|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 6
ELECTRONIC WARFARE (EW) ASSET DEPLOYMENT
| CRITICAL TASKS: | 301-35D-2053 301-35D-2602 301-35D-3007 301-340-3001 |
OVERVIEW
LESSON DESCRIPTION
In this lesson you will learn how to plan for EW support of a combat operation and how to deploy EW assets on a map in support of a given plan.
Terminal Learning Objective:
| Tasks: | Describe the planning for EW support of an offensive combat operation and the deployment of EW assets on a map in support of a given plan. |
| Conditions: | You will be given narrative information and illustrations from FM 34-1, FM 34-10, and FM 100-5. |
| Standards: | Description of EW assets deployment will be in accordance with FM 34-1, FM 34-10, and FM 100-5. |
| References: | The material contained in this lesson was derived from the following publications: FM 34-1FM 34-10 FM 100-5 |
INTRODUCTION
Planning is crucial to the success of EW operations. The effectiveness of EW is dependent on the degree to which it is integrated with the commander's scheme of fire and maneuver. Full integration is best achieved by systematic planning and full understanding of employment factors. IPB is used throughout EW planning. Templates are used to focus EW operations on identified high value target, to determine defensive EW measures to defeat enemy counter-C3 efforts, and to predict good intercept site locations for ES assets. By using graphics in the form of map overlays, IPB provides a detailed analysis of terrain. Those aspects of terrain analysis which effect most EW operations are essentially the same as those of primary concern to other combatants. These aspects of terrain are elevation and relief (key terrain), obstacles, radio LOS (observation and fields of fire), concealment and cover, and mobility corridors (avenues of approach).
PART A: EW PLANNING AND DEPLOYMENT.
The bedrock of sound offensive plans is the ability to find the enemy and accurately predict his future actions. Intelligence drives offensive operations by locating the enemy, predicting his courses of action, and identifying his vulnerability and his center of gravity. Simultaneously, intelligence must help protect friendly information, while aiding the attack of enemy information collectors.
When supporting offensive operations, intelligence must provide the commander information and intelligence that allows him to make informed and timely decisions, reduce uncertainty, and accurately engage high payoff targets. The primary wartime objective of U.S. Army divisions is to aggressively seek out and destroy the enemy. To do this, divisions must use offensive operations. The offense has been and always will be the decisive form of battle. However, as technology increases, the face and nature of offensive operations also will change. In the past, the deep battle shaped the enemy for subsequent engagement in the close battle. Now and in the future, the decisive component of battle will be the deep fight. In conventional operations, dominance of a particular area will depend less on physically occupying a given space than it will on divisional intelligence assets monitoring enemy activity across the battlefield framework so that the division can project overwhelming combat power to any given point. To do this the division commander must have an accurate picture of the enemy beyond the maximum range of lethal assets.
Digitization and night vision technology improves the division's situation awareness. Current technology, to include position location devices, UAVs, electronic attack and communication intercept provide the division with the capability to determine the precise location of enemy obstacles, positions, weapons, command and control facilities, logistic facilities, his reserve, air defenses, and security elements. Finding the enemy is now easier for the division because the enemy's ability to hide from modern sensors is limited. Using our current intelligence collectors, whether on a contiguous or non-contiguous battlefield the division can quickly locate and identify the enemy.
The airland battle concept of fighting sequentially has evolved and changed to an emphasis of conducting operations simultaneously to gain their total, synergistic effect. Intelligence plays a key role in determining which enemy element is most lucrative and vulnerable. When executing offensive operations, the division uses four general forms of offense: movement to contact, attack, exploitation, and pursuit. Intelligence supports each of these forms, and you will see in the following figures.
PART B: MOVEMENT TO CONTACT.
Division offensive operations often start with a movement to contact. This form of the offense develops the situation and establishes or regains contact with enemy forces. By its nature, situation awareness is at its lowest during movement to contact. In this form of the offense, the fog of war is the thickest. At the same time the requirement for intelligence is at the highest. Before the division is committed to the next form, attack, a complete enemy lay down is required. During movement to contact, the intelligence cycle begins with defining the commander's requirements. Intelligence must not collect for the sake of collection, rather we must collect to support commanders. Only then can we truly support their decision-making processes. Collection management is the key function of prioritizing and allocating assets throughout the division's battlespace.
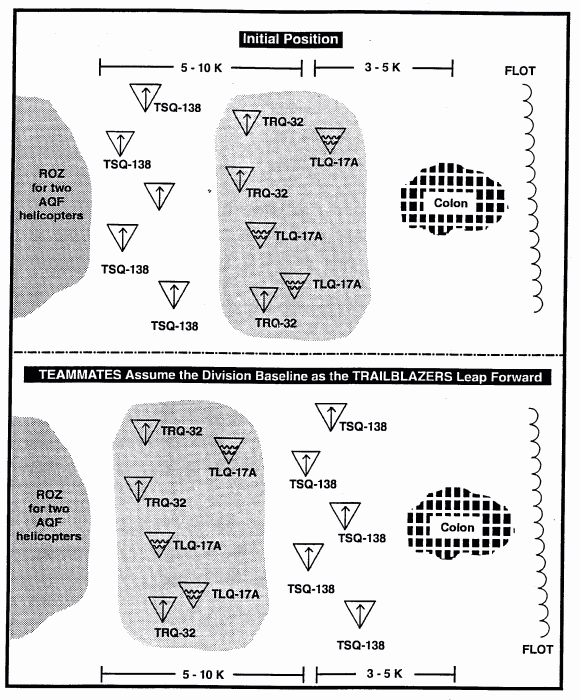
Figure 6-1. Division Employment of IEW Assets During a Movement to Contact.
The collection manager pays keen attention to competing requirements. Only those that directly support the commander's scheme of maneuver should receive valuable and scarce intelligence collection assets. Since the division will fight simultaneously across the entire battlefield framework, phasing the requirements must be event driven rather based on linear plane sequencing. There may be requirements to collect close, deep and rear simultaneously.
Using the intelligence synchronization matrix, developed after wargaming from the BOS synchronization matrix, see Figure 6-1, the collection manager produces the collection plan that will predict the time and place of the division's initial contact.
In addition to orchestrating pure intelligence assets, the collection manager integrates collection with maneuver. In a division movement to contact, the division usually establishes an advanced guard. The organization of the advanced guard is based on METT-T analysis of the situation, but always includes intelligence collection assets.
Typically, these intelligence assets include a slice from each intelligence discipline. Best suited for developing the situation during movement to contact are assets that extend the battlespace and provide near real time information. This may include UAV support and ground and airborne SIGINT collector. HUMINT assets tend to lack the timeliness needed to develop situation awareness during the rapidly changing environment of the movement to contact. However, HUMINT teams should be deployed well forward with the lead units to take advantage of combat questioning of captured enemy soldiers. As the battle progresses and more prisoners are captured and sent to the rear, these HUMINT teams can then move to the division EPW cage.
To support the advanced guard, MI assets are generally organized into a multidiscipline company team. To facilitate command and control of these forward deployed assets, the company team is attached to the advanced guard, normally the division's cavalry squadron. The ACE still provides technical data and receives reports from these assets. Therefore, the long-range connectivity is an important consideration. In addition to connectivity, the mobility of the MI assets must be considered. By its nature, covering force operations are fluid and move rapidly. On the linear battlefield, TRQ-32s generally have the required mobility. However, in some cases, AN/PRD 11, 12, or 13s inserted by air, are better suited. Lessons learned from Operation Desert Storm clearly show that whatever system is chosen; it must have the mobility equal to or greater than the supported maneuver force. MI assets deployed in the advanced guard can also cue and tip off the division's GS assets.
During movement to contact (MTC), other GS MI assets remain under the technical control of the ACE. However, the MI battalion commander is responsible for asset management, and the movement and employment of his systems. Whether attached to the advanced guard or in GS, the primary mission of divisional IEW assets is locating and identifying the enemy prior to contact.
In MTC, the Trailblazer platoon remains in GS and is deployed forward across the division's front. To do this, the platoon normally deploys in a concave baseline. The concave baseline provides longer range DF. As maneuver brigades move forward and beyond DF range, the GS baseline is picked up by the C&J platoon's TRQ-32s and if necessary, QUICKFIX. The C&J platoon fully establishes its baseline prior to the Trailblazer displacing. As the Trailblazer platoon moves forward, it seeks to find terrain that provides LOS out to 30 kilometers. The rapid mobility of the mechanized forces dictates that the platoon must look out to the maximum range of the system capability.
In addition to providing DF and intercept, the C&J platoon also provides the division with ground based electronic attack capability. Since the enemy position is not known, jamming targets may be hard to acquire. In this case, the C&J platoon's TLQ-17As are normally used to reinforce intercept operations. Since they do not have a DF capability, the backup PRD system can be used to provide this capability. When used in this capacity, the TLQ-17A must be in position to rapidly shift their mission from collection to jamming. Therefore, the TLQ-17As must remain forward of all other SIGINT systems. See Figure 6-2.
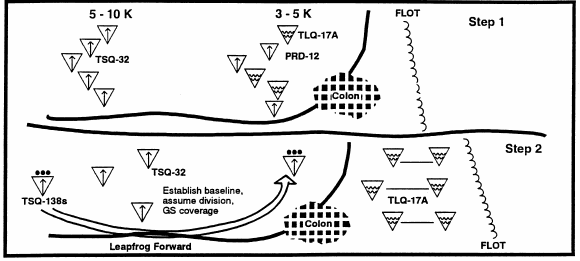
Figure 6-2. ES asset employment during movement to contact.
Flank and rear security protects the division's main body from ground observation and surprise attack. Flank security travels on routes parallel to the main body. These units may be task organized with MI assets. Whether flank or rear security receives IEW support is based on the probable enemy situation and the division commander's intent. UAV, GSR, and SIGINT can fulfill this force protection mission. REMBASS is an ideal sensor for providing early warning during flank security. When devising the collection management strategy, the expected enemy threat on the flanks or rear is weighed against the risk of diluting the main effort's collection capability.
PART C: ATTACKS
Hasty attacks most often follow a movement to contact. The division commander directs actions based on his analysis of the situation and the extent of his knowledge of the enemy situation. Hasty attacks are launched with minimum preparation. While the enemy situation may still be vague, intelligence collection has most likely identified an exploitable weakness. In combat, the force that first locates and identifies vulnerabilities, and then assaults, normally gains an initial advantage. Once established, the enemy situation must be developed. The collection plan that supported the movement to contact is refined and updated. This is especially true if the commander chooses a deliberate attack.
In contrast to hasty attacks, deliberate attacks involve much more detailed intelligence and planning. Deliberate attacks fully synchronize the support of all intelligence assets to paint a detailed and comprehensive picture of the enemy. Generally intelligence assets are placed well forward to exploit their collection ranges.
The division's main effort normally is weighed with additional MI assets. However, if the supporting attack is one of economy of force, it may receive the weighting of intelligence support. This allows a more complete knowledge of the enemy and reduces risk during economy of force missions. See Figure 6-3.
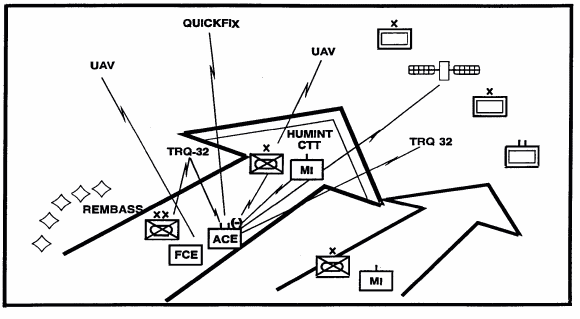
Figure 6-3. IEW Support.
The intelligence products required prior to a deliberate attack must be detailed and graphic. UAVs and satellite viewers can provide the needed graphic depictions and photographs of the enemy's disposition. SIGINT collectors can provide enemy intent and expected actions and reactions. After the attack is launched, the enemy situation must be continually monitored. Predicted enemy courses of action must be confirmed or denied.
Upon initial contact, the division's SIGINT collection assets are focused on second echelon forces and deployed to refine situation awareness. The company team that was attached to the advanced guard reverts back to divisional control. Since the distance from the collector to target tends to be less than MTC, the Trailblazer platoon establishes its baseline in a lazy W or a convex shape. The C&J platoon's collection systems, if not used to reinforce the main effort, can be used in the supporting effort, on the flanks, or attached to the maneuver brigades. In addition to focusing on locating enemy C3 in the close battle, the TRQ-32s and if necessary, the backup PRDs reinforce the collection of tactical data to support electronic attack.
The TLQ-17s are integrated in the friendly plan, providing electronic attack. As always, these jamming assets are deployed forward of the collectors, away from other friendly assets. Typically, jamming targets are executed in concert with lethal fire targets. Once the enemy's center of gravity is determined and HVT are designated, all targets, both lethal and non lethal are linked. This ensures that all fires are directed against the one thing the enemy can least afford to lose. For example, if the enemy's center of gravity is massed artillery, and lethal fires engage the artillery tubes, then the division's TLQ-17s could be used to deny or degrade the enemy's forward fire support assets by jamming the exchange of targeting data on artillery nets. Generally, in a division attack, ground based jamming assets remain in GS. Aerial EA assets, including the division's QUICKFIX, corps and joint assets concentrate on long range artillery, rockets, and missile systems. Both ground and aerial EW assets focus on fire support C3 and target acquisition nodes.
During the early stages of the attack, the interrogators remain well forward with maneuver brigades. During the MTC, their primary source of information was refugees and line crossers. After contact is made, their priority is captured enemy soldiers. They conduct initial interrogations looking for tactical information that supports the friendly attack. As the attack matures, the interrogators, reinforced by corps assets, conduct more thorough interrogations at the division EPW collection point.
The collection manager ensures that the collection effort provides information to support decision points. Enemy actions requiring commitment of the friendly reserve or a move to branches or sequels is fully covered. IEW assets can support other types of attacks including counterattacks, spoiling attacks, raids, feints, and demonstrations.
PART D: EXPLOITATION.
Exploitation usually follows a successful attack. Exploitations disorganize the enemy throughout his depth. The ultimate goal of exploitation is to decimate enemy forces to the point at which his only alternative is to surrender or be destroyed. To do this, intelligence must maintain the situation awareness gained during the attack. It is the responsibility of intelligence to maintain an accurate picture of enemy actions and intent. See Figure 6-4.
To fully support exploitation, MI assets must be deployed well forward. Initial emplacement prior to the attack considers the maintaining of momentum that follows a successful attack. Since the enemy is disorganized, he will generally attempt to regain organization through voice communications. Therefore, the MI battalion's main effort should shift to EW operations.
The Trailblazer quickly establishes a concave baseline in anticipation of the pursuit, attempts to determine future enemy action and intent. The C&J platoon's priority is EA. The TRQ-32's emphasis is collecting and identifying targets for EA. The TLQ-17As and airborne jammers are critical to preventing the enemy from reorganizing by jamming enemy C3 nets.
While ground based collectors are engaged in the prevention of enemy reorganization, the UAV and QUICKFIX identify and target potential counterattack, reserve, and second echelon forces. The QUICKFIX's airborne jamming capability can be used to prevent effective enemy employment of these forces. All IEW assets are positioned to quickly transition to the pursuit.
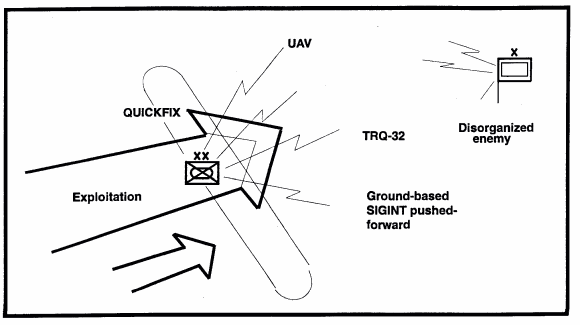
Figure 6-4. Exploitation.
To fully support exploitations, MI assets must be deployed forward. Since, the enemy is disorganized, he will generally attempt to regain organization through voice communication. Therefore, ground based COMINT assets well forward and airborne SIGINT collectors play key roles in determining future enemy actions. UAV can provide near real time information on enemy unit movement and disposition. REMBASS and CI assets can be used in support of force protection in the division's rear as it advances forward.
In some cases, such as Desert Storm, an attack may be continuous (400km in 4 days) with intermediate objectives that are rapidly overcome. In this case, extra effort must be extended to ensure continuous EW support to the division/brigade. The continuous coverage can be accomplished in various ways like:
- Leapfrogging companies/EW teams.
- Covering the movement of ground EW teams with QUICKFIX.
- Using ground based EW teams to set up to provide support in time to affect a critical part or parts of the battle, then pack up and move on, providing no support for the next few hours while they catch up. This requires an acceptance of risk by the supported unit due to EW team site establishment timelines.
PART E: PURSUIT
A pursuit is an offensive operation against a retreating enemy force. It follows a successful attack or exploitation and is ordered when the enemy can not conduct an organized defense and attempts to disengage. The pursuit usually consists of direct pressure and encircling forces. To successfully do this, the commander must have detailed information not only on enemy locations, but more importantly on where the enemy will be and what he is trying to do. Intelligence must not lose contact with the enemy. Doing so forces the division to stop exploiting and begin a new movement to contact.
The mission of the encircling force is to rapidly get to the rear of the enemy and block his escape. The encircling force advances along or flies over routes parallel to the enemy's line of retreat. Intelligence assets supporting the pursuit must have mobility equal to or greater than the maneuver force. QUICKFIX and UAV are ideally suited to supporting pursuits.
METT-T dictates which intelligence assets can best support pursuit operations. Severe weather or an abundance of enemy Air Defense Artillery (ADA) systems may force the use of ground based assets. In this case, planning must consider the deployment of MI assets early. See Figure 6-5.
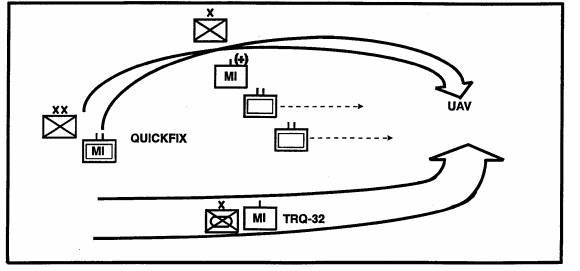
Figure 6-5. Pursuit MI assets must have mobility equal to maneuver unit.
When ground based assets are used to support the encircling force, they are task organized and attached to that force. They remain attached until the encirclement is complete and the fleeing enemy is stopped. Since the MI assets must maintain contact with the enemy and not get left behind by the pursuing force, trailblazers are not suited to this mission.
To gain necessary mobility, early deployment of TRQ-32s or air insertion of PRDs is the logical choice. When deployed early, the security of the TRQ-32s is a key issue. Since TRQ-32s do not have an on-the-move capability, they must establish their base line forward prior to the movement of maneuver forces. They set up at the maximum range of the emplaced Trailblazers, thereby maintaining seamless coverage. After the C&J's TRQ-32 teams have established their baseline, the Trailblazer platoon can begin their movement. As in exploitation, SIGINT collectors focus on identifying enemy intent and providing EA targets to keep the enemy disorganized.
Ground based jammers are quickly moved forward. While they are moving, the division's jamming mission is picked up by the QUICKFIX. Once established, the TLQ-17A teams disrupt the enemy's command and control of their retrograde. During the withdrawal, the enemy is reliant on voice communications and is susceptible to EA. When integrated with lethal fires, EA can prevent the enemy from conducting an organized withdrawal or delay.
In a pursuit, the interrogator's priority is screening the EPWs and questioning only those who can provide the most lucrative information in order to gain intelligence that will provide the most important and time-sensitive information.
While the objective of IPB is the early identification of the enemy course of action, EW planning goes beyond that to the development of the most effective mix of OPSEC, military deception, jamming, and destruction options to defeat the enemy's command control and communication. The figure below is a simplified illustration of how templating may be used for EW planning and execution.
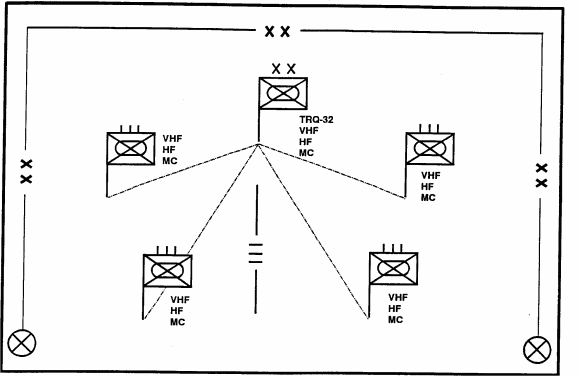
Figure 6-6. Simplified Doctrinal Template with MRD Communications.
Like the intelligence analyst, the EW analyst creates templates to illustrate the enemy's capability to use his electronic systems for C3 reconnaissance, surveillance, target acquisition, and radio electronic combat (REC). Templates also aid him in the selection and use of friendly EW assets. Figure 6-6 is a doctrinal template depicting a motorized rifle division's (MRD's) communication links to subordinate regiments. Terrain is not yet a consideration. The communication links (VHF, HF, and multichannel) are the critical means by which the enemy commands and controls its maneuver forces in battle. A simplified doctrinal template showing an MRD's communications links to its regiments is shown in the above illustration. Terrain is not a consideration. The links (very high frequency (VHF), high frequency (HF), and multichannel (MC) are the means through which enemy C2 maneuvers forces in battle. In the above illustration, the doctrinal template is shown placed over the combine obstacles overlay to visualize how terrain will affect enemy capabilities to communicate.
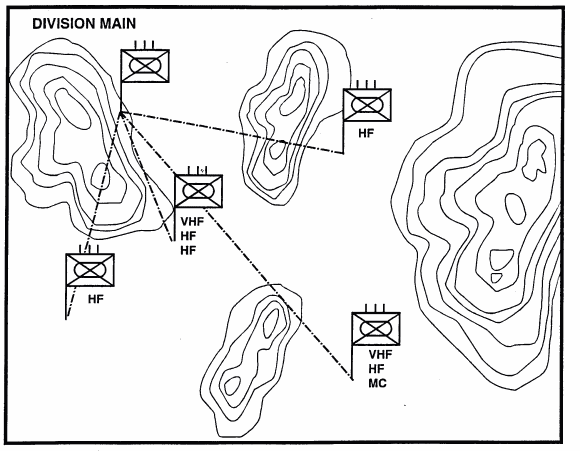
Figure 6-7. Doctrinal Template Over Combine Obstacle Overlay.
The blocking terrain forces the enemy division commander to rely on HF to communicate with two of his regiments.
Figure 6-8 indicates that there are at least two alternate solutions to the enemy's communications problems: The use of relays or the relocating of command posts (CPs) to facilitate communications.
This situation templates (and any others the analyst can create that depict possible solutions to the enemy division commander's communications problems) are compared with other IPB products (such as the event template and events analyst matrix) to provide clues concerning expected enemy communications. ES and EA operators use these clues to determine which frequencies to search and what type of modulations and other technical parameters to look for ES Asset Deployment Based on LOS. The EW planner can then apply LOS analysis to determine where ES assets can be deployed to intercepts and locate the enemy target emitters and where EA assets can be deployed to jam enemy receivers. The above illustration shows ES asset deployment should be based on LOS analysis and the joint-jamming effectiveness template (J-JET).
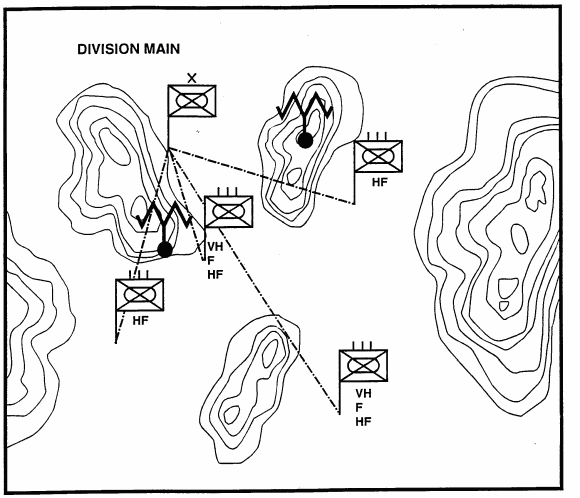
Figure 6-8. Situational Template with Radio Relay.
Aerial ES and EA resources are used to overcome LOS and mobility limitations and fill gaps in coverage left by ground resources. Use of aerial resources is closely coordinated with ground resources. A major advantage in using aerial resources is they are capable of cueing ground ES resources and GSR.
Practice Exercise

