|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 3
ORGANIZATION AND MAINTENANCE OF INTELLIGENCE FILES AND DETERMINING INFORMATION/INTELLIGENCE REQUIREMENTS FOR OB
|
CRITICAL TASK: 301-372-3151
OVERVIEW
LESSON DESCRIPTION:
In this lesson, you will learn to organize and maintain approved intelligence files and determine information/intelligence requirements.
TERMINAL LEARNING OBJECTIVE:
TASKS: Describe the information and procedures required to organize and maintain approved intelligence files and determine information/intelligence requirements.CONDITIONS: You will be given narrative information from AR 25-400-2, AR 220-15, AR 380-5, and FM 34-3.
STANDARDS: Organize and maintain approved intelligence files, and determine information/intelligence requirements IAW AR 25-400-2, AR 220-15, AR 380-5, and FM 34-3.
REFERENCES: The material contained in this lesson is derived from the following publications:
AR 25-400-2
AR 380-5
FM 34-3
Intelligence files are necessary to permit ready access to all available information. The files most commonly maintained are listed below.
PART A: ORGANIZATION AND MAINTENANCE OF INTELLIGENCE FILES
Journal File. The journal file contains a record copy of each message or document noted in the journal. It supports the journal and is also a permanent and official record.
OB Files. The OB files may be just an OB workbook or more extensive files. When made, the extensive files should conform with AR 25-400-2. The file number is 380 or 381. When preparing the OB files, you will use the nine OB factors.
The following list of files is extracted from AR 25-400-2, The Modern Army Recordkeeping System (MARKS), October 86, concerning security and military intelligence.
| File No. | Description | Disposition |
| 381a. | Intelligence reports files.Reports are gathered in intelligence offices resulting from the-- a. Collection, evaluation, analysis, integration, and interpretation of technical intelligence. b. Domestic intelligence or information about activities or conditions in the US which possibly or really threaten the internal security. c. Information on the war potential, military geography, military forces, and other military and related activities of foreign countries. NOTE: Record copies of intelligence reports are kept by the Defense Intelligence Agency (DIA). |
Destroy after 2 years |
| 380-150a | Intelligence collection files. Documents on the procurement and selection of intelligence information. They also include-- a. Intelligence collection plans. b. The scheduling of collection requirements. c. The monitoring and evaluation of collection priorities. |
|
| 380-150b | Scientific and technical intelligence product files. These files consist of-- a. One copy of each confirmed DIA scientific and technical intelligence production (study, trend study, report, handbook,and comparable productions). b. Contributions (inputs) to other agency products. |
Permanent |
| 380-150c | Intelligence dissemination files. Documents on the dissemination and distribution of-- a. Finished intelligence. b. Intelligence reports. c. Scientific and technical information. |
Permanent. |
| 381-20a | Intelligence confidential fund files.Documents on expenditures of special funds. These funds cover expenses incurred in discharging assigned duties of agents for the Deputy Chief of Staff for Intelligence (DCSINT) not otherwise payable from other DA funds. Included are-- a. IG inspection reports of accounts. b. Intelligence contingency funds. c. Property books. |
Offices performing Army-wide responsibility: Destroy after 8 years. |
| 381-20b | Captured documents files.Documents captured or confiscated in wartime by international law. This also includes records of foreign government, military,private, and other institutions. Keep a separate entity to preserve administrative origin and arrangement to the fullest extent practicable. (This description does not include captured cryptologic records.) NOTE: After an Army agency has completed intelligence or other exploitation of captures documents, it will request disposition instructions from HQDA (SAIS-ISP), Washington, DC 20310. |
Permanent. |
The following list of files is extracted from AR 25-500-2.
| File No. | Description | Disposition |
| 381 | These records concern collection, identification, evaluation, control, classification, and dissemination of general and technical intelligence data. Matters relating to subversion, espionage and counterintelligence activities. a. General military intelligence correspondence files. General correspondence relating to military intelligence that cannot logically be filed with the detailed record listed below: b. Documents relating to military intelligence that are received for information only and on which no action is required. |
Destroy after 2 years. Destroy when no longer needed for current operation. |
| 381a | Intelligence reporting files. These files consist of copies of documents that have been submitted to higher headquarters.Included are-- a. Reports on domestic intelligence. b. Foreign positive intelligence c. Technical intelligence. d. Related documents. |
Destroy after 2 years. |
You should use the files listed in AR 25-400-2 at all levels. Approved intelligence files are those files you, as the supervisor, have deemed necessary. The unit records management officer will approve files not shown in regulations.
These files will be cut off on 31 December of each year and a new file will be started. The disposition or time period for which you must retain these files is noted in each extract.
When preparing these files for use, you can prepare one file folder or binder at a time. Prepare succeeding file folders on an "as needed" basis.
The lead file folder will contain the title and disposition; succeeding folders will have the file number and source or document and title. More information on this subject may be found in AR 25-400-2.
Information filed in the information/intelligence files can be cross-referenced to other files with the same or corresponding information. When cross-referencing, you need to place a form (DA Form 1613) in each file which you want cross-referenced. This is described in AR 25-400-2.
Updating the Information/Intelligence Files. Updating the Information/Intelligence Files consists of either adding changes or supplements to existing documents or removing obsolete or superseded documents from the files. Documents may be bound, loose, or stapled together. These documents may be technical or doctrinal studies of enemy weapons or tactics.
When adding supplements to the information/intelligence file, you will place them with the original document. They may be new pages or additional pages to be added to the original. A supplement may be a continuation of the information in the original document.
Changes are made to the content of the original or merely added to the document. When making a change, the analyst should place the DTG when he made the change and his initials on the front page of the change.
The information/intelligence files may be classified, and the analyst must ensure the change or supplement has the same classification markings on it as the original. When an unclassified supplement is added to a classified document, you must either file it as a whole or add it to the document and add classification markings.
Whenever documents are removed from a classified file, a cover sheet with the appropriate classification shown must be attached.
Cross-referencing. The OB and information/intelligence files can be cross-referenced. This means most of the information contained within one file can be found in another file. This saves time when trying to find information on a subject.
In cross-referencing, you will normally write it on a form within the file. For OB files and workbook, you will note next to the data on the data sheet where additional information, or the report is filed.
A DA Form 1613 will be used when cross-referencing the information/intelligence files. The form may be used in the OB files when information is not heavily cross-referenced and will be placed in the front of the files being cross-referenced. Additional information may be obtained from AR 25-400-2.
Maintenance of the Information/Intelligence Files. When using the information/intelligence files, you must remember information will become obsolete or superseded. You must review the files at regular intervals to ensure the information remains current.
In filing, you will put the new information in front of the old. This will keep the newest information within easier reach. It will also make integration easier because the newest information can be compared as you place it in the file.
PART B: DETERMINING INFORMATION/INTELLIGENCE REQUIREMENTS FOR OB
The commander directs the intelligence effort through the G2 or S2. The G2 or S2 translates the commander's guidance and concept of the operation into intelligence requirements and establishes priorities. Intelligence requirements and priorities are expressed in terms of PIR and IR (see Figure 3-1).
DEFINITION OF PIR/IR
INFORMATION AND INTELLIGENCE REQUIREMENTS |
| PRIORITY INTELLIGENCE Those intelligence requirements for which a commander has an anticipated and stated priority in his task of planning and decision making. |
| INFORMATION Those items of information regarding the enemy and his environment which need to be collected and processed in order to meet the intelligence requirements of the commander. |
Figure 3-1.
PIRs are the highest priority intelligence requirements. Any enemy capability, course of action, or characteristic of the battlefield environment which will have a critical impact on the commander's tactical decisions are PIR.
IRs are the specific items of information needed to satisfy the intelligence requirements. They are a basis for collection operations. They include information needed to satisfy PIR as well as the other intelligence requirements.
What does this mean to you as an OB analyst or as an intelligence officer working in OB? PIRs are those items of information which you will need to answer questions regarding the enemy situation. IR is information you need to confirm a specific deduction you have made.
Determining the Initial Information/Intelligence Requirements. The initial requirements for information/intelligence are determined when the unit receives its mission. At division, the corps intelligence estimate will contain the OB information needed to start your files. At brigade and battalion you will use the division's intelligence estimate.
Once you have received the initial OB information, you will determine what information you will need to supplement or complete the information received. This is done by a careful review of the information on hand and the AO. Your review is aimed at finding gaps in the information. If there are gaps in the information, you need to answer questions from the G2 or commander, you will submit a recommendation that information be collected as PIR to fill these gaps. If the gaps are in areas where you need information to clarify deductions or enemy actions, you will submit a recommendation for collection as IR.
You determine periodic requirements for information/intelligence in essentially the same way.
COLLECTIONS AND PROCESSING OF OB INFORMATION
Collection. OB information is collected by all personnel in a unit. The soldiers in the front line will report what they see. This combat information then will be passed through channels for use by the OB analyst.
OB analysts and intelligence officers assist the G2 in continuously planning the collection effort. They may be required to draft collection memoranda for the guidance of collection agencies. The OB analyst or intelligence officer will review the OB files to ascertain what gaps exist in the holding and report these gaps to the G2 for inclusion into the collection effort.
Organization for Collection and Processing. Most of the processing at division is done in the ASIS, Division Tactical Operation Center Support Element (DTOCSE), of Headquarters, Headquarters Company Division. Some of the processing will be done in the battalion and brigade S2s.
The company team will draw its assets from the different companies of the battalion. The Headquarters, Headquarters and Support Company will supply the Deployable Intelligence Support Element (DISE). The collection and jamming (C&J) company will supply the very high frequency (VHF) electronic attack (EA), high frequency (HF)/VHF EA, voice intercept, and transcription and analysis teams. The Intelligence and Surveillance (I&S) company will supply ground surveillance radar, Counterintelligence (CI), and interrogation teams. The company team headquarters may be the headquarters of one of the companies, either Electronic Warfare (EW), C&J, or intelligence and surveillance.
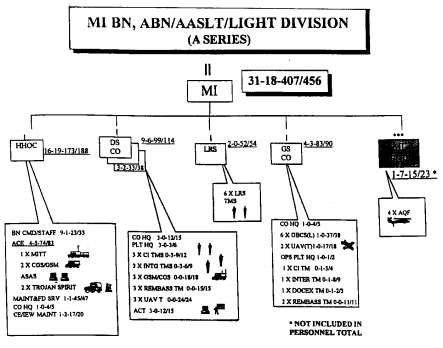
Figure 3-2A MI Bn. (A series)
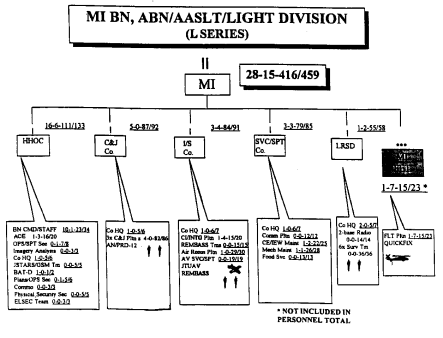
Figure 3-2B MI Bn. (L series)
Other agencies are also used to collect information. The cavalry unit assigned to division and the scout platoons in the battalions will report on the enemy's disposition. The Division G2 will also assign collection missions to units subordinate to the division, and task them through the G3. The corps G2 will provide reports of aerial reconnaissance, long- range ground surveillance and OB references.
The collection effort begins by determining requirements and establishing their priorities. Based on requirements, the analytic and control element (ACE) manages the collection effort. The ACE develops a collection plan that is keyed to mission, enemy, terrain, troops, and time available (METT-T), the commander's concept of the operation, and the current situation. It continuously updates the collection plan.
The ASIS assists the ACE in planning and supervising the collection effort. The All-source production section (ASPS) identifies gaps in the intelligence data base and helps convert intelligence requirements into specific information requirements (SIR). The ASIS monitor incoming reports and advise the ACE PIR and IR are satisfied, new requirements are identified or requested information is no longer needed.
Processing Information. Processing is the phase in the intelligence cycle whereby information becomes intelligence. It consists of recording, evaluating, and analysis (Figure 3-3).
Recording. Recording information into the data base makes evaluation and analysis easier and more accurate. Each echelon must decide on the recording means that permits timely dissemination of information and intelligence. The most common means are the intelligence journal, intelligence files, situation map (SITMAP), intelligence workbook, coordinate register, and OB records. Other files and maps are used when required.
Evaluation. Evaluation of information is needed to determine its intelligence value. Evaluation includes determining the pertinence of information, the reliability of the source or agency, and the credibility of information.
At this stage, the information must also be evaluated for credibility and pertinence. Credibility has two components: Source reliability and information credibility.
Determining Source or Agency Reliability. The headquarters closest to the source, or agency, is ordinarily the best judge of the reliability of the source or agency. Source reliability is determined and recorded on the incoming report by the collecting unit or agency. The ASIS personnel also judge reliability based on the past performances of the reporting unit or agency by comparing it with similar information which may already be available, and assess an overall reliability factor for each incoming report. The overall reliability factor is marked on each report and clearly distinguished from the factor assessed by the reporting agency. The reliability of each incoming item is evaluated by a standard system using letters A to F. The overall source or agency reliability factor is signified by various degrees of confidence as shown in table 1.
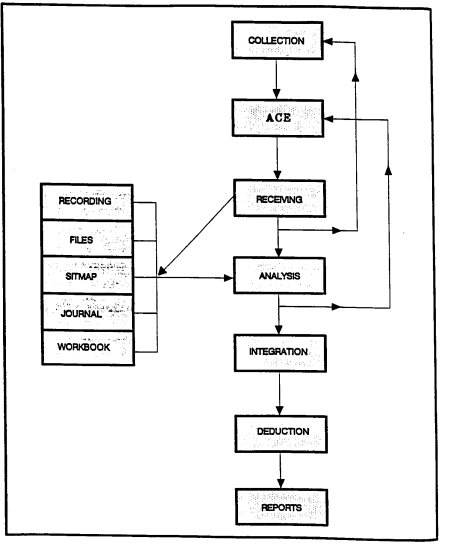
Figure 3-3. Order of battle recording devices and the processing of order of battle information.
Determining Credibility of Information. Credibility is designated by a number between 1 and 6 as shown in table 2.
| LETTER | DEGREES OF CONFIDENCE |
USE |
A |
Completely reliable |
Only assigned under the most unusual circumstances. |
| B | Usually reliable | Indicates a source of energy of known integrity. |
| C | Fairly reliable | Indicates a source or agency that is fairly reliable. |
| D | Not usually reliable | Indicates a source or agency not usually reliable. |
| E | Unreliable | Indicates a source or agency usually unreliable. |
| F | Reliability cannot be judged | Assigned when there is no adequate basis for estimating the reliability of the sources. |
| LETTER | DEGREES OF CONFIDENCE |
USE |
1 |
Confirmed by other sources | Used when it can be stated with certainty that the information originated from two or more different sources. |
| 2 | Probably true | Used when no proof of the above can be established, and no reason exists to suspect that the reported information comes from the same source. |
| 3 | Possibly true | Used when investigation reveals that the reported facts are compatiable with the previously observed behavior of the target, or if known background of a target leads to the deduction that the target might have acted as reported. |
| 4 | Doubtful | Used when reported but unconfirmed information contradicts the estimate to the development or the known behavior of a target. |
| 5 | Improbable | Used when reported information is not confirmed by available data and contradicts the experience assumed to be reliable with regard to the development of a target or issue. |
| 6 | Truth cannot be judged | Used when an investigation or a report reveals that a basis for allocating ratings 1 to 5 does not exist. |
Combined Ratings. To determine the combined ratings, the two aspects of evaluation, reliability and credibility, must be considered independently. The rating is expressed as a letter-number combination. For example, information received from a usually reliable source judged as "probably true" is rated as "B2". Information from the same source, but judged as "cannot be judged" is rated as B6.
Pertinence. The next step in the process is evaluating intelligence and information reports for pertinence. Information is evaluated for pertinence by determining if the information is-
Pertinent in regard to the enemy or the characteristics ofthe AO.
Needed immediately.
Of future value.
Of no apparent value.
A decision is then made concerning the report's value. If a report is determined not to be pertinent, it will be filed for possible future reference. Coordination with the collection manager in the ACE is made to modify or clarify tasking. Pertinent information is then used with other information in the data base.
Analysis consists of three steps, shown below.
Assessment. Assessment is the sifting and sorting of evaluated information to update significant elements with respect to the mission and operations of the unit. Assessment requires judgment and a thorough knowledge of the principles of military operations, the characteristics of the BA, and the enemy situation, to include enemy doctrine and past practices, and a clear understanding of the unit mission and the commander's intent.
Assessment at headquarters above division level often involves detailed research, with greater difficulty caused by the increased volume of information. The individuals who will be involved in performing analysis must relate their efforts to the mission of the command in order to avoid wasted time and effort.
Integration. Integration is the combination of the elements isolated in analysis with other known information. It forms a logical picture or hypothesis of enemy activities or the influence of operational area characteristics on the mission of the command. In the process, more than one hypothesis may be formulated based upon existing intelligence.
Integration, particularly the development of hypotheses, requires the same good judgment and thorough background knowledge essential to making a good analysis. In formulating hypotheses, the intelligence officer must avoid pre-conceived opinions and hypotheses based solely on personal experience or preference. He must attempt to place himself in the role of the enemy commander in the development of these hypotheses.
After they are formulated, hypotheses are analyzed and tested. Analysis of a hypothesis includes determining the indications that should exist if the hypothesis is a valid one. Testing includes verifying the existence or non-existence of these indications within the limitations of available time and means.
Integration may be a mental process completed in a few moments or it may be a lengthy process involving the collection of a large volume of additional information.
Deduction. The last step in the analysis of information is deduction. Meaning is deduced from the hypothesis developed; these are then tested and considered valid as a result of integration. Deduction answers the question, "What does this information mean in relation to the area of operations, the enemy situation and the friendly commander's intent?" The resulting answer reduces friendly vulnerability to being deceived and the false belief that tactical deception (TAC-D) operations are being believed by the enemy.
In the process of assessment, you will sift all the information you have received from all sources and weigh it against the information on file and against known enemy doctrine.
Integration is the placing of new information in the file and purging of superseded information. Place new information with similar information in the file so you can see the progress of an enemy action or determine the lack of a specific action.
You make your deductions based on the information you have gleaned from your files, the enemy situation, and known enemy doctrine as you perceive them.
This process will enable you to answer questions given to you by the commander, G2, or officer-in-charge concerning probable courses of action, current strengths, or disposition of enemy forces.
The commander's PIR will come to you in the form of questions such as, "Will the enemy reinforce? If so, when, where, and in what force?" When you analyze the PIR you will ask yourself what indicators would provide an answer. In the example you would ask yourself, quot;What are the indicators of enemy intent to reinforce?" If you look in appendix C of this subcourse, you will find several indicators listed under reinforcement. They are:
Movement of additional troops toward the front.
Increased traffic toward present position.
Identification of new units in the combat zone.
Additional command posts (CPs) and supply and evacuation installations.
When you review your OB records and incoming messages from collection agencies, you could find a credible message that describes a new enemy unit in the combat zone. If you do, the first part of the commander's question can tentatively be answered "yes," and you have some information useful in answering the second part. When your review of data on hand does not provide answering information, these agencies will be tasked to collect them.
The reports you generate from OB information are a record of your deductions and assumptions. In some reports, you will record and disseminate the actual OB information as well.

