Go to report table of contents
4.0 Developing a Security Strategy
4.1 Basis for Security Strategy
4.2 Phase 1 - Consider Options
4.2.1 Determine Level of Protection4.3 Phase 2 - Evaluate Countermeasures
4.2.2 Establish Functional Requirements
4.2.3 Identify and Select Countermeasures
4.3.1 Performance Characteristics4.4 Phase 3 - Develop Implementation Approach for Countermeasures
4.3.2 Proven Track Record in a Transit Environment
4.3.3 Future Agency Needs
4.3.4 Families of Technologies
4.3.5 Evaluate Cost Efficiency
4.4.1 Assess Implementation Approach4.5 Phase 4 - Implement Strategy
4.4.2 Select Implementation Approach
4.5.1 Implementation, Monitoring, Evaluation and Feedback
4.5.1.1 Tracking Security Effectiveness4.5.2 Take Corrective Action
Figure 4-1 Corresponding Threats to Level of Protection
Figure 4-2 Example of Families of Technologies for Exterior Sensors
How is this chapter useful? For transit managers and security staff it is a resource for
|
A security strategy lays out the actions that are necessary to move toward an integrated transit security system. An effective strategy is comprehensive and dynamic, with the flexibility to respond to any type or level of security threat. Accordingly, developing a security strategy is an iterative process that involves initial assessment, planning, implementation, and constant evaluation. It may include a combination of actions that counter possible threats and vulnerabilities: policies and procedures, access management measures, communications systems and technologies, and systems integration practices.
A transit agency may develop a security strategy proactively to meet the predefined requirements of its security plan, or reactively to address a particular security breach or deficiency.
This chapter describes design considerations for transit agencies as they navigate the process of developing and implementing a transit security strategy, including the implementation of security countermeasures.
go to top of the page4.1 Basis for Security Strategy
Agencies should consider preparing and implementing security strategies that are consistent with its comprehensive security plan and its threat and vulnerability assessment (TVA). The TVA can be used to help determine implementation priorities.
For guidance on preparing a security plan, refer to The Public Transportation System Security and Emergency Preparedness Planning Guide [FTA, 2003].
Transit agency managers should consider prioritizing risks through threat and vulnerability assessments and select sets of countermeasures that provide the best overall risk reduction for the system as a whole. Since funding for security efforts is limited, agencies must strive to ensure that protective security measures for each asset are equal to the threats and vulnerabilities of that particular asset and the potential consequences of an attack.
Although there is no prescriptive approach to developing a security strategy, agencies may consider the following four phase, iterative approach:
- Consider options
- Evaluate and select countermeasures
- Develop implementation approach for countermeasures
- Implement strategy
The Basis for a Security Strategy A comprehensive security plan is an overall approach for mitigating potential threats and vulnerabilities throughout the system. A threat and vulnerability assessment (TVA) identifies the sources and types of threats and the vulnerabilities within a transit agency's system. A TVA helps decision makers evaluate risks, identify priorities, and select solutions. Designing security into the system is easier and cheaper than patching it on later - security managers should be involved in the planning for all new construction and retrofit projects |
4.2 Phase 1 - Consider Options
This begins with a consideration of the agency's overall security goals (as defined in its comprehensive security plan), and understanding the extent they are being met. If the agency's security goals are not being met, the agency must determine what options along with countermeasures should be considered for adding additional levels of security. Security goals might range from the specific, such as hardening critical assets, to the general, such as diversifying redundancy.
Identifying countermeasures requires an agency to:
- Determine the appropriate levels of protection
- Establish functional requirements
- Analyze the necessary balance between cost, effectiveness, and efficiency while providing high quality service then identify and select countermeasures
4.2.1 Determine Level of Protection
Having assessed the problem, agencies should next consider the level of protection required for each of its assets, matching the level of protection with the level of threat. Factors that agencies may take into account include the importance of the asset, the likely method of attack, the type of perpetrator of potential attacks, the probability of attack, and the severity of the consequences. Figure 4 - 1 is a simplified diagram depicting the degree of countermeasures as they correspond to various levels of threat.
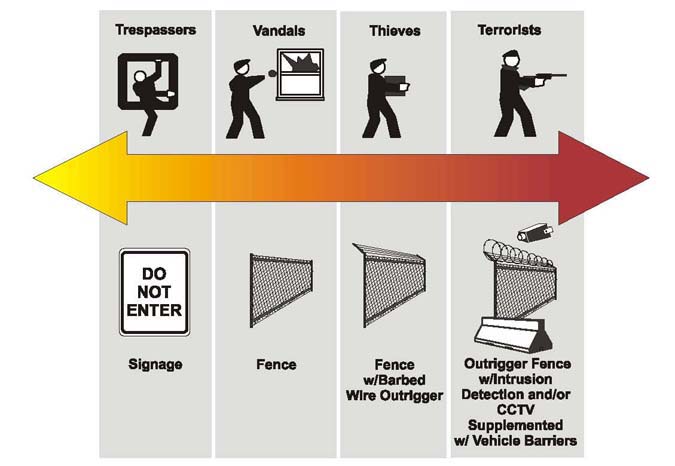 |
Figure 4-1. Corresponding Threats to Level of Protection |
4.2.2 Establish Functional Requirements
Based on the required level of protection and classifications, agencies should consider establishing the functional requirements for the security strategy. These are typically documented in the form of performance requirements but can also be driven by established security standards.
To supplement these transit security considerations, agencies may evaluate and adapt existing security standards and guidelines from other transit agencies, as well as other transportation and non-transportation sources. Examples of such sources (note, these are access management examples) include:
- Department of Health and Human Services (NIOSH) Publication No. 2002-139, Guidance for Protecting Building Environments from Airborne Chemical, Biological, Radiological Attacks 1
- ISO and IEC wireless technology standards for identification cards 14443 2 and 15693 3
- Department of State Vehicle Barrier Guidelines 4
- General Services Administration (GSA) Smart Card Interoperability Specification 5
- TSA Credentialing Guidelines 6
- FEMA risk management guidelines for potential terrorist attacks against building (FEMA 426 7) and commercial building design (FEMA 427 8)
- Illuminating Engineering Society of North America (IESNA) standards 9
Agencies should consider these standards and guidelines as starting points for developing security system performance requirements. Any security program adopted should be tailored to the needs of the particular organization.
1http://www.cdc.gov/niosh/bldvent/2002-139.html
2http://www.wg8.de/sd1.html#14443
3http://www.wg8.de/sd1.html#15693
4See Department of State (DOS) standard, SD-STD-02.01 Revision A, Specification For Vehicle Crash Test of Perimeter Barriers and Gates, dated March 2003 (latest revision) or 12 FAH 5, Foreign Affairs Handbook for more.
5http://csrc.nist.gov/publications/nistir/nistir-6887.pdf
6See http://www.tsa.gov/public/display?theme=68 for information.
7http://www.fema.gov/fima/rmsp426.shtm
8http://www.fema.gov/fima/rmsp427.shtm
4.2.3 Identify and Select Countermeasures
Security countermeasures can be technological or procedural and operational, and cover a wide range of sophistication, cost, and level of integration. Agencies should consider measures that are feasible, that address the identified problems, and that work within the existing security framework. Agencies should keep in mind that many countermeasures exist, and that a complete feasibility assessment of all alternatives can generate solutions that best fit that agency's needs. Measures such as staff training, appropriate facility design, and well-planned procedures may prove more effective and economical in some circumstances than high-tech admission control or vehicle control systems. It is likely that different parts of a single agency will have different needs, so the agency might rely on a combination of countermeasures to address multiple and conflicting requirements.
go to top of the page4.3 Phase 2 - Evaluate Countermeasures
Agencies should consider the following factors when selecting and evaluating countermeasures: performance characteristics, proven track record in a transit environment, future agency needs, families of technologies, and cost efficiencies.
go to top of the page4.3.1 Performance Characteristics
Security systems need to have a high degree of reliability. Agencies should consider evaluating established performance criteria, such as probability of detection, false alarm rates, and vulnerability to defeat. Agencies may also consider evaluating the potential for the selected technology to introduce new vulnerabilities into the system. Potential vulnerabilities may be inherent in a system, or be the result of poor installation or incorrect use. In either case the risk introduced by such vulnerabilities should be known, accepted, and addressed, where feasible, with other measures.
System characteristics, such as resistance of a component to compromise or counterfeiting, can be weighed against the criticality of the asset being protected and the perceived threat level. No system can be made completely secure; knowing the accompanying vulnerabilities is key to providing sensible protection with acceptable risks.
go to top of the page4.3.2 Proven Track Record in a Transit Environment
Security countermeasures should have a documented record of success, if possible within in a transit environment. Transit environments have unique operating characteristics and may place unusual requirements on security equipment, including:
- Environmental characteristics, such as a physically dirty environment, vibrations, electromagnetic interference (EMI), or weather exposure
- Assets distributed over wide area
- Open or public system
- Operational constraints (such as throughput requirements)
Agencies should consider factoring in the experiences of peer agencies and other security users when selecting equipment. Appendix B presents case studies of effective practices for security initiatives at three large U.S. transit agencies and a federal government (non-transit) agency.
go to top of the page4.3.3 Future Agency Needs
The countermeasures selected should meet the agency's current requirements and be consistent with the long-range goals of the agency's comprehensive security plan and strategy. When selecting security solutions, agencies should consider future needs and requirements, such as the potential for expansion, scalability, integration and upgrading. Technology factors to consider include:
- Ability to put multiple security functions on the same hardware platform
- Non-proprietary/off-the-shelf (OTS) software/equipment
- Support for data collection and storage
- Automated problem recognition
- Advanced software options for the operation of integrated controls and displays
- Ability to create single security user profiles used/enforced by multiple security applications
4.3.4 Families of Technologies
When selecting specific countermeasures, agencies should make themselves aware of the wide array of available options, which may have variations designed for different purposes or locations. Agencies should consider analyzing these technology differences within a single family to determine which variation best meets its particular needs. As an example, Figure 4 2 illustrates families of technologies for exterior sensors. Detailed advantages and disadvantages for many of these types of sensors are described in the TCRP Intrusion Detection for Public Transportation Facilities Handbook. 10
10Intrusion Detection for Public Transportation Facilities Handbook, Transit Cooperative Research Program (TCRP). March 2003.
 |
Figure 4-2 Example of Families of Technologies for Exterior Sensors |
4.3.5 Evaluate Cost Efficiency
Security is one of many transit system goals competing with operations, maintenance, and other departments for limited financial, staff, and material resources. It can be difficult to obtain adequate funding for security initiatives, since security is often viewed as a cost factor with no real return on investment for the enterprise. Agency security proponents can counter this view by identifying and championing the potential benefits of implementing a security system. This involves assessing the negative effects of a security breach and the associated costs.
Agencies should consider security costs that are in proportion to the value or criticality of the protected asset and the level of risk. In evaluating countermeasures, agencies should consider their costs, benefits, and effectiveness, and should invest funds and other resources accordingly.
The relative costs and benefits of different security components can be challenging to quantify. Agencies should consider the following security system lifecycle ownership and operation costs:
The Cost of a Security Breach
|
- Equipment and related component costs
- Acquisition and transportation of primary and related equipment
- Project management, including meetings and travel
- Permitting
- Professional architectural, engineering, and design fees
- Construction costs
- Site preparation/clearance
- Structural reinforcement as required to support the equipment
- Construction for environmental enclosures
- Rigging, electrical, HVAC
- Tie-in to existing systems
- Operational costs (labor, enrollment, data management, etc.)
- Operator training and certification; including required improvements in workforce skills
- Customization, integration, installation, testing
- Maintenance, monitoring, calibration/tuning and adjusting
Agencies should also consider the following direct and indirect benefits:
- Personnel efficiencies (particularly security personnel)
- Reduced liability
- Safety
- Terrorism prevention
- Crime prevention
- Criminal investigation and prosecution support
- Improved management control
- Operational advantages
If the available funding or resources are insufficient to implement a solution to address the existing threat/vulnerability, agencies should assess again which countermeasure or combination of countermeasures provide the solution that maximizes the amount of risk reduction within the project budget. Agency management should be made aware of any system vulnerabilities and take steps to manage or formally accept any residual risk.
go to top of the page4.4 Phase 3 - Develop Implementation Approach for Countermeasures
Once the agency identifies countermeasures they should assess and select an implementation approach.
4.4.1 Assess Implementation Approach
Agencies should consider assessing potential implementation approaches in terms of priorities, time, capital, resource constraints, and economies of scale. Implementation approaches may include:
- Targeting key problem areas first.
- Phasing in implementation (facility-by-facility approach; countermeasure-by-countermeasure approach).
- Developing a minimum level of security across the transit agency.
- Implementing stop-gap measures (temporary solutions leading to permanent solutions) starting with lower-cost options.
- Implementing incrementally (from an operations perspective, beginning with simpler technologies can give staff time to gain proficiency).
Agencies may find using an approach that uses pilot programs and operational tests can build support for a project, since early successes are documented and publicized, allowing a move toward wide-scale deployment after full management approval.
go to top of the page4.4.2 Select Implementation Approach
After analyzing security requirements and assessing the implementation options, agency management can then select an implementation approach, taking into account the following factors:
- The full life cycle cost of the solution(s) (it may be desirable to provide several solution options with a range of costs).
- The full costs of non-implementation (business interruption, recovery, liability, loss of ridership, publicity).
- Risks (risk must be communicated effectively - incident history / risk probability should be shown). Estimates of effectiveness (expected risk reduction).
Agencies should also consider evaluating both internal and external needs, resources, and constraints. Internal factors can include available capital, resources (staff availability, contract labor), time, political climate, mandates, policies, and competing projects and priorities. External factors can include privacy, safety, legal and regulatory issues, environmental concerns, and aesthetics.
go to top of the page4.5 Phase 4 - Implement Strategy
As with any other plan, agencies would do well to evaluate the effectiveness of countermeasures once they are implemented, to review vulnerabilities and strategies periodically, and to take corrective action where required in light of changing threats or additional information.
4.5.1 Implementation, Monitoring, Evaluation and Feedback
Having decided on which security countermeasures to implement, the next step is implementation, followed by an evaluation of how the countermeasures are performing. After the risks have been determined and the countermeasures have been chosen, agencies should continue to implement the security strategy by considering the procurement, training and evaluation methods necessary to support the plan. Such methods should reflect the cost, efficiency, and effectiveness decisions that were made previously, and should take advantage of the agency's local and regional partners.
Agencies should then adopt measures to evaluate the program, and the performance of the various components. Agencies should consider security systems from an operational and life-cycle perspective, reviewing then documenting new or modified security systems. Documentation can include approved schematics, wiring diagrams, drawings, and specifications, and logic analyses to ensure the systems work as intended and comply with specified requirements.
Agencies should consider regular maintenance, testing, and evaluation of security countermeasures at initial installation, whenever modifications, repairs, or maintenance that may affect the system is complete, and when programmable controllers (if applicable) have been reprogrammed, in accordance with agency guidelines and/or manufacturer instructions. Security breaches or incidents can be documented and analyzed.
go to top of the page4.5.1.1 Tracking Security Effectiveness
The current security environment at transit facilities is optimized by an on-going security process that establishes a continuous framework for linking strategic goals to tactical execution through performance measurement. Measuring effectiveness is a means of strengthening a security program. Agencies should consider establishing an analytical framework for assessing the effectiveness of security programs and systems over time. One approach consists of:
- Developing a performance plan to help evaluate the current effectiveness and levels of improvement in the security program based on established performance measures. This describes in detail how to conduct reviews of management and security controls in administrative and programmatic processes and applications.
- Establishing acceptable levels of performance for particular facilities, organizations or particular systems, and incorporating them into the agency's security controls.
- Performing random and scheduled reviews of the efficiency and effectiveness of security processes.
- Overseeing compliance with security standards and approved programs through a combination of inspections, tests, interviews, and record reviews.
- Measuring performance against standards to ensure expected standards are met and to drive process improvements.
- Building the capacity to gather and use performance information, possibly by using a data collection and reporting system.
- Developing security program performance reports to measure and document the effectiveness of security initiatives.
Security plans and strategies or their implementation may change:
|
Progress tracking is one of the most powerful benefits of implementing risk management as a closed-loop system. Agencies can use performance measures as tools to evaluate such security areas as management, legal, administrative, human resources, infrastructure and engineering. Appendix C lists typical performance measures by category, such as input, efficiency / effectiveness, adoption, outputs, extensiveness, quality, impact, and usefulness.
Measuring effectiveness can be challenging, since it is difficult to control what cannot be measured. Current security measurement efforts are often limited by data availability. Empirical data are difficult to obtain, uneven in quality, and not routinely collected or reported. It may take a major effort to define the data requirements and put processes in place to collect data. Agencies should consider developing a Performance Management Information System to collect performance data covering a wide variety of metrics, and use the data to identify and quantify performance indicators.
In addition to traditional methods for measuring and evaluating security, agencies should consider alternative methods such as security benchmarking studies. Benchmarking studies identify the industry best practices surrounding security issues that, when implemented, can improve overall operations and lead agencies to exceptional performance.
go to top of the page4.5.2 Take Corrective Action
Agencies should consider reviewing the results of monitoring, testing, and evaluation of new and existing security components either periodically or continuously, depending on the countermeasure. Results can be fed back into the risk management process for prioritization with other known vulnerabilities, and corrective actions taken as appropriate. For example, an agency may choose to update or upgrade various systems or subsystems, retrain a particular functional group of employees, reevaluate the vulnerability assessment, or reassess specific goals as part of restarting this process. Once implemented, the agency should consider updating the TVA to reflect the new measures.
go to top of the page
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

