Appendix C
Communications Security Operations
This appendix gives an overview of COMSEC operations.
SECURE COMMUNICATIONS |
|
| C-1. The MSE network provides secure voice and data communications up to the SECRET level with special provisions for TOP SECRET/sensitive compartmented information (TS/SCI). This is accomplished by using a combination of physically protected wire lines and cryptographic equipment. | |
| Note: When exchanging classified communications with a subscriber outside the MSE system but interfaced with MSE, MSE subscribers should ensure the distant user is communicating within an approved protective communications configuration. |
| PROTECTED WIRE LINES | |
| C-2. Wire lines between subscribers and MSE switchboards are considered approved loops. Operators and users must monitor these wire lines to ensure only authorized subscribers access the network. | |
| CRYPTOGRAPHIC SECURITY | |
| C-3. Overall cryptographic security is the result of netted protection in trunk, orderwire, switch, and subscriber areas. Table C-1 describes equipment architecture and lists equipment allocations. | |
| Trunk | |
| C-4. Throughout the system, TEDs (KG-194/A) encrypt DTGs for transmission between switches. | |
| Orderwire | |
| C-5. The VINSON (KY-57) and the orderwire control unit (OCU) or communications modem (CM) provide secure, half-duplex communications to radio and cable links. The system also provides over-the-air rekey (OTAR) for MSE assemblages. | |
| Switch | |
| C-6. The automatic key distribution center (AKDC) (KGX-93A) provides the generation, storage, and transfer of COMSEC keys. Loop key generators (KG-112s) provide secure communications between the NC/LEN and MSRTs/wire line DSVT. They also protect the transfer of keys between NCs and LENs. | |
Table C-1. COMSEC Equipment Allocations
Assemblage/COMSEC Equipment |
NCS |
LENS |
SENS |
RAU |
LOS |
MSRT |
AKDC, KGX-93A |
1 |
1 |
|
|
|
1 1 1 |
|
1 Has provisions for the KY-90. 2 Two per signal battalion. |
||||||
| Subscriber | |
C-7. The MSRT consists of an RT-1539(P)/G radio, mobile COMSEC unit (MCU), and a DSVT (KY-68). The X key overrides the M key and secures the signaling between the NCS and the DSVT. It does not encrypt the voice traffic transmission. The DSVT secures the connection to the NC/LEN. The SDNRIU (KY-90) provides a secure link between the MSE system and the secure CNR nets. C-8. Additional crypto devices are allocated for generation, storage, transfer, and verification of crypto keys (see Table C-1). |
|
| NET CONTROL DEVICE (NCD) | |
| C-9. The NCD (KYX-15) is used at NCSs and LENSs and stores 16 keys. | |
| ELECTRONIC TRANSFER DEVICE (ETD) | |
| C-10. The ETD (KYK-13) is used at all other locations and can store six keys. | |
| SMART FILL DEVICE | |
| C-11. The smart fill device (KOK-12 or KOK-16) is used for COMSEC key management at signal brigades and battalions. The KOK-12 or KOK-16 can identify COMSEC keys by displaying the assigned key tag number on its liquid crystal display (LCD) screen. The KOK-12 or KOK-16 can also store and transfer up to 160 COMSEC keys. | |
EQUIPMENT USE |
|
| C-12. The SCC-2 COMSEC key manager controls key management and distribution within the corps. He directs the PNS to generate all system common and user keys. Then, through a courier distribution system, certain keys are pre-positioned to leader NCs within the corps. Leader NC key managers, in turn, distribute a pre-positioned set to their supported NC/LENs. Each master NC/LEN link generates the unique TED internodal keys. The leader NC key manager directs the bulk transfer of these keys to the slave NC/LENs. Once the backbone network is stable, the SCC-2 COMSEC key manager directs the bulk transfer of all keys to each leader switch that does the same for their supported NC/LENs. Unit couriers pick up user keys from the corps key manager.
C-13. All key transactions except bulk transfer are recorded manually on COMSEC key management logs and reported through the distribution channels. Bulk transfer transactions are recorded automatically in each NC/LEN database and can be retrieved if necessary. Trunks are bulk encrypted through the TED (KG-194/A). C-14. The Army Key Management System (AKMS) program consists of two systems that provide cryptographic keys, SOIs, and fills for CNRs. The Automated COMSEC Management and Engineering System (ACMES) software resides on laptop computers and is used by both theater and tactical units. The Army Electronic Generation and Distribution System (AEGADS) software resides on desktop computers and is used by strategic and sustainment base units. Both systems use automated net control devices (ANCDs) and key distribution devices (KDDs) to distribute SOIs and COMSEC variables and keys. The AKMS greatly reduces current dependence on paper-based keying materials. C-15. Switch COMSEC functions include generating, storing, transferring, and activating COMSEC keys and providing traffic encryption. This is done in the NCS (LENS in an emergency only) using the LKG, AKDC, and TED during the key generation, distribution, and activation phases. The AKDC in the NCS generates, transfers, and activates keys. The AKDC is driven by software commands using the video display unit (VDU). The operator can also generate and transfer keys directly from the AKDC. Electronic keys are stored in the HUS. The HUS can store up to 512 variables (256 active and 256 reserve). The LKGs in the NCS and LENS provide key control and key transfer to support end-to-end encryption for DSVT subscribers on a per-call basis. C-16. MSRT/subscriber COMSEC functions operate through a key loaded MCU within the RT-1539(P)/G radio and embedded COMSEC within the DSVT. Subscriber COMSEC functions include encrypting radio frequency signaling using the MCU. The DSVT COMSEC encrypts the subscriber's traffic. COMSEC protection at the secure subscriber level begins with the COMSEC keys. The subscriber's ETD (KYK-13) electronically loads the keys into the radio's MCU and the DSVT. C-17. The analog engineer orderwire (EOW), inherent in each LOS radio, is used only for initializing the system. The orderwire is not encrypted and should only be used for unclassified traffic. After establishing the link, the operator switches to the DVOW. The orderwire voice is then encrypted through the VINSON (KY-57) located in the NCS, SENS, LENS, RAU, and LOS assemblages. The DVOW is also used for OTAR or transfer of COMSEC keys. However, this method is only used on an exceptional basis. When using the encrypted DVOW, traffic is not to exceed the SECRET level. When using DVOW for OTAR, a key encryption key (KEK) is used to pass the key. |
|
KEY DESCRIPTION, DISTRIBUTION, INITIALIZATION, AND ACCOUNTABILITY |
|
| C-18. The AKDCs generate keys (except the S key) for the MSE system. Table C-2 lists the different types of keys. It also identifies the key, its use (such as subscriber's KY-68), the type of numeric or key encryption, its distribution, and a short description. | |
| DISTRIBUTION | |
| C-19. The courier method is used for initial key distribution. The S key distribution is a user responsibility. Used with the KOI-18s and KOK-16s, properly cleared personnel physically deliver electronic keys. Reliance on courier delivery will decrease as the AKMS is fielded.
C-20. The bulk transfer method results in the electronic transfer of keys from the designated HUS location(s) of one AKDC to the same type of HUS location(s) of another AKDC. C-21. The OTAR method transfers keys to various assemblages. The DVOW encrypts the keys by using remote keying encryption (K key). Used with the NCD (KYX-15), the KY-57 can transfer keys to another KY-57 or to an ETD (KYK-13). C-22. The electronic method is an operation, transparent to users, that downloads the X and V keys to the DSVT (using the U key). C-23. The PNS generates corps common system operational keys. |
|
| INITIALIZATION | |
| C-24. The division COMSEC material direct support activity (CMDSA)/DCOR stores the pre-positioned keys required for system initialization. On deployment, the trunk key establishes internodal links and the master switch is the controlling NCS. Once the TN key is loaded in each TED, the link is activated.
C-25. The COMSEC key manager oversees the generation of all COMSEC keys. He stores and distributes the keys to teams before deployment. Tables C-3 through C-7 show the appropriate key sets. |
|
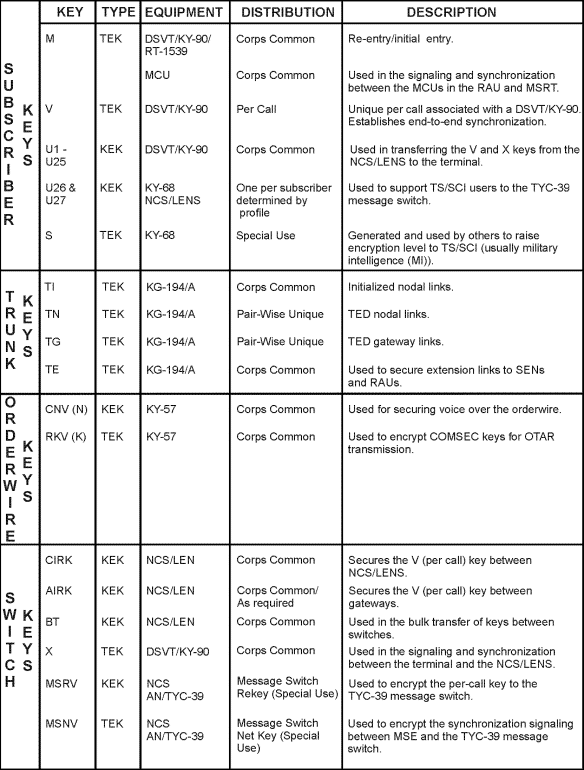
Table C-3. NC Key Set
KEY |
USE |
TI |
TED |
AIRK |
As Required |
CNV |
FM |
Table C-4. LEN Key Set
KEY |
USE |
| TI BTc N K U |
TED |
CNV |
FM |
Table C-5. SEN Key Set
KEY |
USE |
TE |
TED |
M |
KY-90 (if required) |
CNV |
FM |
Table C-6. RAU Key Set
KEY |
USE |
TEc |
TED |
CNV |
FM |
Table C-7. Subscriber Key Set
KEY |
USE |
M * |
DSVT (LD(X)) |
| * I = U Net ID. |
| C-26. The PNS directs initial start-up. The SYSCON switch technician assumes COMSEC key management tasks once the system is activated. | |
| Predeployment | |
|
|
Deployment |
|
|
|
| ACCOUNTABILITY | |
C-27. The MSE system requires key accountability for all key generation, transfer, and activation. The accountability process helps the manager accurately determine where the keys are maintained throughout the network. Accountability is accomplished through a combination of SCC-2 project screens, messages, and log entries. C-28. Project screens within the SCC-2 display the cryptographic state of the network. Whenever a COMSEC project is approved, a record is created on the logbook teletype. C-29. At the NCSs and LENSs, three screens allow the node COMSEC OIC to-
|
|
3-30. Manual transfer of keys requires marking the fill device and creating and recording information on a log entry. 3-31. COMSEC key records (classified CONFIDENTIAL) are maintained for an appropriate period and then destroyed. |
|
| TASK ORGANIZATION | |
C-32. If task organization requires attaching units not previously aligned, all corps common keys and gateway keys must be either physically or electronically transferred (through secure means) to establish communications. (See Table C-1.) |
|
AUTOMATIC KEY DISTRIBUTION CENTER |
|
C-33. The AKDC houses all the keys generated at the NCS/LENS. Table C-8 shows an example of HUS locations and key tag assignments. Keys have A and B locations. The active key is on side A and the reserve key is on side B. SYSCON may authorize storing keys other than those listed. |
|
Table C-8. Example of HUS Locations and Key Tag Assignments
KEY TAG |
HUS |
USE |
|
C001 U003 K028 N029 B032 T100 A126 M224 X225 |
001 002 003 028 029 032 100 126 224 225 |
257 |
CIRK |
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

