|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
Lesson 1
CONSIDERATIONS FOR OFFENSIVE OPERATIONS
OVERVIEW
Lesson Description:
In this lesson you will identify the fundamentals of offensive operation. These doctrinal foundations apply to both light and mechanized forces from company to brigade size. Subject areas include: types, characteristics and phases of offensive operations; the purposes and sequence of tacks; and the various forms of maneuver employed by infantry units.
Terminal Learning Objective:
| Action: | Identify the fundamentals of offensive operations. |
| Condition: | Given the subcourse material contained in this lesson. |
| Standard: | You must correctly answer 70 percent or higher of the questions on a multiple-choice test covering the lesson material. |
| Reference: | The material contained in this lesson was derived from the following publications: |
| FM 7-7 FM 7-10 FM 7-20 FM 71-1 |
FM 71-2 FM 71-3 FM 100-5 FM 101-5-1 |
INTRODUCTION
The object of battle is to win. To win, one must attack. The attacker must identify the decisive point in the enemy's defense, choose a from of maneuver which avoids the enemies strength, and concentrate the effects of his combat power against the decisive point.
CHARACTERISTICS OF THE OFFENSE
Successful offensive operations, whatever their purpose, are characterized by surprise, concentration, speed, flexibility, and audacity.
NOTE: The terms battalion and task force may be used interchangeably throughout this lesson.
1. Surprise. Surprise is achieved by striking the enemy at a time or place or in a manner for which he is unprepared. The enemy may learn of the attack--but he must do so too late to react effectively.
a. Shock. The shock of an unexpected attack slows enemy reactions, overloads his command and control system, and reduces the effectiveness of his weapons. This allows the attacker to quickly overcome the defender.
b. Initiative. Initiative is the setting or changing the terms of battle by action. The attacker's initiative allows him to choose the time, place, and means of battle. Surprise is enhanced by striking the enemy's flank or rear, by infiltrating, or by rapidly and unexpectedly inserting combat forces to the enemy's rear.
c. Exploit. The shock of surprise is brief, so the attacker must exploit it and deny the enemy time to regain his equilibrium.
2. Concentration. Concentration of the unit's combat power on the enemy at the point of attack is required.
a. Protection. The lethality of modern weapons--especially artillery and NBC weapons--increases the threat to massed formations. The attacker must avoid patterns or obvious movements that reveal the time or direction of its attack. Tactical mobility, security, deception, and proper use of terrain and weather are vital to success. Other ways to concentrate the effects of the battalion's weapons on the enemy include the following:
(1) Designate Main Effort. Designate the main effort, focus the resources to support it, and prepare to shift it rapidly.
(2) Synchronize. Synchronization is the arrangement of battlefield activities in time, space, and purpose to produce maximum relative combat power at the decision point. Further discussion can be found in FM 7-20. Synchronize direct fires, indirect fires, and combat air support (CAS). Weight the main effort with indirect fire assets, aviation, or CAS, which can be shifted rapidly as the situation changes.
(3) Integrate. Integrate combat support (CS) and combat service support (CSS) assets. Organize and coordinate support in detail to give the unit the sustainment required for success.
b. Reconnaissance and Surveillance(R&S). R&S are important to allow the attacker to focus the combat power of his weapons on the weakness of the enemy. R&S can be friendly or enemy oriented. See FM 7-20 for greater detail.
3. Speed. Speed is vital to infantry offensive operations. Speed can prevent the enemy from using effective countermeasures. Speed and surprise together compensate for a lack of mass; they deny the enemy the time to recover or to identify the main effort and react effectively.
a. Speed Versus Haste. Speed must not be confused with haste. General Patton, who stressed the use of time in all his operations, carefully distinguished haste from speed.
"Haste exists," he wrote, "when troops are committed without proper reconnaissance, without the arrangement for proper supporting fire, and before every available man has been brought up. The result of such an attack will be to get the troops into action early, but to complete the action very slowly.
"Speed is acquired by making the necessary reconnaissance, providing proper artillery and other tactical support, including air support, bringing up every man, and then launching the attack with a plan so that time under fire will be reduced to a minimum. At battalion level, four hours spent in preparation for an attack will probably ensure the time spent under fire will not exceed thirty minutes. One hour spent in...preparation...will most certainly ensure time under fire lasting many hours with bloody casualties."
b. Speed Can Be Attained In Many Ways.
(1) Training, C2, and Mission Orders. Training and an effective command and control that translates mental agility into decisive, quick action are needed. Mission-type orders at all echelons allow subordinates to use enemy weaknesses created by the rapid-tempo attack.
(2) Mobility, Planning, and Intelligence. Tactical mobility is enhanced by the use of movement techniques, formations, and drills that allow the force to move and react rapidly and use the terrain. Proper planning for the use of engineer, air defense, and aviation assets increases tactical mobility. Good reconnaissance and intelligence collection are vital.
(3) Logistics. Responsive logistical support results in rapid resupply. This ensures the attack can continue.
4. Flexibility. Flexibility is a trait required of commanders. Combat requires that they expect uncertainties. To develop flexibility, detailed war-gaming is critical. War-gaming is detailed in FM 7-20. The following also increase unit flexibility.
a. Intelligence Preparation of the Battlefield (IPB). IPB is conducted to learn the terrain and enemy dispositions for initial and subsequent actions. FM 7-20 explains IPB in detail.
b. Reconnaissance. Conducting continuous reconnaissance to discover enemy weaknesses and ways to attack him on the flank and rear.
c. Reserve. Maintaining a reserve that can assume the mission of the main attack or exploit tactical opportunities.
d. Command and Control. Establishing a command and control (C2) system that allows the commander to make and transmit timely decisions.
e. Intent. Communicating the commander's intent by mission type orders and fragmentary orders (FRAGO).
5. Audacity. Audacity is the willingness to risk bold action to achieve positive results. The audacious commander is daring, confident, and original--he is not rash.
a. Reasoned Approach. The audacious commander's actions, though quick and decisive, are based on a reasoned approach to the tactical problem and his knowledge of soldiers, terrain, and enemy. This commander maneuvers to maintain a positional advantage over the enemy. He seeks to attack the enemy on the flank or rear, and exploits success at once, even if this briefly exposes his flanks. He issues mission-type orders and moves to the place on the battlefield where he can best influence the critical aspects of the attack.
b. "Indirect Approach". Boldness and willingness to accept calculated risk have always been the keystones of successful offensive action. The concept of combat power is more than the sum of a force's combat system. Audacious commanders throughout history have used the "indirect approach." To defeat a numerically superior opponent, they strike at an unexpected time and place.
TYPES OF OFFENSIVE OPERATIONS
The five types of major offensive operations are:
- Movement to contact.
- Hasty attack.
- Deliberate attack.
- Exploitation.
- Pursuit.
1. Movement to Contact. A movement to contact is an offensive operation conducted to gain or reestablish contact with the enemy. Its purpose is also to develop the tactical situation. To maintain flexibility and security when moving to contact, the battalion makes contact with the smallest element possible. This is most important to infantry battalions due to their limited mobility and dependence on restricted terrain. Two of the techniques used most commonly by infantry battalions to conduct a movement to contact are the approach march technique and the search-and-attack technique.
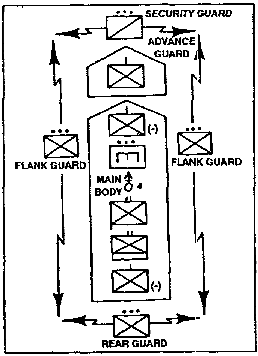
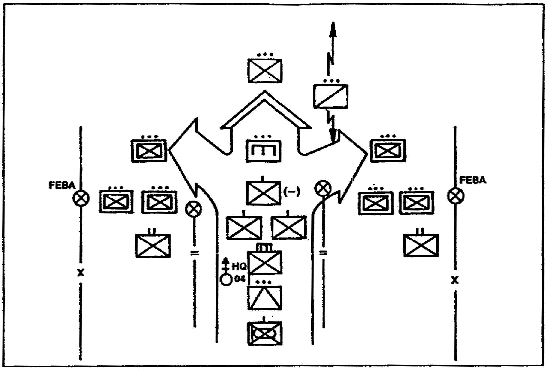
a. Approach March Technique. The approach march is an advance of a combat unit when direct contact with the enemy is imminent. Troops are fully or partially deployed. The approach march ends when ground contact with the enemy is made or when an attack position is occupied. The approach march technique is the "conventional" technique for conducting movement to contact. Using this technique, battalions usually organize into a security force, advance guard, main body, flank guard, and a rear guard (See Figure 1-1). These guarding elements move with and secure the main body.
(1) Planning Considerations. The unit should be assigned an axis of advance or a zone. A march objective is assigned to orient movement. The commander selects routes for the approach march based on IPB, which provide cover and concealment but allow for contact with the enemy. Guard forces are used for all-around security. A detailed discussion is provided in FM 7-20.
Figure 1-1. Single Battalion in March Column.
(2) Organization. The battalion organizes into a security force, advance guard, main body, flank guards, and rear guards when it is conducting movement to contact alone. Units should be close enough together so that units can rapidly come to the aid of the unit ahead. However, they should be far enough apart that enemy fire falling on the leading unit does not limit the trailing unit's ability to maneuver. Support assets are used in the same manner as with search-and-attack, with a some exceptions. A detailed discussion of the employment of maneuver, CS, and CSS assets is outlined in FM 7-20.
- Security Forces. The battalion can employ more reconnaissance and security (R&S) forces to the front and flanks during an approach march. Depending on METT-T, security forces operate two to six kilometers forward of the battalion advance guard. Once they find the enemy, the security force should remain oriented on him. The primary responsibility for finding the enemy is normally given to the scout platoon. A discussion of the scout platoon's role in the security force can be found in FM 7-20.
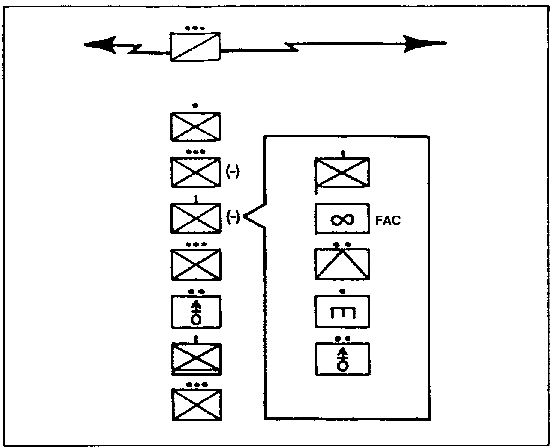
- Advance Guard. The advance guard operates one to two kilometers ahead of the main body. It attempts to develop the enemy situation, provide for the uninterrupted advance of the main body, protect the main body from surprise, and cover the deployment of the main body if it is committed to action (See Figure 1-2). Additional details concerning the duties and actions of the advance guard can be found in FM 7-20.
Figure 1-2. Organization of an Advance Guard
- Flank and Rear Guards. Flank and rear guards are designated when enemy contact on an approach march is possible. Their detailed functions and responsibilities are explained in FM 7-20.
- Main Body. The main body comprises most of the battalion force when the battalion moves to contact. The main body maintains local security while attempting to balance conservation of the unit's fighting strength with the need for march discipline and security. More detail can be found in FM 7-20.
b. Conduct of the Approach March. The battalion should follow several guidelines during movement.
(1) Contact. The battalion makes contact with the smallest force possible.
(2) Movement Technique. The commander selects the movement technique based on the likelihood of enemy contact and the speed of movement desired.
(3) Columns. The commander visualizes how his force will be deployed when contact is made and moves it accordingly.
- Single Column. A single column is used for ease of control or when the terrain permits movement on one axis only.
- Multiple Columns. Multiple columns allow greater security to the flank, are more rapidly deployed, and allow mutual support.
(4) Other Factors. Other factors must also be considered, even though a single column is easier to control than multiple columns. A strongly reinforced battalion may be forced to move in multiple columns, the enemy situation may require movement in a particular configuration, a wide zone may favor multiple columns, while the availability of routes may also dictate the movement technique selected.
c. Search and Attack. This decentralized movement-to-contact technique requires multiple, coordinated patrols (battalions use squad-sized and platoon-sized) to locate the enemy. It is most often used in low intensity conflict against an enemy operating in dispersed elements. When conducting a search and attack, units can expect to spend more time operating in an area of operations rather than just "sweeping" through it. Search and attack can be conducted for many reasons. (FMs 7-10 and 7-20 provide more information on search and attack.)
(1) Purposes. The commander's concept focuses the battalion on one or more of the following:
- Destruction of the enemy.
- Area denial.
- Force protection.
- Information collection.
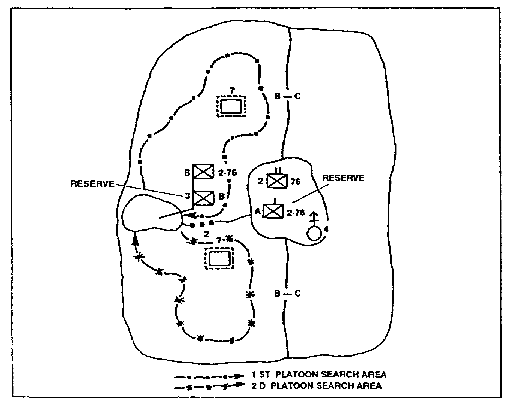
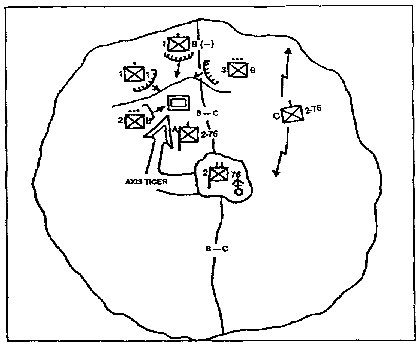
(2) Tasks. Search and attack operations can be conducted in a company-sized or battalion-sized area of operations (See Figures 1-3 and 1-4). The unit can be tasked--
- To locate enemy positions or routes.
- To fix, block, or destroy enemy forces within its capability.
- To maintain surveillance of a larger force until reinforcements arrive.
Figure 1-3. Dispersing to Search.
Figure 1-4. Massing to Attack.
- To establish ambushes.
- To search towns or villages.
- To secure military or civilian property or installations.
- To act as a reserve.
(3) Concept Development. The commander must consider the following actions when developing his concept.
- Finding the Enemy. Much time may be required to establish the pattern of enemy operations. However, the commander will be effective only once these patterns have been identified. Techniques are discussed in detail in FM 7-20.
- Fixing the Enemy. The unit will conduct one of the following actions after developing the situation, based on the commander's guidance and on METT-T factors:
- Prepare to block enemy escape/reinforcement routes for another unit's attack.
- Conduct a hasty attack.
- Maintain surveillance.
- Remain undetected and follow the enemy.
- Finishing the Enemy. Battalions destroy enemy forces during a search and attack by doing the following.
- Conducting hasty or deliberate attacks.
- Blocking for other unit attacks.
- Conducting R&S activities.
- Employing indirect fire/CAS.
- Conducting ambushes.
(4) Execution. The commander must accomplish the following to ensure successful synchronized and decentralized operations.
- Specify where each unit will operate, establish unit consolidation measures before attacks, and establish fire control measures for each unit.
- Concentrate combat power so that it can be rapidly applied once the enemy is located.
- Provide control, but allow for decentralized actions and small-unit initiative.
- Ensure CS assets support the main effort while remaining responsive to the rest of the battalion.
(5) Employment of Support Assets. Synchronization of CS and CSS assets in search and attack operations is harder to achieve than in most other type operations. Distances between units, the terrain, and a vague enemy situation contribute to this difficulty. A detailed discussion of the employment of support assets can be found in FM 7-20.
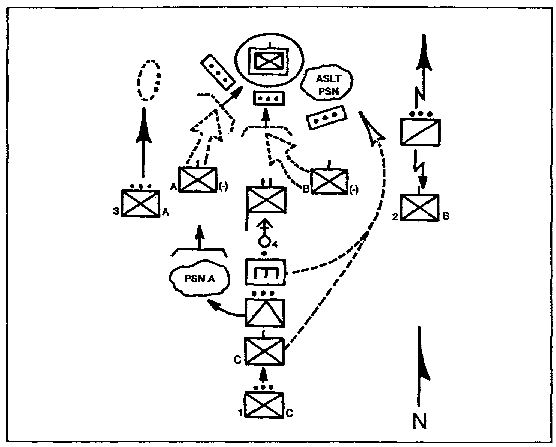
d. Actions on Contact. Commanders at all levels must know their higher commander's intent and concept for actions for contact so that no time is lost waiting for orders (See Figure 1-5). These engagements will often occur in small unit operations and situations where reconnaissance has been ineffective. One of the most important aspects of actions on contact is to fight through at the lowest level possible.
Figure 1-5. Actions on Contact.
(1) Aggressive Action. Movements to contact are characterized at all echelons by aggressive offensive action. The advance guard pushes back or destroys small enemy groups before they can hinder the advance of the main body. When the advance guard encounters large enemy forces or heavily defended areas, it acts promptly to develop the situation and, within its capability, destroys the enemy.
(2) Bypassing Forces. Light enemy resistance should not slow the advance; the battalion must remain mission-oriented. If the enemy is weak and a bypass is authorized, the battalion should use a covered route to suppress and obscure him while bypassing. Commanders must report all bypassed forces to higher headquarters.
(3) Unsuccessful Encounters. The battalion can withdraw to a more favorable position and maintain contact through patrols if its encounter has been unsuccessful and it is in a bad position in close contact with the enemy. If the enemy can be induced to follow up the withdrawal, the battalion might have an opportunity for another offensive move.
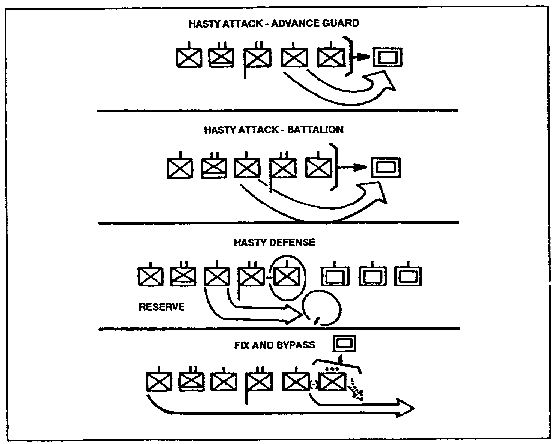
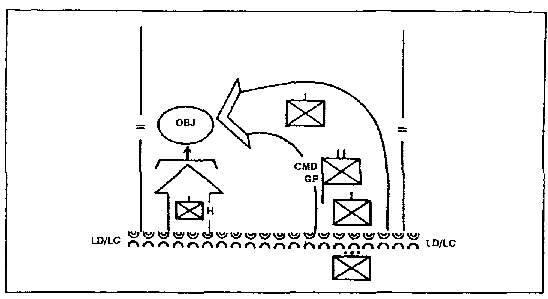
2. Hasty Attack. A hasty attack is one in which preparation time is traded for speed to exploit an opportunity. The commander can conduct a hasty attack to destroy the enemy after a movement to contact (See Figure 1-6). He can conduct a hasty attack to maintain momentum following the seizure of an objective; or, he can conduct a hasty attack to gain or maintain the initiative following a successful defense against an enemy attack.
a. Unprepared Defenders. When the defender is unprepared, hasty attacks may be appropriate--especially when fortifications are poorly constructed/nonexistent, his defenses are shallow, or gaps exist between his units.
b. Control. Tactical units use SOPs and battle drills to switch rapidly to a hasty attack. The scheme of maneuver must be simple and the form of maneuver appropriate to the conditions.
c. Engagement. Forces in contact deploy and engage the enemy. They report the size and composition of the enemy force, the location of enemy flanks, and the routes around and through enemy positions. To support the scheme of maneuver and to synchronize supporting assets, commanders issue FRAGOs to all units.
d. Technique. The enemy is fixed in position and isolated from reinforcements. Overwatch units suppress his positions with direct and indirect fire. If the enemy is stationary, he is destroyed in position. If he is mobile, an engagement area is established. If he withdraws, he can be pursued by fire or maneuver.
Figure 1-6. Example of a Hasty Attack.
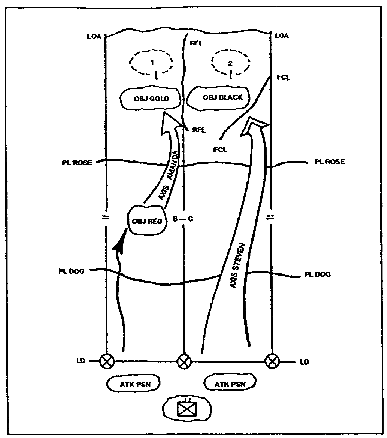
3. Deliberate Attack. The battalion conducts deliberate attacks when detailed planning is required to eliminate enemy forces in pinpointed, prepared positions. Attacks against strongpoints are elaborated in FM 7-20.
a. Planning Considerations. The object is to concentrate strength against the enemy's weakness to shatter his defense.
(1) Intelligence. Detailed information about the enemy and terrain is collected through all available sources.
(2) Breaching the Defense. The attacker may press forward with committed forces toward the center of gravity of the defensive force, or he may turn left or right to attack the flanks of enemy positions.
(3) Press the Attack. The attacker's freedom of maneuver is limited if the enemy has time to develop a well-prepared defense. When an attacking subordinate unit is reaching its culminating point, fresh units should be committed to continue the attack through to the decisive point.
b. Preparation for the Deliberate Attack. Much of the power of a deliberate attack is derived from planning initial actions of all elements, in detail. The preparatory phase includes all preliminary actions such as resupply and movement to assembly areas. Intelligence activity intensifies. Soldiers move to/through attack positions in preparation for crossing the line of departure (LD).
c. Execution. The attack begins when the unit crosses the LD. Unless the unit is ahead of schedule or other adjustments are required before the attack, units do not stop in the attack position. The commander should update his subordinate commanders before they deploy (See Figure 1-7).
Figure 1-7. Example of Deliberate Attack.
(1) Line of Departure/Line of Contact (LC). The LD/LC is the line where contact can be expected. Therefore, the unit should use overwatch techniques.
(2) Advances and Assaults. The entire attack is characterized by a series of rapid advances and assaults, which the battalion supports by fire.
(3) Momentum. The momentum of the attack must be maintained. Obstacles should be bypassed (when possible) and radio silence is used until the attack is discovered. Movement and assault plans must be simple so they can be controlled without radios. Assault elements continue without stopping on intermediate objectives. The force closes on the objective with all of its combat power. Bypassed units are reported to higher headquarters.
(4) Support Elements. CSS elements trail maneuver units by enough distance to avoid interfering with maneuver or coming under direct fire.
d. Actions on Contact. Assault units move out of, or around, indirect fires encountered en route to the objective. Incoming direct fire is returned immediately.
e. Actions in the Assault Position. The battalion assumes the prescribed assault formation as it moves through the assault position. As the battalion shifts artillery fires from the objective to other targets, the assault element prepares to move rapidly onto the objective. Suppressive fires must not be allowed to lapse, as they isolate the objective. If the battalion must halt in the assault position, and the enemy knows of the attack, the battalion deploys in covered positions, screens with smoke, and places all available suppressive fire on the objective.
f. Final Assault. The assault begins as units leave the assault position. Assault elements use fire and movement to close rapidly on the objective, before the defense can react. Direct fire weapons support from overwatch positions.
g. Reserves. Reserves remain near maneuver of the main effort--without interfering. Reserves can be used to shift the main effort or reinforce success by continuing the attack once the main effort has reached its culmination.
h. Consolidation and Reorganization. Seized and/or cleared objectives are reported. Consolidation is rapidly completed in order to reduce vulnerability of the unit. Normally, enemy defensive positions are unsuitable for occupation due to their orientation; therefore, the battalion may continue the attack or fight through and beyond the objective to a position that offers dispersal.
4. Exploitation. Exploitation follows a successful attack. Its purpose is to prevent the enemy from rebuilding his defenses. A bold exploitation should follow every attack unless the unit is restricted by higher headquarters or lack of resources. Due to combat power, logistics, and intelligence limitations battalions normally take part in exploitations as part of a larger force.
a. Battalion Tasks. Battalions attack and disrupts enemy activities in rear areas. It also performs missions which cut off enemy withdrawal routes.
b. Speed is Vital. The battalion moves as if it were moving to contact, launching hasty attacks to destroy enemy targets. It clears only enough of: zone allow advancement. Enemy units that do not jeopardize advancement are bypass and reported, or contained with the smallest unit possible. Minimum control measures are used, following maximum latitude to subordinate commanders.
c. Composition. Exploiting battalions are normally armor reinforced, forming task forces. Other CS and CSS elements may also be attached. Aviation/tactical air may be used for reconnaissance and fire support.
5. Pursuit. Pursuit is an operation designed to annihilate a retreating enemy force. It orients on force rather than on terrain objectives. A pursuit should follow any successful breach and exploitation of the enemy's defensive sector.
a. Constant Press. A pursuit must be rapid, but not reckless. The battalion can obtain decisive results only by destroying the enemy main body. A sound pursuit exerts constant, unyielding pressure on the enemy. Soldiers are pushed to their limits and reserves are committed freely in order to maintain momentum. The battalion continues to pursue day and night. Stop, for any reason, allow the enemy to gain time, during which h may pull units together, employ obstacles, or even slip away. Pursuing forces must prevent the enemy from breaking contact or reconstituting his defense.
b. Night. Pursuit often begins or continues into the fight, because the enemy will most likely try to conceal is withdraw by moving after dark.
c. Techniques. Pursuit can be conducted by direct pressure or by encirclement. The direct pressure for must have sufficient combat power to maintain pressure on the enemy. The encircling force must have good firepower and greater mobility than the enemy. An ideal encircling force consists of air assault forces and attack helicopters or tactical air support.
d. Requires Effort. The pursuit requires commanders and leaders to expend great effort. They must use their energy and willpower, act with initiative, and have flexibility of maneuver.
(1) Energy and Willpower. Constant combat causes units to tire and tend to become disorganized. As a result, soldiers may relax mentally. Unit leaders, at all levels, must lead, initiate, exploit opportunities.
(2) Activity and Initiative. Before the strength of the pursuers fades, commanders must use their initiative to find ways to conserve strength and increase speed and mobility.
(3) Flexibility of Maneuver. Fluid situations require mission-type orders in order to allow subordinate commanders to accomplish their missions. Control measures should be limited where practical, with phase lines incorporated for control.
e. Decentralized Command. To simplify C2, command posts (CP) closely follow lead units and battalion commanders operate forward. Vehicles are used when possible. Moving by leaps and bounds, CPs coordinate all supporting activities according to radio instructions from command groups.
f. Security. Pursuit requires only those security measures that add mobility and speed. The thoroughness normally associated with security is relaxed enough to facilitate rapid movement. Units may be dispersed to prevent ambushes and to prevent the enemy knowing the size of the unit. In all cases, the commander must ensure the withdrawal is not a ruse.
g. Rapid Advance. A pursuit must be rapid. Speed often depends on engineer support, which advances with lead elements.
h. Air Assets. Air assault assets are able to strike key elements deep in the enemy rear. Attack helicopters and CAS engage targets which contribute most to the pursuit. These actions continue until direct pressure forces arrive.
i. Logistics. Aviation assets assist in the pursuit by backhauling casualties and resupplying lead elements. Inoperative vehicles are left behind for recovery by follow-on forces. Rapid movement requires close coordination between the S3 and S4.
THE FIVE FORMS OF MANEUVER
The five forms of maneuver describe the relationships of attacking units to each other and to the enemy. The form(s) of maneuver selected must support the intent of the commander. Infiltration, penetration, envelopment, turning movement, and frontal attack are the five forms of maneuver. Additional detail can be found in FM 7-20.
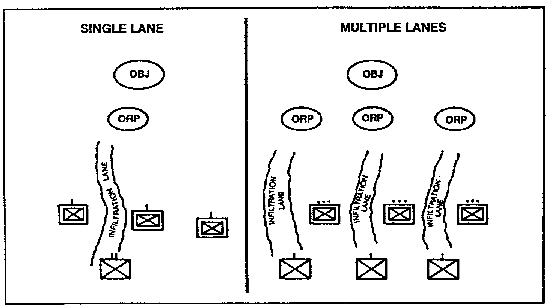
1. Infiltration. The purpose of infiltration is to move by stealth to place a maneuver force in a more favorable position to accomplish a mission. Infiltration is used to avoid detection and engagement (See Figure 1-8). Infiltrating units can seize key terrain, destroy critical communications nodes, and interfere with the resupply and reinforcement of enemy positions.
Figure 1-8. Examples of Infiltration.
a. Types of Infiltration. Three types of infiltration may be used.
(1) Land. Infiltration by foot is most common and is discussed in detail in FM 7-20.
(2) Water. Infiltration by water is described in FM 31-25 and FM 31-11.
(3) Air. FMs 90-4, 100-27, 90-26, and 31-24 provide information for infiltration by air.
b. Advantages. Infiltration can be used when enemy firepower discourages the use of other forms of maneuver. Infiltration can panic and disorganize forces prepared to fight to their front.
c. Disadvantages. Overland infiltration requires a great deal of time, excellent small unit navigation skills, and successful link-up. Forces may be caught and destroyed piecemeal, if the enemy can concentrate combat power.
d. Conditions. The ability to conceal movement enables the commander to achieve surprise. Rough terrain, darkness, and bad weather increase chances for success. Aggressive reconnaissance and routes through areas not covered by surveillance and/or fire will also increase chances for success.
e. Training. Soldiers must be trained in patrolling and light/noise discipline techniques. Elements should have an offensive frame of mind, but ready to break contact, if necessary. Only the required equipment and supplies are carried.
f. Phases. Overland infiltration can be accomplished in five phases.
(1) Patrol. Gaps are identified for use by infiltrating units.
(2) Prepare. Conduct troop-leading procedures.
(3) Infiltrate. The unit infiltrates the gaps.
(4) Consolidate. The unit reassembles at one or more objective rally points (ORP) and prepares to complete the mission.
(5) Execute. The unit completes its mission.
g. Lane Selection. FM 7-20 describes lane selection in detail.
h. Other Control Measures.
- Avoid roads, trails, or other obvious routes of movement.
- Thermal imagery helps in avoiding detection.
- Easily identifiable rally points are a must.
- Reconnoiter and secure the ORP(s) before occupation.
2. Penetration. Penetration is conducted at the enemy's weakest point to rupture his defense (See Figure 1-9). If the METT-T analysis identifies multiple weaknesses in the enemy's position, then multiple penetrations are considered.
Figure 1-9. Battalion Task Force Conducting Penetration.
3. Envelopment. The basic form of maneuver is envelopment. An enveloping unit seeks to apply friendly strengths against enemy weakness by striking the enemy in the flank or rear (See Figure 1-10). The enemy must be forced to fight along undefended or lightly defended avenues of approach. An envelopment can also interdict the enemy's lines of communication, which reduces his ability to fight.
4. Turning Movement. The attacking force making the turning movement passes around the enemy, avoiding him entirely, to secure an objective deep in the enemy's rear area. This maneuver forces the enemy to abandon his position or divert major forces to meet the threat (See Figure 1-11). The selected objective must be along the enemy's lines of communication (LOC). The objective must be important enough to the enemy to cause him to abandon his forward defenses--for example, a key bridge over an unfordable river.
5. Frontal Attack. The least desirable form of maneuver is the frontal attack. The most direct routes are used to strike the enemy all along his front. When possible, companies should try to seize their objectives from a direction other than the front.
Figure 1-10. Battalion Conducting an Envelopment.
THE FOUR PHASES OF OFFENSIVE OPERATIONS
All offensive operations tend to occur in four phases, although the length and nature of each phase varies. The general phases are preparation, attack, exploitation, and pursuit.
1. Preparation. Troop-leading procedures serve as the basis for planning offensive action. Included are planning and issuing orders, preparing personnel and equipment, conducting reconnaissance, and rehearsing.
2. Attack. The attack phase may include either a hasty or deliberate attack. Most attacks consist of an approach to the objective, the assault or actions on the objective, and the reorganization/consolidation.
3. Exploitation. A battalion normally takes part in exploitations as part of a larger force; however the battalion should exploit success at the local level within the higher commanders' concept of the operation.
4. Pursuit. The objective of the pursuit phase of an operation is the total destruction of the enemy force. The battalion may take part in a pursuit as part of a larger force.
Figure 1-11. Battalion Conducting a Turning Movement.
MAIN AND SUPPORTING ATTACKS
In his concept of the offensive operation, the commander designates main and supporting attacks.
1. Main Attack.
a. Main Attack Units. The units conducting the main attack are assigned a mission which, when achieved, successfully accomplishes the unit's mission. The main attack secures a key terrain objective or position or destroys an enemy force. Main attack elements have traditionally been assigned terrain objectives; however, the main attack may also be an attack by fire.
c. Main Attack versus Main Effort. Both "main attack" and "main effort" are mechanisms for allowing the coordination and concentration of combat power, but they are not synonymous. The main attack is the task force's main effort at the decisive phase of the attack. The main effort is the focus of combat power at any given time during the attack.
d. Weighting the Main Attack. In planning the scheme of maneuver, the main attack must have sufficient combat power and support to accomplish its mission. Methods of weighting the main attack include--
- Assigning the main attack to the companies with the highest combat power and bold, aggressive leaders.
- Allocating additional combat platoons.
- Attaching or placing CS elements in direct support.
- Providing priority of CS and allocating priority targets.
- Positioning overwatch of support-by-fire elements to support.
- Coordinating adjacent unit or attack helicopter support by fire.
- Positioning and assigning planning priorities to the reserve.
- Locating the tactical (TAC) CP where it can best control the main attack.
- Providing a priority for CSS.
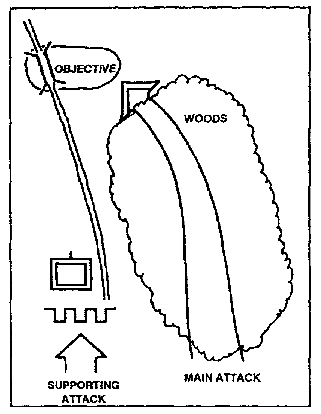
2. Supporting Attack.
a. Contributes to Success. The supporting attack allows the main attack to be successful. It contributes to the success of the main attack by accomplishing one or more of the following:
- Occupying terrain to support by fire the maneuver of the main attack.
- Fixing the enemy in position.
- Deceiving the enemy as to the location of the main attack.
- Isolating the objective.
b. Techniques. Supporting attacks place fire on the objective, and/or on known likely supporting enemy positions. Fires are used to destroy as many of the enemy's major weapons systems as possible before the main attack reaches the objective. Supporting attacks by fire should come from a different direction than that of the main attack. This forces the enemy to defend in two directions and avoids the masking of friendly fire as the main attack closes on the objective. Forces used in a support-by-fire role should be considered as potential reserve forces. Plans to move them forward to assist in the final assault or reorganization and continued operation are part of the commander's contingency planning.
c. Multiple Supporting Attacks. The supporting attack may be by fire and maneuver. In this case, one or more company teams are tasked to secure, or seize terrain dominating the main attack's objective. This form of supporting attack is used when conditions will not allow a supporting attack by fire. The task force/battalion seldom can have more than one supporting attack by fire and maneuver because it will weaken the main attack, make the attack difficult to control, and increase the chance of a piecemeal attack. However, it is possible to have one supporting attack by fire and one by fire and maneuver.
SEQUENCE OF THE ATTACK
Generally, the following sequence is followed in battalion/task force attacks:
1. Reconnaissance. Reconnaissance begins as soon as possible after the task force receives its mission. Information on the avenues of approach, obstacles, and enemy positions is critical to planning the attack. Reconnaissance continues throughout the attack.
2. Movement to the Line of Departure. When attacking from positions not in contact, task forces often stage in rear assembly areas, road march to attack positions behind friendly units in contact with the enemy, conduct a passage of lines, and begin the attack.
3. Maneuver. The task force maneuvers to a position of advantage.
4. Deployment. The task force deploys to attack or fix the enemy, if bypassing.
5. Attack. The enemy position is attacked by fire, assaulted, or bypassed.
6. Consolidation and Reorganization. The task force eliminates resistance and prepares for, or conducts, further operations.
GO TO: