|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 3
INTELLIGENCE IN COMBATTING TERRORISM
Critical Task: 301-340-3002
OVERVIEW
TASK DESCRIPTION:
In this lesson, you will learn how to determine the terrorist threat and how to effectively identify methods used in combatting terrorism.
LEARNING OBJECTIVES:
| ACTIONS: | Define the role of intelligence in identifying the terrorist threat; recommend responses to a terrorist incident; define US Government policy on terrorism and apply legal aspects to countering the terrorist threat. |
| CONDITIONS: | You will be given narrative information, extracts from AR 525-13 and AR 190-40, and FM 100-37 and FM 19-30. |
| STANDARDS: | Recommend counterterrorism courses of action which are consistent with official U.S. Government policy and fall within the parameters of legal constraints. |
| REFERENCES: | The material contained in this lesson was derived from the following publications: AR 190-40. AR 190-52. AR 210-10. AR 525-13. FM 100-37. FC 100-37-1. FC 100-37-2. TC 19-16. |
INTRODUCTION
To meet the terrorist threat, the US Army has developed and implemented an integrated, comprehensive combatting terrorism program. It is designed to foster a protective posture in peacetime that will carry over to a wartime environment.
PART A: INTELLIGENCE SUPPORT IN IDENTIFYING THE TERRORIST THREAT
Assessing the vulnerability of a unit or installation to the terrorist threat helps uncover and isolate security weaknesses. Steps can then be taken to strengthen or to eliminate the weaknesses. An assessment must be fluid. As data for the assessment changes, so does the risk to the installation or unit. Continual revision and evaluation of threat data are essential. The basic elements of a threat assessment are: Information/intelligence; knowledge of the threat capabilities; and an understanding of the installation or unit vulnerabilities.
An installation or unit vulnerability assessment should include but not be limited to the following:
Planners who "think like a terrorist."
Realistic scenarios for exercises such as a command post exercise (CPX), or field training exercise (FTX) in which specific threats are directed against vulnerabilities.
Staff personnel, under direction of the unit or installation operations officer, to provide expertise in preparing and maintaining the threat assessment.
CRIME PREVENTION
The crime prevention portion of the model consists of operations security (OPSEC), personnel protection, and physical security. The three separate, but related elements, together reduce the vulnerability of an installation, unit, or personnel to terrorist attack.
Operations Security. A threat assessment may reveal security weaknesses in day-to-day operations. The security of communications systems, information activities, and personnel must be examined and countersurveillance techniques initiated when possible. Information gleaned from communications can provide terrorists with detailed knowledge about potential targets. Terrorists, not hampered by regulations, fully exploit opportunities presented to them. The objectives of OPSEC, from the combatting terrorism standpoint, are as follows:
To avoid stereotyping operations.
To understand techniques used by terrorists to collect intelligence.
To integrate OPSEC into physical security and personnel protection programs.
To deny intelligence and information to terrorists.
To develop essential elements of friendly information (EEFI) to facilitate and focus efforts to deny that information to terrorists.
Personnel Protection. All military personnel and family members, as well as civilians connected with the military or US government, are potential victims of terrorist attacks. A threat assessment may identify specific personnel who by virtue of their rank, position, or special knowledge are particularly prone to be terrorist targets. Prevention of such attacks depends on the planning and use of personnel protection measures. The most important measure is educating persons who are likely targets to recognize the threat and act to reduce the risk. Personal protection education must emphasize how to deny the risk to the attacker. The objectives of personal protection are: To develop programs that include planning, education, and awareness; to use personal protection measures tailored to the level of the threat; and to protect VIPs and high-risk personnel.
Physical Security. Physical security measures for an installation or unit reduce the opportunity for terrorist attacks by increasing the risk to the terrorist. The more an area is strengthened, the more difficult it becomes for the terrorists to penetrate. Intrusion detection systems; proper use of lighting and fences; authority to close or restrict access to an installation, unit, or facility; secure sensitive storage locations; and well-trained security personnel are all measures that enhance physical security. The objectives of physical security as they pertain to combatting terrorism are:
To identify physical vulnerabilities on installations or units and then take appropriate actions to reduce or eliminate those vulnerabilities.
To involve the installation and unit staffs in implementing a sound physical security program.
To harden targets thereby increasing the risk to potential terrorists.
Vigorous execution of a well conceived crime prevention program reduces or eliminates conditions conducive to crime. Because terrorists generally use criminal methods, proven crime prevention techniques can be successful against terrorists.
AUTHORITY AND JURISDICTION
Since an understanding of who has authority to do what is an essential part of any plan, the terrorism counteraction model includes authority and jurisdiction as a program element. An implicit requirement is for the local commander to determine whether an incident is terrorist or criminal in origin. TC 19-16 provides criteria to assist in making this determination.
CRISIS MANAGEMENT PLANNING
The establishment of a mechanism to respond to a terrorist incident is an essential element of any combatting terrorism program. Normally the commander identifies a Crisis Management Team (CMT) which acts as the principal planning agency for special threats. Crisis management planning must address the activation and responsibilities of local resources and provide mechanisms to obtain support from resources not under local control (for example, medical, aviation, or explosive ordnance disposal (EOD)).
PART B: METHODS IN COMBATTING TERRORISM
The intelligence in combatting terrorism is divided into two components, antiterrorism and counterterrorism. Antiterrorism (defensive measures) is the preventive stage of combatting terrorism. Defensive measures are intended to harden potential targets and to develop procedures to detect planned terrorist actions before they take place, thereby reducing the probability of a terrorist event. Counterterrorism, offensive measures which are reactive, can be the tactical stage of combatting terrorism. Reactive measures, to include direct contact with a terrorist force to end the incident with minimum loss of life and property, are taken in response to a terrorist incident. In addition to reacting to the terrorist incident, collecting information is a high priority which is necessary in combatting terrorism. There is no distinct separation between where anti-terrorism ends and counterterrorism begins. The two should be viewed as parts of a single continuum.
At Department of the Army (DA) level, the Deputy Chief of Staff for Operations and Plans (DCSOPS) has overall staff responsibility for coordinating the Army's combatting terrorism program. At major command (MACOM) level and below, the DCSOPS/G3/S3 has staff responsibility for developing and coordinating the execution of combatting terrorism programs to include security assessments. At each level, the operations officer will organize and supervise those assets necessary to plan and conduct vulnerability assessments for the installation or unit commander. (Examples of vulnerability assessments for installations and deployable units are included in TC 19-16 and FC 100-37-1). Security assessments are performed by task organizing representatives from appropriate agencies (for example, provost marshal, engineers, military intelligence and so on) under the lead of the DCSOPS/G3/S3.
Combatting terrorism planning and execution must be an integral part of the security mind-set of all military personnel. Consideration of the terrorist threat to the force must become a routine factor in planning all missions just as the conventional enemy threat to a mission is routinely considered. The terrorist threat exists throughout the spectrum of conflict. Therefore, all operational orders (OPORDs) and operational plans (OPLANs), whether for training, contingencies, or wartime, must include the terrorist threat as part of the "enemy forces" subparagraph of paragraph 1 to the order or in a supporting annex.
In addition to identifying the terrorist threat in the order, measures to be taken by the command to counter the threat must be identified in paragraph 3 of the order or a supporting annex. Failure to consider the terrorist threat in day-to-day activities increases the vulnerability of the force to a terrorist attack.
COMBATTING TERRORISM MODEL
The combatting terrorism model represents an integrated, comprehensive approach to countering the terrorist threat both to military installations and to units. The model consists of the defensive phase, which lists antiterrorism measures, and the reactive phase, which deals with counterterrorism measures. The defensive phase encompasses the planning, preventive measures, preparation, and training that take place prior to a terrorist incident. During this phase, consideration is given to research (information and intelligence gathering); development and implementation of preventive measures; in-depth planning; and training (awareness, developing skills, and practicing contingency plans). The reactive phase includes actions taken in response to increased threat levels and the steps necessary to resolve a terrorist incident.
Intelligence in combatting terrorism planners must consider ways to deny terrorists the intelligence they need to plan and execute an attack. They must introduce randomness whenever possible; harden and defend potential targets; and introduce a degree of risk that may be unacceptable to the terrorists. Effective use of the combatting terrorism model (see Figure 3-1) will assist in structuring this effort. The model covers six basic areas. Five of the areas are defensive and directed toward procedures, planning, and actions to discourage or prevent terrorist attacks.
The other one is reactive and directed toward the installation's or unit's response. The steps in the defensive phase are:
Criminal information/intelligence.
Threat assessment.
Crime prevention, which consists of OPSEC, personnel protection, and physical security.
Authority and jurisdiction.
Crisis management planning.
The reactive phase consists of performing crisis management.

Figure 3-1. Combatting Terrorism Model.
CRIMINAL INFORMATION AND INTELLIGENCE
Information gathering is of critical importance when conducting intelligence in combatting terrorism planning and operations. Consideration of this information within the context of the social, economic, and political climate of an area provides a basis to determine the terrorist threat to an installation or unit. The basic steps in the criminal information/intelligence process are collecting, evaluating, processing, and disseminating information. All possible sources to include open, criminal information, intelligence, and human sources within the installation or unit will be used for collecting information.
Antiterrorism addresses those defensive measures taken to reduce the vulnerability of personnel (to include family members), installations, and units to terrorist attack. Antiterrorism is, therefore, the foundation of the Army's terrorism counteraction program and includes actions that involve every member of the Army community (military, civilian, and family members).
INTELLIGENCE
Intelligence is the first line of defense in a combatting terrorism program. A well planned, systematic, all source intelligence program is essential. The role of intelligence in combatting terrorism is to identify the threat and provide timely threat intelligence. This includes evaluation of terrorist capabilities, tactics, and targeting strategy, and the dissemination of this information.
RESPONSIBILITIES OF U.S. GOVERNMENT LEAD AGENCIES (NON-US ARMY)
Collecting and processing domestic terrorist information is a responsibility of the Federal Bureau of Investigation (FBI). Overseas, terrorist intelligence collection is a Department of State and host nation responsibility. U.S. Army intelligence activities are conducted in accordance with Presidential Executive Orders, federal law, status of forces agreements (SOFAs), memorandums of understanding, and applicable U.S. Army regulations.
RESPONSIBILITIES OF U.S. ARMY INTELLIGENCE ACTIVITIES
The Deputy Chief of Staff for Intelligence (DCSINT), DA, provides guidance and develops policies, plans and procedures for collecting, reporting, and disseminating information on terrorist activities.
The U.S. Army Intelligence and Security Command (INSCOM) is the lead U.S. Army agency controlling Army foreign intelligence and counterintelligence activities directed against terrorists and terrorist acts. INSCOM has the responsibility to:
Coordinate with appropriate U.S. and host nation agencies and to provide overall direction and coordination of the Army counterintelligence effort.
Operate a 24-hour operations center to receive and disseminate worldwide terrorist threat information to and from applicable INSCOM staff elements, subordinate commands, and national agencies.
Provide Army commanders with information on terrorist threats concerning their personnel, facilities, and operations. To work in conjunction with the FBI or host nation authorities to investigate terrorist incidents for intelligence aspects.
Provide terrorist threat information in subversion and espionage activities directed against US Army (SAEDA) briefings.
Serve as the Army's liaison representative to Federal, State, and local agencies in CONUS, and national, state, and local-level agencies outside of the continental United States (OCONUS) for exchange of information on terrorists.
The intelligence and threat analysis center (ITAC), an element of the U.S. Army Intelligence Agency (USAIA), provides a monthly international terrorism summary and other threat data to supported commanders. On request, ITAC can provide current intelligence data on terrorist groups. The antiterrorism Operations and Intelligence Cell, Army Operations Center, disseminates time sensitive and specific threat warnings to appropriate commands.
RESPONSIBILITIES OF AGENCIES SUPPORTING US ARMY INTELLIGENCE ACTIVITIES
In accordance with AR 381-20, the U.S. Army Criminal Investigation Command (USACIDC) collects and evaluates criminal information and disseminates terrorist related information to supported installation and activity commanders as well as to INSCOM and ITAC. As appropriate, USACIDC elements conduct liaison with local military police and civilian law enforcement agencies.
Intelligence staff elements of MACOMs and commanders at all levels have the responsibility to:
Promptly report all actual or suspected terrorist incidents, activities, and early warnings of terrorist attacks through appropriate chains of command to ITAC. Initiate and maintain liaison with the Provost Marshal's Office; local USACIDC and INSCOM elements; security offices; host nation agencies; and other applicable organizations, elements, and individuals. Maintain liaison with local police, intelligence, and other civilian and military offices and agencies. This liaison is limited in scope as determined by the appropriate Army liaison office or the local INSCOM field office and must be coordinated with the law enforcement staff. In cooperation with the local INSCOM detachment, develop and present terrorism threat awareness training and briefings to all personnel within their commands.
Law enforcement staff elements have the responsibility to:
Report all actual or suspected terrorist incidents or activities to their immediate commander, supported activities, and INSCOM through established reporting channels.
Initiate and maintain liaison with local INSCOM and USACIDC elements.
Maintain liaison with federal, host nation, and local law enforcement agencies or other civil and military terrorism counteraction agencies, as appropriate.
Installation security officers and managers have the responsibility to:
Report all actual or suspected terrorist incidents or activities to their immediate commander, supporting Provost Marshal, other supported activities, and local INSCOM and USACIDC offices.
Conduct regular liaison with supporting Provost Marshal, INSCOM, and USACIDC offices.
Coordinate with the supporting Provost Marshal to prepare and continually update the Intelligence Vulnerability Assessment and take steps to eliminate identified weaknesses.
Ensure that terrorism threat awareness training and briefings are presented to installation personnel and family members, as appropriate.
SOURCES
Intelligence for the terrorism counteraction program is derived from open source information, criminal information sources, government intelligence, and local information.
Open Source Information. This information is publicly available and can be collected, retained, and stored without special authorization (AR 380-13 and AR 381-10). The local and national news media are excellent open sources of information on terrorism. The news media report most major terrorist incidents and often include in-depth reports on individuals, groups, or various government counter-strategies. Government sources include congressional hearings; publications by the Federal Bureau of Investigation (FBI); the Central Intelligence Agency (CIA); the State Department; and the National Criminal Justice reference services. There are private data services that offer timely information on terrorist activities worldwide.
Terrorist groups and their affiliates publish manuals, pamphlets, and newsletters that reveal their objectives, tactics, and possible targets.
Other open source publications include terrorist training and indoctrination manuals. Be aware that information on specific groups and individuals must be maintained in accordance with AR 380-13.
Criminal Information. Both military and civil law enforcement agencies collect criminal information. Since terrorist acts are criminal acts, criminal information is a major source for terrorist intelligence.
Since the collection, retention, and dissemination of criminal information is regulated by AR 380-13, AR 381-1, and AR 381-10, commanders must work through established law enforcement liaison channels. Local USACIDC offices maintain current information that will assist in determining the local terrorist threat.
Government Intelligence. U.S. Army intelligence organizations (specifically ITAC) compile comprehensive intelligence that is disseminated on a need-to-know basis. Excellent intelligence sources outside the Army community include the U.S. Air Force Office of Special Investigations (OSI), Naval Investigative Service (NIS), Defense Intelligence Agency (DIA), the Defense Investigative Service (DIS), and the CIA. Because of the differences in focus, access to these non-Army sources is usually limited to established intelligence channels.
Local Information. Another valuable source of information is the individual soldier, civilian employee, or family member. These informal sources can provide information on unusual or suspicious activity in the local area. Personnel can be encouraged to report useful information through an active crime watch program.
THREAT ASSESSMENT
Threat assessment is the process of compiling and examining all available information to develop intelligence indicators of possible terrorist activities, see Figure 3-2. Threat assessment is the essential first step in determining vulnerability to terrorist attack.
To enhance the U.S. Army's capability to compile and evaluate information from many sources, the ITAC maintains terrorism data. From this data base, ITAC derives worldwide, area, and general threat assessments that are disseminated to the Army. MACOMs then augment or refine the ITAC threat assessment to focus on their area of interest. This process, operative during times of peace and war, promotes coordination between all levels of the intelligence and law enforcement systems; broadens acquisition channels; and enhances timely distribution of information to the supported commander.
Several factors complicate intelligence efforts aimed at terrorists. The smallness of terrorist groups, coupled with their mobility and cellular organization, make it difficult to "find" and "fix" members. Additionally, the traditional orientation of police organizations is toward individual criminals while military intelligence organizations focus on conventional threats. Terrorist activity, therefore, requires some degree of reorientation for police and intelligence operations. The intelligence system should provide critical and timely information to the user. This requires an efficient collection and processing capability and the ability to organize, store, and rapidly retrieve this information. This capability, coupled with early warning, careful observation, and assessment of threat activity, enhances the probability of accurately predicting the types and timing of terrorist attacks.
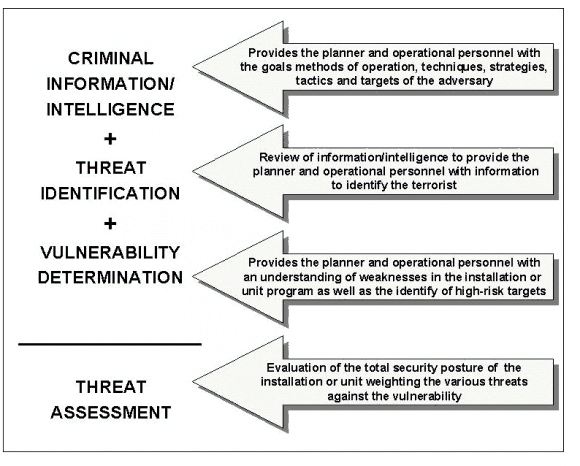
Figure 3-2. Components of Threat Assessment.
CRIME PREVENTION
Terrorist groups do not have unlimited resources. They are particularly constrained in personnel. Even groups that enjoy state support or direction are usually unwilling to attack where there is a high risk of capture or death. Consequently, terrorists attack targets that have the greatest probability of success with the least risk to themselves. Studies of terrorist operations show that hardening a potential target forces the terrorist to either forego the operation or switch to targets not as well protected.
Crime prevention consists of measures that harden the target against terrorist attack. While all preventive measures contribute to the hardening, maximum benefit is gained when planning and implementation are done concurrently. Take, for example, an installation where there is an OPSEC program, a crime prevention program, and a vulnerability assessment. If each complements the other, then a cohesive prevention effect is realized, and the program is more effective than if each was approached in isolation.
A comprehensive crime prevention program reduces the vulnerability of installation, unit, and individual to a terrorist attack. Effective crime prevention measures also reduce the probability that a terrorist incident will occur and help ensure a positive outcome should an attack take place. Planning and implementing antiterrorism procedures, as part of the overall crime prevention program, develop effective practices and procedures and motivate personnel to put them into action.
OPERATIONS SECURITY (OPSEC)
OPSEC is the process of denying adversaries information about friendly capabilities and intentions. It includes identifying, controlling, and protecting information associated with the planning and conducting of military operations and other activities. OPSEC, as it relates to combatting terrorism, is concerned with controlling information and detectable activities that could enable a terrorist to effectively exploit a target's weaknesses and neutralize or preempt a counterterrorist response. Terrorists gather information, reconnoiter potential targets, and select targets that offer the maximum opportunity for success. Information passed on unknowingly by military and DOD civilian personnel and their family members is used by terrorists in their planning efforts. OPSEC procedures used to deny the terrorist this information are:
Protection of itineraries, travel plans, and personnel rosters.
Elimination of rigid movement and security patterns.
Protection of building and facility plans, billeting assignments, and VIP guest lists.
Discussion of classified or sensitive information only on National Security Agency (NSA) approved cryptographically secured telephone or radio circuits such as the automatic secure voice communications system (AUTOSEVOCOM).
Coordination of physical security measures to protect personnel and prevent unauthorized access to equipment, facilities, materiel, and documents.
OPSEC relies on the techniques of information security, signal security, and deception. These are considered interrelated and simultaneous. Protecting information is the cornerstone of the OPSEC program with training and common sense as the building blocks. With planning and an appropriate command emphasis, an OPSEC program can be highly effective in establishing and maintaining an antiterrorist posture among military personnel. It is one of the least expensive proactive measures an installation can employ.
PERSONNEL PROTECTION
Personnel protection (or personal protection) in combatting terrorism pertains to both protective services and those measures taken by personnel to protect themselves from criminal or terrorist acts. Personnel protection programs are designed to train personnel in protective measures and to create an awareness of the threat. This training is especially important for people who are potential high-risk targets. Implementation of personnel protection measures depends on:
Requirements established by US Army regulations and directives.
The degree of risk of terrorist activities. (Intelligence and law enforcement agencies define the degree of risk by specific area or region as high, medium, or low).
The level of antiterrorism training.
Location of assignment. (Overseas Army personnel not assigned to military installations or not working and living on military installations are particularly vulnerable to terrorist acts because of their continual high visibility).
Protective service details, composed of law enforcement personnel, are intended to safeguard a designated individual from political embarrassment, assassination, kidnapping, and injury. The USACIDC and local provost marshals have responsibility to plan and conduct protective service operations for specified individuals. USACIDC is responsible for protecting the Secretary and Deputy Secretaries of Defense; Secretary and Under Secretary of the Army; the Chairman, Joint Chiefs of Staff; and the Chief and Vice Chief of Staff, US Army. When consistent with operational priorities and approved by the Commander, USACIDC, subordinate USACIDC elements provide protective services to other personnel. Installation provost marshals, within their capabilities, provide security to high-risk individuals as designated by the local command. This support, however, is limited by the availability of experienced protective service personnel and equipment.
Individual protective measures decrease the individual's vulnerability to terrorist attack. Alert and trained individuals minimize the likelihood of terrorist success and act as a deterrent to terrorist activity. Commanders must set the example so that security awareness becomes an integral element of Army thinking.
General officers, other VIPs, and their families are categorized as high-risk personnel. Individuals other than general officers and VIPs may be termed high risk because of their past assignments, duty position, or area of assignment. Examples are law enforcement personnel; embassy personnel; US military foreign internal defense missions; foreign area specialists; US Army recruiters; and isolated medical, signal, intelligence, and engineer personnel. Regardless of rank, all high-risk individuals have special security needs. These include host nation protection; greater level of terrorism awareness; additional training (by Mobile Training Teams and exportable training packages); and antiterrorism and physical security considerations that specifically apply to high-risk individuals, their families, aides, and drivers. Items of consideration should include the following:
Defensive and evasive driving.
Self protection.
Hostage survival training that is continually evaluated and balanced against reasonable probability of occurrence.
Physical security improvements of quarters and offices.
Special equipment needs, in selected cases, such as armor plated vehicles and protective vests.
Other personnel, including family members, who are not necessarily classified as high risk by virtue of rank, position, or duty assignment, also have a need for a personal protection program. The sophistication of that program in terms of effort and expense undertaken by the individual depends on the relative threat in the geographical area of concern. Any person connected with the US military can become a target for terrorists.
PHYSICAL SECURITY
Physical security helps to protect facilities and personnel from terrorist acts, thereby preventing unauthorized access to equipment, materiel, and documents. A successful physical security program includes planning, coordinating, executing, reviewing, and evaluating courses of action that improve physical security of quarters, offices, and installation facilities. Physical security, which incorporates human resources and mechanical systems, is an integral part of antiterrorism planning. The installation physical security program is tailored to the local threat. Security requirements are determined by the installation provost marshal, USACIDC field offices, and local military intelligence activities. A sample comprehensive physical security plan is in FM 19-30 and FC 100-37-1. This plan addresses specific detection, assessment, response, delay, and communications measures taken to safeguard personnel, materiel, and equipment. Included are lock and key control; protective barriers, lighting and sensors; MP patrols; interior guards; vehicle checks and searches; community relations programs; and a neighborhood crime watch program.
Priorities are based on the current threat. Periodic review and revision of physical security procedures ensure that potential targets are being hardened, thus reducing the vulnerability to terrorist attack.
AUTHORITY AND JURISDICTION
The authority and jurisdiction over a terrorist incident depends on the location of the incident and the agencies, military or civilian, involved. The unwitting violation of the law during a terrorist incident could keep a terrorist from being prosecuted. The elements of authority and jurisdiction help identify:
The responsibilities of the commander for law, order, and discipline.
The requirements of AR 525-13 and supplements.
The role of the FBI and other federal agencies during combatting terrorism operations.
The role of SOFAs, host nations, and the State Department concerning combatting terrorism planning operations OCONUS.
CRISIS MANAGEMENT PLANNING
A crisis management team (CMT) is set up to facilitate combatting terrorism planning and to function during periods of increased threat or when a terrorist incident occurs. The special threat plan must describe the organization, training, and functions of this team. When forming a CMT, things to consider are:
Who will be members of the team and their responsibilities (for example, military police, medical, engineer, staff judge advocate).
The training needed to prepare team members to execute their responsibilities.
Who will make decisions and have final authority for the team as a whole (Chief of Staff or DCSOPS/G3).
The role of the CMT in the commander's concept for the combatting terrorism planning.
The need for the CMT to participate in exercises and be evaluated at least twice each year.
COUNTERTERRORISM
Counterterrorism, the final phase of combatting terrorism, is the only reactive phase. The counterterrorism phase validates the extensive preparation, planning, and response measures established in the combatting terrorism plan. Counterterrorism includes offensive measures taken in response to terrorist acts. Some aspects of antiterrorism apply to counterterrorism planning and execution. Intelligence, for example, is not limited to antiterrorism, but rather has equal importance in counterterrorism.
Counterterrorism operations sometimes involve the employment of forces to resolve terrorist incidents. Missions range from local force response on a military installation to assisting other U.S. military forces, civil authorities, or other nations' forces if requested by the National Command Authority (NCA). Peacetime and wartime missions include rescuing hostages, locating and recovering sensitive items, and assaulting terrorist positions. The type of forces and command and control relations used in combatting terrorism operations depend on the location, type of incident, and degree of force required. Force selection criteria are governed by legal and political constraints.
Counterterrorism operations often require specially trained personnel capable of mounting swift and effective actions. General purpose forces not specifically trained in counterterrorism are ill-prepared to conduct these operations. General purpose forces may provide support to a specially organized, equipped, and trained counterterrorism unit.
CRISIS MANAGEMENT EXECUTION
Responding to a terrorist incident requires special capabilities and consideration of several factors. First, the incident must be identified as a terrorist event rather than a criminal incident. Next, the OPLAN must be put into effect as quickly as possible. The special considerations for this component of the model are:
Preparation for multiple incidents or terrorist diversionary tactics.
Establishment of communications nets and the ability to monitor conversations in accordance with AR 190-30 and DOD Dir 5200.24.
Activation of required resources.
Submission of required reports.
Implementation of crisis decision-making procedures.
Activation of a think tank.
Preparation for prolonged incidents.
Management of the news media.
Preparation of an after action report.
Using the terrorism counteraction model helps to ensure that the special threat plan is both proactive to prevent a terrorist incident and reactive to reduce the terrorist's chances for success.
PART C: RESPONSE PHASES TO A TERRORIST INCIDENT
Background. The initial response to a terrorist attack on an installation is usually made by the military police or security force patrols on duty at the time of the incident. The initial response force is under the control of the senior military police officer or NCO at the scene. For a deployed unit, the initial response may be made by the unit interior guard. In this case, the response force is under the control of the unit duty officer or guard force commander.
Information and intelligence gathering begins as soon as the initial response force arrives at the scene. The initial response force immediately identifies the nature of the situation and reports it. They isolate the incident and contain the situation until relieved by the Threat Management Force (TMF). The actions of the initial response force are critical. Equally important is that each shift of the security force have trained personnel who are aware of the threat and capable of reacting promptly to any new development. For example, in cases of hostage-taking or facility seizure, criminal hostage takers may claim to be political activists because they believe their demands will be more readily accepted. However, if they claim to be politically motivated but all of their demands are monetary, then their actual motives are suspect. While political (religious) fanatics and those who are psychologically disturbed have been known to conduct suicide missions, criminals do not. If the perpetrators are political fanatics, the planned attack force option may be needed. Once an incident has been identified as a terrorist action, the installation commander should activate the CMT and the TMF.
CRISIS MANAGEMENT ORGANIZATION
Emergency Operations Center (EOC). The installation commander is responsible for command and control of installation resources during a terrorist incident. The commander typically exercises this responsibility through the EOC which is activated in anticipation of or reaction to a terrorist incident. In addition to directing the military response, the EOC coordinates with higher, lower, and adjacent headquarters and civilian organizations involved, see Figure 3-3.
Crisis Management Team (CMT). The CMT is the staff team specializing in counterterrorism. This team plans combatting terrorism, advises the commander, and coordinates support for the EOC which, in turn, directs the combatting terrorism operations.
Threat Management Force (TMF). The tactical element for crisis management is the TMF. When a terrorist incident occurs, the TMF is employed to isolate, contain, and, if required, neutralize the terrorist force. The deputy G3/S3 or provost marshal representative directs the TMF and is the on-site security force commander. The TMF is normally organized into the Special Reaction Team (SRT), composed of specially trained and equipped security personnel; the hostage negotiation team; and the general security force which is split to provide inner and outer perimeter protection. These teams may be supported by communications, medical, logistical, administrative, intelligence, and criminal investigation sections. The TMF is organized, equipped, and trained to support the installation special threat plan.
RESPONSE PHASES TO A TERRORIST INCIDENT
Response to a terrorist incident varies depending on the nature and location of the incident (CONUS or OCONUS). There are three distinct phases through which an incident may evolve. However, most incidents do not develop beyond the first phase. The three phases are as follows:
Phase I. Is the commitment of locally available resources which may include military police, security force patrols, interior guards or backup units. Ideally, all military police shift personnel are familiar with local SOPs for terrorist incidents and have practiced those procedures as part of their unit training program. They must be prepared to secure, contain, and gather information at the scene until the beginning of phase II. Since terrorist incidents often include Improvised Explosive Devices, response forces must be alert to this fact while securing and containing the incident scene. The evacuation of threatened areas is a high priority function.
Phase II. Is the enhancement of the initial response force by the TMF, FBI, crisis management teams, or host nation tactical units. This phase begins when the EOC and the CMT are activated. During this phase, either the FBI or the host nation may assume control over the incident. If that occurs, installation forces must be ready to support the operation. The Special Reaction Team must be ready for employment in this phase of the operation.
Phase III. Is the commitment of the FBI, DOD, or host nation combatting terrorism force. This is the phase in which steps are taken to terminate the incident. Incident termination may be the result of successful negotiations, assault, or other actions including the surrender by the terrorists.
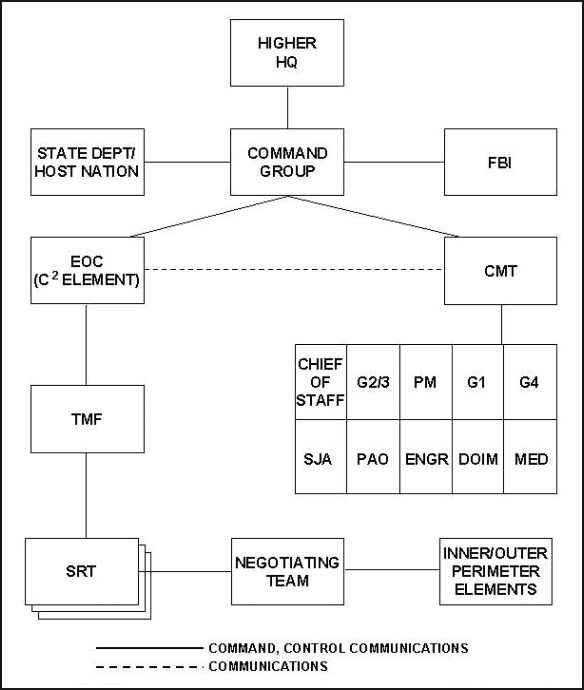
Figure 3-3. Crisis Management Organizational Chart.
ESTABLISHING COMMUNICATIONS
A crucial aspect of implementing the combatting terrorism plan is to establish secure communications among the forces in the incident area, the EOC, and the CMT. Once this is done, all of the other elements of the communications plan are activated. Communications personnel must be able to respond to changing needs during the incident and be able to maintain predetermined channels of communications over a prolonged period.
CONTROLLING EVIDENCE
The primary goal of committing forces to a terrorist incident is to end the incident without injuring hostages or other innocent people. Another consideration is successful prosecution of the terrorist. Witness testimony, photographs, and other physical evidence play an important role in achieving successful prosecution. The acquisition of evidence is an operational requirement during any incident.
DISPOSITION OF APPREHENDED PERSONNEL
Apprehended military personnel must be handled according to Army regulations and applicable installation standard operating procedures (SOPs). In the United States, civilian detainees must be released to the FBI or US federal marshals for disposition. Civilian detainees in OCONUS will be processed according to the SOFA with that particular country.
REPORTING
Reporting to higher headquarters is an important element in any special threat or terrorist situation. A category 1 Serious Incident Report (SIR) must be submitted in accordance with AR 190-40. Immediate telephonic notification will be made to the Army Operations Center (the basic interrogatives, for example: who, what, when, and where are the basis of the report). An electrical message will be submitted to Headquarters DA (DAPEHRE) within 12 hours. SIRs must be revised and updated as needed.
PUBLIC AFFAIRS
When dealing with a Public Affairs Office (PAO) about combatting terrorism matters, the principal objectives are to limit the media exposure terrorists seek and communicate a calm, measured, reasoned reaction on the part of U.S. military personnel. Public affairs programs are designed to:
Identify terrorist activities as criminal acts not justifying public support.
Support DOD public affairs strategy on releasing information pertaining to combatting terrorism plans, operations, or forces involved in combatting terrorism operations.
Agree with US policy on terrorism which identifies all terrorist acts as criminal acts, mandates no concessions to terrorists, refuses to pay ransom, and isolates those nations identified as fostering terrorism.
The Department of Justice has public affairs responsibility for incidents occurring within U.S. territory if the FBI assumes responsibility for resolving the incident. When U.S. military combatting terrorism forces are employed, the DOD provides a spokesman for dealing only with military combatting terrorism operational matters. On military installations, the DOD may delegate the public affairs responsibility to a designated DOD representative.
The Department of State coordinates public affairs during terrorist incidents overseas. The Department of State may delegate the public affairs responsibility to a designated DOD representative.
The office of the Assistant Secretary of Defense (Public Affairs) is the single point of contact for all public affairs aspects of U.S. military combatting terrorism actions. While there is no mandatory requirement to release information, installation commanders are advised to exercise prudent judgement on such matters.
The CMT, when activated, assumes responsibility for the activities of the PAO and media center. The PAO will prepare media releases and conduct briefings during the incident using information provided by the EOC and the commander. The PAO must be fully apprised of the situation as it develops. Neither the PAO nor the media representatives should have direct access to hostages, hostage takers, or anyone directly involved in a terrorist incident.
POST-INCIDENT RESPONSIBILITIES
During the immediate post-incident phase, medical and psychological attention, along with other support services, should be given to all personnel involved in the operation, to include captured terrorists. A final briefing should be given to media personnel but they should not be permitted to visit the incident site. Because of the criminal nature of the terrorist event, the site must be secured until the crime scene investigation is completed by the investigative agency. It is also imperative that every action that occurred during the incident be recorded.
In the aftermath of a terrorist incident, the CMT reviews all the events and actions to revise the threat statement, if necessary, and to determine the effectiveness of the combatting terrorism plan. All personnel involved in the counterterrorism operations should be debriefed and the debriefings recorded. This information will be used to develop lessons learned and after action reports. It is the responsibility of the commander to ensure that all required after action reports are prepared and subsequently reviewed with representatives of the staff judge advocate's office.
PART D: UNITED STATES GOVERNMENT POLICY
The counterterrorist policy of the United States stresses three general rules:
- First, make no deals with terrorists and do not submit to blackmail.
- Second, treat terrorists as criminals, pursue them aggressively, and apply the rule of law.
- Third, apply maximum pressure on states that sponsor and support terrorists by imposing economic, diplomatic, and political sanctions and by urging other states to do likewise.
Since the mid-1970's, terrorist attacks on U.S. citizens both at home and abroad have caused the problem of terrorism to be elevated from a police matter to an aspect of national policy. As policy evolved, it was necessary to delineate major responsibilities and legal constraints regarding policy execution. The following outlines the policy and responsibilities generally applicable to the U.S. Army:
All terrorist actions, whatever their motivation, are criminal, intolerable, and should be condemned.
All lawful measures will be taken to prevent terrorist acts and to bring to justice those who commit them.
Concessions will not be made to terrorist extortion, because to do so invites further demands.
The United States presumes that the host government will exercise its responsibility under international law and protect all persons within its territories. When Americans are abducted or held captive, the host government is expected to do its utmost to effect the safe release of the hostages.
During incidents affecting Americans, the U.S. Government will maintain close and continuous contact with host governments and support them with all practicable intelligence and technical services. The United States will also offer advice on how to respond to specific terrorist demands.
International cooperation to combat terrorism is a fundamental aspect of U.S. policy. All avenues to strengthen such cooperation will be pursued.
PART E: LEGAL CONSIDERATIONS
Terrorist acts are criminal acts, whether committed in peacetime or wartime. One difference in combatting terrorism in wartime involves jurisdiction to punish terrorists. In peacetime, terrorist acts are punishable under the Antiterrorism and Effective Death Penaly Act of 1996. This is also true for a Stability and Support Operations (SASO) (except for joint operations which then it's called Joint Operations Other Than War (OOTW)) which is characterized by police actions to maintain the legitimate government. If, however, the conflict is internationally recognized as an insurgency, then the protections under article III common to the four Geneva conventions apply. Article III requires that noncombatants, including captured terrorists, be treated humanely.
Even in an internationally recognized war or conflict (conventional, limited, or civil war), a terrorist act is a criminal act. Only combatants can legitimately attack proper military objectives. Lawful combatants who commit violations of the law of land warfare, such as attacking unlawful targets, are entitled to prisoner of war status and are subject to the laws of war. Terrorists, by definition, do not meet the four requirements necessary for combatant status (wear distinctive insignia; carry arms openly; commanded by someone responsible for their actions; and conduct operations in accordance with the laws of war). Therefore, they are not afforded prisoner of war status. However, the law of land warfare requires that we treat them humanely.
A commander's authority to enforce security measures and to protect persons and property increases with the level of conflict. Commanders must coordinate with their legal advisors to determine the extent of their authority to combat terrorism in time of conflict.
CONSTITUTIONAL
The constitution restricts the use of military forces to enforce federal laws. When civil law enforcement agencies are unable to control events, however, constitutional exceptions permit the U.S. Government to use military forces to preserve law and order within its territorial limits. Exceptions include the following:
Emergency Authority: This authorizes prompt and vigorous federal action, to include the use of military forces, to prevent loss of life or wanton destruction of property. Emergency authority is used to restore governmental functioning and public order when duly constituted local authorities cannot control the situation. This may occur during unexpected civil disturbances or disasters.
Protection of Federal Property and Functions: This authorizes federal actions, to include the use of military forces, to protect federal property and functions. This authority is used when duly constituted local authorities are unable or decline to provide adequate protection.
STATUTORY
Restrictions on the use of military personnel in the U.S. or its possessions are imposed by the Posse Comitatus Act (18 US Code (USC) 1385). It does not apply in foreign countries; to actions on military bases; in military contracted buildings and spaces; nor in guarding military property in transit. For OCONUS, the host nation has primary authority as set forth in applicable Status of Forces Agreements (SOFAs). Except as authorized by statue or the constitution, the Posse Comitatus Act prohibits the use of DOD uniformed personnel as part of a posse comitatus to assist local law enforcement officers in carrying out their duties. The same prohibition applies to the use of troops to execute federal laws.
Title 10 (USC 371-378) and AR 500-51 provide for military assistance to civilian law enforcement agencies by sharing information, providing equipment, and by training and advising.
Congress, pursuant to its constitutional authority, has provided a broad range of legislation authorizing the President to use regular and federalized forces to execute the laws. The President is currently empowered to use military forces for the following:
To restore and maintain public order.
To meet specified contingencies.
To cope with domestic emergencies.
To protect public safety.
AUTHORITY AND JURISDICTION
At the national level, the Department of State is the lead agency for response to terrorist incidents that take place OCONUS. The Department of Justice (DOJ) is the lead agency for domestic terrorism. Exceptions are actions that threaten the safety of persons aboard aircraft in flight or that involve nuclear weapons. These are the responsibility of the Federal Aviation Administration (FAA) and the Nuclear Regulatory Commission (NRC), respectively. All federal agencies that have resources for responding to terrorism are linked together through agency command centers and crisis management groups to ensure effective coordination of the U.S. response.
Major organizations with jurisdictional authority in a terrorist incident involving military assets in the United States are the DOJ, the FBI, and the DOD.
The DOJ is responsible for overseeing the federal response to acts of domestic terrorism. The Attorney General of the United States, through an appointed Deputy Attorney General, makes major policy decisions and legal judgments related to each terrorist incident as it occurs.
The FBI has been designated as the primary operational agency for the management of terrorist incidents occurring in the United States. When an incident occurs, the first reaction is generally from the special agent in charge (SAC) of the incident area. The SAC is under the supervision of the Director of the FBI. The FBI maintains liaison with each governor's office which is renewed with every change of administration. There is a SAC for each field office throughout the United States. Due to concurrent jurisdiction, the FBI cooperates with state and local law enforcement authorities on a continuing basis.
In accordance with a DOD, DOJ and FBI Memorandum of Understanding, all military preparations and operations, to include the employment of military forces at the scene of a terrorist incident, are the primary responsibility of the Secretary of Defense (SECDEF). In discharging these functions, the SECDEF observes law enforcement policies as determined by the Attorney General. DOD responsibilities are carried out principally through the Department of The Army (DA), since the Secretary of the Army has primary responsibility for these matters as the DOD executive agent. The Attorney General, through the FBI, coordinates the activities of all federal agencies involved in resolving the incident. He also administers justice in the affected area and coordinates these activities with state and local agencies.
Upon notification of Presidential approval to use military force, the Attorney General advises the Director of the FBI who notifies the SAC. The SECDEF advises the military task force commander. The Commander, Task Force (CTF), and the SAC coordinate the transfer of operational control to the CTF. However, the SAC may revoke the military commitment at any time prior to the assault phase if he determines that military intervention is no longer required. The CTF must agree that a withdrawal can be accomplished without seriously endangering the safety of personnel involved in the incident. If the assault phase is required, the CTF will determine when that phase of the operation is completed and then promptly return command and control to the SAC.
On a military installation, the military commander who is responsible for the maintenance of law and order may take immediate action in response to a terrorist incident. The FBI is notified as soon as possible of all terrorist incidents on military installations. The Attorney General, or his designated representative, determines if the incident is of significant federal interest. If it is, the FBI assumes jurisdiction and the Attorney General coordinates the response. Should military assistance be required, it is furnished in accordance with the procedures prescribed in the memorandum of understanding. If the FBI declines to exercise its jurisdiction, military authorities take appropriate action to resolve the incident.
For incidents on U.S. military installations OCONUS, the installation commander's responsibilities under AR 210-10 are the same as in CONUS with the added requirement to notify the host nation and the Department of State. The Department of State will take primary responsibility for dealing with terrorism involving Americans abroad. Any response taken by the installation will be subject to agreements established with the host nation.
The response to off-post OCONUS incidents is the sole responsibility of the host nation. US military response, if any, depends on the applicable SOFA or memorandums of understanding, and is coordinated through the U.S. Embassy in that country. Military forces will not be provided to host nation authorities without a directive from DOD that has been coordinated with the Department of State. The degree of Department of State interest and involvement of U.S. military forces depend on the incident site, the nature of the incident, the extent of foreign government involvement, and the overall threat to U.S. security. A matrix outlining jurisdiction authority for handling terrorist incidents (CONUS and OCONUS) is depicted in Figure 3-4.
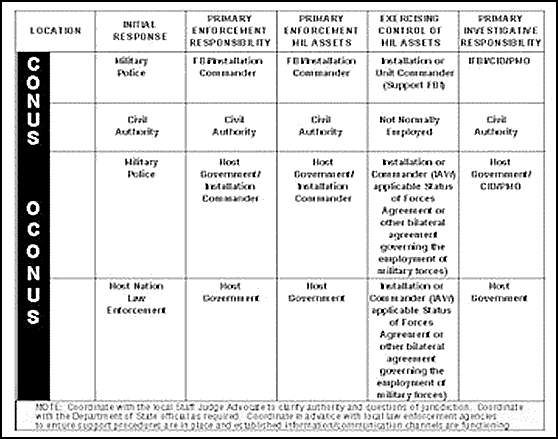
Figure 3-4. Jurisdictional Authority for Terrorist Incidents.
Practice Exercise

