FM 34-45: Tactics, Techniques, and Procedures for Electronic Attack
Chapter 4
Decide
DECIDE, as the first step in the targeting process, provides the overall focus and sets priorities for fires (to include EA) and a portion of intelligence collection. Many key personnel and organizations are involved in DECIDE. They perform a number of structured processes against the framework of the MDMP to plan the use of lethal and nonlethal fires for each phase of the operation.
Based on targeting priorities, the targeting team and other organizations will produce graphics and text tools to maintain focus on the process and synchronize the effects. Planning EA within the MDMP framework as a portion of DECIDE is comprised of five interrelated processes as shown in Figure 4-1.
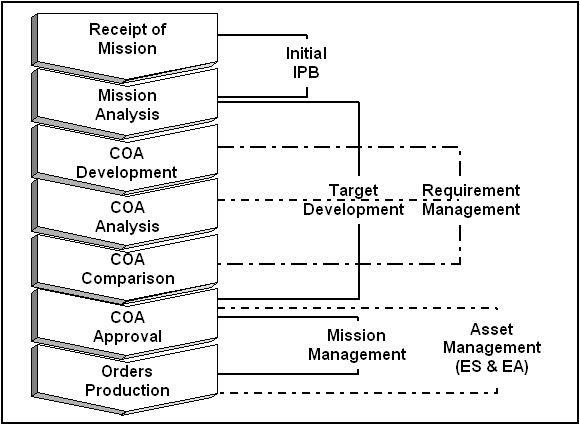
Figure 4-1. Planning EA.
INTELLIGENCE PREPARATION OF THE BATTLEFIELD
4-1. The initial IPB, as a subordinate step to mission analysis (the second step of the MDMP), starts the important analysis that eventually leads to EA planning. In terms of EA planning, the two most important products out of the IPB process (and into target development) are HVTs and EW analysis products. Figure 4-2 illustrates how IPB fits into EA planning. |
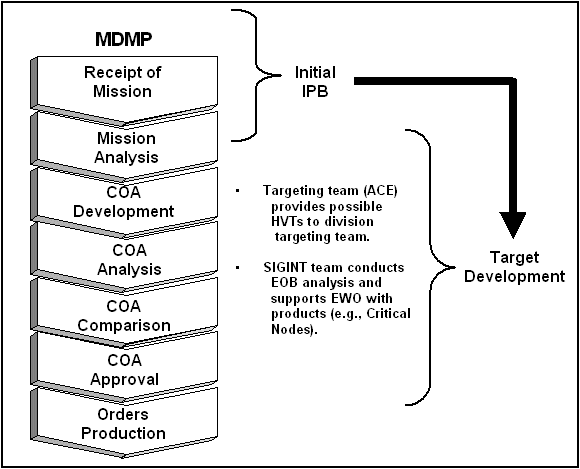
Figure 4-2. IPB in EA Planning.
HIGH-VALUE TARGETS
4-2. An important part of step 3 of the IPB process (evaluate the threat) is creating or updating threat models. A component of the threat model is generic HVTs. As the G2 Plans Officer provides the framework for the initial IPB (in order to support operational planning), the different portions of the ACE support the production of threat courses of action (COAs) and other IPB products. As the ACE develops threat COAs, the targeting team (ACE) analyzes the generic HVTs. Then they capture the most important HVTs for that particular threat COA into an HVTL. The targeting team (to include the EWO) uses the HVTL to help develop HPTs after the wargame. HVTs are not specific or unique to EW; they support the entire targeting process. |
EW ANALYSIS PRODUCTS
4-3. The SIGINT team, as part of both ongoing situation development and analytical support to IPB, uses the threat order of battle (OB) and HVTs (from the targeting team) to prepare net diagrams and other graphic planning and execution products. These products help the EWO identify critical communications nodes. These critical nodes are essential to the threat in order to use the EM spectrum. The EWO depends on assistance from the SIGINT team (through the collection manager) to ensure all HVT net diagrams are further broken down to show unique nodes that will disrupt the entire net if "jammed." These nodes become the initial candidates for EA targets. |
TARGET DEVELOPMENT
4-4. During COA analysis (wargaming), threat COAs are analyzed in terms of their impact on friendly COAs. The wargame takes place using an action or reaction technique. The entire staff identifies the enemy battlefield functions that must be attacked. The commander and his staff analyze the criticality of friendly operating systems in the context of a specific COA. The G3 identifies the best places to attack HPTs in relation to the friendly COA; these places are designated TAIs. TAIs are points or areas where the friendly commander can influence the action by lethal or nonlethal fires and/or maneuvers. This manual discusses only those aspects that are most important to describing EA planning. FM 6-20-10 and FM 34-130 provide comprehensive doctrine for target development. 4-5. The targeting team uses two important products (besides threat COAs and the supporting products) from the IPB process for target development— HVTs and EW analysis products. After target development, the three most important products that flow into RM and MM are the HPTL, AGM, and EA portion of the battlefield operating system synchronization matrix. Figure 4-3 illustrates how target development fits into EA planning. |
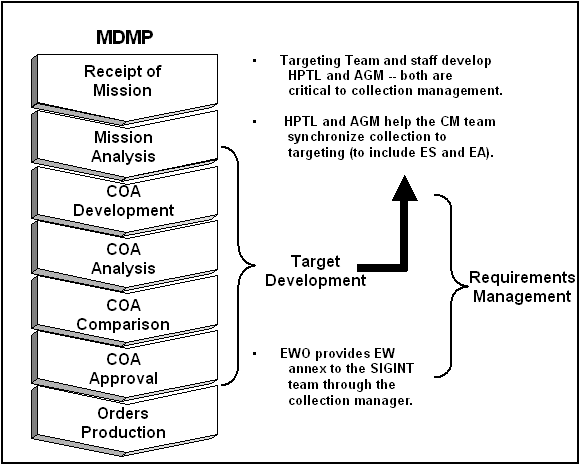
Figure 4-3. Target Development in EA Planning.
HIGH-PAYOFF TARGETS
4-6. Through wargaming the staff identifies the HPTs that must be acquired and attacked for the friendly mission to succeed. During COA analysis, the targeting team develops the HPTL, the targeting portion of the DST, and BOS synchronization matrixes. (This provides times for EA (non-lethal fire.)) For example, during the close fight, enemy artillery could be the priority for lethal and nonlethal fires. From this target set, specific HPTs (for example, an artillery battalion fire direction center [FDC]) is designated for lethal and nonlethal attack for a synergistic effect. The battalion FDC would be engaged with EA to disrupt coordination of fires by causing critical delays during the battle and would eventually be engaged by lethal attack (in accordance with the HPTL, AGM, and the TSS) for destruction. (For a more detailed discussion of the wargaming process, see FM 101-5.) |
ATTACK GUIDANCE AND DAMAGE CRITERIA
4-7. Knowing target vulnerabilities and the effect an attack will have on enemy operations allows a staff to propose the most efficient available attack option. The commander provides critical guidance by stating that he wants to disrupt, delay, limit, damage, or destroy the threat. 4-8. The FSCOORD will provide the EWO with a desired level of damage or degradation. The EWO determines if current EA assets are able to range the target and achieve the mission, and how the mission will take place to achieve the desired effect. |
EFFECTS OF FIRE
4-9. On the basis of the targeting team's guidance, the EWO recommends how each EA target should be engaged in terms of the effects of fire and attack options to use. The effects of fire can be to deny, disrupt, delay, and divert the target. The unique nature of EA, a non-lethal fire, and subjective use of these terms means the EWO must clearly communicate the intent of the terminology to both the targeting team and the collection manager. When applied to EA, these terms differ from when applied to describe physical destruction as defined in FM 6-20-10. The following criteria are captured in the AGM and EW annex. |
Disrupt
4-10. Disrupt is designed to fragment the target's nets. This disruption will in turn cause the flow of information to slow, and in some cases stop the flow, until the net control stations can reinitiate the net and its users. When the enemy will attack, this tactic is effective as they move to LD. This tactic is simple to initiate and requires little coordination. |
Delay
4-11. Delay is designed to fragment movements and deny the threat the ability to communicate in order to change routes. This tactic will necessitate the use of alternate forms of communication to continue movement (for example, hand-and-arm signals, runners). This effort will cause significant delays to the threat's movement, especially if tied in with obstacles. Denying the threat the ability to warn other units of obstacles will cause all follow-on units the same delay and could force the lead element to clear the obstacles without engineer support. |
Divert
4-12. Divert is designed to prevent the target's use of critical resources. This method is used to jam combat support (CS) element's communication with combat units (for example, jamming combat service support [CSS] trucks on their way to an armor refueling or rearming point). Divert is a difficult task due to the intelligence required to pinpoint targets and upcoming events. |
Deny
4-13. Deny is designed to control the EM spectrum and prevent the threat's use of that spectrum for any communications (whether voice or digital). This nonlethal fire is used at surge periods to act as a battlefield multiplier. The success of this fire denies the threat's ability to receive intelligence and to pass guidance. These actions in turn place a "stress" on EA assets and cannot be maintained for long periods. |
EW TARGETS
4-14. The EWO helps develop the EW targets as an integrated portion of the HPTL. The three categories these targets fall into— planned, as acquired, and immediate— are discussed below. |
Planned
4-15. For EW the actual target is the specific communication emitters that are critical to that target set during a specific military operation. The AGM as well as the BOS synchronization matrix will have these targets listed. |
As Acquired
4-16. EA teams will engage these targets of opportunity upon detection. |
Immediate
4-17. Targets (in the form of specific voice and data communications) are targets that the EWO did not or could not plan but that the targeting team identifies during the conduct of the operation and that require immediate EA. |
ADDITIONAL ANALYSIS
4-18. The EWO then analyzes these requirements (in terms of effects and category) to further plan the EA necessary to service the target. He must determine the rough plan based on-
4-19. The EWO analyzes whether organic assets can perform the mission. If not, the EWO requests support from higher through G3 and FS channels. He must also notify the collection manager when he requests support from higher in order to keep ES and EA synchronized between echelons. |
TARGETING PRODUCTS (WITH EA FULLY INTEGRATED)
4-20. The EWO prepares documentation for the missions:
4-21. The EWO must prepare these documents to ensure the synchronization of lethal and nonlethal fires and the synchronization of EA with CM (this includes all three subprocesses-RM, MM, and AM). The end product of this process is the EW annex. |
REQUIREMENTS MANAGEMENT
4-22. After target development, the most important products that flow into RM and MM are the HPTL and AGM. The most important products that flow out of RM into MM are the SIR (that the collection manager designates for ES) that support EA. Figure 4-4 illustrates how RM fits into EA planning. 4-23. During RM the collection manager performs a critical role by-
|
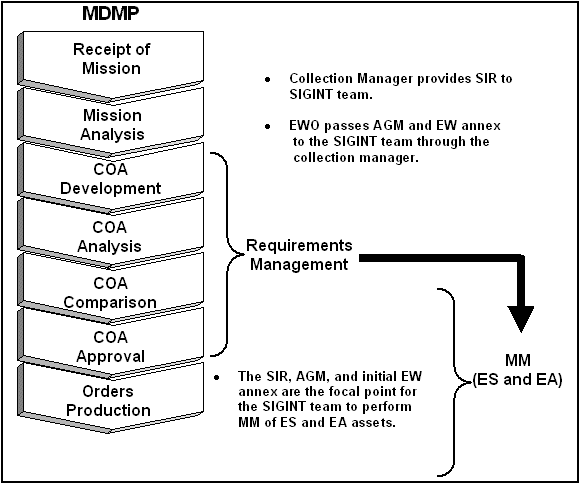
Figure 4-4. Requirements Management in EA Planning.
4-24. During wargaming the commander and entire staff determine decision points (DPs). When tied to targeting, the DPs ensure the decision to engage (or not to engage) occurs at the proper time. DPs and TAIs are recorded on the DST and are included in the intelligence collection plan. Wargaming helps finalize, among other products, the—
|
PRIORITY INTELLIGENCE REQUIREMENTS
4-25. The commander designates his PIR following the wargame. Generally, a PIR should support each HPT or TAI (if the staff plans to engage multiple HPTs within a TAI). This rule ensures that the commander prioritizes collection against HPTs. A latest time intelligence is of value (LTIOV) is a critical part of every PIR. This time (or event in certain circumstances) ensures that friendly collection does not occur after the point when that intelligence is not of use to the commander and friendly forces. |
SPECIFIC INFORMATION REQUIREMENTS
4-26. The collection manager initially combines, validates, and prioritizes PIR and IR and prioritizes these sets of requirements. He then he refines these requirements into SIR that are clear, concise, and a "collectible" subset of the larger requirement. The collection manager takes the time to cross-check the HPT-related PIR against the SIR that support these HPTs. He ensures that there are adequate SIR (especially related to ES) to support the EA as captured on the AGM. The SIGINT team helps the collection manager perform this step because of their expertise in EW. Then the collection manager hands the ES-related SIR over to the SIGINT team. At the same time, the collection manager is capturing ES collection on the ISM. |
MISSION MANAGEMENT
4-27. After RM, both MM and AM begin. In terms of MM, the most important products that are introduced into the process are the AGM (from target development) and the SIR (from RM). The most important products that flows out of MM are the specific taskings down to individual ES and EA assets. During MM the SIGINT team continues the CM process that started with RM. Figure 4-5 illustrates how MM fits into EA planning. FM 34-2 provides doctrine and TTP for MM. |
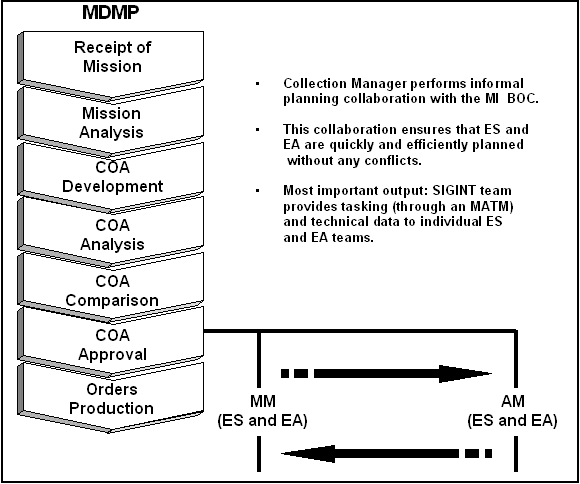
Figure 4-5. Mission Management in EA Planning.
REEVALUATE TARGET ANALYSIS AND IDENTIFY ADDITIONAL ES COLLECTION REQUIREMENTS
4-28. The G2 Plans Officer initially develops the sensor attack matrix, which is further developed during wargaming. The final signal attack matrix, which is developed by the SIGINT team, is used to determine the sensor to detect and locate targets. This matrix will also determine if the resources are available to detect, locate, and engage a specific target. The collection manager will use this matrix to task intelligence assets in locating targets. 4-29. The SIGINT team examines the analysis performed during target development and reevaluates if any subsequent analysis is necessary against the target. (NOTE: The SIGINT team continually provides intelligence in an easy-to-use format to ensure the EWO chooses valid EA targets during target development.) 4-30. The SIGINT team identifies (and later tasks) ES collection based on the SIR. In order to identify and track the critical communications nodes, the SIGINT team uses its EW analysis (using All-Source Analysis System [ASAS] workstations) and the latest OB and situation development intelligence from the all-source team. |
DETERMINE EA VIABILITY
4-31. The SIGINT team ensures that organic assets can perform the mission. If not, the EWO requests support from higher through G3 and FS channels. Additionally, the SIGINT team reviews the AGM, SIR, any guidance from the EWO, and the EWO's initial development of the EW annex. The EWO checks for any fragmentary orders (FRAGOs) that may have changed EA or ES missions. There are two important substeps to determine the viability of EA:
|
ASSESS EA SYSTEM AVAILABILITY
4-32. The determination of availability is based upon three basic sets of information:
|
DETERMINE ATTACK RESOURCES AND SELECT POINT OF ATTACK
4-33. Based on the attack guidance and effects of fire (as captured in the AGM and EW annex), the SIGINT team validates the target and the amount and type of EA necessary. The SIGINT team balances each target against the total workload on the EA and ES assets and determines the best assets to perform missions (they will task these assets later). With guidance from the EWO, the SIGINT team prioritizes all missions and targets. 4-34. The SIGINT team creates alternate targets (at least one to each primary target). The SIGINT team designates the number of assets used on each target and any time coverage is necessary to jump assets forward. At this point, main targets are "locked in" while alternate targets are "plotted in" to ensure the mission is feasible. |
EM SPECTRUM DECONFLICTION
4-35. The EWO and SIGINT team perform several actions with the support of the G6 to ensure that EA missions do not adversely affect friendly forces' use of the EM spectrum. The SIGINT team gathers data on higher and adjacent units' EW targets and assesses what impact (if any) these actions will have on organic missions and vice versa. This same step is performed with the tasking for EA. The SIGINT team will use the RFL to capture any conflicts between friendly communications and EA missions. Finally, the SIGINT team will determine if any interference will occur, taking into effect the harmonics from the EA mission and, if interference does occur, which task is the priority. |
ESTABLISH JAMMING CONTROLS
4-36. The SIGINT team establishes both positive and negative controls on EA assets. It establishes a "stop jam" frequency and states procedures for "stop jam" in case of a loss of communications. The SIGINT team also ensures that the communication frequency is not in the harmonics of the target frequency (if using single channel). |
TASK ES AND EA ASSETS
4-37. The SIGINT team tasks ES and EA assets through the multiple assets tasking message (MATM), which is sent digitally or by voice if the asset does not have the capability to receive digital tasking. The MATM for EA assets will contain technical and mission data necessary to accomplish the mission. Technical data will include callsigns, jargon, jump callsigns, signal strength (in Watts), stop jam frequency, and radio procedures to include threat procedures to follow in case of jamming. Mission data will include primary target, time of attack, alternate targets, and targets of opportunity. The MATM for ES assets will include technical data and mission data. The technical data for ES assets will mirror that for EA. Mission data for EA will include SIR, PIR, and the specific EA systems to cue on targets in accordance with the times detailed in the ISM. |
ASSET MANAGEMENT
4-38. After RM, both MM and AM begin. In terms of AM, the most important products that are produced are the chain of orders (normally an initial OPORD then subsequent FRAGOs) that deploy and provide the framework for ES and EA operations. Figure 4-6 illustrates how AM fits into EA planning. FM 34-2 provides doctrine and TTP for MM. (Refer to Appendix D for message formats.) |
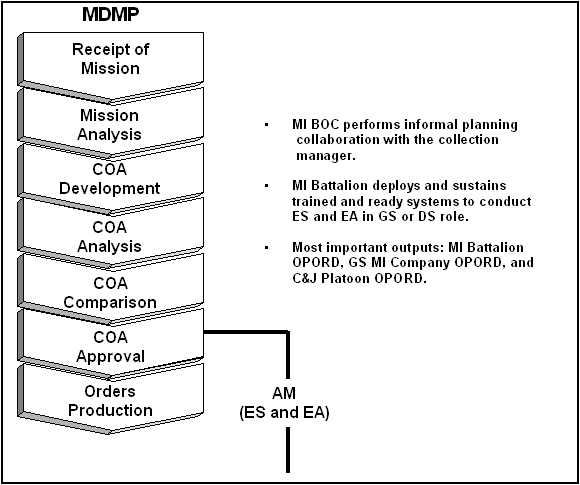
Figure 4-6. Asset Management in EA Planning.
4-39. The MI battalion commander and his Battalion Operations Center (BOC) (coordinating with the collection manager) task organizes EA and ES assets and coordinates the movement of EA and ES systems in order to support EA and ES tasking as developed by the SIGINT team during MM. This task includes planning to provide continuous coverage on the targets while other EA and ES systems move. |
|
NEWSLETTER
|
| Join the GlobalSecurity.org mailing list |
|
|
|

