CHAPTER 4
OFFENSIVE OPERATIONS
The SBCT infantry rifle company has great flexibility due to its organic mobility and robust infantry organization. While retaining its light infantry ethos and warfighting capability, it can move faster and farther and can react rapidly to changes in the tactical situation. Thus, this unit is not constrained by the time-space problem that has historically faced the light infantry.
Section I. GENERAL PLANNING CONSIDERATIONS
The outcome of decisive combat derives from offensive actions. All operations are designed to transition to and support the offense. Only through offensive actions can the company accomplish its primary mission--to close with the enemy by means of fire and maneuver to destroy or capture him, or to repel his assault by fire, close combat, and counterattack. A sound doctrinal foundation during offensive planning assists the commander in capitalizing on the increased tactical flexibility of the SBCT infantry rifle company.
4-1. CHARACTERISTICS OF THE OFFENSE
Traditionally, the characteristics of the offense include surprise, tempo, concentration, and audacity. Due to the nature of modern offensive operations and the digital capabilities of the SBCT company, however, flexibility has been added to the following discussion of the offense. The SBCT infantry rifle company commander must master both analog and digital capabilities. This dual capability provides the flexibility necessary to glean the benefits of digital while retaining the ability to transition rapidly to analog to continue the offense in case of a disruption in digital capability. The commander decides how to apply the following characteristics for each mission.
a. Surprise. Units achieve surprise by striking the enemy at a time, at a place, or in a manner for which he is unprepared. Total surprise rarely is essential; simply delaying or disrupting the enemy's reaction usually is effective.
(1) Surprise delays the enemy's reactions, stresses his command and control, and induces psychological shock in his soldiers and leaders. This may allow an attacker to succeed with fewer forces than might otherwise be required.
(2) The company's abilities to attack during limited visibility, to operate in small units, and to infiltrate are often key to achieving surprise. The company must exploit the effect of surprise on the enemy before he can recover.
b. Tempo. Tempo is the rate of speed of military action. Controlling or altering that rate is essential for maintaining the initiative. Speed promotes surprise, keeps the enemy off balance, contributes to the security of the attacking force, and prevents the defender from taking effective countermeasures.
(1) Properly exploited, speed confuses and immobilizes the defender until the attack becomes unstoppable. Leaders build speed into operations through careful planning.
(2) The company increases its speed through its ability to transition rapidly from moving mounted to moving as light infantry by using simple plans, decentralized control, and mission orders. Speed of movement depends on reconnaissance, reducing the soldiers' loads, using proper movement formations and techniques, and selecting good routes for both mounted and dismounted movement. In the case of dismounted movement, ICVs allow soldiers to shed loads down to fighting loads. Companies develop SOPs to facilitate their transition from mounted movement to dismounted movement.
c. Concentration. The attacker concentrates combat power at the decisive points and times to achieve the unit's purpose. Leaders strive to concentrate the effects of their combat power without concentrating forces.
(1) Because the attacker often moves across terrain the enemy has prepared, he may expose himself to the enemy's fires. By concentrating overwhelming combat power at an area or system that is weak, the attacker can reduce both the effectiveness of enemy fires and the amount of time he is exposed to these fires.
(2) The challenge for the company commander is to concentrate combat power while reducing the enemy's ability to do the same against his unit. Actions that cause the enemy to shift combat potential away from the intended decisive point result in a greater advantage in combat power where and when the commander needs it most. The commander must consider employing his mounted and light infantry capabilities to achieve overwhelming combat power at the decisive point.
d. Audacity. Audacity is the willingness to risk bold action to achieve positive results. The audacious commander develops confidence by conducting a thorough estimate. His actions, although quick and decisive, are based on a reasoned approach to the tactical situation and on his knowledge of his soldiers, the enemy, and the terrain. He is daring and original, but he is not rash.
(1) Audacious commanders throughout history have used the "indirect approach." They maneuver to maintain a position of advantage over the enemy, seek to attack the enemy on the flank or rear, and exploit success at once, even if this briefly exposes their own flanks.
(2) Boldness and calculated risk have always been the keystones of successful offensive operations. They must, however, be consistent with the higher commander's mission and intent.
e. Flexibility. Given the increased capabilities of the SBCT infantry rifle company, the commander has much greater flexibility with this new organization and should plan on maximizing it in planning and execution. At some point in most attacks, the original plan must be adjusted to meet changes in the situation. Mission orders and competent subordinate leaders who exercise initiative ensure the proper adjustments are made.
(1) The commander must expect uncertainties and be ready to exploit opportunities. The flexibility required often depends on the amount of reliable intelligence the commander has on the enemy.
(2) The commander builds flexibility into his plan during the decision-making process. By conducting a thorough wargame, he develops a full appreciation for possible enemy actions. A reserve increases the company commander's flexibility. However, given the SBCT infantry company's organization and increased situational understanding through the COP, its reserve may be smaller than in strictly light and heavy units.
4-2. TYPES OF OFFENSIVE OPERATIONS
The four types of offensive operations, described in FM 3-90, are movement to contact, attack, exploitation, and pursuit. Companies can execute movements to contact and attacks. Platoons generally conduct these forms of the offense as part of a company or larger unit operation. Companies and platoons participate in a higher unit's exploitation or pursuit. The nature of these operations depends largely on the amount of time and enemy information available during the planning and preparing for the operation phases.
a. Movement to Contact. The movement to contact (MTC) is a type of offensive operation designed to develop the situation and establish or regain contact. The company may conduct an MTC on its own or as part of a larger unit's operation when the enemy situation is vague or not specific enough to conduct an attack. (For a detailed discussion of MTC refer to Section VI.)
b. Attack. An attack is an offensive operation that destroys enemy forces or seizes or secures terrain. Movement, supported by fires, characterizes the conduct of an attack. The company likely will participate in a synchronized attack. However, a company may conduct a special purpose attack as part of, or separate from, an offensive or defensive operation. Special purpose attacks consist of ambush, spoiling attack, counterattack, raid, feint, and demonstration. (For a detailed discussion of attack and special purpose attacks refer to Sections V and VII.)
c. Exploitation. Exploitations are conducted at the battalion level and higher. The objective of exploitation is to complete the destruction of the enemy following a successful attack. Companies and platoons may conduct movements to contact or attacks as part of a higher unit's exploitation.
d. Pursuit. Pursuits normally are conducted at the brigade or higher level. A pursuit typically follows a successful exploitation and is designed to prevent a fleeing enemy from escaping and to destroy him. Companies and platoons will participate in a larger unit's exploitation and may conduct attacks as part of the higher unit's operation.
4-3. FORMS OF MANUEVER
Given the typical sequence for offensive operations (refer to Section II), the company maneuvers against the enemy in an area of operation. Maneuver places the enemy at a disadvantage through the application of friendly fires and movement. The five forms of maneuver are:
|
a. Envelopment. Envelopment (Figure 4-1) is a form of maneuver in which an attacking force seeks to avoid the principal enemy defenses by seizing objectives to the enemy rear or flank in order to destroy him in his current positions. "Flank attacks" are a variant of envelopment in which access to the enemy's flank and rear results in enemy movement. A successful envelopment requires discovery or creation of an assailable flank. The envelopment is the preferred form of maneuver because the attacking force tends to suffer fewer casualties while having the most opportunities to destroy the enemy. Envelopments focus on:
|
Figure 4-1. Envelopment.
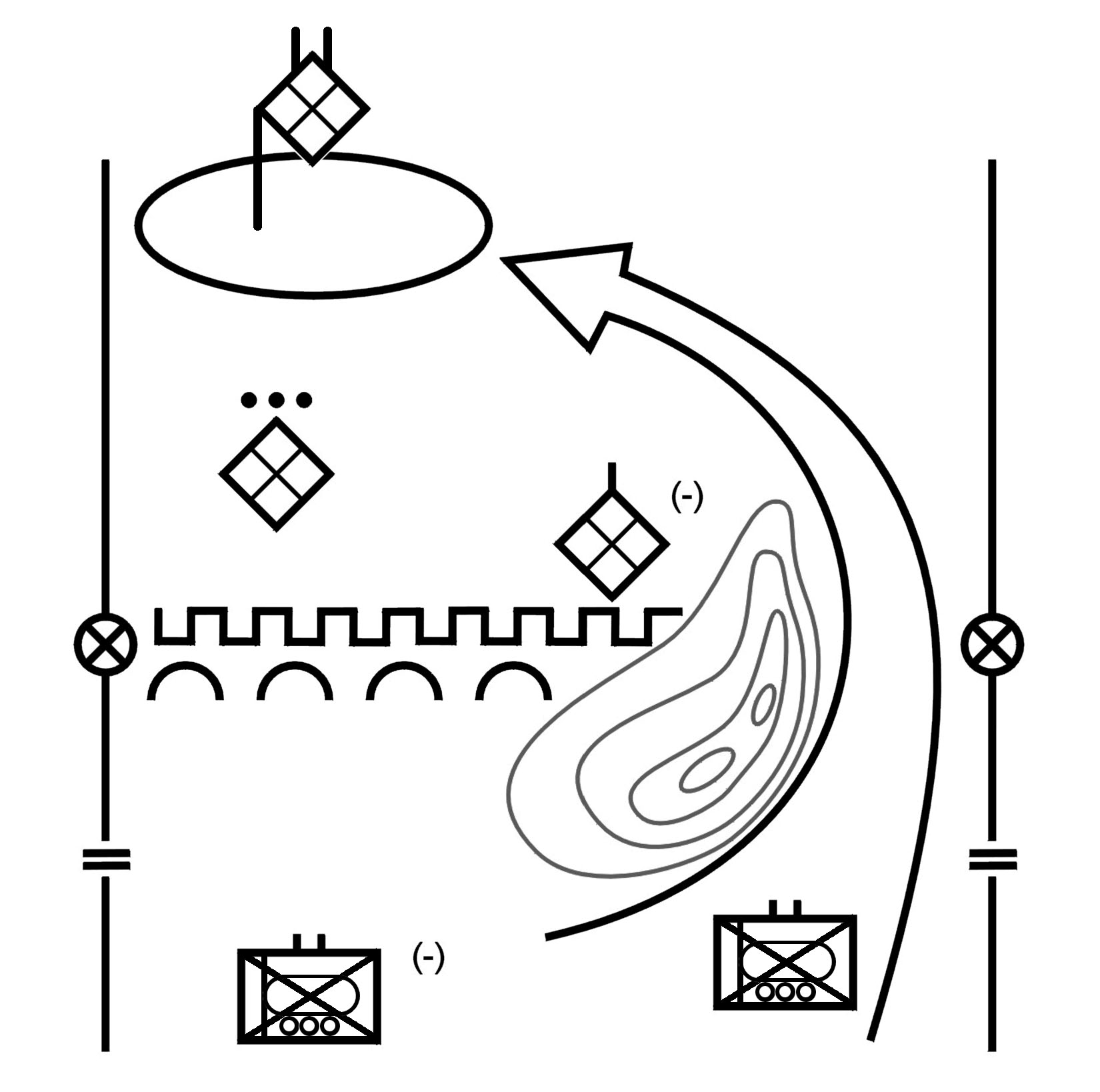
b. Turning Movemen.. Turning movement (Figure 4-2) is a form of maneuver in which the attacking force seeks to avoid the enemy's principal defensive positions by seizing objectives to the enemy's rear and causing the enemy to move out of his current positions or to divert major forces to meet the threat. For a turning movement to be successful, the unit trying to turn the enemy must attack something that the enemy will fight to save. This may be a supply route, artillery emplacement, or a headquarters. In addition to attacking a target that the enemy will fight to save, the attacking unit should be strong enough to pose a real threat to the enemy. The turning movement is a type of envelopment in which the attacker attempts to avoid the defense entirely. Instead, he seeks to secure key terrain deep in the enemy's rear and along his lines of communication. Faced with a major threat to his rear, the enemy is thus "turned" out of his defensive positions and forced to attack rearward. The company will likely conduct a turning movement as part of a battalion supporting an SBCT attack.
|
NOTE: |
Turning movement differs from envelopment in that the force conducting the turning movement seeks to make the enemy displace from his current location whereas an enveloping force seeks to engage the enemy in his current location from an unexpected direction. |
Figure 4-2. Turning movement.
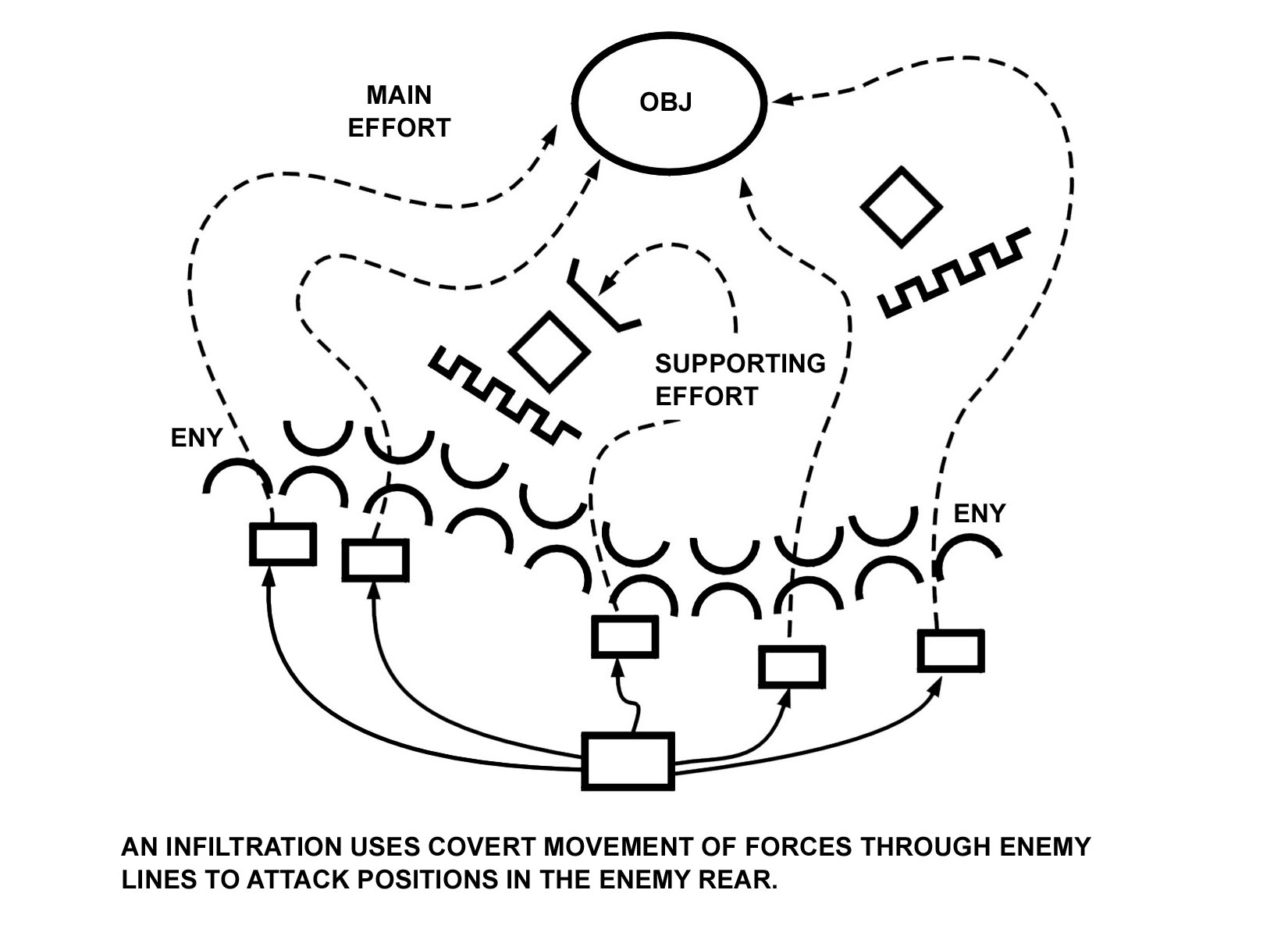
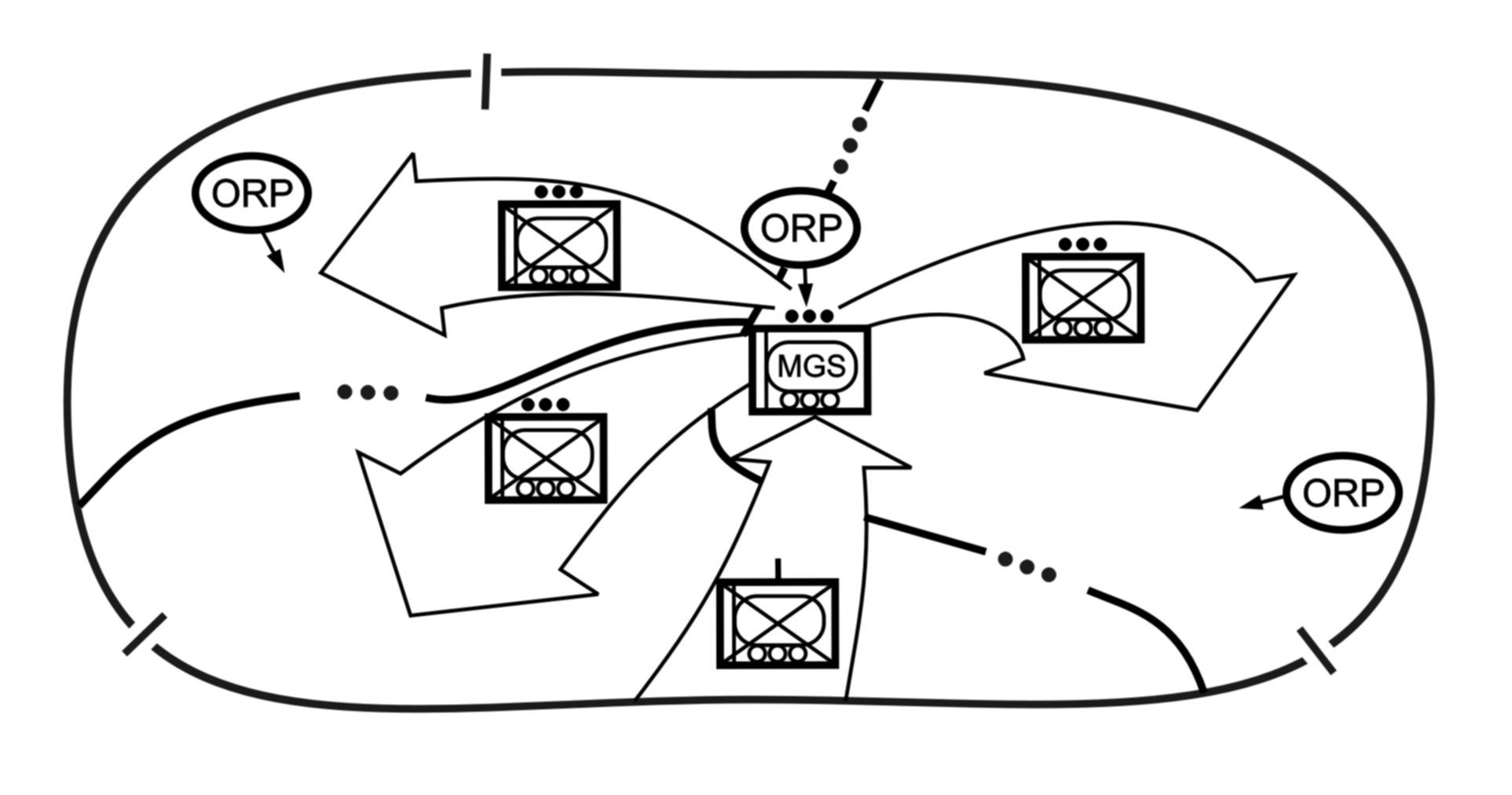
c. Infiltration. Infiltration (Figure 4-3) is a form of maneuver in which an attacking force conducts undetected movement through or into an area occupied by enemy forces to occupy a position of advantage in the enemy rear while exposing only small elements to enemy defensive fires. Moving and assembling forces covertly through enemy positions takes a considerable amount of time. A successful infiltration reaches the enemy's rear without fighting through prepared positions. An infiltration is normally used in conjunction with and in support of another form of maneuver. A company may conduct an infiltration (dismounted or mounted) as part of a larger unit's attack with the battalion employing another form of maneuver. The company commander also may employ maneuver by infiltration to move his platoons to locations to support the battalion's attack. SBCT infantry companies are well suited for infiltrations due to their mobility, positional awareness, COP, and small signature when moving dismounted. A company may conduct an infiltration in order to--
|
Figure 4-3. Infiltration.
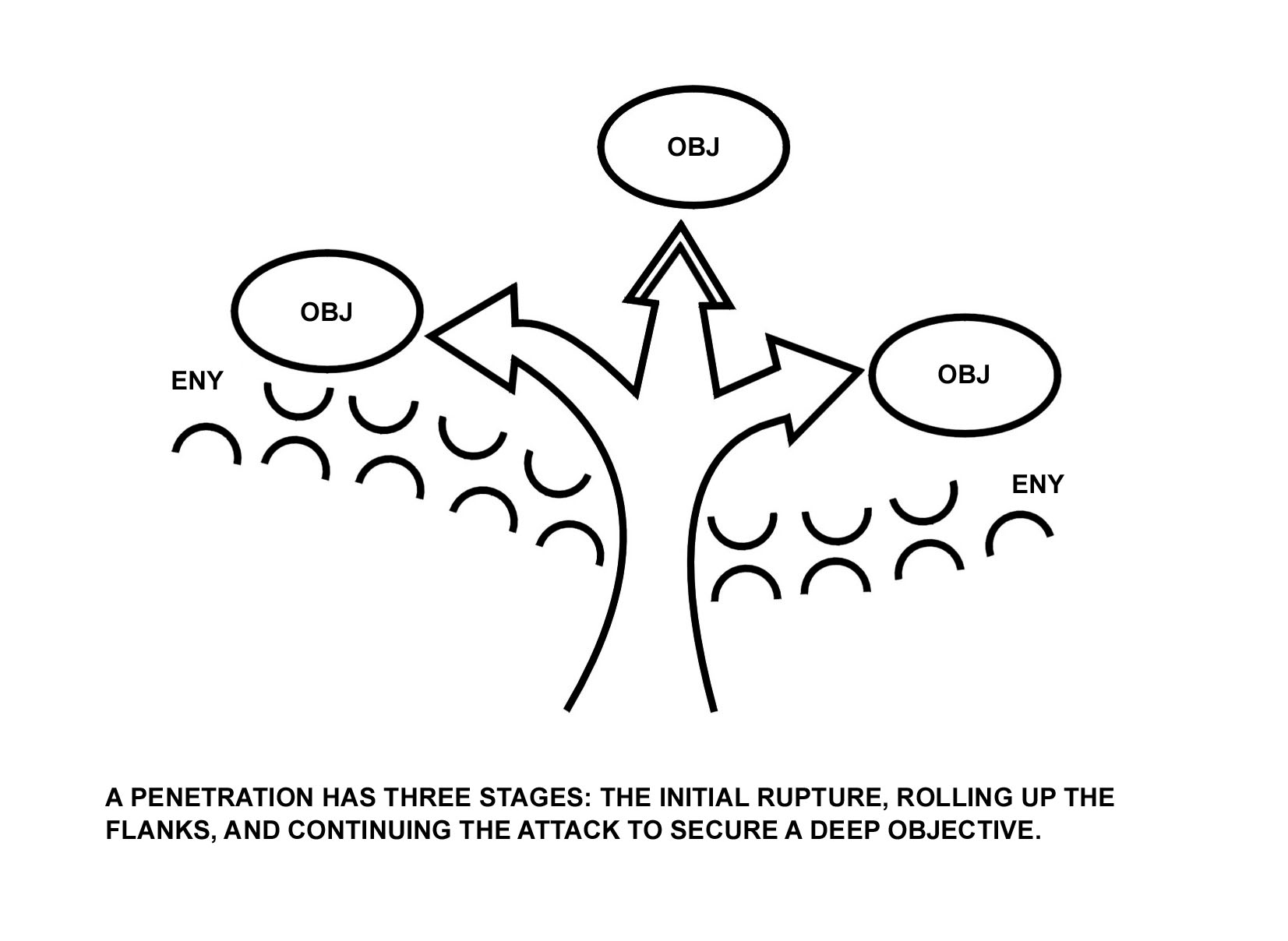
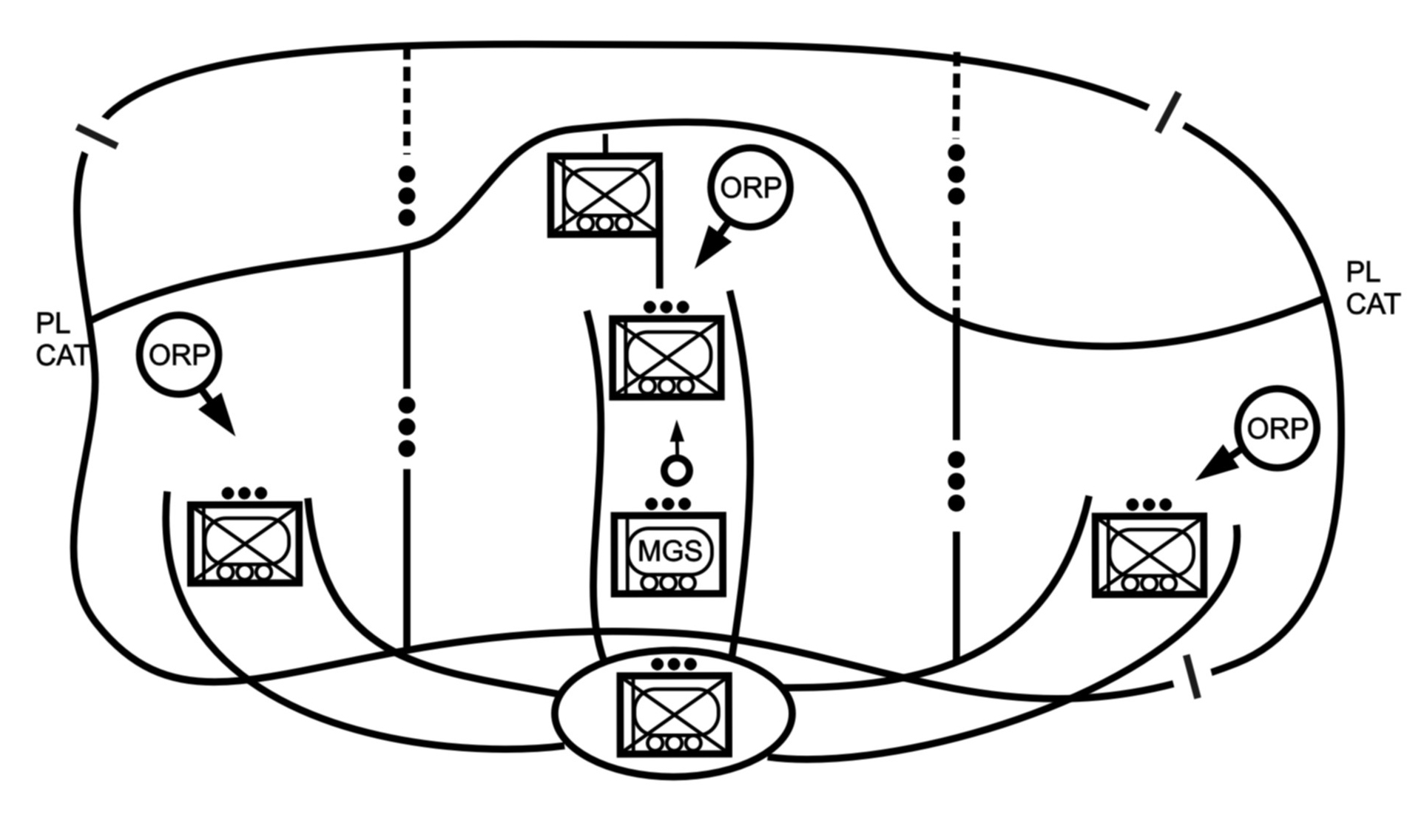
d. Penetration. Penetration (Figure 4-4) is a form of maneuver in which an attacking force seeks to rupture enemy defenses on a narrow front to create both assailable flanks and access to the enemy's rear. Penetration is used when enemy flanks are not assailable, when enemy defenses are overextended, when weak spots in the enemy defense are identified, and when time does not permit some other form of maneuver. A penetration normally consists of three steps:
|
As part of a larger force penetration, the company will normally isolate, suppress, fix, or destroy enemy forces, breach tactical or protective obstacles in the enemy's main defense, secure the shoulders of the penetration, or seize key terrain. A battalion may also use the penetration to secure a foothold within a large built-up area.
Figure 4-4. Penetration.
e. Frontal Attack. Frontal attack is a form of maneuver in which an attacking force seeks to destroy a weaker enemy force or fix a larger enemy force along a broad front. It is the least desirable form of maneuver because it exposes the attacker to the concentrated fire of the defender and limits the effectiveness of the attacker's own fires. However, the frontal attack is often the best form of maneuver for an attack in which speed and simplicity are key; it is useful in overwhelming weak defenses, security outposts, or disorganized enemy forces.
Section II. SEQUENCE OF OFFENSIVE OPERATION
As the company commander plans for an offensive mission, he generally considers the following sequence of events that apply to many, but not all, offensive operations.
|
4-4. ASSEMBLY AREA
The commander directs and supervises mission preparations in the assembly area to prepare the company for the upcoming battle. Preparation time also allows the company to conduct precombat checks and inspections, rehearsals at all levels, and CSS activities. Given the communications capabilities of the company, the commander may conduct on-the-move planning to hasten his attack. (See Appendix G, Road Marches and Assembly Areas, for more information.)
4-5. RECONNAISSANCE
All echelons should conduct reconnaissance. The enemy situation and available planning time may limit the unit's reconnaissance, but leaders at every level must aggressively seek information about the terrain and enemy. Leaders must remember the benefits of having their soldiers on the ground providing real-time information, regardless of the information available via FBCB2. The on-the-ground company reconnaissance effort reports on enemy activity in the company's area of interest (AOI) near the LD, attack position (ATK PSN), assault position (ASLT PSN), or the company-assigned unit objective (OBJ). This provides the maneuver commander with the information needed to execute the best possible tactical plan.
4-6. MOVEMENT TO THE LINE OF DEPARTURE
When attacking from positions not in contact, rifle companies often stage in rear assembly areas, road march to ATK PSN behind friendly units in contact with the enemy, conduct passage of lines, begin the attack, and then move to their AOs. When necessary, the rifle company employs indirect fires, close air support (when available), and direct fire to facilitate its movement.
4-7. MANEUVER
Maneuver is the foundation for the employment of forces on the battlefield. It is defined as the use of movement in combination with fire (or fire potential), employed to achieve a position of advantage with respect to the enemy and to facilitate accomplishment of the mission. At the company level, maneuver is the essence of every tactical operation and task. When possible, the commander employs those techniques that avoid the enemy's strength and conceal the company's true intentions. He deceives the enemy as to the location of the main effort, uses surprise to take advantage of his initiative in determining the time and place of his attack, and uses indirect approaches, when available, to strike the enemy from a flank or the rear. The company commander maneuvers his platoons to close with the enemy, to gain positional advantage over him, and ultimately to destroy him or force him to withdraw or capitulate.
a. Base of Fire Force. The combination of fire and movement first requires a base of fire in which some elements of the company remain stationary and provide protection for the bounding forces by preventing the enemy from reacting to the bounding force.
(1) The base of fire force occupies positions that afford effective cover and concealment, unobstructed observation, and clear fields of fire. Once it is in position, the base of fire is responsible both for suppressing known enemy forces and for aggressively scanning assigned sectors of observation; it identifies previously unknown elements and then suppresses them. The protection provided by the base of fire force allows the bounding unit to continue its movement and to retain the initiative even when it is under enemy observation or within range of enemy weapons.
(2) Because maneuver is decentralized in nature, decisions on where and when to establish a base of fire must be made at the appropriate level. These decisions normally fall to a leader on a specific part of the battlefield who knows what enemy forces can engage the bounding force and what friendly forces are available to serve as the base of fire. At company level, these decisions may be made within the company (with the base of fire provided by a platoon), within platoons (with the base of fire provided by the weapons squad), or within squads (with a fire team as the base of fire).
b. Bounding Force. Movement in a maneuver situation is inherently dangerous. It is complicated not only by the obvious potential for harm posed by enemy weapons but also by the uncertainty caused by unknown terrain and other operational factors.
(1) The bounding force must take full advantage of whatever cover and concealment the terrain provides. Leaders can enhance security by enforcing use of intervening terrain and avoidance of skylining.
(2) All elements and or vehicle crews involved in the maneuver must maintain 360-degree security at all times. Elements in the bounding force must scan their assigned sectors of observation continuously.
(3) Although METT-TC factors ultimately dictate the length of the bounds, the bounding force should never move beyond the range at which the base of fire force can effectively suppress known, likely, or suspected enemy positions. This minimizes the bounding force's exposure to enemy fires.
(4) In severely restricted terrain, bounds are generally much shorter than in more open areas.
(5) If mounted, the bounding force may need to dismount infantry squads or individual crewmen to observe intervening gaps or dead space. Although this usually causes the platoons to make a tactical pause, it does not slow the operation as much as would the loss of a squad or vehicle and crew to a hidden enemy antitank system.
(6) The bounding element must remain focused on its ultimate goal of gaining a positional advantage, which it then can use to destroy the enemy by direct and indirect fires.
4-8. DEPLOYMENT
As a unit deploys and moves toward the assault position, the unit begins the final positioning of its forces so the company can pass through the assault position with minimum delay and confusion. This tactical positioning allows units the opportunity to continue to "flow" the force in its best tactical posture through the ASLT PSN into the attack. Movement should be as rapid as the terrain, force mobility, and enemy situation permit. The probable line of departure is the next control measure following the attack position and represents the point at which the force is fully committed to offensive action.
4-9. ASSAULT
During offensive operations, the unit remains enemy- and effects-oriented; however, based on the factors of METT-TC, the company's objective may be terrain- or force-oriented. Terrain-oriented objectives require the SBCT infantry rifle company to seize and retain a designated area and often require fighting through enemy forces. If the objective is force-oriented, an objective area may be assigned for orientation, but the company's effort is focused on the enemy's actual location. The enemy may be a stationary or moving force. Actions on the objective start when the company begins placing fires on the objective; this normally occurs when the commander initiates his echelonment of fire onto the objective.
4-10. CONSOLIDATION AND REORGANIZATION.
The company consolidates and reorganizes as required by the situation and mission. Consolidation is the process of organizing and strengthening a newly captured position so that it can be defended. Reorganization is the actions taken to shift internal resources within a degraded unit to increase its level of combat effectiveness. The company executes follow-on missions as directed by the SBCT battalion commander. A likely mission is to continue the attack against targets of opportunity in the objective area. Whether a raid, hasty attack, or deliberate attack, a company must posture itself and prepare for continued offensive operations.
Section III. PLANNING CONSIDERATIONS
The battlefield operating systems (BOS) are a listing of critical tactical activities that provides a means of reviewing preparation and execution. Synchronization and coordination among the BOS are critical for success. Selected BOS and other planning considerations are addressed in this section. For a detailed discussion of Command and Control and Intelligence, refer to Chapter 2.
4-11. FIRE SUPPORT
As part of the top-down fire planning system, the company commander must refine the fire plan from higher headquarters to meet his mission requirements. He incorporates the results of his METT-TC analysis and makes key locations and targets from the fire plan an integral part of the company rehearsal. Additionally, he works with the FSO to develop a corresponding observation plan and establishes triggers for initiating or shifting fires. The company commander and the FSO must have a thorough understanding of organic fire support elements and traditional artillery support assets. The majority of the company's fire support is from mortar systems organic to the SBCT infantry battalion and company. The commander employs supporting fires in the offense to achieve a variety of tactical goals:
|
4-12. MOBILITY, COUNTERMOBILITY, AND SURVIVABILITY
The SBCT battalion may task-organize the company with engineers as part of a breaching operation in the offense. The company commander normally receives additional mobility assets, such as an engineer platoon. If attached to heavy forces, it can also receive equipment suited for mounted mobility, such as mine clearing line charges (MICLICs), or armored combat earthmovers, based on METT-TC. Refer to FM 90-13-1 and FM 90-7 for a detailed discussion of mobility and survivability operations and support, and FM 3-34.2 for a detailed discussion of breaching operations.
4-13. AIR DEFENSE
Avengers or mounted Stinger sections may be attached, with organic vehicle support, to travel with the company. Their security must be a consideration in planning for offensive operations. The company commander must plan for and rehearse internal air security and active air defense measures. SOP normally dictates ADA requirements and procedures. The commander must anticipate possible contact with enemy air assets by templating enemy helicopter and fixed-wing air corridors and avenues of approach. Unit SOPs should dictate internal air security measures and active air defense measures.
4-14. COMBAT SERVICE SUPPORT
The main purpose of combat service support in the offense is to assist maneuver elements in maintaining the momentum of the attack. In the offense, CSS functions are performed as far forward as the tactical situation allows. Company trains remain one terrain feature behind the location of the company vehicles when the company has dismounted and is moving forward on foot. The commander must consider the enemy situation and how it relates to the security of the company trains. If the company is conducting decentralized operations, the company trains locate where they can best support the platoons in the accomplishment of the company's mission. The ICVs and medical evacuation team move forward to the objective area to evacuate casualties and conduct resupply. If necessary, the supply sergeant also can move forward to assist with sustainment operations. The company CP reports the company's combat status to the SBCT battalion and requests resupply as needed. Key CSS planning considerations for company offensive operations include the following:
|
4-15. AVIATION
The SBCT does not have organic or assigned helicopter support, but the SBCT infantry company commander must have a good understanding of aviation employment capabilities in case the company is supported by these assets. Refer to Chapter 10 for a detailed discussion of Army aviation support.
a. Reconnaissance. Like their ground-based counterparts, air reconnaissance operations obtain information by visual observation and other detection methods. They must have the ability to develop the situation, process the information, and provide it to the commander in near real time. The company commander, through the battalion, can take advantage of the supporting aviation element's AH-64 Apache helicopters to dramatically improve his 24-hour reconnaissance capability. Under favorable conditions, they can furnish early information concerning the enemy's general disposition and movements to considerable depth beyond the forward line of troops.
b. Security. Aviation assets can extend the company's security area, providing the commander with battle-tracking capability. They can expand the company's maneuver space, provide additional reaction time, and assist in protection of the company.
c. Attack. The primary purpose of attack helicopter operations is the destruction of enemy ground forces at decisive points in close operations. Helicopters are normally most effective when used en masse in continuous operations on the enemy's flanks and rear. Night operations are preferred.
d. Support by Fire. When assigned a support-by-fire mission, attack helicopters establish a base of fire or overwatch position. They then can engage enemy targets while SBCT infantry elements move to or bypass the target area. The helicopters' role may range from suppression to complete destruction of the enemy force. Their most common mission is to fix targets so other friendly elements can maneuver.
e. Attack by Fire. When the enemy situation is vague, as in a movement to contact, and the attack helicopter battalion commander has been assigned his own sector, the commander may establish attack-by-fire positions. From these positions the attack helicopters engage their targets without maneuvering over them. The intent here is to inflict only a specified level of damage. Attack-by-fire positions are best suited to a fluid battlefield. The aviation commander often has the best vantage point from which to synchronize the combat multipliers, clear fires, and prevent fratricide.
f. Air Assault. SBCT forces should always consider the use of air assault to assist them in overcoming obstacles or restricted terrain during the seizure of critical terrain and in executing follow and support missions to preserve the momentum of the attack. The company can participate in an air assault to an objective, and the vehicles can be brought forward during consolidation and reorganization to resupply and prepare for upcoming missions. (Refer to FM 90-4 for a detailed discussion of air assault operations.)
g. Communications. All Army helicopters have SINCGARS radios and can transmit digital information to vehicles equipped to receive such data. While the radio is the primary means of tactical communications, face-to-face contact remains the best method of passing information between air and ground elements. Whenever the situation permits, aviation leaders should land their aircraft, link up with their ground counterparts (such as the company commander), and directly communicate the battlefield situation as gathered from the air.
h. Coordination. Aviation scout assets can easily identify enemy targets and then coordinate with the company FIST to facilitate destruction of the targets with direct and indirect fires. In addition, identifying friendly positions and planned movements during prior coordination between air and ground elements can eliminate a significant number of factors that contribute to fratricide, a vital concern during combined-arms missions.
4-16. INTEGRATION OF VEHICLES
The ICV is primarily a troop transport vehicle that provides increased mobility and tactical flexibility. The purpose of the vehicle is not to provide a substantial increase in firepower for the infantry close fight. However, if the terrain supports wheeled movement and the weapons systems can range the objective area, the commander can use the mounted weapons systems to augment the effects of direct and indirect fires. There are two basic concepts for augmentation fires: complementary and reinforcing. Complementary fires are fires that are different in nature from the "base" weapon system but increase the effects of that base system. For example, a commander may implement complementary fires by utilizing his MGS platoon, with flechette rounds, to increase the lethality of his dismounted suppression element in an attack. Reinforcing fires are additional fires that are similar to the base system but that increase the volume and, subsequently, the lethality of the base weapon system. For example, a commander may employ his mounted weapons systems from the ICVs to reinforce the dismounted suppression element in an attack. The following are employment options for the ICV in the offense:
|
Section IV. ACTIONS ON CONTACT
In both offensive and defensive operations, contact occurs when a member of the SBCT infantry company encounters any situation that requires an active or passive response to the enemy. These situations may entail one or more of the following forms of contact:
|
Leaders at echelons from platoon through battalion conduct actions on contact when they or a subordinate element recognizes one of the forms of contact or receives a report of enemy contact. The company may conduct actions on contact in response to a variety of circumstances, including the following:
|
4-17. DEVELOPING ACTIONS ON CONTACT
SBCT infantry company commanders and platoon leaders analyze the enemy throughout the troop-leading procedures to identify all likely contact situations that may occur during an operation. Through the planning and rehearsals conducted during troop-leading procedures, they develop, modify if necessary, and refine COAs to deal with probable enemy actions. Planning and rehearsals will, when conducted properly, reduce the planning to action time. The COAs eventually become the foundation for the company's scheme of maneuver. During the troop-leading process, the leaders must evaluate a number of factors to determine their impact on the unit's actions on contact. For example, the commander needs to consider how the likelihood of contact affects his choice of movement techniques and formations. By doing this, he can begin preparing the company for actions on contact; for example, he may outline procedures for the transition to more secure movement techniques before a contact situation.
4-18. TIME REQUIREMENTS FOR ACTIONS ON CONTACT
SBCT infantry commanders must understand that properly executed actions on contact require time at both platoon and company levels. To develop the situation fully, a platoon may have to execute extensive lateral movement, dismount and remount infantry squads, conduct reconnaissance by fire, and call for and adjust indirect fires. Each of these activities requires time. The commander must balance the time required for subordinate elements to conduct actions on contact with the need of the company or SBCT battalion to maintain tempo and momentum. In terms of slowing the tempo of an operation, however, the loss of a platoon is much more costly than the additional time required to allow the subordinate element to develop the situation properly.
4-19. THE FOUR STEPS OF ACTIONS ON CONTACT
The company should execute actions on contact using a logical, well-organized process of decision-making and action entailing these four steps:
|
The four-step process is not intended to generate a rigid, lockstep response to the enemy. Rather, the goal is to provide an orderly framework that enables the company and its platoons to respond to the initial contact and then to apply sound decision-making and timely actions to complete the operation. Ideally, the company will acquire the enemy before being sighted by the enemy; it then can initiate physical contact on its own terms by executing the designated COA.
a. Step 1, Deploy and Report. Events that occur during the first step of actions on contact depend in great measure on whether the contact is expected or unexpected. Regardless of whether contact is expected or unexpected, the first step of actions on contact concludes with the unit deployed (into base of fire and bounding forces), the enemy suppressed or destroyed, and the commander sending a contact report to SBCT battalion headquarters. The following discussion examines some of the variables the company commander faces in expected and unexpected contact situations and discusses the roles of platoon battle drills, SOPs, and reports.
(1) Expected Contact. If the commander expects contact, he will already have deployed the company by transitioning to the bounding overwatch movement technique. If the company is alert to the likely presence of the enemy, it has a better chance of establishing visual contact, and then physical contact, on its own terms before being detected by the enemy. An overwatching or bounding platoon usually makes visual or physical contact which initiates the company's actions on contact. In a worst-case scenario, the platoon may be engaged by a previously undetected (but expected) enemy element. In this event, the platoon in contact conducts a battle drill for its own survival and then initiates actions on contact.
(2) Unexpected Contact. In some cases, the company may make unexpected contact with the enemy while using traveling or traveling overwatch. The element in contact or, if necessary, the entire company may have to deploy using battle drills to survive the initial contact.
(3) Battle Drills. Battle drills provide virtually automatic responses to contact situations in which immediate, and in many cases violent, execution of an action is critical both to the unit's initial survival and to its ultimate success in combat. Drills are not a substitute for carefully planned COAs; rather, they buy time for the unit in contact and provide a framework for development of the situation. When contact occurs, the company's platoons deploy immediately, executing the appropriate battle drills under the direction of the commander. (For additional information on dismounted platoon battle drills, refer to FM 3-21.9 [FM7-5].)
(4) Maneuver Standing Operating Procedures. An effectively written, well-rehearsed maneuver SOP helps to ensure quick, predictable actions by all members of the company. The SOP, unlike platoon battle drills, allows leaders to take into account the friendly task organization, a specific enemy, and a specific type of terrain. Therefore, the SOP can assist the company in conducting actions on contact and maintaining the initiative in a number of battlefield situations.
(5) Reports. Timely, accurate, and complete reports are essential throughout actions on contact. As part of the first step of the process, the company commander must send a contact report to the SBCT battalion as soon as possible after contact occurs. He provides subsequent reports to update the situation as necessary.
b. Step 2, Evaluate and Develop the Situation. While the company deploys, the commander must evaluate the situation and, as necessary, continue to maneuver to develop it.
(1) The commander quickly gathers as much information as possible, either visually or, more often, through FBCB2 reports from the platoon(s) in contact. He analyzes the information to determine critical operational considerations, including these:
|
(2) After evaluating the situation, the commander may discover that he does not have enough information to identify the necessary operational considerations. To make this determination, he must further develop the situation in accordance with the SBCT battalion commander's intent, using a combination of these techniques:
|
(3) Once the commander has determined the size of the enemy force the company has encountered, he sends a report to the SBCT battalion.
c. Step 3, Choose a COA. After developing the situation and determining that he has enough information to make a decision, the company commander selects a COA that meets the requirements of the SBCT battalion commander's intent and is within the company's capabilities.
(1) Nature of Contact. The nature of the contact (expected or unexpected) may have a significant impact on how long it takes a commander to develop and select a COA. As an example, in preparing to conduct an attack the company commander determines that the company will encounter an enemy security observation post along its axis of advance. During troop-leading procedures, he develops a scheme of maneuver to defeat the outpost. When the company's lead platoon makes contact with the enemy, the commander can quickly assess that this is the anticipated contact and direct the company to execute his plan. On the other hand, unexpected contact with a well-concealed enemy force may require time for development of the situation at platoon level. As it "fights" for critical information that will eventually allow the commander to make a sound decision, the company may have to employ several of the techniques for developing the situation.
(2) COA Procedures. The company commander has several options in how he goes about the process of selecting a COA.
(a) If his development of the situation reveals no need for change, the company commander directs the company to execute the original plan.
(b) If his analysis shows that the original plan is still valid but that some refinement is necessary, the company commander informs the SBCT battalion commander (prior to execution, if possible) and issues a fragmentary order (FRAGO) to refine the plan.
(c) If his analysis shows that the original plan needs to be changed but that the selected COA will still comply with the SBCT battalion commander's intent, the company commander informs the battalion commander (prior to execution, if possible) and issues a FRAGO to re-task his subordinate elements.
(d) If his analysis shows that the original plan deviates from the SBCT battalion commander's intent and needs to be changed, the company commander must report the situation and, based on known information in response to an unforeseen enemy or battlefield situation, recommend an alternative COA to the SBCT battalion commander.
(e) If the battlefield picture is still vague, the company commander must direct the company or a platoon to continue to develop the situation. This will allow him to gather the information needed to clarify a vague battlefield picture. He then uses one of the first four options to report the situation, choose a COA, and direct further action.
d. Step 4, Execute the Selected COA. In executing a COA, the company transitions to maneuver. It then continues to maneuver throughout execution, either as part of a tactical task or as an advance while in contact, to reach the point on the battlefield from which it executes its tactical task. The company can employ a number of tactical tasks as COAs, any of which may be preceded and followed by additional maneuver. As execution continues, more information becomes available to the company commander. Based on the emerging details of the enemy situation, he may have to alter his COA during execution.
|
EXAMPLE: As the company maneuvers to destroy what appears to be a dismounted infantry platoon, it discovers two additional enemy platoons in prepared positions. The commander must analyze and develop the new situation. He then selects an alternate COA, such as establishing a support-by-fire position to support another company's maneuver against the newly discovered enemy force. |
Section V. COMPANY OFFENSIVE OPERATIONS
The company normally conducts offensive operations--attack, movement to contact, exploitation, and pursuit--as part of an SBCT battalion or larger element. (The company also may conduct these operations independently.) Movement to contact will be discussed in Section VI. This section examines the various roles the company may play in these operations and the tactics for conducting--
|
4-20. ATTACK CHARACTERISTICS
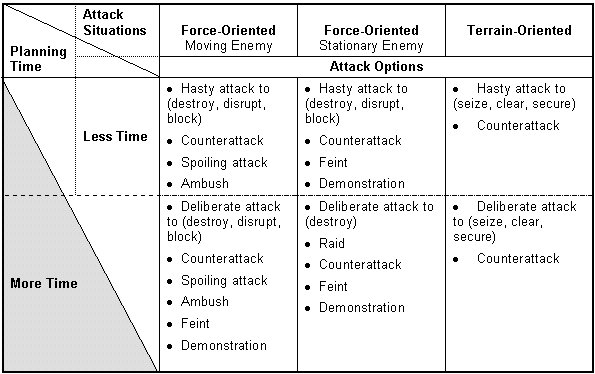
An attack is a type of offensive operation characterized by movement supported by fire. The purpose of an attack is to defeat an enemy force or to seize terrain. The company can attack independently or as part of an SBCT battalion or larger element. The two basic types of attack are the hasty attack and the deliberate attack (see paragraph 4-21). Figure 4-5, illustrates the situations under which a company conducts an attack, compares them to the amount of planning and preparation time required, and provides options for the commander to accomplish his purpose and support the higher commander's intent. All attacks, whether hasty or deliberate, depend on synchronization for success. They require planning, coordination via digital or analog means, and time to prepare.
a. The company commanders translate the mission assigned by the SBCT battalion, through analyzing the task and purpose, into specific missions for subordinate platoons and squads. To facilitate parallel planning, they immediately forward these missions digitally, along with the appropriate portions of the battalion's plans and orders, to subordinate platoons and squads. Commanders and platoon leaders must work together to develop the best plans; this requires sharing information freely between the command posts. The goal is not simply to reduce the time required to produce and distribute the plans, but, more importantly, to produce a better plan by including input from adjacent, higher, and lower elements. Additionally, this collaboration promotes understanding of the plan, thereby enhancing preparation and execution.
b. The information systems available to the SBCT infantry rifle company facilitate detailed planning. By properly leveraging digital systems and sensors, SBCT infantry company commanders can obtain near-real-time knowledge of enemy composition, locations, activity, and probable intentions. Thus, modern technology improves the company commander's ability to develop his COA and plan his actions against an enemy force from either stationary or moving C2 platforms.
c. As the company plans, the enemy also has time to improve his defenses, disengage, or conduct spoiling attacks of his own. Clearly, planning must be accomplished in the shortest time possible and must accommodate the changes driven by what the enemy does.
Figure 4-5. Spectrum of attacks.
4-21. HASTY AND DELIBERATE ATTACKS
Although having different forms based on their purposes, there is no clear distinction between deliberate and hasty attacks. The primary difference between the two is the extent of planning and preparation conducted by the attacking force. Attacks range along a continuum defined at one end by FRAGOs, which direct the rapid execution of battle drills by forces immediately available. These attacks rely on an implicit understanding and electronic communication with detailed orders and appropriate branches and sequels that make understanding explicit. Information on the general enemy situation comes from a movement to contact, and the company launches a hasty attack as a continuation of the meeting engagement. The hasty attack capitalizes on a temporary advantage in relative combat power and may preempt enemy actions. At the other end of the continuum, the company moves into a deliberate attack from a reserve position or assembly area with detailed knowledge of the enemy, a task organization designed specifically for the attack, and a fully rehearsed plan. Most attacks fall somewhere between these two ends of the continuum.
a. Hasty Attack. The commander may conduct a hasty attack during movement to contact, as part of a defense, or whenever he determines that the enemy is in a vulnerable position and can be quickly defeated by immediate offensive action. A hasty attack is used to--
|
Because its primary purpose is to maintain momentum or take advantage of the enemy situation, the hasty attack is normally conducted with only the resources that are immediately available. Maintaining unrelenting pressure through hasty attacks keeps the enemy off balance and makes it difficult for him to react effectively. Rapidly attacking before the enemy can act often results in success even when the combat power ratio is not as favorable as desired. With its emphasis on agility and surprise, however, this type of attack may cause the attacking force to lose a degree of synchronization. To minimize this risk, the commander should maximize use of standard formations; well-rehearsed, thoroughly understood battle drills and SOPs; and digital tools that facilitate rapid planning and preparation. By assigning on-order and be-prepared missions to subordinate companies as the situation warrants, the company is better able to transition into hasty attacks. The hasty attack is often the preferred option during continuous operations. It allows the commander to maintain the momentum of friendly operations while denying the enemy the time needed to prepare his defenses and to recover from losses suffered during previous action. Hasty attacks normally result from a movement to contact, successful defense, or continuation of a previous attack.
(1) Task Organization. The hasty attack is conducted using the principles of fire and movement. The controlling headquarters normally designates a base of fire force and a maneuver force.
(2) Conduct of the Hasty Attack. The company must first conduct actions on contact, allowing the commander to gather the information he needs to make an informed decision. The term "hasty" refers to limits on planning and preparation time, not to any acceleration in the conduct of actions on contact. Because the intelligence picture is vague, the commander normally needs more time, rather than less, during this process to gain adequate information about the enemy force.
(a) Execution begins with establishment of a base of fire, which then suppresses the enemy force. The maneuver force uses a combination of techniques to maintain its security as it advances in contact to a position of advantage. These techniques include, but are not limited to, the following:
|
(b) Once the maneuver force has gained the positional advantage, it can execute a tactical task, such as assault, to destroy the remaining enemy.
b. Deliberate Attack. The SBCT infantry rifle company conducts a deliberate attack only when the enemy's strength prevents it from conducting a hasty attack. It normally conducts a deliberate attack against a strong enemy defense. As the company prepares for the attack, the enemy also continues to strengthen his position. Deliberate attacks follow a distinct period of preparation, which is used for extensive reconnaissance and intelligence collection, detailed planning, task organization of forces, preparation of troops and equipment, coordination, rehearsals, and plan refinement. The deliberate attack is a fully synchronized operation that employs every available asset against the enemy defense. It is characterized by a high volume of planned fires, use of major supporting attacks, forward positioning of resources needed to maintain momentum, and operations throughout the depth of enemy positions. Thorough preparation allows the attacking force to stage a combined arms and fully integrated attack. Likewise, however, the enemy will have more time to prepare his defensive positions and integrate fires and obstacles. The factors of METT-TC dictate how thoroughly these activities are accomplished. The commander normally conducts a deliberate attack when enemy positions are too strong to overcome by a hasty attack. In weighing his decision to take the time required to prepare for and conduct the deliberate attack, he must consider the advantages that may be gained by both friendly and enemy forces.
(1) Task Organization. The SBCT company commander normally task-organizes the company into support and assault forces for conduct of a deliberate attack. He also designates a breach force if the company must conduct a breach as part of the attack. Specific duties of these elements are covered in the discussion of a company-level assault of a strongpoint and tactical tasks (paragraph 4-35).
(2) Conduct of the Deliberate Attack. The SBCT infantry company's deliberate attack normally is broken into the following steps:
(a) Attack in Zone. The attacking SBCT company advances to within assault distance of the enemy position under supporting fires and using any combination of movement techniques. Platoons advance to successive positions using available cover and concealment. The company commander may designate support by fire positions to protect friendly forces with suppressive direct fires. As the company maneuvers in zone, it employs lethal and nonlethal fires to suppress and obscure enemy positions.
(b) Actions at the Probable Line of Deployment (PLD). The PLD is normally a phase line or checkpoint where elements of the attacking company transition to secure movement techniques in preparation for contact with the enemy. Platoons may maneuver from the PLD to designated support-by-fire positions, assault positions, or breach or bypass sites. The PLD may be collocated with the assault position.
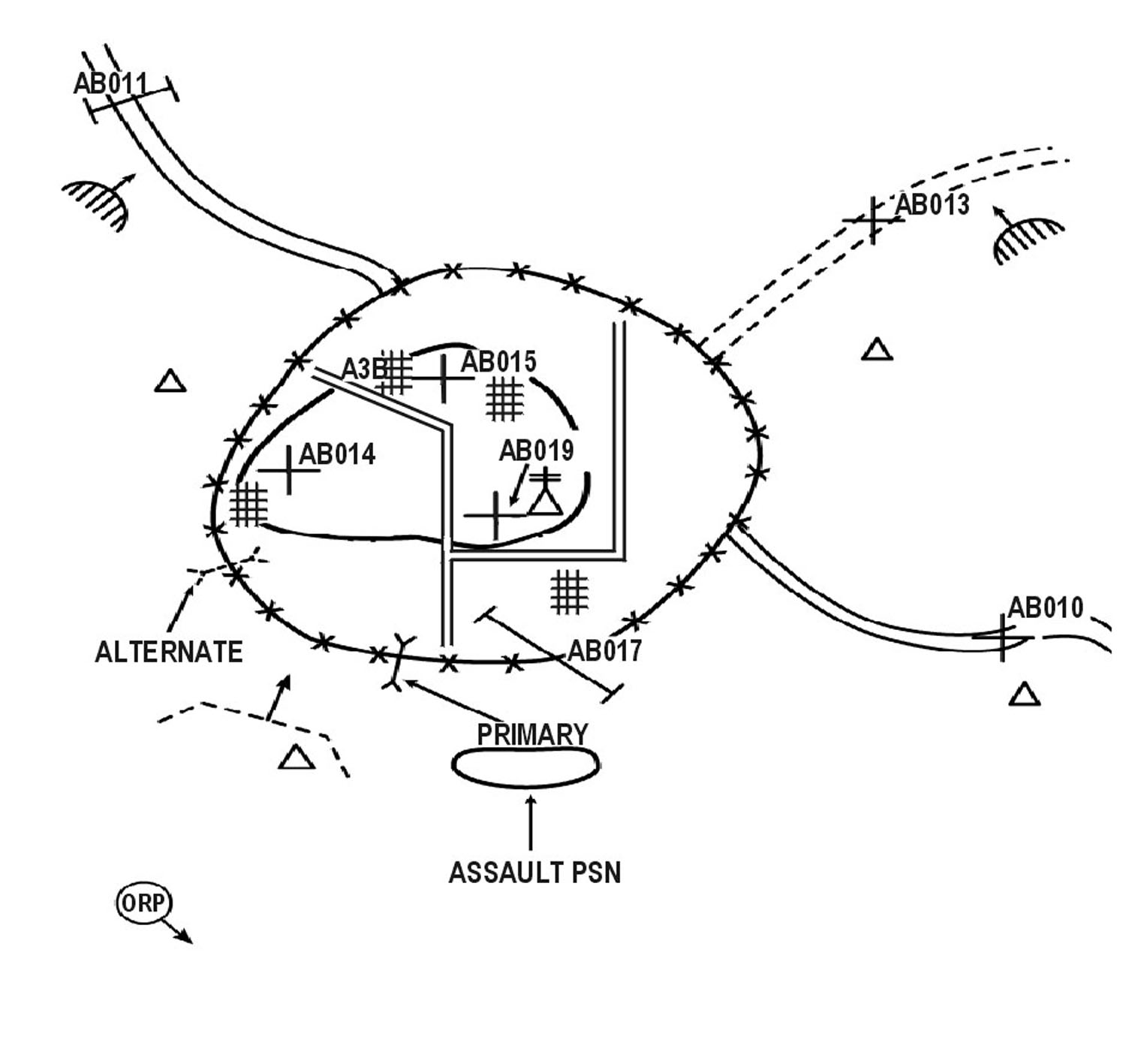
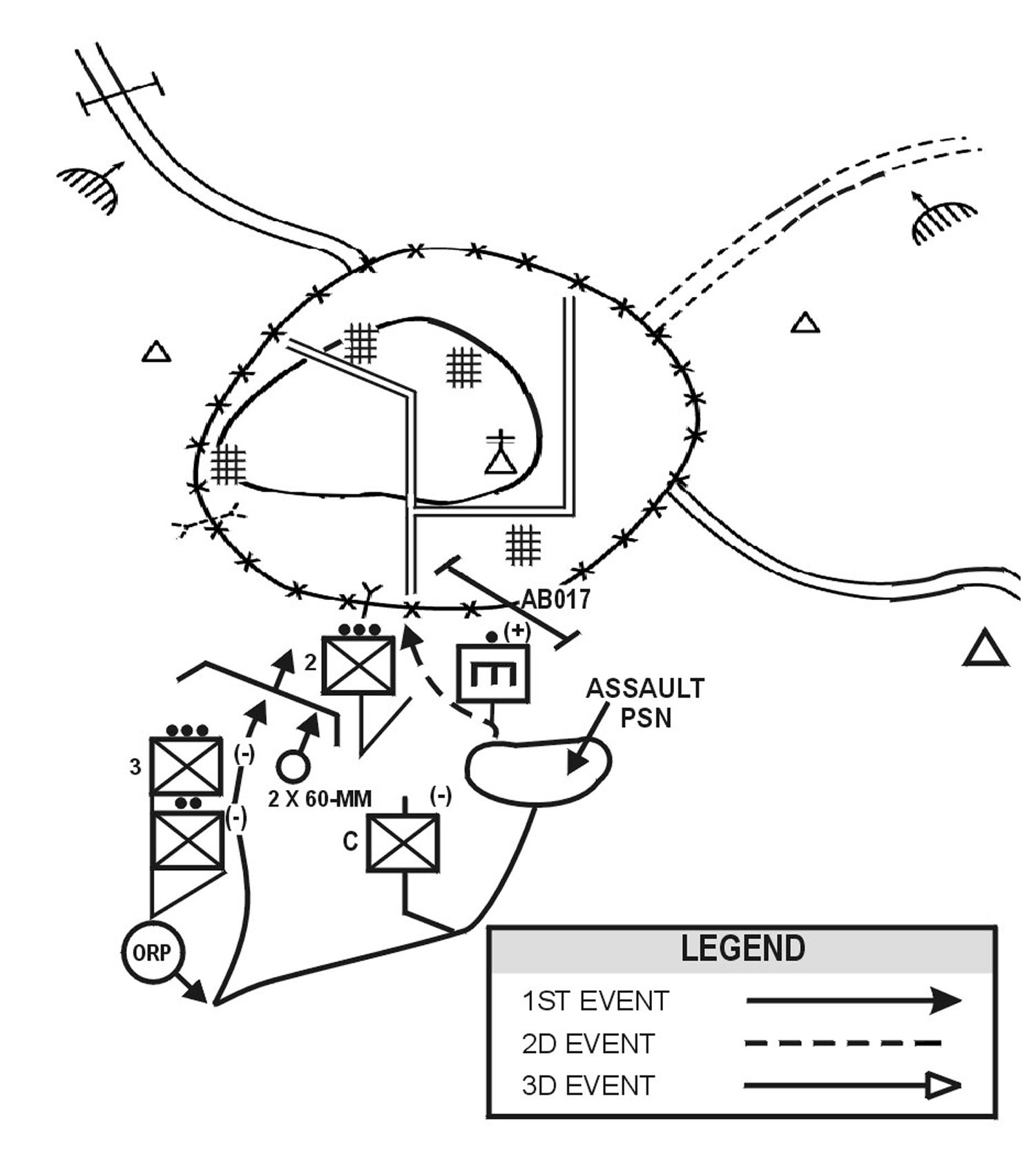
(c) Actions on the Objective. The final assault combines the effects of overwhelming combat power and suppressive fires with the use of maneuver to gain positional advantage over the defending enemy. Suppressive fires from support forces and from supporting indirect fire assets isolate the objective area and suppress the enemy. These fires protect the assault force as it closes with the enemy. Other measures the SBCT infantry company may use to set the conditions for the final assault include, but are not limited to, the following:
|
Once the conditions are set, the assault forces maneuver to close with and destroy the enemy. Other SBCT infantry company elements continue to provide support as necessary throughout the assault.
4-22. ATTACKS DURING LIMITED VISIBILITY
Effective use of digitized and own the night (OTN) equipment during limited visibility attacks enhances squad and platoon ability to achieve surprise and causes panic in a lesser-equipped enemy. OTN enhancements allow the infantry soldier to see farther and with greater clarity. The OTN enhancements and increased friendly and enemy information afford a marked advantage over the enemy. (Refer to paragraph 4-36 for a detailed discussion of limited visibility attacks.)
Section VI. OTHER OFFENSIVE OPERATIONS
The SBCT infantry rifle company normally conducts other offensive operations--movement to contact, exploitation, and pursuit--as part of an SBCT infantry battalion or larger element.
4-23. PLANNING CONSIDERATIONS
The purpose of movement to contact is to gain or regain contact with the enemy. It is most appropriate when the enemy situation is vague and there is not time to reconnoiter extensively to locate the enemy. Because of the increased amount of intelligence available through the RSTA assets, US forces execute movement to contact less frequently than in the past. Movement to contact ends when contact is made. (Contact results in initiation of another operation such as attack against a stationary or moving enemy force, defense, delay, or withdrawal.) The SBCT infantry rifle company normally conducts movement to contact as part of an SBCT battalion or larger element. Based on the factors of METT-TC, however, it can conduct the operation independently. As an example, the company may conduct movement to contact prior to occupation of a screen line. Because the enemy situation is not clear, the company moves in a way that provides security and supports a rapid buildup of combat power against enemy units once they are identified. Two techniques for conducting a movement to contact are the search-and-attack technique and the approach-march technique. If no contact occurs, the company may be directed to conduct consolidation on the objective. The following paragraphs examine the role of the company in a battalion-level movement to contact.
a. Fundamentals. The SBCT infantry rifle company commander analyzes the situation and selects the proper tactics to conduct the mission. He reports all information rapidly and accurately and strives to gain and maintain contact with the enemy. He retains freedom of maneuver by moving the company in a manner that--
|
4-24. THE SEARCH-AND-ATTACK TECHNIQUE
This decentralized technique uses multiple, coordinated, small-unit (team, squad, or platoon) actions to find the enemy. If the company makes contact without being detected by the enemy, the commander gains the initiative. He then has the option to destroy the enemy with the immediately available combat potential, to maneuver the remainder of the company to destroy the enemy, or to follow the enemy back to his base camp and destroy him there. During his planning, the SBCT infantry commander decides how to find the enemy, how to fix or follow him, and then how to finish him.
a. Concept Development. Initially, the decisive points are identified as the most likely enemy locations. Once the enemy has been located, the specific decisive point must be determined as in any attack, and a concept must be developed for generating overwhelming combat power there. The initial concept must include the actions to finish the enemy force once they are located. At times, this part of the plan may be very general or consist only of control measures and be-prepared missions to provide flexibility and to support the rapid issuance of FRAGOs.
(1) The commander must understand the battalion commander's concept and what freedom of action the company has to engage the enemy. At times, the company must engage and destroy all enemy forces within their capabilities. In other cases, the company must locate, follow, and report small enemy units to allow the battalion to concentrate and destroy these forces.
(2) The commander focuses the platoons and squads on the likely enemy locations. He assigns missions IAW the battalion commander's concept. Possible operations include a zone or area reconnaissance, an ambush, or surveillance. The small-unit leaders must know what actions to take when they locate the enemy either with or without being detected. The platoon most likely to make contact normally is designated the main effort.
b. Considerations. The commander determines the number and size of the units that will conduct reconnaissance and combat actions against the enemy. The size of the area, the duration of the mission, the soldier's load, and the probable size of the enemy force are key to this decision.
(1) The size of the area of operations is considered in relation to how much time is available to search the area. When allocating terrain, the commander must consider how the platoons will conduct the reconnaissance, how to provide security, and how to provide control.
(a) One technique is to assign small AOs that keep the platoons more concentrated and help maintain control. The platoons move into the next AO on order.
(b) Another technique is to divide the company area into zones. The commander concentrates most of the company in one zone and uses fire team or squad patrols to reconnoiter the next zone or the rest of the area. Once the company (-) has completed the reconnaissance in the initial zone, it moves into the area the small units have reconnoitered. This technique is effective when a detailed reconnaissance is required, but it also supports the seizure of the initiative through speed, stealth, and surprise. The small, dispersed units have a better chance of locating the enemy undetected. They also provide initial reconnaissance information on which the commander focuses the remainder of the company's reconnaissance efforts.
(2) The commander must consider how the duration of the mission affects the company's ability to conduct contingency operations. If the mission will continue for days or longer, the commander must develop a concept that allows his subordinates to maintain combat effectiveness. The concept must address the use of patrol bases and limited visibility operations. The commander must ensure that the concept provides sufficient rest to maintain his soldiers' stealth, alertness, and security.
(3) The duration of the mission also affects the soldier's load, which has a tremendous impact on a search-and-attack mission. The longer the mission is expected to last, the heavier the soldiers' loads may need to be to reduce the need for resupply. The ability to move with stealth and security while close to the enemy is hindered by heavy loads, but resupply operations also may hinder the company's operation and allow the enemy to locate the unit by following or observing the resupply vehicles.
(a) The company commander must determine what the essential requirements are for the soldiers' loads. If this results in excessive loads, he plans for resupply operations that avoid enemy detection and maintain the security of the company.
(b) The company commander may combine techniques to reduce the risk of moving with these heavy loads. He identifies objective rally points (ORPs) or company patrol bases throughout the AO, and the company moves between these ORPs using the approach-march technique to provide greater control and security. After securing and occupying the ORP, the platoons leave their rucksacks and move out to conduct decentralized search-and-attack operations. A security force secures the ORP until the units return to get their rucksacks and move to the next ORP. Platoons can use this same technique when the risk is acceptable.
(4) Knowing the size of the enemy units with which the company is likely to make contact assists the company commander in determining the risk to the company. The company commander also must consider the enemy's capabilities, likely COAs, and specific weapons capabilities to understand the threat and ensure the security of his company, even when conducting decentralized operations. The company commander may direct specific force protection restraints such as "no patrols smaller than a squad," "platoons must be able to consolidate within 20 minutes," or "platoons will depart their patrol bases NLT 60 minutes prior to BMNT."
c. Find the Enemy. During this step, the focus is on reconnaissance to locate the enemy. Generally, small units able to move quickly and with stealth are more likely to locate the enemy without detection. The company commander's concept may restrict the platoon's authority to destroy the enemy once located. It may be more important to locate and follow enemy units to identify their base camps. When not restricted, however, the unit making contact takes immediate action to destroy the enemy. If it is not within this unit's capabilities, the platoon conducts linkups to mass sufficient combat potential and to coordinate the attack.
(1) Platoons normally do not receive a mission with the vague requirement to search and attack. The company commander must be more specific in stating his concept. His concept must also address the likely actions to destroy the enemy once they are located. Specific taskings may include route, area, and zone reconnaissance or surveillance tasks. Platoons also may be tasked to conduct ambushes, to be prepared to conduct an attack to destroy enemy forces, to provide security for another force such as the CP or the mortar section, or to act as the company reserve.
(2) During limited visibility, reconnaissance is more difficult and potentially more dangerous. If a unit makes contact with the enemy in the dark, a hasty attack is very risky. Reconnaissance is also less effective in the dark because the unit covers less area and is unable to detect many signs of enemy activity. Although observation is reduced during limited visibility, the unit may be more likely to detect the enemy by sight or smell. Route and small-area reconnaissance tasks are more effective for limited visibility.
(3) Ambushes are effective during limited visibility. The enemy may avoid daylight movements if aware of the company's presence in the AO. Ambushes should be set up on the enemy's likely routes or near their water and food sources. Patrol bases should integrate ambushes and observation posts (OPs) (with thermal sights, NVDs, and platoon early warning systems [PEWS]) into their security plans. These tasks support the seizure and maintenance of the initiative.
d. Fix and Finish the Enemy. These steps of a search and attack are closely related. An initial attempt to finish the enemy by the platoon in contact may quickly become the fixing effort for the company's attack if the enemy is too strong for the platoon or the platoon is unable to achieve surprise. When the authority to conduct offensive actions to destroy the enemy has been decentralized to the lowest level, the fundamentals of an attack apply at every echelon.
(1) Achieve Surprise. Locate the enemy without being detected. This allows more time to plan and coordinate the attack. Once detected, speed and violence in the assault may also achieve surprise, but this is rarely true against a prepared enemy defense.
(2) Limit the Enemy's Freedom of Action. Fix the enemy in position. Block his routes of escape with indirect fires, maneuver forces, or both. Suppress his weapons systems, obscure his vision, and disrupt his command and control. Reconnaissance is continuous; leaders at every echelon seek out the enemy's dispositions, strengths, and weaknesses. Initially, these actions are directed toward supporting an attack by the lowest echelon. At some point, the leader of this unit must determine if he is able to achieve fire superiority and conduct the assault. If he determines he does not have sufficient combat power to complete the destruction of the enemy, the leader focuses on fixing the enemy and reconnoitering to support the attack by the next higher echelon.
(3) Maintain Security. While attempting to take these actions against the enemy, the enemy is attempting to do the same. Do not assume the enemy that has been identified is alone; there may be mutually supporting positions or units. The planned envelopment or flank attack of one enemy position may move through the kill zone of another unit, or this maneuver may expose the flank of the assault force to fires from undetected positions.
(4) Concentrate Combat Power. Once contact is made, the plan must support the rapid concentration of combat power to fix and destroy (finish) the enemy. Leaders at each echelon plan to destroy the enemy within their capabilities. The combat potential of small units may be increased by ensuring each has the ability to request fire support.
(a) The company commander may retain a portion of the company in reserve to react quickly to enemy contact by one of the small units. However, when the company is operating in a more dispersed manner, this company reserve may not be responsive enough. It may be more effective for each platoon to retain its own reserve.
(b) If the unit or platoon cannot finish the enemy, the company commander determines how to fix or contain the enemy while concentrating his dispersed combat potential. He then develops an attack plan to destroy the enemy force. He may use the fixing force to support by fire and assault with another platoon(s), or he may use artillery and CAS to destroy him in position.
(c) Each leader must report the results of his reconnaissance to support the company commander's planning. Leaders recommend effective support positions, good assault positions or directions of attack, and likely enemy weak points. The leader of the unit in contact should also identify good linkup points in case the preplanned points are not effective. In most cases, this leader should coordinate face to face with the company commander or the leader of the assault element before initiating the assault.
e. Follow the Enemy. When the purpose of the operation is to locate the enemy's base camps or other fixed sites, the company concept must avoid nondecisive fights between small units. When friendly units locate small enemy units, they report and attempt to follow or track these units back to their base camps. Well-trained trackers familiar with the area may be able to identify and follow enemy tracks that are hours or even days old (FM 7-8). The company commander must ensure that his concept does not risk the security of his force in the attempt to make undetected contact and track enemy units. Units tracking the enemy must be ready to react to enemy contact and avoid likely ambush situations. It also may be possible to track the enemy's movement through the AO by using stationary OPs as trail watchers to report enemy activity.
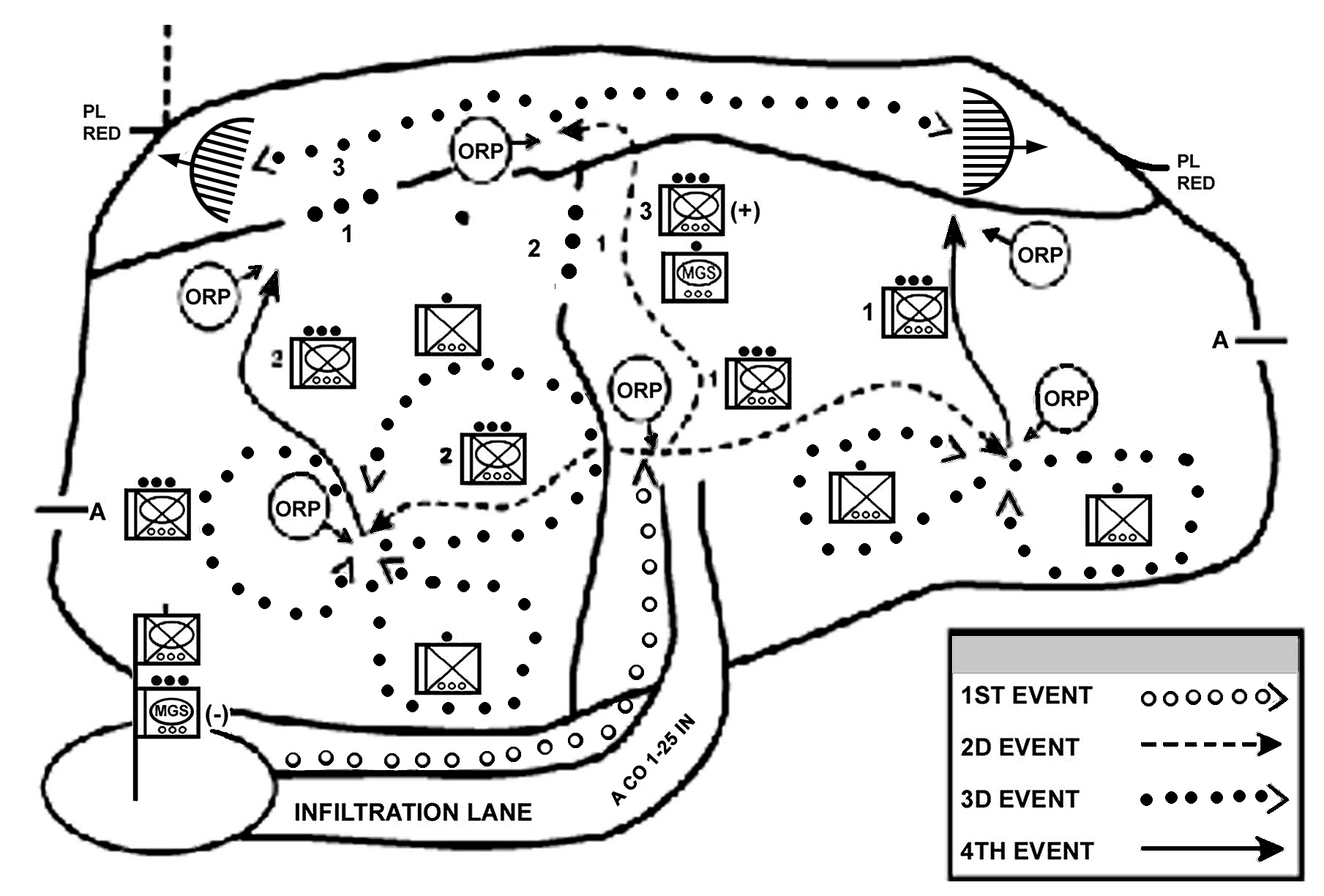
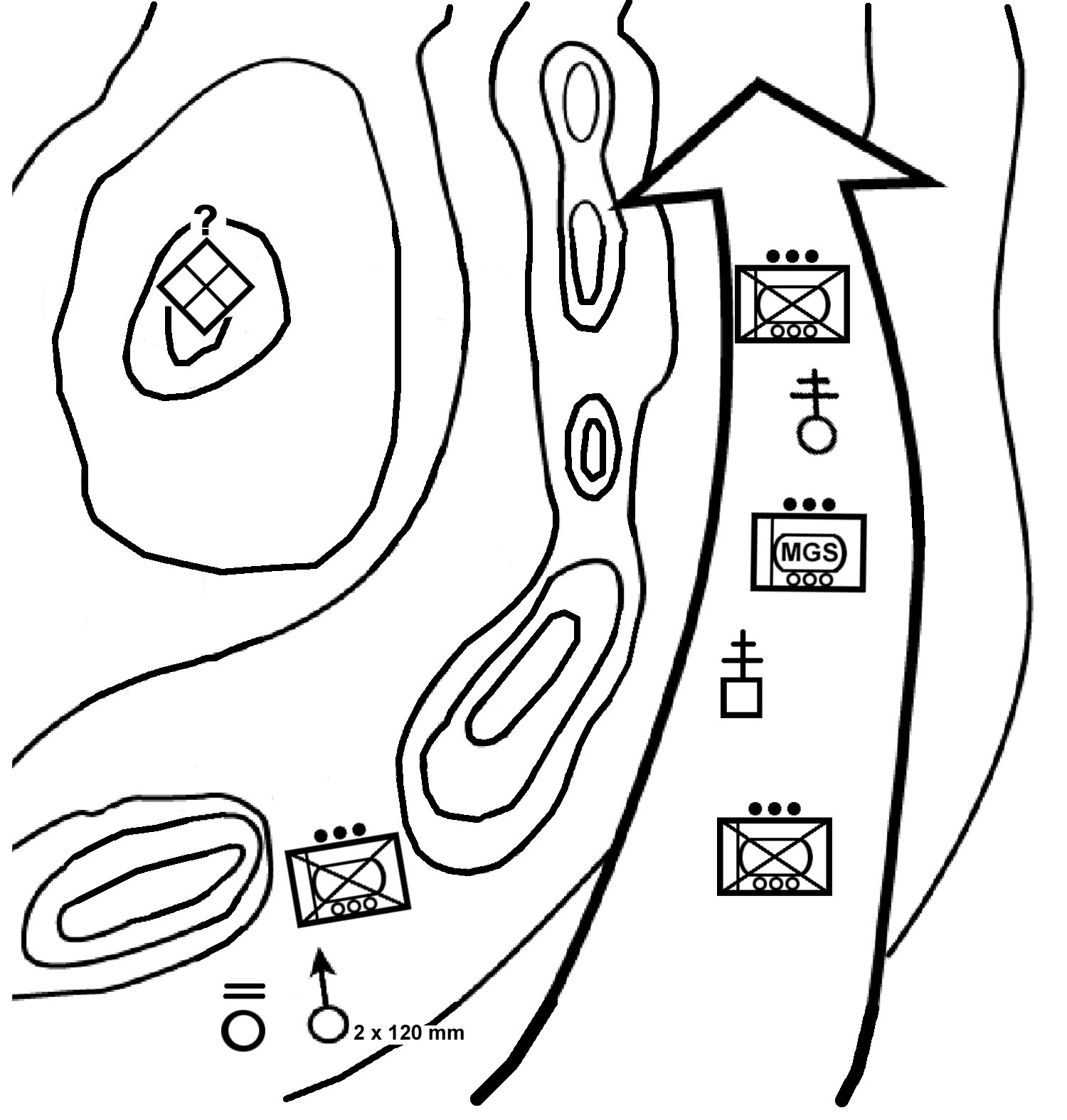
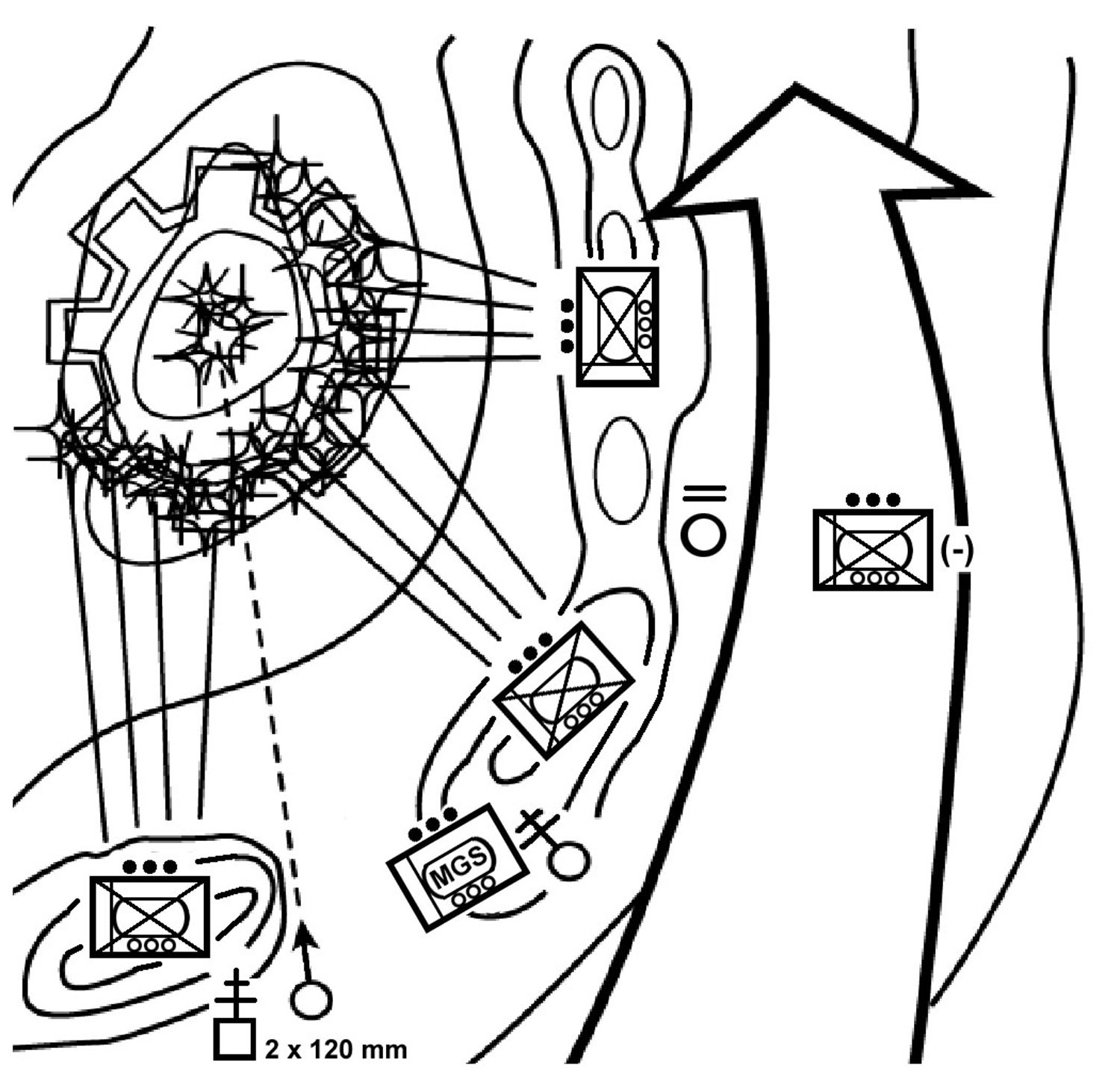
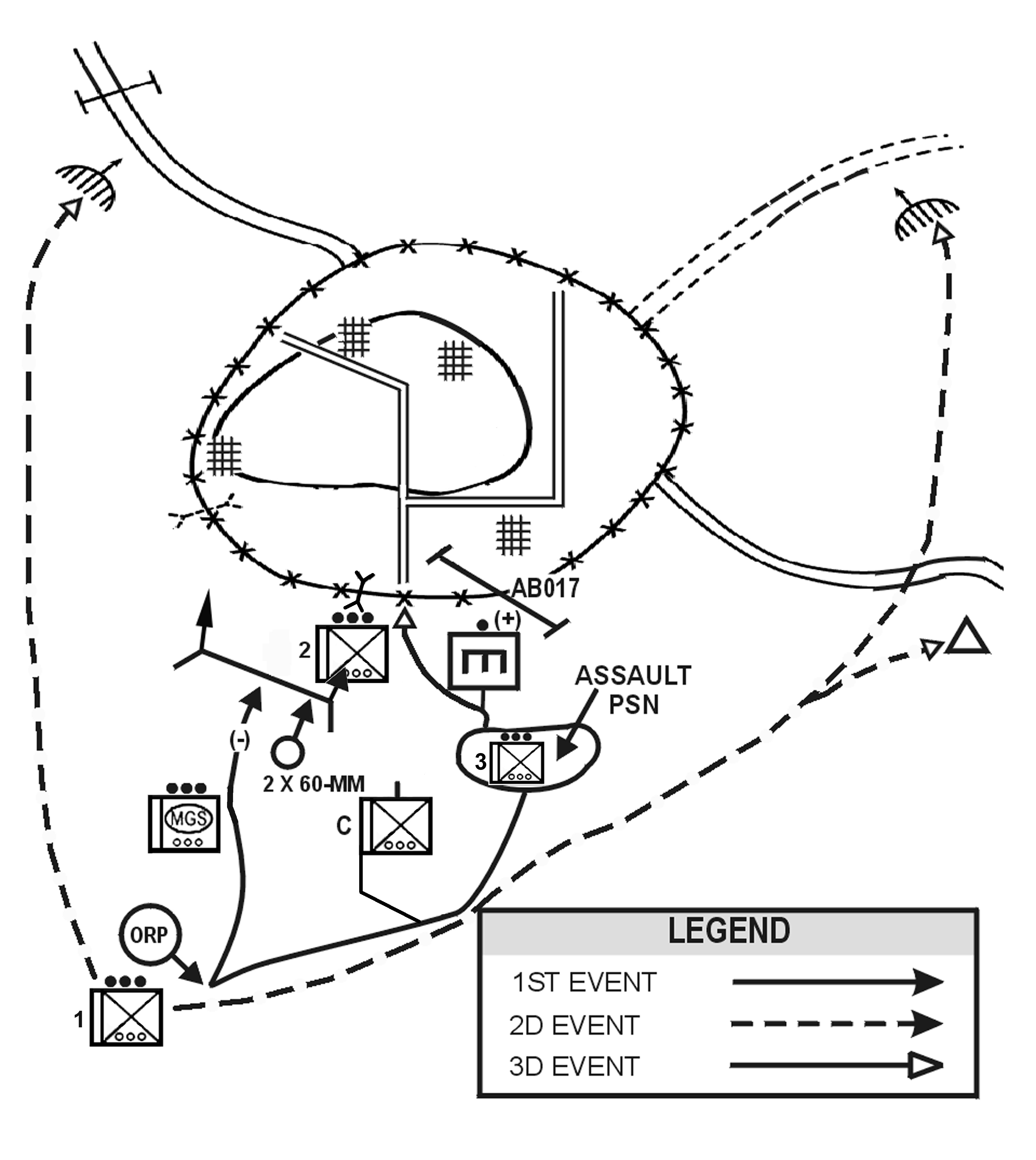
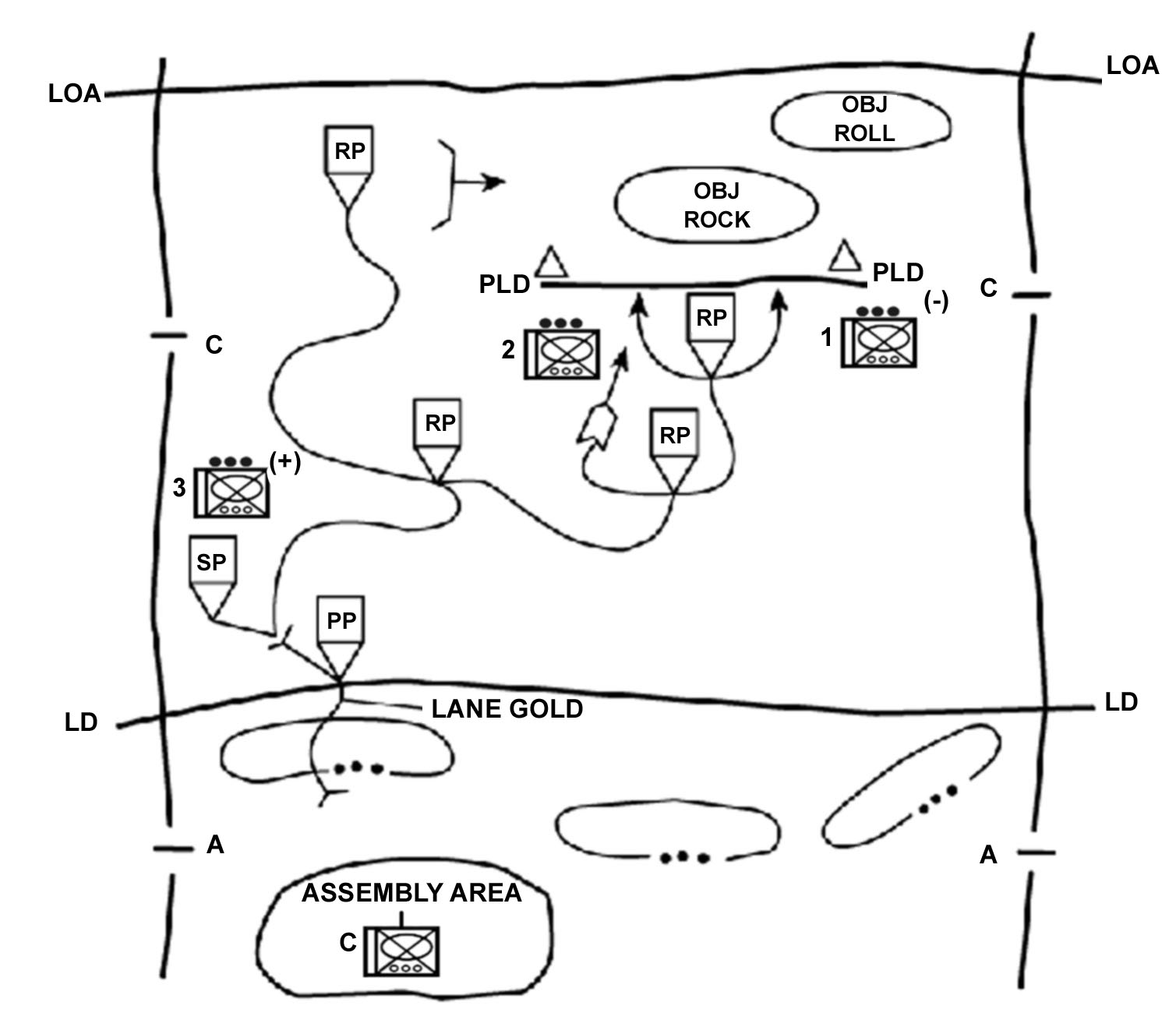
f. Enter the Area of Operations. The company commander decides how the company will enter its zone or area of operations, how to move once in the area, where to locate certain units or facilities, and what the requirements for contingency plans are. This includes establishing the proper graphic control measures to control the movement of the units, to provide for linkups between units, and to support the rapid concentration of the company's combat power. It also includes synchronizing the actions of the company and providing specific tasks or restraints to ensure subordinates understand what actions to take once they make contact with the enemy. The company may enter the area or zone by moving as a company and then splitting up (Figure 4-6), by infiltrating squads and platoons (Figure 4-7), or by air assault.
Figure 4-6. Infiltration by company.
Figure 4-7. Infiltration by squad/platoon.
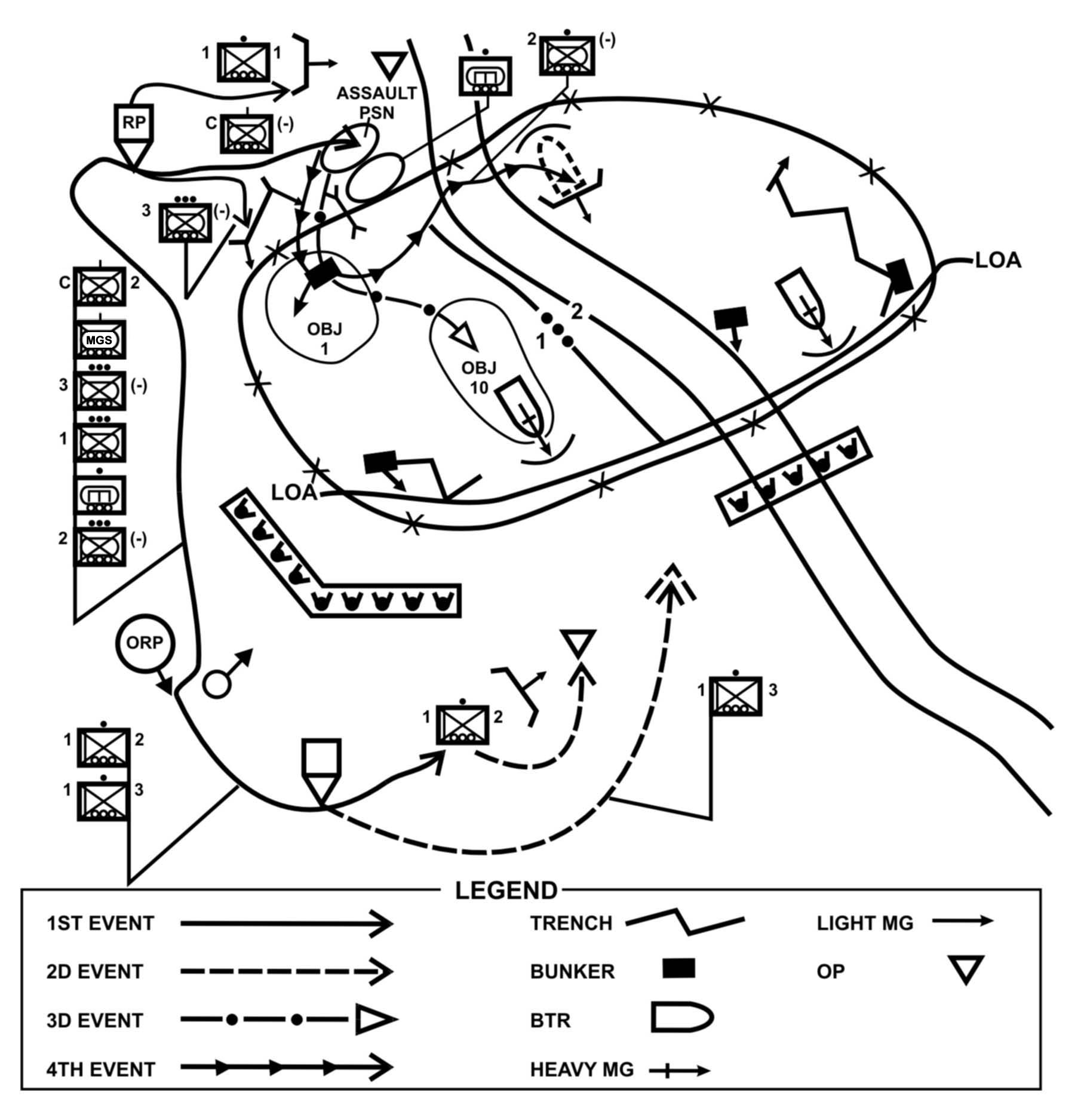
(1) Movement within the area or through the zone of attack may be conducted by the entire company or by individual platoons. Figure 4-8 shows a concept sketch for a search and attack conducted without a company linkup.
Figure 4-8. Company search-and-attack concept sketch.
(2) The SBCT infantry rifle company commander must decide where the company CP will locate. He may collocate it with the main effort platoon or position it in a central location where it can communicate with and move quickly to each platoon's location. A technique to support contingency operations (CONOPS) is to rotate a reserve platoon each day to provide security for the CP and the company mortars. To prevent a serious degradation in effectiveness due to sleep loss, each platoon spends only 48 hours actively searching for the enemy and then rotates into the reserve role.
(3) Company mortars must locate where they have security and can support the platoons. The company commander may collocate the mortars with the company CP. To overcome the difficulties of moving mortar ammunition, the company commander may direct the reserve platoon to carry the ammunition to the next firing position. Another option is to establish company ORPs or patrol bases and place the mortars at these locations. The entire company can then carry the mortar ammunition; the soldiers drop off the rounds before moving out to the platoon areas. However, the entire company must return to this location before continuing the operation through the zone.
(4) The soldier's load and the threat of enemy armor are two primary considerations for employing the antiarmor assets. If there is an armored threat, the company commander must provide guidance to platoon leaders on where to position the antiarmor assets. If the threat does not require antiarmor weapons, the platoons may still use some thermal sights for observation.
(5) Contingency plans may include actions in case one platoon becomes decisively engaged or the company receives a new mission. All units should routinely report possible landing zone/pick-up zone (LZ/PZ) locations, mortar firing positions, any sign of recent enemy activity, and any sightings of civilians in the area.
4-25. THE APPROACH-MARCH TECHNIQUE
The SBCT infantry rifle company normally uses this technique when it conducts a movement to contact as part of the battalion. The company can act as the advance guard, move as part of the battalion main body, or provide flank or rear guards for the battalion, depending on its location in the formation and its assigned mission.
a. Planning. When planning for an approach-march movement to contact, the company commander needs certain information from the battalion commander. With this information, the company commander develops his scheme of maneuver and fire support plan. He provides this same information to the platoon leaders. As a minimum, he needs to know--
|
b. Lead Company Responsibilities. The SBCT battalion may conduct a movement to contact on a single axis or on multiple axes. The lead company on an axis is responsible for--
|
c. Lead Company Movement. The lead company or advance guard on an axis moves using traveling overwatch or bounding overwatch, depending on the situation. It normally is assigned an axis of advance or a zone of action and a march objective on which to orient its movement. Phase lines and checkpoints also can help control movement.
(1) The company commander selects the movement technique and formation based on the likelihood of enemy contact and the speed of movement desired by the battalion commander. Bounding overwatch provides the best security, but traveling overwatch is faster. If the company uses traveling overwatch, the lead platoon may use bounding overwatch for added security.
(2) The company commander must retain the freedom to maneuver his platoons and weapons. He analyzes the terrain, anticipates where he might make contact, and plans fires on those locations. He should avoid terrain that restricts maneuver, such as draws, ravines, narrow trails, and steep slopes.
d. Other Companies. A company not in the lead uses traveling or traveling overwatch. It must be ready to fire or maneuver in support of the lead company, or to assume the lead company's mission.
e. Contact. Once the company makes contact with the enemy, the company commander maintains that contact until ordered to do otherwise by the battalion commander. The following actions must take place at once:
(1) When there is an unexpected contact, the platoon in contact returns fire at once and takes cover. If the enemy is unaware, the platoon making contact reports and deploys to prevent detection. The maneuver to a position of advantage by this platoon (or other units) should maintain the element of surprise until the company completes preparation for the hasty attack. If detected, or once the company commander decides to initiate the hasty attack, the platoon leader attempts to fight through, destroying the enemy with the resources that are immediately available. His FIST should begin calling for fire. The platoon leader then reports to the company commander and develops the situation. The overwatch element immediately fires at the enemy position. Trail platoons that are not able to fire take cover and wait for orders.
(2) The squad or platoon that initially received direct fire immediately executes the attack drill (FM 3-21.9 [FM7-5]). The intent is to use aggressive small-unit actions to seize the initiative rapidly and at the lowest echelon possible. The unit in contact attempts to achieve fire superiority to fix or suppress the enemy with the resources that are immediately available. The unit then executes a flank attack directed against an identified enemy weakness. If this is not possible, the unit develops the situation to identify the enemy's flanks, any covered and concealed routes around the enemy position, possible supporting positions (both friendly and enemy), and any protective obstacles that the enemy has constructed. It then reports this information to the company commander.
(3) Upon receipt of this information, the company commander determines the proper action to take. The XO reports the situation to battalion. The company commander may conduct, or direct his units to conduct, additional reconnaissance. The company FSO requests and coordinates indirect fires to support the company's maneuver. Possible actions include the following.
(a) Conduct a Hasty Attack. If the company commander feels he can defeat the enemy force and an attack supports the battalion commander's concept, he conducts a hasty attack immediately, before the enemy can react.
(b) Bypass the Enemy. The company commander, with battalion permission, may bypass an enemy force. He may bypass the enemy with one platoon at a time or with the entire company at once (Figure 4-9).
Figure 4-9. Bypass.
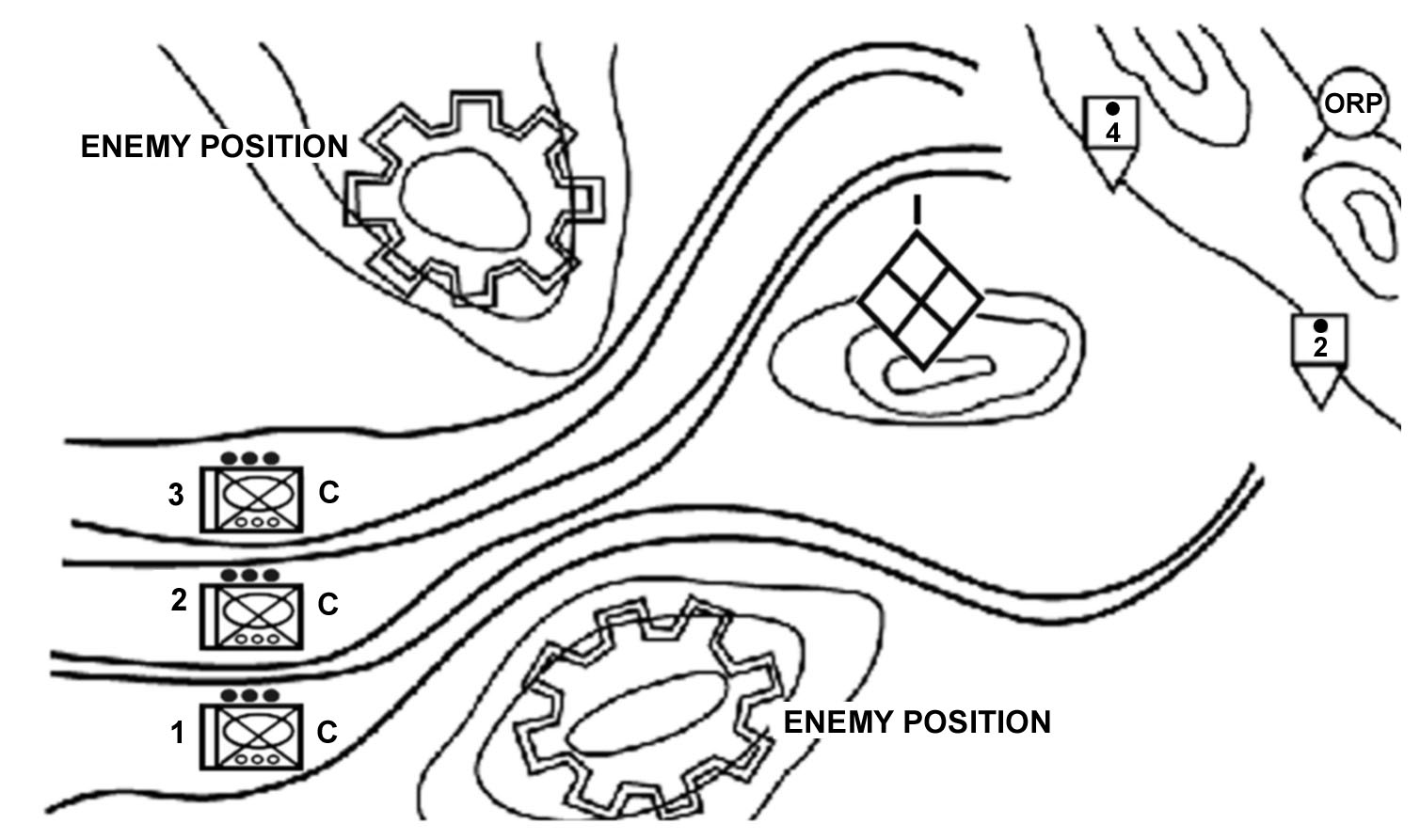
(c) Fix or Suppress the Enemy. When the enemy cannot be bypassed and a hasty attack by the company would be too costly, the battalion normally directs the company to fix or suppress the enemy (Figure 4-10). This ensures that the enemy does not have the freedom to fire or maneuver against the main body of the battalion while the battalion moves to attack the enemy. The company commander supports the battalion commander's planning by reconnoitering to identify the enemy's disposition, strengths, and weaknesses. The company identifies covered and concealed routes, good support positions, and enemy obstacles and reports these to battalion.
Figure 4-10. Fix or suppress.
(d) Establish a Hasty Defense. Although this action tends to give the initiative to the enemy force, it might provide a needed advantage. This might be required in a meeting engagement with a superior force. The company may establish a hasty defense to protect itself while the remainder of the battalion maneuvers against the enemy.
(e) Disengage. This action is not preferred unless disengaging is the only way to ensure preservation of the force. Use of indirect fires and bounding and overwatch elements is essential in disengaging from a superior force. The company may disengage while another unit maintains contact, or the company may disengage by moving back through the battalion to draw the enemy into an ambush.
4-26. CONSIDERATIONS
The battalion may direct the company's technique (search-and-attack or approach-march). If not, the SBCT infantry rifle company commander considers his mission and the battalion concept as he conducts his estimate to select the best technique. Normally, when operating as part of a battalion movement to contact, the company employs the same technique as the battalion. The commander must consider the mounted capabilities of his company during both techniques. The following considerations may also assist the commander in developing his concept.
a. Time Available. The time available for planning, coordinating, and rehearsing may affect the decision. The approach-march technique generally requires much less time for preparation. The company may require only a brief FRAGO assigning the movement formation or technique and some simple graphic control measures to begin movement. The search-and-attack technique may require more preparation time because the platoons and squads have more planning responsibilities (such as patrol base, linkups, and casualty evacuations).
b. Speed of Movement. The speed the company must move is a major factor. With either technique, the faster the company moves, the less effective its R&S efforts are. Thus, it becomes more likely that the enemy will initiate fires at the time and place he selects. The approach-march technique is normally more effective for quickly reacting to enemy contacts.
c. Enemy. The company commander considers the clarity of the enemy situation. If the enemy situation is vague then a movement to contact is required; however the SBCT company commander should have some information via analog activities or digital information. Knowing where the enemy will probably locate and in what strength is key to developing a concept. The company commander considers the enemy's probable locations and strength when planning the company's movement and security needs, and he analyzes the risks for each technique. The company commander also considers the expected enemy action upon contact. If he expects the enemy to fight, then the approach march may be the more effective technique. If the enemy will attempt to avoid detection or quickly disengage, the search-and-attack technique may be the better method.
d. Security. Preparation time, required movement speed, and the enemy situation have a direct impact on the company's security requirements. The company commander also considers the terrain, the adjacent units, the available combat support, and the present status of his unit to determine how to provide security for his company. Successful movements to contact depend on locating the enemy without being detected. This provides the company commander the initiative to develop the situation by fully coordinating and supporting the attack with all available resources.
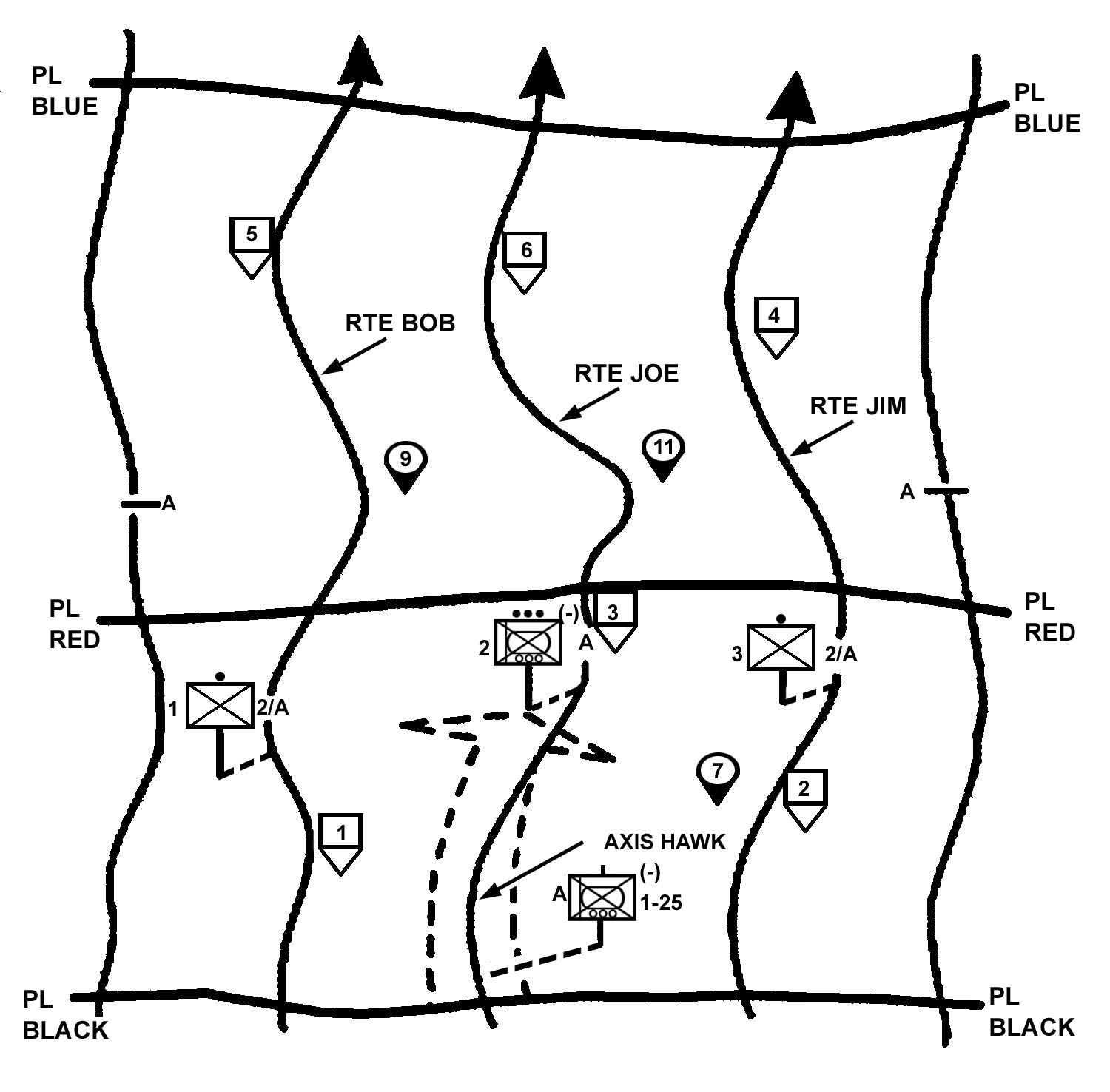
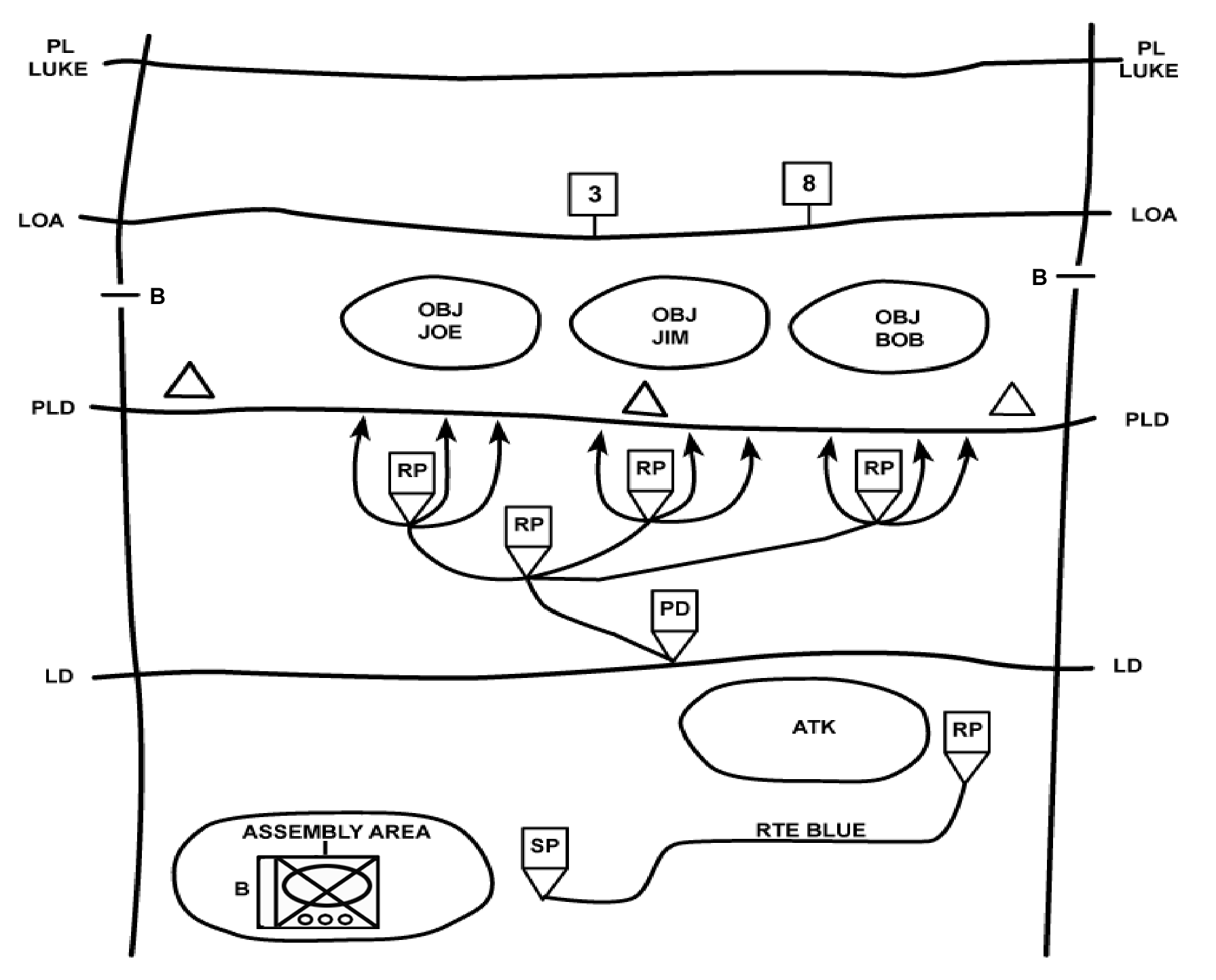
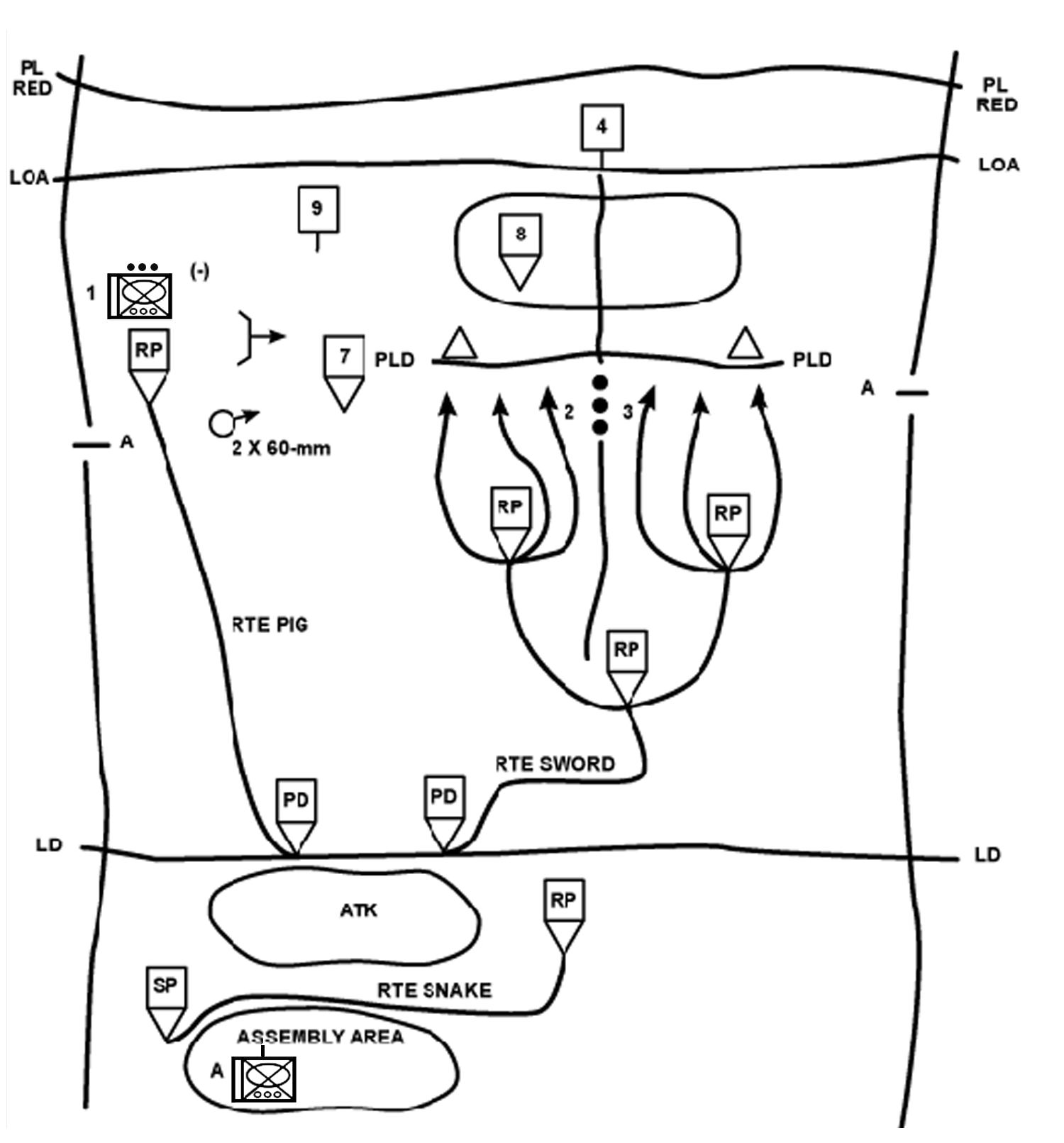
e. Combined Technique. An effective option may be to combine the techniques by having the lead platoon use the search-and-attack technique while the rest of the unit uses the approach-march technique. The lead platoon is assigned reconnaissance missions to find the enemy. In the example illustrated in Figure 4-11, the company commander assigns route reconnaissance tasks to the 2d Platoon. He assigns checkpoints and named areas of interest (NAIs) to focus the subordinate elements on specific locations. He can also use phase lines (PLs) to control the lead platoon by directing that PLs be crossed on order. The company main body follows the reconnaissance at a distance that allows it to rapidly maneuver based on reports from the lead platoon. The formation and movement techniques for the main body vary but generally apply the fundamentals for the approach-march technique.
Figure 4-11. Combined techniques.
4-27. Exploitation
A company normally takes part in exploitations as part of a larger force; however, the company should exploit tactical success at the local level within the higher commanders' concept of the operation.
4-28. PURSUIT
The objective of the pursuit phase of an operation is the total destruction of the enemy force. The SBCT infantry rifle company may take part in a pursuit as part of a larger force or, because of its organic transportation, may act as the pursuit force that can close with and destroy the remnants of the enemy force.
Section VII. SPECIAL PURPOSE ATTACKS
The company conducts a special purpose attack at the direction of the battalion commander. The commander bases his decision on the factors of METT-TC. Special purpose attacks are subordinate forms of an attack and they include--
|
As forms of the attack, they share many of the same planning, preparation, and execution considerations of the offense. Feints and demonstrations are also associated with military deception operations.
4-29. AMBUSH
An ambush is a surprise attack, from concealed positions, on a moving or temporarily halted enemy. It may take the form of an assault to close with and destroy the enemy, or it may be an attack by fire only, executed from concealed positions. An ambush does not require that ground be seized or held. Infantry forces normally conduct ambushes. (For a more detailed discussion of ambushes, refer to FM 7-10.)
a. Purposes. Ambushes are generally executed to reduce the enemy force's overall combat effectiveness. Destruction is the primary reason for conducting an ambush. Other reasons to conduct ambushes are to harass the enemy, capture the enemy, and destroy or capture enemy equipment and supplies.
b. Operational Considerations. The execution of an ambush is offensive in nature. The company, however, may be directed to conduct an ambush in a wide variety of situations. For example, it may stage the ambush during offensive or defensive operations, as part of SBCT battalion rear area operations, or during retrograde operations. The commander must consider the capabilities of his company in the mounted and dismounted role. Operational security is critical to the success of an ambush and is a major reason the operation normally is conducted only by infantry forces. The company must take all necessary precautions to ensure that it is not detected during movement to or preparation of the ambush site. The company must also have a secure route of withdrawal following the ambush.
c. Actions. An ambush normally consists of the following actions:
|
d. Task Organization. The company normally is task-organized into assault, support, and security forces for the execution of the ambush.
(1) Support Force. The support force fixes the enemy force and prevents it from moving out of the kill zone, allowing the assault force to conduct the ambush. The support force generally uses direct fires in this role, but it also may be responsible for calling for indirect fires to further fix the ambushed force.
(2) Assault Force. The assault force executes the ambush. It may employ an attack by fire, an assault, or a combination of those techniques to destroy the ambushed force.
(3) Security Force. The security force provides protection and early warning to the ambush patrol and secures the ORP. It isolates the ambush area both to prevent the ambushed enemy force from moving out of the ambush site and to keep enemy rescue elements from reaching the site. The security force also may be responsible for securing the company's withdrawal route.
e. Types of Ambushes. Once the company receives an order to conduct an ambush, the commander must determine which of the two types of ambush operations is best suited to the situation and the capabilities of his company. In a point ambush, the patrol deploys to attack an enemy force in a single kill zone. In an area ambush, the patrol is deployed to conduct several related point ambushes throughout an ambush area.
4-30. RAID
A raid is a limited-objective form of attack entailing swift penetration of hostile terrain. A raid operation always ends with a planned withdrawal to a friendly location upon the completion of the assigned mission. It is not intended to hold territory. The company can conduct an independent point raid or it can participate in a battalion area raid. A point raid attacks the enemy force in a single kill zone; an area raid encompasses several related point raids or other related operations. It is unlikely that a company would conduct an area raid independently.
a. Company Role. The company conducts raids to accomplish a number of missions, including the following:
|
b. Task Organization. Task organization of a raiding force is based on the purpose of the operation. It normally consists of the following elements:
|
c. Conduct of the Raid. The main differences between a raid and other attack forms are the limited objectives of the raid and the associated withdrawal following completion. Raids may be conducted in daylight or darkness, within or beyond supporting distance of the parent unit. When the area to be raided is beyond supporting distance of friendly lines, the raiding party operates as a separate force. An objective, usually very specific in nature, normally is assigned to orient the raiding unit. During the withdrawal, the attacking force should use a route or axis different from that used to conduct the raid itself.
4-31. SPOILING ATTACK
A spoiling attack is a limited-objective attack to delay, disrupt, or destroy the enemy's capability to attack. SBCT infantry commanders mount spoiling attacks from defensive postures to disrupt expected enemy attacks. A spoiling attack attempts to strike the enemy while he is most vulnerable--during his preparations for attack in assembly areas and attack positions or while he is on the move prior to crossing his line of departure. In most respects, commanders conduct spoiling attacks like any other attack. They may be either hasty (when time is short) or deliberate (when the command has adequate forewarning). When the situation permits, commanders exploit a spoiling attack like any other attack.
4-32. COUNTERATTACK
A counterattack is an attack by defensive forces to regain the initiative or to deny the enemy success with his attack. Commanders conduct counterattacks either with a reserve or with lightly committed forward elements. They counterattack after the enemy launches his attack, reveals his main effort, or creates an assailable flank. SBCT infantry commanders conduct counterattacks much like other attacks but synchronizing them within the overall defensive effort requires careful timing.
a. Commitment of Combat Power. Counterattacks afford the defender the opportunity to create favorable conditions for the commitment of combat power. If it can fix the enemy, then the company can rehearse counterattacks, control their timing, and prepare the ground to be traversed. Counterattacks are most useful when they are anticipated, planned, and executed in coordination with other defending, delaying, or attacking forces and in conjunction with a higher commander's plan.
b. Exploit Success. As in spoiling attacks, commanders prepare to seize the opportunity to exploit success by the entire force. However, counterattacks may be limited to movement to better terrain in order to bring fires on the enemy. Given the same forces on both sides, counterattacks can achieve greater effects than other attacks because the defender can create more favorable conditions through rehearsal and control of the timing.
4-33. FEINT
The feint is in many ways identical to other forms of the attack. Its purpose is to cause the enemy to react in a particular way, such as by repositioning forces, committing its reserve, or shifting fires. The key difference between the feint and other attack forms is that it is much more limited in scope and has an extremely specific objective. The scale of the operation, however, usually is apparent only to the controlling headquarters. For the element actually conducting the feint, such as an SBCT infantry company or battalion, execution is just as rapid and violent as in a full-scale attack.
a. Company Role. The company normally participates in a feint as part of a larger element. Among the planning considerations for the company commander are the following:
|
b. Making Feints Believable. Feints are successful only if the enemy believes that a full-scale attack operation is underway. To be believable, they must be conducted with the same violence and the same level of precision as any attack. The controlling headquarters must issue a clear task and purpose to the unit conducting the feint. This should include identification of the specific enemy action the feint is supposed to trigger (or deny), such as forcing the commitment of an enemy reserve force or preventing an enemy element from repositioning against the main effort attack. Feints are most effective under the following conditions:
|
4-34. DEMONSTRATION
The demonstration is an attack whose purpose is to deceive the enemy about the location of the main attack. This purpose is similar to that of a feint, but the friendly force does not make contact with the enemy. For example, the SBCT infantry company's role might entail establishing an attack-by-fire position beyond the enemy's direct fire engagement range; the purpose would be to cause the enemy to commit a specific element simply by virtue of the positioning of the demonstration force. In preparing to participate in a demonstration as part of a larger force, the company commander should keep in mind the following planning considerations.
a. Limit of Advance. The limit of advance must be carefully planned so the enemy can "see" the demonstration force but cannot effectively engage it with direct fires. The force must also take any other security measures necessary to prevent engagement by the enemy.
b. Contingency Plans. The demonstration force must make contingency plans so it can respond effectively to enemy direct or indirect fires while avoiding decisive engagement.
c. Follow-on Orders. Clear, specific follow-on orders must ensure that the demonstration force is prepared to exploit the success of the main attack, if necessary.
Section VIII. ATTACK TECHNIQUES
The assault on an enemy strongpoint and a limited visibility attack are the two most demanding attacks an SBCT company conducts. The fundamentals and techniques discussed in this section will assist the SBCT infantry commander in planning, preparing, and conducting all attacks.
4-35. ASSAULT OF A STRONGPOINT
The most difficult objective for a light infantry force is to seize or clear an enemy strongpoint complete with obstacles and fortifications. The commander employs techniques that avoid attacking the enemy's main strength. Instead, he tries to identify and attack a weakness in the defense. The SBCT infantry commander deceives the enemy as to the point of the main attack; he uses surprise to take advantage of his initiative in determining the time and place for the attack. He attempts to strike the enemy on exposed flanks or the rear. A deliberate attack of a strongpoint is usually conducted in the following steps:
|
a. Reconnoiter and Develop the Concept. The commander conducts reconnaissance of the objective himself or has someone else do it. The reconnaissance should identify the positions on the objective (crew-served weapons, C2 locations, and vehicles), the level of preparation, the gaps in the defense, and other potential weaknesses. The SBCT infantry commander may conduct reconnaissance of the objective to determine any changes from previous information.
(1) The reconnaissance may be done many different ways. An effective technique is to task-organize a reconnaissance patrol with leaders from the assault, support, and breach elements. There should be sufficient personnel to establish surveillance on the objective and to secure the ORP. The reconnaissance patrol either returns to the company's location or meets the company at a designated linkup point and guides it into the ORP. At times, the scout platoon or other battalion assets may be tasked to conduct reconnaissance in support of the company's mission.
(2) After the commander develops his concept, he often task-organizes his unit into a breach element, a support element, an assault element, and possibly a reserve. The reserve is normally under his control and is positioned where it can best exploit the success of the attack or increase combat power as necessary. The reserve should not be so close that it loses flexibility during the assault. The reserve leader must know where he will locate throughout the attack.
(a) The breach force is usually formed around an infantry unit. Engineers, if available, are also part of the breaching element. Any mechanical or explosive breaching assets are attached to this element. The breach force makes the initial breach and passes the assault element through. It may have to organize its own assault element (to secure the breach), support element (to provide close-in suppression), and breach element (to actually breach the obstacles).
(b) The support element is organized to provide supporting (indirect or direct) fires initially to the breach element, then to the assault element. The support element may consist of any combination of infantry squads, the 120-mm/60-mm mortar section, the machine-gun teams, M203 gunners, the MGS platoon, or the ICVs. Their primary responsibilities are to suppress enemy forces that may engage the breach element and to isolate the objective from enemy reinforcement or escape.
(3) The assault element is usually one or two infantry platoons, depending on the enemy situation (number of personnel, level of preparation, and complexity of fortifications) and the size and composition of the breach and support elements. Often, a small assault element supported by a large volume of accurate suppressive fires is effective in clearing the objective. The assault element may also need to breach enemy protective obstacles on the objective.
(4) The commander determines the best task organization for the entire mission. It should be simple and maintain unit integrity whenever possible. At times, the company moves to the ORP task-organized as usual (no cross attachments), changes task organization in the ORP for the conduct of the assault, and then modifies this task organization to consolidate in defensive positions on the objective.
b. Move to the Objective. The company approaches the objective (Figure 4-12) in a manner that supports its deployment prior to the assault. The SBCT infantry commander must determine the transition between mounted and foot movement based on the enemy situation. This may be a movement intended to avoid detection that allows the company to occupy the ORP and conduct the leader's reconnaissance of the objective. The company may cross the LD (or depart the perimeter defense) supported by heavy suppressive direct and indirect fires. These fires continue until the company reaches its assault position or final coordination line (FCL); they then shift to allow the assault on the objective. In either case, the following fundamentals should be part of this step of the attack:
Figure 4-12. Movement to the objective.
(1) The movement from the assembly area to the LD is timed so that movement to and across the LD is continuous. The lead element of the company starts crossing the LD at the attack time specified in the battalion OPORD. Before the company's movement, a patrol may be sent to reconnoiter and mark the route and check the time it takes to move to the LD.
(2) The support element may precede the assault and the breach elements to the LD in order to be in an overwatch position ready to fire when they cross the LD. Company mortars move forward to a firing position near the LD to allow maximum coverage of the objective area.
(3) The commander normally avoids stopping in the attack position. However, if the company is ahead of schedule or told to hold in the attack position, it occupies the attack position, posts security, and waits until it is time to move (or until told to move).
(4) During movement from the LD to the assault position, the company makes the best use of cover, concealment, smoke, and supporting fire.
(5) If the company is hit by indirect fire en route, it moves quickly out of the impact area. If it meets enemy resistance short of the objective, it returns fire at once. The leader of the platoon in contact calls for and adjusts indirect fire on the enemy. Depending on the company plan and the location and type of resistance, the platoon may bypass an enemy position that cannot affect the mission. The locations of all bypassed enemy are reported to the company commander through FBCB2; he, in turn, forwards them to the battalion.
(6) If the company cannot bypass an enemy position, the company commander and the platoon leader in contact must take prompt and aggressive action. The platoon leader attempts to conduct the platoon attack drill and destroy the enemy position. The commander quickly conducts an estimate of the situation and issues FRAGOs as needed to carry out his plan. He should not commit platoons piecemeal. He coordinates actions and fires so the company can attack the enemy with its full combat power. The commander should maneuver to assault the flank or rear of the enemy position. When it has destroyed or suppressed the enemy, the company continues toward its objective.
(7) The company either bypasses or breaches obstacles along the route. The commander must decide the best way to overcome the obstacle without losing momentum. In selecting the scheme of maneuver, the commander normally tries to avoid COAs that require breaching of enemy obstacles. Because all forces construct defensive obstacles around their positions, however, the attacking unit must be prepared to conduct a breach. In an SBCT battalion deliberate attack, the company may be the breach force; it may conduct breaches with its organic countermine equipment or with attached engineer assets. The company commander informs the battalion commander of obstacles that may affect units following the company. The company commander positions engineers forward to provide a rapid assessment of the obstacle.
(8) The support force (if any) should be in position before the company's assault force reaches the assault position. The support element initiates its fire on the objective on order or at a specified time. Supporting indirect fires are synchronized to impact at the same time.
c. Isolate the Objective and the Selected Breach Site. Normally, the SBCT battalion isolates the objective area to allow the company (or companies) to concentrate its combat potential on the enemy strongpoint (Figure 4-13).
Figure 4-13. Isolate the objective.
(1) The company may begin the isolation during the leader's reconnaissance by positioning security elements to prevent enemy movement into or out of the objective area. The commander must ensure that these units understand what actions to take. Initially, they may only observe and report until the company deploys for the assault. At a designated time or signal, they begin active measures to isolate the objective.
(2) Once the company has isolated the objective area, the commander focuses on isolation at the breach point or point of attack. This isolation is to prevent enemy reinforcement at the breach site and also to suppress enemy weapons and positions that have observation of the breach site. The support force is assigned the main responsibility for this isolation.
(3) The commander masses all available combat power at the initial penetration or breach point. He uses indirect fires to suppress or obscure adjacent enemy positions and isolate them from the breach site.
d. Attack to Seize a Foothold. The breach of the enemy position is normally the SBCT infantry company's initial main effort. The breach force penetrates or bypasses the enemy's protective obstacles, gains a foothold in the trench line, and creates a gap large enough for the assault element to pass through (Figure 4-14).
Figure 4-14. Breach and secure a foothold.
(1) Preparations. A unit conducting a breach must be prepared to execute the following steps:
|
(2) Planning. In planning the breach operation, consider the following:
(a) The breach force moves forward by covered and concealed routes. If possible, the breach should be covert to reduce the time the breach and assault forces are exposed to enemy fire. If this is not possible or if the breaching attempt is compromised, the breach force moves under the suppressive fires of the support force.
(b) The penetration of the enemy position is made on a narrow front. The concept is to make a narrow penetration into the enemy defenses and then expand it enough to allow rapid passage of the assault force. Normally, the company concentrates all combat power at one breach point. It may use two breach sites, however, if they are mutually supporting and do not result in a lack of concentration or a piecemeal assault. When using only one breach site, the company should plan an alternate site as a contingency in case the primary breach is unsuccessful.
(c) The support force provides effective suppression for the breach and assault force(s) to cross the enemy's killing ground. Each weapon in the support element should have a specific enemy position or sector of responsibility assigned. Initially, the support force establishes fire superiority with a maximum volume of fire; they then maintain fire superiority throughout the attack. When indirect fires shift, the support force increases the rate of direct fire to maintain the suppression.
(d) The support force normally occupies one position to simplify control. At times, however, the support force must occupy several positions to provide effective suppression of the enemy. This may be required to prevent the masking of fires by the breach or assault force or because of the characteristics of the supporting weapons (120-mm/60-mm mortars). Also, the support force often needs to reposition once the assault force begins clearing the objective. They may follow the assault force through the breach or reposition outside the enemy position.
e. Exploit the Penetration and Seize the Decisive Point. After the successful breach, the assault force conducts the main attack (Figure 4-15). The assault force passes rapidly through the breach, supported by the fires of the support force and the breach force. In planning the assault, consider the following points:
Figure 4-15. Exploit the penetration.
(1) The assault force must reduce the enemy position as quickly as possible. If the assault force can capture or destroy the enemy's command and control facilities or other key positions and weapons, the enemy may surrender or abandon the position. If there is key terrain, this may be the decisive point for the assault force. Normally, the assault force moves within the enemy's trenches to avoid exposure to enemy fire.
(2) The assault force must also organize into support, assault, and breach elements. As it encounters subsequent positions or bunkers, it may have to repeat the breaching operations. As in the initial breach, the breach element establishes a support-by-fire position and conducts the same sequence of breaching and assaulting to reduce the position.
(3) The designation of a reserve allows the SBCT infantry commander to retain flexibility during the attack. The commander should be prepared to commit his reserve to exploit success and to continue the attack. The reserve also may repulse counterattacks during consolidation and reorganization.
(4) Once an assault starts, the company maneuvers aggressively to allow the enemy less time to react. The commander monitors the situation and adjusts the plan to exploit any weakness found during the attack. If a situation develops that is beyond the capability of his company, he notifies the battalion commander. He may have to hold his position until other companies can maneuver to support him.
(5) In moving from their assault positions, platoons advance in the formation most suitable to the terrain and situation. When the assault element must move through a narrow lane in the obstacles, it maintains dispersion and assaults through the lane by fire commands; signals should be coordinated to support this. The commander moves where he can best control his platoons and supporting fire. Indirect fire and the direct fires of the support force shift when they endanger the advancing soldiers.
(6) The assaulting soldiers clear enemy positions, secure and search prisoners, and move quickly across the objective. When they reach the far side, they take up hasty fighting positions and continue to fire at the withdrawing enemy. When the objective is secured and cleared (seized), the supporting elements and company trains are called forward.
(7) Once it seizes the objective, the company consolidates. Reorganization, if required, is normally conducted concurrently with consolidation and consists of actions taken to prepare for follow-on operations. As with consolidation, the SBCT infantry company commander must plan and prepare for reorganization as he conducts his troop-leading procedures. He ensures that the company is prepared to take the following actions:
|
4-36. ATTACK DURING LIMITED VISIBILITY
Successful attacks during limited visibility depend on leadership, reconnaissance, training, planning, and surprise. Although these fundamentals are also key to daylight attacks, attacks during limited visibility require certain considerations and the proper application of the techniques discussed in this chapter to ensure control in the attack. Darkness, fog, heavy rain, and falling snow limit visibility. Smoke and dust from high explosive (HE) fires also limit visibility, but their effects are more temporary. SBCT infantry companies attack during limited visibility--
|
a. Fundamentals. The SBCT infantry company, when equipped with NVDs, conducts limited visibility attacks very much like daylight attacks (Figure 4-16). The fundamentals for a daylight attack, discussed earlier in this chapter, still apply for night attacks. Conducting attacks in this manner requires--
|
Figure 4-16. Limited visibility attack with NVDs.
b. Challenges. When planning attacks at night, the SBCT infantry commander must consider the increased difficulty of--
|
c. Considerations. In planning limited visibility attacks, the SBCT infantry commander also should consider the following:
(1) Feints and other deceptions may be more effective. (This is true for the enemy also.)
(2) If a small element can infiltrate the enemy position, it can be extremely effective in supporting the main attack. A small element can also covertly breach obstacles or neutralize key positions and weapons to allow the main attack to seize a foothold quickly.
(3) It may be possible to infiltrate the main attack inside the enemy's positions and then fight from the inside to the outside. In this case, the unit inside the position may be able to occupy defensive positions and force the enemy to attack him.
d. Illumination and Indirect Fire. There are two basic decisions to be made for conducting limited visibility attacks:
|
(1) The infantry company normally conducts nonilluminated attacks to exploit its technological and training advantage. For all night attacks, however, illumination should be readily available in case the enemy detects the attack and uses illumination, or if he possesses NVDs. Illumination also may be effective to support reorganization and consolidation after the objective is secure, particularly for casualty evacuation.
(2) The infantry company conducts illuminated night attacks like daylight attacks. Illumination is available from artillery, mortars, M203s, and hand-fired and aircraft flares. Permission to fire illumination is often retained by battalion because the light may affect adjacent unit operations.
(3) Nonilluminated, nonsupported attacks offer the best chance of gaining surprise. These attacks are conducted like daylight attacks.
(4) Illuminated, supported attacks are almost identical to daylight attacks. These may be most effective when speed is essential, when there is limited time for reconnaissance, or when the enemy is weak or disorganized. When conducting these types of attacks, the attacking unit still attempts to use stealth and the concealment of limited visibility to gain surprise. They then initiate illumination and fires to support the assault.
e. Reconnaissance. Reconnaissance is critical in every attack, but especially for attacks at night. It should be conducted during daylight and down to the lowest level possible. Each SBCT unit should reconnoiter the routes on which they will move, the positions they will occupy, and the objective they are assigned. The company must balance the need for detailed information about the enemy against the risk of detection and loss of surprise.
(1) The reconnaissance plan should establish surveillance on the objective in case the enemy repositions units and weapons or prepares additional obstacles. Surveillance and security elements should secure critical locations, such as assault and support positions, the LD or PLD, and key routes and ORPs to protect the company from enemy ambushes and spoiling attacks. These security forces may become part of the isolation element during the attack.
(2) When reconnaissance is not successful due to lack of time, failure to identify critical aspects of the enemy's position, detection by the enemy, or any other reason, the commander should request a delay in the attack time to allow for further reconnaissance. If this is not possible, he should consider an illuminated or supported attack. A night attack with marginal information on the enemy's defense is very risky and difficult to conduct successfully.
f. Simplicity. A simple concept, particularly for the actions on the objective, also supports control during the assault. If possible, SBCT platoon and squad objectives should be small and easily identified.
(1) Avoid developing a concept that requires the company to fight for each enemy fighting position. As in a daylight attack, identify a decisive point and focus combat power at this location. Once the decisive action is accomplished, the plan must also address any remaining enemy. If required by the higher commander's concept or for an effective consolidation, the company may have to clear all enemy forces from the objective area.
(2) A smaller assault force maneuvering on the objective is easier to control and less likely to suffer casualties from enemy or friendly fires. The assault force must have clear signals to ensure control of all supporting fires, both direct and indirect.
(3) The concept for a nonilluminated attack should be flexible to allow for adjustment to a daylight attack if illumination becomes appropriate due to detection by the enemy or the use of illumination by an adjacent unit. This is especially critical for a unit that plans a modified linear assault attack but may be forced to conduct an illuminated attack. A contingency plan that reorients for illumination should be prepared and issued, and every soldier should know under what conditions to execute this plan. In some cases (when already deployed through the PLD and advancing on the enemy, for example), the company may have no choice but to continue the attack as planned or attempt to disengage.
g. Fire Control Techniques. Fire control techniques for limited visibility include--
(1) Tracer Fire. Leaders in the assault force fire all tracers; their men fire where the leader's tracers impact. The support force positions an automatic weapon on a tripod on the flank nearest the assault element. This weapon fires a burst of tracers every 15 seconds to indicate the near limit of the supporting fires. All other weapons in the support force keep their fires on the side of this tracer away from the assault force. The assault force signals to shift fires to the next position or to a set distance. If required, these rounds can be adjusted well over the head of the assault force to preclude casualties.
(2) Luminous Tape or Chemical Lights. Mark assault personnel to prevent fratricide. Do this in a way that avoids enemy detection, such as luminous tape on the back of the helmet or small infrared chemical lights (if the enemy has no NVDs). The support force should know where the lead assault force is. If individual soldier markings do not suffice, use large chemical lights (infrared [IR] or visible). Place these on the ground or throw them in front of the assault force. When clearing a trench line, put the lights on a stick and move them with the lead element.
(3) Weapons Control Restrictions. Assign weapons control restrictions to reduce the risk to the assault force.
(a) The platoon on the right in the assault might be given weapons free to the right flank, because there are no friendly soldiers there, but weapons tight or hold on the left because another friendly unit is located there.
(b) The assault force may be restricted to using only shotguns and pistols.
(c) The assault force may be restricted to no automatic weapons fire on the objective. This ensures that all automatic weapons in use are enemy.
(4) Other Techniques. Use the following techniques to increase control during the assault:
|
h. Supporting Fires. Mortar, artillery, and antiarmor fires are planned for a night attack much like in a daylight attack. However, they do not fire unless the SBCT infantry company is detected or until the company is ready to assault. Some weapons may fire before the attack and maintain a pattern to deceive the enemy or to help cover noise made by the company's movement. This is avoided if it will disclose the attack.
(1) Indirect fire is difficult to adjust when visibility is poor. If doubt exists as to exact friendly locations, indirect fire is directed first at enemy positions beyond the objective and then walked onto the objective. The illumination rounds may be fired to impact on the ground, providing both light and markings on the objective. They may also be placed behind the objective and in the air, causing the enemy to be silhouetted. Once illumination is begun, it should continue until the objective is secure. Sufficient ammunition must be available.
(2) Smoke is planned to further reduce the enemy's visibility, particularly if he has night vision devices. The smoke is laid close to or on enemy positions to avoid restricting friendly movement or hindering the breaching of obstacles. Employing smoke on the objective during the assault may make it hard for assaulting soldiers to find enemy fighting positions, but if sufficient thermal sights are available, using smoke on the objective may provide a decisive advantage for a well-trained unit.
(3) Illumination is always planned for attacks to be conducted in limited visibility. That gives the company commander the option of calling for it. The battalion commander normally controls illumination but may authorize the company commander to call for it when needed. If the company commander decides to use illumination, he should not call for it until the assault is initiated or the attack is detected. It should be placed on several locations over a wide area to confuse the enemy as to the exact location of the attack. It also should be placed beyond the objective to help assaulting soldiers see and fire at withdrawing or counterattacking enemy soldiers.
(4) Illumination also may be required if the enemy uses illumination to disrupt the effectiveness of the company's NVDs. Once used, illumination must be continuous because attacking soldiers will temporarily lose their normal night vision. Any break in illumination also may reduce the effectiveness of suppressive fire when the attackers need it most. Care must be taken to ensure that the squad and platoon leaders do not use hand flares before the commander has decided to illuminate the objective.
(5) The thermal sights of weapons (such as the Javelin) may be employed strictly for observation if there are no targets for these weapons to engage. Positioned outside the objective area, these sights can provide critical current information. They also can assist the support force in controlling their fires or provide the assault force with reports of enemy movements on the objective.
(6) When limited NVDs are available, they must be prioritized and employed at the most critical locations. Priorities to consider include key soldiers in the breach force, key leaders in the assault force, other members of the assault force, and key leaders and weapons in the support force.
i. Consolidation and Reorganization. When it has seized the objective, the SBCT infantry company consolidates and reorganizes. Consolidation and reorganization are the same as for a daylight attack with the following exceptions:
(1) Guides lead trains and support elements forward to their positions.
(2) The consolidation plan should be as simple as possible. Avoid changes in task organization.
(3) Locating and evacuating casualties and enemy prisoners of war (EPWs) takes longer. They may have to be moved to the rear of the objective and kept there until visibility improves.
(4) Platoon positions are closer together to ease control and improve mutual support. Position distances are adjusted as visibility improves.
j. Modified Linear Assault. The modified linear assault is a technique for conducting a nonilluminated attack without NVDs to seize an occupied objective. This technique is effective in controlling the fires of the assault force by maintaining a linear formation. Each soldier assaults using individual movement techniques while remaining generally "on line" with the soldier on his right and left. Each soldier is able to engage or suppress targets to his front with fewer restrictions because there is less chance of fratricide.
(1) Modifications. In the true linear assault, the company deploys through its respective squad release points RPs), and the entire company conducts a linear assault across the objective (Figure 4-17). To reduce the vulnerability of the assault force, this technique is normally modified, which may be done in a number of ways depending on the situation.
Figure 4-17. Linear assault.
(a) The most effective modification is to establish part of the company in a support-by-fire position. The remainder of the company deploys at the PLD and conducts the assault (Figure 4-18). Machine guns, mortars, and Javelins are normally most effective in this role. M203s also may be effective if visibility is sufficient for their employment. It is essential that the flank of the assault force nearest the support force be visible to the support force. The fire team on this flank may mark themselves with chemical lights or glint tape to ensure they are visible.
Figure 4-18. Linear assault with support element.
(b) Other variations of this technique may include attacking on a much narrower front with a smaller assault force and having a large follow-and-support force. For example, instead of two platoons deploying at the PLD, a platoon(-) could deploy against an identified enemy weak point (Figure 4-19). This platoon could be tasked to bypass enemy positions to seize or destroy a critical location or facility quickly, with the follow-and-support force reducing bypassed positions. Another variation is to assign the assault force a shallow objective to support the forward passage of the trailing unit, or to deploy through the platoon release points and then to attack in squad files. The latter is most effective when the situation supports an infiltration through the enemy defenses to seize decisive terrain or positions to the rear.
Figure 4-19. Linear assault with follow and support.
(2) Advantages. The modified linear assault simplifies the control of supporting fires from outside the objective. By establishing support positions perpendicular to the direction of assault, the supporting fires can be employed next to the assault force and then shifted in front of them as they advance.
(3) Disadvantages. The linear formation is the biggest weakness with the modified linear assault. If the enemy is in well-prepared defensive positions, the linear formation ensures at least part of the assault force attacks through the enemy's kill zones. Also, assaulting using this technique makes it very difficult for the leader to concentrate combat power against an identified enemy weakness. Finally, if the enemy has NVDs or the assault force runs into unidentified obstacles after deploying at the PLD, fire superiority may not be achieved and the assault will rapidly come to a halt. This may result in the majority of the company being decisively engaged in the enemy killing ground.
(4) Conduct of the Assault. Although there are significant difficulties with the modified linear attack, it remains a viable technique for attack during limited visibility by units without NVDs. It is most effective against a weak or disorganized enemy. If the enemy has NVDs or a well-prepared defense with protective obstacles, this technique should not be used. An illuminated, supported attack that is conducted as a daylight attack may be the most effective option in that situation.
(a) Before attacking in this manner, the SBCT infantry company should secure the PLD and provide personnel to guide the company from the LD to the PLD. Each platoon provides personnel to secure their portion of the PLD and to guide the platoon from the platoon release point (RP). These soldiers are briefed on the routes from the LD to the platoon RP, actions on enemy contact, time of departure, and other information needed by the patrol units to conduct their mission. They move forward to the platoon RP; then they move forward to reconnoiter and mark the platoon routes, secure their respective parts of the PLD, and observe the objective. The platoon guides go back to the platoon RP to guide their platoons to the squad RP and to the PLD.
(b) Once the company crosses the LD, movement to the PLD is continuous. They move slowly to maintain stealth. Platoons are released at the platoon RP so they can deploy before reaching the PLD. Once their units are deployed, the platoon leaders and the support element leader notify the commander. When the company is fully deployed, the commander informs the battalion commander. On the battalion commander's order, the company moves silently forward from the PLD. The platoons guide on the base platoon.
(c) When the attack is discovered, or on the commander's order, the support element opens fire and the platoons assault. Leaders must recognize that this technique for conducting a limited visibility attack results in a linear assault. To be successful, the assault must achieve surprise and rapidly overwhelm the defender. If the initial assault fails, it is difficult to regain control. Scattered enemy fire must not be taken as a loss of surprise, and it should not be cause to start the assault.
(d) Soldiers assault aggressively using individual movement techniques to maneuver. The support force must quickly gain fire superiority with a heavy volume of fire. Tracers are used to improve accuracy, to control fires, and to allow the assault force to see where its supporting fires are impacting. The FIST calls for indirect fire around and beyond the objective to disrupt enemy reinforcement. As the assault closes on the objective, fires are shifted beyond the limit of advance or lifted entirely. Soldiers must not go beyond the limit of advance.
(e) If the enemy discovers the attack before the company reaches the PLD, the commander may--
|
|
NOTE: |
A linear assault, even a modified variation, is very risky when conducted under illumination. |
Section IX. COMMON OFFENSIVE ACTIVITIES
These activities are the warfighting actions the SBCT infantry rifle company may be called upon to perform in battle.
4-37. INFILTRATION
Infiltration is a form of maneuver used by infantry units in many situations. During an attack, strong enemy defensive positions may be encountered. To avoid the enemy's strength, the SBCT infantry commander may place his ICVs and other vehicles in a secure location and move dismounted by stealth through gaps or around enemy positions to conduct operations in the enemy's rear area. The company may infiltrate to conduct raids, ambushes, or other attacks. The company may also use infiltrations for many other types of operations, such as stay-behind and reconnaissance.
a. Fundamentals. By infiltrating, the SBCT infantry company can maneuver to critical targets undetected, can achieve surprise, and can avoid the effects of enemy fires. Limited visibility, bad weather, and restrictive terrain reduce the chances of detection during an infiltration.
(1) A unit may infiltrate--
|
(2) The steps of an infiltration are as follows:
(a) Patrol. Find gaps or weak areas in the enemy defense and locate enemy positions. The SBCT company may conduct patrols, but RSTA assets are more likely to conduct them.
(b) Prepare. Conduct troop-leading procedures.
(c) Infiltrate. Avoid enemy contact; move by smallest units possible.
(d) Consolidate. Link up and prepare for actions at the objective.
(e) Execute. Complete the mission.
(3) Infiltrations do not always require that all units move through the enemy's positions without detection or contact. Depending on the mission, the company can still complete the mission even though some of the squads make contact en route to the linkup point. Although the enemy may have some idea of what is taking place, it is very difficult for him to estimate exactly what these small contacts mean. OPSEC may require that only key leaders have the entire plan during the infiltration step to prevent disclosure due to casualties or friendly prisoners.
b. Considerations. The SBCT infantry company commander must prepare an infiltration plan and give units enough time for preparation and movement. The company may infiltrate by itself or as part of the SBCT battalion. In either case, movement techniques and formations are based on the likelihood of enemy contact, the terrain, the level of visibility, and the need for speed and control.
(1) Size. The size of the infiltrating unit depends on the amount of time available, the amount of cover and concealment, and the enemy. Other considerations may include the need to communicate, the difficulty of navigation, the number of infiltration routes, and whether or not to take vehicles. Generally, smaller units can move more quickly and make better use of available concealment, but they may increase the number of linkups, requiring more time. Infiltrating by company or platoons ensures control and provides more combat power in the event of contact.
(2) Infiltration Lane. The company may be assigned an infiltration lane or zone. The company commander must decide whether to move the entire company together through the company's lane or to assign each platoon a separate infiltration lane within the company lane. He also has the option to stagger the start time for each platoon on the one company lane. The infiltration lane should be wide enough to allow the infiltrating units to change their planned routes to avoid enemy contact. If the company uses a single company lane (Figure 4-20), the company commander picks a route through it and a company ORP. If the company commander uses multiple lanes (Figure 4-21), the company commander assigns each platoon a lane and a start time, picks linkup points for the platoons, and picks a company ORP. The platoon leaders pick the routes through their lanes. In making his decision whether to use single or multiple lanes, the company commander considers several things.
(a) Moving as a company on a single lane--
|
(b) Moving on multiple lanes or by platoons on one lane--
|
Figure 4-20. Company moving on single infiltration lane.
Figure 4-21. Company moving on multiple infiltration lanes.
(3) Routes. The routes selected must avoid enemy positions, use the best available cover and concealment, ease control and navigation, and avoid obstacles and danger areas.
(a) Routes should be reconnoitered without alerting the enemy. This may be possible by using RSTA assets within the SBCT; however, leaders should consider using a map reconnaissance or guides, or marking the routes.
(b) Rally points may be selected based on the reconnaissance assets available to the commander; others are selected as the company moves along the route. If the infiltrating company is dispersed by enemy action, it rallies at the last rally point passed that is not within enemy small-arms range. The assembled unit then waits until a set number of units or soldiers arrive at the rally point, or until a specified time, before continuing the mission. The senior man at the rally point should, in the absence of the commander, assume command and decide how best to continue the mission within the commander's intent.
(c) Locate the ORP as close to the objective as possible without being detected or losing security. The ORP should be large enough so that the company can deploy in it. It should be cleared before it is occupied.
(4) Linkup Point. When using multiple lanes, the platoons meet at a linkup point and then move as a company to the ORP. Do not plan linkups at the ORP. If a unit misses its linkup, it moves to a contingency linkup point located away from the ORP and links up with a small element from the ORP.
(5) Signals. Visual signals, such as arm-and-hand signals, infrared devices, and flashlights with colored lenses, reduce the chance of detection. Avoid sound signals and flares. Recognition signals are critical for actions at a linkup or rally point.
(a) Radio listening silence should be enforced, except when a unit must report its progress or when a unit detected by the enemy needs supporting fire.
(b) Radio messages to report crossing of phase lines or checkpoints (if required) should be brief--one code word. They may be transmitted without using call signs to identify units, providing each unit has separate code words.
(c) When required, units operating out of radio contact (because of terrain or distances) can monitor or send codes only at a certain time. At these times, they set up expedient antennas or move to terrain better suited for communication.
(6) Fire Support. Indirect fires are always planned but are used only when contact is made or when needed to support the mission. If contact is made with an enemy element, the infiltrating unit should use indirect fire to divert the enemy's attention, suppress enemy positions, and screen friendly movement as they disengage. Indirect fires may also be used to assist in navigation and to cause enemy soldiers on security to seek cover.
(7) Actions on Contact. When infiltrating on multiple lanes, detection of one infiltrating unit may alert the enemy and compromise the other infiltrating units. The company OPORD must state whether to continue the mission or return to friendly lines if detected by the enemy. Units following on the same lane should switch to an alternate lane. If a soldier in the unit speaks the enemy's language, he should be positioned at or near the front of the column in case an enemy OP or patrol challenges the unit. The order also must specify what to do in the event of casualties.
(8) Methods of Handling Casualties and Prisoners. During the infiltration, it may be hard to evacuate casualties or move prisoners without jeopardizing security. Casualties can be carried to the ORP or linkup point and evacuated when the operation has ended, or they can be concealed and left for pickup later. Moving casualties or prisoners to the ORP is dangerous when trying to avoid detection. Soldiers with medical supplies stay with any casualties left behind. The killed in action (KIA) can be concealed and recovered later. Leave prisoners under guard at a rally point and evacuate them when the operation is over.
(9) Rehearsals. Every soldier must know the plan and his role in it. Units should rehearse their formations, their movement techniques, and their actions--
|
4-38. OVERWATCH
Overwatch is the component of tactical movement in which an element observes and, if necessary, provides direct fire support for a friendly moving element. Situational understanding of the tactical environment is crucial for the overwatch unit, whose objective is to prevent the enemy from surprising and engaging the moving unit. The overwatch force must maintain communications with the moving element and provide early warning of enemy elements that could affect it. The overwatch must be able to support the moving element with immediate direct (to include dismounted antiarmor fires) and indirect fires; it can do this in either bounding overwatch or traveling overwatch. The key to successful overwatch is aggressive scanning of gaps and dead space within the moving element's formation and on surrounding terrain. If the overwatch is unable to scan gaps and dead space and effectively engage the enemy, it must alert the moving element of the lapse in coverage. The moving element normally adjusts its movement speed, formation, or both, and initiates its own overwatch until the overwatch force completes movement to a position from which it can continue the overwatch mission.
a. Bounding Overwatch. The overwatch element occupies firing positions that afford effective cover and concealment, unobstructed observation, and clear fields of fire. The leader of the overwatch element (such as the SBCT infantry commander, platoon leader, or section leader) assigns sectors of observation and fire. The overwatch element is responsible for its own security during both occupation of the overwatch position and execution of the operation. A common security measure is to clear the position with the infantry prior to occupying with the vehicles.
(1) Squads or platoons scan their assigned sectors to identify enemy elements and positions. The leader must structure the mission so the overwatch element can effectively scan for known or likely enemy positions, paying close attention to possible gaps and dead space. The overwatching element must have a clear understanding of the enemy situation so soldiers know what to look for and where to look. They use applicable search techniques and employ all available sights and other visual devices (such as binoculars and night vision goggles).
(2) If contact is made, the overwatch element initiates a high volume of direct fires. It moves between primary and alternate positions as necessary to avoid being decisively engaged by the enemy.
b. Traveling Overwatch. While maintaining its location in the overall unit formation, the overwatch element (usually a platoon or section) continuously scans the lead element's battle space and closely monitors all potential gaps and dead space. The overwatch maintains a specified interval from the lead element; this interval is dictated by weapons capabilities and the effects of terrain and movement speed. As needed, the overwatch can execute short halts to provide more effective observation, facilitating acquisition of enemy forces.
4-39. FOLLOW AND SUPPORT
Follow and support forces are employed in the offense to maintain the momentum of an operation. They do this by providing support or assistance that relieves the lead element of hindrances that could slow its advance. Follow and support missions are usually assigned when the enemy situation is vague and speed of the operation is important.
a. The SBCT infantry company may be task-organized to conduct follow and support missions in one of several ways:
|
b. Follow and support operations may require the company to conduct a variety of tactical tasks, including the following:
|
c. The follow and support force receives information on the enemy or the supporting tasks from the lead element's fixing or overwatch force.
d. The follow and support force conducts linkup with the fixing force on the ground, completes the exchange of critical tactical information, and accepts responsibility for the assigned tasks. The fixing force then rejoins the lead element, and the follow and support force executes its tasks. If enemy contact occurs, the follow and support force conducts actions on contact as outlined earlier in this chapter.
4-40. BYPASS
The company may bypass an enemy force or obstacle to maintain the momentum of the attack or for another tactical purpose. The SBCT battalion commander often establishes bypass criteria.
a. The SBCT infantry company commander designates a fixing force to maintain contact with the enemy and assist the remainder of the company during the bypass. This fixing force may not come into direct fire contact with the enemy force.
b. The bypassing force uses covered and concealed routes and, if possible, moves along bypass routes that are outside the enemy's direct fire range. If the situation dictates, the company can also employ smoke to obscure the enemy or to screen the bypassing force's movement. The company must conduct adequate reconnaissance of the route to confirm the feasibility of the bypass; the enemy may intentionally leave a bypass route unguarded to draw attacking forces into his kill sacks.
c. Once the rest of the SBCT infantry company clears the enemy position, the fixing platoon normally hands the enemy over to a supporting force, breaks contact, and rejoins the company. The fixing platoon may be attached to the follow-on force, but this is unlikely.
4-41. CLEAR AN OBJECTIVE
The company may be tasked with clearing an objective area during an attack to facilitate the movement of the remainder of the SBCT battalion or with clearing a specific part of a larger objective area. Situations in which the SBCT infantry company may conduct the tactical task CLEAR include the following:
|
a. Terrain Factors. The commander must take several important terrain considerations into account in planning and executing the task CLEAR. These factors include obstacles, avenues of approach, key terrain, observation and fields of fire, and cover and concealment:
(1) Obstacles. Obstacles influence the maneuver of any vehicle entering the objective area. The narrow corridors, trails, or roads associated with restricted terrain can be obstructed easily with wire, mines, and log cribs.
(2) Avenues of Approach. Avenues of approach are limited. Consider the impact of canalization and estimate how much longer it will take to clear the objective area.
(3) Key Terrain. Key terrain may include areas that dominate the approaches or exits for the objective area as well as any terrain that dominates the fight inside the defile, wooded area, or built-up area.
(4) Observation and Fields of Fire. Observation and fields of fire favor the enemy. The attacking force must neutralize this advantage to be successful. Identify dead space where the enemy cannot see or engage friendly forces. In addition, identify multiple support by fire positions; these are necessary to support a complex scheme of maneuver that covers the company's approach, the actual clearance task, and maneuver beyond the restricted terrain.
(5) Cover and Concealment. Cover and concealment are normally abundant for dismounted infantry elements but scarce for vehicles. Lack of cover leaves vehicles vulnerable to enemy antitank guided missile (ATGM) fires.
b. Enemy Situation. Careful analysis of the enemy situation is necessary for success. The enemy analysis should include the following elements:
|
c. Clearing in Restricted Terrain. Clearing in restricted terrain is time-consuming and resource-intensive. During the planning process, the SBCT infantry company commander evaluates the tactical requirements, resources, and other considerations for each of the three steps of the operation:
|
(1) Approach. The approach focuses on moving combat power into restricted terrain and posturing it to begin clearing. The company commander takes the following actions:
(a) Establishes support-by-fire positions; destroys or suppresses any known enemy positions to allow forces to approach the restricted terrain.
(b) Provides additional security by incorporating suppressive indirect fires and obscuring or screening smoke.
(c) Provides support by fire for the dismounted infantry. Be prepared to cover infantry elements from their dismount points to the points at which they enter the restricted terrain such as high ground on either side of a defile, wooded areas on either side of a trail or road, or buildings on either side of a road in a built-up area.
(d) Moves dismounted infantry elements along axes that provide the best available cover and concealment. The approach ends when the infantry elements are prepared to conduct an attack.
(2) Clear. The clearing begins as the infantry squads begin their attack in and around the restricted terrain.
(a) Locations where this maneuver may take place include the following:
|
(b) The following actions and considerations are applicable during this step:
|
(3) Pass Friendly Forces. The SBCT infantry company may be directed to assist the passage of another element forward to continue the clearing. When clearing is complete, the company must be prepared to take any action necessary to pass friendly forces, such as the following:
|
4-42. THE COMPANY AS A RESERVE
The company may be held as the SBCT battalion reserve during an attack. The SBCT infantry battalion commander commits the reserve to decisively influence the action and to maintain the momentum of the attack. To exploit the success of the other attacking SBCT infantry companies and to achieve surprise, the reserve should attack the enemy from a new direction. Because of the various missions that the reserve may be assigned, the reserve commander must keep abreast of the tactical situation, know the missions and the tactical plans of the other companies, and be familiar with the terrain and the enemy situation in the objective area. The reserve must act quickly and effectively when committed. The reserve may be assigned one or more of the following tasks as part of its be-prepared missions:
|
4-43. SECURITY OPERATIONS
The battalion may assign the SBCT infantry company commander a security mission, such as to screen or guard another friendly unit or asset. This may be part of the SBCT battalion counterreconnaissance mission (FM 3-21.21 [FM 7-22]). The company commander may also assign one of these tasks to his platoons as part of his scheme of maneuver. Security operations require the unit to orient on the friendly forces to prevent enemy forces from detecting, observing, and engaging. The commander analyzes the situation and develops his plan as in any tactical situation. Refer to Chapter 7 for detailed discussion of security operations.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|