Go to report table of contents
3.0 Security in the Transit Environment
3.1 Challenges
3.2 Threats and Countermeasures
3.2.1 ThreatsFigure 3 1. Transit System Assets
3.2.1.1 Arson3.2.2 Countermeasures
3.2.1.2 Explosives
3.2.1.3 Weapons of Mass Destruction
3.2.1.4 Violent Incidents and Hostage Situations
3.2.1.5 Tampering
3.2.1.6 Loss of Power
3.2.1.7 Transit Vehicle as a Weapon
3.2.1.8 Network Failure/Cyber Attack
3.2.1.9 Perpetrators
3.2.2.1 Deter
3.2.2.1 Detect
3.2.2.3 Minimize
3.2.2.4 Respond and Recover
Figure 3 2. Redirection of Blast Force
 |
Transit agencies share a common mission: to provide convenient, affordable transportation that is open, accessible, and available to all. Hundreds of thousands of people pass through bus stops and subway stations in America every hour, embodying the promise of the transit industry to equitably provide safe and reliable public transportation. Public transit systems cannot be closed off or tightly controlled like an airport without compromising their fundamental character. Security must be created in other ways, through physical modifications that don't impinge on the openness of the system (including accessibility as required under the American with Disabilities Act), through employee training and watchfulness, through passenger awareness and participation, and through careful planning for coordinated, efficient, and life-saving response.
Several recent trends highlight the dynamic nature of the transit industry and demonstrate the need for a security-oriented infrastructure. For instance, light rail is increasingly common in the United States, and more and more metropolitan areas are exploring the possibility of introducing bus rapid transit (BRT). These modes introduce new security concerns and needs that are different from the needs of traditional subway and bus systems. Both light rail and BRT operate above ground, making them vulnerable to close-range attack. Vehicles generally come equipped with large windows and doors, making them easily penetrable and open to attack from the outside. In addition, the increase in construction of light rail and BRT infrastructure means that more transit systems will be managing multiple vehicle modes, as systems expand into new neighborhoods and new lines of service with new types of vehicles. This gradual evolution adds to the complexity of protecting public transit assets, but also makes it possible for transit systems to include security considerations in their technical specifications for new vehicles. In some cases, this can be an efficient way to introduce security infrastructure, where retrofitting existing infrastructure can be difficult and costly. This chapter describes:
- Challenges to transit system security
- Threats and countermeasures
3.1 Challenges
The core challenge of addressing the vulnerabilities of a transit system is the degree of openness fundamental to public transit. Public transit agencies operate systems in which public access is crucial not only to daily operations but also to the fulfillment of the agency's mission, but it is difficult to secure and protect any area to which the public is allowed open access. Public transit infrastructure consists of a series of layered spaces, each increasingly closed to the public. The public areas of transit systems have complete and unchecked access, but other facilities are open only to agency employees, contractors, and vendors. In the new security paradigm, efforts must be made to use the technologies of credentialing and access control to ensure that the sensitive areas of systems are accessible only by those permitted to be there.
The high passenger volumes experienced by many transit agencies can add to a transit agency's security concerns. The high concentrations of people in contained spaces-whether it be a full bus crowded with standees, or a downtown subway platform at rush hour-make transit facilities inviting targets and provide another significant challenge for agencies to address. Transit systems must accommodate thousands of daily customers, sometimes 24 hours a day / 7 days a week in many of their facilities. Customers using transit systems may circulate near restricted areas such as tunnels, control rooms, utility rooms, power supplies, or hazardous-material storage areas.
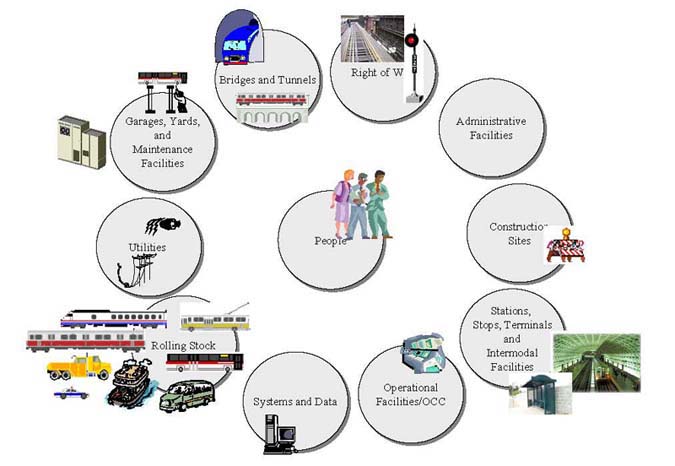 |
Figure 3 1. Transit System Assets
Security systems and strategies for transit environments must work in a wide variety of settings and be effective in protecting diverse asset types (see Figure 3 1). Transit agencies are constantly faced with the challenge of managing risks to their assets. Each asset has its own level of risk based on its attractiveness as a target, vulnerabilities, accessibility, and criticality to the system. The process of evaluating risk and implementing countermeasures designed to protect specific assets requires that transit agency managers prioritize risks through threat and vulnerability assessments and select sets of countermeasures that provide the best overall risk reduction for the system as a whole. Since funding for security efforts is limited, security measures for each asset must be commensurate with the threats and vulnerabilities of that particular asset and the potential consequences of an attack or other disaster.
The increased awareness of the need for security within public transit systems has challenged some of the basic tenets of public transit and has highlighted competing visions of the future of public transit in America. For example, considerations of security could potentially prompt a rethinking of the use of alternative fuels, long promoted as preferable to diesel fuel for environmental and public health reasons. Concerns about security may also generate debate about the current trend toward multimodal transportation facilities, which improve the efficiency and convenience of the transit network but may also be particularly vulnerable to a devastating attack. The demand for security-oriented design may also generate renewed interest in building redundancy into the construction of new transit infrastructure, where feasible, so that agencies can maintain services after an attack or disaster. These examples highlight the ways in which the evolving emphasis on security will need to be balanced against other, long-standing policy priorities.
3.2 Threats and Countermeasures
In the weeks and months that followed September 11, 2001, most transit agencies examined how terrorists could attack their systems. They tried to identify their weakest points, and where an attack would cause the greatest loss to passengers, employees, rolling stock, and facilities. Agency staff, contractors, or the FTA conducted structured assessments. Based on these assessments, the types of security threats that a transit system could face were identified and are described in this section.
The diversity of assets that may be part of a transit system leads to a range of possible threats and countermeasures. Some assets might be targets for a terrorist attack intended to inflict civilian injuries; others might be means for providing misinformation to the public, others for crippling mobility or economic activity within a city or metropolitan area or even for obtaining sensitive information about the system. Transit systems or their components could also be affected indirectly by an attack elsewhere, which may compromise communications, operations, or maintenance capabilities. Results of attacks or incidents might include:
- Loss of life or physical injury to transit riders, staff, and/or passers-by
- Physical damage to transit agency equipment or infrastructure, and possibly to the surrounding environment
- Loss of power through direct attack or by external event
- Failures outside the transit agency that affect operations - service delivery or maintenance
- Excessive traffic on communications networks Breach of communications or operations network security/hacking
3.2.1 Threats
While the threat against transit targets is only now gaining broad recognition, transit systems and railways have long been considered viable targets by terrorists. Throughout the 1980s public transit systems were targeted by some terrorists with the intention of inflicting heavy casualties, while others employed more subtle tactics aimed at disrupting transit service. Threats may result in attacks aimed directly at the transit agency, or those aimed at the environment within which an agency operates.
3.2.1.1 Arson
The hazards of arson, an intentionally set fire, in a transit facility include the destruction of assets within the facility, structural damage to the facility itself, and injuries or fatalities due to direct exposure to fire or to smoke and fumes. In a major fire, ambient temperature can surpass 1,800°F (1,000°C), which may result in structural damage, as well as electrical and mechanical systems failure. Burning fuel, oil, plastics, and some paints can cause dense smoke and toxic fumes. Toxic fumes present a serious health threat and may cause death by asphyxiation. In addition, smoke can reduce visibility, obscuring exit pathways and making escape more difficult for victims. Since fires may occur accidentally as well as intentionally, there is crossover between protection against accidental fires and protection from arson. Arson and explosion-related fires, however, may cause more severe damage because they tend to target or cluster around critical systems and equipment.
3.2.1.2 Explosives
The hazards of an explosive blast include the destruction of assets within a facility, structural damage to the facility itself, and injuries or fatalities. In addition, explosions may start a fire, which may inflict additional material damage, injuries, or fatalities due to direct exposure or to heat, smoke, and fumes. An explosion is an instantaneous or almost instantaneous chemical reaction resulting in a rapid release of energy. The energy is usually released as rapidly expanding gases and heat, which may be in the form of a fireball. The expanding gases compress the surrounding air creating a shock wave or pressure wave. The pressure wave can cause structural damage to the structure while the fireball may ignite other building materials leading to a larger fire. The strength of a blast depends on the type and amount of explosive material used. A bomb that a person can carry is capable of a smaller blast than an explosive-laden truck.
3.2.1.3 Weapons of Mass Destruction
Weapons of mass destruction (WMD) typically refer to nuclear, radiological, chemical, and biological weapons capable of inflicting mass casualties. WMD can also refer to radioactive materials and other contaminants intended to quickly harm large numbers of people, such as any powders, liquids, gases, and dirty bombs; most of these come in a liquid, vapor, gas, or powder form, and are spread through air movement.
The hazards of WMD include fatalities or deleterious health effects, as well as potentially permanent contamination of a facility that may render it unusable. Many agents have little or no plainly discernable characteristics, so symptoms may be the first sign that an attack has occurred. While some chemical agents induce immediate symptoms, other agents will not produce symptoms for hours after the attack. Some biological agents may have an incubation period of up to a few days before symptoms appear.
3.2.1.4 Violent Incidents and Hostage Situations
Violent confrontations by terrorists are common on transit systems throughout the world. These include assaults carried out on board transit vehicles or at transit facilities, with the intent of inflicting casualties, property damage, or both. Violent incidents may include the taking of hostages. Transit vehicles are especially vulnerable to hostage situations because of easy public access, remoteness of the vehicle, and available civilians onboard. Such attacks are meant to create widespread fear and apprehension through public displays of violence and the interruption of public services. Attackers may use a variety of weapons, including small arms, assault rifles, shoulder-mounted rocket-propelled grenades, knives or other bladed weapons, and small explosives.
3.2.1.5 Tampering
Tampering with transit facilities' assets may be a means to achieve any of the above events, such as starting a fire or spreading an airborne chemical agent, or it may be a stand-alone act, such as tampering with track to induce derailment. It can also include the intentional ramming of a facility, with a truck, boat, or airplane, in order to cause structural damage to a facility or injury to its users. The ramming vehicle may be laden with explosives. Depending on the situation, tampering may lead to asset damage, structural damage, contamination, injuries, and/or fatalities.
3.2.1.6 Loss of Power
Loss of electrical power, either locally or over a broad area, can pose a major problem for transit systems in the form of diminished or suspended operations control, computer-aided dispatch, and radio systems. Loss of electricity could be the result of an intentional attack or unintentional event-either within the agency or in the surrounding environment-but in any case could hinder a transit agency's ability to operate or communicate effectively. Apart from service impairment, loss of power may even inadvertently result in damage to property or persons within the agency, service area or in the vicinity.
3.2.1.7 Transit Vehicle as a Weapon
Transit vehicles should be viewed not only as targets, but as weapons as well. There can be a wide range of nefarious uses for both operational and retired vehicles. Perpetrators might attempt to hijack an operational vehicle in order to steer it into a building or bridge, or may plant explosives in the vehicle while in the storage yard in hopes of detonating it at a later time. They might also seek to steal or purchase a retired vehicle, counting on the innocuous nature of a public transit vehicle to set people at ease while they carry out various terrorist activities. Attacks might be directed at the vehicle itself, at the transit system, or at the surrounding environment.
3.2.1.8 Network Failure/Cyber Attack
Transit systems rely on computerized networks to facilitate operations and enhance efficient service delivery, which makes them vulnerable to network failure and cyber attacks. While this document does not offer specific considerations on how to protect computer networks, it is crucial to understand their importance to operating and communicating among agency staff as well as with partner organizations and the public-at-large. Network failure may be caused by faulty or damaged internal components, direct cyber attack to the agency's network, direct attack to a peripheral system or network, or even a blanket computer virus. The result may be loss of communications or operations capabilities as well as misinformation by hacking into a Web site or server.
3.2.1.9 Perpetrators
Transit systems are susceptible to attack by perpetrators hoping to destroy transit property or city environments, to inflict mass casualties, or simply create a nuisance through misinformation or disrupted service. Agencies should attempt to protect themselves against the lone terrorist carrying a bomb or container of sarin gas in a backpack, as well as the cadre of terrorists coordinating to hijack a transit vehicle for more nefarious purposes. Perpetrators may be highly knowledgeable about transit operations generally or at a specific agency (they may even originate within the agency) or they may be ignorant of system operations altogether. Transit agencies or authorities hoping to be successful at providing a high level of security should consider combinations of countermeasures that would address the range of perpetrators attempting to impose a range of threats on the agency or its operating environment.
3.2.2 Countermeasures
It is difficult to prepare for terrorist attacks or other emergencies that might require a coordinated response because such incidents are largely unpredictable. The problems experienced in one emergency may be different during the next. With each new event, agency personnel may be confronted with a shifting set of problems to handle. However, lessons from prior events suggest the following types of strategies help protect a transit system from the effects of a terrorist attack:
- Hardening against a physical attack
- Redundancy, with both duplication and variety
- Backup power supplies
- Prioritization service and dedicated lines
- Network and cyber security
The principal strategies to counter terrorist attacks can be grouped into efforts to (1) deter attackers from attempting an attack; (2) detect potential threats promptly; (3) minimize the impact from an attack; and (4) respond and recover (or resume critical operations as quickly as possible). Applying these concepts to the physical design of infrastructure leads to several general strategies that are applicable to transit assets. Every transit agency faces a particular set of circumstances and needs; no single security strategy is appropriate for every agency. Each agency should consider its operations, infrastructure and communications needs, threat assessments, budget, and existing systems to determine which combinations of countermeasures best fit its circumstances.
3.2.2.1 Deter
CPTED
The concept of Crime Prevention through Environmental Design (CPTED) has evolved as a means to reduce the opportunities for crimes to occur. This is accomplished by employing physical design features that discourage crime, while at the same time encouraging legitimate use of the environment. CPTED design considerations, which have been employed in recent years by transit agencies in the design of safer public facilities, such as transit stations and bus stops, are transferable to endeavors to secure and harden elements of an agency's infrastructure from terrorist attacks. Major elements of the CPTED concept are defensible space, territoriality, surveillance, lighting, landscaping, and physical security planning.
Access Management
Controlling who (or what) may access restricted areas and assets in the system plays an important role in protecting transit infrastructure from all of the major threats identified in this section. A core principle of access management is that valuable assets are protected behind multiple "layers" of secure spaces, with security measures becoming more stringent for deeper layers. Access control may focus on discerning between employees and visitors, on maintaining locks, on screening for weapons, or on barring unauthorized vehicle entry to a transit property. Access management techniques may include procedures and policies, physical barriers, identification and credentialing technology, security personnel, communications systems, surveillance, and intrusion-detection systems.1
Surveillance
Surveillance can include closed-circuit televisions, security personnel, or vigilant vehicle operators or station clerks, who are often the first line in security measures. The presence of agency staff can deter an attack. The presence of surveillance equipment acts as a deterrent not only because an area is being watched remotely, but also because activities are recorded and intruders are aware of the possibility of detection and capture. Surveillance is also useful in warding off attacks against remote, unmanned infrastructure, such as communications towers and power substations. Transit agencies should consider what combination of equipment and personnel are needed to achieve optimal security coverage. Placement should be based on the volume of human and vehicular traffic, the layout of the watched or guarded asset, as well as the location of any blindspots resulting from overlapping or peripheral areas.
1See "Access Management Guidelines for Transit" (FTA/DOT) for more information.
3.2.2.2 Detect
Weapons Detectors and Screeners
Weapons detectors and screeners can be used to detect the presence of both tangible weapons, such as traditional or radiological explosives, and to identify more intangible ones, such as damaging chemicals. Metal detectors can be used in administrative or operations centers or sensors placed in areas of a station to gauge levels of a particular gas and/or agency staff can be charged with randomly screening the bags of transit riders in search of nefarious items. Weapons detectors can help in both preventing attacks and capturing the perpetrator(s).
Intrusion Detection
Devices aimed at detecting unwanted or unauthorized persons or vehicles are helpful in protecting multiple forms of assets. Such devices may detect motion in an unmanned area or passage into a restricted area gained by tampering with a security device. Such methods are useful in access management for unmanned infrastructure as well as for administration or operations centers. These devices may sound an alarm at the site of the intrusion and/or send a silent alarm to a desk in the operations center or security headquarters. When intrusion-detection devices are used in remote or unmanned areas, they should be carefully configured to account for the natural movement of items in the surrounding environment, such as animals or wind-blown objects.
Site/building Layout
The physical characteristics of a site have affected the selection of security measures for safeguarding a facility. Some of these characteristics, such as building location, landscaping, and site circulation are under the control of the transit agency; off-site features such as topography and abutting uses, are not. Some on-site characteristics such as topography and vegetation are under limited control of the transit agency. Proper placement and orientation of buildings and other structures on the site is a major component of an effective security strategy to protect against damage from terrorist attacks. Three fundamental considerations are unobstructed space, standoff distances, and building orientation.
3.2.2.3 Minimize
Facility Hardening/Resiliency
Although prevention is the best strategy, minimizing potential damage in case of an event is also important, as no system can be made 100-percent foolproof. Strategies that harden a facility are those that nullify or minimize the effects of an attack when it occurs. Examples include blast-resistant structural engineering that enables a building to remain standing after a blast, and the use of non-flammable materials that hinders the spread of fire. These efforts may serve to protect both the infrastructure itself and the safety of its users.
Standoff Distances
Since the effective quantity of explosives and distance from the target are the most important factors in determining the destructive effect of an explosion, standoff distances, especially for larger vehicles, are an essential technique for minimizing the risk of damage to a target from a blast. Potentially explosive-laden vehicles should be kept as far away from would-be targets as possible. Standoff distances also diminish the risk of intentional ramming, and help create a safety zone that visibly exposes any transgressors and enhances surveillance.
 |
Trash bins designed to force a blast upwards may help protect nearby people and property. |
Figure 3 2. Redirection of blast force |
Redirection of Blast Force
The impact of an attack can be mitigated by implementing methods of redirecting potentially harmful forces in a direction that will cause less damage or injury, should a blast occur. Assets that are specifically risky can be designed to "blow" away from individuals. For example, trash bins can be built to direct a blast detonated from within upwards rather than outwards (see Figure 3 2). Proper design strategies also avoid creating spaces that will concentrate or "throttle" the force from a blast, such as alleyways, overhangs, or other enclosed spaces.
Redundancy and Dispersion of Assets
All essential systems, such as vehicle monitoring and control, electricity, and fire suppression, should be safeguarded with redundant systems in case of damage or destruction of the primary system. Whenever possible, these duplicate systems should be located at different sites or at different places within the same facility. In addition, key assets and personnel at a single facility should be dispersed throughout the site, so they cannot be disabled by a single attack. Though this might conflict with desires for a unified approach operating from a unified center, loss of multiple coordinating personnel can seriously hinder an agency's ability to effectively manage an emergency situation and/or recover from its effects.
3.2.2.4 Respond and Recover
Emergency Response Features
Lives may be saved in an emergency if physical systems are designed to facilitate rapid evacuation or to shelter people in place while enabling quick entry by responders. Site layout can incorporate exits that are easy for users to locate and access. Technical solutions can include planning independent energy sources for emergency lighting and communications systems, and installing detection alarm systems that promptly signal an emergency situation.
Decontamination Awareness/Materials Selection
Recovery from a chemical or biochemical attack can be difficult. Certain types of materials may speed up the decontamination process or reduce the lingering effects of the agent used in the attack. For example, materials that are porous, such as vehicle carpeting or mesh-screened walls in stations, are more difficult to sanitize and can trap chemical agents within the material. This may prolong the decontamination process or force removal of the material altogether. Agencies may choose to minimize or restrict use of construction materials and components that are less susceptible to decontamination in the event of a chemical, biological, or radiological incident, or perhaps minimize their usage in certain areas. Agencies may also consider educating staff and designer/engineer on decontamination processes and chemicals in order to minimize the post-incident cleanup time and possibly the impacts.
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

