|
RDL Homepage |
Table of Contents |
Document Information |
Download Instructions |
LESSON 1
COMBINED ARMS OBSTACLE OPERATIONS
OVERVIEW
LESSON DESCRIPTION:
This lesson describes the modern battlefield and what you as an engineer can expect from threat forces and their engineers during battle. This lesson also covers US offensive, defensive, and retrograde operations and how engineer missions fit into the defensive framework.
TERMINAL LEARNING OBJECTIVE:
| ACTION: | Identify the role of threat engineers on the modern battlefield. Identify the principles of threat engineer employment, threat engineer support to offensive and defensive operations, and threat mobility and countermobility requirements. Identify US engineer planning considerations for offensive and defensive operations designed to counter threat operations. |
| CONDITION: | Given the material contained in this lesson. |
| STANDARD: | Correctly answer all questions in the practice exercise at the end of this lesson. |
| REFERENCES: | The material contained in this lesson was derived from the following Field Manuals and material approved for instruction by the US Army Engineer School (USAES): |
INTRODUCTION
Any threat to our national interests during the next five to ten years will most likely involve highly trained enemy forces using Soviet-style tactics, organization, and equipment. Therefore, US forces must prepare and train to fight on a battlefield where-
- Highly-mobile forces use combat systems that deliver firepower of unprecedented volume, speed, accuracy, range, and lethality.
- Aerial combat, surveillance, transport, reconnaissance, and target-acquisition systems crowd airspace.
- The enemy targets communications systems with indirect fire. Sophisticated electronic-warfare (EW) operations make command and control (C2) difficult to achieve and maintain.
- Scatterable and "smart" mine systems, rapidly and remotely delivered, severely affect ground mobility.
- Nuclear, biological, and chemical (NBC) weapons pose a growing threat to combatants and noncombatants.
- Success on the battlefield depends on mobility and countermobility efforts. These efforts not only occur near the forward line of own troops (FLOT), but also in rear areas. Commanders must concentrate their forces at the decisive time and place. They must increase unit versatility, use movement and maneuver, and impede the opposing force's movement and maneuver. Additionally, they must prevent enemy reinforcement of committed units and their resupply.
PART A: THREAT ENGINEER OPERATIONS
Engineers play a vital role in the success of threat combined arms operations. In the threat's view, the key to tactical success is tactical mobility. Therefore, the threat combat engineer's mission is to keep the offense moving. Threat engineers organize, equip, and train to accomplish this mission under fire and in all environments including NBC.
1-1. Threat Organization. All tank and motorized rifle units from front to regimental level have organic engineers. In combat, these engineers form special combat groups to perform direct-support (DS) missions. Higher echelons, front or combined arms armies, maintain considerable engineer reserves for concentrated use as needed or for attachment to subordinate formations. These reserves allow rapid switching of engineer effort from one area to another and afford maximum tactical and operational flexibility. It is not unusual for the senior formation commander to divert an engineer element to another mission, even when that element is required for a concentrated effort elsewhere on the battlefield.
Threat doctrine emphasizes that commanders at all levels must strive for maximum flexibility in using engineer assets. Commanders do not isolate engineer tasks but make them a part of the overall tactical plan.
Combat engineer units at any level are one of two types: special/technical or general purpose.
Special/technical units perform the following tasks:
- Engineer reconnaissance.
- Field-fortification construction.
- Assault river crossing.
- Water-supply procurement.
- Camouflage.
- Road and route preparation.
- Bridge construction.
- Obstacle construction and removal.
- Minefield breaching and clearing.
General-purpose units can perform any of the above tasks but usually to a lesser degree than their special/technical counterparts. In either case, the threat envisions their engineers conducting most, if not all, of these tasks under fire or well in advance of main assault elements.
Soldiers of other combat arms units carry out many simple and general engineer tasks. For example, threat commanders expect all of their combat soldiers to be proficient at mine clearance. Tank-mounted mine plow and roller operations are an armored-force responsibility, although engineers are available for advice in deciding whether or not to employ such devices.
The organization of threat engineer units is designed to accomplish the following specific aims:
- Conduct engineer tasks needed to support the tactical employment of other combat arms, especially the movement of tank and motorized rifle elements.
- Attach additional engineer assets to subordinate elements in order to maintain a significant engineer reserve.
- Dovetail and expand engineer tasks in the offense by using follow-on engineer elements with increased capabilities.
- Provide cohesion to the defense and security in the offense by employing mines, obstacles, field fortifications, and antitank (AT) defenses.
The structure of threat engineer units remains constant at the regiment and division levels but not at higher levels of command. Engineer units assigned to a front or a combined arms army vary in size and structure depending on the level of importance of the major command in the overall operational or strategic plan. Most likely, a front engineer reserve is twice as large as that of a combined arms army.
1-2. Principles of Threat Engineer Employment. The threat observes its military principles in order of precedence. To a certain extent, threat military principles appear as a rephrasing of Western principles of war. These eight military principles, in order of priority, are-
- Mobility (speed) and high numbers of combat operations.
- Concentration of main efforts and creation of superiority in forces and a means over the enemy at the decisive time and place.
- Surprise and security.
- Combat activeness (constant combat and pressure).
- Preservation of the combat effectiveness of friendly forces.
- Conformity to the goal.
- Coordination.
- Action upon the enemy to the entire depths of his employment and deep into his rear area.
These principles are basic to a threat officer's approach to any combat problem. Mobility has a profound effect on any decision. For example, achieving high-speed execution of combat missions is the first principle. Therefore, it takes precedence over avoiding casualties and preserving the combat effectiveness of friendly troops. So, in the threat's view, saving time is more important than saving lives. The threat commander takes fewer casualties by exercising battlefield initiative and dictating the terms of combat. In adhering to these principles, the role of threat combat engineers is to aid other combat arms elements. Threat engineers follow these principles closely, thereby attaining greater combat effectiveness.
In addition, the threat has certain principles peculiar to combat engineers. These principles are binding upon the threat engineer commander. They state that combat engineer operations must--
- Correspond to the impending battle concept and support the commander's plan.
- Finish in time to allow the completion of tactical activities to implement the plan.
- Conceal their activities in order to deprive the enemy of intelligence indicators.
- Help direct the effect of the main attack in the offense or the main sector in the defense.
- Maneuver rapidly to adapt to changing battlefield situations.
- Deceive the enemy about the main effort's direction or location.
1-3. Threat Engineer Support of the Offense. Maintaining high rates of movement is the most important tactical principle of threat military doctrine. It is the main function of threat engineers in the offense. Threat engineers emphasize clearing and maintaining routes for advancing combined arms units. This includes breaching or removing mines and obstacles, crossing water obstacles, and aiding in flank protection or protection against counterattack. Threat engineer reconnaissance done independently or jointly with other reconnaissance means, plays a significant role in aiding movement. Camouflage and protection during halts or defensive operations are also basic threat engineer functions. Supporting logistics operations in rear areas receives secondary attention.
These threat engineer requirements create certain key functions that threat engineer troops must perform. These functions include engineer reconnaissance, movement support, mine and countermine warfare, and river crossings.
a. Threat Engineer Reconnaissance. The goal of threat engineer reconnaissance is to provide a comprehensive report on the possibility of march routes. Engineer reconnaissance is conducted by engineer elements attached to combined arms or reconnaissance units or by engineer officers acting as part of the commander's reconnaissance party.
Threat engineer reconnaissance validates plans made from intelligence without prior inspection of the terrain. Engineer elements performing this reconnaissance must determine-
- The degree of passability of the entire route.
- The location and nature of obstacles and the engineer assets required to overcome them.
- The condition of all crossing sites, wet or dry.
- The location and quantity of material needed to improve the march route.
- The nature of the terrain and the location of areas with natural concealment.
The most commonly employed formation in threat engineer reconnaissance is the threat engineer reconnaissance patrol, Inzhenerny Razvedyvatel'ny Dozer (IRD). The IRD varies in strength from a squad to a platoon and is commanded by an officer or senior noncommissioned officer (NCO). The IRD is usually vehicle-mounted, using the reconnaissance version of the BRDM or BTR-60. The commander gets maps and aerial photographs of the march route. He checks column composition showing the number and types of vehicles the' route must accommodate.
Significance to Friendly Forces: The appearance of threat engineer reconnaissance elements serves as an important intelligence indicator of impending offensive action. Higher headquarters provides highly-valuable information on the timing of threat activity in advance since threat engineers normally conduct their reconnaissance one to one-and-a-half days before the main force's movement. High rates of movement and engineers predicate threat offensive tactics and are paramount in executing this movement. Friendly counterreconnaissance action directed against IRDs deprives the threat commander of engineer intelligence vital to executing his tactical plan. Finally, the documents carried by the IRD commander provide portions of the threat commander's actual tactical plan.
Threat engineers conduct their reconnaissance in a different manner than when they support an approach march. They supplement existing intelligence concerning roads, topography, and enemy defenses by using aerial photography and aerial visual reconnaissance. Threat commanders attach their engineers to different combined arms reconnaissance elements. The IRDs are employed to penetrate defenses and to reconnoiter either a specific avenue of approach (AA) or particular defensive fortifications and obstacles. Other threat engineers conduct reconnaissance by setting up covert engineer observation posts (OPs) close to or within the defensive sector.
One threat engineer OP is set up for every 2 kilometers (km) of front in order to observe the entire enemy FLOT and to determine the engineer action and equipment needed to properly support the attack. As the attack progresses, these OPs continue to observe the assault's effectiveness. The OPs make recommendations which concern altering the operations plan (OPLAN) or committing the engineer reserve.
Significance To Friendly Forces: The purpose of threat engineer reconnaissance is to develop intelligence supporting the employment of first-echelon assault elements. The value of denying this information through aggressive counterreconnaissance cannot be overemphasized. Since assault engineer tasks are a prerequisite to the execution of the threat commander's tactical plan, any friendly action that interferes with these tasks will degrade the plan's execution.
b. Movement Support. The threat army believes that without adequate engineer preparation, the approach march is sometimes not possible. Therefore, the results of engineer reconnaissance serve two purposes: selecting column routes that require the least engineer preparation and planning the employment of engineer assets for any route clearing needed.
(1) Movement principles. Considering the results of engineer reconnaissance and the tactical requirements of the OPLAN, the threat commander selects the unit's approach route. The chief of engineer services then drafts the engineer plan for movement support. The plan includes the following two principles:
Engineers are dispersed evenly throughout the march column to ensure proper engineer support to the entire formation.
Engineers work as far in advance as possible. Threat doctrine states that movement-support elements should ideally operate one-half day in advance of the main force.
(2) Route preparation. The manual task of route preparation usually falls to a temporary organization called a movement support detachment, Otryad Obespechentya Dvizheniya (OOD). The threat can form several OODs from the engineer battalions of the tank and motorized rifle divisions. Additional OOD assets exist in the engineer companies of the tank and motorized regiments. The OOD's organization varies, depending on the scale of work undertaken and the assets available. In general, the faster the desired rate of advance, the stronger the OOD. In most cases, tank and motorized rifle elements reinforce OODs to aid engineers in those tasks conducted under fire. Table 1-1 shows the typical variations in the OODs' structures.
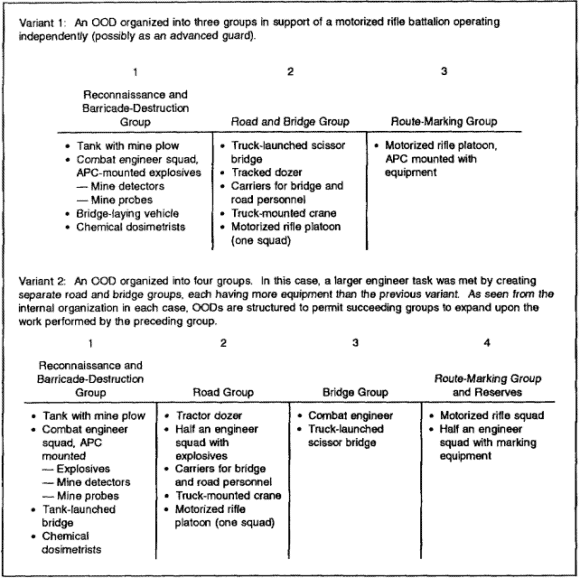
The OOD groups have the following missions:
- Reconnaissance and barricade-destruction group: Reconnoiters the march route, clears obstructions, and selects the column route.
- Road and bridge group: Prepares the route and provides crossings.
- Route-marking group: Marks the route and provides security and traffic control.
(3) Movement. Moving into position directly behind the division's advance guard or sometimes behind the advance guard's point security patrol, the OOD normally moves about one to two hours in advance of the head of the march formation. A typical sequence of activities for an OOD would consist of the following:
- The reconnaissance and barricade-destruction group reconnoiters and clears enemy minefields and obstacles protecting a river-crossing site. Engineers use explosives to clear obstacles while plow- and roller-equipped tanks clear lanes through the minefield. Using information acquired by an IRD, additional reconnaissance of the riverbanks determines the exact extent of preparation needed for bridging. Tank and motorized rifle elements engage enemy troops in the area.
- The road and bridge group improves initial lanes through minefields, prepares banks for bridging equipment, and emplaces bridges.
- As preceding groups continue movement, the route-marking group emplaces the required route and bridge markers. They set up traffic-control points and regulate traffic flow until relieved by military police (MP) traffic units.
Threat doctrine for route preparation requires a division engineer battalion to be available to prepare up to 100 km of route per day. This is in open country where the enemy has not subjected the roads to specific action to block or destroy them. If the enemy has interdicted the route, then only 20 to 40 km per day can be prepared-less if the engineers conduct their tasks under fire. In such cases, it is common for threat engineers to construct a rough track parallel to the planned route, if possible, to maintain the advance's tempo.
Significance To Friendly Forces: The threat bases its offensive operations upon high-speed execution and the sequenced arrival and departure of combined arms teams at specific locations and times. This doctrine depends upon an exceptionally high degree of coordination. This forces the threat commander to rely upon the movement support activities of his engineer troops to a critical extent. Action that denies the accomplishment of engineer route-preparation activities may create a potentially disastrous situation for the threat commander. The delay of an advancing column by an unexpected obstacle disrupts coordination and slows the tempo of the battle. It also causes succeeding units to combine with those in front, creating a good target for friendly fires.
c. Mine and Countermine Warfare. In the threat's view, the most important mine features are speed and ease of emplacement on the battlefield. Emplacing a mine belt is much more effective and efficient against infantry and tanks than trenches, wire, or other fortifications. Mines are a much quicker means of erecting a defense.
(1) Threat engineers use mines often, even in offensive operations. In supporting the offense, engineers employ extensive minefields in several situations such as-
Transition to the defense. If the attack fails, threat engineers must be prepared to conduct rapid fortification and obstacle activity in support of the hasty defense. In this role, they perform as they do in offensive combat and emplace mines following the overall defensive plan.
Protection against counterattack. In planning the offensive employment of his units, the threat commander constantly evaluates the battlefield for suitable enemy counterattack areas. Areas identified as favorable are usually those that would detract from the maneuver of the combined arms teams. The threat commander considers mining these areas to deny the enemy commander the tactical initiative.
Flank protection. Engaging in a battle of dispersion and maneuver creates extensive exposed flanks. To prevent enemy exploitation of such a condition, the threat commander relies on rapid combat-task execution before the enemy can react and on flank protection by extensively using minefields. During the march to contact and the engagement, threat engineers emplace mines on the flanks of their maneuvering units to prevent attack by mobile enemy forces.
(2) In any future war, the threat believes there will be no distinct front line nor a clearly defined forward edge of the battle area (FEBA) or FLOT. Instead, there will be a series of offensive and counteroffensive axes in the form of spurs and salients. The fluidity of combat under such conditions causes a mine obstacle to offer more flexibility in employment than AT ditches, tetrahedrons, or other relatively static obstacles. Minefields will be the threat's preferred means of protecting vulnerable aspects of offensive deployment. Expect more intimidating mined areas than those used in World War II. All threat troops train in the fundamentals of mine warfare, but combat engineers train specially to perform this function. The primary combat engineer element performing mine-warfare support for the offense is a temporary mobile obstacle detachment Podvizhnyy Otryad Zagrazhdeniya (POZ). The threat forms a POZ from elements of regiment and division combat engineers.
In the offense, the threat commander positions POZs on the flanks of the march column and usually associates them with the AT reserve. He equips each POZ with up to three PMR-3/60 mine-laying trailers with towed mine-carrying vehicles or the new GMZ tracked, armored, mine-laying vehicle. The GMZ vehicle is rapidly replacing the older PMR-3/60. In certain instances, the threat will use the Mi-8/HIP helicopter with removable mine racks and chute dispensers to emplace mines from an altitude of about 5 meters. A division POZ equipped with the GMZ can emplace a 1,000-meter minefield containing 750 to 1,000 mines at 4- or 5.5-meter intervals within 30 minutes.
In the late 1960s and early 1970s, threat doctrine required the POZ to create an obstacle by alternating minefields with other AT obstacles along a 6- to 7-km front. Current threat doctrine calls for AT guns to engage enemy tanks as soon as they run into minefields. Thus, they prefer a short deep mine and gun obstacle belt to a long, thin one, making choice of position critical.
The threat rarely includes antipersonnel (AP) mines in an AT minefield laid in support of offensive operations because of the possible need to recover minefields as the advance progresses. They clearly mark and record the locations of minefields left behind and report this information to the chief of engineer services.
Significance To Friendly Forces: In the offense, the threat commander employs mines in areas evaluated as offering the enemy a significant advantage to interfere with the tactical plan. Thus, the detection of mine-laying activity offers the friendly force a sign of the manner in which the threat command will deploy units and highlights those areas critical to success.
(3) The threat, in planning for the widespread employment of mines, fully expects any enemy to engage in extensive mine warfare. Therefore, countermine warfare is an extremely important task entrusted to threat combat engineers. Breaching lanes through enemy minefields is critical to keeping the attack moving. Equally important is conducting mine-breaching operations covertly to preserve surprise. When attacking from the march, finding the enemy minefields is the job of the IRD. An IRD has several types of mine detectors, the most common being the DIM metallic mine detector mounted on the UAZ 69, 1/4-ton, 4 x 4, light-utility vehicle. The DIM synchronizes itself with the vehicle's ignition system and, upon detecting a metallic mine, cuts out the electrical system and kills the engine. The IRD reconnoiters the limits of the minefield and marks it for the following OOD.
The number of lanes threat engineers clear depends on the terrain and the number of columns in the assault echelon. A leading battalion in the assault along a main axis requires six to eight lanes, one for each assaulting platoon. In secondary sectors, as few as two lanes may be enough. However, the threat engineer uses an average of four to six lanes with at least two developed into permanent lanes (6 to 8 meters wide) for passage of artillery and logistics vehicles. Engineers mark minefield lanes and provide traffic control through the minefield. They mark routes to each lane with red triangular metal flags and black-and-white tape and use illuminating markers at night. They mark routes through their own minefields with signs of various shapes placed not less than 20 meters apart on both sides of the route. If possible, they position the signs so they are not visible from enemy positions.
In breaching the required number of lanes through the minefield, the OOD employs several types of mine-breaching equipment. The normal threat method of breaching minefields during an assault or rapid advance is to employ mine plows fitted to the lead tanks. Although threat engineers reconnoiter the minefield, initial breaching is not primarily an engineer task. The threat employs KMT-4 and KMT-6 plows on the scale of one per platoon of three to four tanks. Engineers aid in fitting these plows and plow-roller combinations (KMT-5s), which are commonly used for minefield reconnaissance. The threat estimates clearing speeds of about 6 kilometers per hour (kph) for plow-fitted tanks and about 10 kph for roller-fitted tanks. Combat vehicles follow these plow-equipped tanks in the breaching of a minefield.
The threat also employs a mine-clearing device mounted on the BTR-50 PK armored personnel carrier (APC). There are two assigned to each division engineer battalion. This device fires and then detonates an explosive hose (line charge) across the minefield. It clears a lane about 180 meters long by 6 to 8 meters wide. This equipment is particularly useful during an assault river crossing when there are minefields on the far bank and amphibious vehicles may have to operate initially in the bridgehead without tank support.
Another mine-clearing device is the explosive line charge. It consists of three separate linear charges, a nose section, and a detonator box. Threat engineers can assemble linear charges to any desired length by connecting 2-meter sections together with threaded collars. The light, sheet-metal, 5-centimeter-diameter, tubular sections contain cast trinitrotoluene (TNT) explosive at 9 kilograms (kg) per linear meter. This device contains a single, double, or triple charge. The front section has a roller to help insert the charge into a minefield. The enemy assembles this device in a rear area, tows it by tank to the minefield's edge, pushes it into a minefield, and fires it. The triple line charge will clear a 6-meter-wide path along the entire length of the charge. A squad can assemble a 500-meter-long triple charge in 1 to 1.5 hours.
Threat engineer squads also use bangalore torpedoes. Sections that are 2 meters long and carrying 6 kg of explosive are connected by collars. The clearance depth of a path 1 to 2 meters wide is limited only by the manageable weight that can be manually pushed into the minefield.
In attacking from the line of march, threat engineers use manual mine breaching only under certain conditions, such as-
- For nuisance minefields along or on routes-especially around craters and demolitions-to allow the route-clearing unit to work freely.
- On approaches to water obstacles and water mines.
- To maintain surprise, especially at night.
- When they hope to make a gap in their own minefields.
- When they commit other mine-breaching equipment to an operation.
When committing assault-breaching operations against a defended enemy minefield, the usual threat practice is to attack with combined arms teams led by combat engineers and supported by artillery and tactical aviation. Such a formation is needed if the combat engineers are to avoid crippling losses to defensive fires. Artillery plays a major role in suppressing defensive fires and allowing the execution of engineer tasks. If artillery support is not available or is too short in duration, plow- and roller-equipped tanks will lead the attack's first wave. Combat engineers closely follow to widen lanes. Here again, the use of plow- and roller-equipped tanks is not an engineer responsibility but an engineer function carried out by tank soldiers. Another means of lane improvement entails mine-clearing tanks dragging a variable length of explosive line charge through the minefield. They detonate the charge to clear mines not uncovered by the plow or roller.
Significance To Friendly Forces: Our minefields should be deep enough to prevent the threat from breaching the entire depth with one line charge. The threat breaching capability with one line charge is now in the 50-meter range. A threat squad can assemble a 500-meter-long triple charge in 1 to 1.5 hours by coupling 50-meter sections together. Planners should check the current threat capability for breaching before determining what size minefield is most effective.
As with other threat engineer activity, threat mine and countermine operations provide both intelligence and tactical values to friendly forces. Minefield-breaching activity shows the impending threat offensive action. Identifying such activity greatly aids in determining times and locations of attack. Keep in mind that threat doctrine calls for fake mine-clearing activity as part of the deception plan. Tactically, the denial of threat countermine actions serves to deprive the threat commander of the tactical initiative.
d. River Crossings. Threat military doctrine dictates that they will cross water obstacles along a broad front at multiple points without pause in the march or advance. They hope this tactic will rapidly overwhelm enemy defenses and maintain the attack's tempo. In the threat's view, a delay at a major water obstacle jeopardizes the success of an entire offensive operation in conventional combat. They feel that during a nuclear attack, it will certainly cause the destruction of large forces massed for crossing. Therefore, the threat recognizes two distinct forms of river crossing-hasty and deliberate.
- Hasty crossing. The hasty crossing incorporates the features of rapid movement. The attacking force crosses the water obstacle in stride, does not stop to consolidate bridgeheads, and continues the advance without pausing. This is the preferred form of river crossing.
- Deliberate crossing. The threat conducts a deliberate crossing when an attempted hasty crossing fails or when they begin hostilities against a well-prepared enemy occupying a river-line defense. Deliberate crossings call for more detailed planning, extensive buildup and preparation, and a greater degree of centralization than hasty crossings.
The role of combat engineers in both types of crossings is critical. While all threat forces are fully trained in their individual roles in river-crossing operations, threat engineer functions provide the margin of success. We will not examine river-crossing operations in their entirety, but will define the role of engineers within the overall effort.
Engineer support to assault river crossings by threat forces occurs in the following areas:
- Engineer reconnaissance of water crossings.
- Route and site preparation.
- Crossing preparation and execution.
- Site protection.
- Support to units on the opposite bank.
(1) Engineer reconnaissance of water crossings. In the threat's view, the key to a successful river crossing is thorough reconnaissance to determine the tactical situation and the technical characteristics of the river and its banks. As a general principle, they will carry out reconnaissance across a wide front to avoid focusing attention on one area.
Additionally, this activity identifies the many crossing sites needed to support the crossing of widely dispersed units.
Threat engineer reconnaissance attempts to learn the following information at each site:
- Possible fording, ferrying, bridging, and snorkeling sites.
- Critical terrain features dominating both banks.
- Information on enemy defenses.
- Entry and exit slopes.
- Bank composition and height.
- River width, depth, and current.
- River-bottom composition.
- Approach and exit routes.
In obtaining this information, engineers may accompany combined arms reconnaissance teams or IRDs may operate independently. An IRD will usually operate from the BRDM engineer reconnaissance vehicle outfitted with a variety of reconnaissance equipment. In some instances, engineers are covertly dropped by parachute directly on the water obstacle.
A typical reconnaissance mission for a squad-sized IRD might require the reconnaissance of two sites within a 500- to 600-meter sector. This task usually takes 4 hours. Scuba-equipped engineers check for water mines and test riverbed conditions. Other members of the IRD select and mark concealed approach routes. They retrieve hydrographic data using depth finders and water-current meters and then determine river-bank conditions and the presence of existing or military obstacles. They also identify enemy defenses and conduct fake reconnaissance activity in other areas to avoid disclosing the main crossing sector.
Significance To Friendly Forces: Engineer reconnaissance performed in support of water crossings has both intelligence and tactical value to friendly forces. Conducting engineer reconnaissance aids in identifying planned crossing sites for combined arms teams and attack times. This information is of extreme importance in planning the friendly tactical response. Counterreconnaissance, which prevents the accomplishment of engineer reconnaissance missions, deprives the threat commander of information vital to the attack's successful execution.
(2) Route and site preparation. Route preparation of approaches to crossing points follows the same procedures as in the approach march. The OODs accompany the lead elements to provide trafficable conditions for the types and numbers of vehicles in the column. A division usually crosses a river on a wide front at a minimum of four points (sometimes up to eight). They simultaneously seek to find suitable areas for each type of crossing means. This requires the engineer staff to plan carefully and assign engineer assets.
The preparation of proper entry- and exit-bank slopes is crucial and depends upon the reconnaissance effort. They use earth-moving equipment and explosives in preparing bridge approaches and entry and exit points at ford, ferry, and swim sites. Rapid execution of these tasks is essential since the crossing maneuver units follow closely behind and depend on suitably prepared crossing points before starting operations.
Significance To Friendly Forces: Site preparation represents the most vulnerable aspect of a threat river crossing. Interference with site-preparation activity translates directly to interference with the sequence and timing of the engineer effort. By denying the site-preparation effort, the crossing units that follow will either be unable to perform their function or be forced to halt. This will disrupt the attack's tempo and the bunching of units that creates lucrative targets.
(3) Crossing preparation and execution. After initial site preparation and just before the actual crossing, threat engineers execute final preparatory activities. Scuba-equipped engineers use explosives to destroy previously located water mines. Where needed, they emplace metal matting on soft-bottom fords. Engineers in amphibious APCs accompany initial assault waves and aid in reducing defenses on the far bank.
During crossings, ferry operations and bridge emplacements are solely engineer functions. Additionally, engineers handle traffic control and direction and ensure that the crossing operation runs at high speed. They consider this extremely important. Threat doctrine sets the desired crossing time for the division combat elements at 3 hours during daylight and 6 to 8 hours at night.
Significance To Friendly Forces: The primary role of threat engineers during this phase is to provide the physical means by which the bulk of the division crosses. The threat usually supports this phase with artillery fires. This phase also marks the arrival of major combined arms teams. In most cases, it will be conducted under the protection of the air-defense umbrella.
(4) Site protection. Starting with initial site preparation and continuing through the crossing, threat engineer elements protect the site, equipment, and combined arms teams from floating mines and enemy raids. Scuba divers and power boats constantly patrol upstream and downstream approaches to the crossing site. They also set up outposts along likely land approaches.
Significance To Friendly Forces: When planning raids against threat gap-crossing sites, consider the presence and locations of these security forces.
(5) Support to units on the opposite bank. As the threat force sets itself up on the opposite bank, elements of the engineer reserve accompany combined arms teams in performing engineer tasks needed to keep the advance moving. In this role, engineers function in the same manner as when supporting the attack from the line of march or when in contact with the enemy. The crossing site will gradually become the responsibility of lines of communication (LOC) troops, and the combat engineers will rejoin the division and prepare to support the next crossing operation.
Significance To Friendly Forces: As with other threat engineer activity, the shift of engineer emphasis accompanies a shift in tactical emphasis. Destruction or damage to bridging and ferrying equipment during this phase reduces the threat's ability to conduct river crossings later.
PART B: US ENGINEER COUNTERMOBILITY OPERATIONS
The threat must preserve its ability to move and maneuver on the battlefield in order to attain its primary military principle--nobility and high rates of combat operations. Threat forces are organized, trained, and equipped to accomplish this principle above all others.
US forces design their denial-operation tasks to slow the movement rate specified by the threat US forces integrate countermobility measures into the concept of operations to impede threat mobility and to increase the hit-and-kill probabilities of friendly weapon systems. Obstacles must be sited to reinforce the terrain and to enhance the effectiveness of friendly battle positions and weapon systems.
Scatterable minefields give friendly forces the capability to deny threat mobility anywhere on the battlefield. They should be carefully planned and executed so that they do not impede friendly mobility during future operations.
Executing countermobility is primarily the responsibility of combat engineers. The engineer and the tactical commander must decide early in the planning process how to best position obstacles to increase the effectiveness of friendly fire and maneuver. Tactical commanders should establish countermobility priorities early in the planning process to ensure that maximum effort is assigned to the most critical tasks.
1-4. Offensive Operations. Engineers employ countermobility activities in all types of offensive operations. In the offense, the priority of the engineer effort is to maintain friendly-force mobility. Countermobility activities during the offense halt or slow the enemy's counterattack capability and isolate the battlefield. Such operations aid friendly forces in debating the enemy in detail. Obstacles and mine warfare in offensive operations have three main purposes: prevent enemy reinforcement, aid economy of force, and provide security.
a. Prevent Enemy Reinforcement. Obstacles and mine warfare can prevent the enemy from reinforcing weak areas under friendly attack and can hinder his movement of reserves and logistics. Use air-delivered or artillery scatterable mines for this mission.
b. Aid Economy of Force. Use obstacles and mines in selected sectors to allow defense by reduced forces. Concentrate relieved maneuver units in other sectors for the attack. Under other circumstances, easily defended terrain reinforced with obstacles and on-call scatterable mines allows a relatively small force to control a sector. Armored cavalry units with a screen or protection mission conduct operations of this type.
c. Provide Security. In offensive operations, emplace mines and obstacles along the flanks of advancing forces in critical areas to halt or slow enemy counterattacks. While planning offensive operations, carefully evaluate AAs offering natural flank protection such as a river or a ridge line. During the advance, if possible, protect a flank by destroying all bridges crossing a river or by interdicting all roads and trails crossing a ridge line. Terrain features, such as swamps, canals, lakes, forests, and escarpments, can be reinforced quickly for flank security.
During offensive operations, engineer countermobility plans must permit rapid obstacle emplacement and flexibility. Time and resources do not permit developing the terrain's total offensive potential Based upon likely enemy reaction, use obstacles to close off the most-probable counterattack avenues. Develop plans for other resources to be committed when the enemy, response becomes apparent Scatterable mines are excellent for this purpose. Preplan air- and artillery-delivered scatterable mines on each available route. Deliver the mines in front of on top of, or on the flanks of the lead elements of an enemy counterattack after the enemy commits itself to one of the routes. Rapid-cratering devices are another excellent capability.
Speed is vital in countermobility operations. Engineer support must keep pace with the advancing maneuver forces. During offensive operations, carefully weigh the effort needed to support countermobility operations against the mobility requirements. Plan and use resources wisely. Under ideal circumstances, make plans flexible for engineer forces to perform both mobility and countermobility operations as the tactical battlefield situation requires.
Control of mines and obstacles and accurate reporting to all units are vital. An obstacle or mine hinders friendly and enemy maneuver. Positive C2 prevents executing minefields and obstacles prematurely. Once the minefield or obstacle has been executed, the executing unit reports through operation channels to higher headquarters, then posts this information on operational and intelligence maps. Send out information on obstacles and minefield emplacement with tactical intelligence. Rigidly follow the recording and reporting procedures for scatterable mines.
The following are key factors for offensive countermobility:
- Enemy situation and capabilities.
- A good terrain analysis to determine where friendly forces are vulnerable to counterattack.
- Speed of obstacle emplacement.
- Preplanning and coordination.
- Information flow to inform friendly forces of friendly and enemy obstacle locations.
1-5. Defensive Operations. The defense's immediate purpose is to defeat an enemy attack. All of the defending force's activities must contribute to that goal.
a. Goal of Defensive Operations. It may be necessary to gain time for reinforcements to arrive or to economize forces in one sector while concentrating forces for attack in another. In either case, a defense or delay may achieve these purposes.
In some cases, forces defend because they cannot attack. The defender then takes advantage of position and superior knowledge of the terrain. Once the enemy has been committed to the defense and weakened by losses, friendly forces maneuver to destroy the enemy with fires or counterattacks. Other cases require portions of a force to retain key terrain or essential tactical, strategical, or political objectives. In some instances, defenders will first seize these objectives with airmobile or airborne forces and then hold them until a larger force links with them.
The following are goals of US defensive operations:
- Defeat an enemy attack.
- Gain time.
- Concentrate forces elsewhere.
- Wear down enemy forces as a prelude to offensive operations.
- Control essential terrain.
- Retain tactical, strategical, or political objectives.
The defense is the stronger form of war because denying success to the enemy is easier than forcing the enemy to do your will. The defender has significant advantages over the attacker. Usually, the defender knows the ground better and occupies it first. He becomes stronger as positions improve and forces mass. Once the battle begins, the defender fights from cover against a more exposed enemy. He uses the terrain to mask movement as forces gather to block and attack the enemy. Finally, the defender can postpone the commitment of major forces until the attack has developed. He can then strike the extended enemy over carefully selected and prepared terrain within the defensive area. The effects of obstacles, air power, and conventional weapons on exposed troops-plus certain aspects of nuclear, chemical, and electronic warfare-favor the defender.
Balanced against the defenders advantages however, is the attacker's single greatest asset-initiative. The attacker takes advantage of the opportunities to concentrate his forces first and to surprise the defender by choosing ground, direction of approach, and time of attack. Also, he uses this initial advantage to mislead or distract the defender. This slows recognition of the main attack and delays the start of countermeasures. The defender's ultimate task is to overcome the attacker's initial advantages and quickly regain the initiative.
The key tenets of Army operations-agility, initiative, depth, synchronization, and versatility (AIDSV) -outline the requirements for a successful defense at any level.
- Agility. Agility sets the terms of battle through the flexible use of fire, maneuver, and EW. As the attacker commits to an action, the defender changes the situation and forces a different countermove. This overloads the enemy's C2 system and makes his reaction uncoordinated and indecisive. Effective use of agility leads to the enemy's piecemeal destruction.
- Initiative. Initiative seizes the tactical initiative locally, then more extensively as the battle progresses.
- Depth. Fight the enemy throughout the depth of its formations to delay, disorganize, and create opportunities for offensive action. The defender organizes forces and resources in depth to gain time and space.
- Synchronization. Synchronize all available tools of battle in well-coordinated combat actions. The attackers will initially outnumber the defenders. In the early stages of the battle, the defenders must capitalize on the advantage of fighting from stationary, protected positions to halt the enemy. A deep attack on the enemy, the actions of security forces, and detailed fire and obstacle plans help to contain the attack.
- Versatility. Versatility is the unit's ability to meet diverse mission requirements. For example, engineers in combat need to be able to support mobility, countermobility, and survivability missions.
Once the defender controls the attacker and has concentrated forces in the area of the main attack, he can then operate against exposed segments of the attacking force. Then, through the cover of his own field artillery, air defense, and fighting on ground that he has reconnoitered and prepared, he has the advantage. Once the attacker has extended into the defended area, he is vulnerable to fires from all sides, surprise attacks on the flanks and rear, and loss of the initiative.
To succeed, the attacker must shatter the defense quickly and maintain high-paced operations to prevent reconstitution. To defeat the attacker, the defender must protract operations, keep the tempo slow enough to allow reaction and, ultimately, isolate and destroy attacking forces.
Do not allow the attacker to focus his full strength at one time and place on the battlefield before preparing defensive countermeasures. Do this through skillful use of terrain and interdiction of following forces using deep attack. The attackers ability to sustain momentum and set the pace of battle must be broken. This occurs if it is difficult to employ fire-support assets and to reinforce, resupply, and direct attacking echelons.
Require the attacker to divert his energies and efforts into nonproductive ventures and to strike at nonexistent targets through deception, operations security (OPSEC), and maneuver. This dissipates his strength and reduces his resources.
The US Army designed its defensive doctrine for use anywhere in the world. The defense that the commander chooses depends on the mission, nature of the enemy, terrain possibilities, and capabilities of available units. The commander may elect to defend well forward or in considerable depth if he is not required to hold a specific area or position. He may even choose to preempt the enemy with spoiling attacks if conditions favor such tactics. Depending on the depth available, forces at hand, and the mission, he may defend by striking as the enemy approaches. The commander fights the decisive battle within the main battle area (MBA). He draws the enemy deep into the area of operations (AO), then strikes along enemy's flanks and rear. All of these methods have been used in the past with decisive results (see Figure 1-1).
b. Defensive Framework. The overall commander delineates areas of interest and influence, the covering-force area (CFA), the FEBA, the rear line of the MBA, and the rear area. Elements of the covering force define the FLOT. After contact with the enemy, the FLOT normally defines the line of contact throughout the battle. The commander also establishes an initial fire-support coordination line (FSCL) and any blocking positions, strong points, stay-behind forces, or phase lines (PLs) needed for executing the plan. Corps and divisions fight unified defensive Army operations within a battlefield framework consisting of three elements: deep, close, and rear battles.
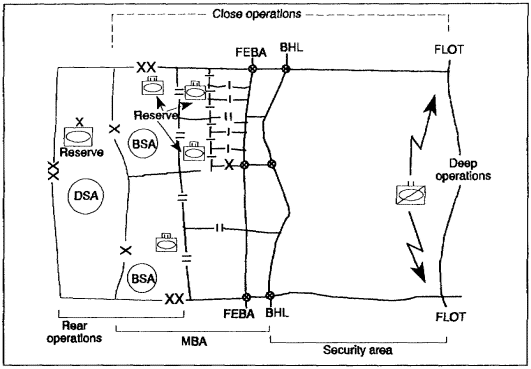
Figure 1-1. Organization of the defense
The commander decides whether to fight a forward or in-depth defense. He organizes the overall defensive effort on the basis of mission, enemy, terrain, troops, and time available (METT-T). The commander assigns forces and resources within the elements of the organizational framework to support the overall scheme. He and his engineer plan complementary actions that support a unified battle plan including deep operations, security-force operations, and the MBA battle.
(1) Deep operations. The deep battle part of Army operations (see Figure 1-2) supports the commander's basic scheme of maneuver by disrupting enemy forces in depth. Its goal is to create opportunities for offensive action against committed enemy forces by delaying the arrival of enemy reserves or follow-on forces or by destroying key enemy organizations. Conduct surveillance operations to identify significant enemy forces in the deep battle area. Use EW, long-range fire, and maneuver in depth to attack enemy forces whose delay or disruption is important to the success of the commander's plan. In the defense, deep-battle activities aim to prevent the enemy from concentrating overwhelming combat power. The main objectives are to separate and disrupt attacking echelons; protect friendly maneuver; and reduce the enemy's fire support, C2 systems, combat support (CS), and combat service support (CSS).
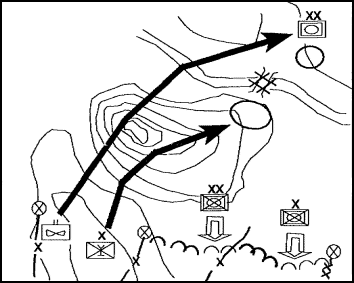
Figure 1-2. Deep battle operations
Engineer support of the deep battle resembles the support given to any other defensive operation. Emphasis is on the speed of ground forces. The first priority of engineer effort will be mobility of the maneuver force. Countermobility, when used for flank security and prevention of counterattack, is the second priority for engineers. Engineers use obstacles that they can install rapidly such as scatterable mines and road craters. Scatterable mines are a significant contributor to success of the deep battle activities. Carefully select the targets and delivery means.
(2) Close operations. Close operations consist of covering-force, MBA, and reserve operations.
(a) Covering-force operations. The covering force normally performs three basic tasks: gain and maintain contact with attacking enemy forces, develop the situation, and delay or defeat the enemy's lead fighting forces.
In the CFA, engineers disorganize enemy movement and enhance friendly fires by using countermobility activities. The density of obstacles in the CFA is less than in the MBA due to the lack of time, the area's depth, and the smaller number of engaged friendly forces. Siting obstacles is extremely important. Manpower and equipment-intensive obstacles are not normally emplaced in the CFA. The commander must decide on the amount of limited resources he will commit to the CFA Obstacles are emplaced in the CFA and the MBA concurrently and compete for the same resources.
Time is a critical consideration in planning the battlefield preparation of the CFA. There is little time for employing obstacles once the enemy attacks. Scatterable mines and quick demolition point target., such as prechambered road craters, are ideal for use in the CFA. Obstacles should aid the covering-force commander by accomplishing the following:
- Enabling CFA units to fire and maneuver without becoming decisively engaged.
- Forcing the enemy to use breaching and bridging assets that he will need later when encountering the MBA.
- Deceiving the enemy as to MBA locations and intentions.
Division and corps combat engineer battalions provide most of the engineer effort in the CFA. Selecting the proper command or support relationship is critical due to the rapidity of the battle.
(b) MBA operations. The MBA is outlined by the corps-designated coordination points that set up the FEBA and the division-designated rear boundaries of the forward defending brigades. Expect the decisive battle to be fought by the forward-committed brigades in this area; therefore, deploy the bulk of the defending forces in the MBA. They prepare to concentrate where needed to defeat the enemy's main thrust For control purposes, subdivide the MBA by division, brigade, and TF boundaries. The MBA should contain a multitude of predetermined (and in some cases, prepared) battle positions from which defending forces fight the battle. The use of battle positions helps to control the combat elements during the flow of battle. They allow the commander to concentrate forces in critical areas with minimal confusion. Using obstacles in the MBA gains time for the commander by slowing the enemy rate of advance. Existing obstacles place certain restrictions on enemy maneuver and speed. To complement this effort, site reinforcing obstacles to disrupt, turn, fix, or block enemy movement.
- Disrupting obstacles break up operational timing, exhaust breaching assets, and separate forces from their assets.
- Turning obstacles move and manipulate the enemy in a desired direction by splitting his forces, canalizing him, or exposing his flanks.
- Fixing obstacles slow and hold the enemy in a specific area so that he can be killed with fires or to generate enough time for the force to break contact.
- Blocking obstacles are complex, employed in depth, and integrated with fires to prevent the enemy from proceeding along a certain AA.
Engineers concentrate most of their obstacle effort in the MBA. In addition to division units, corps combat engineer battalions are available to work in the MBA on a task basis.
(c) Reserve operations. The reserve force, regardless of size, requires engineer support to perform its missions of counterattack, defensive reinforcement or reaction to a rear-area threat. If aviation assets make up the reserve force, then the required engineer support is greatly reduced. Engineers supporting the reserve force may deploy in the MBA with an on-order mission to support the reserve force. This method requires timing and mobility if the engineer unit is to join and deploy with the reserve force. Engineer forces may also be located with the reserve force to provide survivability and countermobility support. This ensures that the unit will remain intact and capable of performing its missions.
(3) Rear operations. The rear area provides for efficient combat support activities. Support elements must train and prepare for self-defense because most combat forces are forward. Obstacles in the rear area normally consist of protective minefields and command priority point obstacles. These obstacles are normally concentrated in areas that enemy helicopters may use as landing or drop zones for airborne forces. Use scatterable mines, especially AP mines, on targets of opportunity in the rear area. The rear-area battle commander competes with maneuver forces for scarce countermobility resources. The overall commander sets priorities for effort and use of materials throughout the battlefield.
1-6. Retrograde Operations. A retrograde operation is an organized movement toward the rear or away from the enemy. Whether forced or voluntary, the appropriate higher commander must approve it. Forces conduct retrograde operations to harass, exhaust resist, delay, and damage the enemy. Such operations gain time, avoid combat under unfavorable conditions, or draw the enemy into unfavorable positions. They are also useful to reposition forces, shorten LOC, or permit the use of forces elsewhere.
The three types of retrograde actions are delays, withdrawals, and retirements. In delays, units give up space to gain time. They do not lose freedom to maneuver and they inflict the greatest possible punishment on the enemy. In withdrawals, all or part of a deployed force voluntarily disengages from the enemy to free itself for a new mission. Withdrawals may occur with or without enemy pressure and aid by other units. In retirements, a force not in contact with the enemy conducts an administrative movement to the rear.
Performing any retrograde operation is difficult Delays and withdrawals are inherently risky. To succeed, organize and execute them properly.
a. Delays. Delay operations occur when forces are inadequate to attack or defend, or when the defensive plan calls for drawing the attacker into an unfavorable situation. These operations normally gain time to-
- Reestablish the defense.
- Protect a friendly unit's flank.
- Cover a defending or withdrawing unit.
- Take part in an economy-of-force effort.
Delays gain time by forcing the enemy to concentrate repeatedly against successive battle positions. As enemy units begin to deploy for the attack, the delaying force withdraws to new battle positions. The enemy must repeat the same time-consuming deployment at the next position. Concurrently, the deep attack slows the enemy's advance and prevents him from massing overwhelming combat power against the delaying force. A delaying force must-
- Maintain contact with the enemy to avoid being outmaneuvered.
- Cause the enemy to plan and conduct successive attacks.
- Preserve its freedom to maneuver.
- Maintain operational harmony.
- Preserve the force.
A delaying force can-
- Harass, exhaust, weaken, and delay enemy forces.
- Expose or discover enemy weaknesses.
- Avoid undesirable combat.
- Gain time for the remainder of the force.
- Conform to movements of other friendly troops or shorten LOC.
- Cover the deployment, movement, retirement, or withdrawal of friendly units.
Although outnumbered, the delaying force must seize the initiative whenever possible in order to conceal a weakness or disrupt enemy plans. To provide the required time, units with a delay mission may attack, defend, screen, ambush, raid, or feint. A commander who is delaying may defend initially and then shift to the delay only after the enemy has concentrated overwhelming combat power against initial positions. The commander then gains time by occupying succeeding battle positions and conducting short counterattacks until space runs out. Limited space may cause the commander to accept greater risks to accomplish the mission. A commander's orders may require delaying the enemy forward of a certain line until a certain time. To do so, the commander would have to accept a decisive engagement.
As the enemy's main effort becomes clear, commanders may add forces to threatened sectors and withdraw them from uncontested areas. Any commander performing a delay maneuver must be alert for opportunities to damage the enemy with short, sharp offensive actions. Such actions keep the enemy on guard and lengthen the delay.
Cavalry units train and organize especially for delaying operations. When available, they should execute the delay.
(1) Delay from successive positions. A delay from successive positions occurs when the sector is so wide that available forces cannot occupy more than a single tier of positions. Maneuver units continuously delay on and between positions throughout their sectors. This method is simple to control. A delay from successive positions is useful in less dangerous sectors. It is easier to penetrate than a delay from alternate positions because the force has less depth and time to prepare (see Figure 1-3).
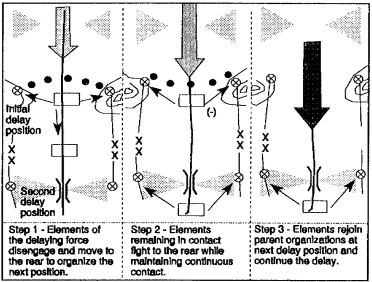
Figure 1-3. Delay from successive positions
(2) Delay from alternate positions. A delay from alternate positions involves two maneuver units in a single sector. While the first unit is fighting, the second one occupies the next position in depth and prepares to assume responsibility for the operation. The first force disengages and passes through or around the second force. It then prepares to resume the delay from a position in greater depth while the second force takes up the fight. A delay from alternate positions is useful in particularly dangerous avenues. This method offers greater security than a delay from successive positions, but requires more forces and continuous coordination of fire and maneuver. It is less certain to maintain contact with the enemy (see Figure 1-4).
(3) Delay preparations. The time available determines the extent of preparations. It is not always possible to complete preparations before the delay starts. Therefore, commanders prepare continuously and adapt plans as situations develop.
- The order for the delay outlines the entire operation and describes its initial phase in detail. The commander issues supplemental orders during the battle to adjust and coordinate the delay. Missions assigned to subordinate elements and their sequence of execution are often more restrictive than other types of operations. Enough initial guidance permits a subordinate commander to fight effectively even if he loses contact with the commander. Each subordinate commander, however, needs enough freedom to exploit any advantage that may develop.
- The delaying-force commander usually organizes the operation by identifying delay positions in depth throughout the area of responsibility. These positions normally follow natural lines of defensible terrain across the sector. Commanders assign times to delay positions showing the minimum acceptable delay in each area. Commanders must carefully weigh the implied risks when imposing time limits on the delay.
- Since sectors in a delay are usually wide, commanders must organize maneuver forces for independent operations. Every subordinate delaying-force commander must understand the tasks and restrictions.
- The commander plans for offensive action as part of the basic delaying maneuver and assigns responsibility to specific units for contemplated counterattacks. Unless reserves prepare to strike and there are preliminary plans for air, artillery, and engineer support the delaying force will miss opportunities.
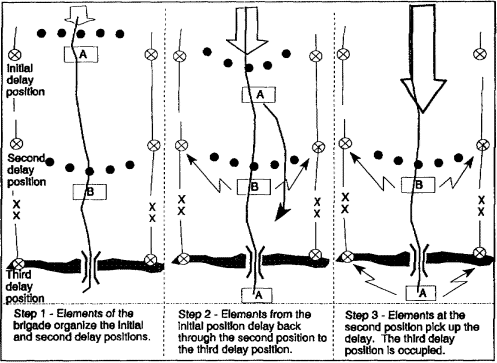
Figure 1-4. Delay from alternate positions
(4) Delay C2. The dynamic nature of the delay places a premium on the commander's ability to stay abreast of the situation and understand the options as the operation progresses. Each commander must be aggressive in gathering and reporting information. Even during active combat, staffs must actively seek information and immediately report essential facts to the commander. Division and corps commanders must pass gathered information to the delaying unit.
Commanders must know the status and location of their own units, flanking units, and enemy units. To enhance coordination, each commander uses prominent terrain features, redundant communications, rehearsals, simple maneuver schemes, and liaison parties. Wide frontages and multiple attacks will make it impossible for the commander to be present at every significant action. The intensity of combat will limit mobility, the condition of forces, and logistics posture. All key personnel must know the obstacle plan well enough to control the operation. Commanders must closely monitor and control radio communications during the delay.
(5) Delay execution. Divisions and smaller units delay from successive positions, alternate positions, or a combination of both. At least a portion of the delaying force maintains constant contact with the enemy. Long-range fire, maneuver, and direct fire cause the enemy to deploy, reconnoiter, maneuver, or halt. Nuclear or chemical fires and short, violent counterattacks or ambushes disorganize and inflict casualties on the enemy.
Spoiling attacks launched as the enemy prepares to attack can also substantially delay his advances. Effective use of obstacles is a key element in executing a successful delay. Regardless of the type of delay tactics used, obstacles enable the commander to effectively trade space for time. Rapidly emplaced obstacles, such as scatterable mines, bridge destruction, and road craters, are ideal to support the delay. Timely and proper placement of obstacles enable a commander to break contact and use economy of force. They also provide valuable time for forces preparing the primary defensive area. Obstacles also weaken the enemy, force his use of breaching asset, and cause him to be more vulnerable when encountering the main defensive area.
- Beginning the delay. If no enemy contact occurs, reconnaissance forces aggressively seek it on a wide front. They will repel enemy reconnaissance forces and determine the direction of enemy movement. At this point, the delay begins.
- Maintaining control. Control during a delay derives from planning The commander must ensure continued coherence by-
- Contesting the initiative. A successful delay requires commanders to contest the initiative whenever possible, throwing the enemy off stride and disorganizing him with-
- Concluding the delay. The delay concludes under several conditions. It will likely occur when enemy forces have halted the attack or when the delaying force has achieved its mission and passed through another force. If the attacking force has halted because of attrition or logistics considerations, the commander of a delaying force can withdraw for another mission or maintain contact. The higher headquarters commander may choose to attack through a delaying force. In this kind of operation, timing for such an attack is usually critical. To aid in timing, the delaying force must help with the forward passage of lines and provide knowledge of the enemy and terrain.
- Passing lines under pressure. If the delaying force withdraws through a defending force, it must pass through lines to the rear and hand off the battle to the defending force. The success of the delay's final stage requires-
A delaying force maintains continuous contact with the enemy but avoids a decisive engagement unless the mission demands it. The delaying operation requires careful planning and should resemble a dynamic defense; however, it must be flexible enough to adjust to enemy maneuver. When the enemy discovers he is facing a delay he will normally try to close and penetrate. Early intelligence of enemy movements permits the defense to adjust and also limits enemy success.
- - Using well-planned and coordinated obstacles.
- Reducing gaps between forces.
- Maintaining surveillance of gaps.
- Ensuring that displacing forces occupy intended positions.
- Maintaining unit integrity, especially smaller units.
- Properly executing all elements of the obstacle plan.
- Ensuring that reports are timely and accurate.
- Maintaining contact with the enemy.
- Gathering intelligence continuously and aggressively about the area of interest.
- Maintaining a reserve.
- - Timely and effective use of obstacles.
- Direct and indirect fires that are violent and coordinated.
- Counterattacks and spoiling attacks.
- Timely nuclear and chemical fires.
- Skillful deception.
- Aggressiveness.
- Effective offensive air support
- - Using obstacles to aid in breaking contact.
- Planning routes.
- Recognizing signals.
- Exchanging liaison parties.
- Supporting with fires.
Passage of lines is especially difficult in limited visibility. Transition should occur just forward of the new defense in such a way as not to reveal location and organization.
In many instances, it will be preferable to pass delaying units to the rear in sectors not under direct attack. Commanders may do so by maneuvering delay forces away from the enemy's front just before they reach the main defense. If the delay force can lead an aggressive enemy into the defense, the delaying force can cause heavy damage.
b. Withdrawals. When the commander finds it necessary to reposition all or a part of the force, he conducts a withdrawal. The deployed force voluntarily disengages from the enemy. The operation may occur with or without enemy pressure or aid by other units.
Without enemy pressure, withdrawals require effective security and depend primarily on speed and deception. Stealth, nuclear, or ground attacks may be needed to divert the enemy's attention. Commanders must have contingency plans in case the enemy detects the withdrawal and attacks. Successful withdrawals normally occur at night or during poor visibility conditions. They also occur in difficult terrain even though poor visibility and difficult terrain complicate friendly control. Smoke and concealed routes can reduce the enemy's ability to observe friendly movements, but commanders must anticipate enemy interference by fires and maneuver in depth.
Under enemy pressure, withdrawals depend on maneuver, firepower, and control. All available fires, perhaps even nuclear fires, support the withdrawal of closely engaged friendly fires. Forward elements move to the rear by aggressive small-unit delaying tactics. Rearward movement must be tightly coordinated and controlled (see Figure 1-5).
When simultaneous withdrawal is not practical, the commander must determine a withdrawal order. If the most heavily engaged units withdraw from the areas of greatest enemy pressure first, the enemy may encircle or destroy major elements of the command. If the least heavily engaged units withdraw first, he may lose all or a major portion of the most heavily engaged units. Commanders must decide what action best preserves force integrity while accomplishing the mission.
Reserves deploy well forward to aid withdrawing units with fire or ground attack. While units are withdrawing under pressure, reserves can launch spoiling attacks to disorganize, disrupt, and delay the enemy. Reserves may also cover the withdrawal or extricate encircled or heavily engaged forces. Army aviation units secure flanks, delay enemy armor, maintain C2, and transport troops and materiel.
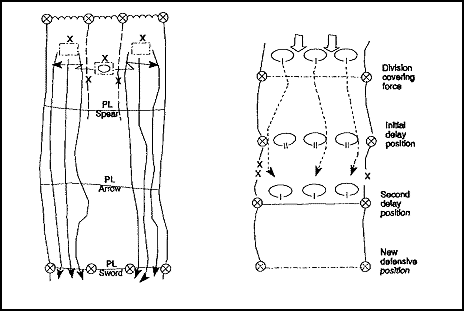
Figure 1-5. Withdrawal operations
Plans and orders for a withdrawal should include-
- New positions to be occupied and new missions.
- Times and priorities for withdrawing units.
- Provisions for breaking contact when the withdrawal is under enemy pressure.
- Organization for combat.
- A comprehensive obstacle plan.
- Deception measures.
- Zones or routes of withdrawal.
- Plans for fire support.
- Provisions for security.
c. Retirements. A retirement is a retrograde operation in which a force out of contact moves away from the enemy. Commanders should have contingency plans if there is any chance of an engagement.
d. Employment of Obstacles in Retrograde Operations. The use of obstacles in retrograde operations varies widely depending upon the nature of the operation. In the delay, planning and executing obstacles are much the same as in the defense. At the other end of the scale, we rarely use obstacles to support retirements, except those that are part of denial operations. Obstacle use in the withdrawal falls between these extremes (see Figure 1-6).
The commander uses obstacles in defensive and retrograde operations, but some significant differences are-
- Friendly forces will have less personnel than the attacker and will be dispersed more widely. With both time and troops to emplace obstacles at a premium, there will be fewer obstacles. These limits, combined with a greater need, places a greater importance on each obstacle.
- Extensive obstacle systems will be rare in retrograde operations. Site single or small groups of mutually supporting obstacles at the most critical locations. Locate obstacles on likely AAs and at each delay position.
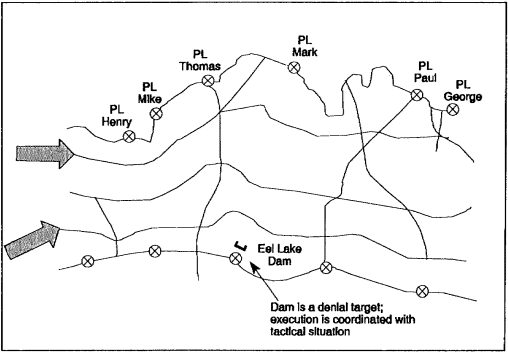
Figure 1-6. Phase-line and obstacle coordination
- Thorough knowledge of the terrain is even more important in retrograde operations than in other operations. Find the most suitable locations for reinforcing obstacles by taking advantage of existing obstacles.
These considerations lead to emphasis upon reinforcing obstacles rapidly emplaced and executed. They offer the greatest delay effect for the preparation effort. These obstacles include bridge demolitions, point obstacles (including point minefields), and scatterable mines. In the delay, obstacles primarily enhance antiarmor direct-fire weapons. Their depth helps delaying forces to break contact.
In the withdrawal, place obstacles to slow the enemy's pursuit and disrupt his plans and to aid friendly forces in avoiding decisive engagement. The enemy will by to use the road net because he seeks rapid movement. The first priority for obstacles goes to those that block key AAs, especially at major choke points (including bridges) and sites available (or hasty river crossings. The next consideration is to develop obstacles that directly aid planned withdrawals (see Figure 1-7).
Figure 1-7. Major choke-point obstacles
Because uncertainty is a large factor in retrograde operations, obstacles that aid in preventing surprise to friendly forces are important. They give the delaying force commander time to shift fires and move reserves to threatened areas. Pay special attention to obstacles that cover the flanks and reinforce lightly-held areas. Potential air drop zones also rate special attention in planning obstacles. Cover them by planned scatterable mines.
In retrograde operations, engineers normally accompany all units. Security forces normally have engineers attached. The basic load of obstacle materials carried by engineers will provide a limited capability to create obstacles. In addition, the retrograde facilitates stockpiling of obstacle material to support rapid placement of planned obstacles (see Figure 1-8).
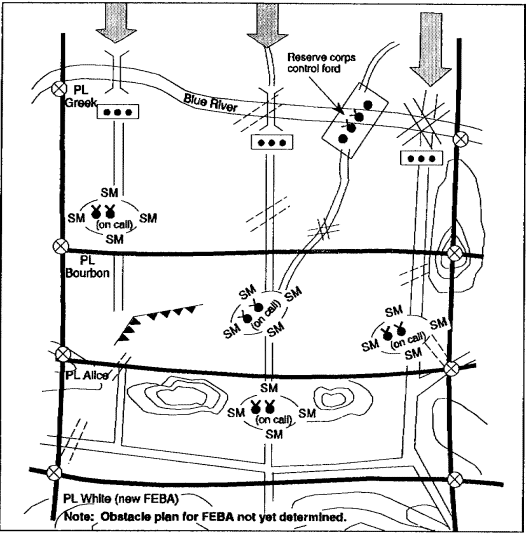
Figure 1-8. Obstacles in retrograde operations
Distributing engineer units throughout the force also places counterobstacle equipment and facilities where they will be able to immediately breach interdictory obstacles (those the attacker might place behind withdrawing forces).
To the maximum extent possible, site obstacles to enhance the kill probabilities of AT weapons. Use remote electronic sensors or other devices to trigger planned artillery fire or mines, and make breaching very costly if observed fire is not possible.
(1) Obstacle planning. In retrograde operations, obstacle planning must be done in as much detail as time will allow. Closely control execution to ensure investment of effort where it is most needed. Use scatterable mines in retrograde operations because they can be placed where, when, and as needed. Carefully plan their use to reduce delivery time. Planned sites include choke points not readily closed by demolitions, likely routes of advance, areas suitable for enemy artillery positions, likely landing or drop zones, and river-crossing sites. Where availability of force permits, specially train, reinforce, and employ selected engineer units to emplace obstacles rapidly after the enemy's main effort is identified or to respond to sudden changes in the situation.
(2) Reserve demolitions. Common in retrograde operations, the lowest-level commander responsible for all units involved in passage of the obstacles will tightly control reserve demolitions. Quickly execute other critical demolitions, such as bridges, to prevent the possibility of capture and the need for demolition guards.
(3) Deception. Deception is important in all retrograde operations and critical to withdrawal. Friendly forces must keep the attacker confused and uncertain of plans, location, and disposition of forces. Plan obstacles so that their execution will not accidentally reveal friendly plans or positions. Concealed obstacles, the use of dummy obstacles, and varied expedient obstacles will aid in deception. Engineers will frequently carry out obstacle emplacement at night and under cover of smoke.
(4) Denial targets. Denial targets are common in retrograde operations. In addition to those assigned by higher headquarters, division and brigade commanders will frequently wish to add their own "tactical" denial targets.
(5) Coordination. Coordinating obstacle planning and preparation takes on the greatest importance in retrograde operations. Corps or theater Army (TA) engineer units may construct positions and obstacle systems well to the rear of the forces that will eventually fight there. In this instance, coordination arrangements between the preparing and final using units become vital.
1-7. Summary. In supporting battlefield operations, the threat combat engineer's role is to keep the offense moving. One cannot overemphasize the extreme importance of this effort to the overall conduct of the offense. Remember, the threat bases its offensive combat upon mobility, rapid advance, surprise, secrecy, and the close coordination of all arms. While first appearing to be highly fluid in nature, close inspection reveals that the threat bases its offensive style upon the carefully synchronized and sequenced interplay of rapidly moving units.
The mission of threat engineers is to create movement conditions that will allow this noticeably complicated activity to occur unhindered and will enable the threat commander to enjoy total tactical initiative while denying it to the enemy.
In order for the threat to attain its primary military principle-mobility and rapid combat operations, it is extremely important to preserve the ability to move and maneuver on the battlefield. Threat forces design, organize, train, and equip to achieve this principle above all others.
US denial-operation tasks must be organized and executed to slow the movement rate specified by the threat. Integrate the use of countermobility by friendly forces into the concept of operations not only to impede threat mobility but also to increase the kill probability of friendly firepower. Site obstacles to reinforce the terrain and increase the effective firepower from friendly battle positions.
Use denial operations along the FLOT as well as deep into the threat's rear area. The use of scatterable minefields gives friendly forces a capability to deny threat mobility anywhere on the battlefield. Carefully plan and execute scatterable minefields so as not to impede friendly mobility during future operations.
Denial-operation execution is primarily the responsibility of combat engineers. The engineer and the tactical commander must decide early in the planning process how to best position obstacles to increase the effectiveness of friendly fire and maneuver. Tactical commanders must set up countermobility priorities early in the planning process. Early planning will increase effort devoted to those countermobility tasks deemed most critical.
Countermobility activities are essential in order to defeat the first principle of the threat by delaying, channeling, or stopping the threat offensive movement. An analysis of recent wars shows that effective and well-planned integration of countermobility activities and firepower can enable an outnumbered force to win.
Practice Exercise

