|
|

Table of Contents |
PART 5. TIME EVENT CHARTING
Time Event Charting
The last two techniques discussed - Link Analysis and Matrix Manipulation are the most difficult of the five tools covered in this paper. They require the most skill and probably the most time to prepare. They are also the most abstract to interpret. The next technique to be covered - Time Event Charting (TEC), is the easiest to prepare, understand, and use.
A TEC chart is a time line. It is a method for placing sad presenting a group's actions in chronological form. Like Link Analysis, a TEC chart uses symbols. In this case, the symbols represent events, dates, and the flow of time. TEC charts share another similarity with link diagrams and matrices: they are all designed to store and display a great deal of information in as little space as possible.
TEC charting evolved out of a problem that the authors encountered in doing research on the development of terorist groups. There did not seem to be a way of looking at the sum total of a group s activities.
without getting bogged down in the details of particular terrorist Incidents. Traditional chronologies were found to be cumbersome and distracting. They were also difficult to use in briefings. Usually appearing in lists of events or on file cards, they require the constant flipping through page after page of incident reports. While event summaries are useful, pages and cards get out of order and the bulk of the material gets in the way of seeing the "big picture." Interested in portraying a large amount of information in s small space, the authors developed a technique to use symbols to represent incidents and to place long chronologies on as few pages as possible.
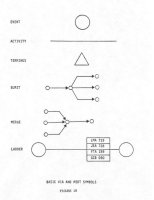
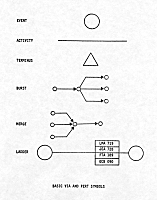
The symbols used in creating TEC charts are simple. Circles are used to represent terrorist incidents or important events. Each incident is portrayed by a single circle. The circles are drawn large enough so that the date of the incident or event can be written inside of it. A short description of the Incident, a few words or sentences at the most, is written underneath the circle. The circles are placed on a page from left to right in rows, running from top to bottom, with arrows drawn to show the flow of time. Each of the symbols is displayed in Figure 16.
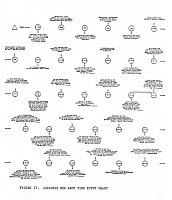
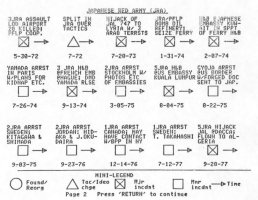
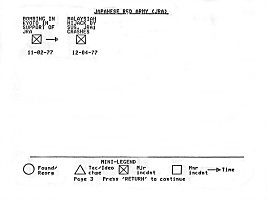
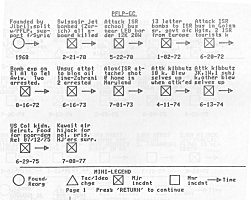
Using this abbreviated format, many events can be displayed on a single page. Figure 17 is a sample TEC chart of the Japanese Red Army (JRA). It comprises thirty-two separate events and incidents in the JRA's history from 1948 until the end of 1977. It follows the group through its many transitions from its beginning as a student movement, Its various ideological and tactical fractionalizations, into its period of terrorist action. Note that many of the textual descriptions accompanying the incidents refer the investigator to a particular file on the incident. Mess references tell the Investigator where to look in existing group files for more information on specific actions without cluttering the page with detail.
TEC charts are excellent for use in briefings. The format is also flexible. Other symbols such as triangles, squares, or pentagons, can be used along with circles to distinguish different kinds of events. Tactical changes can be represented with one symbol, while others are used to represent logistical actions, intelligence operations, and to distinguish between major and minor events. By using a variety of different. symbols, the investigator can better display the changes that have occurred during a group's history. Investigators are limited only by the number of different symbols they can draw, and the,reader's ability to remember what each symbol represents.
VIA and PERT
The techniques reviewed thus far deal with describing, analyzing, and displaying attributes of terrorist groups. Matrices and link analysis are useful for uncovering a group's different organizational structures. Time Event Charting is an excellent way to present a chronology of group activities. The next two techniques look at a different aspect of terrorist investigations. Rather than focusing on a group as a whole, VIA (Visual Investigative Analysis) and PERT (Program Evaluation Review Technique) are used to reconstruct and investigate single terrorist incidents. As with the other techniques, VIA and PERT help the investigator analyze the connections among fragmented bits of information. The next two techniques, however, offer investigators a way to focus on individual incidents in order to develop a general, graphic overview of a crime.
The goals of VIA and PERT are to depict clearly the sequence of activities and events that lead up to the carrying out of a crime. The two techniques have a variety of uses in terrorist investigations, including:
The two techniques break down complex activities into their component parts. Any activity, regardless of how simple it appears on the surface, can be seen as a series of discrete, but interconnected, tasks. We all take driving to work for granted. It Is an activity that confronts us every working day. As long as our car is working, it is a simple task. If you think about its, however, driving to work Is actually a complex series of activities and events. Each of a number of individual tasks must be carried out if the journey from home to work is to be successful. For Instance:
After all these steps, you are just now getting the car away from your house, and you haven't even started driving yet. Even with as simple an activity as this, the logical structure of the activity is clear. Each task has to be performed successfully, or the whole activity collapses and fails. Moreover, there is a defined sequence to the activities. Each task has to be completed in order.
Some activities can be carried out simultaneously, however, if you have someone assisting you. For instance, you can be starting the car while your spouse or child opens the garage door. Performance of an armed robbery requires a similar set of tasks. A gun cannot be used in a crime unless the perpetrator, at some point, has acquired the weapon. If the weapon is loaded, at some point the perpetrator has also had to acquire the ammunition. We can identify four tasks here:
Again, the activity has a logical sequence. Some tasks must be completed before other may begin. Both the gun and the ammunition must be acquired before the gun can be loaded. Some may be carried out simultaneously - both the gun and the ammunition can be acquired at the same time. Each of the activities must be completed before the goal - armed robbery can be achieved. Meanwhile, the perpetrator has probably carried out a number of other tasks, including:
and a host of other tasks, each of which must be carried out before the crimes can occur.
There are two ways to look at the investigation that follows the crime. First, the investigation must be planned in advance. A realistic schedule of activites for the Investigative staff, complete with deadlines, must be generated. Important questions must be answered:
The goal here is to plan in advance the most efficient allocation of Investigative and analytic resources at the department's disposal. It is for such forward planning that PERT was developed.
Second, the crime has to be reconstructed. Each of the elements of the crime must be identified, and evidence collected to show who participated, what their role was, when they were involved, where they were during the entire preparatory process, and how they figured into the final criminal act. VIA is an excellent tool for this kind of retrospective analysis.
Like the other techniques discussed in this paper, PERT and VIA use a number VIA use the same set of symbols, and basically the same rules in putting charts together. The two techniques are distinguished?in that PERT is used to plan activities that will be carried out in the future, while VIA is used to reconstruct and analyze activities that were carried out in the past. The symbols and definitions employed in each are not new. They are, developed from networking and charting techniques that are a regular part of business and industrial management.
VIA was developed for use for the Los Angeles Police Department's Investigation of the assassination of Robert Kennedy. The technique, adapted from PERT, was used to organize and manage the enormous amounts of data that were collected during the investigation. When the chart was entered into testimony during the trial of Sirhan Sirhan, it stretched eighty feet around the courtroom, clearly displaying the suspect's activities during the five days prior to the assassination. It was later used in a variety of California criminal investigations, each of which was characterized by complex crimes involving considerable detail. Among the cases in which VIA charting figured were the prosecutions against the "Zodiac" and the "Slasher" killers.
While VIA experts are difficult to find, individual police departments are encouraged to develop an expertise in using the technique. The symbols are easily learned and interpreted, and form a useful tool in aiding investigators in the management of complex data collection and analysis. Helping to piece together the puzzle of fragmented evidence, the investigator can. ensure that a chart includes all the necessary elements for prosecution. The technique is flexible, and can be adapted to the needs of a particular department or investigation. By using the standard set of symbols, however, users are in a position to communicate with anyone familiar with the techniques.
As stated above, the symbols used in VIA and PERT represent the flow of activities and events that culminate in a finished project. The project can be either a terrorist action or a criminal investigation. Among the symbols used are:
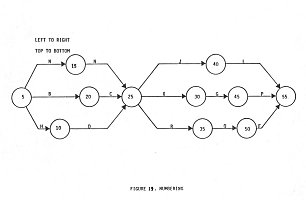
Each of these symbols is displayed in Figure 18. When combined with VIA or PERT chart, the series of events and activities is called an activity line. The activity line is read from left to right, top to bottom on a page. The length of the activity line has no significance. In cases where time is indicated, it is usually noted below the activity line. Elapsed time can also be written in the symbols that represent events:
The activity lines and the events can be labled for clarity. Activities are usually accompanied with a short textual description that sits either above or below the line. For reference purposes, events are numbered in multiples of 5 or 10. The numbers run in sequence from left to right and top to bottom. Figure 19.
The initial concern in constructing a chart is to answer three basic questions:
Answers to these questions set the initial sequence of activities that the chart will represent. Once the activities are placed in order, they are drawn in sequence from left to right. As with link diagrams, care should be taken to make sure that lines do not cross one another.
As stated above, VIA abetting works backward from a set point in time to reconstruct activities that have already occurred. PERT charting, on the other hand, is used in a similar fashion to schedule future events towards the anticipated completion of a series of activities. It helps Investigators and planners decide what has to be done, and predict realistically how long a project will take. It helps identify and coordinate the various tasks that must be performed, decide who will perform them, what must be done first, and what some people can be doing while others work on different tasks.
Like VIA, PERT assumes that each task or activity is independent. It may require that other tasks be performed before it, or that it be finished before others may begin. Yet each task has a definite starting point, and an identified point at which work can be considered complete.
As such, PERT helps place activities in order. For complex investigations, it can greatly assist departments in scheduling the valuable resources of investigators, surveillance teams, analysts, decision makes, informants, and response teams. Used conscientiously, it can help a department bring a complex investigation to a smooth and successful completion.
TIME EVENT CHARTING
A TEC chart is a time line. It is a method for placing and presenting a group's actions in chronological form. Like Link Analysis, a TEC chart uses symbols. In this case, the symbols represent events, dates, and the flow of time. TEC charts share another similarity with link diagrams and matrices: they are all designed to store and display a great deal of information in as little space as possible.
TEC charting evolved out of a problem that the authors encountered in doing research on the development of terrorist groups. There did not seem to be a way of looking at the sum total of a group's activities without getting bogged down in the details of particular terrorist incidents. Traditional chronologies were found to be cumbersome and distracting. They were also difficult to use in briefings. Usually appearing in lists of events or on file cards, they require the constant flipping through page after page of incident reports. While event summaries are useful, pages and cards get out of order and the bulk of the material gets in the way of seeing the "big picture". Interested in portraying a large amount of information in a small space, the authors developed a technique to use symbols to represent incidents and to place long chronologies on as few pages as possible.
The symbos used in creating TEC charts are simple. Circles are used to represent terrorist incidents or important events. Each incident is portrayed by a single circle. The circles are drawn large enough so that the date of the incident or event can be written inside of it. A short description of the incident, a few words or sentences at the most, is written underneath the circle. The circles are placed on a page from left to right in rows, running from top to bottom, with arrows drawn to show the flow of time.
Using this abbreviated format, many events can be displayed on a single page. Figure 1 is a sample TEC chart of the Japanese Red Army (JRA). It comprises thirty-two separate events and incidents in the JRA's history from 1948 until the end of 1977. It follows the group through its many transitions from its beginning as a student movement, its various ideological and tactical fractionalizations, into its period of terrorist action. Note that many of the textual descriptions accompanying the incidents refer the investigator to a particular file on the incident. These references tell the investigator where to look in existing group files for more information on specific actions without cluttering the page with detail.
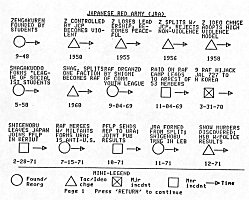
The Time Event Chart format currently available on both the 11/70 and Tektronix versions of TRAP/TARGIT has been modified to allow more efficient analysis of the charts' key components. The modification creates four basic categories of group?related activities: founding/reorganization, tactical/ideological change, major incident, and minor incident, and assigns each category a distinct and easily recognized symbol. These symbols are displayed in Figure 2
The modified TEC is designed to facilitate rapid comprehension of patterns of activities in a group's history. Analysts no longer have to digest lengthy texts or review numerous incidents to familiarize themselves with key events and dates in a group's development. The group's history can be scanned quickly.
TEC charts are excellent for use in briefings. The format is also flexible. Other symbols such as triangles, squares, or pentagons, can be used along with circles to distinguish different kinds of events. Tactical changes can be represented with one symbol, while others are used to represent logistical actions, intelligence operations, and to distinguish between major and minor events. By using a variety of different symbols, the investigator can better display the changes that have occurred during a group's history. Investigators are limited only by the number of different symbols they can draw, and the reader's ability to remember what each symbol represents.
Examples of TEC charts generated from automated TRAP/TARGIT system
VISUAL INVESTIGATIVE ANALYSIS (VIA)
VIA is a recently developed taw enforcement tool used to chart investigations
involving complex crimes. The tremendous amounts of Information detailed in
an investigator's report makes it difficult to analyze the relationships between
isolated pieces of important data necessary to better understanding the elements
involved in a crime. Isolating these elements and charting them In terms of their
logical dependence upon one another allows the observer to visually follow the
crime much as you?would in reading a road map which gives you clear direction a
in reaching a desired goal.
The goal in the use of VIA is an understanding of the Involvement of persons places, and things in the overall completion of a crime from Its initial beginning up to the point of final completion. Through the use of a clearly defined set of symbols the Investigator can chart the relevant pieces of Information available to him into the VIA format. He can then monitor that VIA chart and determine what conclusions can be drawn from the visual relationships indicated, adding to an investigation new problems that are brought to light.
In convincing your supervisor or the District Attorney that it is worthwhile to continue investigating a given case, one is beset wish many problems. The sheer volume of paperwork alone is enough to prevent them from being overwhelmed by the prospect of having to read your report. A VIA dart in this instance can be used to graphically present a general overview of the crime as well as to whether or not the necessary elements exist to pursue the investigation further; to determine if one Is able to prosecute or put the case to some useful purpose.
The supervisor has the capability to monitor the VIA chart to determine how the investigator's time can be better spent and to assure that deployment of material or manpower can be allocated to a given investigation. He is in a position to be on top of the investigation at all times and is therefore able to justify the ongoing activities within his section.
It is a valuable visual aid in making presentations before groups. Through the visual use of the overhead projector or printed handouts of the VIA chart one is able to describe to the audience the various activities indicated in the format in a very logical manner. In one fraud case the jury was given a printed VIA chart where in summation the prosecutor was able to allow the jurors to follow his presentation more clearly. The material on the chart had already been allowed into testimony overriding any defense objections. The prosecutor not only got his conviction but the praise of trial judge for a job wail done.
symbols and definitions used in VIA are not unique in themselves but developed from networking or charting techniques previously used in business sand industry management. PERT (Program Evaluation Review Technique) and CPM (Critical Path Method) are two forms of charting that are extensively used to schedule, monitor and evaluate business projects or programs. PERT principles are primarily used in raking VIA charts In that In reconstructing crimes we are riot as interested in CPS which deals mostly with making sure that certain projects are completed by some future deadline. PERT while also useful in managing future projects lends Itself to charting events not on the basis of time per se but making certain that they occur in some logical order. PERT and CPM today are often used interchangeably and combined as one set of principles.
As Indicated in the above figure it can be seen that PERT/CPM involves futuristic applications for management of future projects whereas VIA is historical In the sense that it deals with reconstructing from beginning to end crimes that have occured in the past. VIA uses as tools the definitions and symbols used in PERT/CPM and Is therefore an offshoot of both of these processes.
VIA was used for the first time in the Robert Kennedy assassination by the Los Angeles Police Department. Previously PERT had been used for administrative projects but the principles were then used as a technique to handle ail the tremendous amounts of information collected during the investigation. The chart when completed circled some 80 feet around the room and charted the five days activities prier to the assassination of Robert Kennedy, tracing the path of Sirhan Sirhan relative to his involvement in the crime.
Following its first application as s law enforcement tool it was later used in many police investigations of a complex nature involving multiplicity of details and events. A few well known examples are noted below.
VIA was Introduced as a project to the California Department of Justice and was funded by LEAA In January of 1973. It was successfully used to many Investigations,. however, the grant expired In June of 1976. The technique is still being advocated as a useful tool In siding the Investigator to manage his often complicated collection of information. So called VIA experts are often difficult to find and departments should Initiate and find that expertise wlthin their own ranks. The use of the symbols is very simple and can be headily learned. The difficulty In making VIA charts is understanding the legal ramifications and determining the relevance of the collected information. The Investigator should already have some familiarity with these crucial considerations, making sure that information is avoided on the chart and yet making sure all the necessary elements for prosecution are included. During these next lessons we will concentrate on the symbols and definitions used in the VIA process. In using the techniques, we suggest a comfortable adaptation to your own needs with a certain degree of flexibility.. However, It Is easier to understand a VIA chart when standard symbols are used in that anyone being familiar with them can relate better to existing techniques.
GLOSSARY OF V.I.A. TERMS AND SYMBOLS
PERT Program Evaluation and Review Technique
PERT is a scientific management information system for planning, scheduling and controlling complex research and development p1rojects. It Is event oriented and makes use of a network to graphically display the sequence of occurrence, dependent relationships and estimated time durations for?all the activities in a project. It provides management with a systematic decision-making guide for monitoring the progress of a project.
VIA Visual Investigative Analysis
VIA Is a modified version of PERT/CPM that makes use of a network to graphically display the sequence of occurrence and dependent relationships of all the elements of a project. VIA Is a scientific management technique that assists in planning and controlling criminal investigations.
ACTIVITY
Activity is a time-consuming element of a project that must be performed. It is represented on the network by a line, or arrow, that connects two events.
EVENT
An event is a clearly defined project, milestone that occurs at a specific instance in time and designates the beginning and end of each activity. An event Is represented by an enclosed geometric symbol (usually a circle) . Every activity In a network must be preceded and succeeded by an event.
BURST
A burst Is an event that signifies, the concurrent Initiation of more than one activity. When the activity that precedes a burst its completed, the succeeding activities simultaneously begin.
MERGE
A merge is an event that signifies the concurrent completion of more then one activity. When all the activities that precede a merge are completed, the succeeding activity begins.
VIA USAGE
HISTORY OF VIA
VIA IN LAW ENFORCEMENT
Join the GlobalSecurity.org mailing list