|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
Lesson 2
CONSIDERATIONS FOR DEFENSIVE OPERATIONS
OVERVIEW
Lesson Description:
In this lesson you will learn the purposes and characteristics of defensive operations. Additionally, this lesson describes the defensive framework and defensive patterns used in such operations. The lesson also lists the support assets, which must be synchronized in order to maximize combat power. Finally, the capabilities of light and heavy forces are discussed.
Terminal Learning Objective:
| Action: | Identify the considerations necessary for defensive operations. |
| Condition: | Given the subcourse material contained this lesson. |
| Standard: | You must correctly answer 70 percent or higher of the questions on a multiple-choice test covering the lesson material. |
| References: | The material contained in this lesson was derived from the following publications: |
| FM 7-10 FM 7-20 FM 71-1 FM 71-21 |
FM 71-3 FM 100-5 FM 101-5-1 |
INTRODUCTION
The ideal outcome of defensive operations is to cause the enemy attack to fail and to create conditions favorable for assuming the offensive. The efforts of every unit participating in a defensive action are directed toward this ultimate goal. As a commander, it is important to master the fundamentals of conducting a defensive operation You may expect to be assigned this basic mission, either as commander of an independent unit or part of larger force.
PURPOSES OF DEFENSIVE OPERATIONS
1. Goal: Assume the Offensive. The defense is the commander's primary means of defeating an attacking enemy. The success of the defense will depend on the commander fully understanding and implementing the five purposes of the defense; defeat an enemy attack, gain time, concentrate forces elsewhere, wear down enemy forces, and retain tactical objectives. While the ultimate goal of defense is to allow friendly forces to assume the offense, a defensive mission may be oriented toward any of these intermediate purposes.
a. Defeat an Enemy Attack. The immediate purpose of any defense is to defeat the attack. Other purposes, while important, are ancillary from an operational perspective.
b. Gain Time. Defense is used to gain time for reinforcements to arrive or to permit maneuver forces to reposition in order to attack and destroy an attacking enemy. Gaining time prevents quick enemy successes that would make a synchronized defense by the unit impossible.
c. Concentrate Forces Elsewhere. Based on his own estimate of the situation and higher commander's concept, the brigade commander decides where to concentrate his main defensive effort and where to economize forces. He then assigns missions; allocates forces, fires, and other supporting assets.
d. Control Key or Decisive Terrain. In some cases, portions of the brigade may be required to defend key or decisive terrain. Based on the commander's estimate, he may decide to defend these areas in either a sector or battle position.
e. Wear Down Enemy Forces. A well coordinated defense will destroy a large portion of the enemy forces and permit the commander to employ his maneuver forces to complete the destruction of enemy forces.
f. Retain Tactical Objectives. The brigade's mission to retain tactical objectives may be ordered if it assists or creates an opportunity for the higher headquarters to shift to the offensive. The brigade defense focuses on regaining the tactical initiative.
2. Advantages and Disadvantages of the Defender. The defender has several advantages and disadvantages when compared to the attacker.
a. Advantages. Advantages include:
-
A better knowledge of the terrain.
-
The ability to use and improve upon the terrain for protection and concealment.
-
A better opportunity to plan the fight.
-
The ability to employ obstacles as part of the overall defensive concept.
-
The ability to adjust preplanned fires in advance of the battle.
b. Disadvantages. Disadvantages include:
-
Exercising the initiative.
-
Normally having more maneuverability and freedom to exploit success.
CHARACTERISTICS OF DEFENSIVE OPERATIONS
In order to take advantage of a defensive posture, the commander must understand the four characteristics of the defense. The following paragraphs discuss the characteristics with respect to the battalion. A more detailed discussion can be found in FM 100-5.
1. Preparation. When the defender arrives in the battle area before the attacker, he takes advantage of the early arrival by making the most thorough preparations for combat that time allows. By analyzing the factors of mission, enemy, terrain, troops, and time available (METT-T), the CO gains an understanding of the tactical situation and identifies potential friendly and enemy weaknesses. He then war-games friendly and enemy options and synchronizes his concept of the operation with all available combat multipliers. Since the enemy decides the time and place of attack, all-round security is posted to provide early warning. The battalion's reconnaissance and security (R&S) operations must begin immediately upon transitioning to the defense and continue throughout the operation.
a. The Defender Owns The Terrain. The attacker must learn the terrain by seeing each compartment for the first time. The defender can prepare positions, construct obstacles, and conceal his efforts in advance. The attacker must commit assets to learn where the defender is located. The defender initiates the fight from hard-to-detect stationary positions that provide cover from enemy fire. The attacker must react to 'the defender by either firing while moving or by losing momentum as he seeks covered positions.
b. The Defender Must Be Flexible. The defender develops flexible plans to control fire, movement, communications, and logistics in all possible situations. The attacker must adhere to a planned scheme and risk destruction or, alter his plan and risk an uncoordinated effort.
c. The Defender Must Know The Enemy. The defender must know how the enemy units are organized and how they deploy in the attack. He also must know the capabilities and limitations of enemy weapons systems and equipment. The battalion S2 provides this information, but the commander must understand it. Thorough preparation begins with sound intelligence preparation of the battlefield (IPB).
d. The Defender Uses The Proper Assets. The defender organizes his defense around the weapons most effective against the principal threat. When facing an armored force, the defender's allocation and positioning of antiarmor weapons (TOW missile systems, Dragons, antitank mines, and tanks) is most important; other assets supplement their fires and minimize vulnerabilities. Against an infantry threat, infantry defeating weapons (machineguns, mortars, artillery, small arms) are integrated to reduce the momentum of the enemy's attack and to destroy the enemy forward of the defender's position. The effect of all weapons is greatly increased when they are positioned where cover and concealment reduce or neutralize enemy suppressive fires.
2. Disruption. Defensive plans vary with circumstances, but all defensive concepts of operation aim at disrupting the attacker's synchronization. Counterattacks, indirect fires, obstacles, and retention of key or decisive terrain disrupt enemy concentration of strength against portions of the defense. Destroying enemy command and control vehicles disrupts enemy flexibility and deception measures disrupt his attack. All of these efforts contribute to the disruption of the enemy's synchronization.
a. Operational Security (OPSEC). Units maintain OPSEC and avoid patterns to hide their dispositions. Enemy reconnaissance and probing attacks must be defeated without disclosing the scheme of defense to the enemy.
b. Disruption of Synchronization. An attacker's strength comes from speed, mass, and the mutual support of maneuver and combat support (CS) elements. The defender must disrupt the attacker's synchronization and destroy the mutual support between maneuver and CS elements. This makes it hard for the attacker to coordinate and concentrate forces and fires or to isolate and overwhelm the defender.
3. Concentration. The defender must concentrate combat power at decisive times and places if he is to succeed. He must be able to obtain a local advantage at points of decision. Offensive action and the use of surprise and deception are often means of gaining this advantage. Local counterattacks may be needed to maintain the integrity of the defense. Indirect fire can be shifted to critical points to rapidly concentrate destructive effects. When concentrating combat power, the defender must economize in some areas, retain a reserve, and maneuver to gain local superiority. Most importantly, the defender must remember that concentration refers to combat power--not just soldiers. Combat power focuses on effects--not just numbers of soldiers/weapons systems.
a. Concentrate Power. The commander concentrates weapons effects by designating the main effort. All weapons and assets support and sustain this main effort. By redesignating it, the commander can shift the focus of his combat power. To weight this main effort, the commander can--
-
Focus counterattack plans to support the main effort.
-
Reduce the size of the main effort's area of operations.
-
Assign the main effort priority for obstacle preparation.
-
Give the main effort priority of indirect fires.
-
Position the reserve near, in, or behind the main effort.
b. Integration of Assets. The commander integrates available assets so that their combined effect on the enemy exceeds the sum of their individual effects.
4. Flexibility. Flexibility is derived from sound preparation, disposition in depth, retention of reserves and effective command and control. The defender must be agile enough to avoid or absorb the attacker's blow and to strike back effectively. Flexibility results from a detailed estimate, an understanding of the unit's purpose, aggressive R&S and, when applicable, organization in depth and retention or reconstruction of a reserve. Flexibility requires that the commander "see the battlefield"--both physically and through timely and accurate reports. Supplementary positions on secondary avenues of approach provide more flexibility to the commander. After a good analysis of the terrain and enemy, reserves can be positioned to allow the commander to react to unexpected events. In short, sound contingency planning permits flexibility.
ALTERNATE DEFENSIVE PATTERNS
While defensive operations may take a wide variety of forms, traditional usage divides defensive arrangements into two broad categories. Mobile defenses focus on the destruction of the attacking force by permitting the enemy to advance into a position which exposes him to counterattack and envelopment by a mobile reserve. Area defenses focus on the retention of terrain by absorbing the enemy into an interlocked series of positions from which he can be destroyed largely by fire.
Although these descriptions convey the general pattern of each type of defense, both forms employ both static and dynamic elements. In mobile defenses, static defensive positions help control the depth and breadth of enemy penetrations, and ensure the retention of ground from which to launch counterattacks. In area defenses, mobile reserves cover gaps among defensive positions, reinforce those positions as necessary, and are available to counterattack key defensive positions should they be lost to the enemy.
Typically, defending commanders will combine both patterns, using static elements to delay, canalize, attrit, and ultimately halt the attacker, and dynamic elements--spoiling attacks and counterattacks--to strike and destroy his committed forces. The balance among these elements will depend on the unit's mission, composition, mobility, and relative combat power, and on character of the battlefield.
1. Mobile Defense. Mobile defenses employ a combination of offensive, defensive, and delaying action to defeat the enemy attack. Their design varies from case to case and must be described in detail in each instance. Commanders conducting a mobile defense deploy relatively small forces forward and use maneuver supported by fire and obstacles to wrest the initiative from the attacker after he has entered the defended area.
A force conducting a mobile defense must have mobility equal to or greater than the enemy's. It must also be able to form a large reserve which will conduct the decisive counterattack. Since doing so will almost invariably require thinning committed forces, a mobile defense cannot be conducted unless the temporary loss of some terrain is acceptable.
Because of the requirement to form a large reserve, mobile defense is normally conducted by division and larger formations. However, large brigades and cavalry regiments may be able to conduct this form of defense in some circumstances. In any case, heavy forces are required for the reserve, and may also be used as security forces to contain anticipated penetrations. Light forces in a mobile defense are usually used to defend strongpoints in suitable terrain within or adjacent to the area of the enemy's penetration, or in some cases, to stop the enemy during the counterattack.
2. Area Defense. An area defense is usually conducted to deny the enemy access to specific terrain for a specified time. Since, unlike the mobile defense, area defense does not promise outright destruction of the attacking force, area defense presumes some other simultaneous or subsequent operation to achieve decisive defeat of the enemy.
In an area defense, the bulk of the defending forces are deployed to retain ground, using a combination of defensive positions and small mobile reserves. Commanders organize the defense around the static framework provided by the defensive positions, seeking to destroy enemy forces by interlocking fires or by local counterattack of enemy units penetrating between defensive positions. Both light and heavy forces may conduct area defense. When the defending force is predominately light, such a defense is usually required.
Unlike mobile defense, for which considerable depth is essential, area defense may be conducted in varying depth, depending on the mission, forces available, and the nature of the terrain. When necessary, the commander may make his main effort well forward, committing most of his combat power to the FEBA and planning to counterattack early, when enemy forces are along the FEBA or even beyond it. While such a forward defense may often be necessary, it is more difficult to execute than a defense in greater depth. This is because its early commitment to decisive combat makes it less flexible, hence more dependent on rapid identification of, and concentration against, the enemy main effort.
When the mission is less restrictive, forces are available, and advantageous terrain extends deep into his defensive sector, the commander may organize his defense in greater depth. In extremely wide sectors, divisions and corps may need to defend in depth in order to gain time and to concentrate against the enemy.
When an area defense is conducted in depth, elements in the security area identify and control the enemy's main effort while holding off secondary thrusts. Counterattacks on the flank of the main attack then seal off, isolate, and destroy penetrating enemy forces. In the extreme, therefore, an area defense in depth begins to look like a mobile defense.
In organization and execution, both defensive patterns vary considerably from the pure form. Each can be visualized as extending across a portion of the defensive continuum. Each uses the five elements of the defensive framework and must be fought in the fluid, nonlinear conditions of contemporary combat. Tactical commanders must therefore adapt their defensive arrangements to the requirements of each situation and avoid becoming wedded to rigid patterns in the design of their defenses.
THE FRAMEWORK OF THE DEFENSE.
Battalions normally conduct defensive operations as part of a larger element. Both mobile and area defenses rely on static and maneuver elements. As a part of either of these elements, the battalion commander must use the overall defensive framework to synchronize the battalion's defensive effort.
1. Elements of the Divisional Defense. Divisions fight conventional defenses that are organized into five elements. These elements are complimentary, as shown in Figure 2-1. Three of these security operations, main battle area (MBA) operations, and reserve operations apply at all echelons. The five elements are as follows:
-
Deep Operations. These take place in the area forward of the front line of own troops (FLOT).
-
Security Operations. These actions are focused on the areas forward and to the flanks of the defending force.
-
Main Battle Area Operations. These actions concern the MBA.
-
Reserve Operations. Reserve operations are carried out in support of the main defensive effort.
-
Rear Operations. Rear operations are conducted to retain freedom of action in the rear area.
2. Deep Operations. Deep operations are actions against enemy forces not yet in contact with friendly forces. Deep operations prevent the enemy from massing and create, for the defender, opportunities for offensive action. To accomplish this, the defender separates the attacking echelons; disrupts the attacker's command and control, CS, and CSS; and slows the arrival time of successive echelons. Battalions may participate in deep operations IAW division or brigade plans.
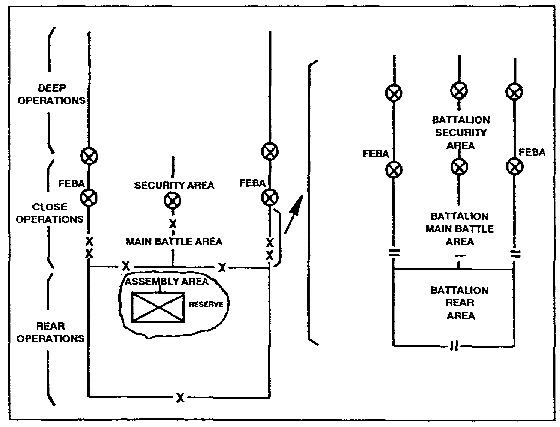
Figure 2-1. Framework of the Defense.
3. Close Operations. Close operations may include security area operations, battle handover, and MBA operations.
a. Brigade and Higher Security Area Operations. The forward security force established by corps or division is called a covering force. This covering force is tactically self-contained. It is organized with enough CS and CSS forces to operate independently from the main body. This force begins the fight against the attacker's leading echelons in the security area. The covering force gains and maintains contact, develops the situation, delays or defeats the enemy's lead forces, and deceives the enemy as to the location of the NBA.
b. Battalion Security Area Operations. The infantry battalion uses a screening force as its forward security echelon. The exact size of the screening force depends on the width of the sector, the nature of the terrain, and the specific tasks the security force is expected to accomplish. It is always tasked with providing early warning. The battalion security force is normally required to establish contact with the covering force, when a covering force is employed, and to aid with its rearward passage and battle handover (BHO). When there is no covering force, the battalion covering force might be required to move farther forward of the MBA to increase its early-warning ability.
c. Battle Handover. BHO provides an orderly transition between the security force battle and combat in the MBA. (See Figure 2-2.) The enemy should be unable to determine that this transition has occurred. The problems inherent in a battle handover arise from when, where, and how the covering force gives up responsibility for the fight to the MBA battalion. The battle handover line (BHL) and contact points on the ground must be coordinated and clearly identifiable to both forces. The headquarters that establishes the covering force designates the BHL and sets up the contact points to aid contact between MBA units and the covering force. MBA and covering force commanders coordinate and recommend BHL location changes to the higher commander. The BHL is shown on the operation overlay as a phase line. The BHL represents the location where control of the battle passes from the covering force to the MBA commander. The BHL is two to four kilometers forward of the FEBA, where MBA forces can use direct fire and observed indirect fire to aid the covering force in its final delay, disengagement, withdrawal, and passage of lines. The BHO takes place at the time or event coordinated between the commanders, or as directed by the senior commander.
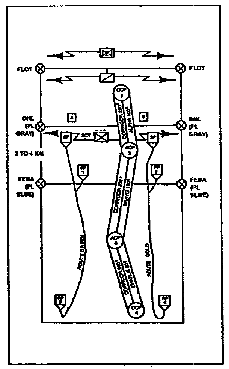
Figure 2-2. Battle Handover
d. Main Battle Area Operations. The brigade commander assigns MBA battalion-sized sectors, areas of operation, or battle positions, based on his estimate of the situation and intent. The brigade commander can strengthen the effort on the most dangerous avenue by narrowing the sector of the unit astride it, or by positioning more forces to cover that avenue. He might be required to use fewer forces in minimum-risk sectors. The battalion fights the decisive battle in the MBA. The commander positions forces in the MBA to control or repel enemy penetrations. He employs reserves to halt the attack, to destroy penetrating enemy formations, and to regain the initiative.
4. Reserve Operations. The primary purpose of the reserve is to retain flexibility. Secondary purposes include reinforcing success or regaining the initiative through counterattacks. The commitment of reserve forces at the decisive point and time may be the key to the success of a defense. The commander should decide the size, composition, and mission of the reserve, early in the planning stage, regardless of the defensive technique employed. The reserve is normally positioned near its most probable area of employment. All movement by the reserve to BPs, during counterattacks or reinforcement, occurs on routes that provide cover from direct fire, and concealment from ground or air observation. The reserve can also be tasked--
a. To Block. The reserve blocks penetrations until the enemy is destroyed or additional forces can be committed.
b. To Prepare Positions. The reserve may be used to prepare positions on less dangerous approaches.
c. To Reinforce. The reserve may reinforce a forward unit when casualties or heavy enemy pressure reduces its relative combat power.
d. To Counterattack. The reserve may counterattack to regain critical positions or terrain.
5. Rear Area Operations. Many command and control, CS, and CSS units are located in the rear area. Their importance, as well as their survivability, reduced mobility, and relatively small-caliber weapons make them prime targets for enemy attack.
However, a maneuver battalion can be assigned a rear area protection mission and can conduct offensive operations there against enemy conventional or unconventional forces.
COMBAT SUPPORT AND COMBAT SERVICE SUPPORT ASSETS
1. Maneuver. The task force commander arrays company or team-sized forces against battalion-sized avenues of approach. Against armored attacks, the defense is organized around weapons systems that can maneuver and destroy the enemy.
a. Scout Platoon. During the defense, the scout platoon's initial mission is to coordinate the BHO of covering force units and facilitate their orderly movement through the battalion defensive sector as battle positions. Concurrently with this mission, the scouts identify the main effort of the enemy moving into the task force sector. Subsequent missions include screening of flank avenues of approach and maintaining contact with adjacent units.
b. Antitank. Antitank units are employed in mass during defensive operations. Antitank units add depth to the defensive fight by being positioned to the rear of the defensive forces to cover and support by fire. The maneuver of forward company teams positioning should allow for engagement of the enemy from the flank and rear.
c. Attack Helicopters. When the brigade employs an attack helicopter battalion, it is usually to cover gaps, to attack by fire penetrations, to provide overwatch for counterattacking forces, or to attack enemy second echelon formations.
2. Intelligence. The brigade S2 must focus on IPB in planning for the defense and analyzing the close operation to predict and confirm enemy intentions. Before the battle, the battalion commander requires specific information about:
-
The composition, equipment, strengths, and weaknesses of the advancing enemy forces.
-
The location, direction, and speed of enemy reconnaissance and first echelon elements.
-
The location and activities of enemy second and follow-on echelons capable of reinforcing the first echelon.
-
Enemy first and second echelon S3 facilities.
A detailed reconnaissance, counterreconnaissance, and surveillance plan is prepared by the battalion's S2s and S3s to prevent the enemy from seeing and reporting the strength and composition of the battalion. During deep, close, and rear battles, the S2 continually updates the commander as to the enemy situation.
a. Ground Surveillance Radar (GSR). In the defense, GSRs are positioned forward to participate in the early identification of enemy units and to confirm enemy movement within named areas of interest (NAI) and target areas of interest (TAI). GSRs are most effective in these roles during limited visibility. Subsequent missions include observation of flank avenues of approach and vectoring of the reserve company/team in support of a night operation mission.
b. Other. Aviation or ground units performing reconnaissance or security missions forward of the task force also provide valuable intelligence.
3. Fire Support. The brigade commander weighs the main effort by establishing fire support priorities.
a. Field Artillery. Field artillery is positioned by brigade to support both the battalion close fight and brigade deep fight. Task force priority targets are planned on the most dangerous avenues of approach. They are then suballocated to units on those approaches and shifted as the battle develops. Priority of fires is initially to the forward security element during BHO; on order, it shifts to the unit designated the main effort.
Close, deep, and counterfires are synchronized with the maneuver forces to disrupt and weaken the enemy's offensive action. The fire support coordinator (FSCOORD) uses the IPB process, full integration of intelligence gathering resources, and the target value analysis process to focus fire support on the systems vital to the enemy's success. The FSCOORD focuses his planning effort on the following tasks:
-
Engaging the enemy early to disrupt the cohesion of his attack.
-
Supporting rear operations.
-
Providing deep fires to delay and disrupt following echelons.
-
Integrating fires with the battalion obstacle plan.
b. Mortars. The battalion mortars are initially deployed to support a secondary avenue of approach. Their alternate mission is to provide responsive smoke to support the maneuver of company teams between battle positions.
c. Air Support. Close air support (CAS) targets are preplanned to support the full depth of the battlefield and the transition to the offense.
4. Air Defense Artillery (ADA). ADA assets are initially positioned well forward to provide area coverage in support of the defensive preparations, the BHO operation, and initial enemy attack. Subsequent employment is area coverage throughout the battlefield with priority to counterattacking forces, choke points, river crossing sites, and other potential high-payoff enemy air targets.
5. Mobility, Countermobility, and Survivability.
a. Engineer. Priority of engineer support is normally to survivability, countermobility, then to mobility. The engineers assist initially in planning and emplacing obstacles to support its countermobility mission.
b. Nuclear, Biological, and Chemical. NBC operations in the defense concentrate on survivability. Smoke is employed in mobility and countermobility roles.
6. Combat Service Support. Logistics support to the combined arms team must be coordinated during the planning and execution phases of each defensive operation. The S4 must understand the commander's intent so that service support priorities can be established and logistics operations planned to ensure the supportability of the defense. All CSS activities must look beyond the defense to support opportunities to transition to the offense.
a. Combat Trains. The combat trains are as far to the rear as possible but close enough to respond to the maneuver units. Combat trains may be required to move frequently to support defensive operations. Operations of combat trains are organized to provide continuous support to, but not interfere with, maneuver elements.
b. Support Platoon. Before defensive operations, the support platoon brings forward barrier material. During defensive operations, the support platoon's priority of support is to Class III and V.
DEFENSIVE CAPABILITIES OF LIGHT AND MECHANIZED INFANTRY
1. Types. Infantry battalions are organized and equipped to perform various missions. Although each type battalion has a specific name, they are routinely divided into two major classifications. The terms "light" and "heavy" are commonly used to differentiate between non-mechanized and mechanized units. When the term "light" is used, the speaker may be referring to any or all of the following battalions (or divisions): light infantry, airborne infantry, air assault infantry, ranger infantry, or infantry. (Additionally, various special light units may be found, such as the mountain battalion or antiarmor battalions; however, they do not exist in great numbers.) The term "heavy" may include units equipped with the Bradley Fighting Vehicle (BFV) or the M113 Armored Personnel Carrier (APC).
2. Light Infantry. Although each type of light infantry may be capable of performing some peculiar mission (e.g., parachute insertion), they have much in common. Generally, light units are designed to fight under all weather and terrain conditions. They are especially adaptable to defending strongpoints, urban terrain, dense forests, and other areas not conducive to heavy vehicle traffic. Light units can be deployed by land or sea, and are by far more adaptable to air assault/air transport/airborne operations than mechanized forces. Light units are readily able to operate as small units, yet highly suitable for integration into special and heavy force operations. The major drawbacks of light units are their austere CS, CSS, and vehicle assets.
3. Heavy Infantry. Mechanized infantry units are organized to fight the enemy either pure or with cross-attached tank units. The mechanized infantry can fight mounted, dismounted, or both. A mechanized battalion fields 36 squad fighting vehicles (plus various scout and C&C vehicles) armed with 25mm (BFV) or caliber .50 machineguns (APC). Additionally, each BFV mounts the TOW missile and firing port weapons. Obviously, heavy forces are capable of producing far greater firepower and have much more armor/vehicle killing ability than light forces. Mechanized infantry is capable of maneuvering with tanks, swimming streams, and in some cases, maneuvering on terrain not trafficable by tanks. Fighting vehicles are capable of negotiating some obstacles and withstanding some small arms fire and fragmentation, which would destroy dismounted formations. The limitations of mechanized forces include their restriction to passable terrain, tremendous ammunition and POL requirements, and transportation required for overseas/intertheater movement.
OPERATIONAL SECURITY MEASURES FOR THE DEFENSE
1. Definition. FM 101-5-1 defines Operational Security (OPSEC) as: "All measures taken to maintain security and achieve tactical surprise. It includes countersurveillance, signal security, physical security, and information security. It also involves the identification and elimination or control of indicators which can be exploited by hostile intelligence organizations." Security measures can be classified as active and passive. Normally, limited visibility conditions warrant increased emphasis on security.
a. Active Security. Active security measures include OPs, stand-tos and patrols. The required number of OPs may vary according to METT-T or the alert status of the unit. Stand-tos include all members of the unit and are used to ensure that each man is dressed, equipped, alert, and ready for action. Constant 100% alert is not practical; therefore, the number of soldiers on alert should be situation dependent and influenced by the need for rest and other mission requirements. In no case, however, will security be sacrificed for rest.
b. Passive Security. Passive security measures include camouflage, movement control, light and noise discipline, proper radiotelephone procedures, and the use of ground sensors. Remotely employed sensors (REMS) can be used to give warning of enemy movement. Antiarmor weapon (TOW and Dragon) sights can be used to enhance the security effort, both day and night.
c. Limited Visibility. Limited visibility security requires increased security measures to ensure that the unit is not surprised by the enemy. This can be accomplished by--
Increasing OPs and patrols.
Occupying supplementary positions, if they allow better coverage during limited visibility.
-
Employing trip flares and other early warning devices.
-
Employing thermal sights and night vision devices (NVD).
-
Employing platoon early warning devices.
-
Adjusting fire control measures.
-
Increasing the number of troops on alert in each position.
-
Maintaining light and noise discipline.
-
Limiting movement and postponing all unnecessary activities.
At night the CO may employ various means of illumination to expose an attacking force. Open flanks should also be considered for illumination. However, all illumination should be coordinated with adjacent units and approved by brigade. The CO must ensure that illumination is not triggered prematurely by probes or other minor activities. When illumination is determined necessary, it is used and the battalion defends as in daylight.
2. Counterreconnaissance. Counterreconnaissance activities entail denying enemy reconnaissance elements accurate information through destruction of enemy recon or through deception. It is seldom possible to deny all information to the enemy. Based on expected enemy reconnaissance action, the CO decides what information and locations he must protect. He also considers what information would make the enemy act the way he wants him to (such as, to deploy prematurely, deploy too late, attack a false objective, or move into a kill zone). Once priorities are established for the counterreconnaissance effort, the CO focuses his efforts toward denying information to the enemy. The battalion's counterreconnaissance plan is integrated into the concept of the operation and coordinated with the brigade's plan. At times, the battalion may be the counterreconnaissance force for the brigade. For more details, see FM 7-20. The concept for the defense must address the counterreconnaissance battle. If the brigade order does not provide sufficient detail, the battalion commander must decide how to defeat the enemy's reconnaissance effort. There are two general approaches to this task.
a. Destruction of Forces. The first approach is to identify and destroy all reconnaissance assets before they reach the company's MBA. To fight the counterreconnaissance battle in this manner requires
-
Unity of command. All assets/units involved in this effort must be controlled by one leader.
-
A well planned concept. It must include clear taskings, effective task organizations, detailed fire planning, engineer support, and detailed CSS planning.
-
A mix of finders and fighters. Certain units are tasked to locate enemy reconnaissance assets. Once located, they report/call for fires. Other units are responsible for destroying these enemy units. Both groups must be mobile enough to cover the battalions area of responsibility.
-
A withdrawal plan which provides for rapid rearward passage of counterreconnaissance forces and must be coordinated with all units involved.
b. Deception. The second option is to allow the reconnaissance element to move through the area in order to achieve surprise on the enemy main body. This option requires brigade's consent and the maximum use of camouflage and concealment. This technique may be varied as required, so long as the enemy is denied an understanding of the defensive scheme.
3. Physical Security for the Force. The infantry battalion may employ its own security forces, serve as the security force for a larger unit, or serve as a part of a larger security force. The operations conducted to secure the main force include: screening, guard, covering, and area security.
a. Screening Force. This force maintains surveillance, provides early warning, impedes and harasses the enemy with supporting indirect fires, and destroys enemy reconnaissance within its capability. The battalion may serve as a screening force or may employ its on screening forces, as required.
b. Guard Force. A guard force accomplishes all the tasks of a screening force. Additionally, this force prevents enemy ground observation of and direct fire against the main body. A guard force reconnoiters, attacks, defends, and delays as necessary to accomplish its mission. A guard force normally operates within the range of main body indirect fire weapons. The battalion may serve as a guard force or part of a larger guard force.
c. Covering Force. A covering force accomplishes all the tasks of screening and guard forces. Additionally, a covering force operates apart from the main body to develop the situation early and deceives, disorganizes, and destroys enemy forces. Unlike screening and guard forces, a covering force is a tactically self-contained force; having sufficient CS and CSS assets to operate independent of the main body. The battalion may operate as part of a brigade or larger covering force, but is incapable of performing such a mission alone.
d. Area Security Force. Area security operations are normally associated with rear battle operations. The requirements for this force are delineated by the HQ assigning the mission.
4. Signal Security (SIGSEC). SIGSEC includes measures intended to deny or counter hostile exploitations of electronic emissions. It includes communications security (COMSEC) and electronic security (ELSEC).
5. Information Security. Information security includes those measures necessary to ensure that access to classified information is restricted to authorized personnel.
GO TO:

