|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 2
TERRORIST ORGANIZATION
CRITICAL TASK: 301-340-1093
OVERVIEW
TASK DESCRIPTION:
In this lesson, you will learn how terrorist groups are organized, how to identify different terrorist groups, what tactics terrorist groups use, why Americans are targets of terrorists, the definition of domestic terrorism, and how to describe the phases of a terrorist incident.
LEARNING OBJECTIVES:
| ACTIONS: | Describe terrorist tactics; identify terrorist groups, outline the terrorist organizational structure; define domestic terrorism; and describe the phases of a terrorist incident. |
| CONDITIONS: | You will be given narrative information, the case history of a terrorist incident, and extracts from AR 525-13. |
| STANDARDS: | Proposals developed to implement a terrorism counteraction plan at the local level will be in accordance with AR 525-13 and FM 100-37. |
| REFERENCES: | The material contained in this lesson was derived from the following publications: AR 525-13. FM 100-37. |
INTRODUCTION
Terrorists organize to function in the environments where they carry out their acts. Organizational details are situation-specific. There are, however, a few general organizational principles. Because terrorists must operate in a hostile environment, security is their primary concern. Security is best served by a cellular structure in which members do not know and cannot identify more than a few of their colleagues in the event of capture or defection. Defection is rare in most groups; defectors or even dissenters are frequently killed or maimed. Yet, terrorists are not immune to human weaknesses. Unless they are united by a charismatic leader, terrorists are affected by group dynamics that produce both problems and opportunities for security forces. Opportunities arise because internal dissension causes security leaks; problems arise because operational patterns may change as different factions prevail. Terrorist groups that are not supported by a government usually create a support structure of sympathizers and people who have been coerced into helping them. The support structure may comprise active and passive members. It furnishes the active terrorists with logistic support, intelligence, dissemination of propaganda, recruiting, and money.
Terrorist recruitment and training are, predictably, security-sensitive. Among groups that are not ethnic-based, the usual sources of recruits are high school and college students who show commitment to the cause. Ethnically based terrorist groups recruit new members personally known to them, people whose backgrounds are known and who often have family ties to the organization. Intelligence penetration of organizations recruited in this way is extremely difficult.
Terrorist training varies considerably. Those with military experience or who have received prolonged training at sophisticated facilities are the equals of most state security forces. At the other end of the spectrum are "throw away" operatives who get little more than inspirational talks before being activated. Typical training includes instruction in the use of small arms and explosives along with intelligence collection and indoctrination in the group's cause.
Contemporary terrorist actions include the traditional assassinations, bombings, arson, hostage-taking, hijacking, kidnapping, seizure and occupation of a building, attacks on a facility, sabotage, and perpetration of hoaxes. Newer categories of operations include ecological terrorism and the still largely potential "high-tech" terrorism using nuclear, biological, and chemical (NBC) weapons and materials. Target selection considerations are equally diverse but include the target's value in terms of its contribution to group goals, its accessibility given group capabilities, and the purpose of the attack, such as to gain attention, collect resources, eliminate a threat, or demonstrate a capability. All these factors are reflected in the group's organization and training.
PART A: TERRORIST TACTICS
The immediate objectives of any given terrorist attack are to attract attention to the group or its cause(s), demonstrate the group's power, extract revenge, obtain logistical support, or cause a government to overreact. Terrorist tactics and strategies are limited only by their imagination. Just as a terrorist incident may have several objectives, the tactics used may also be combined. The more common tactics employed by contemporary terrorist groups are:
Assassination. An euphemism for murder generally applied to the killing of prominent persons and symbolic enemies as well as traitors who defect from the group. There are as many variations to assassination techniques as there are ways to kill a human being.
Arson. Less dramatic than most tactics, arson has the advantage of low risk to the perpetrator and requires only a low level of technical knowledge.
Bombing. The Improvised Explosive Device (IED) is the contemporary terrorist's tactic of choice which is used more frequently than other types of explosives. IEDs are inexpensive to produce and, due to the various detonation techniques available, pose a low risk to the perpetrator. Other advantages include their attention-getting capacity and the ability to control casualties through time of detonation and placement of the device. Two of America's most famous bombings, the World Trade Center and the Federal Building in Oklahoma, showed America how dramatic explosive devices could be.
Hostage-taking. This usually is an overt seizure of one or more people with the intent of gaining publicity or other concessions in return for release of the hostage(s). While dramatic, hostage and hostage barricade situations are risky for the perpetrator when executed in an unfriendly environment. Comparisons of how the environment affects the outcome of hostage-taking situations may be made by comparing the seizure of the Iranian Embassy in London in 1981 and with the seizure of the US Embassy in Teheran in 1979. In the former incident, only one terrorist survived; in the latter, all of the hostage takers survived.
Kidnapping. While similar to hostage-taking, kidnapping has significant differences. Kidnapping is usually a covert action wherein the perpetrators may not be known for some time. News media attention is usually less intense since the event may extend over a prolonged period. Because of the time involved, a successful kidnapping requires elaborate planning and logistics even though the risk to the terrorist is less than in the hostage situation.
Raids. Armed attacks on facilities are usually undertaken for one of three purposes: to gain access to radio or television broadcast capabilities in order to make a statement; to demonstrate the government's inability to secure critical facilities; or for logistical purposes (for example, bank or armory robbery).
Seizure. Similar to the hostage situation, the seizure usually involves a building or object that has value in the eyes of the audience. Publicity is the principal objective. There is some risk to the terrorist because security forces have time to react and may opt to use force to resolve the incident since few or no innocent lives are involved.
Sabotage. The objective in most sabotage incidents is to demonstrate how vulnerable society is to the terrorists' actions. Industrialized societies are more vulnerable to sabotage than less highly developed societies. Utilities, communications, and transportation systems are so interdependent that a serious disruption of any one affects them all and gains immediate public attention. Sabotage of industrial or commercial facilities is one means of identifying the target while making a statement of future intent.
Hijacking. Sometimes employed as a means for escape, hijacking is normally carried out to produce a spectacular hostage situation. Although trains, buses, and ships have been hijacked, aircraft are the preferred target because of their greater mobility and vulnerability.
Hoaxes. Any terrorist group that has established credibility can employ the hoax with considerable success. A threat against a person's life causes that person and those associated with him to devote time and effort to security measures. A bomb threat can close down a commercial building, empty a theater, or delay a plane flight at no cost to the terrorist. The effects of "false alarms" on the security forces are more dangerous than the temporary disruption the hoax causes. Repeated threats that do not materialize dull the analytical and operational efficiency of key security personnel.
Biological and Chemical Weapons. Biological agents are infectious microbes or toxins used to produce illness or death in people, animals or plants. Biological agents can be dispersed as aerosols or airborne particles. Terrorists may use biological agents to contaminate food or water because they are extremely difficult to detect. Chemical agents kill or incapacitate people, destroy livestock or ravage crops. Some chemical agents are odorless and tasteless and are difficult to detect. They can have an immediate effect (a few seconds to a few minutes) or a delayed effect (several hours to several days).
Biological and chemical weapons have been used primarily to terrorize an unprotected civilian population and not as a weapon of war. This is because of fear of retaliation and the likelihood that the agent would contaminate the battlefield for a long period of time. The Persian Gulf War in 1991 and other confrontations in the Middle East were causes for concern in the United States regarding the possibility of chemical or biological warfare. While no incidents occurred, there remains a concern that such weapons could be involved in an accident or be used by terrorists.
Nuclear Devices. A growing concern is that terrorists will cross the threshold to engage in acts of mass or "super terrorism" by using atomic weapons. So far, the international order has been spared terrorist incidents involving nuclear weapons. Fortunately, the threats of nuclear use have yet to be translated into actual incidents, but many believe it is only a matter of time before they are.
All this could easily change as a result of the disintegration of the Soviet Union. The current trade in illicit weapon's grade plutonium serves to underscore the fact that the necessary material and attendant technology will be increasingly available for those terrorist groups who may want to exercise a nuclear option. The illegal trade in weapons and technology will be further exacerbated by the very real dangers resulting from the proliferation of nuclear weapons. There is good reason to fear that either a rogue state, its terrorist surrogates, or independent terrorist groups will have the capacity to go nuclear. Whether this threshold will be crossed will depend in part on the motivation, attendant strategies, and goals of present and future terrorist groups. In sum, there is every reason to be concerned that terrorists will engage in their own form of technical innovation to develop the capacity to make the nightmare of a nuclear threat very real when it comes to the United States.
Fear of alienation by peer and support populations has probably inhibited the use of chemical and biological weapons to date, but this obstacle could evaporate as the competition for headlines increases and public opinion softens.
PART B: TERRORIST GROUPS
For some years security forces categorized terrorist groups according to their operational traditions--national, transnational, and international. National groups operated within the boundaries of a single nation; transnational groups operated across international borders; international groups operated in two or more nations and were usually assumed to receive direction from a foreign government. Ease of international travel and the growing tendency toward cooperative efforts among terrorist groups have rendered these categories of little use. Terrorist groups are also categorized by government affiliation to help security planners anticipate terrorist targets and their sophistication of intelligence and weaponry. Three general categories that have gained acceptance are:
Nonstate supported. A terrorist group that operates autonomously; one receiving no significant support from any government (for example, Italy's Red Brigades, Basque ETA).
State supported. A terrorist group that generally operates independently but receives support from one or more governments (for example, PFLP in the Middle East).
State directed. A terrorist group that operates as an agent of a government receiving substantial intelligence, logistics, and operational support (for example, Libyan "hit teams").
PART C: TERRORIST ORGANIZATION
As with any organization, terrorist groups develop organizational structures that are functional for the environment in which they operate. Since terrorists must, by definition, operate in a hostile environment, security is the primary consideration. As a result, the organization of terrorist groups is usually cellular, with each cell relatively isolated. This type of organization protects members of the group. In the event of defection or capture, no one member can identify more than a few of the others. Some groups have multifunctional cells that combine several skills in one operational entity, while others create cells of specialists that come together for an operation or on an ad hoc basis. The latter procedure is similar to tailoring or task organizing of military forces.
Larger terrorist groups (100 or more members) normally have a central command and control element with one or more subordinate elements that are based on geographical regions. The regional commanders direct the actions of the operational and support cells in their region. Smaller groups (50 or fewer members) may have a single command element that directly controls all of the operational and support cells regardless of where they are established.
Even though terrorist groups generally structure themselves in a manner similar to military organizations, few, if any, groups are tightly disciplined enough to function along clear lines of authority and functionality. Group dynamics, egos, and philosophical differences override organizational principles and create opportunities for security forces to identify members; penetrate the organization; and/or prevent terrorist actions. These personalistic factors cause terrorist groups to splinter into new factions, adding to the growing list of organizational titles in world terrorism. The commonly used deception techniques of claiming credit for an action in the name of a previously unknown group and splintering complicates the intelligence efforts of security forces.
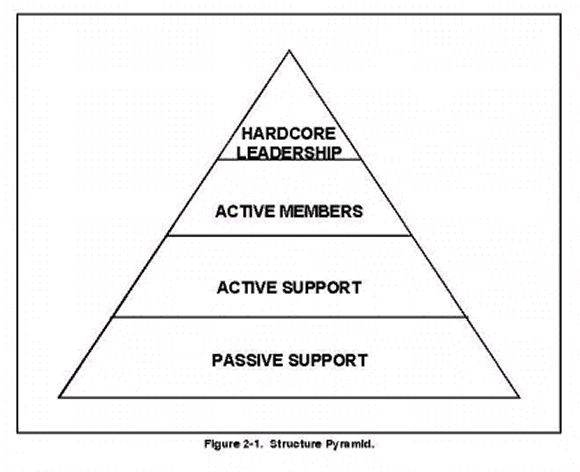
In a broader context, terrorist organizations, especially those with little or no access to government resources, need a support structure. As shown in Figure 2-1, a typical organization consists of operational members who are functionally organized as outlined above and two categories of supporters. At the top is the leadership that defines policy and directs action. Typically, leaders are completely committed to the cause that the group purports to serve and may be charismatic figures. If the group is state supported or directed, the leadership will normally include one or more members who have had extensive training or education by the sponsoring state.
The active cadre, both men and women, are the doers who carry out terrorist attacks and train others. As in the leadership element, many of the doers are deeply committed to the group's cause. The professionals, who may or may not be ideologically motivated, are also part of the active cadre.
Active supporters are people who do not actually commit violent acts, but who assist the terrorists through money, intelligence, legal or medical services, and provision of safe houses or forged documents. Active supporters are frequently ideologically in agreement with all or some of the terrorist group's goals, but may be ambivalent concerning the use of violence. Another motivation is the vicarious thrill derived from safe involvement in violence. Most terrorist groups recruit much of their cadre from the ranks of the active supporters, since these people have proven their loyalty and, to some extent, their skills over a period of time.
Passive supporters are more difficult to define and more difficult to identify. Most of these people are sympathetic to the terrorist group's cause(s), but either cannot or will not assume an active role. Family and acquaintances of activists sometimes fall into this category, especially in cultural environments where family and regional loyalties are strong. The terrorist group relies on passive supporters for financial assistance, displays of public support, and minor logistical or operational tasks.
PART D: TERRORIST TARGETS--UNITED STATES
The new threat environment may see the emergence of a wide variety of sub-national and transnational groups intent on venting their frustrations with Washington for what they perceive to be a lack of support for their causes or, conversely, for supporting their adversaries. As the major military superpower, with an increased global involvement, even when engaged under the United Nations, the United States is likely to be viewed as the primary party in future disputes. Even when neutral, Washington is likely to be viewed suspiciously by one or more warring factions. In addition, when Washington moves beyond "peace keeping" to "peace enforcement" operations, the likelihood of a reaction among one or more disputants is possible.
Even though the United States may not want to be the policeman or the conscience of the world, the parties in any conflict may question whether Washington is intentionally or unintentionally pursuing a political agenda that may be counter to their objective. The result might be the spillover of violence to the United States by one or more parties in the dispute. Resort to terrorism could be a punitive action or it might be an effort to dramatize a cause. As the United States tries to redefine the formulation and execution of its foreign policy in the post-Cold War era, even if Washington is motivated by the highest of ideals, i.e., democratization, humanitarian assistance, or nation-building, those who will be objects of such efforts might resent it. Their use of terrorism on American soil is a likely response.
Mere presence is another factor. Americans in all capacities, from diplomatic service to tourists, are found all over the world. Being available makes targeting Americans easy even for relatively poorly trained nonstate supported terrorist groups. It also adds to the chances of Americans being killed or injured unintentionally. These same considerations apply to members of the US military forces with the added factor of symbolic value. Since the armed forces are clearly visible symbols of US power and presence, terrorists find both installations and personnel appealing targets.
PART E: DOMESTIC TERRORISM
While the US has one of the highest levels of social violence in the world, the incidents of terrorism is very low compared to Europe, Latin America, Africa, or the Middle East. There are several reasons for this seeming inconsistency. First, the United States does not have a tradition of violence for political purposes. Historically, there has been a lack of deep ideological commitment in justifying the taking or sacrifice of life.
The second factor is the absence of ethnic concentrations or restrictive legislation that causes separatist movements. Puerto Rico is the exception with several pro-independence groups practicing terror tactics.
Caution must be exercised in drawing conclusions exclusively from the experiences of the past. Although low levels of domestic terrorism have occurred in the United States to date, terrorism is still a threat in the continental United States (CONUS). Right wing extremist organizations constitute a growing threat to public order. Agents of external causes and foreign powers pose a potential threat that needs only a transoceanic flight or border crossing to become active.
Terrorism is a factor across the spectrum of conflict. It is normally viewed as violence in an environment where there is no armed conflict. Thus, it may be considered as a mode of conflict. In the context of peace, terrorism attracts a great deal of attention and few question its real and potential capacity to kill and destroy. The same can be said of terrorism as an aspect of insurgencies or other forms of internal conflict. Under conditions of open armed conflict, however, terrorism tends to be ignored. The reason for this is our attention (the audience's) is spread over battles and mobilization activities at home and abroad. Thus, acts of terrorism are lost in the sensation-rich atmosphere of war. Although the military commander may not have terrorism brought to his attention during war as it is in times of peace, terrorism does not disappear. The same types of acts that gain attention in peace can hinder military operations in war. Targeting strategies may change and terrorism may be relegated to a tactic rather than a mode of conflict, but the violent acts remain the same. The label may change to sabotage, but the skills required to carry out the attacks are those of the terrorist. More importantly, the defensive practices developed in peace to prevent terrorist acts are the same as those needed in war to thwart sabotage and level I rear area threats.
PART F: ANATOMY OF A TERRORIST INCIDENT
The first phase of a terrorist incident is known as the pre-incident phase which includes extensive and intensive planning by the leadership of the terrorist group. During the pre-incident phase of the operation, intelligence is collected; reconnaissance and rehearsals are conducted; and the political feasibility of the target is considered. Practically all terrorist activities are based on intelligence and security. Normally, the terrorist leaders select several targets, checking all for political feasibility and productivity. Well trained and loyal personnel are used to gather information. Extensive surveillance is maintained and records of the surveillance are kept. Documents showing terrorist surveillance activities, for as long as six months, have been found. Members of the terrorist group are infiltrated into, and new members are recruited from the target area. Rehearsals are generally conducted away from the target area, but normally in an area that resembles the target sight to some degree. In some cases, vehicular ambush rehearsals have actually been conducted on the intended victim prior to the actual attack.
During this phase, the group assembles at a pre-determined point which is usually the last safe area or house used before the strike. This may be where the personnel and the weapons are brought together. The group will put on disguises or other clothing to be used during the strike. Documents, if needed, will be given to the individuals. The final coordination with other groups and within the group will take place. Communication means will be established. Final security aspects for the strikes will be reviewed to ensure everyone understands them. During the final briefing, the actual target will be revealed to the group by the leader. It is during the "movement to the target" that the group is most vulnerable to apprehension by the authorities. The driver may commit a traffic violation or a member of the group may be recognized. Weapons and/or explosives are usually placed in the target area beforehand; but, in some cases, may be carried by the group. Movement to the target may be done individually or by the group as a whole. Transportation may be placed in the target area prior to the group movement.
Attack is when the actual violence begins. Using the element of surprise, the group will detonate the bomb; shoot the victim; or rob the bank. All personnel in the group are fully committed to the act with actions precisely timed to keep the event moving. The execution of the strike will be as dramatic as possible. All members of the group, normally no more than three to five, will attempt to heighten the terror of the moment. Once the attack is completed, the next phase will depend on whether or not hostages were taken. In most cases, no hostages will be taken and the climax phase will follow. If hostages were taken, the terrorists may move into the negotiation phase.
The negotiation phase will exist only when terrorists sieze negotiables, and if there is a possibility of a trade-off between the terrorists and the authorities. Examples of negotiables may be a person or persons (hostages), chemicals, explosives, or facilities. The negotiables seized must be of high value to the authorities. With the advent of a high degree of emphasis on "human rights" by the western democracies in the 1960s, a much greater value was afforded the lives of individual citizens. This situation greatly enhanced the worth of hostages to both terrorists and governments, and led to an increase in this type of terrorist operation. Negotiables may be seized by the terrorists as an intrinsic part of the operations plan, or in the event of contingency or unforseen events such as an unexpectedly rapid response by the authorities. If the seizing of hostages is deliberate, i.e., the objective of the operation, negotiations will probably not begin until both the hostages and terrorists are far removed from the scene of the attack and in an area or location which, if not under the control of the terrorists, is usually at least "neutral ground" in that it is not under the control of the authorities.
If on the other hand, the hostage situation develops because the hostages were taken as a means of "self protection" by the terrorists at the scene of the attack in response to unexpected interference by authorities, it is likely that both the terrorists and hostages will be located in an area or facility at least partially controlled by the authorities. The particular situation has a great bearing on the nature of the negotiations, and how the negotiations will be conducted. Negotiations may be conducted directly between the terrorists and the authorities, through emissaries designated by either party, or even through the media. The negotiation phase is of great importance to the terrorists because of the tremendous amount of publicity generated by and through the media. Terrorist demands may include release of imprisoned comrades, payment of ransom, political concessions by a government or governments, or safe transportation out of the country. Terrorists usually negotiate using the threat of death to hostages as the major bargaining point, while the authorities consider the major function in the negotiations as saving innocent lives. Compromise and agreement become possible when the continued survival of the terrorists becomes a realistic issue.
A major factor in hostage negotiation is a phenomon known as the "Stockholm Syndrome." The term originated after the completion of a psychological study of released hostages following a 1964 non-terrorist hostage situation in Stockholm, Sweden. It was found that during the several days of the hostage situation, a psychological and emotional transference of identity occurred between hostage taker and hostages. This symbiosis was apparently caused by the isolation of hostages and hostage taker from outside stimuli, compounded on the one hand by the total dependence of the hostages on the good will of the hostage taker, and on the other hand by the almost paternal feelings the hostage taker developed toward the hostages because of that dependence. It has been shown that after the first 24 hours of a hostage situation, this syndrome begins to develop, and gains in intensity throughout the situation, leading to an ever-increasing reluctance on the part of the hostage taker to harm or kill the hostages. Both authorities and terrorists have learned from this development. Authorities involved in hostage negotiations generally attempt to lengthen negotiations in order to allow the Stockholm Syndrome to develop and stengthen. Terrorists, realizing that the effects of the Stockholm Syndrome could be a detriment to operations, have developed various methods to prevent its development. Terrorists assigned as guards for hostages are rotated frequently and ordered to have no personal contact with the hostages. When possible, hostages are isolated. In some cases where the terrorist leaders envision the probability of killing one or more hostages for any reason, those to be assigned the task of murder(s) will have no contact with the hostages until the appointed time of the act. Terrorists as well as the authorities learn from mistakes and events, and can be expected to change patterns of activity to meet new tactics and challenges presented by the authorities.
This phase will follow the initiation phase if no negotiation phase is implemented. Examples are bombings, assassinations, or any incident in which an assault is conducted and no hostage/kidnapping or similar situation develops. The end of the climax phase is usually marked by the withdrawal of the terrorist from the target area.
POST INCIDENT PHASE
During the post incident phase, the members of the terrorist organization relocate and regroup to critique their mission. Mistakes are identified; discussed; and solutions recommended for implementation in future planning. Then the cycle begins again.
Practice Exercise

