy's ability to mass combat power, reposition his forces, or commit his reserve. The SBCT develops a scheme of maneuver to mass sufficient combat power to defeat the enemy. The reverse planning process is an essential tool in building an effective plan to attack an enemy. By starting with actions on the objective and working back to the assembly area, the staff can allocate combat power, mobility assets, and fires and effects (suppression and smoke).
4-18. FIRES AND EFFECTS
The fires and effects coordination cell obtains guidance from the commander regarding the effects desired in time, space, and purpose within the AO; it then plans, coordinates, and achieves the desired effects utilizing organic and attached assets.
a. The integration of fires and effects within the SBCT includes lethal indirect and direct fire systems and non-lethal effects.
(1) Infantry battalion and cavalry squadron (RSTA) mortars provide the majority of obscuration and indirect fires to these elements while the artillery battalion provides fires and effects to the SBCT.
(2) Non-lethal effects include IO, CA, computer network attack/defense (CNA/D), and legal support of civil-military operations. Information operations include OPSEC, EW, PSYOP, military deception, counterpropaganda, and possibly the destruction of infrastructure.
b. The nature of restrictive and urban terrain presents some special considerations. The ability to direct and observe fires and effects within isolated compartments of restrictive and urban terrain is required down to the platoon. Minimum engagement ranges are as important as maximum ranges.
c. Considerations for the fires and effects plan include—
- Movement of the fires and effects assets to enable destruction and or engagement of HPTs.
- Movement of the fires and effects assets to support the reconnaissance and surveillance effort.
- Location and employment of combat observation lasing terams (COLTs) to facilitate precision fires and effects.
- Using deception fires to confuse the enemy as to the location of the decisive operation (or main effort).
- Planning suppressive and obscuring fires and effects at the point of penetration.
- Planning suppressive and obscuring fires and effects in support of breaching operations.
- Planning fires and effects in support of the approach to the objective. These fires engage enemy security forces, destroy bypassed enemy forces, and screen friendly movement.
- Synchronizing fires on the objective to suppress, neutralize, or destroy enemy forces that most affect the SBCT's movement to the objective.
- Planning targets to attack repositioning enemy forces and the movement of enemy reserves.
- Planning fires and effects beyond the objective to support an attack or defense.
- Using fires and effects, or CAS, to delay or neutralize enemy reserves.
- Planning locations of critical friendly fire zones (CFFZs) to protect critical assets such as support forces, breaching efforts, and artillery assets.
- Planning to secure counterfire radars.
- Planning for desired effects on civilian populations
- Planning to break the enemy's will to fight through lethal and non-lethal effects.
Section V. SBCT SUPPORTING A HIGHER HEADQUARTERS
The effective employment of the SBCT with both mechanized and light forces or a JTF headquarters requires detailed and coordinated planning and an understanding of the SBCT's capabilities and limitations. The SBCT may be part of a division, corps, or JTF decisive operation or main effort. However, it is more likely to execute an attack as part of a higher headquarters shaping operation, act as a reserve, conduct economy-of-force operations, or (if attached to a mechanized force) conduct offensive operations in restrictive or urban terrain while other elements operate in open and somewhat unrestricted terrain. A higher headquarters has many options on how to employ an attached SBCT. For more information on the integration of heavy and light forces, refer to Appendix E, Integration of Special Operations, Mechanized, and Light Forces.
4-19. BOS PLANNING CONSIDERATIONS
The SBCT commander must be ready to advise the higher commander how to best employ his force. Critical areas in the planning process include the command and support relationship, the composition of the CS and CSS support, and the effective use of terrain. A common SOP or understanding of each unit's SOP is essential to the synchronization of combat, CS, and CSS units.
a. Intelligence. Given the significant capabilities of its ISR assets, the SBCT can expect to detach elements of the cavalry squadron (RSTA) or MICO to the higher headquarters. The SBCT commander should brief the higher commander that this may degrade the expected capabilities of the SBCT. Unless supporting a digitized force, the SBCT must provide the supported headquarters with a robust LNO command and control package. The J3/G3 must consider the capabilities of the SBCT in severely restricted terrain and urban areas. The J2/G2 must recommend to the higher commander as PIR the enemy assets or intentions that are particularly dangerous to the SBCT. Reconnaissance and surveillance plans should be developed jointly between the SBCT and the higher headquarters. When working with higher headquarters that are not yet digitized, the SBCT commander must plan for a different tempo and possibly more physical contact with the enemy when developing plans in conjunction with that force.
b. Maneuver. Mechanized forces are better suited for unrestricted than restricted terrain. The SBCT retains this same mobility; however, with a larger number of infantrymen, it provides the versatility to fight in restrictive and severely restrictive terrain (much like a light force) where enemy mobility is limited and long-range precision fires are muted.
(1) The SBCT does not have the protection requisite to fight and maneuver against armored opponents in unrestricted terrain. The higher commander must consider that it is possible to move (infiltration or air assault) the SBCT infantry battalions so far that the SBCT begins to lose the characteristics that make the SBCT commander uniquely able to share a COP, gain SU, and make decisions. While some of the SBCT has a limited ability to take components of the INFOSYS across the forward line of own troops (FLOT) during infiltrations and air assault operations, the SBCT will function in a degraded mode. Aerial retransmission of voice and data must be redundant and carefully planned and coordinated. Similarly, the higher commander must consider the nature of the objective and the duration of the operations that take the SBCT's forces away from their Stryker vehicles and sustaining bases for lengthy periods of time. The SBCT will require resupply of ammunition and batteries within 48 hours of crossing the FLOT.
(2) The digital INFOSYS capability also presents a challenge. The SBCT will know the location of its subordinate elements and have an unprecedented level of clarity on enemy forces within the AO. Analog units working with the SBCT provide the requisite lethality, protection, and sustainment but may not be able to tie into the INFOSYS, thereby degrading the SBCT. The SBCT commander and staff must aggressively query analog units for information so as not to degrade the tempo of information flow, mission planning, and execution of combat tasks. These units will require LNO teams with INFOSYS to communicate information with the SBCT.
(3) The SBCT cannot fight comparably sized mechanized and or armor forces in open rolling terrain. The SBCT antitank company provides a limited antiarmor capability to the SBCT. The SBCT will require augmentation if intended to fight a comparably sized mechanized and or armor force. This augmentation will likely take the form of an armor or mechanized task force that incorporates tank, antitank, engineers, and mechanized infantry elements.
(4) The cavalry squadron (RSTA) may be required to screen or conduct reconnaissance and surveillance against an armored threat. This may require augmentation of the cavalry squadron (RSTA) with antiarmor systems, a robust fires and effects element, or armored and or mechanized forces.
(5) Aviation augmentation from JTF, corps, or division is required to conduct air assault operations, assist in casualty evacuation, support attacks, and conduct reconnaissance and surveillance. (See Appendix F, Aviation Support of Ground Operations.) The augmenting aviation force should have the capability to move one infantry company in one lift, provide extensive antiarmor protection across the AO, extend the range of reconnaissance, and expand considerably the SBCT's flexibility. It could also add a countermobility capability by distributing air-delivered mine fields. Aviation augmentation will normally be OPCON for a specific duration and then return to the higher headquarters' control.
c. Fires and Effects. The SBCT may detach all or part of the artillery battalion to participate in the higher headquarters' fires and effects plan. If the SBCT is required to conduct an attack, the higher commander must recognize that the cavalry squadron (RSTA) and other ISR assets will precede the ISR effort, and that effort must be supported by a detailed and synchronized fires and effects plan.
(1) The SBCT is vulnerable to artillery fires. The higher headquarters' fires and effects plan must prioritize the suppression of those systems that threaten the SBCT during its employment in an attack.
(2) The SBCT may receive fires and effects augmentation from the higher headquarters. Augmentation may be in the form of reinforcing field artillery, additional target acquisition capabilities, or a higher priority of fires, especially for the conduct of proactive counterfire or to support SBCT offensive operations. Assured linkages to plan and employ joint fires and information operations capabilities will enhance the SBCT commander's ability to shape the battlespace.
d. Air Defense. The SBCT ties into the higher headquarters' air defense plan via the ADAM cell, equipped with the air and missile defense work station (AMDWS), in the main CP. Since the SBCT has no active air defense capabilities beyond point defense with its Stryker self-defense weapons and its crew-served weapons, it would require coverage from the higher unit's air defense assets. When employing attached air defense assets within the SBCT AO, the commander ensures their effects afford redundant protection of those key INFOSYS nodes necessary for successful mission accomplishment. It is essential that the attached ADA assets are tied into the SBCT's INFOSYS to ensure that they enhance the fidelity of the COP by sharing information provided from their related ADA BOS COP.
e. Mobility, Countermobility, and Survivability. The SBCT must plan to receive engineer augmentation when part of a mechanized force. The SBCT's mechanical breaching assets are best suited for obstacles associated with the situations in an SSC. The light force commander, with his limited engineering capability, may not augment the SBCT. However, a higher commander must consider that breaching or gap crossing by the SBCT will take time, and he should provide the appropriate level of support in order to maintain the correct tempo of the overall force.
(1) Additional engineer capabilities across all engineer battlespace functions will be required—mobility, countermobility, survivability, reconnaissance, and sustainment support. In essence, engineer augmentation will require an engineer battalion (versus the organic company) that can be task-organized to provide improved direct support to maneuver elements and to accomplish the other significant engineer tasks inherent within an offensive operation. (Refer to FM 3-34-221 for additional information.) Augmentation requirements include improvement in general engineering, engineer reconnaissance, terrain visualization, and expanded staff support at SBCT and battalion levels. Engineer augmentation will be provided from the higher headquarters and its employment integrated by the MANSPT cell. In a linear battlefield, engineers do not typically perform general engineering tasks while in the offense. However, in a non-contiguous environment, engineers could perform tasks across the full spectrum of operations, to include general engineering.
(2) The SBCT likely will be augmented by an MP company that is capable of expanding capabilities for area security; EPW operations; police intelligence operations; route, logistical, and physical security; counterreconnaissance; crowd control; law and order; and criminal investigation. A smoke and decontamination company with a biological detection platoon will be required to add capabilities for thorough fixed-site decontamination; large area, long duration obscuration; biological detection and early warning; and expanded nuclear, biological, and chemical (NBC) reconnaissance.
f. Command and Control. The SBCT and higher headquarters must exchange LNO teams. Analog units lack the capabilities inherent in the C2 INFOSYS. When the higher headquarters is analog, the SBCT commander must account for a requirement to physically locate with the higher headquarters throughout the planning. There will be greater demands on the SBCT commander and his staff to physically attend meetings and briefings that will affect the normal battle rhythm of the SBCT. Detailed briefbacks are required at the SBCT level of attached analog combat, CS, and CSS units to ensure timing, synchronization, and understanding of intent. The SBCT commander and commanders and staffs of analog units must understand the capabilities and limitations of the other's units and their command and control systems. The S6 from each unit ensures connectivity and interoperability during combined arms operations. An exchange of unit tactical and digitized SOPs and signal operating instructions (SOI) must occur immediately on attachment.
g. Combat Service Support. The BSB will require comprehensive augmentation from JTF, division, or corps across all functional areas of support. The CSS augmentation package will need to be tailored to overcome SBCT sustainment requirements for a variety of systems and vehicles not resident within the higher headquarters' logistics structure, an expanded area of operations, potentially higher operational tempo, and probable requirements to establish direct support with maneuver elements.
4-20. FLANK GUARD
The SBCT can secure an exposed flank for an attacking force in restrictive terrain by clearing severely restricted areas or small urban areas along the axis of advance. In the same vein, the SBCT can secure key terrain that dominates a mechanized or light force's approaches to the objective. This utilization of the SBCT in a large-unit attack frees the mechanized or light force commander from drawing on any of his maneuver forces and limited number of infantrymen required on the objective. It also allows the mechanized force to maintain a fast tempo during movement, giving the defender less time to react and synchronize. For the SBCT, this would still be an attack. The SBCT is uniquely manned and equipped to fight in such terrain, thus providing the higher commander with a force that is optimized for this type of mission. The SBCT's tactical mobility allows it to easily join the mechanized force at a later point in the operation if required to do so.
4-21. SECURE KEY TERRAIN
The SBCT can secure choke points and clear restrictive terrain astride the mechanized force's axis of advance. Conducting such operations in restricted terrain is both time consuming and resource intensive. Higher commanders must account for the time and resources required as the SBCT approaches the AO, clarifies the situation, and conducts attacks. Higher commanders must also ensure that the SBCT has sufficient combat power to successfully accomplish the mission. The SBCT's ability to conduct this type of mission facilitates the unimpeded advance of mechanized forces during their movement.
a. The SBCT may conduct an infiltration in order to secure key terrain, interrupt enemy lines of communication, or destroy a high payoff target. The SBCT has an adequate amount of infantrymen and firepower to infiltrate and attack. The information-gathering capability of the cavalry squadron (RSTA) and other ISR assets provide critical information necessary to successfully conduct an infiltration. This form of maneuver is a viable option for the mechanized force commander to employ the SBCT due to the ability of the SBCT's infantry forces to infiltrate (mounted or dismounted) during hours of limited visibility and communicate adjustments to the tactical plan through the INFOSYS.
b. The SBCT can also conduct an air assault operation to seize key terrain. An air assault gives a commander the ability to position forces deep when no feasible infiltration (mounted or dismounted) routes are available and there is a need to attack a target quickly in severely restricted terrain. As with the infiltration, the cavalry squadron (RSTA) and other ISR assets give the SBCT the ability to gather timely and accurate data and information on a far objective and then establish observation posts around the objective during execution. This allows the infantry battalions to focus on the objective knowing that adequate early warning through the ISR assets is available.
4-22. CONDUCT FOLLOW-AND-SUPPORT
The SBCT can conduct follow-and-support missions with a mechanized or light force. This allows the mechanized or light force the tactical freedom to bypass small pockets of resistance and maintain the momentum of the operation with the assurance that its lines of communication are secure. Consequently, the mechanized or light force can focus on its subsequent objectives during an exploitation or pursuit. The cavalry squadron (RSTA) and other ISR assets give the SBCT the unique ability to observe multiple NAIs and routes, thus providing the SBCT and higher commander with an unprecedented degree of fidelity of their COP regarding isolated or bypassed enemy units. The mounted speed and firepower of the infantry battalions provide the necessary tactical flexibility to focus or refocus combat power as the situation is clarified by the cavalry squadron (RSTA) and other ISR assets.
4-23. MAIN EFFORT IN THE ATTACK
The SBCT can be the main effort for a mechanized force when the objective is in an urban area or when it is in terrain that severely restricts employment of combat vehicles. The mechanized force would serve as a supporting force to isolate the objective area and augment the SBCT as needed. The ability of the SBCT to support itself in close operations throughout the depth of the AO and its strong infantry force make the SBCT the best choice to conduct an attack against an enemy defending in restrictive or urban terrain. The SBCT can also be the main effort for a light force when the objective is distant and the terrain favors the mobility of the Stryker platforms within the organization. The light force may infiltrate or conduct an air assault operation to isolate the objective area or augment the SBCT as needed.
4-24. COUNTERATTACK IN THE DEFENSE
The SBCT can be an effective force for use as a counterattack. The SBCT's tactical mobility and INFOSYS enable it to react quickly and decisively when called upon to execute a counterattack in support of a defense. The SBCT is best used in such a role in situations that maximize its strengths. The best example of where a commander might dedicate an SBCT as a counterattack force is in restrictive terrain (urban or complex) where the enemy situation appears fluid. Such a situation allows the SBCT to employ its ISR assets to clarify the situation as the enemy attacks and then move the infantry battalions rapidly through terrain that appears severely restrictive to a position of advantage. In this manner, the SBCT is able to gain tactical surprise against the enemy force and achieve a decisive result in favor of its higher headquarters. The SBCT can also be effective in less restrictive terrain, but its lack of antiarmor protection and organic mobility and countermobility assets prevents it from truly maximizing its strengths.
4-25. CONDUCT FOLLOW-AND-ASSUME AS AN EXPLOITATION OR PURSUIT FORCE
In certain situations the SBCT is well suited to follow and assume the mission of either a heavy or light force. While a higher commander rarely dedicates a force to exploit or pursue, he can direct his staff to plan such an offensive operation as a branch or sequel.
a. By placing an SBCT in the follow-and-assume role, the commander can easily direct efforts to either a pursuit or exploitation. Additionally, based on the SBCT's ISR capability, the SBCT commander is better able to identify an enemy force preparing to withdraw or regroup. Once the commander identifies those conditions, the SBCT can rapidly move forward and either begin a pursuit (in the case of a withdrawing enemy) or continue an exploitation (if the enemy defenses have been broken). The SBCT commander can then move his infantry battalions out of direct contact with the enemy to either seize key terrain or to strike an enemy force as it attempts to conduct a retrograde. In either case, the SBCT is able to maintain constant pressure on the enemy through mobility and enhanced fidelity of its common operational picture of the enemy and terrain through its organic INFOSYS.
b. The SBCT is best suited to conduct these operations in more restricted areas. A withdrawing or broken enemy can use restricted terrain to regroup and prepare its defenses. The SBCT's infantry battalions are well equipped to assault these positions before they are well established. In open and rolling terrain, the SBCT may be challenged to generate the combat power required to maintain a pursuit or exploitation if the enemy is able to position heavy forces in well-prepared defenses. In that case, the higher commander should augment the SBCT with additional combat power (armor, mechanized infantry, artillery support, CAS) in order to maintain offensive pressure or choose to establish defensive positions until he is able to get his other units forward to continue the mission. As the SBCT continues to exert pressure on the enemy, the higher commander can transition his other units and prepare them to continue the offense once the SBCT has culminated.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|